A List of 181 Hot Cyber Security Topics for Research [2024]
Your computer stores your memories, contacts, and study-related materials. It’s probably one of your most valuable items. But how often do you think about its safety?
Our specialists will write a custom essay specially for you!
Cyber security is something that can help you with this. Simply put, it prevents digital attacks so that no one can access your data. Do you want to write a research paper related to the modern challenges of cyberspace? This article has all you need. In here, you’ll find:
- An overview of cyber security’s research areas.
- A selection of compelling cyber security research topics.
And don’t hesitate to contact our custom writing team in case you need any assistance!
- 🔝 Top 10 Topics
- ✅ Research Areas
- ⭐ Top 10 Cybersecurity Topics
- 🔒 Technology Security Topics
- 🖥️ Cybercrime Topics
- ⚖️ Cyber Law & Ethics Topics

🔍 References
🔝 top 10 cyber security topics.
- How does malware work?
- The principle of zero trust access
- 3 phases of application security
- Should removable media be encrypted?
- The importance of network security
- The importance of end-user education
- Cloud security posture management
- Do biometrics ensure security of IPhones?
- Can strong passwords protect information?
- Is security in critical infrastructure important?
✅ Cyber Security Topics & Research Areas
Cyber security is a vast, constantly evolving field. Its research takes place in many areas. Among them are:

- Safe quantum and space communications . Progress in quantum technologies and space travel calls for extra layers of protection.
- Data privacy. If someone’s personal information falls into the wrong hands, the consequences can be dire. That’s why research in this area focuses on encryption techniques.
- (Inter)national cyberethics, criminology, and law. This branch analyzes how international legal frameworks work online.
- AI and IoT security . We spend more and more of our daily lives online. Additionally, our reliance on AI increases. This scientific field strives to ensure a safe continuation of this path.
As you can see, cyber security extends in various exciting directions that you can explore. Naturally, every paper needs a cover page. We know that it’s one of the more annoying parts, so it’s not a bad thing to use a title page generator for your research paper . Now, let’s move on to our cyber topics list.
⭐ Top 10 Cybersecurity Topics 2024
- Is removable media a threat?
- Blockchain security vulnerabilities
- Why should you avoid public Wi-Fi?
- How to prevent phishing attacks
- Physical security measures in banks
- Security breaches of remote working
- How does two-factor authentication work?
- How to prevent social engineering attacks
- Cybersecurity standards for automotive
- Privacy settings of social media accounts
🔒 Computer Security Topics to Research
Safe computer and network usage is crucial. It concerns not only business but also individuals. Security programs and systems ensure this protection. Explore them with one of our topics:
Just in 1 hour! We will write you a plagiarism-free paper in hardly more than 1 hour
- How do companies avoid sending out confidential information ? Sending an email to the wrong person has happened to the best of us. But what happens if the message’s contents were classified? For your paper, you can find out what technologies can prevent such slip-ups.
- What are the best ways to detect malicious activity ? Any organization’s website gets plenty of daily traffic. People log in, browse, and interact with each other. Among all of them, it might be easy for an intruder to slip in.
- Internet censorship: classified information leaks . China takes internet censorship to the next level. Its comprehensive protection policies gave the system the nickname Great Firewall of China . Discuss this technology in your essay.
- Encrypted viruses as the plague of the century . Antivirus programs are installed on almost every computer. They prevent malicious code from tampering with your data. In your paper, you can conduct a comparison of several such programs.
- What are the pros and cons of various cryptographic methods? Data privacy is becoming more and more critical. That’s why leading messaging services frequently advertise with their encryption technologies .
- What makes blockchain secure ? This technique allows anonymity and decentralization when working with cryptocurrencies . How does it work? What risks are associated with it?
- What are the advantages of SIEM ? Security Incident and Event Management helps organizations detect and handle security threats. Your essay can focus on its relevance for businesses.
- What are the signs of phishing attempts?
- Discuss unified cyber security standards in healthcare .
- Compare and contrast various forms of data extraction techniques.
- What do computers need protocols for?
- Debate the significance of frequent system updates for data security .
- What methods does HTTPS use that make it more secure than HTTP?
- The role of prime numbers in cryptography .
- What are public key certificates , and why are they useful?
- What does a VPN do?
- Are wireless internet connections less secure than LAN ones? If so, why?
- How do authentication processes work?
- What can you do with IP addresses?
- Explain the technology of unlocking your phone via facial recognition vs. your fingerprint.
- How do you prevent intrusion attempts in networks ?
- What makes Telnet vulnerable?
- What are the phases of a Trojan horse attack?
- Compare the encryption technologies of various social networks.
- Asymmetric vs. symmetric algorithms.
- How can a person reach maximum security in the computer networking world ?
- Discuss autoencoders and reveal how they work.
💾 Information Security Topics to Research
Information security’s goal is to protect the transmission and storage of data. On top of that, network security topics are at the forefront of infosec research. If you’re looking for inspiration on the subject, check out these ideas.
- What are the mechanics of password protection ? Passwords are a simple tool to ensure confidentiality. What do users and developers need to keep in mind when handling passwords?
- What are the safest ways to ensure data integrity ? Everybody wants their data to be intact. Accidental or malicious modifications of data can have dire consequences for organizations and individuals. Explore ways to avoid it.
- How can one establish non-repudiation? Non-repudiation proves the validity of your data. It’s essential in legal cases and cyber security .
- How did the advent of these new technologies impact information security ? Mobile networks have changed the way we access information. On a smartphone , everything is permanently available at your fingertips. What adverse consequences did these technologies bring?
- How do big corporations ensure that their database environment stays conflict-free? We expect our computers to always run fast and without errors. For institutions such as hospitals, a smooth workflow is vital. Discuss how it can be achieved.
- Describe solid access control methods for organizations. In a company, employees need access to different things. This means that not everyone should have an admin account. How should we control access to information ?
- Medical device cyber security. For maximum safety, it’s best to employ several measures. Protection on the hard- and software side is just a part of it. What are some other means of security?
- Write an argumentative essay on why a career in information security doesn’t require a degree.
- Pros and cons of various infosec certificates.
- Cybersecurity in cruise ship industry
- The influence of remote work on a businesses’ infosec network .
- What should everyone be aware of when it comes to safeguarding private information?
- Select a company and calculate how much budget they should allocate on cyber security.
- What are the dangers of public Wi-Fi networks ?
- How secure are cloud services ?
- Apple vs. Microsoft : whose systems offer better security?
- Why is it important to remove a USB flash drive safely?
- Is it possible to create an unguessable password?
- Intranet security : best practices.
- Does the use of biometrics increase security?
- Face recognition vs. a simple code: what are the safest locking options for smartphones ?
- How do you recover data from a broken hard drive?
- Discuss the functions and risks of cookies and cache files.
- Online privacy regulations in the US and China.
- Physical components of infosec .
- Debate security concerns regarding electronic health records .
- What are unified user profiles, and what makes them potentially risky?
🖥️ Cybercrime Topics for a Research Paper
Knowledge is one of today’s most valuable assets. Because of this, cybercrimes usually target the extraction of information. This practice can have devastating effects. Do you want to learn more about the virtual world’s dark side? This section is for you.
- Give an overview of the various types of cybercrimes today . Cybercriminals are becoming more and more inventive. It’s not easy to keep up with the new threats appearing every day. What threats are currently the most prominent?
- How does cryptojacking work, and why is it problematic? Cryptocurrency’s value explosion has made people greedy. Countries such as Iceland have become a haven for datamining. Explore these issues in your essay.
- Analyze the success rate of email frauds . You’ve probably seen irrelevant ads in your spam folder before. They often sound so silly it’s hard to believe they work. Yet, unfortunately, many people become victims of such scams.
- How did the WannaCry malware work? WannaCry was ransomware that caused global trouble in 2017. It led to financial losses in the billions. What made it so dangerous and hard to stop?
- Give famous examples of cybercrimes that targeted people instead of money . Not all cybercrimes want to generate profit. Sometimes, the reasons are political or personal. Explore several instances of such crimes in your essay. How did they pan out?

- Analyze the implications of the Cyberpunk 2077 leak. The game’s bugs and issues made many people angry. Shortly after its flop, hackers released developer CD Projekt Red’s source codes. What far-reaching consequences could this have?
- Why do hackers commit identity theft? Social media has made it easy to steal identities . Many like to display their lives online. In your paper, research what happens to the victims of identity thefts.
- Should governments punish cybercrimes like real-life crimes?
- How does ransomware work?
- Describe the phases of a DDoS attack.
- What cybercrime cases led to changes in the legislature ?
- Track the evolution of online scams.
- Online grooming: how to protect children from predators.
- Are cybercrimes “gateway crimes” that lead to real-life misbehavior?
- What are man-in-the-middle attacks?
- Big data and the rise of internet crimes.
- Are cybercrimes more dangerous to society than they are to corporations?
- Is the internet increasing the likelihood of adolescents engaging in illegal activities?
- Do the downsides of cyberlife outweigh its positives?
- Is constantly checking your crush’s Facebook page cyberstalking?
- How do you recognize your online date is a scam?
- Describe what happens during a Brute Force attack.
- What’s the difference between pharming and phishing?
- The Lehman Bank cybercrimes
- Should the punishments for cybercriminals be harsher than they are now?
- Compare various types of fraud methods .
- How do you mitigate a denial-of-service attack?
🕵️ Topics for a Research Paper on Hacking
Blinking screens and flashing lines of code: the movie industry makes hacking look fascinating. But what actually happens when someone breaks into another person’s computer’s system? Write a paper about it and find out! The following prompts allow you to dive deeper into the subject.
- Is it vital to keep shutting down online movie streaming sites? Many websites offer free movie streaming. If one of their domains gets closed down, they just open another one. Are they a threat to the industry that must be stopped? Or should cyber law enforcement rather focus on more serious crimes?
- Explore the ethical side of whistleblowing. WikiLeaks is a platform for whistleblowers. Its founder, Julian Assange, has been under arrest for a long time. Should whistleblowing be a crime? Why or why not?
- How did Kevin Mitnick’s actions contribute to the American cyber legislature? Mitnick was one of the US’s first most notorious hackers. He claimed to have broken into NORAD’s system. What were the consequences?
- Examine how GhostNet operates. GhostNet is a large organization attacking governments. Its discovery in 2009 led to a major scandal.
- Describe how an SQL injection attack unfolds. Injection attacks target SQL databases and libraries. This way, hackers gain unauthorized access to data.
- What political consequences did the attack on The Interview imply? In 2014, hackers threatened to attack theaters that showed The Interview . As a result, Sony only showed the movie online and in limited releases.
- Write about cross-site request forgery attacks. Every website tells you that logging out is a crucial step. But what can happen if you don’t do it?
- What is “Anonymous,” and what do they do?
- Is it permissible to hack a system to raise awareness of its vulnerabilities?
- Investigate the origins of the hacking culture .
- How did industrial espionage evolve into hacking?
- Is piracy destroying the music and movie industries ?
- Explain the term “cyberwarfare.”
- Contrast different types of hacking .
- Connections between political protests and hacking.
- Is it possible to create an encryption that can’t be hacked?
- The role of hackers in modern warfare .
- Can hacking be ethical?
- Who or what are white hat hackers ?
- Discuss what various types of hackers do.
- Is jailbreaking a crime?
- How does hacking a phone differ from hacking a computer?
- Is hacking your personal home devices problematic?
- What is clickjacking?
- Why would hackers target newspapers ?
- Examine the consequences society would have to bear if a hacker targeted the state.
- Compare and analyze different hacking collectives.
⚖️ Topics on Cyber Law & Ethics to Look Into
Virtual life needs rules just like the real one does. The online world brings a different set of values and issues to the table. And, naturally, cyberlife has a legal framework. That’s where researching cyber law and ethics comes into play.
- Is it ethical that governments can always access their citizens’ data? In some countries, online platforms for personal information are standard. From medical exams to debts , everything is available with a click. The system is inarguably convenient. But what about its downsides?
- Is it still morally permissible to use Spotify ? Spotify has made listening to music more accessible than ever. However, artists only receive a tiny fraction of the company’s profits. Discuss the implications of this fact.
- Should internet forums require users to display their real names? Online harassment is a widespread problem. Nicknames hide the identities of ordinary users as well as perpetrators. Can the mandatory use of real names change the situation?
- Analyze online gaming behavior from a psychological standpoint. If one wants to play online games, one needs to have a thick skin. The community can be harsh. You can dedicate your paper to exploring these behaviors. Or you might want to ponder what game publishers can do to reduce hate speech.
- What type of restrictions should sellers implement to prevent domain speculation? Some people buy domains hoping that they will sell them later for more money. This practice makes registering a new website trickier.
- Does the internet need regulations to make adult content less visible? Every computer without parental control can access pornographic websites. Most of them don’t require registration . Their contents can be disturbing, and their ads can appear anywhere. What can be done about it?
- What are cyber laws still missing in America? The US has established many laws to regulate internet usage. Select the most significant ones and explain their relevance.
- Why should cyber ethics be different from real-world norms?
- Are there instances in which illegal downloading is justified?
- The rule of law in real life vs. in cyberspace.
- Does the internet need a government?
- What is cyber terrorism, and what makes it dangerous?
- Who is responsible for online misbehavior?
- How binding are netiquettes?
- What did the implementation of the GDPR change?
- Compare and contrast Indian vs. Venezuelan internet regulations.
- What does the CLOUD entail?
- How should law enforcement adapt to online technologies?
- AI applications : ethical limits and possibilities.
- Discuss trending topics in cyber law of the past ten years.
- Should schools teach online etiquette?
- Does internet anonymity bring out the worst in people?
- Is data privacy more important than convenience and centralization?
- Debate whether bitcoins could become the currency of the future.
- How can online consumers protect themselves from fraud ?
- Is buying from websites like eBay and Craigslist more ethical than buying from other online marketplaces?
- Present RSF’s Minecraft library and discuss its moral implications.
🖱️ Cyberbullying Topics for Essays and Papers
On the web, everyone can remain anonymous. With this added comfort, bullying rises to another level. It’s a serious issue that’s getting more and more problematic. Cyber security measures can alleviate the burden. Do you want to address the problem? Have a look at our cyberbullying topics below.
Receive a plagiarism-free paper tailored to your instructions. Cut 20% off your first order!
- Cyberbullying prevention in online learning environments . Online classes increase the possibility of cyberbullying. What can teachers do to watch out for their students?
- What makes online emotional abuse particularly difficult to bear? Bullying doesn’t necessarily have to be physical to hurt. Statistics show increased suicide rates among students who were harassed online. Explore the reasons behind this phenomenon.
- How can victims of identity theft reclaim their lives? Identity theft leads not only to mental distress. Thieves also have access to credit card information and other essential assets.
- What are the best methods to stay safe online? When surfing the internet, one always has to be on one’s toes. Avoiding harassment and bullying is a particularly challenging task.
- How can parents monitor their children’s behavior on the web? Children are particularly vulnerable online. They might enter dangerous online relationships with strangers if they feel lonely. They are also more susceptible to scams. What can parents do to protect them?
- Cyberbullying among university students. Online abuse in such websites is very common. Everyone can be a potential target, regardless of age or gender. Discuss whether the structure of social networks helps to spread cyberbullying.
- What societal factors contribute to online bullying? Not everyone who uses the internet becomes an abuser. It’s possible to establish several psychological characteristics of cyberbullies. Explore them in your paper.
- Define how cyberbullying differs from in-person harassment .
- Establish a link between feminism and the fight against cyberstalking .
- The emotional consequences of physical vs. verbal abuse.
- The effects of cyberbullying and academics.
- Short vs. long-term mental health effects of internet bullying .
- What are the most widespread means of cyberbullying ?
- Should people who want to play video games online get over the fact that the community is toxic?
- Is defending the freedom of speech more important than preventing the spread of hate speech?
- Reasons and consequences of Amanda Todd’s suicide.
- The dangers of pro-ana/-mia communities for adolescents.
- What are effective strategies to cope with online harassment ?
- Would cyber communism decrease bullying?
- How enhanced cyber security measures can help reduce abuse.
- The importance of parental control mechanisms on children’s computers.
- Traditional vs. cyberbullying in children.
- Do image-heavy websites such as Tumblr and Instagram affect one’s mental state similarly to active abuse?
- What kind of people does cyber abuse affect the most, and why?
- Analyze how the stalker uses the internet in Netflix’s series You .
- Catfishing: effects and solutions.
Thanks for reading through our article. If you found it helpful, consider sharing it with your friends. We wish you good luck with your project!
Further reading:
- 220 Best Science and Technology Essay Topics to Write About
- 204 Research Topics on Technology & Computer Science
- A List of 580 Interesting Research Topics [2024 Edition]
- A List of 179 Problem Solution Essay Topics & Questions
- 193 Interesting Proposal Essay Topics and Ideas
- 226 Research Topics on Criminal Justice & Criminology
- What Is Cybersecurity?: Cisco
- Cyber Security: Research Areas: The University of Queensland, Australia
- Cybersecurity: National Institute of Standards and Technology
- What Is Information Security?: CSO Online
- Articles on Cyber Ethics: The Conversation
- What Is Cybercrime?: Kaspersky
- Types of Cybercrime and How to Protect Yourself Against Them: Security Traits
- Hacking: Computing: Encyclopedia Britannica
- Hacking News: Science Daily
- Cyberbullying and Cybersecurity: How Are They Connected?: AT&T
- Cyberbullying: What Is It and How to Stop It: UNICEF
- Current Awareness: Cyberlaw Decoded: Florida State University
- Share to Facebook
- Share to Twitter
- Share to LinkedIn
- Share to email

Have you ever wondered why everyone has a unique set of character traits? What is the connection between brain function and people’s behavior? How do we memorize things or make decisions? These are quite intriguing and puzzling questions, right? A science that will answer them is psychology. It’s a multi-faceted...
![information security topics for research Student Exchange Program (Flex) Essay Topics [2024]](https://custom-writing.org/blog/wp-content/uploads/2021/01/student-exchange-program-284x153.jpg)
Participating in a student exchange program is a perfect opportunity to visit different countries during your college years. You can discover more about other cultures and learn a new language or two. If you have a chance to take part in such a foreign exchange, don’t miss it. Keep in...

How can you define America? If you’ve ever asked yourself this question, studying US history will help you find the answer. This article will help you dive deeper into this versatile subject. Here, you will find: Early and modern US history topics to write about. We’ve also got topics for...
![information security topics for research 380 Powerful Women’s Rights & Feminism Topics [2024]](https://custom-writing.org/blog/wp-content/uploads/2021/01/Womens-Rights-284x153.jpg)
Are you looking for perfect feminist topics? Then you’ve come to the right place. With our help, you can be sure to craft a great essay. Here, you can find feminist topics for discussion, feminism research topics and other ideas and questions for students. Some people think all feminists hate...

If you have an assignment in politics, look no further—this article will help you ace your paper. Here, you will find a list of unique political topics to write about compiled by our custom writing team. But that’s not all of it! Keep reading if you want to: See how to tackle political essay topics in your paper; Choose a topic that will be interesting for you to research; Refresh your knowledge of essential political concepts. Now, without further ado, let’s get started! Below, you’ll find political topics and questions for your task. 🔝 Top 10...

It’s not a secret that our health largely depends on nutrition. A balanced and wholesome diet improves our immune system. It lowers the risk of getting sick and makes us more productive. But if we don’t eat right, our overall well-being and performance worsen. You see, nutrition topics are more...

A presentation is a speech in which you explain a topic to an audience. It usually includes visuals done in a program such as PowerPoint. Teachers in schools and in colleges love to assign presentations for various reasons: It requires students to put their knowledge into practice.It teaches them how...

In modern societies, people do everything to live peacefully. Still, tensions often arise. We call them social issues when they start negatively impacting a specific group of people. Poverty, discrimination, and addiction are examples of such problems. We need to confront them to ensure equal treatment for everyone.

There are many ways to define popular culture. Here’s one of them: pop culture includes mainstream preferences in society within a specific time frame. It covers fashion, music, language, and even food. Pop culture is always evolving, engaging in new trends, and leaving the old ones behind.
![information security topics for research 500 Sociology Questions and Topics [Examples & Tips]](https://custom-writing.org/blog/wp-content/uploads/2021/01/Sociology-Questions-284x153.jpg)
Sociology is a study that focuses on people’s interactions. It looks at structures and changes in social life. Any situation involving people can become a topic of sociology. This article is designed to help high school and college students with sociology assignments. Whether you’re writing an essay, creating a presentation,...

Controversial issues are the ones that evoke a variety of opinions. They often cause heated debates. And, as you can guess, controversial research topics are not easy to handle. Luckily, we’ve got you covered. This article will: help you pick a controversial question for your essay;provide you a list of...

