Vulnerability Response assignment\n rules overview
Define the criteria by which vulnerable items (VIs) are automatically assigned to an\n assignment group for remediation.
Assignment type, whether Manual or Rule is\n available from the VI form and the list view. Any VI that was originally assigned by a rule\n but subsequently manually reassigned contains a reference to the original rule.
Use Assignment rule and Assignment type information to identify cases where the assignment\n rules did not find a correct match for the intended recipient. You can also use the\n information to identify which rules had the most reassignments.
Case sensitivity for the\n search text you enter in the condition builder is not supported on this record or\n form.

Assigning vulnerable items automatically
- User group: This option allows you to select any of the existing Now Platform® user groups.
- None: Indicates no default value for this mandatory field
- Configuration Item: Approval Group
- Configuration Item: Assignment Group
- Configuration Item: Support Group
- Script: This option allows you to define the conditions using a script. This option\n requires coding or advanced ServiceNow expertise.
Run high priority rules (items that need special handling, where risk is critical, or a VI\n should be handled by regulatory compliance) first. Next, run your general rules, where no\n special handling is required, and you know who should be responsible for them. Finally,\n create a default rule to assign VIs to the group that will figure out what assignment group\n it should belong to. This group could add another rule to cover their decisions. This\n default rule would run last.
Assignment rule evaluation process
Assignment rules are used to evaluate and assign a VI when a new VI is opened, that is,\n imported, created manually, or reopened. Unless you manually reapply assignment rules after\n the VI or its state changes, a VI is evaluated once.
- For each vulnerability assignment rule, the VI is compared to the assignment filter,\n lowest order rule first.
- Where the condition matches, the VI is assigned an assignment group. The lookup\n stops.
- Where the conditions do not find a match among all the other rules, the VI is assigned\n to the default assignment group, if a default rule exists. Once the vulnerable item\n has been assigned, the appropriate remediation task rule uses assignment as one of its\n criteria for placing the vulnerable items into a remediation task. See Vulnerability Response remediation tasks and task rules overview and Filtering within Vulnerability Response for more\n information. Note: The default rule is the rule with the highest execution order\n value. A final rule to use that is a good catch-all is\n active=true . If there is no default rule, the VI\n remains unassigned when the remediation task rule makes the group\n assignment. \n \n
Reapplying assignment rules
If the Reapply all vulnerability assignment rules scheduled job\n has not run before the first time you use Apply Changes , then it\n runs all the assignment rules on all Open VIs except those VIs that were manually\n assigned. After that, all subsequent uses of Apply Changes rerun\n only the changed rules and any dependent rules. Changes to one rule may result in a VI\n matching a different unmodified rule. Reapplying assignment rules does not regroup the\n vulnerable items.
The scheduled job [ Reapply all vulnerability\n assignment rules ] is inactive by default. When activated, it applies all\n the rules to all open VIs except those manually assigned. It can run\n Daily , Weekly ,\n Monthly , Periodically , Once , or On Demand . Depending on how many active VIs you\n have in your environment, remember to set the Run field\n appropriately following the initial run to prevent performance impacts.
Upgrade customers should refer to the VR Release Notes for information regarding the\n impact of this feature on existing VIs.
When an assignment group on an assignment rule changes, the\n vulnerable items can be automatically reevaluated and regrouped by enabling the system\n property sn_vul.rerun_task_rules and business rule Link to Remediation Tasks.
- Navigate to All > System Properties > All Properties .
- Open sn_vul.rerun_task_rules system property.
- In the Value field, set the value to true.
To automate the regrouping of vulnerable items, you must active the business rule Link Remediation Tasks.
- Navigate to All > System Definition > Business Rules .
- Open Link to Remediation Tasks business rule.
- Select the Active check box to activate the business rule.
- The vulnerable items are removed from the tasks without deleting the remediation\n tasks.
- Only those items are removed which are created using remediation task rules or\n remediation effort.
- Regrouping is done automatically only when the assignment group changes as part of\n an assignment rule and not when it is manually changed.
- Installation of Vulnerability Response and supported applications
- Vulnerability Response personas and granular roles
- Vulnerability Response remediation tasks and task rules overview
- Vulnerability Response remediation target rules
- Vulnerability classification groups and rules
- Machine Learning solutions for Vulnerability Response
- CI lookup rules for identifying configuration items from Vulnerability Response third-party vulnerability integrations
- Creating CIs for Vulnerability Response using the Identification and Reconciliation engine
- Discovered Items
- Vulnerability Response remediation task and vulnerable item states
- Removing assignments from vulnerable items and remediation tasks
- Vulnerability Response calculators and vulnerability calculator rules
- Vulnerability Response vulnerable item detections from third-party integrations
- Vulnerability Solution Management
- Patch orchestration with Vulnerability Response
- Exception Management overview
- Exception rules overview
- False Positive overview
- Watchdog for Vulnerability Response
- Change management for Vulnerability Response
- Software exposure assessment using Software Asset Management (SAM)
- Vulnerability Crisis Management
- Domain separation and Vulnerability Response
BreachSight
Vendor risk, trust exchange, product features, vendor risk assessments, security questionnaires.
- Security Ratings
Data Leaks Detection
- Integrations
AI Autofill
- Financial Services
eBooks, Reports, & more
What is a vulnerability assessment and how to conduct one.

Abi Tyas Tunggal
Vulnerability assessment is the process of identifying, classifying, and prioritizing security vulnerabilities in IT infrastructure. A comprehensive vulnerability assessment evaluates whether an IT system is exposed to known vulnerabilities, assigns severity levels to identified vulnerabilities, and recommends remediation or mitigation steps where required.
Vulnerability assessments are a common security procedure as they provide a detailed view of the security risks an organization may face, enabling them to better protect their information technology and sensitive data from cyber threats .
Vulnerabilities can be found in applications managed by third-party vendors or internally made software, and many flaws are easily fixed once identified.
Why is Vulnerability Assessment Important?
Vulnerability assessment is important because it provides you with information about the security weaknesses in your environment and provides direction on how to remediate or mitigate the issues before they can be exploited .
This process provides you with a better understanding of your IT infrastructure, security flaws and overall risk, which greatly improves information security and application security standards while reducing the likelihood that a cybercriminal will gain unauthorized access to your organization.
What are the Different Types of Vulnerability Assessment?
There are several types of vulnerability assessment:
- Network-based assessment: Used to identify possible network security issues and can detect vulnerable systems on wired and wireless networks.
- Host-based assessment: Used to locate and identify vulnerabilities in servers, workstations, and other network hosts. This scan typically examines open ports and services and can offer visibility into the configuration settings and patch management of scanned systems.
- Wireless network assessment: Used to scan Wi-Fi networks and attack vectors in the wireless network infrastructure. It can validate your company's network is securely configured to prevent unauthorized access and can also identify rogue access points.
- Application assessment: The identification of security vulnerabilities in web applications and their source code by using automated vulnerability scanning tools on the front-end or static/dynamic analysis of source code.
- Database assessment: The assessment of databases or big data systems for vulnerabilities and misconfiguration, identifying rogue databases or insecure dev/test environments, and classifying sensitive data to improve data security .
What is the Security Vulnerability Assessment Process?
The security vulnerability process consists of five steps:
- Vulnerability identification: Analyzing network scans, pen test results, firewall logs, and vulnerability scan results to find anomalies that suggest a cyber attack could take advantage of a vulnerability.
- Vulnerability analysis: Decide whether the identified vulnerability could be exploited and classify the severity of the exploit to understand the level of security risk.
- Risk assessment: Assess which vulnerabilities will be mitigated or remediated first based on their wormability and other risks.
- Remediation: Update affected software or hardware where possible.
- Mitigation: Decide on countermeasures and how to measure their effectiveness in the event that a patch is not available.
The vulnerability assessment process is a critical component of vulnerability management and IT risk management lifecycles and must be done on a regular basis to be effective.
For more information, see our guide on vulnerability management .
1. Vulnerability Identification
Vulnerability identification is the process of discovering and making a complete list of vulnerabilities in your IT infrastructure.
This is generally achieved through a combination of automated vulnerability scanning and manual penetration testing .
A vulnerability scanner can assess computers, networks or web applications for known vulnerabilities like those listed on the Common Vulnerabilities and Exposures (CVE) .
Vulnerability testing can be run via authenticated or unauthenticated scans:
- Authenticated scans: Allow vulnerability scanners access networked resources using remote administrative protocols and authenticate using provided system credentials. The benefit of authenticated scans is that they provide access to low-level data such as specific services, configuration details and accurate information about operating systems, installed software, configuration issues, access control , security controls and patch management.
- Unauthenticated scans: Don't provide access to networked resources, which can result in false positives and unreliable information about operating systems and installed software. This type of scan is generally used by cyber attackers and IT security analysts to try and determine the security posture of externally facing assets, third-party vendors and to find possible data leaks .
Learn how to identify vulnerable third-party software >
Like any security testing, vulnerability scanning isn't perfect which is why other techniques like penetration testing are used. Penetration testing is the practice of testing an information technology asset to find exploitable vulnerabilities and can be automated with software or performed manually.
Whether run automatically or performed manually by a security team, pen testing can find security flaws and possible attack vectors that are missed by vulnerability scanning tools. It can also be used to test on-premise security controls, adherence to information security policies , employees susceptibility to social engineering attacks like phishing or spear phishing , as well as to test incident response plans .
2. Vulnerability Analysis
After vulnerabilities are identified, you need to identify which components are responsible for each vulnerability, and the root cause of the security weaknesses. For example, the root cause of the vulnerability could be an outdated version of an open-source library.
In this situation, there is a clear path to remediation, upgrading the library. However, there isn't always a simple solution, which is why organizations often need to run each vulnerability through a security assessment process that classifies the severity of the vulnerability, identifies possible solutions, and decides whether to accept, remediate or mitigate the identified risk based on the organization's risk management strategy.
3. Risk Assessment
The objective of this step is to prioritize vulnerabilities. This often involves using a vulnerability assessment tool that assigns a rank or severity to each vulnerability.
For example, UpGuard BreachSight , an attack surface management tool, uses the Common Vulnerability Scoring System (CVSS) scores to assign a numerical score from 0 to 10 based on the principal characteristics and severity of the vulnerability.
With that said, any good vulnerability assessment report will take in additional factors such as:
- What system is affected
- What sensitive data is stored on the system, e.g. personally identifiable information (PII) or protected health information (PHI)
- What business functions rely on the system
- The ease of attack or compromise
- The business impact of a successful exploit
- Whether the vulnerability is accessible from the Internet or requires physical access
- How old the vulnerability is
- Any regulatory requirement your organization has, e.g. CCPA , FISMA , GLBA , PIPEDA , LGPD , 23 NYCRR 500 , FIPA , PCI DSS, HIPAA, or the SHIELD Act
- The cost of a data breach in your industry
Read our guide on how to perform an IT cybersecurity risk assessment >
4. Remediation
Vulnerability remediation involves fixing any security issues that were deemed unacceptable in the risk assessment process. This is typically a joint effort between development,operations, compliance, risk management, and security teams, who decide on a cost-effective path to remediate each vulnerability.
Many vulnerability management systems will provide recommended remediation techniques for common vulnerabilities, which can be as simple as installing readily-available security patches or as complex as replacing hardware.
Specific remediation steps will vary on the vulnerability but often include:
- Updating operational procedures
- Developing a robust configuration management process
- Patching software
5. Mitigation
Not every vulnerability can be remediated, which is where mitigation comes in. Mitigation is focused on reducing the likelihood that a vulnerability can be exploited or reducing the impact of the exploit.
Specific mitigation steps will vary greatly, depending on your risk tolerance and budget but often include:
- Introducing new security controls
- Replacing hardware or software
- Vendor risk management
- Attack surface management
- Continuous security monitoring
What Potential Threats Can Be Prevented by Vulnerability Assessment?
Examples of cyber attacks that can be prevented by vulnerability assessment include:
- Privilege escalation attacks: Privilege escalation is the exploitation of a programming error, vulnerability , design flaw, configuration oversight or access control in an operating system or application to gain unauthorized access to resources that are usually restricted from the application or user. Read more about privilege escalation here .
- SQL injections: SQL injection attacks happen when invalidated or untrusted data is sent to a code interpreter through form input or another data submission field in a web application. Successful injection attacks can result in data leaks , data corruption, data breaches , loss of accountability, and denial of access.
- XSS attacks: Cross-site scripting (XSS) is a type of security vulnerability typically found in web applications. XSS enables attackers to inject client-side scripts into web pages viewed by other users and may be used to bypass access control , such as the same-origin policy. The impact of XSS can range from a small nuisance to significant cybersecurity risk , depending on the sensitivity of data handled by the vulnerable website, and the nature of any mitigations implemented. Read more about cross-site scripting here .
- Insecure defaults: It's common for software and hardware to ship with insecure settings, such as easily guessable passwords, to make onboarding easier. While this is good from a usability perspective, many people leave these default configurations intact which can leave them exposed.
What are the Different Types of Vulnerability Assessment Tools?
Vulnerability assessment tools are designed to automatically scan for new and existing threats in your IT infrastructure. Types of tools include:
- Web application scanners that map out the attack surface and simulate know attack vectors
- Protocol scanners that search for vulnerable protocols, ports, and other services
- Network scanners that help visualize networks and discover network vulnerabilities like stray IP addresses, spoofed packets, and suspicious packet generation
It's best practice to schedule regular, automated scans of all infrastructure and use the results as part of your ongoing vulnerability assessment process.
UpGuard BreachSight will automatically scan your attack surface daily for vulnerabilities.
What's the Difference Between Vulnerability Assessment and Penetration Testing?
As noted above, a vulnerability assessment often includes penetration testing to identify vulnerabilities that might not be detected by automated scanning. This process is commonly referred to as vulnerability assessment/penetration testing (VAPT).
With that said, penetration testing alone isn't sufficient as a complete vulnerability assessment. Vulnerability assessment aims to uncover vulnerabilities and recommend the appropriate mitigation or remediation steps to reduce or remove the identified risk.
In contrast, penetration testing involves identifying vulnerabilities and attempting to exploit them to attack a system, cause a data breach , or expose sensitive data . While this can be carried out as part of a vulnerability assessment, the primary aim of penetration testing is to check whether a vulnerability exists that is exploitable.
Read our full post on penetration testing for more information .
How UpGuard Can Help With Vulnerability Assessment
Companies like Intercontinental Exchange , Taylor Fry , The New York Stock Exchange , IAG, First State Super, Akamai, Morningstar, and NASA use UpGuard's security ratings to protect their data, prevent data breaches and assess their security operations.
For the assessment of your information security controls, UpGuard BreachSight can monitor your organization for 70+ security controls providing a simple, easy-to-understand cyber security rating and automatically detect leaked credentials and data exposures in S3 buckets, Rsync servers, GitHub repos, and more.
The Vulnerabilities module of UpGuard BreachSight lists published vulnerabilities that may be exploitable in the software that is running on your IT infrastructure. These vulnerabilities are automatically identified through information exposed in HTTP headers and website content.
Each identified vulnerability is given a CVSS, a published standard developed to capture the principal characteristics of a vulnerability, that produces a numerical score between 0 and 10 reflecting its severity.
UpGuard Vendor Risk can minimize the amount of time your organization spends assessing related and third-party information security controls by automating vendor questionnaires and providing vendor questionnaire templates .
Our expertise has been featured in the likes of The New York Times , The Wall Street Journal , Bloomberg , The Washington Post , Forbes , Reuters , and TechCrunch.
You can read more about what our customers are saying on Gartner reviews .
Reviewed by

Kaushik Sen
Ready to see upguard in action, ready to save time and streamline your trust management process, join 27,000+ cybersecurity newsletter subscribers.
Related posts
The top cybersecurity websites and blogs of 2024, 14 cybersecurity metrics + kpis you must track in 2024, what are security ratings cyber performance scoring explained, why is cybersecurity important, what is typosquatting (and how to prevent it), introducing upguard's new sig lite questionnaire.

