Database Security Threats and Challenges
Ieee account.
- Change Username/Password
- Update Address

Purchase Details
- Payment Options
- Order History
- View Purchased Documents
Profile Information
- Communications Preferences
- Profession and Education
- Technical Interests
- US & Canada: +1 800 678 4333
- Worldwide: +1 732 981 0060
- Contact & Support
- About IEEE Xplore
- Accessibility
- Terms of Use
- Nondiscrimination Policy
- Privacy & Opting Out of Cookies
A not-for-profit organization, IEEE is the world's largest technical professional organization dedicated to advancing technology for the benefit of humanity. © Copyright 2024 IEEE - All rights reserved. Use of this web site signifies your agreement to the terms and conditions.
Database security refers to the range of tools, controls and measures designed to establish and preserve database confidentiality, integrity and availability. Confidentiality is the element that’s compromised in most data breaches.
Database security must address and protect the following:
- The data in the database.
- The database management system (DBMS).
- Any associated applications.
- The physical database server or the virtual database server and the underlying hardware.
- The computing or network infrastructure that is used to access the database.
Database security is a complex and challenging endeavor that involves all aspects of information security technologies and practices. It’s also naturally at odds with database usability. The more accessible and usable the database, the more vulnerable it is to security threats; the more invulnerable the database is to threats, the more difficult it is to access and use. This paradox is sometimes referred to as Anderson’s Rule (link resides outside ibm.com).
Get insights to better manage the risk of a data breach with the latest Cost of a Data Breach report.
Register for the X-Force Threat Intelligence Index
By definition, a data breach is a failure to maintain the confidentiality of data in a database. How much harm a data breach inflicts on your enterprise depends on various consequences or factors:
- Compromised intellectual property: Your intellectual property—trade secrets, inventions, proprietary practices—can be critical to your ability to maintain a competitive advantage in your market. If that intellectual property is stolen or exposed, your competitive advantage can be difficult or impossible to maintain or recover.
- Damage to brand reputation: Customers or partners might be unwilling to buy your products or services (or do business with your company) if they don’t feel they can trust you to protect your data or theirs.
- Business continuity ( or lack thereof): Some businesses cannot continue to operate until a breach is resolved.
- Fines or penalties for non-compliance: The financial impact for failing to comply with global regulations such as the Sarbannes-Oxley Act (SAO) or Payment Card Industry Data Security Standard (PCI DSS), industry-specific data privacy regulations such as HIPAA, or regional data privacy regulations, such as Europe’s General Data Protection Regulation (GDPR) can be devastating, with fines in the worst cases exceeding several million dollars per violation .
- Costs of repairing breaches and notifying customers: In addition to the cost of communicating a breach to customer, a breached organization must pay for forensic and investigative activities, crisis management, triage, repair of the affected systems and more.
Many software misconfigurations, vulnerabilities or patterns of carelessness or misuse can result in breaches. The following are among the most common types or causes of database security attacks.
Insider threats
An insider threat is a security threat from any one of three sources with privileged access to the database:
- A malicious insider who intends to do harm.
- A negligent insider who makes errors that make the database vulnerable to attack.
- An infiltrator, an outsider who somehow obtains credentials via a scheme, such as phishing or by gaining access to the credential database itself.
Insider threats are among the most common causes of database security breaches and are often the result of allowing too many employees to hold privileged user access credentials.
Human error
Accidents, weak passwords, password sharing and other unwise or uninformed user behaviors continue to be the cause of nearly half (49%) of all reported data breaches .
Exploitation of database software vulnerabilities
Hackers make their living by finding and targeting vulnerabilities in all kinds of software, including database management software. All major commercial database software vendors and open source database management platforms issue regular security patches to address these vulnerabilities, but failure to apply these patches in a timely fashion can increase your exposure.
SQL or NoSQL injection attacks
A database-specific threat, these involve the insertion of arbitrary SQL or non-SQL attack strings into database queries that are served by web applications or HTTP headers. Organizations that don’t follow secure web application coding practices and perform regular vulnerability testing are open to these attacks.
Buffer overflow exploitation
Buffer overflow occurs when a process attempts to write more data to a fixed-length block of memory than it is allowed to hold. Attackers can use the excess data, which is stored in adjacent memory addresses, as a foundation from which to start attacks.
Malware is software that is written specifically to take advantage of vulnerabilities or otherwise cause damage to the database. Malware can arrive via any endpoint device connecting to the database’s network.
Attacks on backups
Organizations that fail to protect backup data with the same stringent controls that are used to protect the database itself can be vulnerable to attacks on backups.
These threats are exacerbated by the following:
- Growing data volumes: Data capture, storage and processing continues to grow exponentially across nearly all organizations. Any data security tools or practices need to be highly scalable to meet near and distant future needs.
- Infrastructure sprawl : Network environments are becoming increasingly complex, particularly as businesses move workloads to multicloud or hybrid cloud architectures, making the choice, deployment and management of security solutions ever more challenging.
- Increasingly stringent regulatory requirements: The worldwide regulatory compliance landscape continues to grow in complexity, making adhering to all mandates more difficult.
- Cybersecurity skills shortage: Experts predict there might be as many as 8 million unfilled cybersecurity positions by 2022 .
Denial of service (DoS and DDoS) attacks
In a denial of service (DoS) attack, the attacker deluges the target server—in this case the database server—with so many requests that the server can no longer fulfill legitimate requests from actual users, and, often, the server becomes unstable or crashes.
In a distributed denial of service attack (DDoS), the deluge comes from multiple servers, making it more difficult to stop the attack.