Plates break when you drop them. Glasses help you see better. Have you ever wondered why? Physics has the answer. It studies the observable as well as invisible aspects of nature. An essential part of this is examining the structure and interactions of matter.
For enquiries call:
+1-469-442-0620

60+ Latest Cyber Security Research Topics for 2024
Home Blog Security 60+ Latest Cyber Security Research Topics for 2024
The concept of cybersecurity refers to cracking the security mechanisms that break in dynamic environments. Implementing Cyber Security Project topics and cyber security thesis topics /ideas helps overcome attacks and take mitigation approaches to security risks and threats in real-time. Undoubtedly, it focuses on events injected into the system, data, and the whole network to attack/disturb it.
The network can be attacked in various ways, including Distributed DoS, Knowledge Disruptions, Computer Viruses / Worms, and many more. Cyber-attacks are still rising, and more are waiting to harm their targeted systems and networks. Detecting Intrusions in cybersecurity has become challenging due to their Intelligence Performance. Therefore, it may negatively affect data integrity, privacy, availability, and security.
This article aims to demonstrate the most current Cyber Security Topics for Projects and areas of research currently lacking. We will talk about cyber security research questions, cyber security research questions, cyber security topics for the project, best cyber security research topics, research titles about cyber security and web security research topics.
.jpg&w=3840&q=75)
List of Trending Cyber Security Research Topics for 2024
Digital technology has revolutionized how all businesses, large or small, work, and even governments manage their day-to-day activities, requiring organizations, corporations, and government agencies to utilize computerized systems. To protect data against online attacks or unauthorized access, cybersecurity is a priority. There are many Cyber Security Courses online where you can learn about these topics. With the rapid development of technology comes an equally rapid shift in Cyber Security Research Topics and cybersecurity trends, as data breaches, ransomware, and hacks become almost routine news items. In 2024, these will be the top cybersecurity trends.
A) Exciting Mobile Cyber Security Research Paper Topics
- The significance of continuous user authentication on mobile gadgets.
- The efficacy of different mobile security approaches.
- Detecting mobile phone hacking.
- Assessing the threat of using portable devices to access banking services.
- Cybersecurity and mobile applications.
- The vulnerabilities in wireless mobile data exchange.
- The rise of mobile malware.
- The evolution of Android malware.
- How to know you’ve been hacked on mobile.
- The impact of mobile gadgets on cybersecurity.
B) Top Computer and Software Security Topics to Research
- Learn algorithms for data encryption
- Concept of risk management security
- How to develop the best Internet security software
- What are Encrypting Viruses- How does it work?
- How does a Ransomware attack work?
- Scanning of malware on your PC
- Infiltrating a Mac OS X operating system
- What are the effects of RSA on network security ?
- How do encrypting viruses work?
- DDoS attacks on IoT devices
C) Trending Information Security Research Topics
- Why should people avoid sharing their details on Facebook?
- What is the importance of unified user profiles?
- Discuss Cookies and Privacy
- White hat and black hat hackers
- What are the most secure methods for ensuring data integrity?
- Talk about the implications of Wi-Fi hacking apps on mobile phones
- Analyze the data breaches in 2024
- Discuss digital piracy in 2024
- critical cyber-attack concepts
- Social engineering and its importance
D) Current Network Security Research Topics
- Data storage centralization
- Identify Malicious activity on a computer system.
- Firewall
- Importance of keeping updated Software
- wireless sensor network
- What are the effects of ad-hoc networks
- How can a company network be safe?
- What are Network segmentation and its applications?
- Discuss Data Loss Prevention systems
- Discuss various methods for establishing secure algorithms in a network.
- Talk about two-factor authentication
E) Best Data Security Research Topics
- Importance of backup and recovery
- Benefits of logging for applications
- Understand physical data security
- Importance of Cloud Security
- In computing, the relationship between privacy and data security
- Talk about data leaks in mobile apps
- Discuss the effects of a black hole on a network system.
F) Important Application Security Research Topics
- Detect Malicious Activity on Google Play Apps
- Dangers of XSS attacks on apps
- Discuss SQL injection attacks.
- Insecure Deserialization Effect
- Check Security protocols
G) Cybersecurity Law & Ethics Research Topics
- Strict cybersecurity laws in China
- Importance of the Cybersecurity Information Sharing Act.
- USA, UK, and other countries' cybersecurity laws
- Discuss The Pipeline Security Act in the United States
H) Recent Cyberbullying Topics
- Protecting your Online Identity and Reputation
- Online Safety
- Sexual Harassment and Sexual Bullying
- Dealing with Bullying
- Stress Center for Teens
I) Operational Security Topics
- Identify sensitive data
- Identify possible threats
- Analyze security threats and vulnerabilities
- Appraise the threat level and vulnerability risk
- Devise a plan to mitigate the threats
J) Cybercrime Topics for a Research Paper
- Crime Prevention.
- Criminal Specialization.
- Drug Courts.
- Criminal Courts.
- Criminal Justice Ethics.
- Capital Punishment.
- Community Corrections.
- Criminal Law.
Research Area in Cyber Security
The field of cyber security is extensive and constantly evolving. Its research covers a wide range of subjects, including:
- Quantum & Space
- Data Privacy
- Criminology & Law
- AI & IoT Security
How to Choose the Best Research Topics in Cyber Security
A good cybersecurity assignment heading is a skill that not everyone has, and unfortunately, not everyone has one. You might have your teacher provide you with the topics, or you might be asked to come up with your own. If you want more research topics, you can take references from Certified Ethical Hacker Certification, where you will get more hints on new topics. If you don't know where to start, here are some tips. Follow them to create compelling cybersecurity assignment topics.
1. Brainstorm
In order to select the most appropriate heading for your cybersecurity assignment, you first need to brainstorm ideas. What specific matter do you wish to explore? In this case, come up with relevant topics about the subject and select those relevant to your issue when you use our list of topics. You can also go to cyber security-oriented websites to get some ideas. Using any blog post on the internet can prove helpful if you intend to write a research paper on security threats in 2024. Creating a brainstorming list with all the keywords and cybersecurity concepts you wish to discuss is another great way to start. Once that's done, pick the topics you feel most comfortable handling. Keep in mind to stay away from common topics as much as possible.
2. Understanding the Background
In order to write a cybersecurity assignment, you need to identify two or three research paper topics. Obtain the necessary resources and review them to gain background information on your heading. This will also allow you to learn new terminologies that can be used in your title to enhance it.
3. Write a Single Topic
Make sure the subject of your cybersecurity research paper doesn't fall into either extreme. Make sure the title is neither too narrow nor too broad. Topics on either extreme will be challenging to research and write about.
4. Be Flexible
There is no rule to say that the title you choose is permanent. It is perfectly okay to change your research paper topic along the way. For example, if you find another topic on this list to better suit your research paper, consider swapping it out.
The Layout of Cybersecurity Research Guidance
It is undeniable that usability is one of cybersecurity's most important social issues today. Increasingly, security features have become standard components of our digital environment, which pervade our lives and require both novices and experts to use them. Supported by confidentiality, integrity, and availability concerns, security features have become essential components of our digital environment.
In order to make security features easily accessible to a wider population, these functions need to be highly usable. This is especially true in this context because poor usability typically translates into the inadequate application of cybersecurity tools and functionality, resulting in their limited effectiveness.
Writing Tips from Expert
Additionally, a well-planned action plan and a set of useful tools are essential for delving into Cyber Security Research Topics. Not only do these topics present a vast realm of knowledge and potential innovation, but they also have paramount importance in today's digital age. Addressing the challenges and nuances of these research areas will contribute significantly to the global cybersecurity landscape, ensuring safer digital environments for all. It's crucial to approach these topics with diligence and an open mind to uncover groundbreaking insights.
- Before you begin writing your research paper, make sure you understand the assignment.
- Your Research Paper Should Have an Engaging Topic
- Find reputable sources by doing a little research
- Precisely state your thesis on cybersecurity
- A rough outline should be developed
- Finish your paper by writing a draft
- Make sure that your bibliography is formatted correctly and cites your sources.
Discover the Power of ITIL 4 Foundation - Unleash the Potential of Your Business with this Cost-Effective Solution. Boost Efficiency, Streamline Processes, and Stay Ahead of the Competition. Learn More!
Studies in the literature have identified and recommended guidelines and recommendations for addressing security usability problems to provide highly usable security. The purpose of such papers is to consolidate existing design guidelines and define an initial core list that can be used for future reference in the field of Cyber Security Research Topics.
The researcher takes advantage of the opportunity to provide an up-to-date analysis of cybersecurity usability issues and evaluation techniques applied so far. As a result of this research paper, researchers and practitioners interested in cybersecurity systems who value human and social design elements are likely to find it useful. You can find KnowledgeHut’s Cyber Security courses online and take maximum advantage of them.
Frequently Asked Questions (FAQs)
Businesses and individuals are changing how they handle cybersecurity as technology changes rapidly - from cloud-based services to new IoT devices.
Ideally, you should have read many papers and know their structure, what information they contain, and so on if you want to write something of interest to others.
The field of cyber security is extensive and constantly evolving. Its research covers various subjects, including Quantum & Space, Data Privacy, Criminology & Law, and AI & IoT Security.
Inmates having the right to work, transportation of concealed weapons, rape and violence in prison, verdicts on plea agreements, rehab versus reform, and how reliable are eyewitnesses?

Mrinal Prakash
I am a B.Tech Student who blogs about various topics on cyber security and is specialized in web application security
Avail your free 1:1 mentorship session.
Something went wrong
Upcoming Cyber Security Batches & Dates
Research Topics & Ideas: Cybersecurity
50 Topic Ideas To Kickstart Your Research

If you’re just starting out exploring cybersecurity-related topics for your dissertation, thesis or research project, you’ve come to the right place. In this post, we’ll help kickstart your research by providing a hearty list of cybersecurity-related research topics and ideas , including examples from recent studies.
PS – This is just the start…
We know it’s exciting to run through a list of research topics, but please keep in mind that this list is just a starting point . These topic ideas provided here are intentionally broad and generic , so keep in mind that you will need to develop them further. Nevertheless, they should inspire some ideas for your project.
To develop a suitable research topic, you’ll need to identify a clear and convincing research gap , and a viable plan to fill that gap. If this sounds foreign to you, check out our free research topic webinar that explores how to find and refine a high-quality research topic, from scratch. Alternatively, consider our 1-on-1 coaching service .

Cybersecurity-Related Research Topics
- Developing machine learning algorithms for early detection of cybersecurity threats.
- The use of artificial intelligence in optimizing network traffic for telecommunication companies.
- Investigating the impact of quantum computing on existing encryption methods.
- The application of blockchain technology in securing Internet of Things (IoT) devices.
- Developing efficient data mining techniques for large-scale social media analytics.
- The role of virtual reality in enhancing online education platforms.
- Investigating the effectiveness of various algorithms in reducing energy consumption in data centers.
- The impact of edge computing on the performance of mobile applications in remote areas.
- The application of computer vision techniques in automated medical diagnostics.
- Developing natural language processing tools for sentiment analysis in customer service.
- The use of augmented reality for training in high-risk industries like oil and gas.
- Investigating the challenges of integrating AI into legacy enterprise systems.
- The role of IT in managing supply chain disruptions during global crises.
- Developing adaptive cybersecurity strategies for small and medium-sized enterprises.
- The impact of 5G technology on the development of smart city solutions.
- The application of machine learning in personalized e-commerce recommendations.
- Investigating the use of cloud computing in improving government service delivery.
- The role of IT in enhancing sustainability in the manufacturing sector.
- Developing advanced algorithms for autonomous vehicle navigation.
- The application of biometrics in enhancing banking security systems.
- Investigating the ethical implications of facial recognition technology.
- The role of data analytics in optimizing healthcare delivery systems.
- Developing IoT solutions for efficient energy management in smart homes.
- The impact of mobile computing on the evolution of e-health services.
- The application of IT in disaster response and management.
Cybersecurity Research Ideas (Continued)
- Assessing the security implications of quantum computing on modern encryption methods.
- The role of artificial intelligence in detecting and preventing phishing attacks.
- Blockchain technology in secure voting systems: opportunities and challenges.
- Cybersecurity strategies for protecting smart grids from targeted attacks.
- Developing a cyber incident response framework for small to medium-sized enterprises.
- The effectiveness of behavioural biometrics in preventing identity theft.
- Securing Internet of Things (IoT) devices in healthcare: risks and solutions.
- Analysis of cyber warfare tactics and their implications on national security.
- Exploring the ethical boundaries of offensive cybersecurity measures.
- Machine learning algorithms for predicting and mitigating DDoS attacks.
- Study of cryptocurrency-related cybercrimes: patterns and prevention strategies.
- Evaluating the impact of GDPR on data breach response strategies in the EU.
- Developing enhanced security protocols for mobile banking applications.
- An examination of cyber espionage tactics and countermeasures.
- The role of human error in cybersecurity breaches: a behavioural analysis.
- Investigating the use of deep fakes in cyber fraud: detection and prevention.
- Cloud computing security: managing risks in multi-tenant environments.
- Next-generation firewalls: evaluating performance and security features.
- The impact of 5G technology on cybersecurity strategies and policies.
- Secure coding practices: reducing vulnerabilities in software development.
- Assessing the role of cyber insurance in mitigating financial losses from cyber attacks.
- Implementing zero trust architecture in corporate networks: challenges and benefits.
- Ransomware attacks on critical infrastructure: case studies and defence strategies.
- Using big data analytics for proactive cyber threat intelligence.
- Evaluating the effectiveness of cybersecurity awareness training in organisations.
Recent Cybersecurity-Related Studies
While the ideas we’ve presented above are a decent starting point for finding a research topic, they are fairly generic and non-specific. So, it helps to look at actual studies in the cybersecurity space to see how this all comes together in practice.
Below, we’ve included a selection of recent studies to help refine your thinking. These are actual studies, so they can provide some useful insight as to what a research topic looks like in practice.
- Cyber Security Vulnerability Detection Using Natural Language Processing (Singh et al., 2022)
- Security for Cloud-Native Systems with an AI-Ops Engine (Ck et al., 2022)
- Overview of Cyber Security (Yadav, 2022)
- Exploring the Top Five Evolving Threats in Cybersecurity: An In-Depth Overview (Mijwil et al., 2023)
- Cyber Security: Strategy to Security Challenges A Review (Nistane & Sharma, 2022)
- A Review Paper on Cyber Security (K & Venkatesh, 2022)
- The Significance of Machine Learning and Deep Learning Techniques in Cybersecurity: A Comprehensive Review (Mijwil, 2023)
- Towards Artificial Intelligence-Based Cybersecurity: The Practices and ChatGPT Generated Ways to Combat Cybercrime (Mijwil et al., 2023)
- ESTABLISHING CYBERSECURITY AWARENESS OF TECHNICAL SECURITY MEASURES THROUGH A SERIOUS GAME (Harding et al., 2022)
- Efficiency Evaluation of Cyber Security Based on EBM-DEA Model (Nguyen et al., 2022)
- An Overview of the Present and Future of User Authentication (Al Kabir & Elmedany, 2022)
- Cybersecurity Enterprises Policies: A Comparative Study (Mishra et al., 2022)
- The Rise of Ransomware: A Review of Attacks, Detection Techniques, and Future Challenges (Kamil et al., 2022)
- On the scale of Cyberspace and Cybersecurity (Pathan, 2022)
- Analysis of techniques and attacking pattern in cyber security approach (Sharma et al., 2022)
- Impact of Artificial Intelligence on Information Security in Business (Alawadhi et al., 2022)
- Deployment of Artificial Intelligence with Bootstrapped Meta-Learning in Cyber Security (Sasikala & Sharma, 2022)
- Optimization of Secure Coding Practices in SDLC as Part of Cybersecurity Framework (Jakimoski et al., 2022)
- CySSS ’22: 1st International Workshop on Cybersecurity and Social Sciences (Chan-Tin & Kennison, 2022)
As you can see, these research topics are a lot more focused than the generic topic ideas we presented earlier. So, for you to develop a high-quality research topic, you’ll need to get specific and laser-focused on a specific context with specific variables of interest. In the video below, we explore some other important things you’ll need to consider when crafting your research topic.
Get 1-On-1 Help
If you’re still unsure about how to find a quality research topic, check out our Research Topic Kickstarter service, which is the perfect starting point for developing a unique, well-justified research topic.

You Might Also Like:

Submit a Comment Cancel reply
Your email address will not be published. Required fields are marked *
Save my name, email, and website in this browser for the next time I comment.
- Print Friendly
List of 78 Top Cyber Security Topics for Research
Table of contents
- 1 How To Choose The Best Cyber Security Research Topics
- 2 📚10 Cyber Security Topics For Research Paper
- 3 📱Mobile Cyber Security Research Paper Topics
- 4 🕵Top 10 Cyber Security Topics
- 5 👨💻Cyber Security Research Topics 2023
- 6 🔎Best Cyber Security Research Topics
- 7 👨🔬Cyber Security Future Research Topics
- 8 📑Cyber Security Topics For Research Paper
- 9 👩💻Cyber Security Topics on Computer and Software
There are many reasons to choose cyber security research topics for writing purposes. First, cyber security is a growing field, with many new and exciting developments happening all the time. This makes it an ideal topic to write about, as there is always something new to learn and discuss. Second, cyber security research can be used to improve the security of your own computer systems. By understanding the latest threats and vulnerabilities, you can make your systems more secure and less likely to be compromised. Third, writing about cyber security can help raise awareness about the importance of cyber security. By educating others about the dangers of cyber attacks and the importance of protecting their computers, you can help make the internet a safer place for everyone.
How To Choose The Best Cyber Security Research Topics
When it comes to choosing research paper topics on cyber security, there are a few things to consider. First, it is important to make sure that the topic is relevant and timely. Cyber security is an ever-changing field, so it is important to choose a topic that will be relevant for years to come. Second, it is important to choose a topic that is interesting and engaging. Cybersecurity can be a dry topic, so it is important to choose a topic that will keep readers engaged. Finally, it is important to choose a topic that is researchable. There are a lot of cyber security topics out there, but not all of them are easy to research. Make sure to choose a topic that has plenty of information available.
- Identify your audience.
- Define your research goals.
- Choose a topic that is both interesting and relevant to your audience.
- Do some preliminary research to make sure there is enough information available on your chosen topic.
- Make sure your topic is narrow enough to be covered in a single research paper.
📚10 Cyber Security Topics For Research Paper
- The Importance of Cyber Security
- The Evolution of Cyber Security
- The Future of Cyber Security
- The Impact of Cyber Security on Business
- The Role of Cyber Security in National Security
- The Challenges of Cyber Security
- The Costs of Cyber Security
- The Benefits of Cyber Security
- The Risks of Cyber Security
- The Implications of Cyber Security
📱Mobile Cyber Security Research Paper Topics
- Mobile device security: How to protect your mobile device from cyber attacks.
- The rise of mobile malware: How to protect your device from malicious software.
- Mobile phishing attacks: How to protect your device from being scammed.
- The dangers of public Wi-Fi: How to protect your device from being hacked.
- How to keep your data safe on your mobile device: Tips for keeping your personal information secure.
🕵Top 10 Cyber Security Topics
- Cybersecurity threats and attacks
- Cybersecurity risks and vulnerabilities
- Cybersecurity best practices
- Cybersecurity awareness and training
- Cybersecurity tools and technologies
- Cybersecurity policy and compliance
- Cybersecurity incident response
- Cybersecurity governance
- Cybersecurity risk management
- Cybersecurity strategy
👨💻Cyber Security Research Topics 2023
- The future of cyber security: what trends will shape the field in the coming years?
- The impact of AI and machine learning on cyber security
- The role of quantum computing in cyber security
- The challenges of securing the IoT
- The evolving threat landscape: what new threats are emerging and how can we defend against them?
- The role of data in cyber security: how can we better protect our data?
- The importance of user education in cyber security
- The challenges of securing mobile devices
- The future of cyber warfare: what trends are emerging?
- The role of cryptography in cyber security
🔎Best Cyber Security Research Topics
- The Impact of Cybersecurity on Businesses and Consumers
- The Evolution of Cybersecurity Threats and Attacks
- The Role of Cybersecurity in National Security
- The Economics of Cybersecurity
- The Psychology of Cybersecurity
- The Sociology of Cybersecurity
- The Ethics of Cybersecurity
- The History of Cybersecurity
- Cybersecurity threats and attacks.
- Cybersecurity policies and procedures.
- Cybersecurity awareness and training.
- Cybersecurity technologies and solutions.
- Cybersecurity risk management.
- Cybersecurity incident response.
- Cybersecurity governance.
- Cybersecurity compliance.
- Cybersecurity standards.
- Cybersecurity best practices.
👨🔬Cyber Security Future Research Topics
- Developing more effective methods for detecting and responding to cyber attacks
- Investigating the role of social media in cyber security
- Examining the impact of cloud computing on cyber security
- Investigating the security implications of the Internet of Things
- Studying the effectiveness of current cyber security measures
- Identifying new cyber security threats and vulnerabilities
- Developing more effective cyber security policies
- Examining the ethical implications of cyber security
📑Cyber Security Topics For Research Paper
- Cyber security threats and vulnerabilities.
- Cyber security incident response and management.
- Cyber security risk management.
- Cyber security awareness and training.
- Cyber security controls and countermeasures.
- Cyber security governance.
- Cyber security standards.
- Cyber security insurance.
- Cyber security and the law.
- The future of cyber security.
👩💻Cyber Security Topics on Computer and Software
- Cyber security risks associated with computer software
- The importance of keeping computer software up to date
- How to protect your computer from malware and other threats
- The best practices for securing your computer and software
- The different types of cyber security threats and how to avoid them
- The importance of cyber security awareness and education
- The role of cyber security in protecting critical infrastructure
Readers also enjoyed

WHY WAIT? PLACE AN ORDER RIGHT NOW!
Just fill out the form, press the button, and have no worries!
We use cookies to give you the best experience possible. By continuing we’ll assume you board with our cookie policy.
Top 111+ Stunning Cybersecurity Research Topics For 2023

Are you confused about cybersecurity and its research topics? So here, in this blog, we will discuss cybersecurity research topics. This article is important If you are studying computer science or a cybersecurity course.
If you want good grades in cybersecurity research topics, you should pick the latest cybersecurity research topics for your academic exam or test. Here, you can choose the good and latest cybersecurity research topics.
You know that cybercrime is increasing day by day because millions of people use the internet. Several applications deal with the internet, and people normally use the internet for bank transactions, food delivery, online shopping, social media, gaming, etc. Attackers can steal your information, data, and money with the help of malicious software, So we need cybersecurity services.
What is Cybersecurity?
Table of Contents
Cybersecurity is a process of preventing unauthorized access or protecting networks, devices, and data from digital attacks. Cybersecurity is also known as IT(Information Technology)Security which is designed to prevent threats against network systems, applications, and other platforms. In simple words, It prevents or protects any information, data, and others.
Here Are Some of the Best Writing Tips From Statanalytica’s Expert
As you might already know that a well-planned action and a set of useful tools will also help you write a high-quality research paper. On the other hand, remaining motivated throughout the process.
- By choosing an interesting topic for your research paper.
- Conduct some research to find reputable sources.
- Clearly state your cybersecurity thesis.
- A rough plan should be created.
- Finish your paper by drafting it.
- Make sure your content is properly formatted.
- Make sure you understand the assignment before you begin writing your research paper.
Let’s Discuss the 111+ Stunning Cybersecurity Research Topics
Below we listed 111+ cybersecurity research topics that can be used in 2023:
Top 10 Cyber Security Topics of 2023
Here are the top 10 cyber security topics of 2023:
- Can strong passwords protect information?
- Is security in critical infrastructure important?
- The importance of end-user education
- Cloud security posture management
- How does malware work?
- The principle of zero trust access
- 3 phases of application security
- Should removable media be encrypted?
- The importance of network security
- Do biometrics ensure the security of iPhones?
Latest Cybersecurity Research Topics of 2023
- Is removable media a threat?
- Cybersecurity standards for automotive
- How to prevent social engineering attacks
- Security breaches of remote working
- How to prevent phishing attacks
- Physical security measures in banks
- Privacy settings of social media accounts
- Blockchain security vulnerabilities
- Why should you avoid public Wi-Fi?
- How does two-factor authentication work?
- Cryptography
- Discuss the importance of intranet security
- Rise of Automotive Hacking
- What is ethical hacking?
- The evolution of phishing and how it is becoming more sophisticated
- Which antivirus software is the best in the world?
- The most up-to-date and trending cybersecurity technology
- How can organizations prevent network attacks?
- What is Digital Piracy?
- Application of biometrics in cyber security?
- Identity theft on the Internet
- Risk management in computing
- Rise of computer forensics
- Threats are analyzed using digital forensic techniques
- What is a Remote Access VPN?
- Digital security and Social Networks
- The risks of using public Wi-Fi networks
- Popular online scams in 2022
- Artificial intelligence security systems
Network Security Research Topics
- Data storage centralization
- Identify Malicious activity on a computer system.
- Importance of keeping updated Software
- wireless sensor network
- What are the effects of ad-hoc networks
- How can a company network be safe?
- What are Network segmentation and its applications?
- Discuss Data Loss Prevention systems
- Discuss various methods for establishing secure algorithms in a network.
- Talk about two-factor authentication
Topics for Application Security Research
- Discuss SQL injection attacks.
- Inadequately configured security protocols.
- Talk about data leaks in mobile apps.
- Backend access control is critical.
- Logging has many advantages for applications.
- Malicious apps are available on Google Play.
- AI applications: ethical constraints and opportunities.
- What is the effect of insecure deserialization?
- The most effective application security testing practices.
- Apps are vulnerable to XSS attacks.
Information Technology Security Research Topics
- Why should people avoid sharing their details on Facebook?
- What is the importance of unified user profiles?
- Discuss Cookies and Privacy
- White hat and black hat hackers
- What are the most secure methods for ensuring data integrity?
- Talk about the implications of Wi-Fi hacking apps on mobile phones
- Analyze the data breaches in 2022
- Discuss digital piracy in 2022
- critical cyber-attack concepts
- Social engineering and its importance
Operational Security Research Topics In 2023
- Securing containerized applications in cloud environments.
- Implementing secure remote access policies for remote workers.
- Evaluating the effectiveness of endpoint protection solutions.
- Protecting against DNS tunneling attacks.
- Securing cloud-based storage solutions.
- Developing secure mobile device management policies.
- Analyzing the effectiveness of honeypots in detecting attacks.
- Securing software supply chains against attacks.
- Investigating the effectiveness of deception technologies in cybersecurity.
- Developing secure network segmentation strategies.
- Evaluating the effectiveness of network traffic analysis solutions.
- Analyzing the effectiveness of two-factor authentication in securing systems.
- Securing critical infrastructure against cyber threats.
- Developing secure email policies to prevent phishing attacks.
- Investigating the use of artificial intelligence in cybersecurity.
- Developing secure DevOps practices.
- Analyzing the effectiveness of security information and event management (SIEM) solutions.
- Securing the Internet of Things (IoT) devices.
- Evaluating the effectiveness of password management solutions.
- Developing secure incident response strategies.
Topics for a Research Paper on CyberCrime Prevention
- Criminal Specialization.
- Drug Courts.
- Capital Punishment.
- Criminal Courts.
- Crime Prevention.
- Community Corrections.
- Criminal Law.
- Criminal Justice Ethics.
Computer and Software Security Research Topics
- Learn algorithms for data encryption.
- Concept of risk management security.
- How to develop the best internet security software.
- What are Encrypting viruses- How does it work?
- How does a Ransomware attack work?
- Scanning of malware on your PC.
- Infiltrating a Mac OS X operating system.
- What are the effects of RSA on network security?
- How do encrypting viruses work?
- DDoS attacks on IoT devices.
Computer and Software Cyber Security Topics
- The importance of updating computer software.
- How to safeguard your computer against malware and other threats.
- The best security practices for your computer and software.
- The various types of cyber security threats and how to avoid them.
- The significance of cyber security education and awareness.
- The importance of cyber security in protecting critical infrastructure.
Data Security Research Topics
- Importance of backup and recovery.
- Benefits of logging for applications.
- Understand physical data security.
- Importance of Cloud Security.
- In computing, the relationship between privacy and data security.
- Discuss the effects of a black hole on a network system.
Application Security Topics
- Detect Malicious Activity on Google Play Apps.
- Dangers of XSS attacks on apps.
- Insecure Deserialization Effect.
- Check Security protocols.
CyberSecurity Law Research Paper Topics
- Strict cybersecurity laws in China.
- Importance of the Cybersecurity Information Sharing Act.
- USA, UK, and other countries cybersecurity laws.
- Discuss The Pipeline Security Act in the United States.
If you are interested in criminal research topics, then here are the best criminal justice research topics for you.
How to Choose The Best Cybersecurity Research Topics in 2023
There are a few factors to consider when selecting cybersecurity research topics. The first and main thing to consider is to ensure that the topic is current and relevant. Because cyber security is a changing field. As a result, it is very crucial to select a topic that will be relevant for a few months.
On the other hand, the second thing to consider is to select an interesting and engaging topic. Because cyber security can be a dry subject, it is critical to select a topic that will keep readers interested.
Finally, it is very important to select a researchable topic. There are several cybersecurity topics available, but not all of them are simple to research. Choose a topic about which there is a lot of information.
- Determine your target audience
- Define your research objectives
- Choose a topic that your audience will find both interesting and relevant
- Conduct preliminary research to ensure that there is sufficient information available on your chosen topic
- Make sure your topic is focused enough to fit into a single research paper
Research Area in Cyber Security
Cybersecurity is extensive, and constantly evolving field. On the other hand, its research takes place in many areas:

- Quantum & Space
- Data Privacy
- Criminology & Law
- AI & IoT Security
Get More Cybersecurity Research Topics
In this blog, we have covered the 111+ best cybersecurity research topics. These cybersecurity topics help in your exam or test. If you have any difficulty with cybersecurity research topics, you can take cybersecurity research paper help or research paper assignment help at a very affordable price.
Here are some of the benefits of taking cybersecurity research topics help from us.
- 24 Hours Availability
- On-time Delivery
- Free Corrections
- Money-Back Guarantee
- Affordable Deals
- Professional Experts
You can contact us any time and impress your teacher by choosing a good cybersecurity research topic.
This is the end of the post, which is about cybersecurity research topics. On the other hand, we mentioned 111+ stunning cybersecurity research topics for 2023 offer an excellent opportunity for researchers to explore and address critical cybersecurity challenges. However, the ever-evolving technological landscape presents new security challenges every day, and it is essential to keep up with the latest trends to stay ahead of cyber threats.
On the other hand, these research topics provide many areas to explore, from network security, the internet of things, and software security to network security, cryptography, and data security. I hope you like this post.
Q1. What are the types of cyber security threats?
There are several different types of cyber security threats. More popular are Trojan horses, worms, ransomware, and phishing scams. These types of threats can be very dangerous for the cyber system.
Q2. What are the most controversial topics in criminal justice?
1. Prisoners being granted the right to work 2. Carrying a concealed weapon 3. Prison rape and violence 4. Plea agreement/bargain 5. Rehab vs. reform. 6. Is an eyewitness testimony effective? 7. Enforcement and effectiveness of stalking laws. 8. Rape culture and the victim’s rights
Q3. What are the main cyber threats of 2023?
There are multiple cyber security threats, but the main social threats of 2023 are email impersonation and phishing. On the other hand, email impersonation is a phishing technique in which a fake email address that appears to be legitimate is used.
Related Posts

Step by Step Guide on The Best Way to Finance Car

The Best Way on How to Get Fund For Business to Grow it Efficiently
- How It Works
- PhD thesis writing
- Master thesis writing
- Bachelor thesis writing
- Dissertation writing service
- Dissertation abstract writing
- Thesis proposal writing
- Thesis editing service
- Thesis proofreading service
- Thesis formatting service
- Coursework writing service
- Research paper writing service
- Architecture thesis writing
- Computer science thesis writing
- Engineering thesis writing
- History thesis writing
- MBA thesis writing
- Nursing dissertation writing
- Psychology dissertation writing
- Sociology thesis writing
- Statistics dissertation writing
- Buy dissertation online
- Write my dissertation
- Cheap thesis
- Cheap dissertation
- Custom dissertation
- Dissertation help
- Pay for thesis
- Pay for dissertation
- Senior thesis
- Write my thesis
128 High Quality Cybersecurity Research Topics Ideas List

The internet is a global village full of different people. Some people have malicious motives. Once they stumble upon your sensitive data, they will use it to harass you. This also occurs in social media accounts. You may post something and then get some bad or hurtful comments.
That’s a form of cyberbullying that is not acceptable. Therefore, you need to be careful when dealing with people on the internet. Also, try to reduce the data that you expose on your different user profiles. A person may even steal your online identity in a blink of an eye.
Case Situations To Write Cybersecurity Research Paper
Thereby cybersecurity comes in with the motive of defending computers, servers, mobiles, electronic systems, networks, and much more from those malicious attacks. You may need to write a cybersecurity research paper for:
Your final paper, project, thesis, or dissertation. When you are proposing a new strategy to use in your company to prevent cyber-attacks. When you want to bring into light some vulnerabilities being ignored. When you want to do more research and get a better understanding of harassment on the internet.
How To Write Cybersecurity Research Paper
This is the procedure you can use when writing a research paper.
Consult your professor – You will first need to get insights from your professor or teacher on the best way to go about it. You can provide a list of topics you may want to write on for his approval. Brainstorm – Discuss with some like-minded people the best cybersecurity topics to try. You need to be careful to ensure that you choose a topic that you can easily do. Research – Once you settle on a good topic, you can start your research on books, scholarly articles, documentaries, and films to get legit information on your cybersecurity research topic. Jot them down as a draft. Start your paper – Once you are settled with the research, you can use your draft to write a viable research paper. Ensure you follow the right procedure. Proofread the work – Once you are satisfied with your work, consider proofreading it before submitting it.
If you don’t feel like writing research paper yourself, you can get cheap dissertation help from our experts.
Cybersecurity Research Topics
When in high school or college, you need to strive to get good grades. You can use any of these cybersecurity research topics for your paper. Just ensure to do enough research on the concepts.
- The significance of a firewall in the protection of the network.
- Discuss the process of authentication.
- The loss and restoration of data.
- The best data encryption algorithms.
- The best methods to protect your network.
- Evaluate digital piracy and security.
- The significance of social engineering.
- The significance of software updates in devices.
- The major causes of cybersecurity.
- The safety of biometrics.
- The worst cases of IoT hacking.
Cybersecurity Research Paper Topics
Cybersecurity is wide and inexhaustible. Each day, cybercrime are occurring, leading to research on better ways to protect ourselves online. You can use any of these topics for your research paper or project.
- The advantages and disadvantages of unified user profiles.
- The relation between bots and cybersecurity.
- The major cybersecurity vulnerabilities.
- Evaluate digital piracy and its effects on creativity.
- How has automotive hacking grown over the years?
- Evaluate ethical hacking.
- Evolution of phishing over time.
- The best antivirus software currently being used.
- The trends in cybersecurity technology.
- How biometrics is helping in cybersecurity?
- The occurrence of cybersecurity in spoofing.
Cybersecurity Research Topics For Research Papers
Are you in the IT profession? Have you done your project yet? Then you can consider using any of these cybersecurity research topics. They are all ideal and based on current matters.
- The rise of identity theft on the internet.
- Why are more people getting into computer forensics?
- The major threats found using digital forensic techniques.
- The best VPNs in the world that will hide your IP on the internet.
- The disadvantages of exposure of your IP address to the public.
- The major A.I. security systems.
- The centralization of data storage.
- How to identify malicious activity on your devices.
- The safety of a network.
- The applications of network segmentation.
- The major challenges in IT risk management.
PhD Research Topics In Cybersecurity
Are you currently doing your Ph.D.? You can use any of these cybersecurity topics for your paper. They are all based on current matters. There are available resources that you can use to get data.
- The best approach for connected autonomous vehicles.
- The best methods for cognitive cybersecurity.
- The most innovative methods being used to determine the viability of deep learning based on the cybersecurity log analytics system.
- The significance of not sharing sensitive data on social media networks.
- Evaluate cookies on privacy.
- The different types of hackers.
- The disadvantages of Wi-Fi hacking apps on mobile phones.
- The major cyber-attack concepts.
- The best way to develop credible internet security software.
- How to scan malware on your pc.
- Evaluate twitter’s access control policy.
Research Topics In Cybersecurity
You can use any of these research topics in cybersecurity for your papers. You can derive data from some other scholarly articles, documentaries, films, and books. Information about cybersecurity gets updated daily.
- The attack of ransomware.
- The effects of RSA on any network’s security.
- The significance of cloud security.
- How do data leaks occur on mobile apps?
- The effects of a black hole on a network system.
- The significance of applications logging.
- How to detect malicious activities on Google Play apps.
- The best way to check security protocols.
- How does network security deal with cybercrime?
- The network security monitoring process.
- The dangers and flaws of the internet.
Best Research Topics In Cybersecurity
How confident are you about your knowledge of cybersecurity? Then you can consider using any of these topics to test your knowledge capacity. Give it your best to get top grades.
- Initiatives that can be taken to check the growth of cyber hackers.
- The difference between white and black hat hackers.
- How does network intrusion occur and its prevention?
- The authentication processes.
- The most common vulnerabilities.
- The different types of cybercrime.
- The major pandemics caused by cyber viruses.
- The significance of software updates and patches.
- The common laws against cybercrime in the world.
- The best way to suppress the ransomware attack rate.
- The significance of a keylogger.
Hot Topics Cybersecurity Research
These are some of the hottest topics in cybersecurity. You just need to find an ideal topic, do research, jot down the points, and start your research paper.
- The best way to ensure you are safe when downloading files on the internet.
- The best device synchronization and protection methods.
- How can you detect bots on the internet?
- The relation between internet cookies with cybersecurity.
- How are IOS-based apps less prone to ransomware attacks?
- Is it possible for computer hardware to face a cyber-attack?
- The algorithms of data encryption.
- The significance of investing in a strong anti-malware.
- How do encrypting viruses work?
- How do the reverse engineering and vulnerabilities analysis work?
Great Topics For Cybersecurity Research Papers
There are a lot of vulnerabilities on the internet. These great topics for cybersecurity can make you more knowledgeable about the current trends.
- Risk management in computing.
- The most common causes of a data breach in the 21 st
- The best way to protect your device and synchronize the data.
- The significance of computer forensics in the current digital era.
- The major implications of ethical hacking.
- The motivations behind cybercrimes like identity theft.
- The major components of IT and data governance.
- The most secure user authentication methods.
- The threats of digital piracy.
- The significance of device synchronization.
Cybersecurity And Law Research Topics
Did you know that certain laws govern cybersecurity? Then you can use these cybersecurity and law research topics to get a deeper understanding.
- Data and cybersecurity in IoT.
- The correlation between big data analysis with IoT.
- Evaluate Software Defined Network.
- The best tools for excellent email security.
- How to prevent cybercrimes.
- How do phishing scams occur?
- The significance of using strong passwords.
- The worst data breaches of all time.
- How do malicious people use other people’s identities to their benefit?
- How to remove malware from a computer.
Research Topics On Cybersecurity
There are different internet vulnerabilities in the world. Thereby, you can use these research topics on cybersecurity to understand how your security can be compromised on the internet.
- Evaluate botnets in the current world.
- Evaluate a brute force attack.
- The risks of connecting your device to a public wireless network.
- How to secure removable media.
- The occurrence of credit card fraud.
- The most recent cloud security threats.
- The significance of implementing multifactor authentication.
- How is online slandering a cybercrime?
- Email sender spoofing process.
- Stress is caused by periodic cyberbullying.
Cybersecurity Research Topic
Have you ever faced any cyber-attack? How was the experience? These are great topics that can help you become more knowledgeable.
- How to protect yourself from cyberbullying.
- The best security measures to input on Windows, macOS, and Linux.
- How dangerous is cyberstalking?
- Can cyber harassment be termed a crime?
- The major dangers of public Wi-Fi networks.
- Is it possible to identify a phishing attack?
- The best mobile protection methods on your smartphone.
- Malware and how it occurs.
- The best practices to secure your Home Wi-Fi.
- The advantages and disadvantages of antivirus software.
Topic On Cybersecurity
As a student, you need to up your game, to ensure you provide custom work that your teacher or professor will be happy about. Just try any of these topics on cybersecurity.
- The endpoint attacks on devices.
- The dangers posed by tracking cookies.
- The role of backups on your device’s data.
- Evaluate security patches.
- Is it important to read the software terms and conditions?
- Are there any malicious apps on the Google Play Store and Apple Store?
- Evaluate SQL injection attacks.
- The best way to keep your personal information safe.
- The vulnerabilities found in multifactor authentication.
- How to protect your computer.
- How to authenticate on your devices.
Paper Writing Assistance In Cybersecurity Research Paper
Are you busy and wondering how you will do your research paper, project, or thesis? Look no further, you can pay for dissertation and be sure to get perfect result. You just need to order by choosing a topic of your preference and buy it at a cheap price.
You don’t have to worry about not meeting the deadline. With us, you will be sorted. All the best in your research paper.

Leave a Reply Cancel reply
Your email address will not be published. Required fields are marked *
Comment * Error message
Name * Error message
Email * Error message
Save my name, email, and website in this browser for the next time I comment.
As Putin continues killing civilians, bombing kindergartens, and threatening WWIII, Ukraine fights for the world's peaceful future.
Ukraine Live Updates
Burp Scanner
Burp Suite's web vulnerability scanner

Product comparison
What's the difference between Pro and Enterprise Edition?