- UpGuard Vendor Risk
- UpGuard BreachSight
- Product Video
- Release notes
- SecurityScorecard
- All comparisons
- Security Reports
- Instant Security Score
- Third-Party Risk Management
- Attack Surface Management
- Cybersecurity
Home » What Is Vulnerability Management? Process, Assessment, and Best Practices
What Is Vulnerability Management? Process, Assessment, and Best Practices

In recent years, cybersecurity has established itself as a critical concern. However, as new threats come to light, the danger environment continuously changes.
Seventy percent of international company executives believe cybersecurity will become a more significant concern in the next five years. The actions taken by organizations today have an impact on how well they get ready for issues down the road.
An essential cybersecurity technique (and process) that organizations need to implement to prevent unintentional data theft and protect from direct, specific attacks is Vulnerability management.
To keep up with the growing number of threats, vulnerability management is a dynamic field that is becoming more sophisticated. Vulnerability management reveals the increasing severity of attacks and the actual degree of readiness of many organizations in the event of a cyberattack.
The development of a continuous process for vulnerability detection, study, and patching will be addressed in this article.
What is Vulnerability Management?
Vulnerability management is an organization’s multi-step approach to mitigating security risks. Finding vulnerabilities in cloud-based systems, apps, and infrastructure is a sophisticated vulnerability management procedure.
Considering the growing cyber risk that organizations confront as we approach 2024, this step is crucial:
Vulnerability management has evolved gradually from a primarily human approach to increasingly complex, automated methods. Specific tools are needed to detect and rank risks to develop and execute adequate strategies to prevent an intrusion on an IT system’s security.
Using a systematic approach to threat identification, vulnerability management establishes the groundwork for long-term management customized for the requirements and operations of each organization.
In simple terms, Vulnerability management identifies, determines, prioritizes, and minimizes security vulnerabilities inside your IT environment. Reducing the probability of a breach by fixing system weaknesses before they can be used to compromise your systems is the primary goal of vulnerability management.
Any weakness in a network’s architecture, operation, or design that an attacker could leverage to carry out a cybercrime is a security vulnerability.
Typical Vulnerabilities are outlined below:
- Incorrect configurations of the system
- Application Programming Interfaces (APIs) without security
- software that has not been patched or updated
- insufficient or lacking authorization credentials
- inadequate policies for access control
- Incomplete or insufficient data entry
- zero-day vulnerabilities.
Vulnerability Management: Best Practices
Effective vulnerability management is necessary for an organization’s IT infrastructure to remain secure and intact.
In this section, we’ll discuss a few recommended practices for vulnerability management.
Specify your Objectives and Scope
Determining the objectives and constraints of your vulnerability analysis is necessary before you begin examining and evaluating your assets. Which crucial information and systems must you preserve? What threats and risks are there in your line of work? Which security rules and compliance requirements do you have to adhere to?
By answering these questions, you may have a better understanding of your goals, set expectations, and synchronize your goals with those of your stakeholders.
Go Proactive and Determine KPIs
Planning and strategy must come in initial stages, just like in any other company initiative, and then the Key Performance Indicators (KPIs) must be developed.
In addition to giving, you the tools to evaluate the return on investment (ROI) that your vulnerability management software or solution is producing, KPIs also direct your security team and provide you with achievable goals to strive towards.
A few valuable KPIs to incorporate are:
- vulnerability coverage, completeness, and vulnerabilities for each server in each security region
- Frequency and intensity of scans
- Patching time
- The speed at which your programmers are addressing vulnerabilities and the duration of high-risk vulnerabilities that have not yet been patched.
Define Tasks and Asset Classifications
Classifying and prioritizing assets according to their actual and inherent risk to the organization is extremely important, and it comes after taking an inventory of them.
This risk classification will inform the periodicity of vulnerability scanning and the order of importance of remedial operations.
Designating system owners as the ultimate responsible parties for the risks connected with an asset and their obligation if the asset is compromised is another crucial aspect of assigning ownership of assets.
Develop a Database for Vulnerability Management
A comprehensive picture of your company’s IT assets and the level of importance of each asset is obtained by mapping out and identifying all digital assets, systems, related and third-party systems and processes, IT infrastructure, hardware, software, computers, databases, management systems for content, development frameworks, ports, and so forth during the discovery phase of virtual machine (VM) deployment.
Just building the database once and leaving it that way is inadequate. The security posture of your virtual machine database is only as effective as the data before the update. As a result, you need to update the VM database often.
Conduct Regular Automated Vulnerability Analysis
Organizations should regularly perform automated vulnerability scanning tools for every machine on the network as part of persistent vulnerability management.
Tools for vulnerability scanning ought to be dependable, Adaptable, and reliable.
Regardless of the framework you choose, scanning should occur at least once a month or once every three months.
On the other hand, threat actors find new vulnerabilities daily, and many of them are turned into weapons within hours or days after their discovery. This implies that the final 29 days might expose your company to risk if you conduct monthly scanning.
Certera advises continuously approaching your scans. Weekly or even daily scans can be suitable, depending on your organization. ~ Website Vulnerability Scanning
Use the Appropriate Frameworks and Standards
Your vulnerability assessment in your sector can be guided and supported by several different standards and frameworks. NIST SP 800-115, OWASP Top 10, ISO/IEC 27001, PCI DSS, and CVSS are a few of the widely used ones.
Best techniques, processes, standards, metrics, and references are offered by these frameworks and standards for doing vulnerability evaluations in various settings and domains.
Applying the appropriate frameworks and standards can help you accomplish security and compliance while fitting your goals and scope.
Set Vulnerabilities in Order of Significance and Carry Out Measures to Fix Them
Organizations must rank vulnerabilities according to how they affect the company and implement the necessary fixes.
High-risk vulnerabilities should be fixed first in a well-established vulnerability remediation procedure. Not CVSS scores, but business risk is what we mean when we term “high risk” in business terms.
Blend Vulnerability Management with Additional Security Procedures And Solutions
As part of a comprehensive approach, vulnerability management should be combined with other security procedures and solutions.
Companies ought to think about combining vulnerability management with the following:
- Threat Intelligence
- Incident Response
- Network Security
- Access Control
An organization’s security posture may be improved by taking a comprehensive approach to security by integrating vulnerability management with other security procedures and solutions.
The Lifecycle of Vulnerability Management
An organization can actively address system vulnerabilities by using the Vulnerability Management Lifecycle, which is intended to be a continuous management process that involves identification, prioritization, evaluation, acting, rechecking, and enhancement.
Identification:
Identifying and focusing on the assets that need to be a part of the vulnerability assessment is called identification.
Prioritization:
The assets according to importance or influence on the firm’s operations and prioritize them.
Based on the asset finding, carry out the vulnerability scan. Make reports to make sure every object is scanned correctly and yields information.
Discuss the vulnerability report with the relevant parties. Create a plan for risk acceptance or remediation.
Evaluate again to make sure dangers are removed and to show that mitigation measures are effective.
Regularly assess the status of your vulnerability program. Explore methods to enhance and protect your network from novel and upcoming dangers.
Vulnerability Management vs. Vulnerability Assessment
Vulnerability management involves a thorough system scan by cyber security professionals to get information on vulnerabilities, of which vulnerability assessments are only a tiny portion.
- Which dangers pose a risk to the company’s network?
- Which risks are the biggest?
- Which dangers are most likely to materialize?
Frequent scanning sessions are necessary for assessment to gather information for creating an action plan and ranking the hazards that demand immediate attention.
Let’s explore this distinction from the perspective of a physical property owner to clarify it more. If you own a valuable construction, you most likely take certain precautions to keep it safe.
- You maintain it.
- You have insurance for it.
- You confirm that the windows and doors are locked.
- You configure the alarms.
These steps are part of controlling the risk to the property and its contents.
Suppose you hired an individual only to test your alarms and external defenses and provide a report. An evaluation would be a better term for it. While your assessment is a one-time exercise with set objectives or standards, the administration of the security on your property is a continuous procedure made up of everything pertinent to the process.
Similar methods are used to address cybersecurity issues. Vulnerability assessments are one technique used in a more extensive, comprehensive approach called vulnerability management.
Vulnerability Management Benefits
We now have a better understanding of vulnerability management, including its definition, methodology, structure, and implications for you and your company.
To save you time, we’ve compiled a list of a few advantages of vulnerability management.
Very Economical
Cost-effectiveness is unquestionably one of the main advantages for every organization, and vulnerability management offers several cost-saving benefits.
Ad hoc patching is removed, which might result in missing fixes and increased expenses.
By assisting the company in focusing attention and setting priorities around assets that pose the most significant risk of being exploited, it also helps to lower technological debt.
In other words, vulnerability management gives an organization’s security posture more excellent structure and accuracy. This helps the organization justify its security posture to stakeholders, who are more willing to support vulnerability efforts.
Reacting Instantly to Threats
The bad guys never sleep or take a vacation! Every day, new vulnerabilities are discovered that catch us off guard.
For example, all organizations were put on high alert after the Log4j vulnerability was discovered the day before November 2021.
Organizations may transition from a reactive to a proactive reaction with vulnerability management.
A continuous patch management procedure guarantees that significant vulnerabilities are identified and prioritized and that the resources are available to fix them immediately. Doing this creates the framework for a speedier and more efficient reaction to any new risks.
Improves Transparency And Access
As was previously said, vulnerability management aids in developing a tracking and reporting system while doing a vulnerability assessment.
A project’s transparency can aid in supporting other initiatives by helping stakeholders understand the return on investment in security.
The team is further helped by vulnerability reporting, which offers actionable dashboards and trend data for fast program evaluation and performance assessment. Senior management may use these contextualized reports’ essential metrics and indicators to make well-informed choices on important initiatives.
Boost Consumer Confidence
Organizations have been compelled to audit third-party suppliers due to the improvement in ransomware and supply chain attacks, such as the Kaseya ransomware attack, which has increased stakeholder awareness of the risks associated with unsecured systems. Key metric indicators and executive-level reports give customers and stakeholders insight into the program’s status.
This is a crucial aspect of contemporary business practices, as more and more stakeholders evaluate the risk of conducting business in light of an organization’s security posture. Possessing the information and tools necessary to report on the company’s state increases its legitimacy and the likelihood of conducting business.
If you still need to develop a cybersecurity program, establishing security policies is an excellent place to start.
Challenges in Implementing Vulnerability Management
The following are a few factors why most companies still see vulnerability management to be a significant challenge:
Monitoring the Number of Vulnerabilities
Common Vulnerabilities and Exposures , or CVEs, are in the hundreds and are added monthly. It makes sense that organizations cannot patch even the most severe vulnerabilities on time. Even years after fixes have been released, many businesses still use known vulnerabilities.
Serious Software Vulnerabilities that are Difficult to Patch or Repair
Patching is insufficient or unavailable at times. Organizations must use other strategies to reduce these vulnerabilities, such as opening ports, incorrect setups, and lax access and authentication procedures. Unfortunately, this procedure may be very resource-intensive for a lot of businesses. Cybersecurity experts must assess the vulnerability, identify its mitigation, and personally carry out any necessary corrections.
Considering Patching and Maintenance Tasks for IT and Cybersecurity as a Top Priority
Due to competing goals and a lack of resources, many organizations need help to address vulnerabilities. Examples include:
- Introducing new apps.
- Allocating funds and staff to handle patch maintenance and vulnerability concerns.
- Addressing other time-consuming tasks like compliance reporting.
In most cases, manual patching procedures or a lack of automation are the underlying causes of this lack of priority in organizations. IT and cybersecurity operations must catch up if prioritization isn’t a component of your vulnerability management plan since it takes so long to test, patch, or deploy updates to resolve vulnerabilities.
In What Ways Does Certera Support Vulnerability Management?
Certera, a cutting-edge and renowned Certificate Authority, offers ongoing, on-demand security testing by providing various security solutions for your company. You could track the platform’s progress through exploration, evaluation, repeat testing, and correction phases.
We’ll support your security teams in identifying and fixing vulnerabilities before hackers take profit from them, whether the objectives are to launch a product, meet regulatory requirements, or show compliance.
Common FAQ’s
What is a vulnerability in practice.
Vulnerability involves uncertainty, danger, and emotional exposure. It occurs when you take a risk, attempt something different, or step beyond your comfort zone. It’s like that crazy rush of emotions you get when you first try out yoga, and you don’t know what you are doing, but you do it anyway.
What is the Most Effective Way to Handle Vulnerabilities?
Organizations should begin with these fundamental vulnerability management best practices:
- Map all assets and evaluate exposure.
- Threat data powers vulnerability management lifecycles.
- Encourage inter-team cooperation in the correction of vulnerabilities.
- Combine with other company security solutions.
The systematic detection, prioritization, prevention, validation, and reporting of vulnerabilities inside an organization’s information systems and software applications is done through a continuous and organized process called the Vulnerability Management Lifecycle.
Vulnerability Management Lifecycle: What Is It?
By regularly addressing and managing vulnerabilities considering the changing threat landscape, this lifecycle is essential to enhancing an organization’s overall security posture, guaranteeing the protection and confidentiality of sensitive data, and lowering the chance of exploitation.

Janki Mehta
Janki Mehta is a passionate Cyber-Security Enthusiast who keenly monitors the latest developments in the Web/Cyber Security industry. She puts her knowledge into practice and helps web users by arming them with the necessary security measures to stay safe in the digital world.
EncryptedFence Blog
Subscribe to our newsletter.
Never miss any Update on Cyber Security
We respect your privacy and we will not use your email for spam!
Home > Learning Center > Vulnerability Assessment
Article's content

Need help protecting your applications?
See how imperva can help, vulnerability assessment, what is vulnerability assessment.
A vulnerability assessment is a systematic review of security weaknesses in an information system. It evaluates if the system is susceptible to any known vulnerabilities, assigns severity levels to those vulnerabilities, and recommends remediation or mitigation, if and whenever needed.
Examples of threats that can be prevented by vulnerability assessment include:
- SQL injection , XSS and other code injection attacks.
- Escalation of privileges due to faulty authentication mechanisms.
- Insecure defaults – software that ships with insecure settings, such as a guessable admin passwords.
There are several types of vulnerability assessments. These include:
- Host assessment – The assessment of critical servers, which may be vulnerable to attacks if not adequately tested or not generated from a tested machine image.
- Network and wireless assessment – The assessment of policies and practices to prevent unauthorized access to private or public networks and network-accessible resources.
- Database assessment – The assessment of databases or big data systems for vulnerabilities and misconfigurations, identifying rogue databases or insecure dev/test environments, and classifying sensitive data across an organization’s infrastructure.
- Application scans – The identifying of security vulnerabilities in web applications and their source code by automated scans on the front-end or static/dynamic analysis of source code.
This is part of an extensive series of guides about [ data security ]
Vulnerability assessment: Security scanning process
The security scanning process consists of four steps: testing, analysis, assessment and remediation.

1. Vulnerability identification (testing)
The objective of this step is to draft a comprehensive list of an application’s vulnerabilities. Security analysts test the security health of applications, servers or other systems by scanning them with automated tools, or testing and evaluating them manually. Analysts also rely on vulnerability databases, vendor vulnerability announcements, asset management systems and threat intelligence feeds to identify security weaknesses.
2. Vulnerability analysis
The objective of this step is to identify the source and root cause of the vulnerabilities identified in step one.
It involves the identification of system components responsible for each vulnerability, and the root cause of the vulnerability. For example, the root cause of a vulnerability could be an old version of an open source library. This provides a clear path for remediation – upgrading the library.
3. Risk assessment
The objective of this step is the prioritizing of vulnerabilities. It involves security analysts assigning a rank or severity score to each vulnerability, based on such factors as:
- Which systems are affected.
- What data is at risk.
- Which business functions are at risk.
- Ease of attack or compromise.
- Severity of an attack.
- Potential damage as a result of the vulnerability.
4. Remediation
The objective of this step is the closing of security gaps. It’s typically a joint effort by security staff, development and operations teams, who determine the most effective path for remediation or mitigation of each vulnerability.
Specific remediation steps might include:
- Introduction of new security procedures, measures or tools.
- The updating of operational or configuration changes.
- Development and implementation of a vulnerability patch.
Vulnerability assessment cannot be a one-off activity. To be effective, organizations must operationalize this process and repeat it at regular intervals. It is also critical to foster cooperation between security, operation and development teams – a process known as DevSecOps .
Battling Bad Bots: The Latest Trends, Stats & Defense Strategies
Register Now
Vulnerability assessment tools
Vulnerability assessment tools are designed to automatically scan for new and existing threats that can target your application. Types of tools include:
- Web application scanners that test for and simulate known attack patterns.
- Protocol scanners that search for vulnerable protocols, ports and network services.
- Network scanners that help visualize networks and discover warning signals like stray IP addresses, spoofed packets and suspicious packet generation from a single IP address.
It is a best practice to schedule regular, automated scans of all critical IT systems. The results of these scans should feed into the organization’s ongoing vulnerability assessment process.
Vulnerability assessment and WAF
Imperva’s web application firewall helps protect against application vulnerabilities in several ways:
- As a gateway for all incoming traffic, it can proactively filter out malicious visitors and requests, such as SQL injections and XSS attacks. This eliminates the risk of data exposure to malicious actors.
- It can perform virtual-patching — the auto-applying of a patch for a newly discovered vulnerability at the network edge, giving developers and IT teams the opportunity to safely deploy a new patch on the application without concern.
- Our WAF provides a view of security events. Attack Analytics helps contextualize attacks and expose overarching threats, (e.g., showing thousands of seemingly unrelated attacks as part of one big attack campaign).
- Our WAF integrates with all leading SIEM platforms to provide you with a clear view of the threats you’re facing and help you prepare for new attacks.
See Additional Guides on Key Data Security Topics
Together with our content partners, we have authored in-depth guides on several other topics that can also be useful as you explore the world of data security .
Authored by Cynet
- EDR Security: Protecting the Network From Endpoint Threats
- EPP vs. EDR: What Matters More, Prevention or Response?
- Endpoint Detection and Response (EDR) in Healthcare
Incident Response
- What Is Incident Response? Strategy, Process, Templates & More
- What Is a SOC? 10 Core Functions and 6 Key Challenges
- Security Stack Examples & 6 Best Practices for Building Your Stack
See how Imperva Web Application Firewall can help you with vulnerability assessment.
Object Storage
Authored by Cloudian
- What is Object Storage: Definition, How It Works and Use Cases
- Object Storage vs. File Storage: What’s the Difference?
- Object Storage vs. Block Storage: Head to Head
Latest Blogs

Luke Richardson
Dec 27, 2023 6 min read

Erez Hasson
Dec 21, 2023 2 min read

Dec 7, 2023 6 min read
Latest Articles
- Testing and Assessment
664.5k Views
202.2k Views
124.1k Views
83.8k Views
41.8k Views
28.9k Views
28.6k Views
2024 Bad Bot Report
Bad bots now represent almost one-third of all internet traffic
The State of API Security in 2024
Learn about the current API threat landscape and the key security insights for 2024
Protect Against Business Logic Abuse
Identify key capabilities to prevent attacks targeting your business logic
The State of Security Within eCommerce in 2022
Learn how automated threats and API attacks on retailers are increasing
Prevoty is now part of the Imperva Runtime Protection
Protection against zero-day attacks
No tuning, highly-accurate out-of-the-box
Effective against OWASP top 10 vulnerabilities
An Imperva security specialist will contact you shortly.
Top 3 US Retailer

What is vulnerability management?
Vulnerability management is a risk-based approach to discovering, prioritizing, and remediating vulnerabilities and misconfigurations.
- Discover Microsoft Defender Vulnerability Management

Vulnerability management defined
Vulnerability management is a continuous, proactive, and often automated process that keeps your computer systems, networks, and enterprise applications safe from cyberattacks and data breaches. As such, it is an important part of an overall security program. By identifying, assessing, and addressing potential security weaknesses, organizations can help prevent attacks and minimize damage if one does occur.
The goal of vulnerability management is to reduce the organization's overall risk exposure by mitigating as many vulnerabilities as possible. This can be a challenging task, given the number of potential vulnerabilities and the limited resources available for remediation. Vulnerability management should be a continuous process to keep up with new and emerging threats and changing environments.
How vulnerability management works
Threat and vulnerability management uses a variety of tools and solutions to prevent and address cyberthreats. An effective vulnerability management program typically includes the following components:
Asset discovery and inventory IT is responsible for tracking and maintaining records of all devices, software, servers, and more across the company’s digital environment, but this can be extremely complex since many organizations have thousands of assets across multiple locations. That’s why IT professionals turn to asset inventory management systems, which help provide visibility into what assets a company has, where they’re located, and how they’re being used.
Vulnerability scanners Vulnerability scanners usually work by conducting a series of tests against systems and networks, looking for common weaknesses or flaws. These tests can include attempting to exploit known vulnerabilities, guessing default passwords or user accounts, or simply trying to gain access to restricted areas.
Patch management Patch management software is a tool that helps organizations keep their computer systems up to date with the latest security patches. Most patch management solutions will automatically check for updates and prompt the user when new ones are available. Some patch management systems also allow for deployment of patches across multiple computers in an organization, making it easier to keep large fleets of machines secure.
Configuration Management Security Configuration Management (SCM) software helps to ensure that devices are configured in a secure manner, that changes to device security settings are tracked and approved, and that systems are compliant with security policies. Many SCM tools include features that allow organizations to scan devices and networks for vulnerabilities, track remediation actions, and generate reports on security policy compliance.
Security incident and event management(SIEM) SIEM software consolidates an organization's security information and events in real time. SIEM solutions are designed to give organizations visibility into everything that's happening across their entire digital estate, including IT infrastructure. This includes monitoring network traffic, identifying devices that are trying to connect to internal systems, keeping track of user activity, and more.
Penetration testing Penetration testing software is designed to help IT professionals find and exploit vulnerabilities in computer systems. Typically, penetration testing software provides a graphical user interface (GUI) that makes it easy to launch attacks and see the results. Some products also offer automation features to help speed up the testing process. By simulating attacks, testers can identify weak spots in systems that could be exploited by real-world attackers.
Threat intelligence Threat protection software provides organizations with the ability to track, monitor, analyze, and prioritize potential threats to better protect themselves. By collecting data from a variety of sources—such as exploit databases and security advisories—these solutions help companies identify trends and patterns that could indicate a future security breach or attack.
Remediation vulnerabilities Remediation involves prioritizing vulnerabilities, identifying appropriate next steps, and generating remediation tickets so that IT teams can execute on them. Finally, remediation tracking is an important tool for ensuring that the vulnerability or misconfiguration is properly addressed.
Vulnerability management lifecycle
The vulnerability management lifecycle has six key phases. Organizations looking to implement or improve their vulnerability management program can follow these steps.