Because databases are network-accessible, any security threat to any component within or portion of the network infrastructure is also a threat to the database, and any attack impacting a user’s device or workstation can threaten the database. Thus, database security must extend far beyond the confines of the database alone.
When evaluating database security in your environment to decide on your team’s top priorities, consider each of the following areas:
- Physical security: Whether your database server is on-premises or in a cloud data center, it must be located within a secure, climate-controlled environment. If your database server is in a cloud data center, your cloud provider takes care of this for you.
- Administrative and network access controls: The practical minimum number of users should have access to the database, and their permissions should be restricted to the minimum levels necessary for them to do their jobs. Likewise, network access should be limited to the minimum level of permissions necessary.
- User account and device security: Always be aware of who is accessing the database and when and how the data is being used. Data monitoring solutions can alert you if data activities are unusual or appear risky. All user devices connecting to the network housing the database should be physically secure (in the hands of the right user only) and subject to security controls at all times.
- Encryption: All data, including data in the database and credential data, should be protected with best-in-class encryption while at rest and in transit. All encryption keys should be handled in accordance with best practice guidelines.
- Database software security: Always use the latest version of your database management software, and apply all patches when they are issued.
- Application and web server security: Any application or web server that interacts with the database can be a channel for attack and should be subject to ongoing security testing and best practice management.
- Backup security: All backups, copies or images of the database must be subject to the same (or equally stringent) security controls as the database itself.
- Auditing: Record all logins to the database server and operating system, and log all operations that are performed on sensitive data as well. Database security standard audits should be performed regularly.
In addition to implementing layered security controls across your entire network environment, database security requires you to establish the correct controls and policies for access to the database itself. These include:
- Administrative controls to govern installation, change and configuration management for the database.
- Preventive controls to govern access, encryption, tokenization and masking.
- Detective controls to monitor database activity monitoring and data loss prevention tools. These solutions make it possible to identify and alert on anomalous or suspicious activities.
Database security policies should be integrated with and support your overall business goals, such as protection of critical intellectual property and your cybersecurity policies and cloud security policies . Ensure that you have designated responsibility for maintaining and auditing security controls within your organization and that your policies complement those of your cloud provider in shared responsibility agreements. Security controls, security awareness training and education programs, and penetration testing and vulnerability assessment strategies should all be established in support of your formal security policies.
Today, a wide array of vendors offer data protection tools and platforms. A full-scale solution should include all of the following capabilities:
- Discovery: Look for a tool that can scan for and classify vulnerabilities across all your databases—whether they’re hosted in the cloud or on-premises—and offer recommendations for remediating any vulnerabilities that are identified. Discovery capabilities are often required to conform to regulatory compliance mandates.
- Data activity monitoring: The solution should be able to monitor and audit all data activities across all databases, regardless of whether your deployment is on-premises, in the cloud, or in a container . It should alert you to suspicious activities in real-time so that you can respond to threats more quickly. You’ll also want a solution that can enforce rules, policies and separation of duties and that offers visibility into the status of your data through a comprehensive and unified user interface. Make sure that any solution you choose can generate the reports you need to meet compliance requirements.
- Encryption and tokenization capabilities: Upon a breach, encryption offers a final line of defense against compromise. Any tool that you choose should include flexible encryption capabilities that can safeguard data in on-premises, cloud, hybrid or multicloud environments. Look for a tool with file, volume and application encryption capabilities that conform to your industry’s compliance requirements, which might demand tokenization (data masking) or advanced security key management capabilities.
- Data security optimization and risk analysis: A tool that can generate contextual insights by combining data security information with advanced analytics will enable you to accomplish optimization, risk analysis and reporting with ease. Choose a solution that can retain and synthesize large quantities of historical and recent data about the status and security of your databases, and look for one that offers data exploration, auditing and reporting capabilities through a comprehensive but user-friendly self-service dashboard.
Continuous edge-to-edge cloud protection for your data and applications with regulatory compliance.
Wide visibility, compliance and protection throughout the data security lifecycle.
Comprehensive data protection for the most critical enterprise data.
Learn more about data organization in the cloud.
Now in its 17th year, the 2022 Cost of a Data Breach report shares the latest insights into the expanding threat landscape and offers recommendations for how to save time and limit losses.
In this introduction to networking, learn how computer networks work, the architecture used to design networks, and how to keep them secure.
Learn how the IBM Security Guardium family of products can help your organization meet the changing threat landscape with advanced analytics, real-time alerts, streamlined compliance, automated data discovery classification and posture management.
- Search Menu
- Editor's Choice
- Author Guidelines
- Submission Site
- Open Access
- About Journal of Cybersecurity
- Editorial Board
- Advertising and Corporate Services
- Journals Career Network
- Self-Archiving Policy
- Journals on Oxford Academic
- Books on Oxford Academic

Editors-in-Chief
Tyler Moore
About the journal
Journal of Cybersecurity publishes accessible articles describing original research in the inherently interdisciplinary world of computer, systems, and information security …
Latest articles

Call for Papers: Workshop on the Economics of Information Security
Journal of Cybersecurity is inviting submissions to a new special issue from the workshop on the economics of information security. Authors whose papers appeared at the workshop are invited to submit a revised version to the journal.