Download the latest version of Burp Suite.

How I choose a security research topic

James Kettle
Director of Research
Published: 14 June 2023 at 13:09 UTC
Updated: 14 June 2023 at 13:16 UTC

How do you choose what topic to research? That’s the single most common question I get asked, probably because selecting a topic is such a daunting prospect. In this post, I’ll take a personal look at how I select topics for security research. As a case study, I’ll use my latest research, which will be presented at Black Hat USA and DEF CON this August:
Smashing the State Machine: the True Potential of Web Race Conditions
The hardest part
Before we start, I should mention that I firmly believe that choosing a topic is not the hardest part of web security research.
I’ve spoken to so many people who have cool ideas but never attempt to execute them. On the rare occasion that someone does mention a research idea that I think is doomed from the outset, it’s clear that attempting it will still provide them with a major learning experience - hardly a terrible outcome.
In fact, I don’t think that coming up with research ideas is the hard part either. Once you start researching, you’ll likely find every topic you explore leaves you with ideas for three more projects.
I think the hardest part of research is knowing when to bail, and when to push on.

Fast failure
My primary criteria when I evaluate a topic is how much time I’ll need to invest before I have enough information to decide whether to abandon it or continue. Knowing when to abandon a topic and when to push on is an extremely valuable skill for research, and it’s worth putting thought into this before starting.
This year, the attack-concept I wanted to explore initially looked like it required a major up-front time investment. However, I identified a short-cut - if I could build a test website that was vulnerable and reasonably realistic, that would prove the concept was pursuing. I built the website, quickly discovered that the attack concept was extremely unrealistic, and quickly pivoted to a different concept.
The second concept showed just enough promise to make me waste six weeks on it before it flopped too. When looking for a third concept, race conditions was an attractive topic because I already had powerful tooling from the prior project. This meant it would only take about a day to adapt the tooling, and a week or two of manual testing to see if I could discover something significant in the wild. I found a novel high-impact vulnerability in under a week, which cemented my commitment to the topic.
The fear factor
I like to research topics I’m scared of. Fear is a great indicator of something I don’t fully understand, and challenges that I don’t know how to tackle. Race conditions provided this in buckets, and I place this up-front and center in my abstract:
For too long, web race-condition attacks have focused on a tiny handful of scenarios. Their true potential has been masked thanks to tricky workflows, missing tooling, and simple network jitter hiding all but the most trivial, obvious examples. In this session, I’ll introduce multiple new classes of race condition that go far beyond the limit-overrun exploits you’re probably already familiar with... [read full abstract]
Direct impact vs audience impact
As a security professional, it’s tempting to rate a research project’s impact based on the direct impact. For example, over the years I’ve seen a range of serious flaws in a certain popular CDN, and I suspect that if I directly targeted it, I could find multiple ways to take over all their customers’ websites - a reasonable chunk of the web. In terms of direct impact, this would be pretty good.
But when you submit to Black Hat, they ask you to specify ‘three actionable take-aways’ for the audience. How would my hypothetical CDN-popping talk answer this? The only action required would be from that sole CDN vendor - in effect I’d just be giving a war-story talk. These can be entertaining and inspiring, but that’s not what I’m aiming for.
I try to pick a topic where the audience will take away novel attack techniques, and any tools or methodology required to make them practical to apply.
Applicable audience
Over the last five years, my research has been focused on HTTP Request Smuggling and Web Cache Poisoning . Since I’m well-versed in this topic, doing further research directly on top has become relatively easy, and I’m perpetually aware of multiple promising ideas.
However, while creating the presentation for last year’s Browser-Powered Desync Attacks , I became acutely aware that it demanded an exceptional amount of prior technical knowledge from the audience.
Building on a little recent research often works well because you can summarise it yourself. However, building on a large volume of recent research means that anyone in the audience who isn’t already familiar is going to struggle, and overall less people will get the benefit.
This year, by focusing on race conditions - a topic with minimal recent developments - I’ve been able to start building on a foundation that most attendees will be familiar with. Relative to last year’s talk, you can expect this talk to have both greater potential for the experts, and greater accessibility for the masses.
Existing skill-sets vs personal development
There’s a second, more personal reason why I changed my research focus away from request smuggling. I expect request smuggling to keep yielding good research for years to come, but just like any topic, at some point it’ll dry up. If I maintain my exclusive focus on this topic, there’s a risk I’ll become over-specialised and end up in a bad place when the topic stops yielding fruit.
I deliberately choose race conditions to avoid this over-specialisation risk, even though I regarded it as a much riskier bet than doing even more request smuggling exploration. Personal development is a huge and easily overlooked part of research. I rarely repeat my presentations across months for the same reason - if you spend your time sharing the same presentation over and over, you’re sacrificing novel research time.
That said, there’s a balance to be had here - if you have specialist knowledge, that will give you an edge on certain topics. Race conditions appealed from the start because I’d observed low-level HTTP quirks that could enhance these attacks, and I’d also observed them in the wild when trying to exploit response queue poisoning.
No topic is perfect; this presentation has fewer case studies than usual for me because fully automated detection of these vulnerabilities is not practical. On the plus side, this leaves a large number of vulnerabilities on the table that the audience can find simply by applying the methodology.
Ultimately, I see over-thinking topic choice as a pitfall. Save your energy for the research itself - you’ll need it! If you found this useful, you might also like So you want to be a web security researcher , and the presentation Hunting Evasive Vulnerabilities .
If you’re got any thoughts or queries, feel free to ping me on Twitter or LinkedIn . Hopefully I’ll see some of you in-person at the presentation too!
Back to all articles
Related Research
Making desync attacks easy with trace, using form hijacking to bypass csp, hiding payloads in java source code strings.
This is a potential security issue, you are being redirected to https://csrc.nist.gov .
You have JavaScript disabled. This site requires JavaScript to be enabled for complete site functionality.
An official website of the United States government
Here’s how you know
Official websites use .gov A .gov website belongs to an official government organization in the United States.
Secure .gov websites use HTTPS A lock ( Lock Locked padlock icon ) or https:// means you’ve safely connected to the .gov website. Share sensitive information only on official, secure websites.
- Drafts for Public Comment
- All Public Drafts
- NIST Special Publications (SPs)
- NIST interagency/internal reports (NISTIRs)
- ITL Bulletins
- White Papers
- Journal Articles
- Conference Papers
- Security & Privacy
Applications
Technologies.
- Laws & Regulations
- Activities & Products
- News & Updates
- Cryptographic Technology
- Secure Systems and Applications
- Security Components and Mechanisms
- Security Engineering and Risk Management
- Security Testing, Validation, and Measurement
- Cybersecurity and Privacy Applications
- National Cybersecurity Center of Excellence (NCCoE)
- National Initiative for Cybersecurity Education (NICE)
Security and Privacy
- digital signatures
- key management
- lightweight cryptography
- message authentication
- post-quantum cryptography
- random number generation
- secure hashing
- cybersecurity supply chain risk management
- general security & privacy
- access authorization
- access control
- Personal Identity Verification
- public key infrastructure
- personally identifiable information
- privacy engineering
- categorization
- continuous monitoring
- controls assessment
- privacy controls
- security controls
- risk assessment
- roots of trust
- system authorization
- advanced persistent threats
- information sharing
- intrusion detection & prevention
- vulnerability management
- accessibility
- testing & validation
- acquisition
- asset management
- audit & accountability
- awareness training & education
- configuration management
- contingency planning
- incident response
- maintenance
- media protection
- patch management
- personnel security
- physical & environmental protection
- program management
- security automation
- reliability
- artificial intelligence
- cloud & virtualization
- combinatorial testing
- personal computers
- quantum information science
- smart cards
- operating systems
- communications & wireless
- cyber-physical systems
- cybersecurity education
- cybersecurity framework
- cybersecurity workforce
- industrial control systems
- Internet of Things
- mathematics
- positioning navigation & timing
- small & medium business
Laws and Regulations
- Comprehensive National Cybersecurity Initiative
- Cybersecurity Strategy and Implementation Plan
- Cyberspace Policy Review
- Executive Order 13636
- Executive Order 13702
- Executive Order 13718
- Executive Order 13800
- Executive Order 13905
- Executive Order 14028
- Executive Order 14110
- Federal Cybersecurity Research and Development Strategic Plan
- Homeland Security Presidential Directive 7
- Homeland Security Presidential Directive 12
- OMB Circular A-11
- OMB Circular A-130
- Cyber Security R&D Act
- Cybersecurity Enhancement Act
- E-Government Act
- Energy Independence and Security Act
- Federal Information Security Modernization Act
- First Responder Network Authority
- Health Insurance Portability and Accountability Act
- Help America Vote Act
- Internet of Things Cybersecurity Improvement Act
- Federal Acquisition Regulation
Activities and Products
- annual reports
- conferences & workshops
- quick start guides
- reference materials
- standards development
- financial services
- hospitality
- manufacturing
- public safety
- telecommunications
- transportation
- Write my thesis
- Thesis writers
- Buy thesis papers
- Bachelor thesis
- Master's thesis
- Thesis editing services
- Thesis proofreading services
- Buy a thesis online
- Write my dissertation
- Dissertation proposal help
- Pay for dissertation
- Custom dissertation
- Dissertation help online
- Buy dissertation online
- Cheap dissertation
- Dissertation editing services
- Write my research paper
- Buy research paper online
- Pay for research paper
- Research paper help
- Order research paper
- Custom research paper
- Cheap research paper
- Research papers for sale
- Thesis subjects
- How It Works
50 Great Cybersecurity Research Paper Topics

Students are required to write papers and essays on cyber security topics when pursuing programs in cyber security disciplines. These topics are technical and they require learners to inherently understand this subject. What’s more, students should have impeccable research and writing skills.
Additionally, students should choose cyber security topics to write their papers and essays carefully. As a science field, cyber security is developing rapidly and constantly. As such, learners can always find interesting topics to write papers and essays about.
Pick Cyber Security Topics From Our List
Software and computer administration cyber security topics.
- Cyber Security Research Paper Topics on Data Protection
- Cyber Security Awareness Topics
Network Security Topic Ideas
- Current and Interesting Topics in Cyber Security
Nevertheless, selecting cybersecurity topics for research shouldn’t be a rushed process. That’s because the chosen topics will influence the experience of students while writing and the grades they will score. Therefore, learners should focus on choosing topics that they will be comfortable researching and writing about.
If you’re having a hard time choosing the topics to research and write about, here are categories of some of the best cybersecurity paper topics that you can consider. We also advise you to check out capstone project topics .
The cyber security of a company can be compromised in many ways when it comes to software and computer administration. As such, software and computer administration is a great sources of cybersecurity research paper topics. Here are some of the best topics in this category.
- Evaluation of the operation of antimalware in preventing cyber attacks
- How does virus encryption work
- Is countering malware difficult because of the fast evolution of technology?
- Why should companies train their staff on cyber security?
- Why should people worry about identity theft?
- How important are software updates when it comes to cyber security?
- What causes cyber crimes?
- What are the major threats to the cyber security of social media users?
- What are the most effective methods of preventing phishing?
- What is the major threat to cyber security today and why?
These topics address issues that affect anybody or any organization that uses a computer or any device to access the internet and exchange information. As such, most people, including teachers and professors, will be impressed by papers and essays written about them.
CyberSecurity Research Paper Topics on Data Protection
Individuals and companies send and receive a lot of data every day. As such, this category has some of the best cybersecurity topics for presentation. That’s because they address issues that affect many people and organizations. Here are some of the best information security topics to consider when writing papers and essays or preparing a presentation.
- The best security measures for protecting your data
- How third-party applications can be used to access and acquire data without permission
- How to prevent the loss of data from a computer
- Can biometrics be used to prevent unauthorized data access?
- Can you protect yourself from cyber crimes by keeping personal data private?
- What should you do in case of a data breach?
- How can you secure your data with a 2-steps authentication process?
- How can public Wi-Fi or the internet be used to steal personal data?
- What information can be accessed by unauthorized persons if they hack an account?
- Can software updates help in protecting personal data?
Every computer or internet user wants to be sure that their data is safe and protected. Papers and essays that are written on these topics address issues of data protection. As such, many people will find them worth reading.
CyberSecurity Awareness Research Paper Topics
The best cyber security topics for research papers do more than just address a single issue. They also inform the readers. Here are some of the best cyber security topics for research papers that also focus on creating awareness.
- What is reverse engineering?
- How efficient are RFID security systems?
- How does the dark web propagate organized cyber crimes?
- How can steganalysis be applied?
- Analyze the best authorization infrastructures today
- How important is computer forensics in the current digital era?
- What strategies have been proven effective in preventing cyber-attacks?
- Which forensic tools are the best when it comes to detecting cyber threats?
- Can changing the password regularly help in predicting a cyber attack?
- How can you tell that you’re at risk of online identity theft?
Many people are not aware of many things that affect their cyber security. These topics are relevant because they enhance the awareness of the internet and computer users.
Most organizations today have networked systems that enhance their operations. Unfortunately, criminals have learned to target those networked systems with their criminal activities. As such, students can address some of these issues with their cyber security thesis topics. Here are interesting topics that learners can research and write about in this category.
- Evaluation of the cyber security legal framework in the U.S
- Analysis of the most difficult aspect of the administration of cyber security
- How can the possibilities of multiple threats be managed effectively?
- How does data backup help when it comes to cyber security?
- How effective is two-factor authentication?
- How should a company respond to hacking in its system?
- Which are the best cyber security protection approaches for a multinational company?
- What are the pros and cons of unified user profiles?
- What are the most important components of effective data governance?
- What motivates individuals to commit cybercrimes?
These computer security topics can be used to write papers and essays for college or even commissioned by organizations and used for presentation purposes.
Current and Interesting Topics in CyberSecurity
Some computer security research topics seek to address issues that affect society at the moment. Here are examples of such topics.
- How phishing is evolving and getting more sophisticated
- Explain the evolution of Ransomware strategies
- Explain how the cryptocurrency movement affects cybersecurity
- Cyber-Physical Attacks: How do they work?
- What are state-sponsored attacks and how do they affect cyber security at a global level?
- Discuss cyber security risks when it comes to third-party vendor relationships
- How digital advertisements are being used to collect user characteristics
- How can a person sync all their devices while ensuring their protection
- Why it’s advisable to avoid downloading files from sites that are not trusted
- Why consumers should read the terms and conditions of software before they decide to install it
Such technology security topics are trendy because they address issues that affect most people in modern society. Nevertheless, students should conduct extensive research to draft solid papers and essays on these topics.
This cyber security topic list is not exhaustive. You can contact our thesis writers if you need more ideas or help. Students have many topics to consider depending on their academic programs, interests, and instructions provided by educators or professors. Nevertheless, students should focus on choosing topics that will enable them to come up with informative and comprehensive papers. Thus, every student should choose an information security topic for which they can find relevant and supporting data.
Leave a Reply Cancel reply
75 Cyber Security Research Topics in 2024
Introduction to Cybersecurity Research
Cybersecurity research aims to protect computer systems, networks, and data from unauthorised access, theft, or damage. It involves studying and developing methods and techniques to identify, understand, and mitigate cyber threats and vulnerabilities.
The field can be divided into theoretical and applied research and faces challenges such as
- Increasing complexity
- New forms of malware
- The growing sophistication of cyber attacks
On a daily basis, approximately 2,200 cyber attacks occur, with an average of one cyber attack happening every 39 seconds. This is the reason why researchers must stay up-to-date and collaborate with others in the field.
In this article, let’s discuss the different cybersecurity research topics and how they will help you become an expert in the field.

Check out our free technology courses to get an edge over the competition.
Here are some of the latest research topics in cyber security –
Emerging Cyber Threats and Vulnerabilities in 2024
Continual technological advancements lead to changes in cybersecurity trends, with data breaches, ransomware, and hacks becoming more prevalent.
- Cyber Attacks and Their Countermeasures – Discuss – This research paper will discuss various cyber attacks and their corresponding countermeasures. It aims to provide insights on how organisations can better protect themselves from cyber threats.
- Is Cryptography Necessary for Cybersecurity Applications? – Explore the role of cryptography in ensuring the confidentiality, integrity, and availability of data and information in cybersecurity. It would examine the various cryptographic techniques used in cybersecurity and their effectiveness in protecting against cyber threats.
Here are some other cyber security topics that you may consider –
- Discuss the Application of Cyber Security for Cloud-based Applications
- Data Analytics Tools in Cybersecurity
- Malware Analysis
- What Are the Behavioural Aspects of Cyber Security?
- Role of Cyber Security on Intelligent Transporation Systems
- How to Stop and Spot Different Types of Malware?
Check Out upGrad’s Software Development Courses to upskill yourself.
Machine Learning and AI in Cybersecurity Research
Machine learning and AI are research topics in cybersecurity, aiming to develop algorithms for threat detection, enhance intelligence and automate risk mitigation. However, security risks like adversarial attacks require attention.