Phase 1: Discovery
Create a full asset inventory across your organization’s network. Develop a baseline for your security program by identifying vulnerabilities on an automated schedule so you can stay ahead of threats to company information.

Phase 4: Reporting
Next, determine the various levels of risk associated with each asset based on your assessment results. Then, document your security plan and report known vulnerabilities.

Phase 2: Prioritization of assets
Assign a value to each asset group that is reflective of its criticality. This will help you understand which groups need more attention and will help streamline your decision-making process when faced with allocating resources.

Phase 5: Remediation
Now that you know which vulnerabilities are the most pressing for your business, it’s time to fix them, starting with those that pose the highest risks.

Phase 3: Assessment
The third part of the vulnerability management lifestyle is assessing your assets to understand the risk profile of each one. This allows you to determine which risks to eliminate first based on a variety of factors, including its criticality and vulnerability threat levels as well as classification.

Phase 6: Verification and monitoring
The final phase of the vulnerability management process includes using regular audits and process follow-up to ensure that threats have been eliminated.
Vulnerability management benefits
Vulnerability management helps businesses identify and fix potential security issues before they become serious cybersecurity concerns. By preventing data breaches and other security incidents, vulnerability management can prevent damage to a company's reputation and bottom line.
Additionally, vulnerability management can improve compliance with various security standards and regulations. And finally, it can help organizations better understand their overall security risk posture and where they may need to make improvements.
In today’s hyperconnected world, running occasional security scans and dealing with cyberthreats in a reactive manner is not a sufficient cybersecurity strategy. A solid vulnerability management process has three key advantages over ad hoc efforts, including:
Improved security and control By regularly scanning for vulnerabilities and patching them in a timely manner, organizations can make it significantly harder for attackers to gain access to their systems. Additionally, robust vulnerability management practices can help organizations identify potential weaknesses in their security posture before attackers do.
Visibility and reporting Vulnerability management provides centralized, accurate, and up-to-date reporting on the status of an organization’s security posture, giving IT personnel at all levels real-time visibility into potential threats and vulnerabilities.
Operational efficiencies By understanding and mitigating security risks, businesses can minimize system downtime and protect their data. Improving the overall vulnerability management process also decreases the amount of time required to recover from any incidents that do occur.
How to manage vulnerabilities
Once you have a vulnerability management program in place, there are four basic steps for managing known and potential vulnerabilities as well as misconfigurations.
Step 1: Identify vulnerabilities Scanning for vulnerabilities and misconfigurations is often at the center of a vulnerability management program. Vulnerability scanners—which are typically continuous and automated—identify weaknesses, threats, and potential vulnerabilities across systems and networks.
Step 2: Evaluate vulnerabilities Once potential vulnerabilities and misconfigurations are identified, they must be validated as a true vulnerability, rated according to risk, and prioritized based on those risk ratings.
Step 3: Address vulnerabilities After evaluation, organizations have a few options for treating known vulnerabilities and misconfigurations. The best option is to remediate, which means fully fixing or patching vulnerabilities. If full remediation isn’t possible, organizations can mitigate, which means decreasing the possibility of exploitation or minimizing the potential damage. Finally, they can accept the vulnerability—for example, when the associated risk is low—and take no action.
Step 4: Report vulnerabilities Once vulnerabilities are treated, it’s important to document and report known vulnerabilities. Doing so helps IT personnel track vulnerability trends across their networks and ensures that organizations remain compliant with various security standards and regulations.
Vulnerability management solutions
Clearly, having a solid vulnerability management process in place is not only a smart decision—it’s a necessary one. It's critical to find a vulnerability management solution that bridges the gap between teams, maximizes resources, and provides all your visibility, assessment, and remediation capabilities in a single place.
Learn more about Microsoft Security
Vulnerability management.
Bridge the gap between security and IT teams to seamlessly remediate vulnerabilities.
Microsoft SIEM and XDR
Get integrated threat protection across devices, identities, apps, email, data and cloud workloads.
Endpoint security
Secure Windows, macOS, Linux, Android, iOS, and network devices against threats.
Reduce security vulnerabilities
Get a comprehensive walk-through of threat and vulnerability management.
Frequently asked questions
What are some types of vulnerabilities in cybersecurity.
Some common types of vulnerabilities in cybersecurity include:
- Weak passwords
- Insufficient authentication and authorization procedures, such as those that lack 2FA and MFA
- Unsecure networks and communications
- Malware and viruses
- Phishing scams
- Unpatched software and hardware vulnerabilities
Why do we need vulnerability management?
Vulnerability management is essential for any organization that relies on information technology, as it helps to protect against known and unknown threats. In today's hyperconnected world, new vulnerabilities are constantly being discovered, so it's important to have a process in place for managing them. By implementing a vulnerability management program, you can reduce the risk of exploitation and safeguard your organization against potential attacks.
What is the difference between vulnerability management and assessment?
The key difference between vulnerability management and assessment is that vulnerability management is an on-going process while vulnerability assessment is a one-time event. Vulnerability management is the process of continuously identifying, evaluating, treating, and reporting vulnerabilities. Assessment, on the other hand, is the act of determining the risk profile of each vulnerability.
What is vulnerability scanning in cybersecurity?
Vulnerability scanning is the process of identifying known and potential security vulnerabilities. Vulnerability scanners—which can be operated manually or automatically—use various methods to probe systems and networks. Once a vulnerability is found, the scanner will attempt to exploit it in order to determine whether a hacker could potentially exploit it as well. This information can then be used to help organizations patch their systems and develop a plan to improve their overall security posture.
What are some common methods for managing vulnerabilities?
There are many ways to manage vulnerabilities, but some common methods include:
- Using vulnerability scanning tools to identify potential vulnerabilities before they can be exploited
- Restricting access to sensitive information and systems to authorized users only
- Updating software and security patches regularly
- Deploying firewalls, intrusion detection systems, and other security measures to protect against attacks
Follow Microsoft
- Chat with sales
Available M-F 6 AM to 6 PM PT.

Point of Contact
- Vulnerability 101
Mass Assignment Vulnerability: Understanding & Mitigating the Risks in API
Mass assignment vulnerability is a critical security concern that often goes unnoticed in API development. Understanding the risks associated with this vulnerability is crucial for protecting sensitive user data. In this article, we will delve into the details of mass assignment vulnerabilities and explore effective mitigation strategies.
Introduction:
The "Mass Assignment" vulnerability is a security flaw that occurs when an application assigns user input directly to model attributes without proper validation or sanitization. This can lead to unauthorized access and modification of sensitive data, potentially compromising the security of the application and its users.
Addressing the "Mass Assignment" vulnerability is crucial for developers as it can have serious consequences, including data breaches, unauthorized access, and legal implications. Understanding and mitigating this vulnerability is essential to ensure the integrity and security of an application.
Understanding the "Mass Assignment" Vulnerability:
The "Mass Assignment" vulnerability occurs when an attacker is able to manipulate the values of model attributes by submitting unexpected or malicious data. This can happen when developers use frameworks or libraries that automatically map user input to object properties without proper validation or filtering.
Common scenarios where developers may unintentionally introduce the "Mass Assignment" vulnerability include:
- Using frameworks or libraries that provide automatic mapping of user input to object properties without considering the security implications.
- Allowing users to submit data that directly maps to sensitive attributes without proper validation.
- Failing to implement proper input validation and sanitization techniques.
The impact of the "Mass Assignment" vulnerability can be severe. Attackers can exploit this vulnerability to gain unauthorized access to sensitive data, modify user privileges, or even execute arbitrary code on the server. This can lead to data breaches, compromised user accounts, and potential legal issues.
Common Examples of "Mass Assignment":
There are several common examples of the "Mass Assignment" vulnerability. Let's explore a few of them:
User Profile Update: Suppose an application allows users to update their profile information, including their email address and password. If the application blindly maps user input to the corresponding model attributes without proper validation, an attacker can manipulate the request to update other sensitive fields such as admin privileges.
Role-Based Access Control: In applications with role-based access control, developers often use a single parameter to assign roles to users. If this parameter is not properly validated, an attacker can modify it to gain unauthorized access to sensitive functionality or elevate their privileges.
API Endpoints: APIs that accept JSON or XML payloads are also susceptible to the "Mass Assignment" vulnerability. If the API endpoint maps the incoming request directly to model attributes without proper validation, an attacker can manipulate the payload to modify sensitive data or gain unauthorized access.
These examples highlight the importance of implementing proper validation and sanitization techniques to mitigate the risks associated with the "Mass Assignment" vulnerability.
Risks and Consequences:
The "Mass Assignment" vulnerability poses significant risks and consequences for both developers and users. Some of the potential risks and consequences include:
Data Breaches: Exploiting the "Mass Assignment" vulnerability can lead to unauthorized access to sensitive data, including personal information, financial records, and confidential business data. This can result in serious privacy breaches and financial losses.
Unauthorized Access and Privilege Escalation: Attackers can manipulate the values of model attributes to gain unauthorized access to restricted functionality or elevate their privileges within the application. This can lead to unauthorized actions, such as modifying critical settings, accessing sensitive data, or impersonating other users.
Reputation Damage: Security breaches resulting from the "Mass Assignment" vulnerability can severely damage the reputation of the application and its developers. Users lose trust in the application's ability to protect their data, leading to a loss of user base and potential legal consequences.
Legal Implications: Depending on the nature of the application and the data involved, security breaches resulting from the "Mass Assignment" vulnerability can have legal implications. Developers may face legal actions, regulatory fines, and potential lawsuits for failing to protect user data adequately.
Real-world examples of security breaches resulting from the "Mass Assignment" vulnerability include the 2012 GitHub incident, where an attacker exploited the vulnerability to gain administrative access to repositories. This incident highlighted the severity and impact of this vulnerability.
Best Practices for Mitigating the "Mass Assignment" Vulnerability:
To mitigate the risks associated with the "Mass Assignment" vulnerability, developers should follow these best practices:
Whitelist Input Validation: Developers should implement strong input validation techniques to ensure that only expected and valid data is accepted. This includes whitelisting allowed attributes and rejecting any unexpected or malicious input.
Use Role-Based Access Control (RBAC): Implement RBAC to control user privileges and access to sensitive functionality. Do not rely solely on user input to determine roles and permissions.
Implement Attribute-Level Access Controls: Instead of blindly mapping all user input to corresponding attributes, developers should implement attribute-level access controls. This ensures that only authorized users can modify specific attributes.
Sanitize and Filter User Input: Before assigning user input to model attributes, developers should sanitize and filter the data to remove any potential malicious content. This includes validating data types, length restrictions, and ensuring data integrity.
Implement Secure Coding Practices: Follow secure coding practices, such as avoiding dynamic attribute assignment, using strong encryption for sensitive data, and regularly updating frameworks and libraries to their latest secure versions.
Regular Security Testing and Auditing: Conduct regular security testing and auditing of the application to identify and mitigate any vulnerabilities, including the "Mass Assignment" vulnerability. This includes penetration testing, code review, and vulnerability scanning.
Tools and Resources:
To aid developers in addressing the "Mass Assignment" vulnerability, the following tools, libraries, and resources can be helpful:
OWASP Cheat Sheet - Mass Assignment: The OWASP Cheat Sheet provides guidelines and recommendations for securing web applications against the "Mass Assignment" vulnerability. It offers practical advice and code snippets for developers to implement secure coding practices.
Security-Focused Libraries and Frameworks: Many programming languages and frameworks provide security-focused libraries and modules that can help mitigate the "Mass Assignment" vulnerability. Examples include Django's ModelForm, Laravel's Mass Assignment Protection, and Ruby on Rails' Strong Parameters.
Platform-Specific Security Guidelines: Developers should refer to platform-specific security guidelines and resources provided by the framework or platform they are using. These guidelines often include best practices and recommendations for securing applications against common vulnerabilities, including "Mass Assignment."
Code Review and Testing Tools: Developers should leverage code review and testing tools to identify and mitigate the "Mass Assignment" vulnerability. Tools like SonarQube, OWASP ZAP, and Burp Suite can help identify security flaws in the code and test the application for vulnerabilities.
The Role of Security Testing and Auditing:
Regular security testing and auditing play a crucial role in identifying and mitigating the "Mass Assignment" vulnerability. Various testing techniques can be employed, including:
Penetration Testing: Conducting penetration tests can help identify vulnerabilities and potential attack vectors, including the "Mass Assignment" vulnerability. Ethical hackers simulate real-world attacks to identify security weaknesses and provide recommendations for improvement.
Code Review: Manual code review or automated tools can help identify insecure coding practices, including instances of the "Mass Assignment" vulnerability. Developers should review their code regularly and ensure it follows best practices for secure coding.
Vulnerability Scanning: Automated vulnerability scanning tools can scan the application for known vulnerabilities, including the "Mass Assignment" vulnerability. These tools can help identify potential weaknesses and provide guidance on how to address them.
By employing these testing techniques, developers can proactively identify and mitigate the "Mass Assignment" vulnerability, ensuring the security and integrity of their applications.
Conclusion:
Addressing the "Mass Assignment" vulnerability is crucial for developers to protect the integrity and security of their applications. By understanding the definition, risks, and consequences of the vulnerability, developers can take proactive measures to mitigate its impact.
Implementing best practices, such as whitelisting input validation, utilizing role-based access control, and regular security testing and auditing, can significantly reduce the risks associated with the "Mass Assignment" vulnerability.
Need Help? Hire us part-time
Hire a dedicated, part-time security consultant with over 10+ years of experience to work closely with your dev/security team. you only pay for the time you need, with no long-term contracts. learn more.
Secured High Growth Companies Worldwide
Let's find out if we are a good fit with a 30-min intro call
Plans start from $1,000. No Contracts, Cancel Anytime.
See NinjaOne in action!
What Is a Vulnerability Assessment & Why Is It Important?