Call for Papers
Journal of Cybersecurity is soliciting papers for a special collection on the philosophy of information security. This collection will explore research at the intersection of philosophy, information security, and philosophy of science.
Find out more

Submit your paper
Join the conversation moving the science of security forward. Visit our Instructions to Authors for more information about how to submit your manuscript.

High-Impact Research Collection
Explore a collection of freely available high-impact research from 2020 and 2021 published in the Journal of Cybersecurity .
Browse the collection here

Email alerts
Register to receive table of contents email alerts as soon as new issues of Journal of Cybersecurity are published online.

Read and Publish deals
Authors interested in publishing in Journal of Cybersecurity may be able to publish their paper Open Access using funds available through their institution’s agreement with OUP.
Find out if your institution is participating
Related Titles

Affiliations
- Online ISSN 2057-2093
- Print ISSN 2057-2085
- Copyright © 2024 Oxford University Press
- About Oxford Academic
- Publish journals with us
- University press partners
- What we publish
- New features
- Open access
- Institutional account management
- Rights and permissions
- Get help with access
- Accessibility
- Advertising
- Media enquiries
- Oxford University Press
- Oxford Languages
- University of Oxford
Oxford University Press is a department of the University of Oxford. It furthers the University's objective of excellence in research, scholarship, and education by publishing worldwide
- Copyright © 2024 Oxford University Press
- Cookie settings
- Cookie policy
- Privacy policy
- Legal notice
This Feature Is Available To Subscribers Only
Sign In or Create an Account
This PDF is available to Subscribers Only
For full access to this pdf, sign in to an existing account, or purchase an annual subscription.
database security Recently Published Documents
Total documents.
- Latest Documents
- Most Cited Documents
- Contributed Authors
- Related Sources
- Related Keywords
NETWORK DATABASE SECURITY WITH INTELLECTUAL ACCESS SUPERVISION USING OUTLIER DETECTION TECHNIQUES
Comparison of performance rot13 and caesar cipher method for registration database of vessels berthed at p.t. samudera indonesia.
Database security is a very important aspect of an information system. A general information is onlyintended for certain groups. Therefore, it is very important for a company to prevent database leakage sothat the information contained in it does not fall to unauthorized people. Cryptographic technique is an alternative solution that can be used in database security. One way to maintain the security of the database is to use encryption techniques. The method used to secure the database is encryption using the ROTI3 and Caesar Cipher methods. Both of these methods have advantages in processing speed. For thisreason, the author will compare the use of the two algorithms above in terms of the encryption and decryption process time
A Novel Framework for Efficient Multiple Signature on Certificate with Database Security
Abstract PKI gives undeniable degree of safety by transferring the key pair framework among the clients. By constructing, a PKI we combine digital identities with the digital signatures, which give an end-to-end trust model. Basically, PKI is an attempt, which can simulate the real-world human analyzation of identity and reliability in a computerized fashion. In any case, the existing applications are centered on a tight trust model which makes them inadequate as an overall device for trust examination. After years of research, development and deployment, PKI still facing strong technical and organizational challenges such as attacks against Certificate Authorities (CA). CAs are the primitive component of PKIs which plays powerful role in the PKI model. CA must be diligent, creditable and legitimate. In any case, a technocrat who picks up control on a CA can use CA's certificate to issue bogus certificate and impersonate any site, such as - DigiNotar, GobalSign, Comodo and DigiCert Malaysia. In this paper we proposed an approach to reduce the damage of compromised CA/CA’s key by imposing Multiple Signatures (MS) after verifying/authenticating user’s information. One single compromised CA is not able to issue a certificate to any domain as multiple signatures are required. Private key and other perceptive information are stored in the form of object/blob. Without knowing the structure of class no one can access the object and object output stream. Proposed MS achieve better performance over existing MS schemes and control fraudulent certificate issuance with more database security. The proposed scheme also avoids MITM attack against CA who is issuing certificate to whom which is using the following parameters such as identity of Sender, Receiver, Timestamp and Aadhar number.
A guiding framework for enhancing database security in state-owned universities in Zimbabwe
Technique for evaluating the security of relational databases based on the enhanced clements–hoffman model.
Obtaining convincing evidence of database security, as the basic corporate resource, is extremely important. However, in order to verify the conclusions about the degree of security, it must be measured. To solve this challenge, the authors of the paper enhanced the Clements–Hoffman model, determined the integral security metric and, on this basis, developed a technique for evaluating the security of relational databases. The essence of improving the Clements–Hoffmann model is to expand it by including a set of object vulnerabilities. Vulnerability is considered as a separate objectively existing category. This makes it possible to evaluate both the likelihood of an unwanted incident and the database security as a whole more adequately. The technique for evaluating the main components of the security barriers and the database security as a whole, proposed by the authors, is based on the theory of fuzzy sets and risk. As an integral metric of database security, the reciprocal of the total residual risk is used, the constituent components of which are presented in the form of certain linguistic variables. In accordance with the developed technique, the authors presented the results of a quantitative evaluation of the effectiveness of the protection of databases built on the basis of the schema with the universal basis of relations and designed in accordance with the traditional technology of relational databases.
Hybrid Security Approach for Database Security using Diffusion based cryptography and Diffie-Hellman key exchange Algorithm
Application of network database security technology based on big data technology, database security in a dynamic it world.
Databases are vulnerable. Public statements by Target, Home Depot, and Anthem following their extremely advertised data breaches are each uniform and succinct on how their breaches unfolded: unauthorized access to those systems that ultimately led to the extraction of sensitive information. A comprehensive strategy to secure a database is over data security. Usually, security events will be related to the later action: illegitimate access to data confidentiality damage, injury to the integrity of knowledge, loss of data accessibility (Discover). Loss of privacy of data, creating them accessible to others without a right of access is not visible within the database and does not need changes deductible database. This paper addresses these events to confirm database security.
A Review of Database Security Concepts, Risks, and Problems
Currently, data production is as quick as possible; however, databases are collections of well-organized data that can be accessed, maintained, and updated quickly. Database systems are critical to your company because they convey data about sales transactions, product inventories, customer profiles, and marketing activities. To accomplish data manipulation and maintenance activities the Database Management System considered. Databases differ because their conclusions based on countless rules about what an invulnerable database constitutes. As a result, database protection seekers encounter difficulties in terms of a fantastic figure selection to maintain their database security. The main goal of this study is to identify the risk and how we can secure databases, encrypt sensitive data, modify system databases, and update database systems, as well as to evaluate some of the methods to handle these problems in security databases. However, because information plays such an important role in any organization, understanding the security risk and preventing it from occurring in any database system require a high level of knowledge. As a result, through this paper, all necessary information for any organization has been explained; in addition, also a new technological tool that plays an essential role in database security was discussed.
Database protection model based on security system with full overlap
Security is one of the most important characteristics of the quality of information systems in general and databases, as their main component, in particular. Therefore, the presence of an information protection system, as a complex of software, technical, cryptographic, organizational and other methods, means and measures that ensure the integrity, confidentiality, authenticity and availability of information in conditions of exposure to natural or artificial threats, is an integral feature of almost any modern information system and database. At the same time, in order to be able to verify the conclusions about the degree of security, it must be measured in some way. The paper considers a database security model based on a full overlap security model (a covered security system), which is traditionally considered the basis for a formal description of security systems. Thanks to expanding the Clements-Hoffman model by including a set of vulnerabilities (as a separately objectively existing category necessary to describe a weakness of an asset or control that can be exploited by one or more threats), which makes it possible to assess more adequately the likelihood of an unwanted incident (threat realization) in a two-factor model (in which one of the factors reflects the motivational component of the threat, and the second takes into account the existing vulnerabilities); a defined integral indicator of database security (as a value inverse to the total residual risk, the constituent components of which are represented in the form of the corresponding linguistic variables); the developed technique for assessing the main components of security barriers and the security of the database as a whole, based on the theory of fuzzy sets and risk, it becomes possible to use the developed model to conduct a quantitative assessment of the security of the analyzed database.
Export Citation Format
Share document.
TechRepublic