- Using AI/ML to Analyse Cyber Threats – This cyber security research paper analyses cyber threats and could include an overview of the current state of cyber threats and how AI/ML can help with threat detection and response. The paper could also discuss the challenges and limitations of using AI/ML in cybersecurity and potential areas for further research.
Here are some other topics to consider –
- Developing Cognitive Systems for Cyber Threat Detection and Response
- Developing Distributed Ai Systems to Enhance Cybersecurity
- Developing Deep Learning Architectures for Cyber Defence
- Exploring the Use of Computational Intelligence and Neuroscience in Enhancing Security and Privacy
- How is Cyber Security Relevant for Everyone? Discuss
- Discuss the Importance of Network Traffic Analysis
- How to Build an App to Break Ceasar Cipher
You can check out the Advanced Certificate Programme in Cyber Security course by upGrad, which will help students become experts in cyber security.
IoT Security and Privacy
IoT security and privacy research aim to develop secure and privacy-preserving architectures, protocols, and algorithms for IoT devices, including encryption, access control, and secure communication. The challenge is to balance security with usability while addressing the risk of cyber-attacks and compromised privacy.
- Service Orchestration and Routing for IoT – It may focus on developing efficient and secure methods for managing and routing traffic between IoT devices and services. The paper may explore different approaches for optimising service orchestration.
- Efficient Resource Management, Energy Harvesting, and Power Consumption in IoT – This paper may focus on developing strategies to improve energy use efficiency in IoT devices. This may involve investigating the use of energy harvesting technologies, optimising resource allocation and management, and exploring methods to reduce power consumption.
Here are some other cyber security project topics to consider –
- Computation and Communication Gateways for IoT
- The Miniaturisation of Sensors, Cpus, and Networks in IoT
- Big Data Analytics in IoT
- Semantic Technologies in IoT
- Virtualisation in IoT
- Privacy, Security, Trust, Identity, and Anonymity in IoT
- Heterogeneity, Dynamics, and Scale in IoT
- Consequences of Leaving Unlocked Devices Unattended
Explore our Popular Software Engineering Courses
Blockchain security: research challenges and opportunities.
Blockchain security research aims to develop secure and decentralised architectures, consensus algorithms, and privacy-preserving techniques while addressing challenges such as smart contract security and consensus manipulation. Opportunities include transparent supply chain management and decentralised identity management.
- Advanced Cryptographic Technologies in the Blockchain – Explore the latest advancements and emerging trends in cryptographic techniques used in blockchain-based systems. It could also analyse the security and privacy implications of these technologies and discuss their potential impact.
- Applications of Smart Contracts in Blockchain – Explore the various use cases and potential benefits of using smart contracts to automate and secure business processes. It could also examine the challenges and limitations of smart contracts and propose potential solutions for these issues.
Here are some other topics –
- Ensuring Data Consistency, Transparency, and Privacy in the Blockchain
- Emerging Blockchain Models for Digital Currencies
- Blockchain for Advanced Information Governance Models
- The Role of Blockchain in Future Wireless Mobile Networks
- Law and Regulation Issues in the Blockchain
- Transaction Processing and Modification in the Blockchain
- Collaboration of Big Data With Blockchain Networks
Cloud Security: Trends and Innovations in Research
Cloud security research aims to develop innovative techniques and technologies for securing cloud computing environments, including threat detection with AI, SECaaS, encryption and access control, secure backup and disaster recovery, container security, and blockchain-based solutions. The goal is to ensure the security, privacy, and integrity of cloud-based data and applications for organisations.
- Posture Management in Cloud Security – Discuss the importance of identifying and addressing vulnerabilities in cloud-based systems and strategies for maintaining a secure posture over time. This could include topics such as threat modelling, risk assessment, access control, and continuous monitoring.
- Are Cloud Services 100% Secure?
- What is the Importance of Cloud Security?
- Cloud Security Service to Identify Unauthorised User Behaviour
- Preventing Theft-of-service Attacks and Ensuring Cloud Security on Virtual Machines
- Security Requirements for Cloud Computing
- Privacy and Security of Cloud Computing
Explore Our Software Development Free Courses
Cybercrime investigations and forensics.
Cybercrime investigations and forensics involve analysing digital evidence to identify and prosecute cybercriminals, including developing new data recovery, analysis, and preservation techniques. Research also focuses on identifying cybercriminals and improving legal and regulatory frameworks for prosecuting cybercrime.
- Black Hat and White Hat Hacking: Comparison and Contrast – Explore the similarities and differences between these two approaches to hacking. It would examine the motivations and methods of both types of hackers and their impact on cybersecurity.
- Legal Requirements for Computer Forensics Laboratories
- Wireless Hacking Techniques: Emerging Technologies and Mitigation Strategies
- Cyber Crime: Current Issues and Threats
- Computer Forensics in Law Enforcement: Importance and Challenges
- Basic Procedures for Computer Forensics and Investigations
- Digital Forensic Examination of Counterfeit Documents: Techniques and Tools
- Cybersecurity and Cybercrime: Understanding the Nature and Scope
An integral part of cybercrime investigation is to learn software development. Become experts in this field with the help of upGrad’s Executive Post Graduate Programme in Software Development – Specialisation in Full Stack Development .
Cybersecurity Policy and Regulations
Cybersecurity policy and regulations research aims to develop laws, regulations, and guidelines to ensure the security and privacy of digital systems and data, including addressing gaps in existing policies, promoting international cooperation, and developing standards and best practices for cybersecurity. The goal is to protect digital systems and data while promoting innovation and growth in the digital economy.
- The Ethicality of Government Access to Citizens’ Data – Explore the ethical considerations surrounding government access to citizens’ data for surveillance and security purposes, analysing the potential risks and benefits and the legal and social implications of such access.
- The Moral Permissibility of Using Music Streaming Services – Explore the ethical implications of using music streaming services, examining issues such as intellectual property rights, artist compensation, and the environmental impact of streaming.
- Real Name Requirements on Internet Forums
- Restrictions to Prevent Domain Speculation
- Regulating Adult Content Visibility on the Internet
- Justification for Illegal Downloading
- Adapting Law Enforcement to Online Technologies
- Balancing Data Privacy With Convenience and Centralisation
- Understanding the Nature and Dangers of Cyber Terrorism
Human Factors in Cybersecurity
Human factors in cybersecurity research study how human behaviour impacts cybersecurity, including designing interfaces, developing security training, addressing user error and negligence, and examining cybersecurity’s social and cultural aspects. The goal is to improve security by mitigating human-related security risks.
- Review the Human Factors in Cybersecurity – It explores various human factors such as awareness, behaviour, training, and culture and their influence on cybersecurity, offering insights and recommendations for improving cybersecurity outcomes.
- Integrating Human Factors in Cybersecurity for Better Risk Management
- Address the Human Factors in Cybersecurity Leadership
- Human Factors in IoT Security
- Internal Vulnerabilities: the Human Factor in It Security
- Cyber Security Human Factors – the Ultimate List of Statistics and Data
In-Demand Software Development Skills
Cybersecurity education and awareness.
Cybersecurity education and awareness aims to educate individuals and organisations about potential cybersecurity threats and best practices to prevent cyber attacks. It involves promoting safe online behaviour, training on cybersecurity protocols, and raising awareness about emerging cyber threats.
- Identifying Phishing Attacks – This research paper explores various techniques and tools to identify and prevent phishing attacks, which are common types of cyber attacks that rely on social engineering tactics to trick victims into divulging sensitive information or installing malware on their devices.
- Risks of Password Reuse for Personal and Professional Accounts – Investigate the risks associated with reusing the same password across different personal and professional accounts, such as the possibility of credential stuffing attacks and the impact of compromised accounts on organisational security.
- Effective Defence Against Ransomware
- Information Access Management: Privilege and Need-to-know Access
- Protecting Sensitive Data on Removable Media
- Recognising Social Engineering Attacks
- Preventing Unauthorised Access to Secure Areas: Detecting Piggybacking and Tailgating
- E-mail Attack and Its Characteristics
- Safe Wifi Practice: Understanding VPN
With the increasing use of digital systems and networks, avoiding potential cyber-attacks is more important than ever. The 75 research topics outlined in this list offer a glimpse into the different dimensions of this important field. By focusing on these areas, researchers can make significant contributions to enhancing the security and safety of individuals, organisations, and society as a whole.
upGrad’s Master of Science in Computer Science program is one of the top courses students can complete to become experts in the field of tech and cyber security. The program covers topics such as Java Programming and other forms of software engineering which will help students understand the latest technologies and techniques used in cyber security.
The program also includes hands-on projects and case studies to ensure students have practical experience in applying these concepts. Graduates will be well-equipped to take on challenging roles in the rapidly growing field of cyber security.

Pavan Vadapalli
Something went wrong
Our Popular Software Engineering Courses
Our Trending Software Engineering Courses
- Master of Science in Computer Science from LJMU
- Executive PG Program in Software Development Specialisation in Full Stack Development from IIIT-B
- Advanced Certificate Programme in Cyber Security from IIITB
- Full Stack Software Development Bootcamp
- Software Engineering Bootcamp from upGrad
Popular Software Development Skills
- React Courses
- Javascript Courses
- Core Java Courses
- Data Structures Courses
- ReactJS Courses
- NodeJS Courses
- Blockchain Courses
- SQL Courses
- Full Stack Development Courses
- Big Data Courses
- Devops Courses
- NFT Courses
- Cyber Security Courses
- Cloud Computing Courses
- Database Design Courses
- Crypto Courses
- Python Courses
Frequently Asked Questions (FAQs)
Artificial intelligence (AI) has proved to be an effective tool in cyber defence. AI is anticipated to gain even more prominence in 2024, mainly in monitoring, resource and threat analysis, and quick response capabilities.
One area of focus is the development of secure quantum and space communications to address the increasing use of quantum technologies and space travel. Another area of research is improving data privacy.
The approach to cybersecurity is expected to change from defending against attacks to acknowledging and managing ongoing cyber risks. The focus will be on improving resilience and recovering from potential cyber incidents.
Related Programs View All
Certification
40 Hrs Live, Expert-Led Sessions
2 High-Quality Practice Exams
View Program

Executive PG Program
IIIT-B Alumni Status

Master's Degree
40000+ Enrolled Learners

Job Assistance
32-Hr Training by Dustin Brimberry
Question Bank with 300+ Practice Qs
45 Hrs Live Expert-Led Training
Microsoft-Approved Curriculum
159+ Hours of Live Sessions
126+ Hours of Live Sessions
Fully Online
13+ Hrs Instructor-Led Sessions
Live Doubt-Solving Sessions

2 Unique Specialisations
300+ Hiring Partners
20+ Hrs Instructor-Led Sessions
16 Hrs Live Expert-Led Training
CLF-C02 Exam Prep Support

24 Hrs Live Expert-Led Training
4 Real-World Capstone Projects
17+ Hrs Instructor-Led Training
3 Real-World Capstone Projects
289 Hours of Self-Paced Learning
10+ Capstone Projects
490+ Hours Self-Paced Learning
4 Real-World Projects
690+ Hours Self-Paced Learning
Cloud Labs-Enabled Learning
288 Hours Self-Paced Learning
9 Capstone Projects
40 Hrs Live Expert-Led Sessions
2 Mock Exams, 9 Assessments

Executive PG Certification
GenAI integrated curriculum

Job Prep Support
Instructor-Led Sessions
Hands-on UI/UX
16 Hrs Live Expert-Led Sessions
12 Hrs Hand-On Practice
30+ Hrs Live Expert-Led Sessions
24+ Hrs Hands-On with Open Stack
2 Days Live, Expert-Led Sessions
34+ Hrs Instructor-Led Sessions
10 Real-World Live Projects
24 Hrs Live Expert-Led Sessions
16 Hrs Hand-On Practice
8 Hrs Instructor-Led Training
Case-Study Based Discussions
40 Hrs Instructor-Led Sessions
Hands-On Practice, Exam Support
24-Hrs Live Expert-Led Sessions
Regular Doubt-Clearing Sessions
Extensive Exam Prep Support
6 Hrs Live Expert-Led Sessions
440+ Hours Self-Paced Learning
400 Hours of Cloud Labs
15-Hrs Live Expert-Led Sessions
32 Hrs Live Expert-Led Sessions
28 Hrs Hand-On Practice
Mentorship by Industry Experts
24 Hrs Live Trainer-Led Sessions
Mentorship by Certified Trainers
GenAI Integrated Curriculum
Full Access to Digital Resources
16 Hrs Live Instructor-Led Sessions
80+ Hrs Hands-On with Cloud Labs
160+ Hours Live Instructor-Led Sessions
Hackathons and Mock Interviews
31+ Hrs Instructor-Led Sessions
120+ Hrs of Cloud Labs Access
35+ Hrs Instructor-Led Sessions
6 Real-World Live Projects
24+ Hrs Instructor-Led Training
Self-Paced Course by Nikolai Schuler
Access Digital Resources Library
300+ Hrs Live Expert-Led Training
90 Hrs Doubt Clearing Sessions
56 Hours Instructor-Led Sessions
78 Hrs Live Expert-Led Sessions
22 Hrs Live, Expert-Led Sessions
CISA Job Practice Exams
Explore Free Courses
Learn more about the education system, top universities, entrance tests, course information, and employment opportunities in Canada through this course.
Advance your career in the field of marketing with Industry relevant free courses
Build your foundation in one of the hottest industry of the 21st century
Master industry-relevant skills that are required to become a leader and drive organizational success
Build essential technical skills to move forward in your career in these evolving times
Get insights from industry leaders and career counselors and learn how to stay ahead in your career
Kickstart your career in law by building a solid foundation with these relevant free courses.
Stay ahead of the curve and upskill yourself on Generative AI and ChatGPT
Build your confidence by learning essential soft skills to help you become an Industry ready professional.
Learn more about the education system, top universities, entrance tests, course information, and employment opportunities in USA through this course.
Suggested Tutorials

Explore Python programming with this concise tutorial, covering basics to advanced concepts for beginners and enthusiasts alike.

Introduction to C Programming, Learn all the C programming language concepts in this tutorial.
Suggested Blogs
12 Apr 2024
![information security topics for research Scrum Master Salary in India: For Freshers & Experienced [2023]](https://www.upgrad.com/__khugblog-next/image/?url=https%3A%2F%2Fd14b9ctw0m6fid.cloudfront.net%2Fugblog%2Fwp-content%2Fuploads%2F2020%2F05%2F486.png&w=3840&q=75)
by Rohan Vats
05 Mar 2024
![information security topics for research SDE Developer Salary in India: For Freshers & Experienced [2024]](https://www.upgrad.com/__khugblog-next/image/?url=https%3A%2F%2Fd14b9ctw0m6fid.cloudfront.net%2Fugblog%2Fwp-content%2Fuploads%2F2020%2F05%2F482-1.png&w=3840&q=75)
by Prateek Singh
29 Feb 2024
by venkatesh Rajanala
by Harish K
by Geetika Mathur
by spandita hati

Cyber threats have grown exponentially as the modern web and powerful AI systems have proliferated. We’re designing systems to secure the hybrid cloud and AI for sensitive datasets to ensure organizations can continue to operate safely and securely.
What is red teaming for generative AI?
- Adversarial Robustness and Privacy
- Fairness, Accountability, Transparency
- Foundation Models
- Natural Language Processing
- Trustworthy AI
IBM and VU Amsterdam researchers reveal a new vulnerability in all major CPU architectures
DARPA and IBM are ensuring that anyone can protect their AI systems from hackers
- Data and AI Security
The 2023 IBM Research annual letter
- Accelerated Discovery
- Hybrid Cloud
- Semiconductors
The era of quantum utility must also be the era of responsible quantum computing
- Quantum Community
- Quantum Safe
An AI model trained on data that looks real but won’t leak personal information
- See more of our work on Security
- Cloud Security: Infrastructure and Applications Advancing the system integrity of cloud systems in mission-critical situations.
- Confidential Computing The cloud computing revolution has brought new security challenges. Confidential computing aims to protect applications and their data when running in the cloud. It works by consistently keeping the application and data encrypted, and only decrypting it inside the processor using keys known to the application/data owner and the processor.
- Cryptography Building the next generation of private, authenticated, and confidential communication cyrtopgraphy tools.
- Data and AI Security Designing systems to monitor and protect sensitive data for robust and secure AI systems on the hybrid cloud.
- Quantum-Safe Cryptography and Migration Designing cryptographic algorithms that are quantum-safe to ensure the world’s digital infrastructure is secure.
- Threat Management Building the next wave of tools to help security teams detect and deflect against advanced cybersecurity threats.
Publications
- Kenneth G. Paterson
- Nathan Manohar
- Eurocrypt 2024
- Shiqiang Wang
- INFOCOM 2024
- Xiaokui Shu
- S&P 2024
- Banashri Karmakar
- Nishat Koti
- Fred Araujo

IBM Security Solutions
Innovations from our Security Research teams are regularly developed into cutting-edge new capabilities for IBM’s Security offerings.
Quantum-safe Cryptography Algorithms
- Cryptography
Privacy Enhancing Technologies for Regulatory Compliance
Custom Essay, Term Paper & Research paper writing services
- testimonials
Toll Free: +1 (888) 354-4744
Email: [email protected]
Writing custom essays & research papers since 2008
154 exceptional cybersecurity research topics for you.

If you are studying computer science or IT-related course, you will encounter such a task. It is one of the most technical assignments, primarily in the era of advanced digital technologies. Students may not have the muscles to complete such papers on their own. That is why we provide expert help and ideas to make the process easier.
Do you want to excel in your cybersecurity paper? Here is your number one arsenal!
What You Need To Know About Cyber Security Research Topics
A cybersecurity paper deals with the practices of protecting servers, electronic systems, computers, and networks from malicious attacks. Although most students think this only applies to computers, it also applies to mobile computing and other business models.
There are various categories in cybersecurity, including:
Network security Application security Information security Operational security Disaster recovery and business continuity
Therefore, your cybersecurity topics for research should:
Examine the common security breaches in systems and networks Offer practical ways of protecting computers from such attacks Highlight the legal and ethical implications of hacking and other related practices Point out the challenges encountered in combating cybercrime
Since this is a technical paper, you should endeavor to do your research extensively to prevent rumors and unverified facts. The topics should also inform and educate people who are not conversant with cybersecurity in simple terms. Avoid using jargon at all costs, as this will make the paper difficult to read and understand.
Are you worried about where you can get professional cybersecurity topics and ideas? Well, here are a few of the most reliable sources that can furnish you with top-rated issues.
- Government legislation on cybersecurity (Acts of Parliament)
- The UN Office of Counter-Terrorism (Cybersecurity initiatives)
- The CISCO magazine
- Forbes also has excellent coverage on cybersecurity
You can find impressive topic ideas from these sources and more. Furthermore, news headlines and stories on cybersecurity can also help you gather many writing ideas. If all these prove futile, use our tip-top writing prompts below:
Quality Cyber Security Thesis Topics
- Impacts of coronavirus lockdowns on cybersecurity threats in the US
- Why ethical hacking is contributing to more harm than good
- The role of computer specialists in combating cyber threats before they occur
- Technological trends that are making it difficult to manage systems
- Are passwords reliable when protecting computer systems?
- Effects of having more than one systems administrator in a company
- Can the government shut down the dark web once and for all?
- Why should you bother about the security of your mobile device?
- Evaluate reasons why using public WIFI can be harmful to your security
- The role of cybersecurity seminars and conferences
- How universities can produce ethical computer hackers who can help the society
- How to counter-terrorism with advanced cybersecurity measures
- Impacts of teaching children how to use computers at a tender age
- Latest innovations that are a threat to cybersecurity
- The role of monitoring in combating frequent cyber attacks
- How social media is contributing to cyber attacks
- Discuss the relationship between cyberbullying and cybersecurity
- Why fingerprints may be the best method of protecting devices
- The role of YouTube in contributing to the rising number of hackers
Top Research Topics For Cyber Security For Master Thesis
- Impact of cyber threats on attaining the sustainable development goals
- Why websites are becoming easy to hack in the 21 st century
- Effects of not having an SSL certificate for a website
- Discuss the security threats associated with WordPress websites
- Impacts of frequent maintenance while the website is still running
- How computer colleges can contribute to a safe cyberspace
- Latest cyber threats to business and financial websites
- Discuss the implications of cyber threats on privacy
- The role of Facebook in advancing cyberbullying and hacking
- Is hacking becoming a global epidemic in the digital world?
- Why using Cyber Cafes may be detrimental to your digital security
- The role of systems analysts in responding to data breaches
- How cybersecurity movies are contributing to cyber threats
- Should hackers face lifetime jail imprisonment when found guilty?
- Loopholes in cyber laws that make the practice challenging to curtail
Good Thesis Topics For Cyber Security
- The relationship between privacy and data security in computing
- Why cloud computing offers a haven for computer hackers
- The role of character and human-based behavior in cybersecurity
- How to determine safe organizational security management and policy
- How the Internet of Things is promoting cyber attacks
- Effects of using cracked computer software
- Are biometrics in cybersecurity able to put off hackers?
- The role of studying mobile platform security
- Why companies should frequently monitor their firewalls
- The role of antimalware in curbing cyber attacks
- Why is Ransomware a headache to most companies handling big data?
- How does antivirus software improve the security of your computer?
- Compare and contrast between the security of UNIX and Ubuntu
- The role of data encryption technologies in ensuring system security
- Is the process of encrypting viruses safe?
Top-Grade Thesis Topics For Cyber Security
- Describe the effectiveness of cybersecurity audits on company systems
- Is it proper to conduct device synchronization?
- Why is it difficult to manage the security of an intranet?
- Discuss the effects of logging in to many devices at the same time
- Evaluate the significance of computer forensics
- How are hackers inventing new ways of breaching the systems of companies?
- Why it is necessary to review the data protection laws
- Practices that increase the vulnerability of a system to cyber attacks
- Can organizations implement impenetrable network systems?
- Why administrators should check the background of users before giving them rights and privileges
- The role of risk management cybersecurity
- Discuss the impact of reverse engineering on computing systems
- Effects of a cyber-attack on a company’s economic performance
- What legal frameworks work best for a computer company?
- The role of social engineering in cybersecurity
Information Security Research Topics
- The implication of the proliferation of the internet globally
- Innovative technologies used in keeping off hackers
- The role of information communication technologies in maintaining the security
- Are online courses on informative security practical?
- Why should people avoid sharing their details on Facebook?
- Effects of using your image on social media
- The role of pseudo names and nicknames on social media
- Discuss the implications of Wi-Fi hacking apps on mobile phones
- How to detect malicious activity on a system
- Evaluate the potential threats of conduct self-hacking on a system
- The impact of sharing personal details with hiring agencies
- How con artists lure unsuspecting applicants into giving out their details
- Effects of frequent maintenance on systems
- How to strengthen the firewall of an information system
- The role of the media in propagating security breaches to information systems
Latest Computer Security Research Topics
- Tricks that black hat hackers use to infiltrate company systems
- How children learn about cybersecurity from their parents
- The impact of watching hacking movies and TV series
- How various companies are protecting themselves from cyber attacks
- Why every company should have a systems security consultant
- Discuss the implication of digital piracy
- Threats that biometrics are bringing to digital systems
- How to block a network intrusion before it causes any effect
- Why MacOS is challenging to infiltrate, unlike Windows
- Results of two-step authentication security measures for login systems
- The role of updating computer systems during working days
- Evaluate times of the year when hackers infiltrate systems the most
- Why it isn’t easy to manage big data on the cloud
- What happens during a system breakdown and maintenance?
- Discuss the role of data synchronization in creating a backup
Network Security Research Paper Topics
- The impact of having self-configuring and decentralized network systems
- Effects of ad-hoc networks for large companies
- Discuss the role of wireless sensor networks in contributing to security breaches
- How malicious nodes join a network
- Why it is difficult to detect a passive network attack
- How active network attacks reduce a network’s performance
- Evaluate the various parameters used in network security
- Analyze how a black hole affects a network system
- Describe techniques used in detecting malicious nodes on networks
- How to improve the safety of a company network
- The role of data encryption in maintaining the security of a network
- Describe the various channels of establishing secure algorithms in a network
- How does RSA increase the safety of a particular network?
- Effective policies and procedures for maintaining network security
- The role of a unique ID and Password in securing a website
Computer Security Research Topics
- Why it is challenging to maintain endpoint security
- The role of a critical infrastructure cybersecurity
- How to create secure passwords for your computer network
- The part of scanning for malware often on your PC
- How to detect apps that invade your privacy unknowingly
- Why ordering software from the black market is a threat to security
- Safe computing techniques for first-time computer users
- The role of digital literacy in preventing hacking
- Why most online users fall to online scams
- The role of smartphones in enhancing cybersecurity threats
- Evaluate the mobile landscape concerning data security
- The implication of private email accounts in data breaches
- Sites that contain a barrel of internet criminals
- How to develop comprehensive internet security software
- How children can navigate the internet safely
Impressive Cyber Crime Research Topics
- Why cyber currencies are a threat to online security
- Why cyberbullying is rampant in the 21 st century unlike in any other time
- The impact of online persuasion campaigns on cybersecurity
- Why teenagers are victims of cyberbullying than adults
- Discuss the effects of technology evolution on cybercrime
- How online hackers collect information without the knowledge of the victim
- Traits of a robust cybersecurity system
- Practices that can help reduce cybercrime in institutions of higher learning.
- Effects of global coordinated cyber attacks
- The penalties of cyber-attack in the First Amendment
- Why the world is experiencing increased cyber attacks
- Critical concepts of cyber attacks
- Cybercriminals and enterprises
- Role of NGOs in combating cyber terrorism
- Cyberbullying in campus
World-Class Cyber Security Thesis Ideas
- Effects of the cyber-attack on Sony in 2014
- The role of globalization in enhancing cybersecurity
- How to prevent automotive software from malicious cyber attacks
- The role of cyber technology in changing the world since the 1990s
- How the private sector is essential in combating cyber threats
- Computer infrastructure protection against cyber attacks
- Impact of social networking sites on cybersecurity
- Threats that cyber-attacks pose the national security of a country
- How cyber monitoring affects ethical and legal considerations
- Factors leading to the global nature of cyber attacks
- Analyze law enforcement agencies that deal with cyber attacks
- Evaluate cyber-crime court cases
- Evolution of the cybersecurity industry
- Cyber terrorism in the US
- Implementing adequate data protection strategies
We offer paper writing help on any cybersecurity topic. Try us now!


- Bachelor’s Degrees
- Master’s Degrees
- Doctorate Degrees
- Certificate Programs
- Nursing Degrees
- Cybersecurity
- Human Services
- Science & Mathematics
- Communication
- Liberal Arts
- Social Sciences
- Computer Science
- Admissions Overview
- Tuition and Financial Aid
- Incoming Freshman and Graduate Students
- Transfer Students
- Military Students
- International Students
- Early Access Program
- About Maryville
- Our Faculty
- Our Approach
- Our History
- Accreditation
- Tales of the Brave
- Student Support Overview
- Online Learning Tools
- Infographics
Home / Blog
Three Breakthrough Cybersecurity Research Topics
July 27, 2016

As individuals, corporations, and government agencies increasingly store and transmit digital information, the ability to protect valuable data becomes more crucial. Unfortunately, cyber theft and cyber attacks are becoming more sophisticated and prolific each year — meaning cybersecurity is more important than ever. Luckily, breakthroughs in cybersecurity are also increasing, which allows organizations to stay one step ahead of those who attempt to commit cyber crimes.
Individuals who wish to become part of the workforce addressing digital and internet threats by earning a bachelor’s in cybersecurity online should be aware of prominent cybersecurity research topics. Here are two recent breakthroughs in cybersecurity, as well as a detailed infographic that delves into the complexity of this field.
Trend #1: Single Photon Generation
A cybersecurity research team at the University of Sydney has solved an issue that could lead to a major breakthrough in the way information is transmitted, allowing for more secure computer systems worldwide. The issue is the ability to generate single photons — tiny particles of light — that carry quantum information in security systems.
“Implementing optical quantum technologies has now come down to one fundamental challenge: having indistinguishable single photons on demand,” says Dr. Chunle Xiong, from the School of Physics.
The Sydney team has developed a way to generate single photons more reliably. By advancing quantum computing technology, the ability to more securely exchange data and more quickly search databases is becoming a reality. This makes photons one of the key cybersecurity research topics.
“The ability to generate single photons, which form the backbone of technology used in laptops and the internet, will drive the development of local secure communications systems — for safeguarding defense and intelligence networks, the financial security of corporations and governments and bolstering personal electronic privacy, like shopping online,” says Professor Ben Eggleton, co-author of the paper published in Nature Communications.
Trend #2: Privacy Homomorphism
A research student recently solved a cryptography problem that has been stumping experts for decades. Craig Gentry, a Stanford PhD student at the time of the breakthrough, found a way to analyze encrypted information without sacrificing confidentiality. It is called privacy homomorphism, or fully homomorphic encryption.
This new technology will allow cloud computing providers to manipulate certain data without exposing the original data. Charles Lickel, vice president of software research at IBM, says, “Fully homomorphic encryption will enable businesses to make more informed decisions, based on more studied analysis, without compromising privacy.”
There are still challenges in making this technology viable for large-scale businesses, but the possibilities are wide-ranging. In the future, it should allow cloud providers to host confidential data from businesses as well as governments. It holds for now as one of the key research topics in cybersecurity.
Trend #3: Normalizing Working-from-Home: Security for Remote Teams
The COVID-19 global pandemic dramatically impacted traditional workplace standards through 2020. To avoid the potential for employees spreading the highly contagious virus, businesses worldwide moved to remote working standards for the foreseeable future.
As a result, cybersecurity needs have adjusted to risk management as employees access data and other sensitive materials from home — as well as how not to impede their work in the process.
Bart Willemsen, VP analyst with Gartner, says that companies should focus on three primary goals: safety, productivity, and user and organizational privacy. The challenge for cybersecurity leaders is to find a healthy balance between all three goals.
“Take privacy versus safety for example,” Willemsen says. “The trade-off would be, how much do we invade privacy to offer a certain level of safety? It’s making a concession between both values. It would actually be better to try and fulfill both values.”
Prepare for Cybersecurity Careers and Beyond
Cybersecurity managers are valuable assets to their organizations, and employer demand is likely to remain high in the years ahead. Companies will need these professionals to safeguard their IT systems as the evolution of technology gives rise to new types of cyber threats. Maryville University offers both an online bachelor’s and an online master’s in cybersecurity , providing degree opportunities for aspiring security professionals at any stage of their career.
In the meantime, see the infographic below for facts about the current state of the ever-changing cybersecurity sector:

Add This Infographic to Your Site
Ars Technica, “Worried About Cybersecurity and the Connected Car? There’s a Bill for That”
CNET, “Two-Factor Authentication: What You Need to Know (FAQ)”
ComputerWeekly.com, “Cryptography Breakthrough Paves Way to Secure Cloud Services”
ComputerWeekly.com, “The Internet of Things: A Second Digital Revolution Worth Millions”
FedTech, “How Federal Agencies Can Improve Cybersecurity With Better Data Encryption”
Heimdal Security, “10 Alarming Cybersecurity Facts That Threaten Your Data”
MIT Technology Review, “Cybersecurity in the Age of Digital Transformation”
Nature Communications, “Cell Shape-Independent FtsZ Dynamics in Bacteria”
Phys.org, “Breakthrough Technology to Improve Cybersecurity”
Quatr.us, “What Is a Photon? Physics of Light”
Gartner, “6 Principles for Employee Privacy”
Bring us your ambition and we’ll guide you along a personalized path to a quality education that’s designed to change your life.
Take Your Next Brave Step
Receive information about the benefits of our programs, the courses you'll take, and what you need to apply.
Security Management Research Paper Topics

Security management research paper topics are a critical area of study for management students looking to explore the complex world of safeguarding organizational assets. Security management covers various facets, including information security, physical security, risk management, compliance, and more. The study of security management is increasingly relevant in our technology-driven world. Research within this field equips students with the knowledge to protect an organization’s information and physical resources, and the skills to respond to rapidly evolving security threats. This page provides a comprehensive list of research topics to assist students in selecting a subject that aligns with their interests and the current industry demands. The following sections will provide an in-depth look into various security management research topics, organized into ten categories with ten subjects each. Additionally, this page will offer insights into how to choose and write about these topics, along with an overview of iResearchNet’s customized writing services for those who seek professional assistance.
100 Security Management Research Paper Topics
The field of security management is as vast as it is vital in today’s global landscape. From protecting information systems to ensuring the physical safety of assets, security management plays a central role in the smooth operation of organizations across various sectors. As we dive into this comprehensive list of security management research paper topics, students will find a plethora of subjects that are both challenging and relevant. The topics are divided into ten distinct categories, each focusing on a different aspect of security management.
Academic Writing, Editing, Proofreading, And Problem Solving Services
Get 10% off with 24start discount code.
- Role of Encryption in Data Protection
- Security Protocols in Wireless Networks
- Cloud Security Management Strategies
- Biometric Security Measures
- Ethical Hacking and Defense Strategies
- Security Risks in Internet of Things (IoT)
- Mobile Application Security
- Compliance with GDPR and Other Regulations
- Social Engineering Attacks and Prevention
- Virtual Private Networks (VPNs) and Security
- Designing Secure Buildings and Facilities
- Access Control Systems and Technologies
- Surveillance and Monitoring Techniques
- Security Personnel Training and Management
- Risk Assessment for Physical Threats
- Vehicle Security and Fleet Management
- Maritime Security Protocols
- Security Measures for Public Events
- Emergency Response and Evacuation Planning
- Integration of Technology in Physical Security
- Enterprise Risk Management Strategies
- Security Policies and Compliance Auditing
- Regulatory Compliance in Different Industries
- Risk Mitigation and Disaster Recovery Planning
- Cyber Insurance and Risk Transfer
- Security Awareness and Training Programs
- Third-party Vendor Risk Management
- Financial Risk Management in Security Operations
- Implementing ISO Security Standards
- Privacy Policies and Consumer Protection
- Cyber Threat Intelligence and Analysis
- Intrusion Detection Systems and Firewalls
- Secure Software Development Lifecycle
- Incident Response and Crisis Management
- Security Considerations in E-commerce
- Protecting Against Ransomware and Malware
- Security in Social Networking Sites
- Cybersecurity in Critical Infrastructure
- Mobile Device Security in the Workplace
- Privacy vs. Security in Cyber Law
- Role of CISO (Chief Information Security Officer)
- Security Leadership and Governance
- Insider Threat Management and Mitigation
- Security Culture and Employee Behavior
- Contractual and Legal Aspects of Security
- Intellectual Property Protection
- Security Metrics and Performance Indicators
- Outsourcing Security Services
- Security Budgeting and Financial Management
- Integrating Security with Business Strategy
- Terrorism and Counterterrorism Strategies
- Security Intelligence and Law Enforcement
- Border Control and Immigration Security
- Cyber Warfare and State-sponsored Attacks
- Protection of Critical National Infrastructure
- Emergency Preparedness and Response
- Security Considerations in International Relations
- Humanitarian Security and Crisis Management
- Nuclear Security and Non-proliferation
- Global Maritime Security Issues
- Security in Hospitals and Healthcare Facilities
- Patient Data Privacy and HIPAA Compliance
- Medical Device and IoT Security
- Emergency Medical Services and Security
- Security Measures for Mental Health Facilities
- Pharmaceutical Supply Chain Security
- Bioterrorism and Public Health Security
- Security Education for Healthcare Professionals
- Medical Records Security and Management
- Telemedicine and Remote Healthcare Security
- Security Considerations in Online Retail
- Fraud Detection and Prevention Strategies
- Payment Security and PCI Compliance
- Inventory Security and Loss Prevention
- Consumer Trust and Brand Protection
- E-commerce Regulations and Compliance
- Security in Omnichannel Retailing
- Secure Customer Experience Design
- Mobile Commerce Security
- Retail Surveillance and Anti-shoplifting Techniques
- Campus Safety and Security Measures
- Cybersecurity Education and Curriculum
- Student Data Privacy and Protection
- Security in Online Learning Platforms
- Intellectual Property Rights in Academia
- Emergency Response Plans for Educational Institutions
- School Transportation Security
- Security Measures for Laboratories and Research Facilities
- Ethical Guidelines in Academic Research
- Security Considerations in International Student Exchange
- Artificial Intelligence in Security
- Quantum Computing and Cryptography
- Security Implications of 5G Technology
- Sustainable and Green Security Practices
- Human Factors in Security Design
- Blockchain for Security Applications
- Virtual and Augmented Reality Security
- Security in Autonomous Vehicles
- Integration of Smart Technologies in Security
- Ethical Considerations in Emerging Security Technologies
Security management is an ever-evolving field, reacting to both technological advancements and global socio-political changes. The above categories and topics encompass a broad spectrum of the security management domain. This comprehensive list is designed to inspire students and guide them towards a research paper that not only interests them but also contributes to the growing body of knowledge in security management. By exploring these topics, students will have the opportunity to deepen their understanding of current issues and become part of the ongoing conversation in this vital area of study.
Security Management and the Range of Research Paper Topics
Introduction to security management.
Security management has increasingly become a central concern for organizations, governments, and individuals in our interconnected and technologically driven world. Its primary focus is on safeguarding assets, information, and people by assessing risks and implementing strategies to mitigate potential threats. From the micro-level of individual privacy protection to the macro-level of national security, the concepts and practices within this field permeate almost every aspect of our daily lives. This article delves into the fundamental aspects of security management and explores the extensive range of research paper topics it offers.
Key Principles and Concepts in Security Management
- Risk Assessment and Mitigation: At the core of security management lies the process of identifying, evaluating, and minimizing risks. It involves recognizing potential vulnerabilities, assessing the likelihood of threats, and implementing measures to reduce the potential impact.
- Compliance and Regulation: Security management is also heavily influenced by various laws, regulations, and industry standards. Whether it’s GDPR for data protection or HIPAA for healthcare, compliance with these regulations is essential to avoid legal consequences.
- Physical and Cyber Security: Security management encompasses both the physical and digital realms. Physical security focuses on protecting tangible assets, such as buildings and equipment, while cyber security emphasizes safeguarding digital information.
- Human Factors: People are often considered the weakest link in security. Training, awareness, and a robust security culture are crucial in ensuring that employees and stakeholders understand and adhere to security protocols.
- Technology and Innovation: With the advent of new technologies like AI, blockchain, and IoT, security management must continuously evolve to address the unique challenges and opportunities they present.
- Global Perspectives: In a globally connected world, security management must consider international laws, cross-border data flows, and the unique risks associated with different geographical regions.
- Ethics and Social Responsibility: Ethical considerations in security management include respecting individual privacy, transparency in surveillance, and social responsibility in using technology for security purposes.
Range and Depth of Research Paper Topics
Given the complexity and multidimensionality of security management, the range of research paper topics in this field is vast. The following sections provide an insight into the various dimensions that can be explored:
- Information Security Management: Research can focus on encryption, authentication, intrusion detection, or explore the psychological aspects of social engineering attacks.
- Physical Security Management: Topics may include architectural design for security, biometrics, or the balance between security and convenience in access controls.
- Organizational Security Management: This includes leadership and governance in security, insider threats, and the alignment of security strategies with business goals.
- Global and National Security Management: Areas to explore here include counterterrorism strategies, cybersecurity policies among nations, or human rights considerations in security protocols.
- Retail and E-commerce Security Management: From payment security to fraud detection, this area explores the unique challenges in the retail and online shopping environment.
- Emerging Trends in Security Management: This invites research into the future of security management, considering technological advancements, emerging threats, and the ethical implications of new tools and techniques.
Security management is an intricate field that intertwines technological, human, organizational, and societal aspects. It continues to evolve in response to the rapidly changing global landscape marked by technological innovation, geopolitical shifts, and emerging threats. The range of research paper topics in security management reflects this diversity and offers a wealth of opportunities for students to engage with cutting-edge issues.
The ongoing development of this field requires fresh insights, innovative thinking, and a commitment to understanding the underlying principles that govern security management. By delving into any of the areas outlined above, students can contribute to this exciting and ever-changing field. Whether exploring traditional aspects like risk management or venturing into the realms of AI and blockchain, the possibilities for research are as broad and varied as the field itself.
This article provides a foundational understanding of security management and serves as a springboard for further exploration. It’s a gateway to a myriad of research avenues, each offering a unique perspective and challenge, all united by the common goal of enhancing the security and safety of our interconnected world.
How to Choose Security Management Research Paper Topics
Selecting a topic for a research paper in the field of security management is a crucial step that sets the tone for the entire research process. The breadth and depth of this field offer a wide array of possibilities, making the choice both exciting and somewhat daunting. The topic must be relevant, engaging, unique, and, most importantly, aligned with the researcher’s interests and the academic requirements. This section provides a comprehensive guide on how to choose the perfect security management research paper topic, with 10 actionable tips to simplify the process.
- Identify Your Interests: Begin by exploring areas within security management that truly intrigue you. Whether it’s cyber threats, risk management, or physical security measures, your passion for the subject will drive a more engaging research process.
- Understand the Scope: Security management spans across various sectors such as IT, healthcare, retail, and more. Assess the scope of your paper to determine which sector aligns best with your academic needs and professional goals.
- Consider the Relevance: Choose a topic that is pertinent to current trends and challenges in security management. Researching emerging threats or innovative technologies can lead to more compelling findings.
- Assess Available Resources: Ensure that there is enough accessible information and research material on the chosen topic. A topic too obscure might lead to difficulties in finding supporting evidence and data.
- Consult with Your Advisor or Mentor: An experienced academic advisor or mentor can provide valuable insights into the feasibility and potential of various topics, helping you make an informed decision.
- Balance Complexity and Manageability: Selecting a topic that is too broad can be overwhelming, while a narrow topic might lack depth. Striking the right balance ensures that you can comprehensively cover the subject within the stipulated word count and time frame.
- Consider Ethical Implications: Especially in a field like security management, ethical considerations must be at the forefront. Any topic involving human subjects, privacy concerns, or potentially sensitive information should be approached with caution and integrity.
- Align with Learning Objectives: Reflect on the specific learning outcomes of your course or program, and choose a topic that aligns with these objectives. It ensures that your research contributes to your overall academic development.
- Evaluate Potential Contributions: Think about what new insights or perspectives your research could offer to the field of security management. Choosing a topic that allows you to make a meaningful contribution can be more satisfying and impactful.
- Experiment with Preliminary Research: Before finalizing a topic, conduct some preliminary research to gauge the existing literature and potential research gaps. It can help refine your focus and provide a clearer direction.
Choosing a research paper topic in security management is a multifaceted process that requires thoughtful consideration of various factors. By following the tips outlined above, you can navigate through the complexities of this task and select a topic that resonates with your interests, aligns with academic goals, and contributes to the broader field of security management. Remember, a well-chosen topic is the foundation upon which a successful research paper is built. It’s the starting point that leads to a journey filled with discovery, analysis, and intellectual growth. Make this choice wisely, and let it be a gateway to an engaging and rewarding research experience.
How to Write a Security Management Research Paper
A. introductory paragraph.
Writing a research paper on security management requires more than just a keen interest in the subject; it demands a systematic approach, adherence to academic standards, and the ability to synthesize complex information. Security management, with its multifaceted nature encompassing physical security, cybersecurity, risk assessment, and more, offers an exciting but challenging landscape for research. In this section, we will delve into a step-by-step guide comprising 10 vital tips on how to write an effective security management research paper. These tips aim to guide you through the research, planning, writing, and revision stages, ensuring a coherent and impactful paper.
- Choose the Right Topic: Guidance: Reflect on your interests, the current trends in the field, and the available resources. Consult with mentors and refer to the previous section for more insights into selecting the perfect topic.
- Conduct Thorough Research: Guidance: Use reliable sources like academic journals, books, and reputable online resources. Gather diverse viewpoints on the topic and keep track of the sources for citation.
- Develop a Strong Thesis Statement: Guidance: The thesis should encapsulate the main argument or focus of your paper. It should be clear, concise, and specific, providing a roadmap for the reader.
- Create an Outline: Guidance: Outline the main sections, including introduction, literature review, methodology, findings, discussion, conclusion, and references. An organized structure helps maintain coherence and logical flow.
- Write a Compelling Introduction: Guidance: Begin with a hook that grabs the reader’s attention, provide background information, and conclude with the thesis statement. The introduction sets the stage for the entire paper.
- Employ the Appropriate Methodology: Guidance: Choose the research methods that align with your research question and objectives. Explain the rationale behind your choices, ensuring that they adhere to ethical standards.
- Analyze Findings and Discuss Implications: Guidance: Present your research findings in a clear and unbiased manner. Discuss the implications of the results in the context of the existing literature and real-world applications.
- Conclude with Insight: Guidance: Summarize the main findings, restate the thesis in the context of the research, and discuss the potential limitations and future research directions. The conclusion should leave the reader with something to ponder.
- Adhere to Academic Formatting: Guidance: Follow the specific formatting guidelines required by your institution or the style guide (APA, MLA, etc.). Pay attention to citations, references, headings, and overall presentation.
- Revise and Proofread: Guidance: Allocate ample time for revising content, structure, and language. Use tools or seek help from peers or professionals for proofreading to ensure grammatical accuracy and clarity.
Writing a security management research paper is a rigorous and intellectually stimulating endeavor that requires meticulous planning, research, and execution. The tips provided in this guide are meant to facilitate a well-structured and insightful paper that adheres to academic excellence. By following these guidelines, you not only develop a comprehensive understanding of security management but also contribute valuable insights to this evolving field. Remember, writing is a process of exploration, articulation, and refinement. Embrace the challenge, learn from the journey, and take pride in the scholarly contribution you make through your research paper on security management.
iResearchNet’s Custom Research Paper Services
In the complex world of security management, crafting a top-notch research paper can be a daunting task. The landscape of security management is multifaceted, encompassing areas such as cybersecurity, risk analysis, policy development, physical security, and much more. For students juggling multiple responsibilities, producing a quality research paper on these intricate subjects may seem nearly impossible. That’s where iResearchNet comes into play. Offering tailor-made solutions to your academic needs, iResearchNet is your go-to service for custom security management research papers. Below are the features that make iResearchNet the ideal choice for your academic success.
- Expert Degree-Holding Writers: At iResearchNet, we employ writers who not only hold advanced degrees but also have extensive experience in security management. Their expertise ensures that your paper is insightful, well-researched, and academically sound.
- Custom Written Works: Every research paper is crafted from scratch, tailored to your specific needs, guidelines, and preferences. Our writers work closely with you to understand your vision, making the paper uniquely yours.
- In-Depth Research: Our team engages in thorough research, using reputable sources and cutting-edge methodologies. This diligent approach guarantees a comprehensive understanding of the subject and a well-rounded paper.
- Custom Formatting: Adhering to academic standards is crucial, and our writers are skilled in various formatting styles. Whether APA, MLA, Chicago/Turabian, or Harvard, your paper will be formatted to perfection.
- Top Quality: Quality is at the core of our services. From the initial draft to the final submission, we maintain the highest standards of excellence, ensuring that your paper stands out.
- Customized Solutions: We recognize that each student’s needs are unique. Hence, our solutions are not one-size-fits-all but are customized to meet your specific requirements, timelines, and academic level.
- Flexible Pricing: Quality doesn’t have to break the bank. Our pricing structure is designed to be affordable and flexible, providing various options to fit different budgets.
- Short Deadlines: Whether you’re facing a last-minute crunch or planning ahead, our writers can accommodate tight deadlines. Even within as short as 3 hours, we deliver without compromising on quality.
- Timely Delivery: Your time is valuable, and we respect that. Our commitment to timely delivery ensures that you receive your paper well before the deadline, giving you ample time for review.
- 24/7 Support: Questions or concerns? Our support team is available around the clock. With 24/7 assistance, you can rest assured that help is always just a click away.
- Absolute Privacy: Your privacy is our priority. We employ stringent security measures to protect your personal information. With iResearchNet, your details are safe, secure, and confidential.
- Easy Order Tracking: With our user-friendly tracking system, you can easily monitor the progress of your order. Stay updated, provide feedback, and enjoy a smooth and transparent process.
- Money Back Guarantee: Your satisfaction is our goal. If, for any reason, our services do not meet your expectations, our money-back guarantee ensures that you are not at a loss.
iResearchNet’s custom security management research paper services are more than just a promise; they are a commitment to excellence, convenience, and integrity. Our blend of expert writers, personalized solutions, quality assurance, and robust support makes us the preferred choice for students across the globe. Dive into the world of security management without the stress of paper writing, knowing that iResearchNet has got your back. Embark on your academic journey with confidence and trust in a partner who understands your needs and shares your pursuit of excellence. With iResearchNet, you’re not just ordering a paper; you’re investing in your future.
Secure Your Academic Success Today
Are you feeling overwhelmed with the prospect of writing your security management research paper? Perhaps you’re struggling to find the right topic, or the research is becoming a tedious task? You don’t have to go through this alone. With iResearchNet’s specialized writing services, all your academic challenges can be turned into opportunities for success.
What sets iResearchNet apart from other writing services is not just our expertise and quality but our understanding of students’ needs. We know that every research paper is not just a task but a step towards your future career in security management. That’s why we invest our best resources to make sure your paper is nothing short of perfect. Our expert writers, meticulous research, and dedication to your satisfaction are all geared towards one goal – helping you excel.
We don’t just write papers; we create opportunities for learning and growth. When you choose iResearchNet, you’re not only receiving a top-notch research paper but also gaining access to a treasure trove of knowledge in security management. With our 24/7 support, flexible pricing, and customizable solutions, your success is no longer a distant dream but a tangible reality.
Take the step towards a brighter academic future. Don’t let the burden of research and writing hold you back from achieving your best. Click the button below to place your order and begin a collaborative journey with iResearchNet. With our secure and user-friendly platform, ordering your custom security management research paper is just a few clicks away. Empower yourself with the right partner, and let iResearchNet pave the way to your academic success.
ORDER HIGH QUALITY CUSTOM PAPER

Numbers, Facts and Trends Shaping Your World
Read our research on:
Full Topic List
Regions & Countries
- Publications
- Our Methods
- Short Reads
- Tools & Resources
Read Our Research On:
Key findings about Americans and data privacy
Many Americans have endless digital tools at their fingertips. And each device, site or app collects, analyzes and uses personal data. What does this mean for Americans now that so much of their day-to-day life leaves a digital footprint?
Pew Research Center has a long record of studying Americans’ views of privacy and their personal data, as well as their online habits. This study sought to understand how people think about each of these things – and what, if anything, they do to manage their privacy online. ( Read the full report .)
This survey was conducted among 5,101 U.S. adults from May 15 to 21, 2023. Everyone who took part in the survey is a member of the Center’s American Trends Panel (ATP), an online survey panel that is recruited through national, random sampling of residential addresses. This way nearly all U.S. adults have a chance of selection. The survey is weighted to be representative of the U.S. adult population by gender, race and ethnicity, partisan affiliation, education and other categories. Read more about the ATP’s methodology .
Here are the questions used for this analysis , along with responses, and its methodology .
Here are nine takeaways from a new Pew Research Center report exploring these issues.
Americans, especially Republicans, are growing more concerned about how the government uses the data it collects about them. About seven-in-ten U.S. adults (71%) say they are very or somewhat concerned about this, up from 64% in 2019. Concern has grown among Republicans and those who lean Republican but has held steady among Democrats and Democratic leaners.
Many Americans have little trust in companies to use AI responsibly. Among those who have heard of artificial intelligence (AI):
- 70% say they have little to no trust in companies to make responsible decisions about how they use AI in their products.
- 81% say the information companies collect will be used in ways that people are not comfortable with
- 80% say it will be used in ways that were not originally intended.
Still, 62% of those who have heard of AI say companies using it to analyze personal details could make life easier.
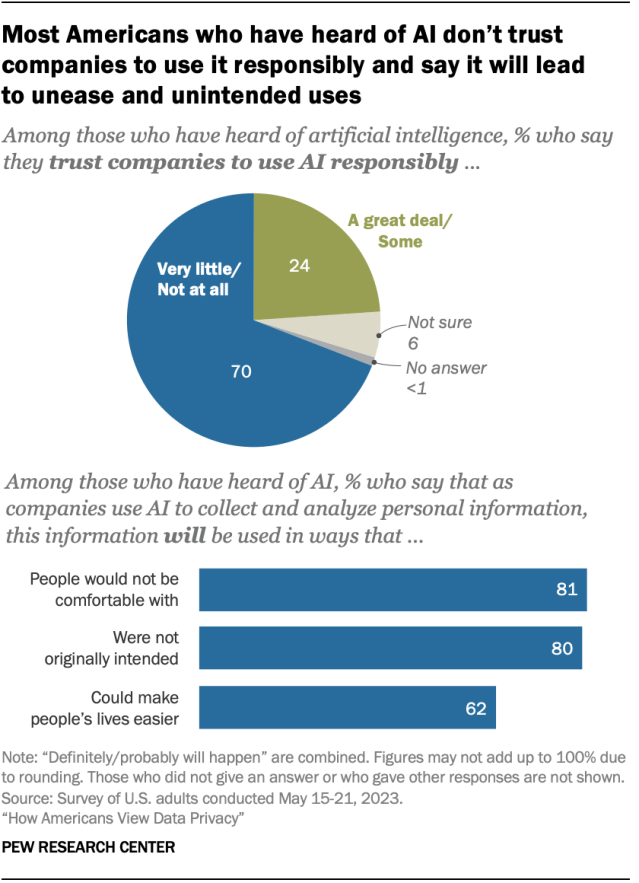
Many trust themselves to make the right decisions but are skeptical their actions matter. About eight-in-ten (78%) say they trust themselves to make the right decisions to protect their personal information.
But a majority (61%) are skeptical anything they do will make much difference. And only about one-in-five are confident that those with access to their personal information will treat it responsibly.
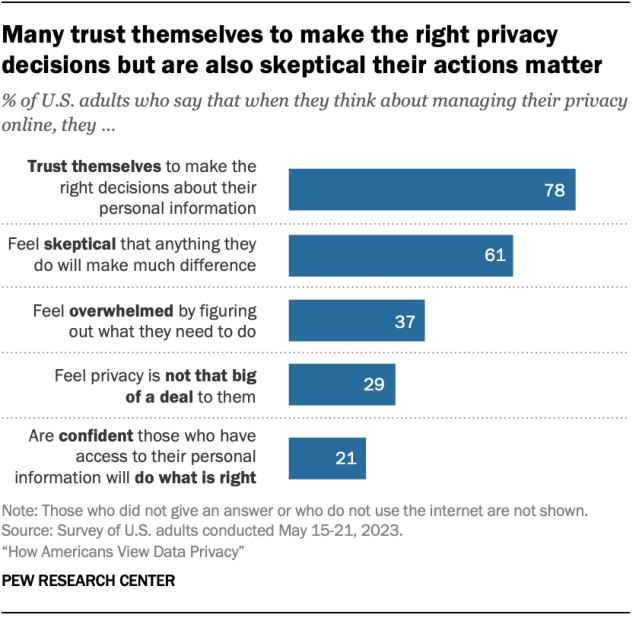
More than half of Americans (56%) say they always, almost always or often click “agree” without reading privacy policies. Another 22% say they do this sometimes and 18% rarely or never do this.
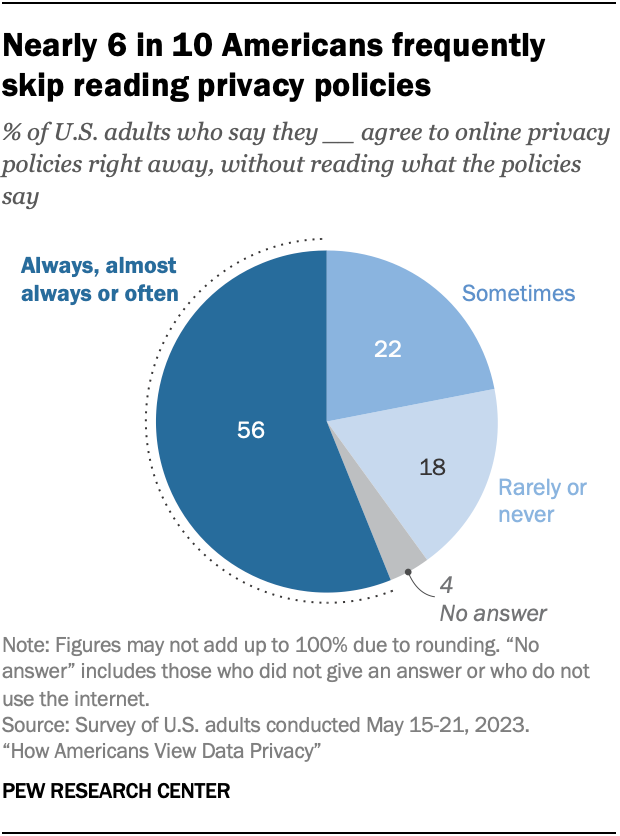
People are also largely skeptical that privacy policies do what they’re intended to do. About six-in-ten Americans (61%) think they’re ineffective at explaining how companies use people’s data.
About seven-in-ten Americans are overwhelmed by the number of passwords they have to remember. And nearly half (45%) report feeling anxious about whether their passwords are strong and secure.
Despite these concerns, only half of adults say they typically choose passwords that are more secure, even if they are harder to remember. A slightly smaller share (46%) opts for passwords that are easier to remember, even if they are less secure.
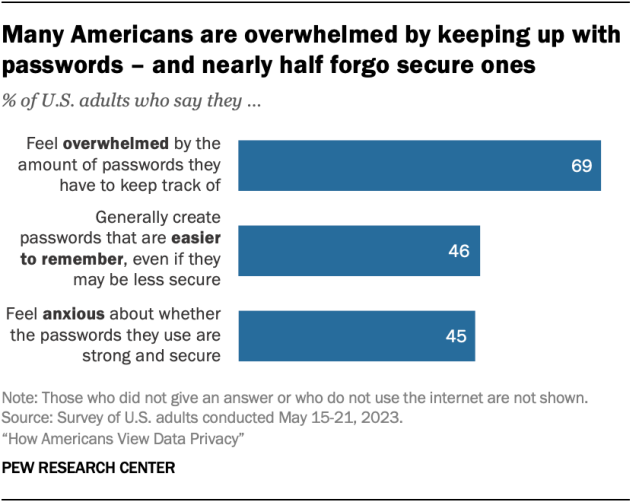
Some Americans have been targets of data breaches and hacking. In the past 12 months:
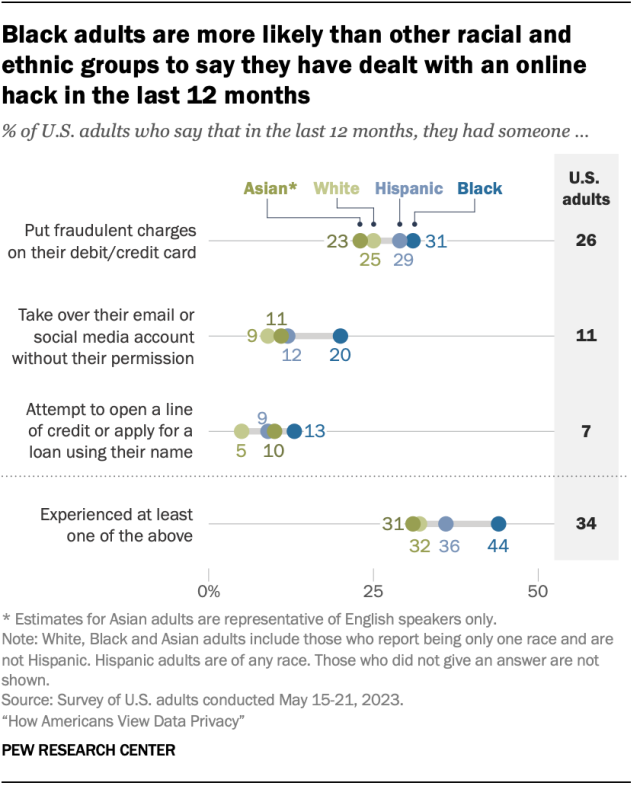
- Roughly a quarter of Americans (26%) say someone put fraudulent charges on their debit or credit card.
- A smaller share say they have had someone take over their email or social media account without their permission (11%).
- And 7% have had someone attempt to open a line of credit or apply for a loan using their name.
In total, 34% of Americans have experienced at least one of these issues in the past year. However, Black Americans are more likely than members of other racial and ethnic groups to have faced this.
Americans have little faith that social media executives will protect user privacy. Some 77% of Americans have little or no trust in leaders of social media companies to publicly admit mistakes and take responsibility for data misuse.
They are no more optimistic about the government reining them in: 71% have little to no trust that tech leaders will be held accountable for their missteps.
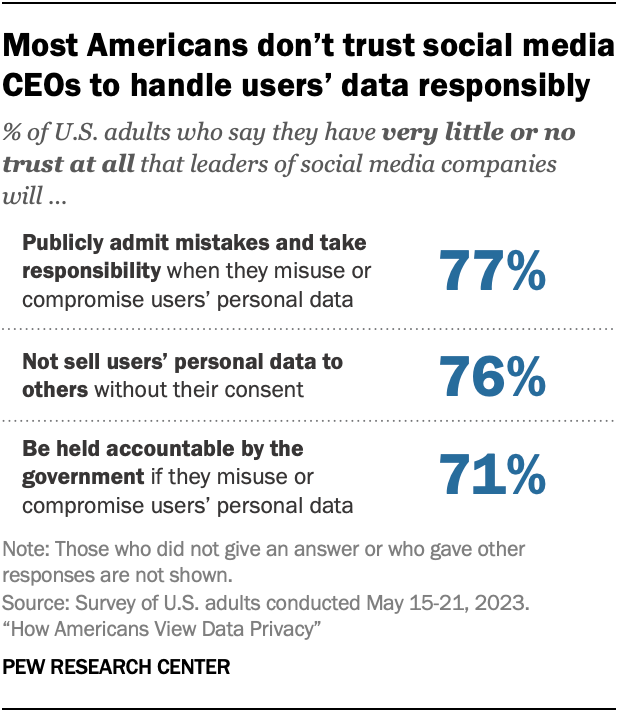
There is bipartisan support for more regulation to protect personal information. Some 78% of Democrats and 68% of Republicans think there should be more government regulation of what companies can do with customers’ personal information.
These findings are largely similar to our 2019 survey , which also showed strong support for increased regulation across parties.
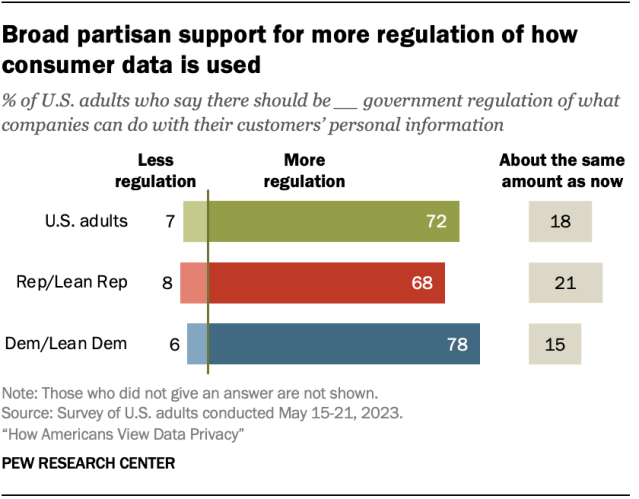
About nine-in-ten Americans (89%) are concerned about social media sites knowing personal information about children. Most Americans are also concerned about advertisers using data about children’s online activities to target ads to them (85%) and online games tracking children on the internet (84%).
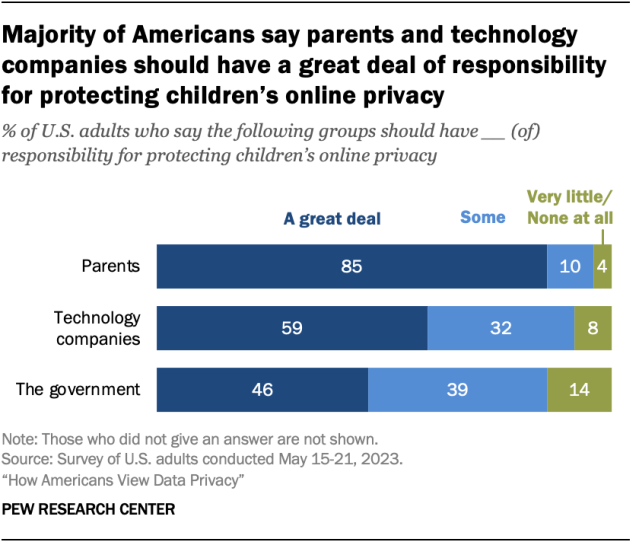
When it comes to who should be responsible for protecting kids’ online privacy, a vast majority (85%) says parents should bear a great deal of the responsibility. Still, roughly six-in-ten say the same about technology companies, and just under half believe the government should have a great deal of responsibility.
Note: Here are the questions used for this analysis , along with responses, and its methodology .
- Artificial Intelligence
- Online Privacy & Security
- Privacy Rights
- Social Media

