- MARKETPLACE
Body cam video shows East Lyme police chief at call despite being on administrative leave
East Lyme ― Body-worn camera footage provided Tuesday by the police department shows embattled Police Chief Michael Finkelstein responding to a police call despite being on paid administrative leave.
But was it the act of a Good Samaritan or a violation of his forced leave?
Footage from cameras belonging to three of the four officers show their response to an Aug. 16 report that went out over the department’s radio frequency of a man in the area of Cedar Ridge Golf Course who might be suicidal and could be carrying a gun.
Finkelstein was the first one to arrive, according to written reports and body camera footage from Det. William Turcotte, Officer Lindsay Cutillo and Officer Taylor Desjardins.
Finkelstein, who is facing domestic violence charges, has been on paid administrative leave for nearly 80 days.
He remained at the scene for about two minutes, the footage shows. His presence there prompted an emergency meeting of the Board of Police Commissioners early last week.
Emergency meetings, which are allowed under state law, are understood to involve an “unexpected situation or sudden occurrence of a serious and urgent nature that demands immediate action.”
No action was taken by the police commission at the meeting or since.
Written reports from the officers described their surprise at finding Finkelstein at the scene when they got there because he had been placed on leave.
Body camera footage revealed him sitting on a pile of logs alongside the unnamed man.
“He’s got no gun,” Finkelstein told Cutillo in the video from her body camera.
Finkelstein, in a long sleeve T-shirt and athletic shorts, continued to talk with the man for almost a minute. The interaction was cut short when Cutillo began to pat down the man to ensure he did not have a weapon.
Finkelstein stood there watching for another minute with his hands on his hips, a multicolored child’s bracelet on the wrist of the father of seven. It was only after Turcotte stepped away from the group that Finkelstein followed him.
The conversation was audible in footage from the detective’s body camera.
“I’m driving down and I saw him sitting over here,” Finkelstein said. “Just wanted to make sure he didn’t have anything on him.”
About 30 seconds of small talk and awkward silence ensued as they watched the other officers and the man. Finally, Finkelstein said, “You guys are all set.”
Turcotte responded with a “thank you, Chief” that made Finkelstein laugh out loud on his way to the town-provided Ford Taurus he’d parked nearby.
Finkelstein was placed on leave June 5 by First Selectman Daniel Cunningham and police commission Chairman Daniel Price to give them time to review the allegations against the chief, which at that time consisted of two misdemeanor charges related to the domestic violence allegations.
He was subsequently charged with violating a protective order against him based on his alleged failure to turn over his gun following his arrest, which is a felony.
“You are instructed not to enter the premises of your regular duty areas unless specifically authorized in advance by me,” Cunningham wrote.
He said not complying with the directives in the letter could result in disciplinary action, “up to and including termination of employment.”
‘Is he gone?’
After Finkelstein left the scene of the Friday afternoon call, Turcotte could be seen on Cutillo’s video footage gesturing toward the side road where the chief had been parked.
“Is he gone?” Turcotte asked.
Cutillo, who was in the middle of dealing with the man along with Desjardins, said she didn’t know where Finkelstein was.
“That’s what I’m trying to figure out,” Cutillo said.
The chief in the footage could be seen leaving on the side street. Sgt. Paul Renshaw, whose body camera footage was not initially provided with the others, arrived as Finkelstein was pulling away.
John Nazzaro, Finkelstein’s attorney, said last week his client was only doing what “any Good Samaritan should do.”
Nazzaro said Finkelstein learned of the potentially suicidal man “through public information,” not police communications. He declined to say what he meant by “public information.”
Nazzaro said the police radio in the car provided for him by the town had been disabled.
Cutillo in her written report said the man told her Finkelstein did not identify himself as a police officer or conduct any searches.
Nazzaro put it this way: “He did what any Good Samaritan should do. He’s still a peace officer and he’s not going to turn a blind eye to something happening right in front of him.”
Price, the police commission chairman, did not respond Tuesday to a call for comment.
Comments are limited to 200 words in length.

Post your comment Cancel reply
Comments policy.
Story comments on theday.com are intended to be civil, friendly conversations. Please treat other participants with respect and in a way that you would want to be treated. You are responsible for what you say. Please, stay on topic. If you see an objectionable post, please report it to us using the "Report" link included on every post.
Please note that comments are monitored by theday.com staff. We reserve the right at all times to remove comments that are off-topic, unlawful, threatening, abusive, libelous, defamatory, obscene, vulgar, pornographic, profane, indecent or otherwise objectionable. Personal attacks, especially on other participants, are not permitted. We reserve the right to permanently block any user who violates these terms and conditions.
Comments that are long, have multiple paragraph breaks, include code of any kind, or include hyperlinks to objectionable material may not be posted.
Read the full policy here.
Total word count: 0 words. Words left: 200 .
Jury finds ex-politician guilty of murder in 2022 killing of Las Vegas investigative reporter 06:07 pm
Congresswomen press FDA on why a proposal to ban hair-straightening chemicals is delayed 06:05 pm
Supreme Court rebuffs Biden administration plea to restore multibillion-dollar student debt plan 06:03 pm
Gunman in Trump assassination attempt saw rally as 'target of opportunity,' FBI official says 06:02 pm
Israel launches a large-scale military operation in the occupied West Bank, killing 9 Palestinians 06:23 am
State will not allow New London waterfront restaurant to operate after October
Norwich man charged in drunken shooting incident
Intoxicated woman leads to marine search in East Lyme
Stonington police: Officers subdue man who attacked them with knives
An altar boy in Newport, Rhode Island
Bee rescuer patrick gaudin, reporting on church sex abuse cases for over 20 years, dictionary researcher joshua pendragon, providing victims of church abuse some justice and accountability.
Assignment of Benefits vs Direction to Pay vs Assignment of Policy

Assignment of Benefits vs. Assignment of Policy
Assignment of Benefits forms, also known as AOBs, play a crucial role in the restoration industry’s contractor-client dynamics. These legal documents empower policyholders to transfer their insurance policy benefits to a third party, effectively connecting their restoration contractor directly to their insurance company. By doing so, policyholders can bypass many of the complications and anxieties typically associated with a restoration project, streamlining the process.
According to Josh Ehmke, Co-owner and General Consult at One Claim Solution , there’s a common misunderstanding between assignment of benefits and assignment of policy. An assignment of policy refers to the transfer of the benefits and rights of an insurance policy from one party (the policyholder) to another party (the assignee).
“An assignment of policy is never going to be valid. In fact, I haven’t come across a state that allows an assignment of an insurance policy without the insurance company’s prior written consent,” Josh said. “The reason it’s not allowed is because it’s against public policy. It increases the insurance risk substantially.”
For example, a policyholder might have a history of filing numerous claims against their insurance provider, suggesting a pattern that they might be well-versed in exploiting certain loopholes and taking advantage of insurance companies. Additionally, there are concerns that they may not adequately maintain or safeguard their property, leading to an increased risk for the insurance company.
“That is absolutely different from an assignment of benefits, which grants the rights the policyholder had to the payment under the policy to be transferred to the assignee,” Josh said. ”The only prerequisite for an assignment of benefits other than having a covered claim, is that the loss has already occurred. If you get an assignment of benefits before the loss occurs, that’s essentially a transfer of a policy.”
OCS recently encountered a case where the question arose regarding the scope of an assignment of benefits. Specifically, the issue was whether only the rights of the policyholder are transferred, or if the policyholder’s obligations are also transferred alongside the benefits under the assignment.
“By taking the assignment, the contractor doesn’t assume the policyholder’s obligations under that policy,” Josh said. “It’s very important to word your assignment of benefits appropriately to clearly state that you’re not agreeing to assume any of those policy obligations, and to specify which rights you want.”
Direction to Pay vs. Assignment of Benefits
Direction to pay (DTP) is a financial arrangement where the policyholder, who is entitled to receive an insurance claim payment, instructs the insurance company to pay the claim proceeds directly to a third party. This third party could be a vendor, contractor, service provider, or any other entity to whom the policyholder owes a debt or has entered into an agreement.
“The issue with direction to pay is that the carrier doesn’t have to honor it because it’s not enforceable,” Josh said. “It’s very limited in what it can do, whereas an assignment of benefits is much more powerful because it obligates the insurance company legally to pay you.”
According to Josh, DTP’s are rarely used, except in states like Texas and Florida where AOBs are detrimental to contractors or illegal.
“A DTP is better than nothing and allows you to at least show the carrier that the homeowner granted approval to request payment,” Josh said. “But outside of those situations, the direction to pay in my mind is worthless. When you can have an assignment of benefits, there’s no reason to have a direction to pay at all.”
A Final Word
Understanding the differences between an AOB, Assignment of Policy, and DTP is crucial because each term represents distinct legal and financial arrangements that can significantly impact insurance claims and policyholder rights. To learn more about the value of assignment of benefits in helping you navigate the restoration process, be sure to subscribe to our newsletter .