8 Best Data Science Tools and Software
Apache Spark and Hadoop, Microsoft Power BI, Jupyter Notebook and Alteryx are among the top data science tools for finding business insights. Compare their features, pros and cons.

EU’s AI Act: Europe’s New Rules for Artificial Intelligence
Europe's AI legislation, adopted March 13, attempts to strike a tricky balance between promoting innovation and protecting citizens' rights.

10 Best Predictive Analytics Tools and Software for 2024
Tableau, TIBCO Data Science, IBM and Sisense are among the best software for predictive analytics. Explore their features, pricing, pros and cons to find the best option for your organization.

Tableau Review: Features, Pricing, Pros and Cons
Tableau has three pricing tiers that cater to all kinds of data teams, with capabilities like accelerators and real-time analytics. And if Tableau doesn’t meet your needs, it has a few alternatives worth noting.

Top 6 Enterprise Data Storage Solutions for 2024
Amazon, IDrive, IBM, Google, NetApp and Wasabi offer some of the top enterprise data storage solutions. Explore their features and benefits, and find the right solution for your organization's needs.
Latest Articles

Top 10 CRM Features and Functionalities
Discover the top CRM features for business success. Explore a curated list of key capabilities to consider when choosing the right CRM solution, including marketing tools, activity tracking and more.


Combatting Deepfakes in Australia: Content Credentials is the Start
The production of deepfakes is accelerating at more than 1,500% in Australia, forcing organisations to create and adopt standards like Content Credentials.

The Top 5 Pipedrive Alternatives for 2024
Discover the top alternatives to Pipedrive. Explore a curated list of CRM platforms with similar features, pricing and pros and cons to find the best fit for your business.