- by Lauren Ballejos | reviewed by Stan Hunter
- Last updated March 7, 2024

While cloud computing has ushered in a new era of connectivity and convenience, it has also exposed organizations to a myriad of vulnerabilities. Cyberattacks, data breaches, and security incidents have become all too common, leaving no room for complacency.
The need for proactive cybersecurity measures has never been greater. It’s in this context that vulnerability assessments play a vital role in safeguarding organizations against malicious threat actors. This guide to vulnerability assessments will explain what they entail, why they are crucial, the various types of assessments, and how they fit into modern security architecture.
What is a vulnerability assessment?
A vulnerability assessment is the process of identifying, quantifying, and prioritizing any vulnerabilities within a network, system, or application. These vulnerabilities, if left unaddressed, could potentially be exploited by attackers to compromise the confidentiality, integrity, or availability of applications, data, and supporting systems.
A vulnerability assessment is an important part of the vulnerability management process , and it’s also a security health check for an organization’s digital assets. It involves the evaluation of technology components, including software, hardware, configurations, and even human factors that may pose security risks. By conducting such assessment activities, organizations gain valuable insights into their security posture and can take proactive measures to mitigate any vulnerabilities identified.
Differences from other cybersecurity evaluations
To put vulnerability assessments in context, it is helpful to differentiate them from other cybersecurity evaluations to understand their specific role and focus:
- Vulnerability assessment vs. penetration testing (pen testing): While both vulnerability assessments and penetration testing aim to identify weaknesses in an organization’s security measures, they differ in scope and approach. Vulnerability assessments focus on discovering vulnerabilities, while penetration testing goes further by attempting to exploit those vulnerabilities to assess their real-world impact.
- Vulnerability assessment vs. risk assessment: Vulnerability assessments are a subset of risk assessments. A risk assessment evaluates an organization’s overall security posture, considering threats, vulnerabilities, and potential impacts to quantify resultant risks. Vulnerability assessments specifically concentrate on identifying and mitigating vulnerabilities.
- Vulnerability assessment vs. security audits: Security audits are compliance-driven and verify whether an organization complies with established security policies and standards. Vulnerability assessments, on the other hand, are proactive measures aimed at identifying potential vulnerabilities, whether or not they violate specific compliance requirements.
The importance of vulnerability assessments
Vulnerability assessments serve as a crucial defense mechanism in this ongoing battle against evolving cybersecurity threats and are an integral part of an organization’s broader cybersecurity strategy.
The primary goal of vulnerability assessments is to safeguard IT systems, networks, data, and applications from potential threats. They provide critical data and insights that inform decision-making processes. With a clear understanding of vulnerabilities, organizations can allocate resources more effectively, implement security controls, and prioritize remediation efforts.
The consequences of undetected vulnerabilities can be severe. Data breaches can lead to financial losses, damage to an organization’s reputation, legal repercussions, and the loss of customer trust. By identifying and addressing vulnerabilities proactively, organizations can significantly reduce the risk of these negative outcomes.
Types of vulnerability assessments
There are several types of vulnerability assessment, each focusing on specific aspects of cyber security. Some of the better-known examples are:
Network-based assessments
Network-based vulnerability assessments concentrate on identifying vulnerabilities within an organization’s network infrastructure. This includes routers, switches, firewalls, and other network nodes and devices. By examining network configurations and traffic patterns, assessors can pinpoint weaknesses that could be exploited by attackers.
Host-based assessments
Host-based assessments concentrate on individual devices or systems within an organization’s network. This includes servers, workstations, and mobile devices. Assessors analyze the operating system, installed software, and configurations to detect vulnerabilities that may be specific to a particular host.
Application assessments
Application assessments evaluate the security of software applications used within an organization. This includes web applications, mobile apps, and desktop software. Assessors examine the application’s code, functionality, and configurations to identify vulnerabilities such as SQL injection, cross-site scripting (XSS) , and insecure authentication mechanisms.
Database assessments
Database assessments focus on the security of an organization’s databases, which often contain sensitive information. Assessors scrutinize database configurations, access controls, and data encryption practices to identify vulnerabilities that could lead to data breaches or unauthorized access.
Wireless network assessments
Wireless network assessments target an organization’s wireless infrastructure, including Wi-Fi networks and access points. Assessors examine wireless security protocols, encryption practices, and access controls to uncover vulnerabilities that could be exploited by unauthorized users or attackers.
Vulnerability Assessment and Penetration Testing (VAPT)
Vulnerability Assessment and Penetration Testing (VAPT) is a comprehensive security assessment approach that combines vulnerability assessments with penetration testing. While vulnerability assessments emphasize the identification of weaknesses, penetration testing takes the assessment process a stage further. By attempting to exploit identified vulnerabilities to establish whether a vulnerability represents a threat in the context of the tested platform, a penetration test will determine the real-world impact.
VAPT provides organizations with a holistic view of their security posture. It not only identifies vulnerabilities but also assesses the effectiveness of security controls, incident response procedures, and security awareness among employees.
Synergies and differences
The synergy between vulnerability assessments and penetration testing is evident in their shared goal of enhancing security. However, they differ in several key aspects:
- Scope: Vulnerability assessments have a broader scope, aiming to identify vulnerabilities across various components. Penetration testing has a narrower focus on exploiting vulnerabilities to assess their impact.
- Approach: Vulnerability assessments use automated scanning tools and manual inspections to identify vulnerabilities. Penetration testing involves ethical hackers actively attempting to exploit vulnerabilities through simulated attacks.
- Reporting: Vulnerability assessments provide a list of identified vulnerabilities, their severity, and recommendations for remediation. Penetration testing reports include details on successful exploits, their impact, and insights into an organization’s ability to detect and respond to those attacks.
Vulnerability assessment process
The vulnerability assessment process typically consists of several stages, each serving a specific purpose:
- Preparation: Define the assessment scope, as well as objectives and limitations. Assemble the assessment team and develop a comprehensive plan.
- Asset identification: Identify all assets, including systems, networks, applications, and data, that will be included in the assessment.
- Vulnerability scanning: Use automated scanning tools to discover vulnerabilities within the identified assets. This phase involves both network-based and host-based scanning.
- Vulnerability analysis: Assess, categorize, and prioritize the vulnerabilities based on potential impact and severity.
- Reporting: Compile a detailed report that includes a list of identified vulnerabilities, severity levels, and recommendations for remediation.
- Remediation: Develop and implement a plan that addresses and mitigates identified vulnerabilities. The plan may involve applying security patches, adjusting configurations, or improving security controls.
- Validation: Verify that remediation efforts have been successful by retesting previously identified vulnerabilities.
Tools and techniques
During the vulnerability assessment process, assessors leverage various tools and techniques to uncover vulnerabilities:
- Automated scanning tools: These tools scan networks, systems, and applications to identify known vulnerabilities. Examples include Nessus, OpenVAS, and Qualys.
- Manual testing: Assessors manually verify vulnerabilities, conducting tests that automated tools may miss, and validate findings.
- Credential and authentication testing: This involves assessing vulnerabilities that require user authentication, such as weak passwords or insecure authentication methods.
- Risk assessment: Assessors evaluate vulnerabilities based on their potential impact and likelihood of exploitation to prioritize remediation efforts effectively.
How to perform penetration testing
Penetration testing , often referred to as pen testing or ethical hacking, is a proactive and authorized attempt to exploit vulnerabilities in an organization’s systems, networks, or applications. The primary objectives of penetration testing include:
- Identifying vulnerabilities that may not be discovered through automated scans or vulnerability assessments.
- Evaluating the effectiveness of security controls and incident response procedures.
- Simulating real-world cyberattacks to assess an organization’s security posture.
Preparing for penetration testing
When preparing for a pen test, defining the scope is crucial. This includes specifying the systems, networks, and applications to be tested, as well as any restrictions or limitations and the person authorizing the test. A well-defined scope ensures that the test aligns with organizational objectives and avoids unnecessary disruption.
Penetration testing involves activities that may trigger security alerts, including intrusion detection systems (IDS) or intrusion prevention systems (IPS). It is essential to obtain written permission from the organization’s management and IT team to conduct the test to prevent false alarms or unnecessary responses.
Stages of penetration testing
Penetration testing typically follows a structured approach, encompassing several stages:
- Planning: Define the scope, objectives, and methodology of the test. Create a detailed test plan, including timelines and resource requirements.
- Discovery: Gather information about the target systems, networks, and applications. This phase may include passive reconnaissance, scanning, and enumeration to identify potential entry points.
- Attacking: Actively exploit vulnerabilities to gain unauthorized access or control over systems. This phase involves attempting various attack techniques, such as SQL injection, cross-site scripting (XSS), or privilege escalation.
- Reporting: Document the findings, including successful exploits, vulnerabilities, and their potential impact. Provide detailed recommendations for remediation and improving security controls.
Tools and methodologies
Penetration testers employ an array of tools and methodologies to simulate attacks and assess security defenses. Some commonly used tools and techniques include:
- Metasploit: An exploitation framework that offers a wide range of tools for testing, exploiting, and validating vulnerabilities.
- Nmap : A versatile network scanning tool used for host discovery, port scanning, and service enumeration.
- Burp Suite: A web application testing tool that helps identify and exploit vulnerabilities in web applications.
- Kali Linux: A Linux distribution designed for penetration testing and ethical hacking, containing numerous pre-installed tools.
- Social engineering: Testers may use social engineering techniques to assess an organization’s vulnerability to phishing attacks, impersonation, or manipulation of employees.
Understanding and addressing findings: Remediation strategies and retesting
The true value of a penetration test lies not only in identifying vulnerabilities but also in guiding organizations toward effective remediation. After receiving the penetration test report, organizations should follow these steps to address the findings:
- Prioritize remediation: Review the findings and prioritize identified vulnerabilities based on their severity, potential impact, and exploitability. Focus on addressing critical vulnerabilities that pose the most significant risks to the organization first.
- Develop remediation plans: Create vulnerability remediation plans for each identified vulnerability, outlining specific steps and timelines for mitigation. Assign responsibilities to individuals or teams within the organization to ensure accountability.
- Implement security patches and configurations: Apply security patches and updates to systems and software to address known vulnerabilities. Adjust system configurations to align with security best practices and recommendations.
- Enhance security controls: Strengthen security controls, including firewalls , intrusion detection systems, and access controls, to mitigate vulnerabilities and prevent future attacks.
- Employee training and awareness: Conduct security training and awareness programs for employees to reduce the likelihood of falling victim to social engineering attacks.
- Incident response: Review and enhance incident response procedures to ensure swift and effective responses to security incidents.
- Retesting: After addressing any vulnerabilities identified, conduct follow-up testing to verify that remediation efforts were successful. Retesting provides assurance that vulnerabilities have been properly mitigated and that the organization’s security posture has improved.
Enhance security posture with vulnerability assessments
Vulnerability assessments and penetration testing play pivotal roles in safeguarding organizations against cyber threats. They provide a systematic approach to identifying, analyzing, and prioritizing vulnerabilities within IT systems, while penetration testing takes the assessment process further by simulating cyberattacks to evaluate an organization’s security defenses.
The importance of these assessments cannot be overstated, given the high stakes involved. Data breaches, financial losses, reputation damage, and legal consequences await organizations that fail to address vulnerabilities proactively. By systematically identifying and addressing weaknesses, organizations can enhance their security posture, protect critical assets, and maintain the trust of their customers and stakeholders.
As organizations continue to embrace digital transformation and the adoption of new technologies, there is a growing need for robust cybersecurity measures. Effectively mitigate patch and configuration vulnerabilities at scale with NinjaOne’s unified IT management platform , which provides endpoint monitoring, real-time alerting, and automated prioritization.
- Category: Security , IT Ops
You might also like

What Is a Winmail.dat file and Is It Safe?

Tackling High Chrome RAM Usage: Tips and Tricks to Improve Performance

What to Do When Windows 10 Desktop Icons Are Missing

How to Upgrade RAM on Your Laptop or PC

What Is Windows Registry? Your Complete Guide
How to Change File Associations in Windows 10
Ready to become an it ninja.
Learn how NinjaOne can help you simplify IT operations.
NinjaOne Terms & Conditions
By clicking the “I Accept” button below, you indicate your acceptance of the following legal terms as well as our Terms of Use :
- Ownership Rights : NinjaOne owns and will continue to own all right, title, and interest in and to the script (including the copyright). NinjaOne is giving you a limited license to use the script in accordance with these legal terms.
- Use Limitation : You may only use the script for your legitimate personal or internal business purposes, and you may not share the script with another party.
- Republication Prohibition : Under no circumstances are you permitted to re-publish the script in any script library belonging to or under the control of any other software provider.
- Warranty Disclaimer : The script is provided “as is” and “as available”, without warranty of any kind. NinjaOne makes no promise or guarantee that the script will be free from defects or that it will meet your specific needs or expectations.
- Assumption of Risk : Your use of the script is at your own risk. You acknowledge that there are certain inherent risks in using the script, and you understand and assume each of those risks.
- Waiver and Release : You will not hold NinjaOne responsible for any adverse or unintended consequences resulting from your use of the script, and you waive any legal or equitable rights or remedies you may have against NinjaOne relating to your use of the script.
- EULA : If you are a NinjaOne customer, your use of the script is subject to the End User License Agreement applicable to you (EULA).
- Standards & Protocols
- Data Center
- Unified Communications

Enterprise Networking Planet content and product recommendations are editorially independent. We may make money when you click on links to our partners. Learn More .
Network vulnerability assessment (NVA) is a process that identifies and assesses security flaws in a network’s publicly accessible devices. It also provides mitigation strategies to address these vulnerabilities and reduce the risk of security breaches.
A vulnerability assessment is important because it enables you to discover and fix security vulnerabilities before attackers can exploit them. It can protect your organization from data theft, system disruptions, and other security incidents.
Security professionals conduct regular vulnerability assessments because new vulnerabilities occur constantly. These assessments provide valuable information for developing plans to mitigate identified risks.
Table of Contents
What do network vulnerability assessments look for?
Network vulnerability assessments look for potential threats and weaknesses across applications and IT infrastructure to strengthen network security . These specialized tools probe unpatched software and operating systems, open ports and services, unsecured wireless networks, misconfigurations in web or network applications, network architecture weak points, security policy compliance, mobile device vulnerabilities, access control and permissions, physical security issues, exposed (Internet of Things) IoT devices, weak passwords, and application-level vulnerabilities:
- Unpatched software and operating systems: Unpatched software and operating systems are a major cause of network vulnerabilities. Hackers can use these vulnerabilities to access sensitive data or launch attacks.
- Open ports and services: Attackers can bypass security controls through open ports and gain access to network systems. Detecting open ports and services pinpoint potential entry points for attackers.
- Unsecured wireless networks: Unprotected wireless networks represent a prevalent vulnerability malicious actors can leverage to gain unauthorized access to sensitive information or initiate attacks.
- Misconfigurations in network or web applications: Network or web application setup errors can cause vulnerabilities that attackers can take advantage of. Misconfigurations like incorrectly installed firewalls and insecure SSL/TLS settings are some examples.
- Network architecture weaknesses: Overall network design evaluation is crucial to find potential weaknesses, such as single points of failure or inadequate segmentation that could allow attackers to move laterally.
- Security policy compliance: Deviations from the security policies may expose your organization to breaches, data loss, and legal liabilities. Vulnerability assessments minimize these risks by checking security policy compliance.
- Access control and permissions: Monitoring user and system access controls ensure that only authorized individuals or systems can access sensitive resources.
- Physical security issues: Inspecting the physical security of network equipment can help to prevent unauthorized access or tampering, which could compromise the integrity of the network.
- Vulnerable mobile devices: Comprehensive network vulnerability assessment evaluates mobile devices for possible vulnerabilities — insecure configurations, outdated operating systems, malicious apps , and user behavior.
- Exposed IoT devices: Unsecured IoT devices can pose a significant risk to your organization’s security and privacy. They may be vulnerable to a variety of cyberattacks , such as denial of service, malware , passive wiretapping, SQL injection (SQLi), wardriving, zero-day exploits, and ransomware .
- Weak passwords: Weak passwords are another major cause of network vulnerabilities. Hackers can use brute force attacks to guess weak passwords and gain access to sensitive data.
- Application-level vulnerabilities: Application-level vulnerabilities can allow attackers to access, modify, or destroy sensitive data, execute malicious code, bypass authentication or authorization mechanisms, or cause denial of service. Some examples of typical application-level vulnerabilities include SQLi, cross-site scripting, and buffer overflow attacks.
11 types of vulnerability assessments
There are many different types of vulnerability assessments that you can conduct to discover and evaluate the security risks and weaknesses in your systems, networks, and applications. Below is a comparison showing various vulnerability assessment types and their key differences:
Numerous vulnerability assessment solutions in the market can perform these vulnerability assessments effectively.
Vulnerability assessment platforms
There are two major categories of vulnerability assessment platforms: multi-faceted and focused.
- Multi-faceted platforms can perform several types of assessments like network-based, host-based, wireless, database, and application assessments.
- Focused platforms , on the other hand, only perform one assessment type but provide specialized features that allow you to assess vulnerabilities reliably.
6 key steps to running vulnerability assessments
There are six essential steps in the vulnerability assessment process: planning and designing, asset discovery, configuration, network scanning, result analysis, vulnerability prioritization, and report generation.
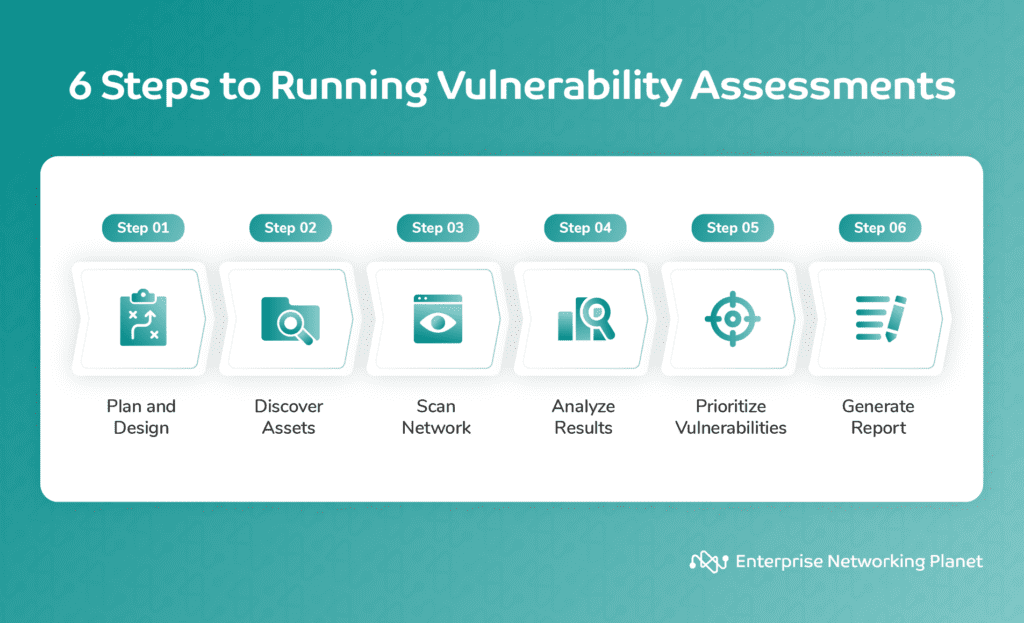
1. Planning and designing
To begin a network vulnerability assessment, you must first determine the scope and exact components for assessment. This includes hardware, user devices, applications, and network infrastructure.
After establishing the scope, identify assets and set baselines for their individual security capabilities, risk tolerance, user permissions, configuration, and other factors.
Finally, set up the test environment, gather any necessary tools and resources, and complete any further planning and preparation.
2. Asset discovery
The next step is deciding what you want to scan. This can include Bring Your Own Device (BYOD) mobile devices or IoT devices. Then, specify the network components for the assessment, such as devices, applications, hardware, and network infrastructure. You must identify these assets and set baselines for their security capabilities, risk tolerance, user permissions, configuration, and other factors.
3. Network scanning
Network scanning involves checking your network for security vulnerabilities. You can use a vulnerability scanner to spot potential security risks in your network.