(602) 491-2588
335 E Germann Rd #340 Gilbert, AZ 85297
WHO WE SERVE
Partner With Us
PRIVACY POLICY
All rights reserved. Copyright © 2024.
Connor Trahan
Account executive.
Hi there! I’m Connor, the Account Executive for One Claim. My goal is to guide our contractors through the sales process, ensuring you’re equipped with all the information you need to make your decision and hit the ground running once aboard. We view ourselves as an extension of your business and I strive to make the process an enlightening and consultative one. My career has primarily been focused in software sales over a few different industries but the last few years were spent helping general contractors solve similar problems to what we’re doing here at OCS! Outside of work, I love spending time with my family, cooking and boating during the summer months.
Nicole Liesenfelt
Director, human resources.
Hello! I’m Nicole, and I’m here to champion for our employees, recruit for new talent, and impact culture at One Claim Solution. I find satisfaction in supporting a memorable employee experience and bring innovation, problem solving, and strategic view to the process. Nothing is more important than our people, and a healthy culture is my top priority! I have had the pleasure of building my career in various sectors, specializing in small to medium size firms focused on high-growth. My experience is centered around driving and implementing change, leading high-performing teams, and driving process improvements. I am excited to make an impact at One Claim. Outside of work, my family and I enjoy getting outdoors as much as possible to explore beautiful Colorado!
Elizabeth McGlone
Demand generation manager.
Great to meet you! I’m Elizabeth, and I’m the one behind all the emails and advertisements you’ve been seeing. As the Demand Generation Manager at One Claim Solution, my mission is to connect with contractors like you who need our services. I’m passionate about having an impact on others and I bring a wealth of experience in demand generation and marketing strategy to create moments of delight, curiosity, and education for you.
Prior to One Claim Solution, I had the privilege of building marketing departments from the ground up at companies in a variety of industries, including IT consulting, first protection, and healthcare. Personally, I love being outdoors, playing Dungeons and Dragons and board games, singing, and traveling.
Alisha Yartzoff
Director of contractor success.
Welcome! I’m Alisha, and I’m here to champion your success as the Director of Contractor Success at One Claim. With a passion for helping contractors thrive, I bring a wealth of experience in onboarding, customer service, and account management to ensure your journey with us is nothing short of exceptional.
Prior to joining One Claim, I had the privilege of scaling SMB and Enterprise Customer Success teams at fast-growing SaaS startups. With over six years of experience at companies like Mavenlink, Teamwork, and ServiceTitan, I honed my expertise in building high-performing teams and fostering proactive, consultative relationships. This background has equipped me with a deep understanding of the challenges faced by businesses like yours, and I’m dedicated to helping you overcome them.
Hi there, my name is Eric! I am the Chief Technology Officer here at OCS, spearheading our technical strategy. I have a background in computer science, graduating cum laude from BYU-Idaho with a Bachelor’s degree in Computer Information Technology.
Before coming to One Claim, I served as the Director of Engineering at Slingshot Technology, Inc., a company later acquired by WorkWave in 2021. My professional journey has spanned both emerging startups and established corporations, with a steadfast focus on cultivating high-trust, low bureaucracy teams and innovating technology using agile methodologies.
In my free time, you can find me flying drones, enjoying the outdoors, and spending time with my family.
Hello, my name is Cam, I’m the COO of One Claim Solution! I come from a management consulting background (Bain & Company) and hold an MBA from the University of Michigan. I have worked at a wide variety of organizations, from Fortune 500 to small-cap, in an equally wide variety of industries. I have over 15 years of experience in operations and strategic growth, and I have spent much of my career focused on developing high-performing tech-enabled service organizations through early stage and high growth phases.
Outside of work, my wife Brittny and I have four kids, ages 13 to 6. As residents of Mesa, Arizona, we love to ski and explore the national parks of the southwest!
Hello, my name is Dan, and I am the CEO of One Claim Solution. I am super excited by everything we are doing at OCS to be the market leading insurance billing specialist that advocates on behalf of our restoration contractors.
My professional experiences are predominantly corporate in nature. My career started at General Electric in finance and accounting. Immediately prior to joining OCS, I spent time as an investor at Bondcliff Partners and management consultant with Bain & Company. I also hold an MBA from the Kellogg School of Management at Northwestern University and got my BS in finance and accounting from Northeastern University.
Outside of the office, I enjoy spending time with my wife, two young children, and our family dog, Whiskey. We live in Charleston, SC and take advantage of the beautiful weather by spending as much time as possible outside at the beach or adventuring around town
Co-Founder and General Counsel
Hi, I’m Josh! In 2016, I co-founded One Claim Solution with my partner Jeremy Traasdahl, and I serve as General Counsel of One Claim Solution. Working in the restoration industry, Jeremy and I saw contractors struggling to get paid quickly and fairly and we knew there was a need for change. We founded One Claim Solution to be this change and it’s been my privilege to see our company grow and to advocate for our clients as general counsel.
Outside of my passion for helping the restoration industry, I enjoy spending time outdoors, fly-fishing, hunting, skiing, and coaching my kids’ baseball teams. I’ve been married to my amazing wife for 20 years and we have a beautiful family of 5 children.
Jeremy Traasdahl
Hey, I’m Jeremy! In 2016, I co-founded One Claim Solution with my partner Josh Ehmke. Working in the restoration industry, Josh and I saw contractors struggling to get paid quickly and fairly and we knew there was a need for change. We founded One Claim Solution to be this change and it’s been my privilege to lead our amazing team.
Prior to One Claim Solution, I started my career as an inside sales rep for Avnet, then moved to Pepsico as a district sales manager. Outside of work, I love spending time with my wife and four children, two boys and two girls!
This browser is no longer supported.
Upgrade to Microsoft Edge to take advantage of the latest features, security updates, and technical support.
Tutorial: Create a custom policy definition
- 5 contributors
A custom policy definition allows customers to define their own rules for using Azure. These rules often enforce:
- Security practices
- Cost management
- Organization-specific rules (like naming or locations)
Whatever the business driver for creating a custom policy, the steps are the same for defining the new custom policy.
Before creating a custom policy, check the policy samples to see whether a policy that matches your needs already exists.
The approach to creating a custom policy follows these steps:
- Identify your business requirements
- Map each requirement to an Azure resource property
- Map the property to an alias
- Determine which effect to use
- Compose the policy definition
Prerequisites
If you don't have an Azure subscription, create a free account before you begin.
Identify requirements
Before creating the policy definition, it's important to understand the intent of the policy. For this tutorial, we'll use a common enterprise security requirement as the goal to illustrate the steps involved:
- Each storage account must be enabled for HTTPS
- Each storage account must be disabled for HTTP
Your requirements should clearly identify both the "to be" and the "not to be" resource states.
While we've defined the expected state of the resource, we've not yet defined what we want done with non-compliant resources. Azure Policy supports many effects . For this tutorial, we'll define the business requirement as preventing the creation of resources if they aren't compliant with the business rules. To meet this goal, we'll use the Deny effect. We also want the option to suspend the policy for specific assignments. As such, we'll use the Disabled effect and make the effect a parameter in the policy definition.
Determine resource properties
Based on the business requirement, the Azure resource to audit with Azure Policy is a storage account. However, we don't know the properties to use in the policy definition. Azure Policy evaluates against the JSON representation of the resource, so we'll need to understand the properties available on that resource.
There are many ways to determine the properties for an Azure resource. We'll look at each for this tutorial:
- Azure Policy extension for VS Code
- Export existing resource
- Creation experience
- Quickstart templates (GitHub)
- Template reference docs
Azure Resource Explorer
View resources in vs code extension.
The VS Code extension can be used to browse resources in your environment and see the Resource Manager properties on each resource.
ARM templates
There are several ways to look at an ARM template that includes the property you're looking to manage.
Existing resource in the portal
The simplest way to find properties is to look at an existing resource of the same type. Resources already configured with the setting you want to enforce also provide the value to compare against. Look at the Export template page (under Settings ) in the Azure portal for that specific resource.
The ARM template exported by Azure portal can't be plugged straight into the deployment property for an ARM template in a deployIfNotExists policy definition.
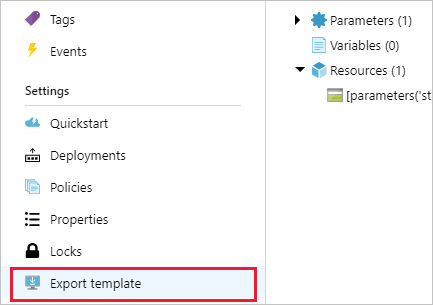
Doing so for a storage account reveals a template similar to this example:
Under properties is a value named supportsHttpsTrafficOnly set to false . This property looks like it may be the property we're looking for. Also, the type of the resource is Microsoft.Storage/storageAccounts . The type lets us limit the policy to only resources of this type.
Create a resource in the portal
Another way through the portal is the resource creation experience. While creating a storage account through the portal, an option under the Advanced tab is Security transfer required . This property has Disabled and Enabled options. The info icon has additional text that confirms this option is likely the property we want. However, the portal doesn't tell us the property name on this screen.
On the Review + create tab, a link is at the bottom of the page to Download a template for automation . Selecting the link opens the template that creates the resource we configured. In this case, we see two key pieces of information:
This information tells us the property type and also confirms supportsHttpsTrafficOnly is the property we're looking for.
Quickstart templates on GitHub
The Azure quickstart templates on GitHub has hundreds of ARM templates built for different resources. These templates can be a great way to find the resource property you're looking for. Some properties may appear to be what you're looking for, but control something else.
Resource reference docs
To validate supportsHttpsTrafficOnly is correct property, check the ARM template reference for the storage account resource on the storage provider. The properties object has a list of valid parameters. Selecting the StorageAccountPropertiesCreateParameters-object link shows a table of acceptable properties. supportsHttpsTrafficOnly is present and the description matches what we are looking for to meet the business requirements.
Another way to explore your Azure resources is through the Azure Resource Explorer (Preview). This tool uses the context of your subscription, so you need to authenticate to the website with your Azure credentials. Once authenticated, you can browse by providers, subscriptions, resource groups, and resources.
Locate a storage account resource and look at the properties. We see the supportsHttpsTrafficOnly property here as well. Selecting the Documentation tab, we see that the property description matches what we found in the reference docs earlier.
Find the property alias
We've identified the resource property, but we need to map that property to an alias .
There are a few ways to determine the aliases for an Azure resource. We'll look at each for this tutorial:
Azure PowerShell
Get aliases in vs code extension.
The Azure Policy extension for VS Code extension makes it easy to browse your resources and discover aliases .
The VS Code extension only exposes Resource Manager mode properties and doesn't display any Resource Provider mode properties.
In Azure CLI, the az provider command group is used to search for resource aliases. We'll filter for the Microsoft.Storage namespace based on the details we got about the Azure resource earlier.
In the results, we see an alias supported by the storage accounts named supportsHttpsTrafficOnly . This existence of this alias means we can write the policy to enforce our business requirements!
In Azure PowerShell, the Get-AzPolicyAlias cmdlet is used to search for resource aliases. We'll filter for the Microsoft.Storage namespace based on the details we got about the Azure resource earlier.
Like Azure CLI, the results show an alias supported by the storage accounts named supportsHttpsTrafficOnly .
Determine the effect to use
Deciding what to do with your non-compliant resources is nearly as important as deciding what to evaluate in the first place. Each possible response to a non-compliant resource is called an effect . The effect controls if the non-compliant resource is logged, blocked, has data appended, or has a deployment associated to it for putting the resource back into a compliant state.
For our example, Deny is the effect we want as we don't want non-compliant resources created in our Azure environment. Audit is a good first choice for a policy effect to determine what the impact of a policy is before setting it to Deny. One way to make changing the effect per assignment easier is to parameterize the effect. See parameters below for the details on how.
Compose the definition
We now have the property details and alias for what we plan to manage. Next, we'll compose the policy rule itself. If you aren't yet familiar with the policy language, reference policy definition structure for how to structure the policy definition. Here is an empty template of what a policy definition looks like:
The first three components are policy metadata. These components are easy to provide values for since we know what we are creating the rule for. Mode is primarily about tags and resource location. Since we don't need to limit evaluation to resources that support tags, we'll use the all value for mode .
While we didn't use a parameter for changing the evaluation, we do want to use a parameter to allow changing the effect for troubleshooting. We'll define an effectType parameter and limit it to only Deny and Disabled . These two options match our business requirements. The finished parameters block looks like this example:
Policy rule
Composing the policy rule is the final step in building our custom policy definition. We've identified two statements to test for:
- The storage account type is Microsoft.Storage/storageAccounts
- The storage account supportsHttpsTrafficOnly isn't true
Since we need both of these statements to be true, we'll use the allOf logical operator . We'll pass the effectType parameter to the effect instead of making a static declaration. Our finished rule looks like this example:
Completed definition
With all three parts of the policy defined, here is our completed definition:
The completed definition can be used to create a new policy. Portal and each SDK (Azure CLI, Azure PowerShell, and REST API) accept the definition in different ways, so review the commands for each to validate correct usage. Then assign it, using the parameterized effect, to appropriate resources to manage the security of your storage accounts.
Clean up resources
If you're done working with resources from this tutorial, use the following steps to delete any of the assignments or definitions created above:
Select Definitions (or Assignments if you're trying to delete an assignment) under Authoring in the left side of the Azure Policy page.
Search for the new initiative or policy definition (or assignment) you want to remove.
Right-click the row or select the ellipses at the end of the definition (or assignment), and select Delete definition (or Delete assignment ).
In this tutorial, you successfully accomplished the following tasks:
- Identified your business requirements
- Mapped each requirement to an Azure resource property
- Mapped the property to an alias
- Determined the effect to use
- Composed the policy definition
Next, use your custom policy definition to create and assign a policy:
Create and assign a policy definition
Was this page helpful?
Additional resources
Assignment in Insurance Policy | Meaning | Explanation | Types
Table of Contents
- 1 What is Assignment in an Insurance Policy?
- 2 Who can make an assignment?
- 3 What happens to the ownership of the policy upon Assignment?
- 4 Can assignment be changed or cancelled?
- 5 What happens if the assignment dies?
- 6 What is the procedure to make an assignment?
- 7 Is it necessary to Inform the insurer about assignment?
- 8 Can a policy be assigned to a minor person?
- 9 Who pays premium when a policy is assigned?
- 10.1 1. Conditional Assignment
- 10.2 2. Absolute Assignment
What is Assignment in an Insurance Policy?
Assignment means a complete transfer of the ownership of the policy to some other person. Usually assignment is done for the purpose of raising a loan from a bank or a financial institution .

Assignment is governed by Section 38 of the Insurance Act 1938 in India. Assignment can also be done in favour of a close relative when the policyholder wishes to give a gift to that relative. Such an assignment is done for “natural love and affection”. An example, a policyholder may assign his policy to his sister who is handicapped.
Who can make an assignment?
A policyholder who has policy on his own life can assign the policy to another person. However, a person to whom a policy has been assigned can reassign the policy to the policyholder or assign it to any other person. A nominee cannot make an assignment of the policy. Similarly, an assignee cannot make a nomination on the policy which is assigned to him.
What happens to the ownership of the policy upon Assignment?
When a policyholder assign a policy, he loses all control on the policy. It is no longer his property. It is now the assignee’s property whether the policyholder is alive or dead, the assignee alone will get the policy money from the insurance company.
If the assignee dies, then his (assignee’s) legal heirs will be entitled to the policy money.
Can assignment be changed or cancelled?
An assignment cannot be changed or cancelled. The assignee can of course, reassign the policy to the policyholder who assigned it to him. He can also assign the policy to any other person because it is now his property. We can think of a bank reassigning the policy to the policyholder when their loan is repaid.
What happens if the assignment dies?
If the assignee dies, the assignment does not get cancelled. The legal heirs of the assignee become entitled to the policy money. Assignment is a legal transfer of all the interests the policyholder has in the policy to the assignee.
What is the procedure to make an assignment?
Assignment can be made only after issue of the policy bond. The policyholder can either write out the wording on the policy bond (endorsement) or write it on a separate paper and get it stamped. (Stamp value is the same, as the stamp required for the policy — Twenty paise per one thousand sum assured). When assignment is made by an endorsement on the policy bond, there is no need for stamp because the policy is already stamped.
Is it necessary to Inform the insurer about assignment?
Yes, it is necessary to give information about assignment to the insurance company. The insurer will register the assignment in its records and from then on recognize the assignee as the owner of the policy. If someone has made more than one assignment, then the date of the notice will decide which assignment has priority. In the case of reassignment also, notice is necessary.
Can a policy be assigned to a minor person?
Assignment can be made in favour of a minor person. But it would be advisable to appoint a guardian to receive the policy money if it becomes due during the minority of the assignee.
Who pays premium when a policy is assigned?
When a policy is assigned normally, the assignee should pay the premium, because the policy is now his property. In practice, however, premium is paid by the assignor (policyholder) himself. When a bank gives a loan and takes the assignment of a policy a security, it will ask the assignor himself to pay the premium and keep it in force. In the case of an assignment as a gift, the assignor would like to pay the premium because he has gifted the policy.
Types of assignment
Assignment may take two forms:
- Conditional Assignment.
- Absolute Assignment.
1. Conditional Assignment
It would be useful where the policyholder desires the benefit of the policy to go to a near relative in the event of his earlier death. It is usually effected for consideration of natural love and affection. It generally provides for the right to revert the policyholder in the event of the assignee predeceasing the policyholder or the policyholder surviving to the date of maturity.
2. Absolute Assignment
This assignment is generally made for valuable consideration. It has the effect of passing the title in the policy absolutely to the assignee and the policyholder in no way retains any interest in the policy. The absolute assignee can deal with the policy in any manner he likes and may assign or transfer his interest to another person.
Related Posts

Can a policy be assigned during the minority of the life assured?
Can a general insurance policy(say fire/motor) under agreed bank clause should be assigned as the stock/motor is hypo/mortgaged to a bank