The Australian Government’s Manufacturing Objectives Rely on IT Capabilities
The intent of the Future Made in Australia Act is to build manufacturing capabilities across all sectors, which will likely lead to more demand for IT skills and services.

Udemy Report: Which IT Skills Are Most in Demand in Q1 2024?
Informatica PowerCenter, Microsoft Playwright and Oracle Database SQL top Udemy’s list of most popular tech courses.

Gartner: 4 Bleeding-Edge Technologies in Australia
Gartner recently identified emerging tech that will impact enterprise leaders in APAC. Here’s what IT leaders in Australia need to know about these innovative technologies.

Llama 3 Cheat Sheet: A Complete Guide for 2024
Learn how to access Meta’s new AI model Llama 3, which sets itself apart by being open to use under a license agreement.

Zoho vs Salesforce (2024): Which CRM Is Better?
Look at Zoho CRM and Salesforce side-by-side to compare the cost per functionality and top pros and of each provider to determine which is better for your business needs.

9 Innovative Use Cases of AI in Australian Businesses in 2024
Australian businesses are beginning to effectively grapple with AI and build solutions specific to their needs. Here are notable use cases of businesses using AI.

How Are APAC Tech Salaries Faring in 2024?
The year 2024 is bringing a return to stable tech salary growth in APAC, with AI and data jobs leading the way. This follows downward salary pressure in 2023, after steep increases in previous years.

Anthropic Releases Claude Team Enterprise AI Plan and iOS App
The enterprise plan seeks to fill a need for generative AI tools for small and medium businesses. Plus, a Claude app is now on iOS.

Top Tech Conferences & Events to Add to Your Calendar in 2024
A great way to stay current with the latest technology trends and innovations is by attending conferences. Read and bookmark our 2024 tech events guide.

TechRepublic Premium Editorial Calendar: Policies, Checklists, Hiring Kits and Glossaries for Download
TechRepublic Premium content helps you solve your toughest IT issues and jump-start your career or next project.

IBM Acquires HashiCorp for $6.4 Billion, Expanding Hybrid Cloud Offerings
The deal is intended to strengthen IBM’s hybrid and multicloud offerings and generative AI deployment.

6 Best Enterprise CRM Software for 2024
Freshsales, Zoho CRM and Pipedrive are among the top enterprise CRM software that organize and automate data workflows to help achieve businesses’ client management goals in 2024.
Create a TechRepublic Account
Get the web's best business technology news, tutorials, reviews, trends, and analysis—in your inbox. Let's start with the basics.
* - indicates required fields
Sign in to TechRepublic
Lost your password? Request a new password
Reset Password
Please enter your email adress. You will receive an email message with instructions on how to reset your password.
Check your email for a password reset link. If you didn't receive an email don't forgot to check your spam folder, otherwise contact support .
Welcome. Tell us a little bit about you.
This will help us provide you with customized content.
Want to receive more TechRepublic news?
You're all set.
Thanks for signing up! Keep an eye out for a confirmation email from our team. To ensure any newsletters you subscribed to hit your inbox, make sure to add [email protected] to your contacts list.
We've detected unusual activity from your computer network
To continue, please click the box below to let us know you're not a robot.
Why did this happen?
Please make sure your browser supports JavaScript and cookies and that you are not blocking them from loading. For more information you can review our Terms of Service and Cookie Policy .
For inquiries related to this message please contact our support team and provide the reference ID below.
Cloud data security for distributed embedded systems using machine learning and cryptography
- Original Research
- Published: 07 May 2024
Cite this article