Many Americans think generative AI programs should credit the sources they rely on
Americans’ use of chatgpt is ticking up, but few trust its election information, q&a: how we used large language models to identify guests on popular podcasts, striking findings from 2023, what the data says about americans’ views of artificial intelligence, most popular.
1615 L St. NW, Suite 800 Washington, DC 20036 USA (+1) 202-419-4300 | Main (+1) 202-857-8562 | Fax (+1) 202-419-4372 | Media Inquiries
Research Topics
- Age & Generations
- Coronavirus (COVID-19)
- Economy & Work
- Family & Relationships
- Gender & LGBTQ
- Immigration & Migration
- International Affairs
- Internet & Technology
- Methodological Research
- News Habits & Media
- Non-U.S. Governments
- Other Topics
- Politics & Policy
- Race & Ethnicity
- Email Newsletters
ABOUT PEW RESEARCH CENTER Pew Research Center is a nonpartisan fact tank that informs the public about the issues, attitudes and trends shaping the world. It conducts public opinion polling, demographic research, media content analysis and other empirical social science research. Pew Research Center does not take policy positions. It is a subsidiary of The Pew Charitable Trusts .
Copyright 2024 Pew Research Center
Terms & Conditions
Privacy Policy
Cookie Settings
Reprints, Permissions & Use Policy
Four things to know about research security
This article summarizes four areas of guidance that MIT research administrators should be aware of, for your own knowledge and to support the valuable advice you provide to your colleagues in research.
Maintaining research security is all about preserving the integrity of the research enterprise and the public’s trust while we pursue MIT’s core mission in research and teaching.
There are four things you can do to help with this, as a research administrator:
- Know when to ask for help
- Recognize risks and learn how to mitigate them
- Understand the difference between institutional responsibilities and outside professional activities
- Think critically before using generative AI tools
1. Know when to ask for help
The Office of the Vice President for Research (VPR) has developed a Discussion Guide on Research Security and Compliance to support principal investigators (PIs) in fostering an open dialogue with their research groups and advisees on key topics. The guide was designed for use as a conversational tool to support informal discussions in a setting such as a lab meeting, where it’s important for PIs to establish clear expectations with their group members.
However, research administrators may also find it serves as a useful primer or onboarding resource with respect to some of the key principles and policies affecting MIT research groups: transparent reporting, export controls, cyber security, international travel, and working outside the research group. The guide is not comprehensive; rather, it is intended to help researchers identify situations that require particular care. The guide points to several key resources for help — including [email protected] , which you can use to contact the Research Compliance team in VPR for advice on matters of research security and compliance at any time.
2. Recognize risks and learn how to mitigate them
As Maria Zuber and Richard Lester noted in a March 2024 letter , “Many worthwhile activities that advance MIT’s research and teaching mission may nevertheless pose some amount of risk in the current global context.”
“With well-informed judgment,” they added, “such risks can often be mitigated or eliminated.”
A new VPR webpage on Assessing and Mitigating Risk compiles requirements and guidance associated with a range of academic and research activities, including:
- Participation in talent recruitment programs
- Informal international collaborations
- Hosting students, researchers, and visitors from outside the US
- Accepting gifts
- Traveling abroad
- Participating in executive and professional activities
- Mentoring, advising, or tutoring non–MIT-enrolled students
- Taking a sabbatical or leave of absence from MIT
- Lectures, teaching engagements, or serving on review panels
3. Understand the difference between institutional responsibilities and outside professional activities
Outside professional activities (OPA) can create potential conflicts of interest or commitment. As OPA reporting season approaches in May, take a few minutes to review current guidance from the Office of the Provost. A new webpage on outside professional activities summarizes the internal MIT reporting requirements, including:
- Examples of the types of activities that are, or are not, necessary to report.
- Clarification on how faculty and others with consulting privileges may use a limited amount of Institute time to pursue OPA. Note that this varies by role.
- Guidance on pursuing OPA while on leave/sabbatical or while on a visa.
- Expectations regarding the involvement of other MIT personnel or resources in OPA.
- Additional considerations relating to external academic appointments, consulting, new commercial ventures or start-ups, and international OPA.
4. Think critically before using generative AI tools
IS&T has released new guidance, developed with the Office of General Counsel, on the use of generative AI tools .
We encourage you to read the full guidance, but research administrators should particularly take note of this point:
Do not enter MIT proprietary information, third party information, or data classified as Medium Risk or High Risk into publicly available generative AI tools or services not subject to an Institute licensing agreement.
Examples of such information and data include:
- Non-public research results and data
- Unpublished research papers
- Confidential information received from third parties (such as research sponsors and collaborators)
- Unpublished invention disclosures and patent applications
- Institute financial and human resources information
- Personally identifiable information (including, for example, student records, medical records)
- Any information subject to legal or regulatory requirements necessitating its proper safeguarding and handling
- And any other information not intended to be freely available to the general public, or to the MIT community without access controls.
A few examples of generative AI tools that are NOT licensed by MIT (at time of publication) include Midjourney, Stable Diffusion, and OpenAI’s ChatGPT and DALL-E.
IS&T has published a list of tools that are licensed for use by the MIT community . For more information on MIT’s approach, please review the full guidance from IS&T
- Uniform Guidance Fixed Rate Requirements
- F&A Methodology
- F&A Components
- MIT Use of a de minimis Rate
- Fund Account Overhead Rates
- Allocation Rates
- Determination of On-Campus and Off-Campus Rates
- Employee Benefits (EB) Rates
- Vacation Accrual Rates
- Graduate Research Assistant Tuition Subsidy
- Historical RA Salary Levels
- MIT Facts and Profile Information
- Classification of Sponsored Projects
- Types of Sponsored Awards
- How Are Sponsored Projects Generated?
- Cost Principles and Unallowable Costs
- Direct and Indirect Costs
- Pre-Proposals / Letters of Intent
- MIT Investigator Status
- Components of a Proposal
- Special Reviews
- Applying Through Workspace
- Proposal Preparation Checklist
- Proposals and Confidential Information
- Personnel Costs
- Subcontracts and Consultants
- Annotated Budget Justification - Federal Research
- Annotated Budget Justification - Non-Federal Research
- Annotated Budget Justification - Federal Non-Research
- Annotated Budget Justification - Non-Federal Non-Research
- Kuali Coeus Approval Mapping
- Roles and Responsibilities
- Submission of Revised Budgets
- Standard Contract Terms and Conditions
- Contractual Obligations and Problematic Terms and Conditions
- Review and Negotiation of Federal Contract and Grant Terms and Conditions
- Industrial Collaboration
- International Activities
- MIT Export Control - Export Policies
- Nondisclosure and Confidentiality Agreements
- Negative Confirmation On Award Notices
- Routing and Acceptance of the Award Notice
- COI and Special Review Hold Notice Definitions
- Limiting Long-Term WBS Account Structures
- SAP Project WBS Element Conditions
- Kuali Coeus Electronic Document Storage (EDS)
- Billing Agreements
- PI Absence from Project
- Cost Transfers
- Equipment Threshold
- Uniform Guidance and the FAR
- MIT Standard Terms and Policies
- Guidelines for Charging Faculty Summer Salary
- Key Personnel
- Limitations on Funds - Federal Contracts
- Managing Salary Costs
- Monitoring Project Budgets
- Monthly Reconciliation and Review
- No-Cost Extensions
- Reporting Requirements
- Return of Unexpended Funds to Foundations
- Determining the Sponsor Approved Budget (SAB)
- Working With the Sponsor Approved Budget (SAB)
- Sponsor Approved Budget (SAB) and Child Account Budgets
- Sponsor Approved Budget (SAB) and Prior Approvals
- Submitting an SAB Change Request
- When a PI Leaves MIT
- Research Performance Progress Reports
- Closing Out Fixed Price Awards
- Closeout of Subawards
- Record Retention
- Early Termination
- Reporting FAQs
- Using SciENcv
- AFOSR No-Cost Extension Process
- Terms and Conditions
- New ONR Account Set Ups
- Department of Defense Disclosure Guidance
- Department of Energy / Office of Science Disclosure Guidance
- Introduction to Industrial Sponsors
- General Considerations for Industrial Proposals
- SRC Guidance to Faculty Considering Applying for SRC Funding
- Find Specific RFP Information
- Industrial Proposal Checklist
- Proposal Formats
- Special Requirements
- Deadline Cycles
- Model Proposals
- Non-Competitive Industrial Proposals
- Master and Alliance Agreements With Non-Standard Proposal Processes
- Template Agreements
- New Consortium Agreements
- Competitive Industrial Proposals
- Collaborative (No-cost) Research Agreements
- National Aeronautics and Space Administration Disclosure Guidance
- NASA Graduate Research Fellowship Programs
- NASA PI Status and Definitions
- NIH Checklists and Preparation Guides
- National Institutes of Health Disclosure Guidance
- Human Subjects and NIH Proposals
- NIH Data Management and Sharing
- NIH Research Performance Progress Reports
- Grant Opportunities for Academic Liaison with Industry (GOALI) proposals
- MIT Guidance Regarding the NSF CAREER Program
- Research Experiences for Undergraduates (REU) Supplements
- National Science Foundation Disclosure Guidance
- NSF Proposals: Administrative Review Stage
- NSF Collaborations
- NSF Pre-Award and Post-Award Actions
- NSF Reporting
- NSF Frequently Asked Questions
- NSF Safe and Inclusive Working Environment
- Process, Roles and Responsibilities
- What Is Allowable/Eligible Cost Sharing?
- MIT’s Preferred Cost Sharing Funds
- Third-Party Cost Sharing
- Showing Cost Sharing in a Proposal Budget
- Sponsor Specific Instructions Regarding Location in the Proposal
- Funding F&A Costs as Cost Sharing
- Using Faculty Effort for Cost Sharing
- Information about Completing the Cost Sharing Template
- NSF Cost Sharing Policy
- Tracking/Reporting Cost Sharing
- Special Cost Sharing Topics
- International Activities Examples
- Rubicon Fellowships
- Marie Skłodowska-Curie Fellowships
- Criteria for Subrecipients
- Subawards at Proposal
- Requesting New Subawards
- Managing Subawards
- RAS Subaward Team Contacts
- Funding and Approval
- Proposal Phase
- Award Set-up
- Monitoring Research During Project Period
- Closeout Phase
- Voluntary Cost Sharing
- Sponsor-Specific Guidance
- Audits and Auditors
- Upcoming Trainings and Events
- Research Administration Practices (RAP)
- NCURA Virtual Workshops and Webinars
- Guide to RA Resources and Training
- Career Paths
- Newsletters
- Tools and Systems
- Award Closeout & Audits
- Award Setup
- Cost Sharing
- Export Control
- Financial Conflict of Interest
- Kuali Coeus
- Project Monitoring
- Proposal Preparation & Submission
- Research Sub Awards
- Research Administration Email Lists
- RAS Operations
- VPR Research Administration Organization Chart
- By department
- By administrator
- Research Administrator Day
- News & Announcements
- Onsite searching on the VPR public websites

Information Security Research Paper Topics
What is the importance of information security research paper topics? In this article, we will discuss more information in this title. Read this article so you can have knowledge of this study.
What is the Importance of Information Security Research Paper Topics?
An information security research paper should explore topics in the field of information security, including cryptography, computer network security, and data protection . Also, the paper should answer questions about how to keep data safe from hackers and other threats.
Information security is very important for the company or organization because the data that the company has is very important for business, so that information should be kept safe. The hacker can break into the system and can take data from the company.
Because of this, the company’s data is in danger, so to avoid this risk, companies need to hire information security researchers. Also, it is to identify threats and develop strategies to protect their data.
The paper should include research results about information security technology. Also, the paper should explore how this technology can be to protect data.
Topics for Next Generation Internet Researchers
“What are the topics for next-generation internet researchers?” is one of the most frequently asked questions by students who are interested in researching on the internet. Below, you will find information about this title. Take a look at it so you can know about this study.
The Internet is now the backbone of every business. The services that are over the internet, such as online shopping, online banking, social networking websites, and the like rely on internet technology. Also, businesses that provide services or products can market their products to customers over the internet.
The development of internet technology has many new jobs for people who work in many different fields, ranging from computer science to business. The development of the Internet has even a new field of study in which students can study to become experts on the Internet. These experts are called next-generation internet researchers.
What Do Technical Writers Do?
Technical writers, also known as technical writers, create manuals and other documents for products and services. They also provide instructions about how to use these products and services. Their job is to ensure that the users of these products and services will be able to use them easily and efficiently.
Technical writers may work for companies that design products, such as computer software programs or mobile apps. Also, they may work for companies that sell products or services.
For example, technical writers can work for a company that designs and sells computer software to accounting. Their job would be to write manuals and other documents about how to use their accounting software program.
Technical writers face certain risks when they do their job. First, they can suffer from repetitive stress injuries if they spend a lot of time doing tasks that involve typing.
Technical writers also face risks related to their safety and security . For example, some companies hire technical writers on a freelance basis.
Freelance technical writers often work from home and communicate with clients and other people via email and instant messaging. This is a good way for them to earn money because they do not have to pay for office space or health insurance.
In conclusion, technical writers have many different responsibilities, and they may work for different types of employers. To succeed in this career, technical writers need to know how to use a variety of computer programs and other technology.
Leave a Comment Cancel Reply
Your email address will not be published. Required fields are marked *
Save my name, email, and website in this browser for the next time I comment.

- Privacy Overview
- Strictly Necessary Cookies
This website uses cookies so that we can provide you with the best user experience possible. Cookie information is stored in your browser and performs functions such as recognising you when you return to our website and helping our team to understand which sections of the website you find most interesting and useful.
Strictly Necessary Cookie should be enabled at all times so that we can save your preferences for cookie settings.
If you disable this cookie, we will not be able to save your preferences. This means that every time you visit this website you will need to enable or disable cookies again.
Search code, repositories, users, issues, pull requests...
Provide feedback.
We read every piece of feedback, and take your input very seriously.
Saved searches
Use saved searches to filter your results more quickly.
To see all available qualifiers, see our documentation .
information-security-research
Here are 4 public repositories matching this topic..., ansjdnakjdnajkd / ios.
Most usable tools for iOS penetration testing
- Updated Nov 6, 2023
w8mej / Threat_Modeling_Bank
A curated threat modeling library collection
- Updated Dec 1, 2023
scific-conference / scific
Student Conference of Information, Functional and Cybersecurity (SCIFiC)
- Updated Nov 30, 2023
Hunterfosho / Hunterfosho
Welcome to my Cyber Security Repo
- Updated Mar 15, 2023
Improve this page
Add a description, image, and links to the information-security-research topic page so that developers can more easily learn about it.
Curate this topic
Add this topic to your repo
To associate your repository with the information-security-research topic, visit your repo's landing page and select "manage topics."

An official website of the United States government
Here’s how you know
Official websites use .gov A .gov website belongs to an official government organization in the United States.
Secure .gov websites use HTTPS A lock ( Lock A locked padlock ) or https:// means you’ve safely connected to the .gov website. Share sensitive information only on official, secure websites.
- Publication Library
Ammonia Port Preparedness and Emergency Response Fact Sheet
AmPPER will enable the Department of Homeland Security Science and Technology Directorate to provide critical information on ammonia storage and its potential impact on ports and surrounding communities. Through data-driven mitigation and resilience recommendations, we empower the U.S. Coast Guard, FEMA, and emergency response communities to enhance preparedness.
- Fact Sheets
- Science and Technology
- Climate Change

IMAGES
VIDEO
COMMENTS
204 Research Topics on Technology & Computer Science. A List of 580 Interesting Research Topics [2024 Edition] A List of 179 Problem Solution Essay Topics & Questions. 193 Interesting Proposal Essay Topics and Ideas. 226 Research Topics on Criminal Justice & Criminology.
Cyber Security Research Topics. Cyber Security Research Topics are as follows: The role of machine learning in detecting cyber threats. The impact of cloud computing on cyber security. Cyber warfare and its effects on national security. The rise of ransomware attacks and their prevention methods.
The concept of cybersecurity refers to cracking the security mechanisms that break in dynamic environments. Implementing Cyber Security Project topics and cyber security thesis topics/ideas helps overcome attacks and take mitigation approaches to security risks and threats in real-time. Undoubtedly, it focuses on events injected into the system, data, and the whole network to attack/disturb it.
Cybersecurity-Related Research Topics. Developing machine learning algorithms for early detection of cybersecurity threats. The use of artificial intelligence in optimizing network traffic for telecommunication companies. Investigating the impact of quantum computing on existing encryption methods.
9 👩💻Cyber Security Topics on Computer and Software. There are many reasons to choose cyber security research topics for writing purposes. First, cyber security is a growing field, with many new and exciting developments happening all the time. This makes it an ideal topic to write about, as there is always something new to learn and ...
Explore the latest full-text research PDFs, articles, conference papers, preprints and more on INFORMATION SECURITY. Find methods information, sources, references or conduct a literature review on ...
Operational Security Research Topics In 2023. Securing containerized applications in cloud environments. Implementing secure remote access policies for remote workers. Evaluating the effectiveness of endpoint protection solutions.
Topic modeling of Information Systems Security research between 1990 and 2020. Delphi study of CISOs to rank order important Information Systems Security concerns. Explores the gap between what practitioners consider to be important and what researchers are currently studying.
These great topics for cybersecurity can make you more knowledgeable about the current trends. Risk management in computing. The most common causes of a data breach in the 21 st. The best way to protect your device and synchronize the data. The significance of computer forensics in the current digital era.
Direct impact vs audience impact. As a security professional, it's tempting to rate a research project's impact based on the direct impact. For example, over the years I've seen a range of serious flaws in a certain popular CDN, and I suspect that if I directly targeted it, I could find multiple ways to take over all their customers ...
Share sensitive information only on official, secure websites. ... Topics Select a term to learn more about it, and to see CSRC Projects, Publications, News, Events and Presentations on that topic. ... Energy Independence and Security Act; Federal Information Security Modernization Act; First Responder Network Authority;
Each of these working groups focuses on a unique topic or aspect of cloud security, including AI, IoT, DevSecOps, and much more. Then, every month, research publications created by these working groups and reviewed by the industry are released on the CSA website, free for anyone to download and read. In this article, we've defined 12 CSA ...
Technology allows individuals and organizations access to more comprehensive and diverse information, but this access requires that electronic information, networks, data repositories, and data transmissions be adequately safeguarded. RAND has developed a large body of research focused on recognizing the potential threats to information security and data integrity, as well as implications for ...
The cyber security of a company can be compromised in many ways when it comes to software and computer administration. As such, software and computer administration is a great sources of cybersecurity research paper topics. Here are some of the best topics in this category. Evaluation of the operation of antimalware in preventing cyber attacks.
Cybersecurity research aims to protect computer systems, networks, and data from unauthorised access, theft, or damage. It involves studying and developing methods and techniques to identify, understand, and mitigate cyber threats and vulnerabilities. The field can be divided into theoretical and applied research and faces challenges such as.
Security. Cyber threats have grown exponentially as the modern web and powerful AI systems have proliferated. We're designing systems to secure the hybrid cloud and AI for sensitive datasets to ensure organizations can continue to operate safely and securely. Cloud computing and AI have dramatically transformed global computational ...
Topic modeling of Information Systems Security research between 1990 and 2020. • Delphi study of CISOs to rank order important Information Systems Security concerns. • Explores the gap between what practitioners consider to be important and what researchers are currently studying. • Develop a research agenda in Information Systems Security.
Network security. Application security. Information security. Operational security. Disaster recovery and business continuity. Therefore, your cybersecurity topics for research should: Examine the common security breaches in systems and networks. Offer practical ways of protecting computers from such attacks.
Trend #1: Single Photon Generation. A cybersecurity research team at the University of Sydney has solved an issue that could lead to a major breakthrough in the way information is transmitted, allowing for more secure computer systems worldwide. The issue is the ability to generate single photons — tiny particles of light — that carry ...
Enterprise cyberdefense strategies must include network security best practices. Get advice on essential network security topics such as remote access, VPNs, zero-trust security, NDR, endpoint management, IoT security, hybrid security, Secure Access Service Edge, mobile security and more. More about Network Security.
Security management research paper topics are a critical area of study for management students looking to explore the complex world of safeguarding organizational assets. Security management covers various facets, including information security, physical security, risk management, compliance, and more. The study of security management is increasingly relevant in our technology-driven world.
About six-in-ten Americans (61%) think they're ineffective at explaining how companies use people's data. About seven-in-ten Americans are overwhelmed by the number of passwords they have to remember. And nearly half (45%) report feeling anxious about whether their passwords are strong and secure. Despite these concerns, only half of adults ...
Maintaining research security is all about preserving the integrity of the research enterprise and the public's trust while we pursue MIT's core mission in research and teaching. There are four things you can do to help with this, as a research administrator: Know when to ask for help. Recognize risks and learn how to mitigate them.
An information security research paper should explore topics in the field of information security, including cryptography, computer network security, and data protection. Also, the paper should answer questions about how to keep data safe from hackers and other threats. Information security is very important for the company or organization ...
Add this topic to your repo. To associate your repository with the information-security-research topic, visit your repo's landing page and select "manage topics." GitHub is where people build software. More than 100 million people use GitHub to discover, fork, and contribute to over 420 million projects.
AmPPER will enable the Department of Homeland Security Science and Technology Directorate to provide critical information on ammonia storage and its potential impact on ports and surrounding communities. Through data-driven mitigation and resilience recommendations, we empower the U.S. Coast Guard, FEMA, and emergency response communities to enhance preparedness.