- Privacy Policy
Moving from Excluded Scopes to Exemptions
Policy exemptions.
The changes implementing Option A below makes JSON files easier to read than CSV files. We recommend using Policy definition Ids or Names for new exemptions and JSON files instead of CSV files. Of course, CSV files are still supported. You may even mix and match the two formats in the same folder.
Exemption Folder Structure
Exemptions can be defined as JSON or CSV files (we recommend that you use CSV files). The names of the definition files don't matter. If multiple files exists in a folder, the lists from all the files are added together.
The pacEnvironment (see global-settings.jsonc) is represented with a folder structure under the folder policyExemptions, such as epac-dev, tenant, ... A missing folder indicates that the pacEnvironment's Exemptions are not managed by this solution. To extract existing exemptions, the operations script Get-AzExemptions.ps1 can be used to generate JSON and CSV files. The output may be used to start the Exemption definitions. This same output is also created when Extract existing Policy Resources from an Environment .
A typical folder structure might look like this:
JSON Schema
The GitHub repo contains a JSON schema which can be used in tools such as VS Code to provide code completion.
To utilize the schema add a $schema tag to the JSON file.
Defining Exemptions
In v10.0.0, exemptions can be defined by specifying the Policy definition Ids or Names instead of Policy Assignment Ids. This significantly reduces the complexity of defining exemptions for Policy Sets with overlapping Policy definitions.
Each exemption must define the following properties:
- name - unique name, we recommend a short human readable name.
- displayName - descriptive name displayed on portal.
- exemptionCategory - Waiver or Mitigated .
- Item to exempt; one of the following:
- policyDefinitionId , or policyDefinitionName - exempts the Policy definition in all applicable Policy Assignments.
- policySetDefinitionId , or policySetDefinitionName - exempts all Policies in the Policy Set, or a subset if policyDefinitionsReferenceIds are specified.
- policyAssignmentId to be exempted. For Assignments of a Policy Set, you may add policyDefinitionReferenceIds to exempt specific Policies within the Policy Set.
- scope or scopes - Management Group, subscription, Resource Group or resource.
- expiresOn - empty or expiry date.
- assignmentScopeValidation - Default or DoNotValidate
- resourceSelectors - valid JSON (see JSON format below)
- metadata - valid JSON (see JSON format below)
You can use metadata for additional information.
EPAC injects deployedBy into the metadata section. This is a string that identifies the deployment source. It defaults to epac/$pacOwnerId/$pacSelector . You can override this value in global-settings.jsonc
Not recommended: Adding deployedBy to the metadata section in the Policy definition file will override the value for this Exemption only from global-settings.jsonc or default value.
Specifying Policy or Policies to be Exempted
The following properties can be used to specify the Policy or Policies to be exempted.
assignmentScopeValidation value DoNotValidate only works for Option B . It may work for Option A and C in some cases, but it is not recommended. EPAC cannot gracefully handle this and display a specific error message. Instead, it will display a generic error message with the following text "Exemption entry $($entryNumber): No assignments found for scope $($currentScope), skipping entry." .
Option A : Policy definition Ids or Names
We recommend using this option for new exemptions, except when exempting multiple Policies in a Policy Set.
It creates one exemption per Assignment containing the Policy definition (direct or indirect through a Policy Sets). policyDefinitionReferenceIds must be empty (omitted). This is the simplest and most readable way to define exemptions. Specify one of the following:
- policyDefinitionId for built-in Policy definitions in the form "/providers/Microsoft.Authorization/policyDefinitions/00000000-0000-0000-0000-000000000000" .
- policyDefinitionName for custom Policy definitions. In CSV files specify the cell in assignmentReferenceId as "policyDefinitions/{{policyDefinitionName}}" .
Option B : Policy Assignment Id
It creates one exemption for the specified Policy Assignment. This is the traditional way of defining an Exemption. It is still useful for exempting multiple Policies in an assigned Policy Set with one exemption. Specify the following:
- policyAssignmentId for the Policy Assignment in the form /providers/Microsoft.Management/managementGroups/{{managementGroupId}}/providers/Microsoft.Authorization/policyAssignments/{{policyAssignmentName}} .
- Optionally, for Policy Set Assignments only, policyDefinitionReferenceIds containing an array of strings as detailed below .
In CSV files, the column policyAssignmentId is still supported for backward compatibility for Option B only.
We recommend using the column assignmentReferenceId for every options, including option B .
Option C : Policy Set definition Ids or Names
It creates one exemption per Assignment assigning the Policy Set definition. It is useful for exempting multiple Policies in a Policy Set with one exemption. Specify the following:
- policySetDefinitionId for built-in Policy Set definitions in the form "/providers/Microsoft.Authorization/policySetDefinitions/00000000-0000-0000-0000-000000000000" .
- policySetDefinitionName for custom Policy Set definitions. In CSV files specify the cell in assignmentReferenceId as "policySetDefinitions/{{policySetDefinitionName}}" .
In CSV files use the column assignmentReferenceId , and optionally policyDefinitionReferenceIds .
Specifying policyDefinitionReferenceIds
policyDefinitionReferenceIds is used to exempt specific Policies within a Policy Set. It is only used explicitly with policyAssignmentId and policySetDefinitionId or policySetDefinitionName . For policyDefinitionId and policyDefinitionName , it is calculated by EPAC and should be empty.
policyDefinitionReferenceIds is an array of strings. Each string can be one of the following:
- policyDefinitionReferenceId as specified in the Policy Set definition.
- policyDefinitionName for custom Policy definitions in the form "policyDefinitions/{{policyDefinitionName}}" .
In CSV files, policyDefinitionReferenceIds is a list of ampersand & separated strings. In JSON files, it is an array of strings.
Defining the Scope with scope or scopes
The scope property is used to define a single scope. The scopes property is used to define multiple scopes. scopes was introduced in v10.1.0.
Using a scopes array creates nicely concatenated values for displayName and description for single scope. We recommend to always use scopes . You can suppress the concatenation by adding a colon : at the beginning of each string before the scope.
scope defines a single scope
It is unchanged from previous versions.
scopes Defines multiple Scopes in a single Entry
A list of Management Groups, subscriptions, Resource Groups or resource Ids. In CSV files it is a list separated by an ampersand & . In JSON files it is an array of strings.
The last part of the scope is used as a postfix in the exemption displayName and description to make it easier to identify the scope. This behavior can be overridden by:
- Adding a human readable name followed by a colon : before the scope: humanReadableName:/subscriptions/11111111-2222-3333-4444-555555555555 .
- Adding just a colon : before the scope to suppress the concatenation: :/subscriptions/11111111-2222-3333-4444-555555555555 .
In CSV files, the scope column is still supported for backward compatibility. We recommend using the scopes column for all new exemptions. scopes is a list of ampersand & separated strings.
In JSON files, scope is a string and scopes is an array of strings.
Combining Policy Definitions at multiple Scopes
When using Option A or Option C and/or scopes , EPAC needs to generate concatenated values for name , displayName , and description to ensure uniqueness and readability.
- name is generated by concatenating the name with a dash - and the Assignment name (the last part of the policyAssignmentId ).
- displayName and description are generated by concatenating the displayName and description with a a space dash space ( - ), the last part of the scope, or the human readable name before the colon : (if using scopes ).
It is best to explain the details with examples. They are based on JSON files, but the same principles apply to CSV files.
Example with policyDefinition and scopes
Definition file:, generated fields for each assignment with the policy specified:.
- name is the same for all the scopes: "short-name-assignmentName"
- displayName : "Descriptive name displayed on portal - 11111111-2222-3333-4444-555555555555 - assignmentName"
- displayName : "Descriptive name displayed on portal - resourceGroupName1 - assignmentName"
- description : "More details - 11111111-2222-3333-4444-555555555555 - assignmentName"
- description : "More details - resourceGroupName1 - assignmentName"
Example with policyDefinition , scopes and a human readable name
- displayName : "Descriptive name displayed on portal - humanReadableName - assignmentName - humanReadableName"
- displayName : "Descriptive name displayed on portal - resourceGroupName1 - assignmentName "
- description : "More details - humanReadableName - assignmentName"
Example with policyDefinition and a single scope
Generated fields for the assignment with the policy specified:.
- name : "short-name-assignmentName"
- displayName : "Descriptive name displayed on portal - assignmentName"
- description : "More details - assignmentName"
Example with policyAssignmentId and scopes
Generated fields for this assignment:.
- name : "short-name"
- displayName : "Descriptive name displayed on portal - 11111111-2222-3333-4444-555555555555
- displayName : "Descriptive name displayed on portal - resourceGroupName1"
- description : "More details - 11111111-2222-3333-4444-555555555555"
- description : "More details - resourceGroupName1"
Example with policyAssignmentId , scopes and a human readable name
- displayName : "Descriptive name displayed on portal - humanReadableName"
- description : "More details - humanReadableName"
Example with policyAssignmentId and a single scope
- displayName : "Descriptive name displayed on portal"
- description : "More details"
The columns must have the headers as described below. The order of the columns is not important.
Regular Columns
- name - unique name, we recommend a GUID.
- scope - individual Management Group, subscription, Resource Group or resource.
- scopes - list of ampersand & separated Management Groups, subscriptions, Resource Groups or resource Ids. Ampersand is used instead of commas since it is not a valid character in a scope name and therefore doesn't conflict.
- policyDefinitionReferenceIds - list of ampersand & separated strings as defined above .
Breaking change: v10.1.0 replaced the usual comma in policyDefinitionReferenceIds with an ampersand & to avoid conflicts with the scope Ids. You must replace in-cell commas with ampersands.
Option A columns: Policy definition Ids or Names
- Column assignmentReferenceId must be formatted:
- For Built-in Policy definition: /providers/Microsoft.Authorization/policyDefinitions/00000000-0000-0000-0000-000000000000
- For Custom Policy definition: policyDefinitions/{{policyDefinitionName}}
- Column policyDefinitionReferenceIds must be empty
Option B columns: Policy Assignment Id
- Column assignmentReferenceId must be a Policy Assignment Id:
- /providers/Microsoft.Management/managementGroups/{{managementGroupId}}/providers/Microsoft.Authorization/policyAssignments/{{policyAssignmentName}}
- Column policyDefinitionReferenceIds must be an ampersand separated list containing any of the following:
- Empty for Policy Assignment of a single Policy, or to exempt the scope from every Policy in the assigned Policy Set
- One of the options as detailed above
Legacy column policyAssignmentId is still supported for backward compatibility for Option B only.
Option C columns: Policy Set definition Ids or Names
- Column assignmentReferenceId must be a Policy Set definition Id or Name
- Built-in Policy Set definition: /providers/Microsoft.Authorization/policySetDefinitions/00000000-0000-0000-0000-000000000000
- Custom Policy Set definition: policySetDefinitions/{{policySetDefinitionName}}
- Empty to exempt all Policies in the Policy Set
If you are moving from using excluded scopes to the use of exemptions the by default EPAC will not deploy new exemptions that are part of an assignment excluded scopes. As well as this - EPAC will delete any exemption if finds that is deployed to an excluded scope.
You can override this behavior by using the switch -SkipNotScopedExemptions when you call Build-DeploymentPlans .

- Peterborough

How to Write a Policy Assignment
What is a policy assignment, policy critique.
- Policy Brief/Briefing Note
Reading and Analyzing Policy
Writing policy assignments, research and writing process.
Understanding, evaluating, and writing policy documents are important competencies to develop as undergraduate students in a wide range of fields, spanning from Health Care to Environmental Science to Education. Policy is informed by strong research and accurate evidence, often compiled and presented by government and non-governmental organizations. Public policies include formal legislation, official plans, and regulations created by various levels of government. Each of these can act as guiding principles for governmental decision making and program delivery. Non-governmental and para-governmental organizations publish policy briefs, commission reports, and fact sheets to inform policy makers and recommend policy change.
Course instructors often ask students to analyze policy documents to better understand issues and policy alternatives, and students in many disciplines must write policy documents, including critiques and briefs or briefing notes. This guide offers steps to reading policy and keys for effective policy writing.
Types of Policy Assignments
In a policy critique, students are expected to read and critically analyze one or more policy documents that address a common issue. The goal of this assignment is to present an overall assessment of current or proposed policies and their efficacy or potential considering both scholarly theory and real-world, practical application with consideration of environmental, social, or economic contexts.
Proposed structure
- Issue: what is the policy in question?
- Background: where did it emerge? What problem does it try to address?
- Application: so far, based on evidence, how effective has it been?
- Limits: what are limits with the policy? How has it been adapted? What questions remain?
- Evaluation/potential: based on concepts and theories from course materials, what is the potential for this policy to address particular issue/problem?
Policy Brief (Briefing Note)
Policy briefs or briefing notes are documents written by governmental and non-governmental organizations to propose evidence-based policy solutions to a well-defined social, environmental, or economic issue. Briefs present findings from academic and grey literature to demonstrate the scope of an issue and to analyze its context and background. The brief is organized with clear headings and short sections, which are supported by figures or tables.
- Executive Summary: similar to an abstract, briefly explains the goal, findings, and recommendations. Although it is placed first in the document, it is written last.
- Issue Definition: identify and explain the key issue and its scope and significance.
- Policy Background: synthesize evidence to explain the context of the issue – its origins, key stakeholders, overlapping issues, and potential barriers – and any existing policy.
- Best Practices: describe relevant policies from other jurisdictions and introduce specific examples of policy and best practices that reinforce the argument your briefing note presents.
- Policy Options: synthesize your research to present a few policy options; for each option, describe the approach and present advantages, challenges, and potential barriers. Present one policy recommendation from these options.
- References: divide references into sections (e.g., academic sources, grey literature, policy documents etc.)
Each policy document is focused on a specific issue and establishes particular goals; when you read any policy document, you are working to understand and analyze the issue and how the policy addresses the issue. These messages are often presented in different ways. Policy briefs are, well, brief, but other policy documents or commissioned reports can be quite lengthy, so it is important to develop a reading strategy for each new document. Generally, it is best to follow this process: preview, plan, read and take notes, and assess within course context.
Because policy documents vary significantly in form and purpose, it is essential to preview the document prior to reading it: identify its author, its purpose, and its form. Take time to read the executive summary, which presents a short explanation of the issue and purpose of the document. Understand its authorship and the interests of the individual or organizational author.
Make a plan
Identify your goal in reading the document: do you wish to better understand the issue, to identify policy alternatives, to appreciate broader context, or to determine efficacy of policy? How will this document inform your understanding of the issue you are studying? What sections will be most useful or relevant?
Read and take notes
Your preview and plan can direct your reading and notetaking. Read closely to understand the policy or issue, its context, and the evidence used to support it. Identify stakeholders and their interests, the goals of the policy and how those goals are measurable and actionable. You may find it helpful to refer to the table of contents or index (or to use the ‘find’ tool in your browser) to seek out sections that contain relevant keywords in documents spanning more than 100 pages.
Assess policy within course context
Refer to theories, frameworks, and indices that you have discussed in class to assess a policy. Consider whether it follows a particular conceptual framework or achieves particular numerical targets. Compare it to other policies in similar contexts and analyze its parts to assess its adaptability to different contexts. Evaluate its fit to the specific issue and its relevance for various stakeholder needs or values.
Reading an Official Plan
An official plan is often a lengthy document that covers many topics and issues within a set of overarching goals for an organization, like a university, hospital, or municipality. Your aim should be to understand the overarching goals of the plan and its broader context, which are likely laid out in the executive summary and introductory sections. Then you may need to seek out references to a particular topic, issue, or stakeholder; the index, table of contents, or “find” tool can be helpful for this.
Reading a Policy Brief
The goal of a policy brief is to inform and persuade policy makers, so your aim should be to understand the issue the brief identifies and to analyze the policy it proposes. The structure and design of the policy brief will guide your reading. Take time to understand the context of the issue and the policy: who are the stakeholders, what are the goals, what is the process, and what are the barriers? Analyze the policy within the disciplinary concepts you’re learning in class; how does the policy fit particular frameworks, theories, or indices you’ve discussed? What is unique about this policy? How can this policy be adapted to different contexts? What is its potential to address the issue?
Successful policy assignments are focused, well-researched, analytical, organized, and concise. Therefore, it is important to take time to define the issue, understand the context of the issue, and seek out policy alternatives prior to identifying a recommended course of action.
- Focused Issue
- Using Research
- Demonstrating Analysis
- Organized, Concise, and Clear Writing
Focused issue
It is essential that you present a focused and clear issue, and that issue must be at the scale of policy action. For example, policy briefs can address ER wait times or agricultural pesticide use, but issues such as access to health care or the sustainability of food production are too complex for you to address in a short policy assignment. Often, course material and core concepts provide useful direction for you to narrow your issue.
In policy assignments, an issue is clearly defined and contextualized with evidence from scholarly and grey literature. It is important for you to explain how scholars, governments, or NGOs have discussed the issue, and numerical data or figures can demonstrate the scale of an issue or its projected trajectory. Provide details about the issue in its context: be specific about place, time, and stakeholders, and acknowledge any overlapping economic, environmental, or social issues.
Example: Effective issue definition 1
Age-friendly municipalities foster solidarity among generations within communities and reach out to older people at risk of isolation by making them feel socially included and involved (WHO, 2007). It is well documented that these trends are happening across Canada, and evidence suggests that local governments have a key role in enabling older people to live longer. It is unclear to what degree Aurora’s municipal government is prepared to support its expanding ageing population. It is essential to continue to examine new approaches to housing and transportation infrastructure within Aurora in order to improve public policy matters in regards to their ageing population.
- Issue is grounded by focused concept and evidence; writer demonstrates value of municipal policy to address the issue
- Writer precisely identifies the issue to be discussed in brief and the goals of the report
Example: Ineffective issue definition 1
In addition to the infrastructure issue in Peterborough, there is also an issue regarding how spread out the community is. The city is too big for residents to be able to walk the entire city. Amenities are also very spread out; it is unlikely that pedestrians would be able to access the required amenities within walking distance from their house. Ultimately, the main issues surrounding the walkability in the City of Peterborough are the lack of infrastructure and maintenance, as well as the lack of available activities near to peoples’ residences.
- Not grounded in conceptual framework or theory; writer needs to explain why walkability is an issue that a municipality should address
- Lack of precision or evidence to support claims about the size of the city or accessibility to amenities
Using research
Policy is informed by evidence from scholarly literature, government data, and research by various stakeholder organizations. Effective policy assignments synthesize evidence from academic and grey literature to create an accurate account of the issue and policy options. Common forms of evidence in policy writing include numerical and financial data, figures such as graphs and maps, excerpts from existing policies, recommendations from NGOs, and conceptual frameworks.
In policy writing, your goal is to present research both accurately and accessibly, as decision-makers in government and business may not be familiar with terminology or concepts presented by scholars. Make efforts to paraphrase the evidence you use and be sure to include citations in the form requested by your professor (footnotes or author-date systems are common).
One of the key factors in Municipal Cultural Planning is increasing cross-sectoral strategies by building new partnerships “…between the municipality and its community and business partners” (Municipal Cultural Plan, toolkit, 2011, p.21) for long term sustainability. Therefore, municipal cultural planning “…does not look at policy sectorally” (Gollmitzer, 2008, p.18), but instead strengthens and integrates “…cultural resources across all facets of government planning and decision making” (Municipal Cultural Plan Toolkit, 2011, p.21). Building new networks are supported by leveraging the sense of place within a community. Adopting a place-based planning approach allows “…government, community organizations and citizens to explore, measure and asses the values, resources and assets of the community” (Huhtala, 2016, p.66), in order to leverage them for economic prosperity.
- Writer synthesizes academic and grey literature to demonstrate how concepts are applied in policy.
- Writer also demonstrates analysis of evidence and its relevance to the brief’s focused issue.
- Use of direct quotation can feature the language of a policy if the writer wishes to analyze discourse; however, this excerpt relies too heavily on direct quotation, and it would be stronger if this evidence was paraphrased.
Demonstrating analysis
The quality of your policy assignment is closely tied to your analysis of the issue and the policy options you present. It is important to evaluate policy options as you research and to critically analyze how those options address the issue within its particular context. Take time to examine specific factors and parties involved in an issue and consider how these factors may facilitate or challenge each policy option; furthermore, you should also assess the advantages and disadvantages of each policy option and its impacts on these factors or parties.
You may find it valuable to consider theories, concepts, or frameworks from your course to develop your argument and to establish coherence throughout your assignment. If you assess all policy options through the same critical lens or theory, then your message will be clear and consistent throughout your document.
Integrating senior housing into the fabric of the inner core communities could make housing developments viable and situate seniors in settings where they can access these services by foot or nearby transit (Fang, 2013). This concept can allow seniors, who may be considering downsizing, to remain within their community where they can keep active, live within easy access to medical and community services, and stay close to their support network that they have spent their lives establishing. However, the growing demand for these developments could put major pressure on the municipality. City officials would have to amend current zoning by-laws to allow commercial and residential uses to be a part of mixed-use development and appropriate provisions need to be provided to ensure compatibility and to minimize potential negative impacts.
- Writer presents both advantages and challenges of policy option within common concept of healthy aging communities.
- Writer also includes potential impacts and barriers of policy option, which demonstrates their consideration of the issue and its context.