- Sadaf Bashir 1 ,
- Zahrah Ayub 1 &
- M. Tariq Banday ORCID: orcid.org/0000-0001-8504-5061 1
Explore all metrics
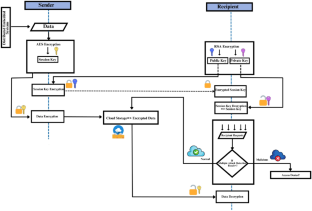
In the growing demand for distributed embedded systems that efficiently execute complex processes and high-end applications, safeguarding sensitive data is imperative. The landscape of security threats, cyber-attacks, and associated challenges has reached unprecedented sophistication and magnitude. Whether you are an individual, an organization, or a company invested in distributed embedded systems, your paramount concern revolves around protecting invaluable data. In this digital age, data security is genuinely where the wealth resides. This paper introduces a novel framework for securing the sensitive data of distributed embedded systems. The framework comprises five stages, each contributing to an efficient and robust data security approach. Additionally, this work proposes developing an efficient Multiple Attack Detection model using a supervised machine-learning system. The targeted cyber-attacks include phishing, malware, Distributed Denial-of-Service (DDoS), and DNS over HTTPS attacks. Each targeted cyber-attack is trained on eight supervised machine learning classifiers. The classifier exhibiting the best overall performance in evaluation metrics (accuracy, recall, precision, and F1-score) is integrated into the proposed Multiple Attack Detection model. Furthermore, this paper explores deploying a machine learning-based Multiple Attack Detection model to a cloud environment using Streamlit Cloud.
This is a preview of subscription content, log in via an institution to check access.
Access this article
Price includes VAT (Russian Federation)
Instant access to the full article PDF.
Rent this article via DeepDyve
Institutional subscriptions
Research data policy and data availability
The data supporting this study's findings are available from the corresponding author upon reasonable request.
Yen T-Y, Wolf W (1995) Communication synthesis for distributed embedded systems. In: Proc. IEEE Int. Conf. Comput. Aided Des., pp 288–294
Sentilles W, Vulgarakis A, Bureš T, Carlson J, Crnković I (2008) A component model for control-intensive distributed embedded systems. In: Int. Symp. Component-Based Softw. Eng., pp 310–317
Ghugar U, Pradhan J, Bhoi SK, Sahoo RR, Panda SK (2018) PL-IDS: physical layer trust based intrusion detection system for wireless sensor networks. Int J Inf Technol 10(4):489–494. https://doi.org/10.1007/S41870-018-0147-7/METRICS
Article Google Scholar
Kamaldeep, Malik M, Dutta M (2023) Feature engineering and machine learning framework for DDoS attack detection in the standardized internet of things. IEEE Internet Things J 10(10):8658–8669
Beigh BM (2015) Framework for choosing best intrusion detection system. BVICA M’s Int J Inf Technol 7(1):821–827
Google Scholar
Streamlit. https://streamlit.io/cloud . Accessed 17 Feb 2024
Fairosebanu AA, Jebaseeli ACN (2023) Data security in cloud environment using cryptographic mechanism. Bull Electr Eng Inform 12(1):462–471
Jabbar AA, Bhaya WS (2023) Security of private cloud using machine learning and cryptography. Bull Electr Eng Inform 12(1):561–569
Gajra N, Khan SS, Rane P (2014) Private cloud security: secured user authentication by using enhanced hybrid algorithm. In: 2014 International Conference on Advances in Communication and Computing Technologies (ICACACT 2014), pp 1–6
Anwer M, Khan SM, Farooq MU, Waseemullah W (2021) Attack detection in IoT using machine learning. Eng Technol Appl Sci Res 11(3):7273–7278
Saghezchi FB, Mantas G, Violas MA, Manuel de Oliveira Duarte A, Rodriguez J (2022) Machine learning for DDoS attack detection in industry 4.0 CPPSs. Electronics 11(4):602
Banadaki YM, Robert S (2020) Detecting malicious dns over https traffic in domain name system using machine learning classifiers. J Comput Sci Appl 8(2):46–55
Yeboah-Ofori A (2020) Classification of malware attacks using machine learning in decision tree. Int J Secur 11(2):10–25
Nishitha U, Kandimalla R, Vardhan RM, Kumaran U (2023) Phishing detection using machine learning techniques. In: 2023 3rd Asian Conference on Innovation in Technology (ASIANCON), pp 1–6
Zebin T, Rezvy S, Luo Y (2022) An explainable AI-based intrusion detection system for DNS over HTTPS (DoH) attacks. IEEE Trans Inform Forensics Secur 17:2339–2349
Zhou X, Tang X (2011) Research and implementation of RSA algorithm for encryption and decryption. In: Proceedings of 2011 6th international forum on strategic technology, pp 1118–1121
Gebrye H, Wang Y, Li F (2023) Traffic data extraction and labeling for machine learning based attack detection in IoT networks. Int J Mach Learn Cybern 14(7):2317–2332
Elijah AV, Abdullah A, JhanJhi NZ, Supramaniam M, Abdullateef B (2019) Ensemble and deep-learning methods for two-class and multi-attack anomaly intrusion detection: an empirical study. Int J Adv Comput Sci Appl. https://doi.org/10.14569/IJACSA.2019.0100969
Pei J, Chen Y, Ji W (2019) A DDoS attack detection method based on machine learning. J Phys Conf Ser 1237:032040
Prathap A, Mounika L, Reethika M, Navya N, Sahithi RS (2023) Phishing website detection using machine learning models. Mach Learn 52(4):1140-1145
Kishore N, Sharma S (2016) Secured data migration from enterprise to cloud storage-analytical survey. BVICA M’s Int J Inf Technol 8(1):965