4. Result analysis
After scanning, you’ll have to analyze any flagged concerns to pinpoint possible vulnerabilities.
5. Vulnerability prioritization
Then you can assess and score the newly-discovered vulnerabilities based on their associated risk.
6. Report generation
Finally, create a comprehensive report detailing the findings from the assessment. The report should also include information on actions taken and recommendations for future assessments.
Network vulnerability checklist
A network vulnerability checklist is a must-have for conducting a network vulnerability assessment. It lets you plan and organize your assessment activities, ensuring completeness and accuracy. The checklist also enables you to follow best practices and standards of network security, boosting your assessment efficiency.
Keep in mind that there is no one-size-fits-all answer to what should exactly be on a network vulnerability checklist, as different organizations have varied network security needs and goals.
Some common items that the checklist typically includes are asset identification, scope definition, scan configuration, scan execution, result analysis, risk evaluation, remediation plan, implementation of fixes, network vulnerability assessment process update, and repetitive testing.
1. Asset identification
To identify assets, you need to discover and document network assets, including devices, systems, applications, and data. This involves enumerating all network components, devices, systems, and software, by making a list of everything that makes up your network.
2. Scope definition
Determine the network extent that you will evaluate by specifying the systems and components, such as servers, routers, firewalls, and switches for evaluation. You also need to set the parameters and constraints like the time frame, budget, and resources.
3. Scan setup
Prepare for scanning activities by configuring your vulnerability scanning tool with the target IP addresses. Select appropriate tools and methods for the network. Additionally, document the plan and seek approval from stakeholders as part of the setup process.
4. Scan execution
Initiate the vulnerability scan on the defined targets to detect known threats and vulnerabilities within the network. Run scans using selected tools and methods, and evaluate the functionality and performance of network security controls such as antivirus, firewall, email filters, and DDoS protection.
5. Scan result analysis
Evaluate the scan results and explain the findings using facts and evidence to support your conclusions. You must also validate the results, removing any false positives or negatives that might skew your analysis.
6. Risk evaluation
You need to rank vulnerabilities based on how severe, impactful, and exploitable they are. You can use this information to create and execute a mitigation plan, as well as to revise and refine the network vulnerability assessment process.
7. Plan for remediation
You must create a mitigation plan to address the identified vulnerabilities. Document the remediation actions for each vulnerability, such as patching, updating, configuring, or replacing the affected systems or components. You must also obtain approval from the stakeholders for the mitigation plan.
8. Execute the mitigation plan
Execute the remediation actions outlined in the plan, including applying patches, updates, or other fixes. Monitor and test the effectiveness of these actions, ensuring they don’t introduce new vulnerabilities or issues. The goal of these fixes is to resolve or reduce vulnerabilities and enhance network security.
9. Review and update the assessment process
After conducting the assessment, document the outcomes and lessons learned. Additionally, update and adjust the network vulnerability assessment process using feedback and best practices. Thoroughly document the network vulnerability assessment process, covering all activities from start to finish, along with the discovered threats and the methods for mitigating them. This documentation is of utmost importance.
10. Repetitive testing
It is vital to constantly review and analyze systems to discover new threats and attacks and take all possible steps to mitigate them.
How much does a network vulnerability assessment cost?
The cost of a network vulnerability assessment can vary drastically depending on the tools used, the size and skill of your IT department, and the size and complexity of your network. According to some sources , the average cost of a network vulnerability assessment is between $4,000 and $5,000.
It’s worth noting that there are many open-source vulnerability assessment tools available today. These tools are typically free to use, which means you could potentially conduct a vulnerability assessment at little to no cost.
Keep in mind that while the tool itself may be free, proficiently using it often requires a certain level of expertise. Therefore, there may still be costs associated with training or hiring a professional to use these tools optimally.
Factors affecting network vulnerability assessment cost
The actual network vulnerability assessment cost can vary depending on several factors, like your network’s scope and complexity, your organization’s size and scale, the type of vulnerability scanning tools, your report’s comprehensiveness, support quality for remediation, and assessment frequency.
- Network scope and complexity: Assessing a larger and more complex network or system can significantly increase the cost due to the additional time and resources required.
- Organization size and scale: The size and scale of your organization can also affect the cost. Assessing a larger organization’s network components may take longer and require more resources than that of a smaller organization.
- Type of vulnerability scanning tool: Your choice of vulnerability scanning tool can also influence the cost, as some tools might be pricier but offer more thorough and precise assessments.
- Comprehensiveness of assessment report: The level of detail and complexity in the assessment report can also raise the cost since generating and analyzing more detailed reports may demand additional time.
- Quality of remediation support: The extent of support offered for remediation, which involves fixing identified vulnerabilities, can also impact the cost. Extensive remediation support from a vendor could raise the overall cost.
- Assessment frequency: The frequency of assessments can affect the cost. Conducting assessments regularly or frequently may result in higher overall costs, but it can potentially lead to long-term savings by detecting and addressing vulnerabilities before they become exploitable.
Benefits of network vulnerability assessment for your organization
Carrying out regular network vulnerability assessments can bring many benefits to your organization, such as risk mitigation, cost savings, better patch management, optimized resource allocation, and continuous improvement.
Risk mitigation
Your organization can proactively manage and mitigate risks by uncovering vulnerabilities, effectively reducing the likelihood and impact of cyberattacks. This approach allows you to address potential security threats before hackers or bad insiders can manipulate them, thereby stopping cyberattacks before they occur.
Cost savings
You can save your organization significant financial resources and avoid spending on incident response, recovery, and legal costs by preventing data breaches, downtime, and other cyber incidents through vulnerability assessments.
Better patch management
Regular vulnerability assessments can aid organizations in promptly addressing known vulnerabilities by finding outdated software and configurations that require patching or updating. As a result, your organization can maintain a more secure environment by addressing known vulnerabilities promptly.
Optimized resource allocation
You can decide where to best allocate your security resources by conducting vulnerability assessments. This ensures that time and budget are spent on areas of greatest need, increasing the efficiency of security efforts.
Continuous improvement
Network vulnerability assessments are ongoing processes, not one-time activities. Regular assessments promote a culture of continuous improvement in cybersecurity, allowing organizations to adapt to evolving threats and technologies.
Vulnerability assessment vs. penetration testing
Some people use the terms penetration testing (or pentesting) and vulnerability assessment interchangeably, but there are critical differences between the two approaches.
Pentesting is a security practice where ethical hackers simulate real-world attacks to find vulnerabilities in computer systems, networks, and applications. The goal is to assess security controls and discover potential entry points for malicious actors.
Vulnerability assessment is a list-based, automated, and high-level process that scans the system for potential vulnerabilities and reports them without attempting to exploit them.
Here are the key distinctions between pentesting and vulnerability assessment:
Bottom line: Network vulnerability assessment provides a proactive approach to network security
Network vulnerability assessments are a critical part of a comprehensive vulnerability management strategy and any organization’s security posture. By identifying and addressing vulnerabilities, you can protect your organization from a wide range of attacks. There are a number of different ways to conduct a network vulnerability assessment, and the best approach will vary depending on the specific needs of your organization.
Assessing networks for vulnerabilities and taking steps to address them enables you to stay one step ahead of the attackers and helps you to fix any security issues before they become serious problems. Ultimately, network vulnerability assessments empower you to elevate your network’s performance and reliability.
Boost your vulnerability assessment practices and fortify your network security using one of the top vulnerability management tools .
Related Articles
8 best firewalls for small & medium business (smb) networks, mobile network security: how to secure mobile networks, 8 best mobile vpns for every use case in 2024, get the free newsletter.
Subscribe to Daily Tech Insider for top news, trends, and analysis.
Latest Articles
Top 9 enterprise wi-fi solutions for businesses in 2024, 9 best network switches for 2024: speed and features compared, top 10 mobile security threats for devices, networks, and apps — and how to prevent them, what is a router in networking core function explained, follow us on social media, explore more.

Whitepapers
- News & Updates
- Feature Reviews
- On-demand Webinars
Cyber Leaders
- US Privacy Laws Tracker
- Global Privacy Laws Tracker

- Secure Africa
How to Conduct a Vulnerability Assessment

Michelle Ofir Geveye
- January 4, 2024
- Yair Solow Featured on Bugy's Founder Interviews
- Centraleyes Chosen as Global Top 5 Startups of the Year - Interview
- Centraleyes on Cyber Ghost: Interview with Yair Solow
- Spotlight Q&A with Centraleyes at Safety Detectives
- Centraleyes Expands Automated Risk Register To Cover All Enterprise Risk
- New Centraleyes 4th Generation Release Officially Goes Live
- Yair Solow Featured on VPN Mentor
- Yair Solow on CNN
- CyGov Signs a Strategic Agreement with R3 (Spanish)
- Centraleyes Welcomes Co-Founder of Optiv, Dan Burns, to Its Board of Directors
- Centraleyes Continues to Expand Its Global Network of Strategic Partners with UK-based ITC Secure
- Centraleyes Introduces First Automated Risk Register
- Yair Solow Featured on Website Planet
- Trevor Failor named head of sales at CyGov
- CyGov is rebranding its platform as Centraleyes
- Cybersecurity Company Cygov Partners With Risk Management Company Foresight
- CyGov agrees strategic partnership with top 200 MSSP Cybriant
- Cyber Resilience Resource for Businesses Re-Deploying Remotely
- The Four New Pillars of Corporate Protection Yair Solow on InfoSecurity Magazine
- CyGov selected by SixThirty as Top Cyber Security Startup
- Europe's Top Cyber Security Startups
- CyGov Interviewed by MediaSet
- Eli Ben Meir's article in Security Intelligence
- Yair Solow on i24 News
- CyGov Selected by WorldBank
- Eli Ben Meir OpEd in the Houston Chronicle
- Yair Solow and Eli Ben Meir Present at the SparkLabs Demoday 8
- Financial Institutions
- Life Science
Platform Feature Reviews
- Enhance Your Cyber Maturity With ITSM Integration and Automated Remediation
- Ensure Your Ongoing Compliance With Automatic Framework Reassessment Tasks
- Stay in the Know With a Full Activity Log of Your Assessment Collection
- Add a New Entity to Perform Your Assessment in 10 Seconds
- Quantify Financial Risk With Centraleyes Platform Primary Loss Calculator
- Cover Your Entire Environment With Centraleyes's Risk Application Assessments
- Communicate Cyber Risk With Your Executives in an Intuitive, Beautifully Visualized Board Reporting
- Stay on Top of Your Vendors' Cyber History With In-Depth External Scans
- Automate the Creation and Maintenance of a Risk Register, Saving Hours on Manual Work
- Add a New Framework and Distribute Assessments in Your Organization
- View Your Organization's Risk Scoring Through the NIST Tiering Lens
- Most Intuitive Way for Compliance With the Framework Navigation Tool
- Always Prepared for the Next Task With Automated Remediation
- Effective Team Work With Drag-and-Drop Control Assignment
- Get Real-Time Critical Alerts That are Specifically Relevant to You
- MSSPs Can Manage Multiple Clients Under One Platform
- Onboard a New Vendor in Just 30 Seconds
- Turn Hours of Work Into Seconds with Centraleyes Vendor Risk Profile
- Always Informed with Centraleyes Domain Benchmarking
News & Updates
- What was Behind the Change Healthcare Breach that Shook the Healthcare Industry?
- Cisco Raises Concerns Over Surge in Brute-Force Attacks Targeting VPN and Web Services
- Bipartisan Proposal Sparks Hope for American Privacy Rights Act
- Microsoft Responsible for Made-in-China Hack that Targeted US Officials
- AI Gets an Endorsement from Coalition
- NIST NVD "Under Construction"
- TutaCrypt to Thwart 'Harvest Now, Decrypt Later' Attacks
- 9.8/10 Severity Flaw in Team City- Patch Now!
- Blackcat Claims Responsibility for the UnitedHealth Change Breach
- US Gov's Cyber Survival Guide for Water Utilities
- Safeguarding Elections Amidst the Deepfake Deluge
- Faking the Figures (and the Faces): Deepfake Financial Frauds
- Trello Got a Scrape
- Advisory Issued for Androxgh0st Malware
- X Marks the Spot: Mandiant and SEC's Security Sway on Twitter
- Quantum Quandary: Navigating the Path to Unbreakable Encryption
- Chameleon Android Banking Trojan Morphs with Advanced Tactics, Expands Targets
- Ubiquiti Resolves User Access Bug
- The U.S. Needs a Better AI Plan
- Navigating the Cyber Currents: Ensuring a Watertight Critical Infrastructure
- Dollar Tree Breach: Supplier Roots Sprout Risks
- Applying Digital Pressure to Stop the “Citrix Bleed”
- 30-Year-Old Medical Protocol Making Headlines
- 88 Million Americans Affected in 2023 By Healthcare Data Breaches
- Critical Atlassian Flaw Has a Simple Fix
- D.C. Voter Data Leak: What We Know So Far
- Centraleyes Leads the Way with Full PCI DSS 4.0 Compliance Support on its Innovative Platform
- Will the Real Admin Please Step Up?
- Straightening Out the curl Vulnerability
- Vague in the Hague: Who Is Behind the ICC Data Breach?
- Forever 21 Discloses Data Breach Impacting Over Half a Million
- FBI on a Wild Duck Hunt after Qakbot
- The Enemy Within: Tesla’s Data Breach Was an “Inside Job”
- NIST CSF is Getting a Makeover
- Russia Prime Suspect for UK Electoral Commission Cyber Attack
- Storm-0558 Isn’t Over Yet
- Google-Owned VirusTotal Data Leak: Result of Human Error
- Made-In-China Hack Infiltrates the US Government
- EU-U.S. Data Privacy Framework: Is Adequate Good Enough?
- Anonymous Sudan Or Anonymous Russia?
- How to Build a Successful GRC Program to Help Reduce Your Risk Posture
- How to Stay Secure and Compliant in a World of Regulatory turmoil
- Don’t Keep Your Head in the Clouds – How to Protect Yourself from Virtual Risk
- Flash Webinar: How to Know When it's Time to Build a Risk Management Program
- Enhancing Cyber Risk Management Through the Power of Automation - Boutique Webinar
- Flash Webinar: From Technical to Business Risk - How to Communicate With Your Board
- Flash Webinar: What You Can Learn From the SolarWinds Attack to Lower Your Chances of Being Breached
- Flash Webinar: Supply Chain, 3rd-Party Vendors and the Silent Assassin Among Them
- Flash Webinar: Cyber Risk Management - it Doesn't Have to Be So Painful
Navigating AI Regulations in the Insurance Sector: A Comprehensive Guide
Manual vs automated risk management: what you need to know, fisma vs. fedramp in government cybersecurity.
- The Ultimate Guide to Excelling in Your External Audit: 5 Proven Strategies
- Digital Risk Types Demystified: A Strategic Insight into Online Threats
- FISMA Compliance: A Complete Guide to Navigating Low, Moderate, and High Levels
- Understanding the Different Types of Audit Evidence
- Data Loss Prevention: Best Practices for Secure Data Management
- What is Maryland’s Online Data Privacy Protection Act?
- Enhancing Security and Reducing Costs with Advanced Zero Trust Implementation
- Navigating Legal Challenges of Generative AI for the Board: A Strategic Guide
- Exploring the Cost of a Data Breach and Its Implications
- Best 5 Privacy Management Tools for 2024
- Introduction to ISO 42001 and Its Impact on AI Development
- The Best SIEM Tools To Consider in 2024
- The 11 Best GRC Tools for 2024
- 8 Best Compliance Automation Tools: How to Choose
- The Best 10 Vendor Risk Management Tools
- Best 8 Vulnerability Management Tools for 2024
- Protecting Patient Data Post-Change Healthcare Breach
- Ensuring Business Resilience: Integrating Incident Response and Disaster Recovery Plans
- Understanding the Key Updates in NIST Cybersecurity Framework 2.0
- What's in the NIST Privacy Framework 1.1?
- The 5 C’s of Audit Reporting
- Cloud Compliance Frameworks: Ensuring Data Security and Regulatory Adherence in the Digital Age
- Generative AI Governance: Balancing Innovation and Ethical Responsibility
- Overview of AI Regulations and Regulatory Proposals of 2023
- Risk and Regulation: A Strategic Guide to Compliance Risk Assessment
- Understanding the ISO 27001 Statement of Applicability in Cybersecurity
- 5 Benefits of Identity and Access Management
- Unveiling the Threat Landscape: Exploring the Security Risks of Cloud Computing
- Future of Compliance: 2024's Essential Cybersecurity Insights
- What Do You Do if You Have a Third-Party Data Breach
- 7 Steps to Measure ERM Performance
- The EU AI Act: What It Means for Your Compliance
- How Do You Quantify Risk? Best Techniques
- How to Prepare for Compliance With the SEC Cybersecurity Rules Update
- Protecting Endpoints in an Evolving Threat Landscape
- The Goals of Security Compliance
- Data Privacy in the United States: A Recap of 2023 Developments
- Cyber Leaders of the World: Chris Lockery, CISO at Help at Home
- Cyber Leaders of the World: Michael Anderson, CISO at the Dallas Independent School District
- Cyber Leaders of the World: Timothy Spear, Co-Founder and CTO of Whonome
- Cyber Leaders of the World: Marc Johnson, CISO at Impact Advisors
- Cyber Leaders of the World: Craig Williams, CISO at Secure Data Technologies
- Cyber Leaders of the World: Bill Genovese, CIO Advisory Partner at Kyndryl
- Cyber Leaders of the World: Dr. Brian Callahan, Graduate Program Director & Lecturer at ITWS@RPI, and CISO at PECE
- Cyber Leaders of the World: Chris Grundemann, Research Category Lead for Security and Risk at GigaOm
- Cyber Leaders of the World: Barak Blima, CISO at CHEQ
- Cyber Leaders of the World: Tony Velleca, CEO at CyberProof and CISO at UST
- Cyber Leaders of the World: Rob Black, CEO and Founder of Fractional CISO
- Cyber Leaders of the World: Zachary Lewis, CISO at the University of Health Sciences and Pharmacy in St. Louis
- Cyber Leaders of the World: Dan Wilkins, CISO at the State of Arizona
- Cyber Leaders of the World: Sagar Narasimha, CISO at Amagi
- Cyber Leaders of the World: Seema Sharma, Global Head of Information Security & Data Privacy at Servify
- Cyber Leaders of the World: Shay Siksik, VP of Customer Experience at XM Cyber
- Cyber Leaders of the World: Raz Karmi, CISO at SimilarWeb
- AI Auditing
- Data Exfiltration
- Data Sovereignty
- Control Objectives for Information and Related Technologies (COBIT)
- Audit Management Software
- Vendor Framework
- AI Governance
- AI Transparency
- Internal Penetration Testing
- Cybersecurity Automation
- GDPR Compliance Risk Assessment
- Audit Fatigue
- Compliance Operations
- Risk Management Automation
- Corporate Sustainability Reporting Directive
- Man-in-the-Middle Attack
- Digital Rights Management
- Content Disarm and Reconstruction
- Calculated Risk
- Data Residency
- Asset Risk Management
- Identity Security
- Risk Modeling
- CISO Board Report
- Risk Communication
- SOC 2 Bridge Letter
- Audit Documentation
- Enterprise Risk Management (ERM)
- Compliance Gap Analysis
- Security Misconfiguration
- Security Program Management
- Digital Risk Protection
- Advanced Persistent Threat
- Continuous Auditing
- Risk Control
- ISMS Awareness Training
- Risk Management Policy
- Risk Avoidance
- Resilience Management
- What are the main steps in the threat modeling process?
- What exactly is considered PHI according to HIPAA?
- What does the PCI Compliance Auditor Look At?
- How to Detect and Prevent Data Leakage?
- What are the Challenges Associated with Cloud Security Management?
- How Many Techniques Are There in MITRE Att&ck?
- What Are the Benefits of Conducting a Risk Assessment?
- What are the categories of controls in ISO 27001?
- How Does ABAC Differ From Other Access Control Models?
- What Does a Compliance Management System Look Like?
- What Are the NIST CSF Implementation Tiers?
- What is the Purpose of Compliance Attestation?
- How do I become NIST 800-171 compliant?
- Why are the three rules of HIPAA necessary?
- What are the seven categories of risk?
- What are the Six Types of Vulnerability Scanning?
- Which are the most important compliance frameworks?
- How do you implement GRC automation?
- How Can I Measure the ROI of Implementing a Compliance Solution?
- How do you determine whether HIPAA violations need to be reported?
- What are the three major threats to cybersecurity today?
- How Do You Manage Compliance Risk?
- How Does a GRC platform handle data privacy and security?
- How Often Should Supplier Risk Assessments Be Conducted?
- How is a SOC 2 Report Structured?
- What Are the Major Risk Factors in Cyber Security?
- How Do You Read a Risk Matrix Table?
- What is the Risk Rating Matrix Used For?
- What are the Benefits of Risk Assessment Software?
- How does the CMMC differ from NIST?
- What are the penalties for not reporting a HIPAA violation?
- What are the different versions of HECVAT?
- What are the 4 objectives of Enterprise Risk Management?
- Who needs to be ITAR compliant?
- What are the best practices for vendor risk management for CISOs?
- What are the three stages of the zero-trust security model?
- What are the NIST control families?
- Can ChatGPT replace compliance officers?
- How can thread modeling help an organization identify and mitigate potential risks?
- What is the average cost of penetration testing?
- Generative AI Governance
- Security Events
Ignorance can be costly when safeguarding your cloud or hybrid networks. Today’s security teams face the challenge of monitoring the well-being and performance of a diverse array of on-premises and cloud applications, software, IoT devices, and remote networks. To add to the complexity, hackers relentlessly hunt for vulnerabilities on the attack surface to gain entry for malicious purposes.
Regular vulnerability assessments are a cybersecurity best practice and an essential proactive measure to safeguard your organization’s digital assets.