Organized, concise, and clear writing
Policy writing should be well-organized and easy to follow. Use headings and subheadings to create structure and to support your reader. It is common to number sections and subsections to further clarify the order of your ideas. In addition, good paragraph structure also supports organization and clarity, so we encourage you to use specific topic sentences to introduce the main idea of a paragraph.
Well-written policy assignments employ a formal writing style and use third-person voice (e.g., they) rather than first-person (e.g., I, we) or second-person (e.g., you) voice. Further, they avoid jargon, but use specific and clear language. When you revise your draft, take time to consider each sentence and remove repetitive or redundant phrases and words.
Finally, it is important to pay attention to the details. Label any figures or tables in your document; make reference to these figures or tables in the text of your work (e.g., see Figure 1). Also be sure to follow assignment instructions for referencing evidence in your text (e.g., footnotes or author-date system) and in your list of sources, which is often categorized by type of source (e.g., academic, government, NGOs).
There are many ways to approach a policy assignment, but it is important to take time to research and analyze issues and policy options thoroughly prior to writing. Consider the following steps to complete your policy assignment:
- Read assignment instructions closely
- Preliminary research: review course materials, brainstorm, conduct environmental scan or site visit, consider current issues relevant to course concepts
- Define issue: consider questions and frameworks
- Research issue and context
- Research and evaluate policy alternatives in other places
- Analyze policy alternatives and consider fit for current issue and context; select policy options to present
- Outline sections: what evidence goes where? How does evidence work together?
- Write sections (leave Executive Summary until last)
- Revise for organization, analysis, and use of evidence. See Strategies for Revision and Proofreading.
- Edit for clarity, concision, and grammar
- Complete final proof of document
- These examples are not to be reproduced in whole or part. Use of the ideas or words in this example is an act of plagiarism, which is subject to academic integrity policy at Trent University and other academic institutions.
- Practical Law
Assignment of insurance policies and claims
Practical law uk practice note w-031-6021 (approx. 19 pages), get full access to this document with a free trial.
Try free and see for yourself how Practical Law resources can improve productivity, efficiency and response times.
About Practical Law
This document is from Thomson Reuters Practical Law, the legal know-how that goes beyond primary law and traditional legal research to give lawyers a better starting point. We provide standard documents, checklists, legal updates, how-to guides, and more.
650+ full-time experienced lawyer editors globally create and maintain timely, reliable and accurate resources across all major practice areas.
83% of customers are highly satisfied with Practical Law and would recommend to a colleague.
81% of customers agree that Practical Law saves them time.
- Construction and engineering
- Construction insurance
- Credit, terrorism and political risks
- Cyber insurance
- Directors and officers
- Disputes, investigations and enforcement
- Insurance in commercial transactions
- Insurance intermediaries
- Legal expenses
- Making and dealing with claims
- Reinsurance
- Security, risk management and business continuity

Assignment under Insurance Policies
By J Mandakini, NUALS
Editor’s Note: This paper attempts to explore the concept of assignment under Indian law especially Contract Act, Insurance Act and Transfer of Property Act. It seeks to appreciate why the assignment is made use of for securities of a facility sanctioned by ICICI Bank. Also, it explains how ICICI Bank faces certain problems in executing the same.
INTRODUCTION
For any facility sanctioned by a lender, collateral is always deposited to secure the same. Such mere deposition will not suffice, the borrower has to explicitly permit the lender to recover from the borrower, such securities in case of his default.
This is done by the concept of assignment, dealt with adequately in Indian law. Assignment of obligations is always a tricky matter and needs to be dealt with carefully. The Bank should not fall short of any legally permitted lengths to ensure the same. This is why ambiguity in its security documents have to be rectified.
This paper attempts to explore the concept of assignment in contract law. It seeks to appreciate why the assignment is made use of for securities of a facility sanctioned by ICICI Bank. The next section will deal with how ICICI Bank faces certain problems in executing the same. The following sections will talk about possible risks involved, as well as defenses and solutions to the same.
WHAT IS ASSIGNMENT?
Assignment refers to the transfer of certain or all (depending on the agreement) rights to another party. The party which transfers its rights is called an assignor, and the party to whom such rights are transferred is called an assignee. Assignment only takes place after the original contract has been made. As a general rule, assignment of rights and benefits under a contract may be done freely, but the assignment of liabilities and obligations may not be done without the consent of the original contracting party.
The liability on a contract cannot be transferred so as to discharge the person or estate of the original contractor unless the creditor agrees to accept the liability of another person instead of the first. [i]
Illustration
P agrees to sell his car to Q for Rs. 100. P assigns the right to receive the Rs. 100 to S. This may be done without the consent of Q. This is because Q is receiving his car, and it does not particularly matter to him, to whom the Rs. 100 is being handed as long as he is being absolved of his liability under the contract. However, notice may still be required to be given. Without such notice, Q would pay P, in spite of the fact that such right has been assigned to S. S would be a sufferer in such case.
In this case, that condition is being fulfilled since P has assigned his right to S. However, P may not assign S to be the seller. P cannot just transfer his duties under the contract to another. This is because Q has no guarantee as to the condition of S’s car. P entered into the contract with Q on the basis of the merits of P’s car, or any other personal qualifications of P. Such assignment may be done with the consent of all three parties – P, Q, S, and by doing this, P is absolved of his liabilities under the contract.
1.1. Effect of Assignment
Immediately on the execution of an assignment of an insurance policy, the assignor forgoes all his rights, title and interest in the policy to the assignee. The premium or loan interest notices etc. in such cases will be sent to the assignee. [ii] However, the existence of obligations must not be assumed, when it comes to the assignment. It must be accompanied by evidence of the same. The party asserting such a personal obligation must prove the existence of an express assumption by clear and unequivocal proof. [iii]