Anjana, Singh A (2019) Security concerns and countermeasures in cloud computing: a qualitative analysis. Int J Inf Technol 11(4):683–690. https://doi.org/10.1007/s41870-018-0108-1
Tan CL. Phishing dataset for machine learning: feature evaluation. Mendeley Data. https://www.kaggle.com/datasets/shashwatwork/phishing-dataset-for-machine-learning . Accessed 17 Feb 2024
Mukherjee A. Automated-malware-analysis. GitHub. https://github.com/Anustup900/Automated-Malware-Analysis/blob/master/dataset_malwares.csv . Accessed 17 Feb 2024
Kumbam YR. APA-DDoS dataset. Kaggle. https://www.kaggle.com/datasets/yashwanthkumbam/apaddos-dataset . Accessed 17 Feb 2024
Shatoori M, Reza M, Davidson L, Kaur G, Lashkari AH (2020) Detection of doh tunnels using time-series classification of encrypted traffic. In: 2020 IEEE international conference on dependable, autonomic and secure computing, pp 63–70
Yavuz FY, Ünal D, Gül E (2018) Deep learning for detection of routing attacks in the internet of things. Int J Comput Intell Syst 12(1):39–58
Fowdur TP, Baulum BN, Beeharry Y (2020) Performance analysis of network traffic capture tools and machine learning algorithms for the classification of applications, states and anomalies. Int J Inf Technol 12:805–824
Singh P (2021) Deploy machine learning models to production. Springer, Cham
Book Google Scholar
Download references
Department of Science and Technology, Government of India, supported the research work through its FIST Program. Grant Number: SR/FST/ET-1/2019/445(C).
Author information
Authors and affiliations.
Department of Electronics and Instrumentation Technology, University of Kashmir, Srinagar, India
Sadaf Bashir, Zahrah Ayub & M. Tariq Banday
You can also search for this author in PubMed Google Scholar
Contributions
All authors contributed to reviewing the literature, devising research hypotheses, conducting experiments, and writing and revising the manuscript.
Corresponding author
Correspondence to M. Tariq Banday .
Ethics declarations
Conflict of interest.
The Authors declare that they do not have any conflict of interest.
Human and animal rights
This article contains no studies with human participants or animals performed by authors.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
Reprints and permissions
About this article
Bashir, S., Ayub, Z. & Banday, M.T. Cloud data security for distributed embedded systems using machine learning and cryptography. Int. j. inf. tecnol. (2024). https://doi.org/10.1007/s41870-024-01892-0
Download citation
Received : 16 January 2024
Accepted : 18 April 2024
Published : 07 May 2024
DOI : https://doi.org/10.1007/s41870-024-01892-0
Share this article
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
- Distributed embedded systems
- Cloud storage
- Hybrid encryption- decryption
- Machine learning
- Cyber-attacks
- Cloud deployment
- Find a journal
- Publish with us
- Track your research
Journal of Materials Chemistry C
Development of high-performance direct x-ray detector materials: from hybrid halide perovskites to all-inorganic lead-free perovskites.
X-rays Detection plays a vital role in medical imaging, industrial defect detection, security screening and scientific research. Direct X-ray detectors are of greater interest to researchers because they offer the advantages of faster imaging, higher resolution and simpler construction than indirect detectors. Due to their intrinsic properties, traditional materials have inherent problems that limit their performance in detector applications. Perovskite is a new material with excellent properties that has great potential in the field of X-ray detectors. This paper summaries the research progress of perovskite materials in the field of X-ray detectors. First, the problems of traditional materials are listed according to the principle and material requirements of X-ray detectors. Then, the problems and challenges of different types of perovskite materials are divided from the classification of perovskite materials, from organic to inorganic materials, and from halide perovskite to lead-free perovskite. The intention is to provide ideas for the development of more environmentally friendly and higher performance X-ray detectors.
- This article is part of the themed collection: Journal of Materials Chemistry C Recent Review Articles
Article information
Download citation, permissions.
X. Wu, A. Li, M. Yang, X. Hao, L. Wu, R. Su and J. Zhang, J. Mater. Chem. C , 2024, Accepted Manuscript , DOI: 10.1039/D4TC00423J
To request permission to reproduce material from this article, please go to the Copyright Clearance Center request page .
If you are an author contributing to an RSC publication, you do not need to request permission provided correct acknowledgement is given.
If you are the author of this article, you do not need to request permission to reproduce figures and diagrams provided correct acknowledgement is given. If you want to reproduce the whole article in a third-party publication (excluding your thesis/dissertation for which permission is not required) please go to the Copyright Clearance Center request page .
Read more about how to correctly acknowledge RSC content .
Social activity
Search articles by author.
This article has not yet been cited.
Advertisements