What is a Vulnerability Assessment?
Vulnerability assessments are a systematic process designed to discover, prioritize, and mitigate vulnerabilities within a digital system. This process is an integral component of cybersecurity practices, frequently employed alongside other tools to comprehensively understand an organization’s cyber posture and risks.
What is the Relationship Between Vulnerability Management (VM) and Vulnerability Assessment (VA)?
While vulnerability assessment initiates the vulnerability discovery process, vulnerability management is a continuous, comprehensive strategy that extends beyond the initial evaluation. VM encompasses a broader array of activities, including decision-making regarding risk remediation, mitigation, or acceptance, alongside a focus on overall infrastructure enhancement and robust reporting.
Notably, Gartner outlines a five-step VM cycle that most organizations adopt, with the initial phase being the vulnerability assessment:
- Assess : Here, vulnerability assessments shine by identifying assets, conducting scans, and producing detailed reports.
- Prioritize : The assessment results prioritize risks, considering the vulnerabilities themselves and contextualizing them within the existing threat landscape and potential future developments.
- Act : This phase segregates identified vulnerabilities into three categories—remediate, mitigate, or accept. Remediation involves completely eliminating the threat where possible, while mitigation aims to reduce vulnerability exploitation likelihood. The acceptance category may include devices or software earmarked for replacement, requiring no immediate action.
- Reassess Post-action, the team validates that risks have been properly addressed, necessitating a rescan to confirm risk resolution.
- Improve : The final phase evaluates metrics for accuracy and up-to-dateness, ensuring that risk assessment remains precise. Furthermore, this stage targets eliminating underlying issues contributing to system vulnerabilities.
The Imperative of Regular Vulnerability Scanning and Assessment
Regular vulnerability assessments cannot be overstated. These assessments are your proactive shield against threats that lurk in the shadows.
Consider these two recent statistics from Edgescan :
- 33% of all vulnerabilities across the full stack discovered in 2022 were either High or Critical Severity
- Over 25% of the vulnerabilities exploited in 2022 were reported in 2015 or earlier!
By conducting routine vulnerability assessments, you:
- Stay Ahead of Threats: Regular assessments ensure you’re not caught off guard by vulnerabilities that malicious actors quickly exploit.
- Reduce Response Time: With timely identification of vulnerabilities, your team can swiftly deploy patches, minimizing the exposure window.
- Protect Reputation: Preventing data breaches and disruptions safeguards your organization’s reputation and trustworthiness.
- Mitigate Financial Risks: Addressing vulnerabilities promptly mitigates the financial risks associated with cyberattacks and regulatory fines.
- Ensure Business Continuity: Vulnerability assessments are a cornerstone of a resilient cybersecurity strategy, ensuring uninterrupted business operations.
The Three Primary Objectives of Vulnerability Assessments
A vulnerability assessment typically serves three primary objectives:
- Identification: It identifies vulnerabilities, ranging from critical design flaws to simple misconfigurations.
- Documentation: Vulnerabilities are documented to facilitate developers in identifying and replicating findings.
- Guidance: The assessment generates guidance to assist developers in remediating identified vulnerabilities.
Types of Vulnerability Assessments
Given the multifaceted nature of vulnerabilities, various types of assessments are available, tailored to different aspects of an organization’s infrastructure
Vulnerability testing can take various forms, including:
- Dynamic Application Security Testing (DAST): Involves executing an application, often a web application, to identify security defects in real-time.
- Static Application Security Testing (SAST): Analyze an application’s source or object code to identify vulnerabilities without running the program.
- Network-Based Scans: Identify potential network security attacks and detect vulnerable systems on wired or wireless networks.
- Host-Based Scans: Locate and identify vulnerabilities in servers, workstations, or network hosts, offering greater visibility into configuration settings and patch history.
- Wireless Network Vulnerability Assessment Scans: Focus on potential points of attack in Wi-Fi networks, validating secure configurations.
- Application Scans: Test websites to detect software vulnerabilities and incorrect configurations in network or web applications.
To effectively manage cybersecurity risks, organizations often conduct a combination of these assessments regularly. Given the dynamic nature of both an organization’s architecture and the evolving cyber threat landscape, routine vulnerability assessments are crucial, allowing for adjustments to security practices and policies as needed
How Often Should You Perform a Vulnerability Analysis?
It is an industry-standard practice to advise organizations to conduct regular scans of their internal and external systems, with a recommended frequency of monthly assessments. Compliance standards often dictate the specific requirements for assessment frequency. For example:
- Payment Card Industry (PCI DSS) mandates quarterly assessments.
- Health Information Protection Accountability Act (HIPAA) does not require scanning but emphasizes establishing a detailed assessment process.
- Cyber Security Maturity Model Certification (CMMC) sets assessment frequency from weekly to quarterly, depending on auditor requirements.
- The National Institute of Standards and Technology (NIST) recommends quarterly to monthly assessments based on the governing framework.
Moreover, conducting assessments more frequently increases the likelihood of identifying vulnerabilities promptly. It’s essential to assess when significant changes are introduced to the network. This ensures that no new vulnerabilities have been inadvertently introduced during the change process, providing an updated and comprehensive analysis.
The frequency of vulnerability assessments plays a pivotal role in maintaining a resilient security posture for organizations.
Start Getting Value With Centraleyes for Free
See for yourself how the Centraleyes platform exceeds anything an old GRC system does and eliminates the need for manual processes and spreadsheets to give you immediate value and run a full risk assessment in less than 30 days
Vulnerability Assessment Best Practices
To ensure the effectiveness of a vulnerability assessment, adhering to best practices is essential. The following checklist outlines some points worth noting:
- Define Desirable Business Outcomes: Establish the desired outcomes for each assessment, including prioritizing risks, achieving compliance, preventing data breaches, or reducing recovery time.
- Prioritize Before Assessing: Before initiating assessments, prioritize the most critical assets and components, considering the various types of assessments and their structure.
- Preparation Is Key: Technical preparation involves conducting meetings, constructing threat models, interviewing system developers, and verifying test environments. Understanding when and where to use different vulnerability assessment methodolgy is crucial.
- Review Continuously: During assessments, manually review results to distinguish false positives from true vulnerabilities. Record steps taken and collect evidence for a comprehensive understanding.
- Create Detailed Reports: Comprehensive reporting is vital, including descriptions of vulnerabilities, associated risk levels, mitigation steps, and remedies. These reports serve as valuable resources for future incident prevention and response.
- Invest in Education: Ongoing education and training, alongside retaining assessment results and reports, enable continuous improvement in preventing and responding to incidents. Detailed reports also aid in conveying issues to non-technical stakeholders.
A Step-by-Step Guide On How To Conduct a Vulnerability Assessment
- Preparation and Vulnerability Assessment Planning:
Define Objectives:
- Clearly outline the objectives of your vulnerability assessment. Are you focusing on network, application, or system vulnerabilities? What is your desired outcome?
Assemble Your Team:
- Form a team of cybersecurity experts, including network administrators, system engineers, and penetration testers, to ensure comprehensive coverage.
- Asset Identification:
Identify and Document Assets:
- Create a detailed inventory of all assets within your organization, including hardware, software, and data. This will serve as your baseline.
Categorize Assets:
- Group assets by criticality, function, and location. Prioritize those that are most vital to your operations and data protection.
- Vulnerability Scanning:
Choose the Right Vulnerability Assessment Tools:
- Select a reliable vulnerability scanning tool such as Nessus, Qualys, or OpenVAS. Ensure it can scan your entire infrastructure.
Schedule Regular Scans:
- Set up a recurring scanning schedule. Regular scans help identify vulnerabilities as they emerge.
- Vulnerability Detection:
Scan Your Network:
- Run the chosen scanning tool across your network and systems. It will identify vulnerabilities, weaknesses, and misconfigurations.
Analyze Scan Results:
- Thoroughly review the scan results. Prioritize vulnerabilities based on severity, potential impact, and ease of exploitation.
- Validation and Testing:
Perform Manual Testing:
- Conduct manual testing to confirm the existence of vulnerabilities and validate their severity. This step helps eliminate false positives.
- Patch Management:
Develop a Patching Strategy:
- Create a well-defined patch management strategy, specifying how and when patches should be applied.
Execute Patching:
- Swiftly apply patches to address high-risk vulnerabilities. Ensure all patches are thoroughly tested before deployment.
- Risk Mitigation:
Implement Security Controls:
- Enhance your security posture by implementing appropriate security controls, like firewalls, intrusion detection systems, and access controls.
Monitor and Respond:
- Continuously monitor your network for new vulnerabilities. When new vulnerabilities arise, assess their potential impact and respond promptly.
- Documentation and Reporting:
Maintain Records:
- Keep detailed records of vulnerability assessments, including findings, actions taken, and patch management.
Generate Reports:
- Create comprehensive reports summarizing your vulnerability assessment results. Share these reports with stakeholders, including senior management.
Following these vulnerability assessment steps, you can effectively identify and mitigate security risks, safeguarding your organization from potential threats.
Centraleyes For Vulnerability Management
Centraleyes offers a comprehensive suite of tools to safeguard your data and IT assets.
Our cyber GRC platform combines the latest technology with expert guidance to help you:
- Identify and Prioritize Vulnerabilities: Centraleyes assists in identifying vulnerabilities across your network, systems, and applications, prioritizing them based on their potential impact.
- Streamline Vulnerability Management: We provide the tools and insights to manage vulnerabilities effectively. Our platform supports your end-to-end vulnerability management process, from scanning your network to validating results.
- Enhance Risk Mitigation: Centraleyes enables you to implement robust security controls, monitor your network for emerging vulnerabilities, and respond promptly to new threats.
- Document and Report: Our platform simplifies the documentation and reporting of vulnerability assessments, helping you maintain comprehensive records and share results with key stakeholders.
Remember, knowledge is power in cybersecurity, and Centraleyes is your trusted source for the knowledge and tools you need to stay secure.
Learn More About Centraleyes
Related Content

- All Resources

500 7th Avenue New York, NY 10018
- +1-212-655-3023
- [email protected]
- Internal Risk Management
- Vendor Risk Management
- NIST 800-53
- Partner Resources
- Compliance Automation

Sign up for our Centraleyes Intelligence Report
- Vendor risk management
- Compliance management
- Become a partner
Try the Centraleyes Risk & Compliance
Free for 30 Days