Assignment of a contract to a third party destroys the privity of contract between the initial contracting parties. New privity is created between the assignee and the original contracting party. In the illustration mentioned above, the original contracting parties were P and Q. After the assignment, the new contracting parties are Q and S.
1.2. Revocation of Assignment
Assignment, once validly executed, can neither be revoked nor canceled at the option of the assignor. To do so, the insurance policy will have to be reassigned to the original assignor (the insured).
1.3. Exceptions to Assignment
There are some instances where the contract cannot be assigned to another.
- Express provisions in the contract as to its non-assignability – Some contracts may include a specific clause prohibiting assignment. If that is so, then such a contract cannot be assigned. Assignability is the rule and the contrary is an exception. [iv]
Pensions, PFs, military benefits etc. Illustration
1.4. enforcing a contract of assignment.
From the day on which notice is given to the insurer, the assignee becomes the beneficiary of the policy even though the assignment is not registered immediately. It does not wait until the giving of notice of the transfer to the insurer. [vi] However, no claims may lie against the insurer until and unless notice of such assignment is delivered to the insurer.
If notice of assignment is not provided to the obligor, he is discharged if he pays to the assignor. Assignee would have to recover from the assignor. However, if the obligor pays the assignor in spite of the notice provided to him, he would still be liable to the assignee.
The following two illustrations make the point amply clear:
Illustrations
1. Seller A assigns its right to payment from buyer X to bank B. Neither A nor B gives notice to X. When payment is due, X pays A. This payment is fully valid and X is discharged. It will be up to B to recover it from A
2. Seller A assigns to bank B its right to payment from buyer X. B immediately gives notice of the assignment to X. When payment is due, X still pays A. X is not discharged and B is entitled to oblige X to pay a second time.
An assignee doesn’t stand in better shoes than those of his assignor. Thus, if there is any breach of contract by the obligor to the assignee, the latter can recover from the former only the same amount as restricted by counter claims, set offs or liens of the assignor to the obligor.
The acknowledgment of notice of assignment is conclusive proof of, and evidence enough to entertain a suit against an assignor and the insurer respectively who haven’t honoured the contract of assignment.
1.5. Assignment under various laws in India
There is no separate law in India which deals with the concept of assignment. Instead, several laws have codified it under different laws. Some of them have been discussed as follows:
1.5.1. Under the Indian Contract Act
There is no express provision for the assignment of contracts under the Indian Contract Act. Section 37 of the Act provides for the duty of parties of a contract to honour such contract (unless the need for the same has been done away with). This is how the Act attempts to introduce the concept of assignment into Indian commercial law. It lays down a general responsibility on the “representatives” of any parties to a contract that may have expired before the completion of the contract. (Illustrations to Section 37 in the Act).
An exception to this may be found from the contract, e.g. contracts of a personal nature. Representatives of a deceased party to a contract cannot claim privity to that contract while refusing to honour such contract. Under this Section, “representatives” would also include within its ambit, transferees and assignees. [vii]
Section 41 of the Indian Contract Act applies to cases where a contract is performed by a third party and not the original parties to the contract. It applies to cases of assignment. [viii] A promisee accepting performance of the promise from a third person cannot afterwards enforce it against the promisor. [ix] He cannot attain double satisfaction of its claim, i.e., from the promisor as well as the third party which performed the contract. An essential condition for the invocation of this Section is that there must be actual performance of the contract and not of a substituted promise.
1.5.2. Under the Insurance Act
The creation of assignment of life insurance policies is provided for, under Section 38 of the Insurance Act, 1938.
- When the insurer receives the endorsement or notice, the fact of assignment shall be recorded with all details (date of receipt of notice – also used to prioritise simultaneous claims, the name of assignee etc). Upon request, and for a fee of an amount not exceeding Re. 1, the insurer shall grant a written acknowledgment of the receipt of such assignment, thereby conclusively proving the fact of his receipt of the notice or endorsement. Now, the insurer shall recognize only the assignee as the legally valid party entitled to the insurance policy.
1.5.3. Under the Transfer of Property Act
Indian law as to assignment of life policies before the Insurance Act, 1938 was governed by Sections 130, 131, 132 and 135 of the Transfer of Property Act 1882 under Chapter VIII of the Act – Of Transfers of Actionable Claims. Section 130 of the Transfer of Property Act states that nothing contained in that Section is to affect Section 38 of the Insurance Act.
I) Section 130 of the Transfer of Property Act
An actionable claim may be transferred only by fulfilling the following steps:
- Signed by a transferor (or his authorized agent)
The transfer will be complete and effectual as soon as such an instrument is executed. No particular form or language has been prescribed for the transfer. It does not depend on giving notice to the debtor.
The proviso in the section protects a debtor (or other person), who, without knowledge of the transfer pays his creditor instead of the assignee. As long as such payment was without knowledge of the transfer, such payment will be a valid discharge against the transferee. When the transfer of any actionable claim is validly complete, all rights and remedies of transferor would vest now in the transferee. Existence of an instrument in writing is a sine qua non of a valid transfer of an actionable claim. [x]
II) Section 131 of the Transfer Of Property Act
This Section requires the notice of transfer of actionable claim, as sent to the debtor, to be signed by the transferor (or by his authorized agent), and if he refuses to sign it, a signature by the transferee (or by his authorized agent). Such notice must state both the name and address of the transferee. This Section is intended to protect the transferee, to receive from the debtor. The transfer does not bind a debtor unless the transferor (or transferee, if transferor refuses) sends him an express notice, in accordance with the provisions of this Section.
III) Section 132 of the Transfer Of Property Act
This Section addresses the issue as to who should undertake the obligations under the transfer, i.e., who will discharge the liabilities of the transferor when the transfer has been made complete – would it be the transferor himself or the transferee, to whom the rest of the surviving contract, so to speak, has been transferred.
This Section stipulates, that the transferee himself would fulfill such obligations. However, where an actionable claim is transferred with the stipulation in the contract that transferor himself should discharge the liability, then such a provision in the contract will supersede Ss 130 and 132 of this Act. Where the insured hypothecates his life insurance policies and stipulates that he himself would pay the premiums, the transferee is not bound to pay the premiums. [xi]
FACILITIES SECURED BY INSURANCE POLICIES – HOW ASSIGNMENT COMES INTO THE PICTURE
Many banks require the borrower to take out or deposit an insurance policy as security when they request a personal loan or a business loan from that institution. The policy is used as a way of securing the loan, ensuring that the bank will have the facility repaid in the event of either the borrower’s death or his deviations from the terms of the facility agreement.
Along with the deposit of the insurance policy, the policyholder will also have to assign the benefits of the policy to the financial institution from which he proposes to avail a facility. The mere deposit, without writing, or passing of any document of title to such a claim, does not create any equitable charge. [xii]
ETHICS OF ASSIGNING LIFE INSURANCE POLICY TO LENDERS
The purpose of taking out a life insurance policy on oneself, is that in the event of an untimely death, near and dear ones of the deceased are not left high and dry, and that they would have something to fall back on during such traumatic times. Depositing and assigning the rights under such policy document to another, would mean that there is a high chance that benefits of life insurance would vest in such other, in the event of unfortunate death and the family members are prioritized only second. These are not desirable circumstances where the family would be forced to cope with the death of their loved one coupled with the financial crisis.
Thus, there is a need to examine the ethics of:
- The bank accepting such assignment
The customer should be cautious before assigning his rights under life insurance policies. By “cautious”, it is only meant that he and his dependents and/or legal heirs should be aware of the repercussions of the act of assigning his life insurance policy. It is conceded that no law prohibits the assignment of life insurance policies.
In fact, Section 38 of the Insurance Act, 1938 , provides for such assignments. Judicial cases have held life insurance policies as property more than a social welfare measure. [xiii] Further, the bank has no personal relationship with any customer and thus has no moral obligation to not accept such assignments of life insurance.
However, the writer is of the opinion that, in dealing with the assignment of life insurance policies, utmost care and caution must be taken by the insured when assigning his life insurance policy to anyone else.
CURRENT STAND OF ICICI REGARDING FACILITIES SECURED BY INSURANCE POLICY, WITH SPECIFIC REFERENCE TO ASSIGNMENT OF OBLIGATIONS
This Section seeks to address and highlight the manner in which ICICI Bank drafts its security documents with regard to the assignment of obligations. The texts placed in quotes in the subsequent paragraphs are verbatim extracts from the security document as mentioned.
Composite Document for Corporate and Realty Funding
“ 8 . CHARGING CLAUSE
The Mortgagor doth hereby:
iii) Assign and transfer unto the Mortgagee all the Bank Accounts and all rights, title, interest, benefits, claims and demands whatsoever of the Mortgagor in, to, under and in respect of the Bank Accounts and all monies including all cash flows and receivables and all proceeds arising from Projects and Other Projects_______________, insurance proceeds, which have been deposited / credited / lying in the Bank Accounts, all records, investments, assets, instruments and securities which represent all amounts in the Bank Accounts, both present and future (the “Account Assets”, which expression shall, as the context may permit or require, mean any or each of such Account Assets) to have and hold the same unto and to the use of the Mortgagee absolutely and subject to the powers and provisions herein contained and subject also to the proviso for redemption hereinafter mentioned;
(v) Assign and transfer unto the Mortgagee all right, title, interest, benefit, claims and demands whatsoever of the Mortgagors, in, to, under and/or in respect of the Project Documents (including insurance policies) including, without limitation, the right to compel performance thereunder, and to substitute, or to be substituted for, the Mortgagor thereunder, and to commence and conduct either in the name of the Mortgagor or in their own names or otherwise any proceedings against any persons in respect of any breach of, the Project Documents and, including without limitation, rights and benefits to all amounts owing to, or received by, the Mortgagor and all claims thereunder and all other claims of the Mortgagor under or in any proceedings against all or any such persons and together with the right to further assign any of the Project Documents, both present and future, to have and to hold all and singular the aforesaid assets, rights, properties, etc. unto and to the use of the Mortgagee absolutely and subject to the powers and provisions contained herein and subject also to the proviso for redemption hereinafter mentioned.”
ICICI Bank’s Standard Terms and Conditions Governing Consumer Durable Loans
“ insurance.
The Borrower further agrees that upon any monies becoming due under the policy, the same shall be paid by the Insurance Company to ICICI Bank without any reference / notice to the Borrower, but not exceeding the principal amount outstanding under the Insurance Policy. The Borrower specifically acknowledges that in all cases of claim, the Insurance Company will be solely liable for settlement of the claim, and he/she will not hold ICICI Bank responsible in any manner whether for compensation, recovery of compensation, processing of claims or for any reason whatsoever.
Reference has been made only to assignment of assets, rights, benefits, interests, properties etc. No specific reference has been made to the assignment of obligations of the assignor under such insurance contract.
THE ISSUE FACED BY ICICI BANK
Where ICICI Bank accepts insurance policy documents of customers as security for a loan, in the light of the fact that the documents are silent about the question of assignment of obligations, are they assigned to ICICI Bank? Where there is hypothecation of a life insurance policy, with a stipulation that the mortgagor (assignor) should pay the premiums, and that the mortgagee (assignee) is not bound to pay the same, Sections 130 and 132 do not apply to such cases. [xiv] With rectification of this issue, ICICI Bank can concretize its hold over the securities with no reservations about its legality.
RISKS INVOLVED
This section of the paper attempts to explore the many risks that ICICI Bank is exposed to, or other factors which worsen the situation, due to the omission of a clause detailing the assignment of obligations by ICICI Bank.
Practices of Other Companies
The practices of other companies could be a risk factor for ICICI Bank in the light of the fact that some of them expressly exclude assignment of obligations in their security documents.
There are some companies whose notice of assignment forms contain an exclusive clause dealing with the assignment of obligations. It states that while rights and benefits accruing out of the insurance policy are to be assigned to the bank, obligations which arise out of such policy documents will not be liable to be performed by the bank. Thus, they explicitly provide for the only assignment of rights and benefits and never the assignment of obligations.
Possible Obligation to Insurance Companies
By not clearing up this issue, ICICI Bank could be held to be obligated to the insurance company from whom the assignor took the policy, for example, with respect to insurance premiums which were required to be paid by the assignor. This is not a desirable scenario for ICICI Bank. In case of default by the assignor in the terms of the contract, the right of ICICI Bank over the security deposited (insurance policy in question) could be fraught in the legal dispute.
Possible litigation
Numerous suits may be instituted against ICICI Bank alleging a violation of the Indian Contract Act. Some examples include allegations of concealment of fact, fraud etc. These could be enough to render the existing contract of assignment voidable or even void.
Contra Proferentem
This doctrine applies in a situation when a provision in the contract can be interpreted in more than one way, thereby creating ambiguities. It attempts to provide a solution to interpreting vague terms by laying down, that a party which drafts and imposes an ambiguous term should not benefit from that ambiguity. Where there is any doubt or ambiguity in the words of an exclusion clause, the words are construed more forcibly against the party putting forth the document, and in favour of the other party. [xv]
The doctrine of contra proferentem attempts to protect the layman from the legally knowledgeable companies which draft standard forms of contracts, in which the former stands on a much weaker footing with regard to bargaining power with the latter. This doctrine has been used in interpreting insurance contracts in India. [xvi]
If litigation ensues as a result of this uncertainty, there are high chances that the Courts will tend to favour the assignor and not the drafter of the documents.
POSSIBLE DEFENSES AGAINST DISPUTES FOR THE SECURITY DOCUMENTS AS THEY ARE NOW
This section of the paper attempts to give defences which the Bank may raise in case of any disputes arising out of silence on the matter of assignability of obligations.
Interpretation of the Security Documents
UNIDROIT principles expressly provide a method for interpretation of contracts. [xvii] The method consists of utilizing the following factors:
This defence relates to the concept of estoppel embodied in Section 115 of the Indian Evidence Act, 1872. According to the Section, when one person has, by his declaration, act or omission, intentionally caused or permitted another person to believe a thing to be true and to act upon such belief, neither he nor his representative shall be allowed, in any suit or proceeding between himself and such person or his representatives, to deny the truth of that thing.
If a man either by words or by conduct has intimated that he consents to an act which has been done and that he will not offer any opposition to it, and he thereby induces others to do that which they otherwise might have abstained from, he cannot question legality of the act he had sanctioned to the prejudice of those who have so given faith to his words or to the fair inference to be drawn from his conduct. [xviii] Subsequent conduct may be relevant to show that the contract exists, or to show variation in the terms of the contract, or waiver, or estoppel. [xix]
Where the meaning of the instrument is ambiguous, a statement subsequently interpreting such instrument is admissible. [xx] In the present case, where the borrower has never raised any claims with regard to non assignability of obligations on him, and has consented to the present conditions and relations with ICICI Bank, he cannot he cannot be allowed to raise any claims with respect to the same.
Internationally, the doctrine of post contractual conduct is invoked for such disputes. It refers to the acts of parties to a contract after the commencement of the contract. It stipulates that where a party has behaved in a particular manner, so as to induce the other party to discharge its obligations, even if there has been a variation from the terms of the contract, the first party cannot cite such variation as a reason for its breach of the contract.
Where the parties to a contract are both under a common mistake as to the meaning or effect of it, and therefore embark on a course of dealing on the footing of that mistake, thereby replacing the original terms of the contract by a conventional basis on which they both conduct their affairs, then the original contract is replaced by the conventional basis. The parties are bound by the conventional basis. Either party can sue or be sued upon it just as if it had been expressly agreed between them. [xxi]
The importance of consensus ad idem has been concretized by various case laws in India. Further, if the stipulations and terms are uncertain and the parties are not ad idem there can be no specific performance, for there was no contract at all. [xxii]
In the present case, the minds of the assignor and assignee can be said to have not met while entering into the assignment. The assignee never had any intention of undertaking any obligations of the assignor. In Hartog v Colin & Shields, [xxiii] the defendants made an offer to the plaintiffs to sell hare skins, offering to a pay a price per pound instead of per piece.
AVOIDING THESE RISKS
To concretize ICICI Bank’s stand on the assignment of obligations in the matter of loans secured by insurance policies, the relevant security documents could be amended to include such a clause.
For instances where loans are secured by life insurance policies, a standard set by the American Banker’s Association (ABA) has been followed by many Indian commercial institutions as well. [xxvi] The ABA is a trade association in the USA representing banks ranging from the smallest community bank to the largest bank holding companies. ABA’s principal activities include lobbying, professional development for member institutions, maintenance of best practices and industry standards, consumer education, and distribution of products and services. [xxvii]
There are several ICICI security documents which have included clauses denying any assignment of obligations to it. An extract of the deed of hypothecation for vehicle loan has been reproduced below:
“ 3. In further pursuance of the Loan Terms and for the consideration aforesaid, the Hypothecator hereby further agrees, confirms, declares and undertakes with the Bank as follows:
(i)(a) The Hypothecator shall at its expenses keep the Assets in good and marketable condition and, if stipulated by the Bank under the Loan Terms, insure such of the Assets which are of insurable nature, in the joint names of the Hypothecator and the Bank against any loss or damage by theft, fire, lightning, earthquake, explosion, riot, strike, civil commotion, storm, tempest, flood, erection risk, war risk and such other risks as may be determined by the Bank and including wherever applicable, all marine, transit and other hazards incidental to the acquisition, transportation and delivery of the relevant Assets to the place of use or installation. The Hypothecator shall deliver to the Bank the relevant policies of insurance and maintain such insurance throughout the continuance of the security of these presents and deliver to the Bank the renewal receipts / endorsements / renewed policies therefore and till such insurance policies / renewal policies / endorsements are delivered to the Bank, the same shall be held by the Hypothecator in trust for the Bank. The Hypothecator shall duly and punctually pay all premia and shall not do or suffer to be done or omit to do or be done any act, which may invalidate or avoid such insurance. In default, the Bank may (but shall not be bound to) keep in good condition and render marketable the relevant Assets and take out / renew such insurance. Any premium paid by the Bank and any costs, charges and expenses incurred by the Bank shall forthwith on receipt of a notice of demand from the Bank be reimbursed by the Hypothecator and/or Borrower to the Bank together with interest thereon at the rate for further interest as specified under the Loan Terms, from the date of payment till reimbursement thereof and until such reimbursement, the same shall be a charge on the Assets…”
The inclusion of such a clause in all security documents of the Bank can avoid the problem of assignability of obligations in insurance policies used as security for any facility sanctioned by it.
An assignment of securities is of utmost importance to any lender to secure the facility, without which the lender will not be entitled to any interest in the securities so deposited.
In this paper, one has seen the need for assignment of securities of a facility. Risks involved in not having a separate clause dealing with non assignability of obligations have been discussed. Certain defences which ICICI Bank may raise in case of the dispute have also been enumerated along with solutions to the same.
Formatted by March 2nd, 2019.
BIBLIOGRAPHY
[i] J.H. Tod v. Lakhmidas , 16 Bom 441, 449
[ii] http://www.licindia.in/policy_conditions.htm#12, last visited 30 th June, 2014
[iii] Headwaters Construction Co. Ltd. v National City Mortgage Co. Ltd., 720 F. Supp. 2d 1182 (D. Idaho 2010)
[iv] Indian Contract Act and Specific Relief Act, Mulla, Vol. I, 13 th Edn., Reprint 2010, p 968
[v] Khardah Co. Ltd. v. Raymond & Co ., AIR 1962 SC 1810: (1963) 3 SCR 183
[vi] Principles of Insurance Law, M.N. Srinivasan, 8 th Edn., 2006, p. 857
[vii] Ram Baran v Ram Mohit , AIR 1967 SC 744: (1967) 1 SCR 293
[viii] Sri Sarada Mills Ltd. v Union of India, AIR 1973 SC 281
[ix] Lala Kapurchand Godha v Mir Nawah Himayatali Khan, [1963] 2 SCR 168
[x] Velayudhan v Pillaiyar, 9 Mad LT 102 (Mad)
[xi] Hindustan Ideal Insurance Co. Ltd. v Satteya, AIR 1961 AP 183
[xii] Mulraj Khatau v Vishwanath, 40 IA 24 – Respondent based his claim on a mere deposit of the policy and not under a written transfer and claimed that a charge had thus been created on the policy.
[xiii] Insure Policy Plus Services (India) Pvt. Ltd. v The Life Insurance Corporation of India, 2007(109)BOMLR559
[xiv] Transfer of Property Act, Sanjiva Row, 7 th Edn., 2011, Vol II, Universal Law Publishing Company, New Delhi
[xv] Ghaziabad Development Authority v Union of India, AIR 2000 SC 2003
[xvi] United India Insurance Co. Ltd. v M/s. Pushpalaya Printers, [2004] 3 SCR 631, General Assurance Society Ltd. v Chandumull Jain & Anr., [1966 (3) SCR 500]
[xvii] UNIDROIT Principles, Art 4.3
[xviii] B.L.Sreedhar & Ors. v K.M. Munireddy & Ors., 2002 (9) SCALE 183
[xix] James Miller & Partners Ltd. v Whitworth Street Estates (Manchester) Ltd., [1970] 1 All ER 796 (HL)
[xx] Godhra Electricity Co. Ltd. v State of Gujarat, AIR 1975 SC 32
[xxi] Amalgamated Investment & Property Co. Ltd. v Texas Commerce International Bank Ltd., [1981] 1 All ER 923
[xxii] Smt. Mayawanti v Smt. Kaushalya Devi, 1990 SCR (2) 350
[xxiii] [1939] 3 All ER 566
[xxiv] Terrell v Alexandria Auto Co., 12 La.App. 625
[xxv] http://www.uncitral.org/pdf/english/CISG25/Pamboukis.pdf, last visited on 30 th June, 2014
[xxvi] https://www.phoenixwm.phl.com/shared/eforms/getdoc.jsp?DocId=525.pdf, last visited on 30 th June, 2014
[xxvii] http://www.aba.com/About/Pages/default.aspx, last visited on 30 th June, 2014

Related Posts:

Leave a Comment Cancel reply

Give it a try, you can unsubscribe anytime :)
Thanks, I’m not interested
Azure Policy Explained with Example [Step-by-Step]
January 3, 2023
Azure Policy Overview
While organizations are transitioning towards deploying more and more resources in the cloud, it becomes imperative to ensure that the resources being deployed are in accordance with the organization’s standards. In this article, we will understand how we can ensure that our resources in the Azure cloud stay compliant via the use of Azure Policies.
Azure Policy is a service in Azure that you use to create, assign and manage policies. These polices are a mechanism through which we enforce compliance and enable auditing across our organization. Azure Policy does this by running evaluations of your resources and scanning for those not compliant with the policies you have created
Given below are the advantages of using Azure Polices:
- Enforcement and compliance : Turn on built-in policies or build custom ones for all resource types. Real time policy evaluation and enforcement. Periodic and on-demand compliance evaluation.
- Apply policies at scale : Apply policies to a Management Group with control across your entire organization. Apply multiple policies and aggregate policy states with policy initiative. Define an exclusion scope.
- Remediation : Real time remediation, and remediation on existing resources.
Here are some use cases for Azure Polices:
- Specify the resource types that your organization can deploy.
- Prohibit the creation of resources for controlling costs.
- Restrict access to a service when we don’t want it being deployed.
- Specify a set of virtual machine SKUs that your organization can deploy.
- Restrict the locations your organization can specify when deploying resources to enforce geographical compliance.
- Enforce a required tag and its value.
- Audit if Azure Backup service is enabled for all Virtual machines.
We can implement Azure Policies at various scopes within our organization. These are as follows:
- Management groups
- Subscriptions
- Resource groups
- Individual resources
Azure Policy components
Policy definition.
These are used to define what we will be monitoring for compliance and we also define the actions that will take place based on that evaluation. Azure offers several inbuilt policy definitions that we can use. Some of them are listed below.
- Allowed Storage Account SKUs (Deny) : Determines if a storage account being deployed is within a set of SKU sizes. Its effect is to deny all storage accounts that don't adhere to the set of defined SKU sizes.
- Allowed Resource Type (Deny) : Defines the resource types that you can deploy. Its effect is to deny all resources that aren't part of this defined list.
- Allowed Locations (Deny) : Restricts the available locations for new resources. Its effect is used to enforce your geo-compliance requirements.
- Allowed Virtual Machine SKUs (Deny) : Specifies a set of virtual machine SKUs that you can deploy.
- Add a tag to resources (Modify) : Applies a required tag and its default value if it's not specified by the deploy request.
- Not allowed resource types (Deny) : Prevents a list of resource types from being deployed.
To implement these policy definitions (both built-in and custom definitions), you'll need to assign them. You can assign any of these policies through the Azure portal, PowerShell, or Azure CLI.
Policy assignment
Once we define our policy, we need to assign it to a scope and that is where policy assignment comes into the picture. We can assign policies to management groups, subscriptions, resource groups or even individual resources within the Azure cloud.
Initiative definition
An initiative definition is a collection of policies that are tailored towards achieving a single high-end goal together. They simplify by grouping a set of policies as one single item. For example, ensuring that VMs are deployed as per standards.
Azure Policy example
An example of an Azure policy could be a scenario where we require resources to be tagged.
- Policy definition : In this case, we can define that the virtual machines in our environment must have the tag “linux-cloud”. If this tag is missing then the creation of the virtual machine is denied.
- Policy assignment : We would assign this policy at the scope of the resource group under which the VMs would be created.
With this policy in effect, when we try to deploy a VM without the required tag in the resource group with the policy applied, then the creation of that virtual machine will be denied.
Azure Policy Example
Now that we’ve understood the need of Azure policies, gone through the use cases and its different components, now it’s time to perform some hands on and see Azure policies in action. For the purpose of this demonstration, we’ll be using a built in Azure policy definition.
Step 1: Open the Azure policy service pane
Log in to the Azure portal and within the search bar, type policy and select the first result.
![Azure Policy Explained with Example [Step-by-Step] Azure Policy Explained with Examples](https://www.golinuxcloud.com/wp-content/uploads/azure-39.png)
This will bring us to the overview section of our Azure Policy service. If you don’t have any existing policies applied, the page should look similar to the one shown below.
![Azure Policy Explained with Example [Step-by-Step] Azure Policy Explained with Examples](https://www.golinuxcloud.com/wp-content/uploads/azure-40.png)
This page shows us the overall compliance status of our resources and also if any resources are in a non-compliant state so that we may take corrective actions.
Step 2: Create Azure policy definition
Towards the left side of the page, we have a section named authoring and within this section, there is a tab called definitions. Click on this tab to create a policy definition or use an existing one.
![Azure Policy Explained with Example [Step-by-Step] Azure Policy Explained with Examples](https://www.golinuxcloud.com/wp-content/uploads/azure-41.png)
Clicking on the definitions tab takes us to the policy definitions page where we can view all of the pre-existing policies and initiative definitions.
![Azure Policy Explained with Example [Step-by-Step] Azure Policy Explained with Examples](https://www.golinuxcloud.com/wp-content/uploads/azure-42.png)
We can use filters on this page to view only custom or only built-in policies under the type. We can filter polices based on different categories which are basically different Azure services. Also, we can search for a policy by typing the policy name in the search bar. We are going to search for location based policies so we’ll type in the keyword location in the search bar.
![Azure Policy Explained with Example [Step-by-Step] Azure Policy Explained with Examples](https://www.golinuxcloud.com/wp-content/uploads/azure-43.png)
The policy that we are going to use is “ allowed locations ”. We will click on this policy so that we may examine it.
![Azure Policy Explained with Example [Step-by-Step] Azure Policy Explained with Examples](https://www.golinuxcloud.com/wp-content/uploads/azure-44.png)
What we’ll see here is the JSON that defines the policy. Given below is the full JSON policy definition.
Description:
- The definition contains information related to the policy like the display name, description and many other things. This policy is going to allow us to restrict the locations where we may deploy resources in the Azure cloud. This allows us to enforce geographical compliance in the environment.
- The parameters section contains a parameter (of type array) named listOfAllowedLocations .
- The listOfAllowedLocations parameter is being matched in the policy rule section such that any location that is not listed in this parameter will not be allowed. After this condition, we have an exemption section wherein if the field contains the location global or if the resource being created is an Azure Active Directory resource, then the policy is not enforced.
- In the next section, we see the effect of non-compliance i.e., deny.
Step 3: Assign Azure Policy
Right above the policy definition JSON, we see an Assign button. Click on this button and we will now need to select the scope for this policy. We have selected our subscription and a resource group under that subscription.
![Azure Policy Explained with Example [Step-by-Step] Azure Policy Explained with Examples](https://www.golinuxcloud.com/wp-content/uploads/azure-45.png)
We can also site exclusions from this policy if we wish to but we are not going to do this in this demonstration. From here click next . This brings us to the allowed locations parameters section where we need to select the locations, we would like to allow resources to be built in.
![Azure Policy Explained with Example [Step-by-Step] Azure Policy Explained with Examples](https://www.golinuxcloud.com/wp-content/uploads/azure-46.png)
We will select Asia and Asia Pacific .
![Azure Policy Explained with Example [Step-by-Step] Azure Policy Explained with Examples](https://www.golinuxcloud.com/wp-content/uploads/azure-47.png)
Now click review and create and then click on create on the next page.
![Azure Policy Explained with Example [Step-by-Step] Azure Policy Explained with Examples](https://www.golinuxcloud.com/wp-content/uploads/azure-48.png)
This will now create the policy assignment which could take up to 30 minutes to take effect.
Step 4: Test the new azure policy
To test the policy, we’ll deliberately attempt to create a virtual machine that is not in one of the two allowed locations. So, we quickly navigate to the Virtual Machine service window in Azure, fill in the subscription, resource group, name and image.
In the region we’ve specified “ West US ” which is NOT Asia or Asia Pacific .
![Azure Policy Explained with Example [Step-by-Step] Azure Policy Explained with Examples](https://www.golinuxcloud.com/wp-content/uploads/azure-49.png)
With these parameters entered, click on review and create . On the next page, we’ll encounter the following error.
![Azure Policy Explained with Example [Step-by-Step] Azure Policy Explained with Examples](https://www.golinuxcloud.com/wp-content/uploads/azure-50.png)
Click on the arrow to view the error details.
![Azure Policy Explained with Example [Step-by-Step] Azure Policy Explained with Examples](https://www.golinuxcloud.com/wp-content/uploads/azure-51.png)
The above error message clearly states that the VM deployment failed because we were trying to create a VM in a location is not one of the allowed locations thus verifying the successful enforcement of our Azure Policy .
In this article, we discussed the need and benefits of using Azure policy and we also practically demonstrated the enforcement of an Azure policy. We encourage you try out other pre-built Azure polices and examine the different levels and types of restrictions that could be enforced.
We’ve referred to the official Azure documentation along with the "Control and organize Azure resources with Azure Resource Manager" and "Build a cloud governance strategy on Azure" modules part of the managing resources in Azure learning path. Azure Policy Overview Control and organize Azure resources with Azure Resource Manager Build a cloud governance strategy on Azure

Sahil Hulage
He possesses over 5+ years of experience as a Cloud Consultant, specializing in Azure DevOps and CloudLinux. With his expertise, he implements and optimizes cloud solutions, ensuring seamless operations and efficient resource management. You can connect with him on his LinkedIn profile.
Can't find what you're searching for? Let us assist you.
Enter your query below, and we'll provide instant results tailored to your needs.
If my articles on GoLinuxCloud has helped you, kindly consider buying me a coffee as a token of appreciation.