IMAGES
VIDEO
COMMENTS
The goal of this study was accomplished by evaluating the current state of DB privacy and suggesting areas that needed further research work. With the SMS, researchers may better connect the data from literary research to a series of questions [34, 35].SMS is a descriptive investigation that involves picking and putting combine all published research articles associated with a particular ...
This SMS study aimed to identify the most up-to-date research in database security and the different challenges faced by users/clients using various databases from a software engineering ...
By synthesizing existing research, this review aims to contribute to the advancement of database security and assist organizations in protecting their sensitive data. Components and working ...
Explore the latest full-text research PDFs, articles, conference papers, preprints and more on DATABASE SECURITY. Find methods information, sources, references or conduct a literature review on ...
With the growth and increasing sophistication of the Internet and the increasing dependence, it appeared more and more services over the Internet-based database, so it increases the risks facing databases. The number of attacks against these repositories has also increased. A database danger refers to an item, individual or other entity that poses a risk of misuse or manipulation of ...
Database security refers to the range of tools, controls and measures designed to establish and preserve database confidentiality, integrity and availability. Confidentiality is the element that's compromised in most data breaches. The data in the database. The database management system (DBMS). Any associated applications.
The article first presents an attack model and the main relevant challenges of data security, encryption overhead, key management, and integration footprint. Next, the article reviews related academic work on alternative encryption configurations pertaining to encryption locus; indexing encrypted data; and key management.
Journal of Applied Security Research Volume 18, 2023 - Issue 3. Submit an article Journal homepage. 549 ... This study evaluates mechanisms to secure relational databases against security vulnerabilities and utilized PostgreSQL and Microsoft SQL Server due to data breach incidences reported across the world. Emulation experiments with ...
Cybercrime is estimated to have cost the global economy just under USD 1 trillion in 2020, indicating an increase of more than 50% since 2018. With the average cyber insurance claim rising from USD 145,000 in 2019 to USD 359,000 in 2020, there is a growing necessity for better cyber information sources, standardised databases, mandatory reporting and public awareness. This research analyses ...
Global status of data security governance. Countries and economic communities across the globe have devised countermeasures to cope with emerging big data security issues, and prepare for upcoming problems through enhancing data security governance. 1.1. Stepping up legislative efforts in protecting personal data.
Encrypted data is the referral to cipher or encoded text. In a database, there are two states for data security. Data is in two statuses: at rest and in motion - data stored in a database, on a backup disk, or a hard drive. Once transiting through the network, it necessitates the use of various encryption solutions.
This paper aims at identifying research trends in the field through a systematic bibliometric literature review (LRSB) of research on AI and system security. the review entails 77 articles published in the Scopus ® database, presenting up-to-date knowledge on the topic. the LRSB results were synthesized across current research subthemes ...
3 Strategies to overcome data security challenges in 2024 . 3 min read - There are over 17 billion internet-connected devices in the world — and experts expect that number will surge to almost ...
Large scale database and its security truly depend on different defensive methods. This paper talks about the basics of database including its meaning, characteristics, role etc. with special focus on different security challenges in the database. Moreover, this paper highlights the basics of security management, tools in this regard.
About the journal. Journal of Cybersecurity publishes accessible articles describing original research in the inherently interdisciplinary world of computer, systems, and information security …. Journal of Cybersecurity is soliciting papers for a special collection on the philosophy of information security. This collection will explore ...
Database security: Research and practice. As an increasing number of organizations become dependent on access to their data over the Internet, the need for adequate security measures is becoming more and more critical. The most popular security measure these days is a firewall.
The article is a full research paper (i.e., not a presentation or supplement to a poster). ... Data security governs information management in line with the risk strategy for protecting sensitive information. This includes protecting data at rest and in transit, as well as managing the lifecycle of the assets that hold the information ...
One way to maintain the security of the database is to use encryption techniques. The method used to secure the database is encryption using the ROTI3 and Caesar Cipher methods. Both of these methods have advantages in processing speed. For thisreason, the author will compare the use of the two algorithms above in terms of the encryption and ...
the research on database security, and find these factors closely related to dat a-base security: data, role, defense sys tem, external factors. Therefore, we mark off .
Three strategies are summarized in this section. The first is for clinical data and provides a practical user access rating system, and the second is majority for genomic data and designs a network architecture to address both security access and potential risk of privacy disclosure and reidentification.
Depending on the amount of data, the extent of the damage caused by a data breach can be significant, with the average cost being USD 392 million 1 (IBM Security 2020). This research paper reviews the existing literature and open data sources related to cybersecurity and cyber risk, focusing on the datasets used to improve academic ...
Databases are essential for storing and managing data, but they also pose security risks if not properly protected. Hackers can exploit vulnerabilities in database to steal sensitive information, cause damage, or disrupt operations.Therefore, it is important to follow some best practices to secure your database and prevent unauthorized access. In this article, we will share 10 tips and tricks ...
Ensuring privacy for the metaverse while still being able to pinpoint users for their actions in the metaverse is a significant research issue. Solving the aforementioned issue, we propose a third-party identity management solution for the metaverse based on creating a decentralized oracle network (DON) providing identity authentication and ...
The public sector has long been seen as a reliable provider of retirement security. But a recent survey suggests that some younger workers—especially women—have significant concerns about their future financial health.. Published by the MissionSquare Research Institute, the survey data points to a gender gap in expected retirement security between male and female state and local public ...
Big Data Big Data Tableau Review: Features, Pricing, Pros and Cons . Tableau has three pricing tiers that cater to all kinds of data teams, with capabilities like accelerators and real-time analytics.
Microsoft in November unveiled the Secure Future Initiative, its most significant security plan since co-founder Bill Gates halted Windows development in 2002 and ordered engineers to prioritize ...
Database security is an area focused on safeguarding databases against harmful access. It involves ensuring data accuracy, blocking unauthorized entry, and preventing harmful code within the database.
In the growing demand for distributed embedded systems that efficiently execute complex processes and high-end applications, safeguarding sensitive data is imperative. The landscape of security threats, cyber-attacks, and associated challenges has reached unprecedented sophistication and magnitude. Whether you are an individual, an organization, or a company invested in distributed embedded ...
X-rays Detection plays a vital role in medical imaging, industrial defect detection, security screening and scientific research. Direct X-ray detectors are of greater interest to researchers because they offer the advantages of faster imaging, higher resolution and simpler construction than indirect detector Journal of Materials Chemistry C Recent Review Articles