- NIST 800-53
- Common Controls Hub
RA-5 VULNERABILITY SCANNING
The organization employs vulnerability scanning tools that include the capability to readily update the information system vulnerabilities to be scanned.
The organization updates the information system vulnerabilities scanned Selection (one or more): Assignment: organization-defined frequency ; prior to a new scan; when new vulnerabilities are identified and reported .
The organization employs vulnerability scanning procedures that can identify the breadth and depth of coverage (i.e., information system components scanned and vulnerabilities checked).
The organization determines what information about the information system is discoverable by adversaries and subsequently takes Assignment: organization-defined corrective actions .
The information system implements privileged access authorization to Assignment: organization-identified information system components for selected Assignment: organization-defined vulnerability scanning activities .
The organization employs automated mechanisms to compare the results of vulnerability scans over time to determine trends in information system vulnerabilities.
Withdrawn: Incorporated into CM-8 .
The organization reviews historic audit logs to determine if a vulnerability identified in the information system has been previously exploited.
Withdrawn: Incorporated into CA-8 .
The organization correlates the output from vulnerability scanning tools to determine the presence of multi-vulnerability/multi-hop attack vectors.
How To Prevent
- API7:2019 Security Misconfiguration
- API8:2019 Injection
- API9:2019 Improper Assets Management
- API10:2019 Insufficient Logging & Monitoring
- What's Next For Developers
- What's Next For DevSecOps
- Methodology and Data
- Acknowledgments
API6:2019 - Mass Assignment
Is the api vulnerable.
Objects in modern applications might contain many properties. Some of these properties should be updated directly by the client (e.g., user.first_name or user.address ) and some of them should not (e.g., user.is_vip flag).
An API endpoint is vulnerable if it automatically converts client parameters into internal object properties, without considering the sensitivity and the exposure level of these properties. This could allow an attacker to update object properties that they should not have access to.
Examples for sensitive properties:
- Permission-related properties : user.is_admin , user.is_vip should only be set by admins.
- Process-dependent properties : user.cash should only be set internally after payment verification.
- Internal properties : article.created_time should only be set internally by the application.
Example Attack Scenarios
Scenario #1.
A ride sharing application provides a user the option to edit basic information for their profile. During this process, an API call is sent to PUT /api/v1/users/me with the following legitimate JSON object:
The request GET /api/v1/users/me includes an additional credit_balance property:
The attacker replays the first request with the following payload:
Since the endpoint is vulnerable to mass assignment, the attacker receives credits without paying.
Scenario #2
A video sharing portal allows users to upload content and download content in different formats. An attacker who explores the API found that the endpoint GET /api/v1/videos/{video_id}/meta_data returns a JSON object with the video’s properties. One of the properties is "mp4_conversion_params":"-v codec h264" , which indicates that the application uses a shell command to convert the video.
The attacker also found the endpoint POST /api/v1/videos/new is vulnerable to mass assignment and allows the client to set any property of the video object. The attacker sets a malicious value as follows: "mp4_conversion_params":"-v codec h264 && format C:/" . This value will cause a shell command injection once the attacker downloads the video as MP4.
- If possible, avoid using functions that automatically bind a client’s input into code variables or internal objects.
- Whitelist only the properties that should be updated by the client.
- Use built-in features to blacklist properties that should not be accessed by clients.
- If applicable, explicitly define and enforce schemas for the input data payloads.
- CWE-915: Improperly Controlled Modification of Dynamically-Determined Object Attributes
- Engineering Mathematics
- Discrete Mathematics
- Operating System
- Computer Networks
- Digital Logic and Design
- C Programming
- Data Structures
- Theory of Computation
- Compiler Design
- Computer Org and Architecture
- Cyber Security Tutorial
Introduction
- OSI Security Architecture
- Active and Passive attacks in Information Security
- Types of Security Mechanism
- A Model for Network Security
Cyber Technology
- Basics of Wi-Fi
- The Internet and the Web
- What is a Website ?
- Cryptography and Network Security Principles
- Public Key Infrastructure
- What is Electronic Signature?
- Identity and Access Management
- What Is Cloud Computing ?
Cyber Ethics
- Intellectual Property Rights
- Fundamental Rights (Articles 12-35): A Comprehensive Guide
- Introduction to Ethical Hacking
- What is a Scam?
Cyber Crimes
- Psychological Profiling in Cybersecurity
- Social Engineering - The Art of Virtual Exploitation
- Cyber Stalking
- How to Defend Against Botnets ?
- Emerging Attack Vectors in Cyber Security
- Malware and its types
- What is Phishing?
- Cyber Crime - Identity Theft
- What is Cyber Terrorism?
- What is Proxy Server?
Cyber Crime Techniques
- Worms, Viruses and beyond !!
- Trojan Horse in Information Security
Keyloggers and Spyware
- Types of SQL Injection (SQLi)
- Buffer Overflow Attack with Example
- Reverse Engineering - Software Engineering
- Difference Between Vulnerability and Exploit
- Basic Network Attacks in Computer Network
- Kali Linux - Hacking Wi-Fi
- Web Server and its Types of Attacks
- Types of VoIP Hacking and Countermeasures
- How to Spoof SMS Message in Linux ?
- Difference between Backup and Recovery
- Manual Code Review : Security Assessment
- Penetration Testing - Software Engineering
Prevention and Protection
What is vulnerability assessment.
- Secure coding - What is it all about?
- Chain of Custody - Digital Forensics
- Digital Forensics in Information Security
- Introduction of Computer Forensics
- What is Network Forensics?
Cyber Forensics
- Cybercrime Causes And Measures To Prevent It
- Digital Evidence Collection in Cybersecurity
- Digital Evidence Preservation - Digital Forensics
- Computer Forensic Report Format
- How to Stop Phishing
Cyber Crime Investigation
- Intellectual Property in Cyberspace
- Cyber Security Policy
- History of Cyber Security
- What is Internet? Definition, Uses, Working, Advantages and Disadvantages
- Cyber Security Metrics
- What is Cybersecurity Framework?
- Cyber Security, Types and Importance
Cyber security Evolution
- Substitution Cipher
- Difference between Substitution Cipher Technique and Transposition Cipher Technique
- Difference between Block Cipher and Transposition Cipher
Cyber security Objectives
- Data encryption standard (DES) | Set 1
- Strength of Data encryption standard (DES)
- Differential and Linear Cryptanalysis
Classical Encryption Techniques
- Difference between AES and DES ciphers
- Advanced Encryption Standard (AES)
Block Ciphers and the Data Encryption Standard
- Implementation of RC4 algorithm
- Introduction to Chinese Remainder Theorem
- Discrete logarithm (Find an integer k such that a^k is congruent modulo b)
- Public Key Encryption
Advanced Encryption Standard
- Key Management in Cryptography
- Implementation of Diffie-Hellman Algorithm
Moreon Symmetric Ciphers
- Message Authentication Requirements
- How message authentication code works?
- Hash Functions in System Security
Introduction to Number Theory
- Whirlpool Hash Function in Python
- HMAC Algorithm in Computer Network
Public-Key Cryptography and RSA
- Types of Authentication Protocols
- Digital Signature Standard (DSS)
Key Management:OtherPublic-Key Cryptosystems
- X.509 Authentication Service
- PGP - Authentication and Confidentiality
Message Authentication and Hash Functions
- IP security (IPSec)
- IPSec Architecture
- Internet Protocol Authentication Header
Hashand MAC Algorithms
- Web Security Considerations
- Secure Socket Layer (SSL)
- Transport Layer Security (TLS)
Digital Signatures and Authentication Protocols
- Intruders in Network Security
- Password Management in Cyber Security
Authentication Applications
Electronic mail security, ip security, web security, malicious software.
The Information System is an integrated set of the component for collecting, storing, processing and communicating information. There are various phases involved in making an information system. One of such phases includes a review of the system security. All systems are prone to attacks like Cross-site scripting(XSS) and SQL injection . Thus, it is important that the organization reviews the system for possible threats beforehand. This helps in identifying the vulnerabilities and weaknesses of the system. This kind of systematic review of a system is called vulnerability assessment.
How does Vulnerability Assessment help?
It helps any organization safeguard itself from cyber attacks by identifying the loopholes in advance. Here are some threats that we can prevent if we use vulnerability assessment.
- Injection attacks like XSS and SQL injection
- Authentication faults that lead to unidentified access to important data
- Insecure settings and weak defaults
What are the different types of Vulnerability Assessments?
Vulnerability assessments can be of different types depending on the need and type of a system.
- Host Vulnerability Assessment: Applications and information systems often use servers to work at the backend. Many attackers use these servers to inject threats in the system. Thus, it is important to test servers and review them for vulnerability.
- Database Vulnerability Assessment: Database is one of the most important aspect of any information system. It is where crucial user data is stored. Breach in a database system might lead to heavy losses. Thus, it is important to make sure that any outsider can neither access the data nor alter or destroy it. This can be done by assessing the database for possible threats and vulnerabilities.
- Network Vulnerability Assessment: Private as well as public networks are prone to injection attacks. Checking a network for possible issues is a better way to prevent huge losses in data.
- The frontend
- The backend
Both of these parts have their own source code which must be statically as well as dynamically analyzed for possible vulnerabilities. This assessment is often done through automated scans of the source code.
The Process of Vulnerability Assessment:
The process of Vulnerability Assessment is divided into four stages. Let us discuss them one by one.
- Testing or Vulnerability Identification: All the aspects of a system like networks, servers, and databases are checked for possible threats, weaknesses, and vulnerabilities. The goal of this step is to get a list of all the possible loopholes in the security of the system. The testing is done through machines as well as manually and all parameters are kept in mind while doing so.
- Analysis: From the first step, we get a list of vulnerabilities. Then, it is time that these are analyzed in detail. The goal of this analysis is to identify where things went wrong so that rectification can be done easily. This step aims at finding the root cause of vulnerabilities.
- Risk Assessment: When there are many vulnerabilities, it becomes important to classify them on the basis of risks they might cause. The main objective of this step is to prioritize vulnerabilities on the basis of data and systems they might affect. It also gauges the severity of attacks and the damage they can cause.
- Rectification: Once if have a clear layout of the risks, their root cause, and their severity, we can start making corrections in the system. The fourth step aims at closing the gaps in security by introducing new security tools and measures.
Tools for Vulnerability Assessment:
Manually testing an application for possible vulnerabilities might be a tedious job. There are some tools that can automatically scan the system for vulnerabilities. A few such tools include:
- Simulation tools that test web applications.
- Scanners that test network services and protocols.
- Network scanners that identify malicious packets and defects in IP addresses.
Advantages of Vulnerability Assessment:
- Detect the weakness of your system before any data breach occurs.
- A list of all possible vulnerabilities for each device present in the system.
- Record of security for future assessments.
Disadvantages of Vulnerability Assessment:
- Some advanced vulnerabilities might not be detected.
- Assessment tools might not give exact results.
Please Login to comment...
Similar reads.
- Cyber-security
- Geeks-Premier-League-2022
- Geeks Premier League
Improve your Coding Skills with Practice
What kind of Experience do you want to share?
- Mass Assignment
What is a Mass Assignment Attack?
In order to reduce the work for developers, many frameworks provide convenient mass-assignment functionality. This lets developers inject an entire set of user-entered data from a form directly into an object or database. Without it, developers would be forced to tediously add code specifically for each field of data, cluttering the code base with repeated form mapping code.
The downside of this functionality is that it is often implemented without a whitelist that prevents users from assigning data to protected fields. An attacker may exploit this vulnerability to gain access to sensitive data or to cause data loss.
As demonstrated by prominent cases , even the best teams of developers can miss this non-obvious vulnerability.
An Example of a Vulnerability
In this example, a web shop allows users to sign up and keep track of their orders. The owner of the web shop has a special administrator account that allows them to manage other users and their orders. The administrator account is created in the database, just like a regular user account, except it has an is_administrator flag set.
On the sign up page, the user is asked to enter their email address and select a password:
The corresponding controller action creates the user in the database:
An attacker may inject their own HTML into form (or otherwise modify the request):
The controller action will create the user, letting the attacker gain complete control of the web shop:
How To Defend Against Mass Assignment Attacks
In the example above, the developer should change the code to either explicitly assign the attributes for the allowed fields, or use a whitelisting function provided by the framework (Ruby on Rails in this case):
More useful information may be found at:
- https://www.owasp.org/index.php/Mass_Assignment_Cheat_Sheet
- http://guides.rubyonrails.org/v3.2.9/security.html#mass-assignment
- https://laravel.com/docs/5.0/eloquent#mass-assignment
- https://odetocode.com/Blogs/scott/archive/2012/03/11/complete-guide-to-mass-assignment-in-asp-net-mvc.aspx
- https://coffeeonthekeyboard.com/mass-assignment-security-part-10-855/
- https://nvisium.com/resources/blog/2014/01/17/insecure-mass-assignment-prevention.html
Let Us Review Your Software
We provide code security reviews as a service. Based on our extensive experience in the field of sofware engineering and IT security, we know how to efficiently review entire code bases and identify security critical parts of the software.
This enables us to provide our security code review service at a fixed rate per review, providing our customers a transparent, efficient and reliable process.
- Security review of your software by experts
- OWASP Top 10 vulnerability check
- Security Report with recommendations
- Invaluable insights into the state of security in your application
Fixed Price per Review
- Broken Access Control
- Broken Authentication
- Cross-Site Request Forgery (CSRF)
- Cross-Site Scripting (XSS)
- Insecure Direct Object Reference
- Security Misconfiguration
- Sensitive Data Exposure
- SQL Injection
- Timing Attack
- Unvalidated Redirection
- Vulnerable Dependencies
Technologies
- Microsoft .Net
- Ruby on Rails
ROPE Security is a Software Security Consultancy Firm based in Denmark. Our clients range from large international enterprises to start-ups and small businesses.
If you have any questions, do not hesitate to contact us at [email protected]

Mass Assignment Vulnerabilities
Web application security is of critical importance in today’s digital landscape. Developers need to be aware of various vulnerabilities that malicious actors can exploit. One such critical vulnerability is “Mass Assignment Vulnerability,” a commonly overlooked security flaw in web applications. This article aims to shed light on the nature of this threat, its implications, and how developers can prevent it. Additionally, we’ll provide an example of vulnerable PHP code to help illustrate the concept.
- Anthony Cole
- September 15, 2023
Table of Contents
What is mass assignment vulnerability.
Mass Assignment Vulnerability occurs when a web application allows users to submit a more extensive set of data than is intended or safe. Typically, this vulnerability arises due to careless handling of user inputs and inadequate validation and sanitization. In some cases, the developer might intend to allow specific data updates using a particular request but unintentionally enables the modification of sensitive or protected fields.
The potential consequences of this vulnerability can be severe, as attackers can exploit it to alter data, escalate privileges, or even gain unauthorized access to critical system components. Therefore, it is crucial for developers to identify and mitigate this vulnerability in their applications.
Example of Vulnerable PHP Code
Consider a hypothetical scenario with a PHP-based web application that allows users to update their profile information, such as name, email, and account type. The developer has created a simple class to handle user updates:

In this code snippet, the developer fetches a JSON object from the POST body and directly uses it to update the user’s profile without proper validation. An attacker could manipulate the POST request, including additional data fields like ‘isAdmin’ or ‘isActivated,’ which should never be allowed to be modified by regular users. The above code also implements an auto-mapper functionality that populates the User class properties with the corresponding values found in the $userObject object, which is user-controlled input. In figure 2 an example of a HTTP request with the expected JSON input object can be seen. In figure 3, a request showing how the “isAdmin” property can be updated is shown.

To prevent a user from populating class properties that should be inaccessible, an allow list should be implemented as seen in the code below. The highlighted code defines an allow list containing the “name” and “email” properties. When the auto-mapper assigns values to the class properties, the current property is checked against the allow list.

Mitigation Techniques
To prevent Mass Assignment Vulnerabilities, developers can implement the following best practices:
- Allowlist Input: Only update specific, intended fields. Create a list of allowed fields and update only those explicitly mentioned in the whitelist.
- Blocklist Rejected Fields: If the application requires users to update almost all fields except a few, developers can create a blocklist of disallowed fields.
- Input Validation: Always validate and sanitize user inputs to ensure they adhere to the expected format and are free from malicious data.
- Role-based Access Control (RBAC): Implement RBAC to define different user roles and permissions, ensuring that sensitive fields are only accessible to authorized personnel.
- Use Frameworks with Built-in Protection: Utilize web application frameworks with built-in security mechanisms to prevent Mass Assignment Vulnerabilities.
Mass Assignment Vulnerabilities pose a significant threat to web applications, potentially allowing attackers to manipulate critical data and gain unauthorized access. Developers must be vigilant and implement robust input validation and access control mechanisms to prevent this vulnerability. Developers can create more secure web applications and protect sensitive user data from potential breaches by adhering to best practices, testing and staying updated on the latest security measures.

Anthony Cole, Sr. Penetration Tester at Redbot Security
Anthony Cole is a Sr. Security Consultant with over 22 years of experience in information technology, IT security and software development. Anthony is fully GIAC certified in all facets of information security, enabling him to facilitate successful outcomes for customers. Anthony’s vast knowledge of both offensive and defensive security ensures that Redbot Security’s customers will receive the best service in the industry.
Anthony is Redbot Security’s AppSec SME and formerly a Sr. Level Application Penetration Testing Engineer for NetSpi and Presidio as well as Blutique LLC’s Chief Technical Officer and Sr. Application Developer.
Pen-Test Project Quote
Our expert team will help scope your project and provide a fast and accurate project estimate.
Popular Keywords
No Record Found
Related Articles

Machine Learning & Artificial Intelligence
Machine Learning (ML) is a subset of AI, and, more than likely, closely aligns with what we consider to be AI in the media.

Navigating Cybersecurity Threats with Monte Carlo Simulations and LLMs
Through repeated random sampling, allows us to simulate a wide array of social engineering attacks with a depth and breadth previously unimaginable.

From an Attacker’s Perspective: Client-Side Desync
Client-side desyncs are a class of browser-powered HTTP smuggling attacks. What you need to know and how to prevent a malicious actor from taking advantage of this vulnerability.

ICS/SCADA Penetration Testing: Where to Start
Becoming proficient in Operational Technology (OT), Industrial Control Systems (ICS), and Supervisory Control and Data Acquisition (SCADA) network testing can appear daunting as there are fewer learning resources.

Application Penetration Testing – Offensive Security
What is an API? APIs, including local and remote, come in various forms and are fundamental to modern software development. They serve as the bridge between different software components, enabling them to work together seamlessly.

From Military Cyberwarfare to Commercial Pen Testing
The following article is a discussion about helping you to best utilize your military skills to successfully transition into the commercial space.

Evolving Your Cybersecurity: From Penetration Testing to Red Teaming
While penetration testing is valuable in identifying technical vulnerabilities, red teaming provides a more holistic assessment by simulating realistic threat scenarios. By embracing red teaming, organizations can bolster their defenses, uncover weaknesses, and stay one step ahead of sophisticated adversaries.

NTLM relaying attack – Taking complete control
Active Directory Certificate Services (AD CS) presents various security risks for organizations. This article will help you understand a Relay Attack.

Examining the Modbus Protocol from an Offensive Security Perspective
While plenty of articles cover the Modbus protocol with varying degrees of detail and usage, this article aims to examine the Modbus protocol with an offensive security lens.

Attack Surface Management (ASM)
Today, cybercriminals have plenty of entry points to exploit. Therefore, it has become crucial for organizations to improve their attack surface visibility to have more effective protection. This is where attack surface management (ASM) comes into play. This article will explore all about attack surface management (ASM), including its importance, working principle, and benefits.
Additional Articles
Offensive security, what is social hacking, what you need to know about pci penetration testing, what is penetration testing (pen-testing), our nation under attack, manual penetration testing – manual testing vs automated testing, what is penetration testing & its different types, common cybersecurity issues that are easy to fix, security management platform, cyber threat news feed.
Check out the latest cybersecurity news around the globe

Redbot Security is a boutique penetration testing firm with a Sr. Level Team of cybersecurity experts. The entire team of Redbot Security is passionate about delivering cost-effective solutions that consider customers’ goals and priorities first.
- Customer Reviews
- Network Pen-Testing
- App Pen-Testing
- Wireless Testing
- ICS/SCADA Testing
- Red Teaming
- Cloud Security
- Social Engineering
- News and Updates
- Tech Insight Articles
© Copyright 2016-2023 powered by REDBOT SECURITY

Mass Assignment
Description.
Mass Assignment is a vulnerability wherein an active record pattern is manipulated into modifying data items that should normally restrict user functions such as passwords, granted permissions, or admin access. They arise when objects on the backend e.g. database records, are created by using the object representation received with the client request including fields that are not intended to be freely altered.
Active record and object-relational mapping are common features in many web application frameworks as they allow for serialized external data to be automatically converted upon input into internal objects and, subsequently, into the database records field. Depending on the framework, developers are sometimes allowed to automatically bind HTTP request parameters into program code variables or objects for ease of use. However, if the conversion interface for the framework is overly permissive and developers haven’t marked specific fields as immutable, the potential for exploitation is open.
Malicious attackers can leverage Mass Assignment vulnerabilities to manipulate the internal state of the application and potentially compromise its confidentiality, integrity, and availability. By overwriting the value of certain fields, an attacker may be able to modify an admin permission flag, thus effecting an authorization bypass which, depending on the level of authorization, could lead to full server access.
In 2012, none other than Github, the world’s code repository, was shown to be harbouring a potentially catastrophic Mass Assignment vulnerability that ended up being exposed by a security researcher in a fairly public stoush. The issue was fortunately resolved with no loss of data; but the security researcher in question was able to upload his public key to any organisation and thus potentially make malicious changes in their repositories.
The following exemplifies a Mass Assignment attack within a web application that stores users in a NoSQL database and implements access control by simply keeping one boolean flag is_admin for each user.
Upon sign up, some fields need to be used to create the new user. If the web application uses the whole POST data to build a new User object, a malicious actor could add the is_admin=1 field to the post data to overwrite the default value and gain administrative privileges on the application.
Developers must avoid using functions that bind client input into variables or internal objects automatically. Additionally, developers must explicitly define all payloads and parameters that the server is expecting.
Depending on the application framework, it may be possible to only allow fields that are determined safe to be fetched from the client request. If the application does not allow for this process, developers must ensure they manually determine which fields are allowed to be extracted from the request and used in downstream contexts.
Verify that frameworks protect against mass parameter assignment attacks, or that the application has countermeasures to protect against unsafe parameter assignment, such as marking fields private or similar.
- OWASP ASVS : 5.1.2
- OWASP Testing Guide : Test Business Logic Data Validation , Test Ability to Forge Requests , Test Integrity Checks
Table of contents
- Mass Assignment in .NET
- Mass Assignment in Java
- Mass Assignment in NodeJS
- Mass Assignment in PHP
- Mass Assignment in Python
- Mass Assignment in Ruby

IGNOU: BPAG-171 Solved Assignment 2022-2023 (DISASTER MANAGEMENT)
- 1 Assignment A
- 2 Answer the following in about 500 words each.
- 3 1. Define vulnerability and various factors that cause it.
- 4 2. Briefly discuss the relationship between disaster and development.
- 5 Assignment B
- 6 Answer the following in about 250 words each.
- 7 3. Write a note on the National Policy on Disaster Management, 2009 and National Disaster Management Plan, 2016.
- 8 4. List out the statutory provisions for mainstreaming disaster risk reduction.
- 9 5. Examine the case study of ‘The Indian Ocean Tsunami, 2004.’
- 10 Assignment C
- 11 Answer the following in about 100 words each.
- 12 6. What do you mean by epidemics?
- 13 7. Discuss the key components of disaster preparedness framework.
- 14 8. Comment on the concept of social and economic rehabilitation.
- 15 9. Write a note on the types of traditional knowledge.
- 16.1 How to Download BPAG-171 Solved Assignment?
- 16.2 Is the BPAS BPAG-171 Solved Assignment Free?
- 16.3 What is the last submission date for BPAG-171 Solved Assignment?
Welcome to the complete solution guide for IGNOU BPAG-171 Solved Assignment 2022-2023. This assignment will provide you with comprehensive answers to all the questions in the course material, helping you to score better grades and gain a deeper understanding of the subject. Whether you are a student enrolled in the program or just looking to improve your knowledge, this resource is perfect for you.

Assignment A
Answer the following in about 500 words each., 1. define vulnerability and various factors that cause it..
Ans: Vulnerability refers to the susceptibility or exposure to harm or damage. It can refer to physical, emotional, or psychological weaknesses, as well as to gaps or flaws in systems, processes, or structures that can be exploited or attacked. Vulnerability can arise from a variety of factors, including but not limited to:
- Physical or mental health conditions: Physical or mental illnesses or disabilities can leave a person vulnerable to harm, neglect, or abuse.
- Poverty or financial insecurity: People who struggle to make ends meet or who live in poverty are often more vulnerable to exploitation, crime, or other forms of harm.
- Social or cultural factors: Vulnerability can also result from social or cultural factors such as race, ethnicity, gender, sexual orientation, or religion, which can make a person more susceptible to discrimination, prejudice, or violence.
- Age: Older adults, children, and the elderly are often seen as more vulnerable due to declining physical or mental abilities, social isolation, or limited access to resources.
- Geography: People living in certain geographic areas, such as natural disaster zones or conflict-prone regions, are often more vulnerable to harm or displacement.
- Political or economic instability: Political or economic instability can also increase vulnerability, especially for marginalized or minority populations.
- Technology: As technology becomes increasingly central to our daily lives, so too does the potential for cyber attacks, data breaches, and other forms of technological vulnerability.
- Environmental factors: Environmental factors such as climate change or pollution can increase vulnerability by affecting access to resources, health, and well-being.
- Personal choices or circumstances: Personal choices or circumstances, such as substance abuse or involvement in criminal activities, can also increase vulnerability.
It is important to note that vulnerability is often interrelated and can compound over time. For example, a person living in poverty may be more vulnerable to health problems, which in turn can increase their vulnerability to exploitation or abuse.
2. Briefly discuss the relationship between disaster and development.
Ans: Disaster and development are two concepts that are closely intertwined, with one often having a significant impact on the other. In many cases, disasters can have a devastating effect on development efforts, reversing gains made and setting back progress. On the other hand, disaster risk reduction and resilience can be considered a key component of sustainable development.
Disasters have both direct and indirect impacts on development. Direct impacts include physical destruction of infrastructure, loss of lives, and disruption of economic activities. Indirect impacts can be just as severe, including the displacement of populations, loss of livelihoods, and long-term economic and social disruption. These impacts can have a ripple effect, undermining years of development work and leaving communities vulnerable to future disasters.
However, disasters can also present opportunities for development. For instance, the aftermath of a disaster can provide a unique window of opportunity to build back better and stronger, incorporating disaster risk reduction measures into development planning and implementation. This not only helps reduce the risk of future disasters, but also contributes to sustainable development.
Incorporating disaster risk reduction into development planning is critical for ensuring that development is sustainable and resilient. This includes investing in infrastructure and services that are resilient to disaster, building the capacities of communities and governments to prepare for and respond to disasters, and strengthening governance and institutions to better manage disaster risk.
Another important aspect of the relationship between disaster and development is the role of aid and financing. Aid and financing can play a critical role in supporting disaster-affected communities, but they can also have unintended consequences, such as hindering local ownership and sustainability. As such, it is important to ensure that aid and financing are aligned with local development goals and strategies, and that they support local capacities and institutions.
Assignment B
Answer the following in about 250 words each., 3. write a note on the national policy on disaster management, 2009 and national disaster management plan, 2016..
Ans: The National Policy on Disaster Management, 2009 and the National Disaster Management Plan, 2016 are two important documents that outline India’s approach to disaster management.
The National Policy on Disaster Management, 2009 provides a comprehensive framework for disaster management in India, encompassing the full spectrum of activities from preparedness and risk reduction to response, relief, and recovery. The policy recognizes the importance of community-based disaster risk management, strengthens the role of the government in disaster management, and encourages multi-stakeholder partnerships and collaboration.
The National Disaster Management Plan, 2016, on the other hand, provides a detailed plan of action for disaster management in India, covering all phases of the disaster management cycle, including preparedness, response, and recovery. The plan is based on the principles of risk reduction, preparedness, response, and recovery, and is intended to serve as a blueprint for action at all levels of government, including local, state, and national.
Both the National Policy on Disaster Management, 2009 and the National Disaster Management Plan, 2016 play an important role in guiding and directing disaster management efforts in India. They provide a comprehensive framework for disaster management and help to ensure that disaster management efforts are effective, efficient, and consistent across the country.
4. List out the statutory provisions for mainstreaming disaster risk reduction.
Ans: There are several statutory provisions for mainstreaming disaster risk reduction (DRR) into development planning and implementation, including:
- The Disaster Management Act, 2005: This act provides the legal framework for disaster management in India, including provisions for DRR, emergency response, and recovery efforts. The act establishes the National Disaster Management Authority and State Disaster Management Authorities, which are responsible for implementing DRR policies and programs.
- National Disaster Management Plan, 2016: The National Disaster Management Plan outlines India’s approach to DRR and provides a comprehensive plan of action for disaster management, covering all phases of the disaster management cycle, including preparedness, response, and recovery.
- National Building Code, 2016: This code provides guidelines for the construction of buildings and infrastructure, including provisions for ensuring that they are disaster-resistant and resilient.
- Environmental Impact Assessment Notification, 1994: This notification requires that all development projects undergo an environmental impact assessment, including a risk assessment for disasters, and that mitigation measures be incorporated into the project design.
- National Land Use Policy, 2011: This policy provides guidelines for the sustainable use of land, including provisions for reducing disaster risk and incorporating DRR into land-use planning and decision-making.
- National Water Policy, 2012: This policy provides guidelines for the sustainable use of water resources, including provisions for reducing disaster risk and incorporating DRR into water-resource management.
- National Forest Policy, 1988: This policy provides guidelines for the sustainable management of forests, including provisions for reducing disaster risk and incorporating DRR into forest management and conservation.
These statutory provisions for DRR help to ensure that disaster risk is considered in all phases of development planning and implementation, from project design to implementation and monitoring. They are critical for reducing the risk of disasters and ensuring that development efforts are sustainable and resilient.
5. Examine the case study of ‘The Indian Ocean Tsunami, 2004.’
Ans: The Indian Ocean Tsunami of 2004 is a powerful case study of the devastating impact that natural disasters can have on communities and the importance of disaster risk reduction (DRR) measures. On December 26, 2004, a massive earthquake struck off the coast of Sumatra, Indonesia, generating a huge tsunami that impacted several countries in the Indian Ocean region, including India, Sri Lanka, Thailand, and the Maldives.
The Indian Ocean Tsunami resulted in widespread loss of life and property, with over 230,000 people killed and millions more left homeless. The disaster also had a significant impact on the local economies, with many coastal communities and fishing villages destroyed, leaving residents without livelihoods and access to basic services.
The Indian Ocean Tsunami highlighted the critical importance of DRR measures, including early warning systems, evacuation plans, and risk-informed land use planning, in reducing the impact of disasters. In the aftermath of the disaster, many countries in the region, including India, took steps to enhance their DRR efforts, including the development of early warning systems, risk assessments, and evacuation plans, as well as improved land-use planning and zoning to reduce the risk of future disasters.
Assignment C
Answer the following in about 100 words each., 6. what do you mean by epidemics.
Ans: Epidemics refer to the sudden and rapid spread of a disease within a specific population or geographic area. They occur when the number of new cases of a disease exceeds what is normally expected in a given time period and location. Epidemics can be caused by a variety of factors, including the emergence of new or drug-resistant strains of a disease, inadequate public health infrastructure, and poor sanitation and hygiene conditions. Epidemics can have significant health and social impacts, including widespread illness, hospitalization, and death, as well as economic losses and disruptions to daily life. Effective disease surveillance, preparedness, and response measures are crucial in controlling and preventing epidemics.
7. Discuss the key components of disaster preparedness framework.
A disaster preparedness framework is a comprehensive system that helps communities and organizations prepare for and respond to disasters. The key components of a disaster preparedness framework include:
- Risk assessment: Understanding the potential risks and hazards faced by a community or organization, including natural, technological, and human-made disasters.
- Planning: Developing and testing plans for disaster response and recovery, including evacuation plans, communication strategies, and logistics support.
- Training and drills: Providing training and conducting drills to familiarize personnel with response plans, procedures, and equipment.
- Resource management: Ensuring the availability of adequate resources, including personnel, equipment, and supplies, to respond to disasters.
- Public education and outreach: Educating the public on disaster risks and preparedness measures and encouraging them to take proactive steps to prepare for disasters.
- Monitoring and evaluation: Monitoring the effectiveness of preparedness efforts and evaluating the results to make necessary improvements.
These components work together to build a robust and effective disaster preparedness framework, which is critical in ensuring the safety and well-being of communities and organizations during and after disasters.
8. Comment on the concept of social and economic rehabilitation.
Ans: Social and economic rehabilitation refers to the process of rebuilding and restoring the social and economic fabric of communities affected by disasters or conflicts. This includes activities aimed at restoring essential services, such as healthcare, education, and housing, as well as programs that support the recovery of livelihoods, such as employment and income generation initiatives.
The goal of social and economic rehabilitation is to help communities and individuals recover from the impacts of disasters and conflicts, and return to a state of normalcy as quickly as possible. This involves addressing both immediate needs, such as emergency shelter and food assistance, as well as long-term challenges, such as rebuilding infrastructure and restoring livelihoods.
Effective social and economic rehabilitation requires a coordinated effort between government agencies, non-government organizations, and the affected communities themselves. It is also important to take a comprehensive and inclusive approach, considering the needs of vulnerable groups, such as women, children, and people with disabilities, to ensure that their specific needs are met.
9. Write a note on the types of traditional knowledge.
Ans: Traditional knowledge refers to the cultural and environmental knowledge, skills, and practices passed down from generation to generation within a community. There are various types of traditional knowledge, including:
- Agricultural knowledge: Knowledge related to traditional agricultural practices, including crop selection, soil management, and pest control.
- Ecological knowledge: Knowledge of the local environment and its resources, including the use of local flora and fauna for food, medicine, and other purposes.
- Medicinal knowledge: Knowledge of traditional healing practices, including the use of herbal remedies, massage techniques, and other natural therapies.
- Spiritual knowledge: Knowledge of traditional beliefs, rituals, and practices related to spirituality, including religious customs and spiritual healing practices.
- Artistic knowledge: Knowledge of traditional arts, crafts, music, and dance, which are often closely tied to cultural and spiritual practices.
Traditional knowledge is often closely tied to local cultural and environmental conditions, and can provide valuable insights into sustainable development practices. However, traditional knowledge is often under threat from modernization, globalization, and other factors, and efforts are needed to preserve and protect this important cultural heritage.
10. List out the principles of community based disaster management.
Ans: Community-based disaster management (CBDM) is a participatory approach to disaster management that involves communities in the planning and implementation of disaster preparedness and response activities. The principles of CBDM include:
- Community participation: Encouraging active community involvement in all aspects of disaster management, from risk assessment to recovery and rehabilitation.
- Empowerment: Empowering communities to take ownership of their own disaster management, including developing and implementing disaster preparedness plans.
- Inclusiveness: Ensuring that all members of the community, including vulnerable groups such as women, children, and people with disabilities, are involved and represented in disaster management activities.
- Sustainability: Promoting sustainable disaster management practices that prioritize long-term resilience over short-term solutions.
- Collaboration: Building partnerships and networks between communities, government agencies, and non-government organizations to enhance disaster management efforts.
By following these principles, CBDM helps to build more resilient communities and ensure that disaster management efforts are community-led, effective, and sustainable.
How to Download BPAG-171 Solved Assignment?
You can download it from the www.edukar.in , they have a big database for all the IGNOU solved assignments.
Is the BPAS BPAG-171 Solved Assignment Free?
Yes this is absolutely free to download the solved assignment from www.edukar.in
What is the last submission date for BPAG-171 Solved Assignment?
For June Examination: 31st March, For December Examination: 30th September
Related Posts:

Leave a Comment Cancel reply
Save my name, email, and website in this browser for the next time I comment.

You are viewing this page in an unauthorized frame window.
This is a potential security issue, you are being redirected to https://nvd.nist.gov
You have JavaScript disabled. This site requires JavaScript to be enabled for complete site functionality.
Official websites use .gov A .gov website belongs to an official government organization in the United States.
Information Technology Laboratory
National vulnerability database.
- Vulnerabilities
NIST has updated the NVD program announcement page with additional information regarding recent concerns and the temporary delays in enrichment efforts.
Weakness Enumeration
Change history, new cve received by nist 5/01/2024 5:15:51 pm.

IMAGES
VIDEO
COMMENTS
Define the criteria by which vulnerable items (VIs) are automatically assigned to an assignment group for remediation. Starting with v15.0 of Vulnerability Response, the table labels for vulnerability ... If the Reapply all vulnerability assignment rules scheduled job has not run before the first time you use Apply Changes, then it ...
Vulnerability assessment is the process of identifying, classifying, and prioritizing security vulnerabilities in IT infrastructure. A comprehensive vulnerability assessment evaluates whether an IT system is exposed to known vulnerabilities, assigns severity levels to identified vulnerabilities, and recommends remediation or mitigation steps ...
Vulnerability management is an organization's multi-step approach to mitigating security risks. Finding vulnerabilities in cloud-based systems, apps, and infrastructure is a sophisticated vulnerability management procedure. Considering the growing cyber risk that organizations confront as we approach 2024, this step is crucial: Vulnerability ...
A vulnerability in the context of the CVE Program is defined by Section 7. Assignment Rules. In general, a vulnerability is defined as a weakness in the computational logic (e.g., code) found in software and hardware components that, when exploited, results in a negative impact to confidentiality, integrity, OR availability.
OCTAVE (Operationally Critical Threat, Asset, and Vulnerability Evaluation) is a security framework for determining risk level and planning defenses against cyber assaults. The framework defines a methodology to help organizations minimize exposure to likely threats, determine the likely consequences of an attack and deal with attacks that succeed.
A vulnerability assessment is a systematic review of security weaknesses in an information system. It evaluates if the system is susceptible to any known vulnerabilities, assigns severity levels to those vulnerabilities, and recommends remediation or mitigation, if and whenever needed. Examples of threats that can be prevented by vulnerability ...
Vulnerability management defined. Vulnerability management is a continuous, proactive, and often automated process that keeps your computer systems, networks, and enterprise applications safe from cyberattacks and data breaches. As such, it is an important part of an overall security program.
The "Mass Assignment" vulnerability is a security flaw that occurs when an application assigns user input directly to model attributes without proper validation or sanitization. This can lead to unauthorized access and modification of sensitive data, potentially compromising the security of the application and its users.
A vulnerability assessment is a way you can discover, analyze and mitigate weakness within your attack surface to lessen the chance that attackers can exploit your network and gain unauthorized access to your systems and devices. With an ever-expanding attack surface, protecting your organization from cyber risk is challenging.
A vulnerability assessment is the process of identifying, quantifying, and prioritizing any vulnerabilities within a network, system, or application. These vulnerabilities, if left unaddressed, could potentially be exploited by attackers to compromise the confidentiality, integrity, or availability of applications, data, and supporting systems.
Network vulnerability assessment (NVA) is a process that identifies and assesses security flaws in a network's publicly accessible devices. It also provides mitigation strategies to address these vulnerabilities and reduce the risk of security breaches.
The National Vulnerability Database (NVD) is tasked with analyzing each CVE once it has been published to the CVE List, after which it is typically available in the NVD within an hour. Once a CVE is in the NVD, analysts can begin the analysis process. The processing time can vary depending on the CVE, the information available, and the quantity ...
Notably, Gartner outlines a five-step VM cycle that most organizations adopt, with the initial phase being the vulnerability assessment: Assess: Here, vulnerability assessments shine by identifying assets, conducting scans, and producing detailed reports. Prioritize: The assessment results prioritize risks, considering the vulnerabilities ...
Shares information obtained from the vulnerability scanning process and security control assessments with Assignment: organization-defined personnel or roles to help eliminate similar vulnerabilities in other information systems (i.e., systemic weaknesses or deficiencies).
The attacker also found the endpoint POST /api/v1/videos/new is vulnerable to mass assignment and allows the client to set any property of the video object. The attacker sets a malicious value as follows: "mp4_conversion_params":"-v codec h264 && format C:/". This value will cause a shell command injection once the attacker downloads the video ...
Testing or Vulnerability Identification: All the aspects of a system like networks, servers, and databases are checked for possible threats, weaknesses, and vulnerabilities. The goal of this step is to get a list of all the possible loopholes in the security of the system. The testing is done through machines as well as manually and all ...
In this article, we'll define the vulnerability assessment process and then go into the details of the process. But before going into the specifics, here's a bird's eye view of this idea. In technical terms, a vulnerability assessment methodically examines an information system's security flaws.
What is risk-based vulnerability management (RBVM)? Risk-based vulnerability management (RBVM) is an approach to identifying and addressing security vulnerabilities in an organization's IT environment that prioritizes remediating vulnerabilities that pose the greatest risk.. In IT, a vulnerability is a flaw in software code or design that could lead to security being compromised, such as an ...
The main impact of a Mass Assignment vulnerability is linked to modifying or creating variables. Depending on the variables or objects affected, the impact can be more or less significant, ranging ...
In order to reduce the work for developers, many frameworks provide convenient mass-assignment functionality. This lets developers inject an entire set of user-entered data from a form directly into an object or database. Without it, developers would be forced to tediously add code specifically for each field of data, cluttering the code base ...
Mass Assignment Vulnerability occurs when a web application allows users to submit a more extensive set of data than is intended or safe. Typically, this vulnerability arises due to careless handling of user inputs and inadequate validation and sanitization. In some cases, the developer might intend to allow specific data updates using a ...
Mass Assignment is a vulnerability wherein an active record pattern is manipulated into modifying data items that should normally restrict user functions such as passwords, granted permissions, or admin access. They arise when objects on the backend e.g. database records, are created by using the object representation received with the client ...
There are a variety of factors including environmental factors, socioeconomic factors (housing, easy accessibility to food and nutrition, and healthcare), and social determinants (employment status and education levels) play a major role in regards to vulnerability in community health. 4.
Assignment A Answer the following in about 500 words each. 1. Define vulnerability and various factors that cause it. Ans: Vulnerability refers to the susceptibility or exposure to harm or damage. It can refer to physical, emotional, or psychological weaknesses, as well as to gaps or flaws in systems, processes, or structures that can be exploited or attacked.
National Vulnerability Database NVD. Vulnerabilities; NOTICE UPDATED - April, 25th 2024. ... CVE Dictionary Entry: CVE-2024-4058 NVD Published Date: 05/01/2024 NVD Last Modified: 05/02/2024 Source: Chrome. twitter (link is external) facebook (link is external) linkedin (link is ...
An Improper input validation vulnerability that could potentially lead to privilege escalation was discovered in JFrog Artifactory. Due to this vulnerability, users with low privileges may gain administrative access to the system. ... CVE Dictionary Entry: CVE-2024-4142 NVD Published Date: 05/01/2024 NVD Last Modified: 05/02/2024 Source: JFrog ...