For any other feedbacks or questions you can send mail to [email protected]
Thank You for your support!!
Leave a Comment Cancel reply
Save my name and email in this browser for the next time I comment.
Notify me via e-mail if anyone answers my comment.
We try to offer easy-to-follow guides and tips on various topics such as Linux, Cloud Computing, Programming Languages, Ethical Hacking and much more.
Recent Comments
Popular posts, 7 tools to detect memory leaks with examples, 100+ linux commands cheat sheet & examples, tutorial: beginners guide on linux memory management, top 15 tools to monitor disk io performance with examples, overview on different disk types and disk interface types, 6 ssh authentication methods to secure connection (sshd_config), how to check security updates list & perform linux patch management rhel 6/7/8, 8 ways to prevent brute force ssh attacks in linux (centos/rhel 7).
Privacy Policy
HTML Sitemap
Azure Policy: Starter Guide
My coworkers and teammates often reach out to me with similar questions regarding the best practices for creating and applying Azure Policy . That tendency encouraged me to compile this starter guide for Azure Policy, which is based on my practical experience in multiple projects and covers the 20% baseline that allows you to implement 80% of typical use cases, aka the Pareto principle .
Learn the topic
RTFM stands for “read the fucking manual,” bro.
Seriously, I mean, read the Microsoft Azure Policy docs first. Microsoft is doing a great job with documenting their services and solutions recently, and without knowing the basic Azure Policy principles, it will be really hard for you to grasp the concepts. After investigating what Azure Policy is for, I suggest looking through the list of built-in policies to get an idea about typical use cases for different Azure service types.
The two most important points to pay attention to initially are understanding Azure Policy effects and Azure Policy deployment scopes . The effects will give you some insights into what you can actually do with the policies. At the same time, the deployment scope will save you time for troubleshooting why you cannot assign a policy deployed at the subscription level to another subscription.
The evaluation of logical conditions in policy rules, I would say less critical. It might cause you some headache initially, but as soon as you understand how the double negation works, you shall be fine.
Although Azure policies can modify the configuration of existing Azure resources and even deploy new resources, I suggest starting with auditing resource configuration (Audit and AuditIfNotExists effects) and putting some guardrails (Deny effect) in your environment as the latter ones are easier to learn and understand.
Apart from the official documentation, I definitely recommend watching a few learning courses about Azure Governance on Pluralsight :
- Mastering Microsoft Azure Governance by James Bannan
- Microsoft Azure DevOps Engineer: Implementing Infrastructure Control and Compliance by John Savill
They are just a few hours long and can provide you with a really good starting point to advance your Azure Policy learning.
Make an assessment
“Think first before you act.” An unknown guru.
Before making any changes in your environment, i.e., assigning a new Azure Policy to your subscription, it is worth knowing first what policies are already in effect and their compliance results. Besides, assigned policies are evaluated in a specific order you should be aware of. Otherwise, it is easy to mess up your Azure environment: policies usually control something on a global scale (a whole subscription or management group), therefore impacting lots of resources.
In 80 percent of use cases, using the Azure portal to assess what existing policy and initiative assignments are and their compliance state will be the right choice – when there are only a few policies applied, no need to overcomplicate things.
In more advanced scenarios, when an organization already deployed dozens of custom Azure Policy definitions and extensively uses them at the management group level and on the individual subscriptions, manual assessment is somewhat complicated. Here I can suggest using AzGovViz – a community build solution (a PowerShell script) that can help you quickly create a comprehensive report in different formats containing all the details about Azure Policy configuration in your environment and more. You can event integrate AzGovViz with Azure DevOps pipelines to document the policy configuration as part of your deployments.
Create your policy
“Let’s roll up your sleeves and get to work!” A motivational speech.
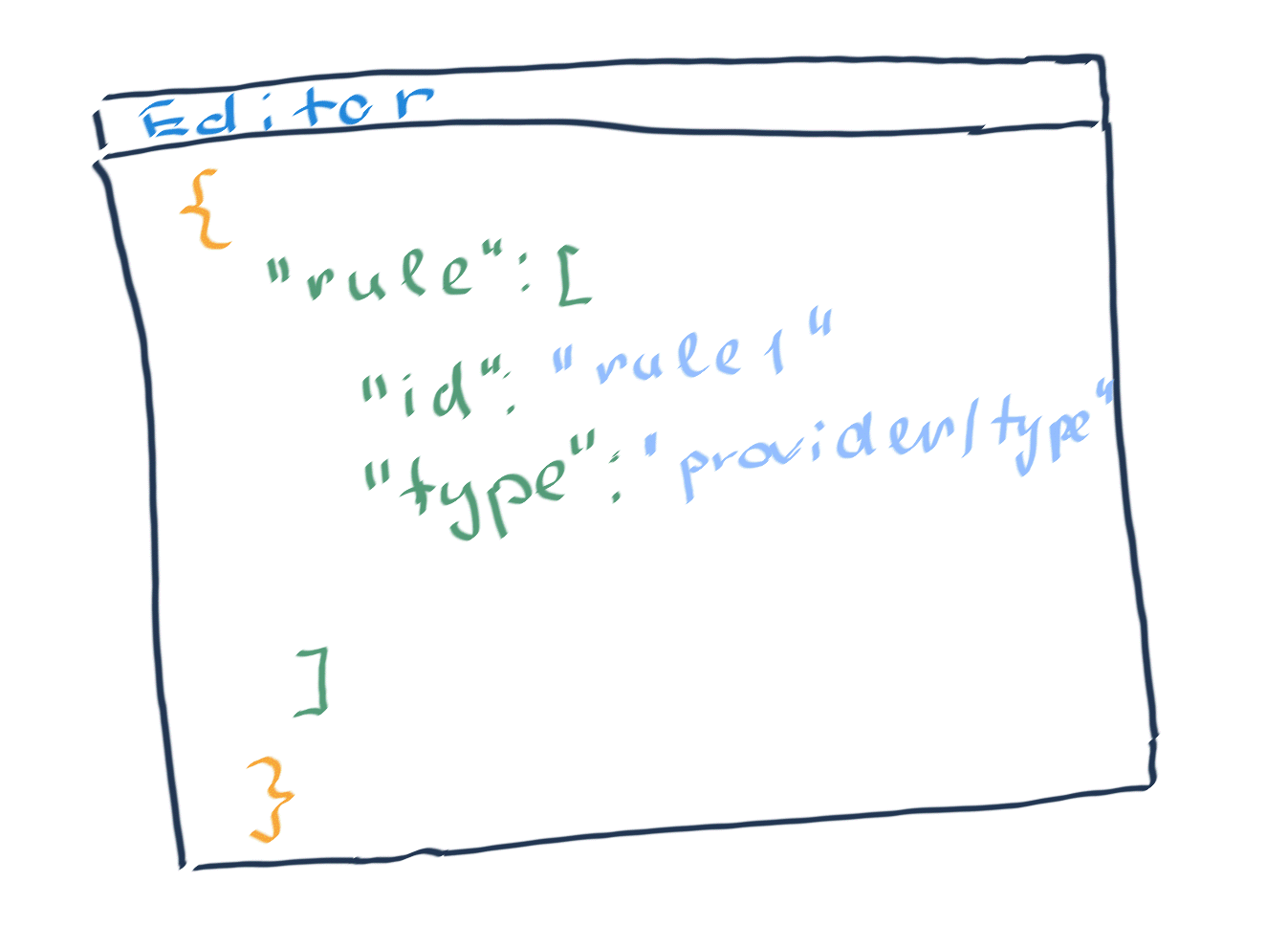
Even though Microsoft already provided us with lots of useful built-in ready-to-use policies, I encourage you to not hurry on assigning them left and right. You will never understand how Azure Policy works to the full extent until you learn how to create and manage your custom policies.
A typical antipattern to avoid is dozens of individually assigned policies when they should be applied as a group via a policy initiative.
Firstly, you can look into the source code of built-in Azure policies (check the last column with the links to GitHub) and use it as a draft for your custom policy or initiative definitions. Alternatively, you can go straight to the Azure Policy Samples repository on GitHub , clone it, and explore with your coding tools.
Probably, the best coding experience with Azure Policy as of now is to use Visual Studio Code with Azure Policy extension for it . Additionally, I suggest installing the ARM Tools extension . It will significantly help you with syntax validation, snippets, and auto-completion if you decide to define your policies in ARM templates to make your deployment experience more consistent.
Recently, Microsoft has updated its docs with some ARM snippets for policy definitions , policy set definitions (aka policy initiatives), and their assignments . Still, those articles miss many nuances and details, and I suggest checking out my work on Azure Policies and my repository for sample Azure Policies on GitHub .
For more advanced cases, check the recent updates to Azure Policy on AzPolicyAdvertizer . As documenting new policies usually takes some time, AzPolicyAdvertizer closes that gap by providing short information about policies and recent changes to them.
A common use case is to duplicate a built-in policy logic in your custom definition completely. The reason for that is the way how Azure Policy engine handles updates to the existing definitions. When you update a definition, all existing policy assignment of it will automatically be using the new definition. Although there are some controls for backward compatibility, and Microsoft usually doesn’t introduce breaking changes in the existing definitions, many teams prefer to have full control over their configuration.
“Damn it! I said, test it first!” A senior developer, fixing a bug in production.
I honestly must warn you that testing Azure Policy is not an easy task. Nevertheless, I strongly encourage you to test your policy work before putting it into use. Considering the usual scope the policies are applied and the effects they can make (change configuration, deploy new resources), the results of careless policy assignments can be quite devastating to your environment.
First of all, you need to ensure that the syntax of your policy or initiative is correct. Whether you define your definitions in JSON policy format or ARM templates, the Visual Studio Code extensions mentioned above should help you find and fix basic syntax errors. If you stick with the ARM template option , you can use Test-Az*Deployment Azure PowerShell cmdlets to validate your templates’ syntax against Azure Resource Manager APIs. Unfortunately, the policy-related cmdlets in the Az.Resources module don’t support any testing options yet.
As a matter of caution, set the policy ‘enforcementMode’ parameter into the disabled state when creating assignments for your tested policies so you can safely audit their work results.
Secondly, be aware that Azure Policy assignments don’t come into effect immediately. There is a policy evaluation delay , which is around 30 minutes or so. Also, auditing your resources might take some time as the Azure Policy engine needs to evaluate all resources against policy rules within the assigned scope. In other words, you cannot test the results of your policy work immediately. Apart from that, the delay effectively complicates automated tests for Azure Policy.
Although there is an option to initiate an on-demand evaluation scan , it still won’t make the whole process much faster if a policy needs to process thousands of resources.
Due to all the complications, I would say that the testing process for your policies will be manual or semi-manual in most cases. You will validate the syntax, deploy the definitions into a test environment, i.e., a dedicated subscription, assign them to a test scope, deploy some resources to test the expected policy behavior, and check results on the portal . In the end, the code for Azure Policy is not something that is often updated, and manual testing can be a reasonable tradeoff to creating automated test cases.
However, in advanced scenarios, when you need to create and maintain more than a handful of simple policies, creating automated Azure Policy tests as part of your CI/CD pipeline is a must. I’m planning to cover this topic in detail in a separate post as it requires quite a lot of explanation not explicitly tied to Azure Policy.
“Do. Or do not. There is no try.” Master Yoda to young Skywalker.
As I already mentioned, before actually deploying your custom policy or initiative definitions, you should clearly understand what the deployment scopes are. Besides, you should also understand how Azure Policy inclusions, exclusions, and exemptions work. Apart from that, you should have a clear distinction between a policy/initiative definition and its assignment: you should deploy the definition and assign it to your scope to make your Azure policy work.
Technically, you can deploy policies and create assignments using any supported method: the portal, Azure CLI, Azure PowerShell, Azure REST API, etc . It’s really up to you to choose which one o them fits your configuration management and deployment practices.
When I started working with Azure Policy myself, I was a bit frustrated with the default programming experience of maintaining two separate files for each definition and came up with a solution on how to deploy Azure Policy with ARM templates . However, things have changed since then, and now the policies are defined in a single file . A slight improvement, but the Azure PowerShell cmdlets still require lots of additional parameters that should be duplicated on their usage.
Optionally, you can try using the AzOps deployment framework, which could be a good choice for large environments when you run your Azure Governance as a separate project.
Just be consistent in the way you do your deployments and preferably manage Azure Policy as a part of your CI/CD pipelines .
Check the results
“A man reaps what he sows” A proverb.
Finally, your first policy is deployed, the assignment is created, and it’s time to see what we have got.
Remember about the time it takes for policy to come into effect and evaluate your resources .
Using the Azure portal to get Azure Policy compliance results would be the most obvious and probably the most reasonable choice at the beginning – it won’t heart to keep things simple.
For advanced scenarios, when you are already proficient with managing Azure Policy from deployment pipelines, you might want to check how you can get Policy insights with code to evaluate them in your test cases. Also, take a look at the Az.PolicyInsights PowerShell module, and what kind of data you can extract with it.
In conclusion
Just reading this guide won’t make you an expert in Azure Policy. For that, you need to have some practice too. So, give it a try – look into your Azure infrastructure, find some areas you can improve with Azure Policy (trust me, there is always something that can be improved 😉), come up with a solution, test it, apply and reap the benefits!
If you have any questions about this topic, put them in the comments below 👇.
Written by:
Andrew Matveychuk
Member discussion:.
- 855-717-0022
- Log In / Create an Account
Assignment of benefits
Assignment of benefits is an agreement that gives your claims benefits to someone else.
What is an assignment of benefits?
An assignment of benefits (or AOB for short) is an agreement that gives your claims benefits, and in some instances complete control of your claim, to someone else. It’s usually used so that a contractor can "stand in your shoes" and file a claim, make decisions about repairs, and collect insurance payments from your insurance company directly for covered repairs. In some states, the contractor will even file a lawsuit against your insurer as your assignee.
Why do homeowners agree to an assignment of benefits?
Homeowners may sign an assignment of benefits form because they think it’s more convenient and efficient than dealing with the claims process firsthand.
Once a contractor has been assigned your benefits, they tell the insurance company what work they believe is required and negotiate the claim. For example, say you have a water leak in the house. You call a home restoration company to stop the water flow, clean up the mess, and restore your home to its former glory. The restoration company may ask for an assignment of benefits so it can deal directly with the insurance company without your input. That may sound like a relief at first glance – someone else can deal with all that!
But signing away your rights in the claims process may not be worth the risk.
Assignment of benefits in Florida: a case of rampant fraud
Because the assignment of benefits takes control out of the homeowner’s hands, insurance fraud is a major concern. Some contractors may take advantage of the situation and inflate repair needs and costs or bill for work that was never completed. They may also hire attorneys to sue the insurance company if it does not pay the full amount of their estimate or denies claims.
These lawsuits became a huge problem in Florida – by 2018, there were 135,000 AOB lawsuits , a 70 percent increase in 15 years. On the whole, the FBI estimates fraudulent claims account for nearly $6 billion of the $80 billion appropriated for post-hurricane reconstruction.
Florida eventually passed a bill in 2019 to curb the abuse of the assignment of benefits.
Ultimately, AOB fraud hurts homeowners the most. It increases homeowners insurance rates across the board, and you may be stuck with incomplete work and no recourse.
What responsibilities does the AOB contractor have?
Once you sign an AOB, a contractor has full power to make all decisions about the claim without consulting you. The assignment of benefits gives contractors the ability to:
- File the insurance claim .
- Work directly with insurance claims adjusters.
- Make repair decisions.
- Complete repairs.
- Directly bill the insurance carrier for all work completed.
- Sue your insurance company regarding your claim.
Sometimes the assignment of benefits limits the scope of the work the contractor was hired for. For example, say your home has a leaky pipe. You may hire a plumber to fix the leak, a remediation company to dry the walls and carpet, and a general contractor to replace the bathroom cabinets. Each of the three contractors may have a respective assignment of benefits for their part of the job.
How assignment of benefits impact homeowners
Under some circumstances, an assignment of benefits agreement could work out for homeowners who don’t want to handle their insurance claim. If the contractor is reputable, performs the work, and knows what information the insurance company needs, it can be a big help.
For example:
- The claims adjuster will work directly with the contractor.
- The contractor would handle remediation and repairs.
- The contractor would bill the insurance company, not the homeowner.
AOB arrangements only work for covered damage in need of repair. If you must replace belongings or appliances, you’d still need to work directly with your insurer and payments would go to you.
Protecting yourself in an assignment of benefits agreement
Don’t sign an assignment of benefits agreement right off the bat. Before you hire any contractor:
- Get multiple quotes.
- Check references, licenses, and their insurance.
- Get written estimates for potential work.
- Get a guarantee to back the workmanship.
- Make sure you get to approve the completed work.
- Request copies of all paperwork sent to your insurance company.
- Require that the contractor show you the documents you are actually signing.
You might be tempted to hire the first contractor you find, but you save yourself headaches if you do some due diligence before signing an assignment of benefits. Great contractors use this to expedite repairs and spare you some work. Take a beat to find that great contractor.
Related Posts: Keep exploring
Displaying post 1 / 3
Navigation Menu
Search code, repositories, users, issues, pull requests..., provide feedback.
We read every piece of feedback, and take your input very seriously.
Saved searches
Use saved searches to filter your results more quickly.
To see all available qualifiers, see our documentation .
- Notifications You must be signed in to change notification settings
create-and-manage.md
Latest commit, file metadata and controls.
| title | description | ms.date | ms.topic | ms.custom |
|---|---|---|---|---|
Tutorial: Create and manage policies to enforce compliance
Understanding how to create and manage policies in Azure is important for staying compliant with your corporate standards and service-level agreements. In this tutorial, you learn to use Azure Policy to do some of the more common tasks related to creating, assigning, and managing policies across your organization, such as:
[!div class="checklist"] Assign a policy to enforce a condition for resources you create in the future Create and assign an initiative definition to track compliance for multiple resources Resolve a non-compliant or denied resource Implement a new policy across an organization
If you would like to assign a policy to identify the current compliance state of your existing resources, the quickstart articles go over how to do so.
Prerequisites
If you don't have an Azure subscription, create a free account before you begin.
Assign a policy
The first step in enforcing compliance with Azure Policy is to assign a policy definition. A policy definition defines under what condition a policy is enforced and what effect to take. In this example, assign the built-in policy definition called Inherit a tag from the resource group if missing to add the specified tag with its value from the parent resource group to new or updated resources missing the tag.
Go to the Azure portal to assign policies. Search for and select Policy .
:::image type="content" source="../media/create-and-manage/search-policy.png" alt-text="Screenshot of searching for Policy in the search bar." border="false":::
Select Assignments on the left side of the Azure Policy page. An assignment is a policy that has been assigned to take place within a specific scope.
:::image type="content" source="../media/create-and-manage/select-assignments.png" alt-text="Screenshot of selecting the Assignments node from the Policy Overview page." border="false":::
Select Assign Policy from the top of the Policy | Assignments page.
:::image type="content" source="../media/create-and-manage/select-assign-policy.png" alt-text="Screenshot of selecting the 'Assign policy' button on the Assignments page." border="false":::
On the Assign Policy page and Basics tab, select the Scope by selecting the ellipsis and selecting either a management group or subscription. Optionally, select a resource group. A scope determines what resources or grouping of resources the policy assignment gets enforced on. Then select Select at the bottom of the Scope page.
Resources can be excluded based on the Scope . Exclusions start at one level lower than the level of the Scope . Exclusions are optional, so leave it blank for now.
Select the Policy definition ellipsis to open the list of available definitions. You can filter the policy definition Type to Built-in to view all and read their descriptions.
Select Inherit a tag from the resource group if missing . If you can't find it right away, type inherit a tag into the search box and then press ENTER or select out of the search box. Select Select at the bottom of the Available Definitions page once you have found and selected the policy definition.
:::image type="content" source="../media/create-and-manage/select-available-definition.png" alt-text="Screenshot of the search filter while selecting a policy definition.":::
The Version is automatically populated to the latest major version of the definition and set to autoinjest any non-breaking changes. You may change the version to others, if available or adjust your ingesting settings, but no change is required. Overrides are optional, so leave it blank for now.
The Assignment name is automatically populated with the policy name you selected, but you can change it. For this example, leave Inherit a tag from the resource group if missing . You can also add an optional Description . The description provides details about this policy assignment.
Leave Policy enforcement as Enabled . When Disabled , this setting allows testing the outcome of the policy without triggering the effect. For more information, see enforcement mode .
Select the Parameters tab at the top of the wizard.
For Tag Name , enter Environment .
Select the Remediation tab at the top of the wizard.
Leave Create a remediation task unchecked. This box allows you to create a task to alter existing resources in addition to new or updated resources. For more information, see remediate resources .
Create a Managed Identity is automatically checked since this policy definition uses the modify effect. Type of Managed Identity is set to System Assigned . Permissions is set to Contributor automatically based on the policy definition. For more information, see managed identities and how remediation access control works .
Select the Non-compliance messages tab at the top of the wizard.
Set the Non-compliance message to This resource doesn't have the required tag . This custom message is displayed when a resource is denied or for non-compliant resources during regular evaluation.
Select the Review + create tab at the top of the wizard.
Review your selections, then select Create at the bottom of the page.
Implement a new custom policy
Now that you've assigned a built-in policy definition, you can do more with Azure Policy. Next, create a new custom policy to save costs by validating that virtual machines created in your environment can't be in the G series. This way, every time a user in your organization tries to create a virtual machine in the G series, the request is denied.
Select Definitions under Authoring in the left side of the Azure Policy page.
:::image type="content" source="../media/create-and-manage/definition-under-authoring.png" alt-text="Screenshot of the Definitions page under Authoring group." border="false":::
Select + Policy definition at the top of the page. This button opens to the Policy definition page.
Enter the following information:
The management group or subscription in which the policy definition is saved. Select by using the ellipsis on Definition location .
[!NOTE] If you plan to apply this policy definition to multiple subscriptions, the location must be a management group that contains the subscriptions you assign the policy to. The same is true for an initiative definition.
The name of the policy definition - Require VM SKUs not in the G series
The description of what the policy definition is intended to do - This policy definition enforces that all virtual machines created in this scope have SKUs other than the G series to reduce cost.
Choose from existing options (such as Compute ), or create a new category for this policy definition.
Copy the following JSON code and then update it for your needs with:
- The policy parameters.
- The policy rules/conditions, in this case - VM SKU size equal to G series
- The policy effect, in this case - Deny .
Here's what the JSON should look like. Paste your revised code into the Azure portal.
The field property in the policy rule must be a supported value. A full list of values is found on policy definition structure fields . An example of an alias might be "Microsoft.Compute/VirtualMachines/Size" .
To view more Azure Policy samples, see Azure Policy samples .
Select Save .
Create a policy definition with REST API
You can create a policy with the REST API for Azure Policy Definitions. The REST API enables you to create and delete policy definitions, and get information about existing definitions. To create a policy definition, use the following example:
Include a request body similar to the following example:
Create a policy definition with PowerShell
Before proceeding with the PowerShell example, make sure you've installed the latest version of the Azure PowerShell Az module.
You can create a policy definition using the New-AzPolicyDefinition cmdlet.
To create a policy definition from a file, pass the path to the file. For an external file, use the following example:
For a local file use, use the following example:
To create a policy definition with an inline rule, use the following example:
The output is stored in a $definition object, which is used during policy assignment. The following example creates a policy definition that includes parameters:
View policy definitions with PowerShell
To see all policy definitions in your subscription, use the following command:
It returns all available policy definitions, including built-in policies. Each policy is returned in the following format:
Create a policy definition with Azure CLI
You can create a policy definition using Azure CLI with the az policy definition command. To create a policy definition with an inline rule, use the following example:
View policy definitions with Azure CLI
Create and assign an initiative definition.
With an initiative definition, you can group several policy definitions to achieve one overarching goal. An initiative evaluates resources within scope of the assignment for compliance to the included policies. For more information about initiative definitions, see Azure Policy overview .
Create an initiative definition
:::image type="content" source="../media/create-and-manage/definition-under-authoring.png" alt-text="Screenshot of the Definitions page under the Authoring group.":::
Select + Initiative Definition at the top of the page to open the Initiative definition wizard.
:::image type="content" source="../media/create-and-manage/initiative-definition.png" alt-text="Screenshot of the initiative definition page and properties to set.":::
Use the Initiative location ellipsis to select a management group or subscription to store the definition. If the previous page was scoped to a single management group or subscription, Initiative location is automatically populated.
Enter the Name and Description of the initiative.
This example validates that resources are in compliance with policy definitions about getting secure. Name the initiative Get Secure and set the description as: This initiative has been created to handle all policy definitions associated with securing resources .
For Category , choose from existing options or create a new category.
Set a Version for the initiative, such as 1.0 .
[!NOTE] The version value is strictly metadata and isn't used for updates or any process by the Azure Policy service.
Select Next at the bottom of the page or the Policies tab at the top of the wizard.
Select Add policy definition(s) button and browse through the list. Select the policy definition(s) you want added to this initiative. For the Get Secure initiative, add the following built-in policy definitions by selecting the checkbox next to the policy definition:
- Allowed locations
- Endpoint protection should be installed on machines
- Non-internet-facing virtual machines should be protected with network security groups
- Azure Backup should be enabled for Virtual Machines
- Disk encryption should be applied on virtual machines
- Add or replace a tag on resources (add this policy definition twice)
After selecting each policy definition from the list, select Add at the bottom of the list. Since it's added twice, the Add or replace a tag on resources policy definitions each get a different reference ID .
:::image type="content" source="../media/create-and-manage/initiative-definition-2.png" alt-text="Screenshot of the selected policy definitions with their reference ID and group on the initiative definition page.":::
[!NOTE] The selected policy definitions can be added to groups by selecting one or more added definitions and selecting Add selected policies to a group . The group must exist first and can be created on the Groups tab of the wizard.
Select Next at the bottom of the page or the Groups tab at the top of the wizard. New groups can be added from this tab. For this tutorial, we aren't adding any groups.
Select Next at the bottom of the page or the Initiative parameters tab at the top of the wizard. If we wanted a parameter to exist at the initiative for passing to one or more included policy definitions, the parameter is defined here and then used on the Policy parameters tab. For this tutorial, we aren't adding any initiative parameters.
[!NOTE] Once saved to an initiative definition, initiative parameters can't be deleted from the initiative. If an initiative parameter is no longer needed, remove it from use by any policy definition parameters.
Select Next at the bottom of the page or the Policy parameters tab at the top of the wizard.
Policy definitions added to the initiative that have parameters are displayed in a grid. The value type can be 'Default value', 'Set value', or 'Use Initiative Parameter'. If 'Set value' is selected, the related value is entered under Value(s) . If the parameter on the policy definition has a list of allowed values, the entry box is a dropdown list selector. If 'Use Initiative Parameter' is selected, a dropdown list select is provided with the names of initiative parameters created on the Initiative parameters tab.
:::image type="content" source="../media/create-and-manage/initiative-definition-3.png" alt-text="Screenshot of the options for allowed values for the allowed locations definition parameter on the policy parameters tab of the initiative definition page.":::
[!NOTE] In the case of some strongType parameters, the list of values cannot be automatically determined. In these cases, an ellipsis appears to the right of the parameter row. Selecting it opens the 'Parameter scope (<parameter name>)' page. On this page, select the subscription to use for providing the value options. This parameter scope is only used during creation of the initiative definition and has no impact on policy evaluation or the scope of the initiative when assigned.
Set the 'Allowed locations' value type to 'Set value' and select 'East US 2' from the dropdown list. For the two instances of the Add or replace a tag on resources policy definitions, set the Tag Name parameters to 'Env' and 'CostCenter and the Tag Value parameters to 'Test' and 'Lab' as shown below. Leave the others as 'Default value'. Using the same definition twice in the initiative but with different parameters, this configuration adds or replaces an 'Env' tag with the value 'Test' and a 'CostCenter' tag with the value of 'Lab' on resources in scope of the assignment.
:::image type="content" source="../media/create-and-manage/initiative-definition-4.png" alt-text="Screenshot of the entered options for allowed values for the allowed locations definition parameter and values for both tag parameter sets on the policy parameters tab of the initiative definition page.":::
Select Review + create at the bottom of the page or at the top of the wizard.
Review the settings and select Create .
Create a policy initiative definition with Azure CLI
You can create a policy initiative definition using Azure CLI with the az policy set-definition command. To create a policy initiative definition with an existing policy definition, use the following example:
Create a policy initiative definition with Azure PowerShell
You can create a policy initiative definition using Azure PowerShell with the New-AzPolicySetDefinition cmdlet. To create a policy initiative definition with an existing policy definition, use the following policy initiative definition file as VMPolicySet.json :
Assign an initiative definition
Locate the Get Secure initiative definition you previously created and select it. Select Assign at the top of the page to open to the Get Secure: Assign initiative page.
:::image type="content" source="../media/create-and-manage/assign-definition.png" alt-text="Screenshot of the 'Assign' button on the initiative definition page." border="false":::
You can also select and hold (or right-click) on the selected row or select the ellipsis at the end of the row for a contextual menu. Then select Assign .
:::image type="content" source="../media/create-and-manage/select-right-click.png" alt-text="Screenshot of the context menu for an initiative to select the Assign functionality." border="false":::
Fill out the Get Secure: Assign Initiative page by entering the following example information. You can use your own information.
- Scope: The management group or subscription you saved the initiative to become the default. You can change scope to assign the initiative to a subscription or resource group within the saved location.
- Exclusions: Configure any resources within the scope to prevent the initiative assignment from being applied to them.
- Initiative definition and Assignment name: Get Secure (pre-populated as name of initiative being assigned).
- Description: This initiative assignment is tailored to enforce this group of policy definitions.
- Policy enforcement: Leave as the default Enabled .
- Assigned by: Automatically filled based on who is logged in. This field is optional, so custom values can be entered.
Select the Parameters tab at the top of the wizard. If you configured an initiative parameter in previous steps, set a value here.
Select the Remediation tab at the top of the wizard. Leave Create a Managed Identity unchecked. This box must be checked when the policy or initiative being assigned includes a policy with the deployIfNotExists or modify effects. As the policy used for this tutorial doesn't, leave it blank. For more information, see managed identities and how remediation access control works .
Check initial compliance
Select Compliance in the left side of the Azure Policy page.
Locate the Get Secure initiative. It's likely still in Compliance state of Not started . Select the initiative to get full details of the assignment.
:::image type="content" source="../media/create-and-manage/compliance-status-not-started.png" alt-text="Screenshot of the Initiative compliance page showing assignment evaluations in a Not started state." border="false":::
Once the initiative assignment has been completed, the compliance page is updated with the Compliance state of Compliant .
:::image type="content" source="../media/create-and-manage/compliance-status-compliant.png" alt-text="Screenshot of the Initiative compliance page showing assignment evaluations complete and in a Compliant state." border="false":::
Selecting any policy on the initiative compliance page opens the compliance details page for that policy. This page provides details at the resource level for compliance.
Remove a non-compliant or denied resource from the scope with an exclusion
After assigning a policy initiative to require a specific location, any resource created in a different location is denied. In this section, you walk through resolving a denied request to create a resource by creating an exclusion on a single resource group. The exclusion prevents enforcement of the policy (or initiative) on that resource group. In the following example, any location is allowed in the excluded resource group. An exclusion can apply to a subscription, a resource group, or an individual resource.
A policy exemption can also be used skip the evaluation of a resource. For more information, see Scope in Azure Policy .
Deployments prevented by an assigned policy or initiative can be viewed on the resource group targeted by the deployment: Select Deployments in the left side of the page, then select the Deployment Name of the failed deployment. The resource that was denied is listed with a status of Forbidden . To determine the policy or initiative and assignment that denied the resource, select Failed. Click here for details -> on the Deployment Overview page. A window opens on the right side of the page with the error information. Under Error Details are the GUIDs of the related policy objects.
:::image type="content" source="../media/create-and-manage/rg-deployment-denied.png" alt-text="Screenshot of a failed deployment that was denied by a policy assignment." border="false":::
On the Azure Policy page: Select Compliance in the left side of the page and select the Get Secure policy initiative. On this page, there's an increase in the Deny count for blocked resources. Under the Events tab are details about who tried to create or deploy the resource that was denied by the policy definition.
:::image type="content" source="../media/create-and-manage/compliance-overview.png" alt-text="Screenshot of the Events tab and policy event details on the Initiative compliance page." border="false":::
In this example, Trent Baker, one of Contoso's Sr. Virtualization specialists, was doing required work. We need to grant Trent a space for an exception. Create a new resource group, LocationsExcluded , and next grant it an exception to this policy assignment.
Update assignment with exclusion
Select Assignments under Authoring in the left side of the Azure Policy page.
Browse through all policy assignments and open the Get Secure policy assignment.
Set the Exclusion by selecting the ellipsis and selecting the resource group to exclude, LocationsExcluded in this example. Select Add to Selected Scope and then select Save .
:::image type="content" source="../media/create-and-manage/request-exclusion.png" alt-text="Screenshot of the Exclusions option on the Initiative Assignment page to add an excluded resource group to the policy assignment." border="false":::
[!NOTE] Depending on the policy definition and its effect, the exclusion could also be granted to specific resources within a resource group inside the scope of the assignment. As a Deny effect was used in this tutorial, it wouldn't make sense to set the exclusion on a specific resource that already exists.
Select Review + save and then select Save .
In this section, you resolved the denied request by creating an exclusion on a single resource group.
Clean up resources
If you're done working with resources from this tutorial, use the following steps to delete any of the policy assignments or definitions created above:
Select Definitions (or Assignments if you're trying to delete an assignment) under Authoring in the left side of the Azure Policy page.
Search for the new initiative or policy definition (or assignment) you want to remove.
Right-click the row or select the ellipses at the end of the definition (or assignment), and select Delete definition (or Delete assignment ).
In this tutorial, you successfully accomplished the following tasks:
[!div class="checklist"] Assigned a policy to enforce a condition for resources you create in the future Created and assign an initiative definition to track compliance for multiple resources Resolved a non-compliant or denied resource Implemented a new policy across an organization
To learn more about the structures of policy definitions, look at this article:
[!div class="nextstepaction"] Azure Policy definition structure

IMAGES
COMMENTS
East Lyme ― Body-worn camera footage provided Tuesday by the police department shows embattled Police Chief Michael Finkelstein responding to a police call despite being on paid administrative ...
Policy assignments define which resources are to be evaluated by a policy definition or initiaitve. Further, the policy assignment can determine the values of parameters for that group of resources at assignment time, making it possible to reuse policy definitions that address the same resource properties with different needs for compliance. ...
An assignment is a policy definition or initiative that has been assigned to a specific scope. This scope could range from a management group to an individual resource. The term scope refers to all the resources, resource groups, subscriptions, or management groups that the definition is assigned to. Assignments are inherited by all child ...
To remove the policy assignment created in this article, follow these steps: On the Policy pane, select Compliance and locate the Audit VMs that do not use managed disks policy assignment. Select the policy assignment's ellipsis and select Delete assignment. Next steps. In this quickstart, you assigned a policy definition to identify non ...
Assigning a single Policy or Policy Set. Each assignment assigns either a Policy or Policy Set. In EPAC this is done with a definitionEntry or a definitionEntryList. Exactly one occurrence must exist in any collated tree branch. For each entry, you need to specify one of the following: policyName - custom Policy.
An assignment of policy refers to the transfer of the benefits and rights of an insurance policy from one party (the policyholder) to another party (the assignee). "An assignment of policy is never going to be valid. In fact, I haven't come across a state that allows an assignment of an insurance policy without the insurance company's ...
The ARM template creates a policy assignment for a resource group scope and assigns the built-in policy definition Audit VMs that do not use managed disks. Create the following ARM template as policy-assignment.json. Open Visual Studio Code and select File > New Text File. Copy and paste the ARM template into Visual Studio Code.
Search for the new initiative or policy definition (or assignment) you want to remove. Right-click the row or select the ellipses at the end of the definition (or assignment), and select Delete definition (or Delete assignment). Review. In this tutorial, you successfully accomplished the following tasks:
A parameter uses the following properties in a policy definition: name: The name of your parameter. Used by the parameters deployment function within the policy rule. For more information, see using a parameter value. type: Determines if the parameter is a string, array, object, boolean, integer, float, or dateTime.
A custom policy definition allows customers to define their own rules for using Azure. These rules often enforce: Security practices. Cost management. Organization-specific rules (like naming or locations) Whatever the business driver for creating a custom policy, the steps are the same for defining the new custom policy.
Assignment means a complete transfer of the ownership of the policy to some other person. Usually assignment is done for the purpose of raising a loan from a bank or a financial institution. Assignment is governed by Section 38 of the Insurance Act 1938 in India. Assignment can also be done in favour of a close relative when the policyholder ...
Policy definition is the conditions which you want controlled. There are built in definitions such as controlling what type of resources can be deployed to enforcing the use of tags on all resources. Policy assignment is the scope of what the policy definition can take effect around. Scope of assignment can be assigned to a individual, resource ...
It creates one exemption per Assignment containing the Policy definition (direct or indirect through a Policy Sets). policyDefinitionReferenceIds must be empty (omitted). This is the simplest and most readable way to define exemptions. Specify one of the following:
Writing Policy Assignments. Successful policy assignments are focused, well-researched, analytical, organized, and concise. Therefore, it is important to take time to define the issue, understand the context of the issue, and seek out policy alternatives prior to identifying a recommended course of action. Focused Issue.
With collateral assignment of life insurance, ownership of an asset transfers from the borrower to the lender. This transfer only remains in place until the loan is paid in full. In this situation, the transferred asset is your life insurance policy. The goal is only to satisfy your loan obligation. Once that debt is repaid, you'll end the ...
Assignment of benefits, widely referred to as AOB, is a contractual agreement signed by a policyholder, which enables a third party to file an insurance claim, make repair decisions, and directly ...
An overview of the legal principles that apply when assigning an insurance policy or the right to receive the insurance monies due under the policy to a third party. It considers the requirements that must be met for the assignment to be valid and explains the difference between assignment, co-insurance, noting of interest and loss payee clauses.
1.1. Effect of Assignment. Immediately on the execution of an assignment of an insurance policy, the assignor forgoes all his rights, title and interest in the policy to the assignee. The premium or loan interest notices etc. in such cases will be sent to the assignee.
Policy definition: In this case, we can define that the virtual machines in our environment must have the tag "linux-cloud". If this tag is missing then the creation of the virtual machine is denied. Policy assignment: We would assign this policy at the scope of the resource group under which the VMs would be created.
A common use case is to duplicate a built-in policy logic in your custom definition completely. The reason for that is the way how Azure Policy engine handles updates to the existing definitions. When you update a definition, all existing policy assignment of it will automatically be using the new definition.
Policy Assignment. definition. Policy Assignment means the Assignment of Life Insurance Policy as Collateral, in substantially the form of Exhibit C hereto, duly executed by Borrower to Bank to secure the Obligations, including any amendment or modification thereof. Policy Assignment means the assignment dated on or around the Commencement Date ...
An assignment of benefits (or AOB for short) is an agreement that gives your claims benefits, and in some instances complete control of your claim, to someone else. It's usually used so that a contractor can "stand in your shoes" and file a claim, make decisions about repairs, and collect insurance payments from your insurance company ...
Absolute assignment of a life insurance policy is irrevocable due to its complete transfer of ownership from the assignor to the assignee. It is a binding legal agreement with no control over the assignor. Exceptions include a mutual agreement or legal provisions. Absolute assignment should be considered carefully for estate planning, gifting ...
Search for the new initiative or policy definition (or assignment) you want to remove. Right-click the row or select the ellipses at the end of the definition (or assignment), and select Delete definition (or Delete assignment). Review. In this tutorial, you successfully accomplished the following tasks: