Browse Course Material
Course info, instructors.
- Prof. Erik Demaine
- Prof. Srini Devadas
- Prof. Nancy Lynch

Departments
- Electrical Engineering and Computer Science
- Mathematics
As Taught In
- Algorithms and Data Structures
- Computer Networks
- Cryptography
- Applied Mathematics
Learning Resource Types
Design and analysis of algorithms, lecture 22: cryptography: encryption.
Description: In this lecture, Professor Devadas continues with cryptography, introducing encryption methods.
Instructors: Srinivas Devadas
- Download video
- Download transcript

You are leaving MIT OpenCourseWare
Symmetric and Asymmetric Key Encryption – Explained in Plain English

Encryption is a way of scrambling data so that it can only be read by the intended recipient.
Encryption is an integral part of our daily lives – whether you are sending messages to friends on WhatsApp, visiting a website and your browser is making sure it's legitimate, or entering your bank details when buying something online. Encryption protects your data from potentially malicious and prying eyes.
This article will cover:
- Encryption algorithms and keys
- Symmetric and asymmetric key encryption
- How TLS/SSL uses both symmetric and asymmetric encryption
Encryption Algorithms and Keys
At the start of this article, I described encryption as a way of scrambling data so that it can only be read by the intended recipient. Let’s break down what this means.
Let's say you want to write a letter to your friend and want to ensure that only the friend can read its contents. How would you prevent the prying eyes of all the intermediaries the letter could pass through before it gets to your friend? That is, how do you prevent the postman, the concierge in their building, or one of their friends from reading the letter?
You start with an unscrambled letter that anyone can read. This is called plaintext . To scramble the contents of the message, you need an encryption algorithm and a key . The encryption algorithm uses the key to scramble the contents of the message. This encrypted message is called ciphertext .
The process of encryption is shown in the image below:
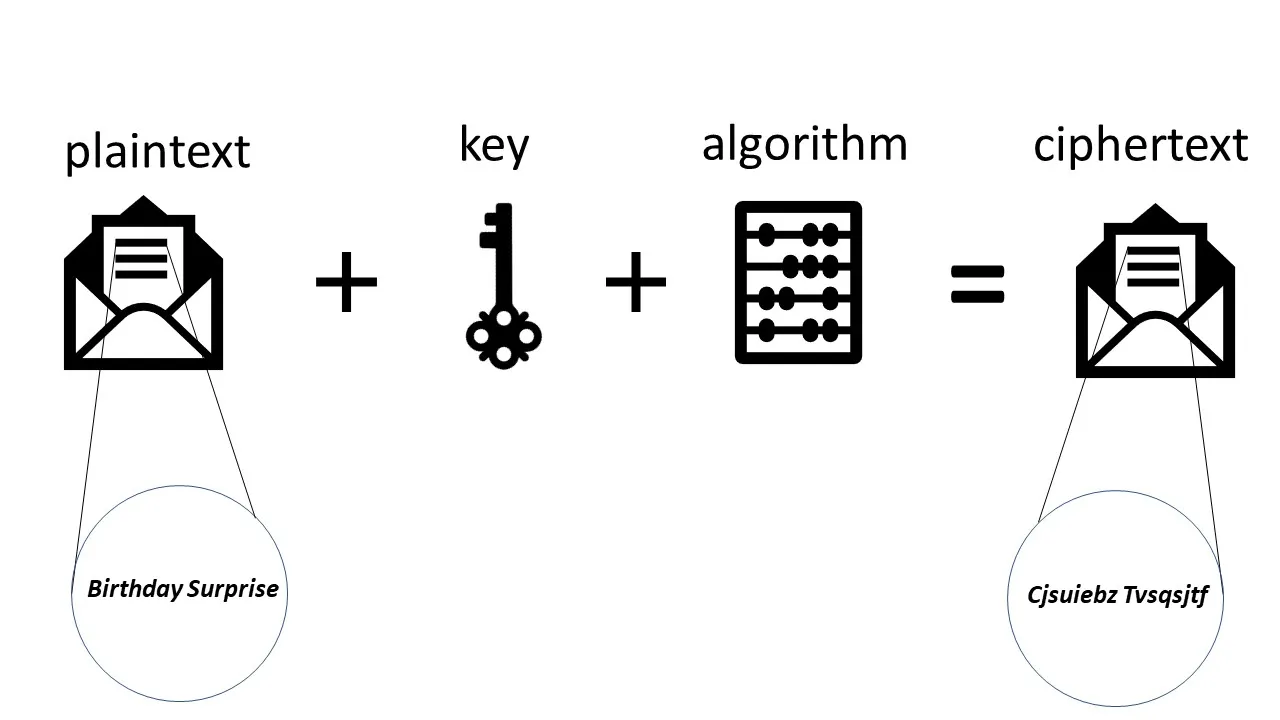
When your friend gets the message, they will need to descramble it using the algorithm and the key . This is illustrated below:
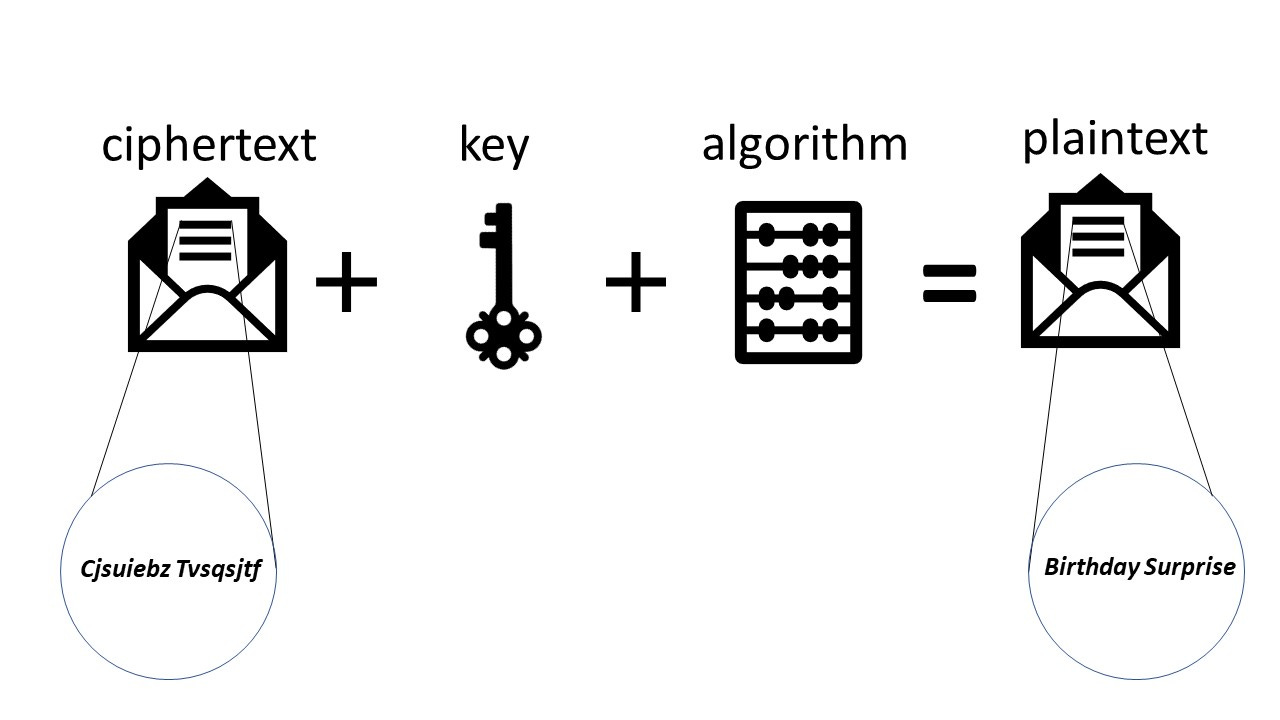
The two key ingredients needed to send a message to your friend that only they can read is an encryption algorithm and a key .
The encryption algorithm is simply a mathematical formula designed to scramble data, while the key is used as part of the formula. The encryption algorithm is generic, but the key, used as an input to the algorithm, is what ensures the uniqueness of the scrambled data.
Let’s look at one of the simplest encryption algorithms, called the Caesar Cipher. In its simplest form, this algorithm simply replaces each letter by the next letter in the alphabet. So A becomes B, and B becomes C and so on.
With this algorithm, the text ‘Birthday Surprise’ becomes ‘Cjsuiebz Tvsqsjtf’, indistinguishable from gibberish to the untrained eye.
With the Caesar Cipher example, the algorithm is the formula used to replace each letter of the alphabet with another. The key is the number of shifts made between each letter. With a key of 0, A is A, an obviously poor choice of key as the data is unscrambled. With a key of 1, A becomes B. With a key of 10, A becomes K.
The Caesar Cipher is a relatively poor encryption algorithm. Why? Since there are only 26 letters in the English language, you can only produce a maximum of 25 possible ciphertexts. If you don’t have the key, you only need to shift each letter up to 25 times until you see coherent words and sentences, at which point you know that you have successfully decrypted the message.
A bad encryption algorithm is one that is easily decrypted by using a small amount of brute force (that is, trying every possible permutation) – and 25 possible ciphertexts is an objectively small number of possible options to go through.
Modern encryption algorithms like AES-256 used by AWS, GCP, and Azure for encrypting data are considerably more complicated and secure than the Caesar Cipher. Based on current computing capability, it would take trillions and trillions of years for the most advanced supercomputer to use brute force to decrypt data encrypted using AES-256 [ 1 ]. Even the universe is not that old.
Symmetric and Asymmetric Key Encryption
The core of any encryption process is the encryption algorithm and the key. There are many types of encryption algorithms. But there are, broadly speaking, two types of keys – symmetric and asymmetric keys.
In symmetric key encryption, the same key used to encrypt the data is used to decrypt the data. In asymmetric key encryption, one key is used to only encrypt the data (the public key) and another key is used to decrypt (the private key).
Asymmetric key encryption
First, let’s look at asymmetric key encryption with a simple analogy.
Imagine you wanted to send something to your friend, but it was absolutely essential that nobody else, except your friend, could have access to that object. So, your friend buys an indestructible box, fabricated from the strongest metal on the planet, and sends it to you so that you can place the object in it. Your friend also sends you the key that can only be used to lock the box.
Now, this box has one more special property. It has two keyholes. One keyhole to open the box, another to lock the box.
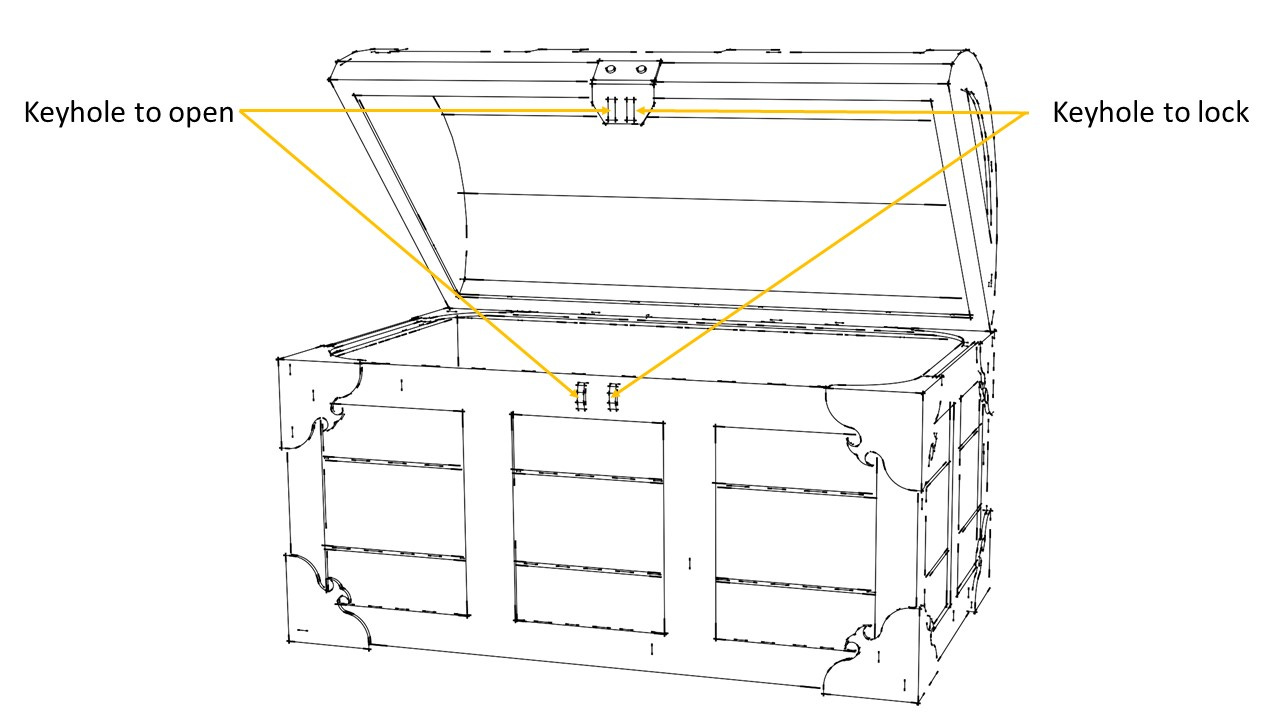
Naturally, this box will also need two keys – one to open and another to lock it.
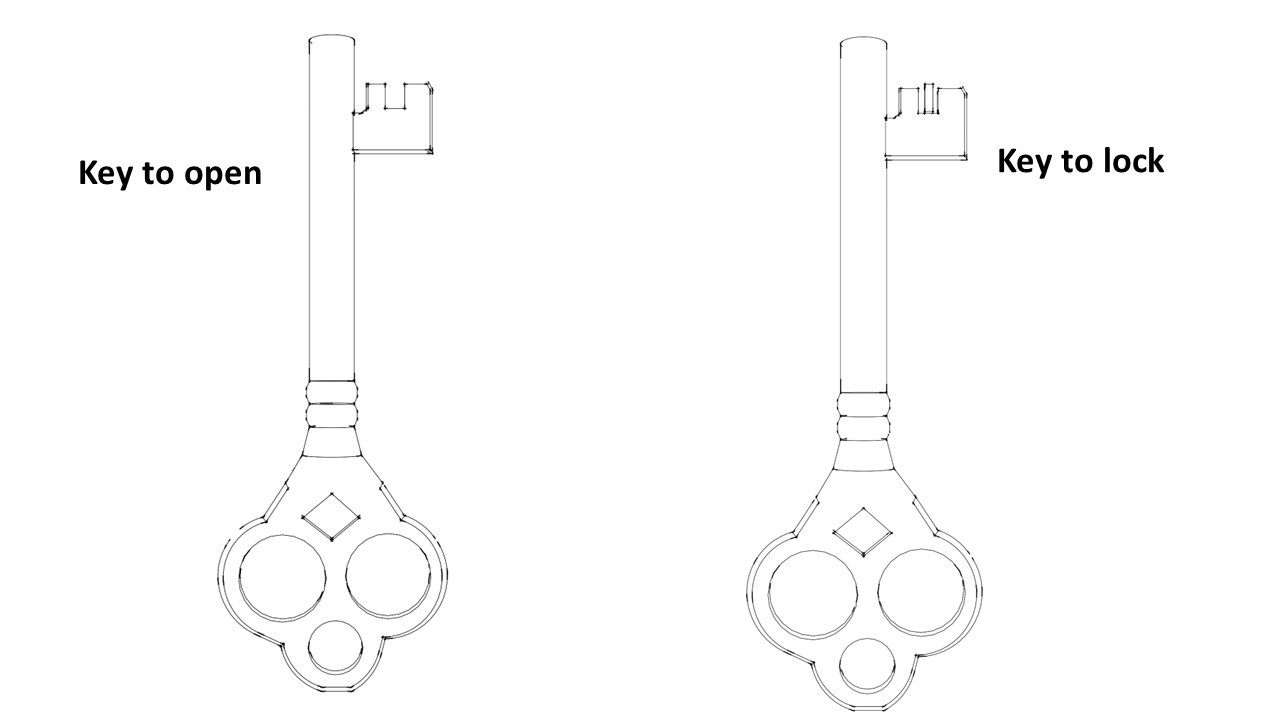
Both keys are similar, but not identical. As you can see in the image above, for example, the key used to open the box has two prongs while the key used to lock the box has three prongs.
As the sender of the object, all you have is the box to place the object in and a key to lock the box. Only your friend has the key that can unlock the box.
The key used to lock the box is called the public key, and cannot be used to open it, as that requires the private key. If anyone intercepted the package and made a copy of the public key, it could not be used to open the box, only to lock it. Only the person who holds the private key can open the box.
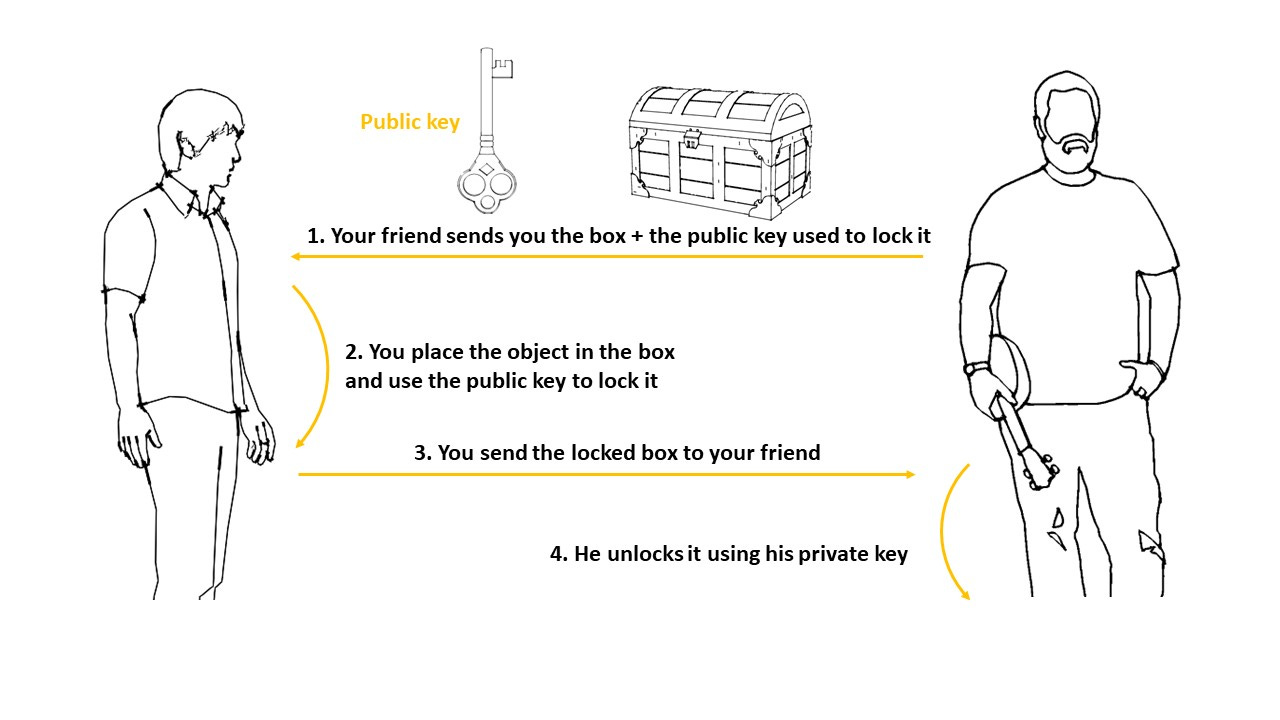
Asymmetric key encryption is used when there are two or more parties involved in the transfer of data. This type of encryption is used for encrypting data in transit, that is encrypting data being sent between two or more systems. The most popular example of asymmetric key encryption is RSA .
Symmetric key encryption
Symmetric key encryption uses the same key for encryption and decryption. This makes sharing the key difficult, as anyone who intercepts the message and sees the key can then decrypt your data.
This is why symmetric key encryption is generally used for encrypting data at rest. AES-256 is the most popular symmetric key encryption algorithm. It is used by AWS for encrypting data stored in hard disks (EBS volumes) and S3 buckets. GCP and Azure also use it for encrypting data at rest.
How TLS/SSL Uses Both Symmetric and Asymmetric Encryption
The main strength of symmetric key encryption is that it is computationally easier and faster to encrypt and decrypt data using a single key, just as it is easier to build a box with a single lock and key.
The weakness of symmetric key encryption is that if the key is exposed, your data is no longer securely encrypted. So, if you needed to share the key with an external party, there is a risk that the key could be exposed, leaving your data at risk of being decrypted.
Symmetric key encryption is ideal for encrypting data at rest, where you do not need to share the key with another system.
With asymmetric encryption, this is not a problem since two separate keys are used – the public key to encrypt data and the private key to decrypt data.
The public key can be easily shared with anyone and poses no risk to your data being decrypted, since the private key is needed for decryption.
The drawback of asymmetric key encryption is that the encryption and decryption process is slower and more complicated. Asymmetric key encryption is ideal for encrypting data in transit, where you need to share the key with another system.
What if there was a way of getting the speed and computational simplicity of symmetric encryption without increasing the risk of exposing your keys?
TLS/SSL encryption use both symmetric and asymmetric keys to encrypt data in transit, and is used with the HTTP protocol for secure communications over a computer network.
TLS/SSL Encryption Explained
TSL (Transport Layer Security) and SSL (Secure Sockets Layer) are often used interchangeably to mean the same thing. But when people say SSL, they often mean TLS.
TLS is generally considered more secure than SSL due to several improvements made to the protocol, such as stronger cryptographic algorithms. Due to security concerns with SSL, most modern web browsers and applications have dropped support for SSL and only support TLS. As a result, TLS has become the standard for secure communication over the internet.
How to Use Symmetric and Asymmetric Encryption at the Same Time
Let's say you want to securely send a parcel to your friend. But you don’t want to keep using the special indestructible box that has two keyholes and two locks. It is expensive, heavy and impractical to use for frequent communications. You still want to use an indestructible box, but one that is simpler, with a single lock and key.
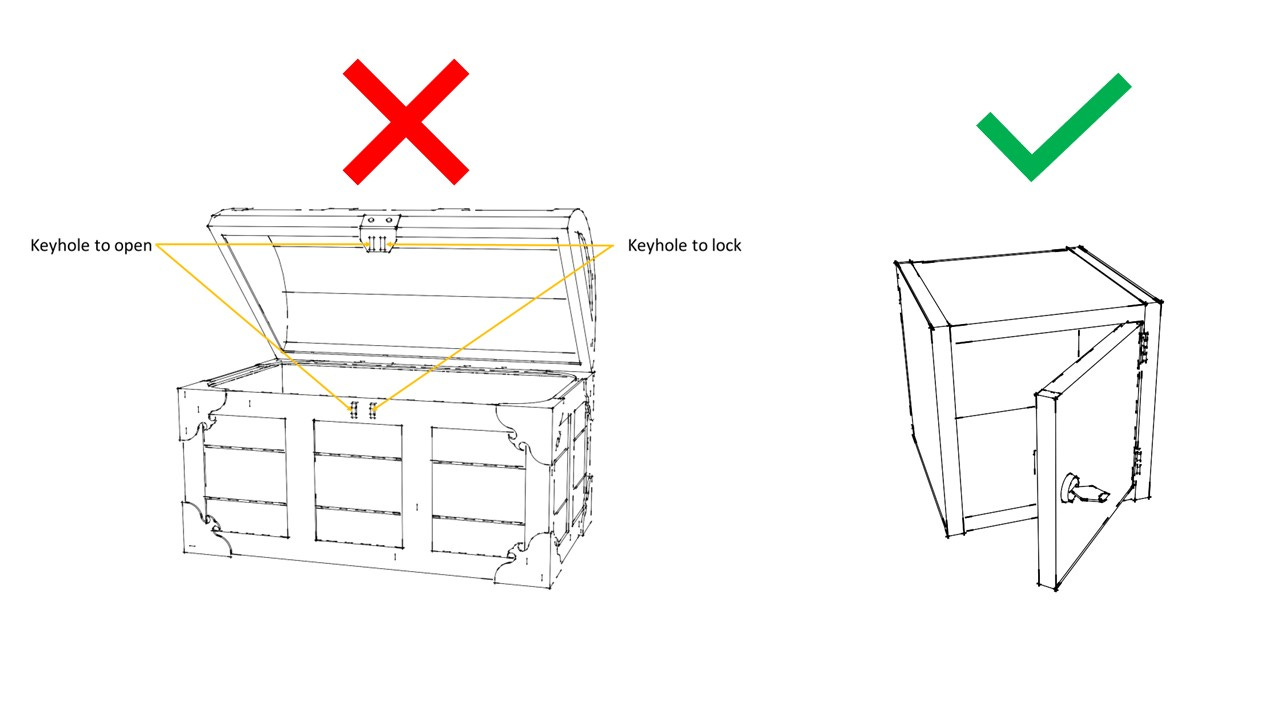
However, if you are using a box with only a single lock and key, you now need to figure out how to securely share the key for that simpler box with your friend.
Since the same key is used to both open and lock it, you cant just send the key to your friend without somehow protecting it first. If the key is intercepted and a copy is taken by someone, they can now open your box and take what is inside.
How can you securely share this key with your friend so that you can use this simpler box for future communication?
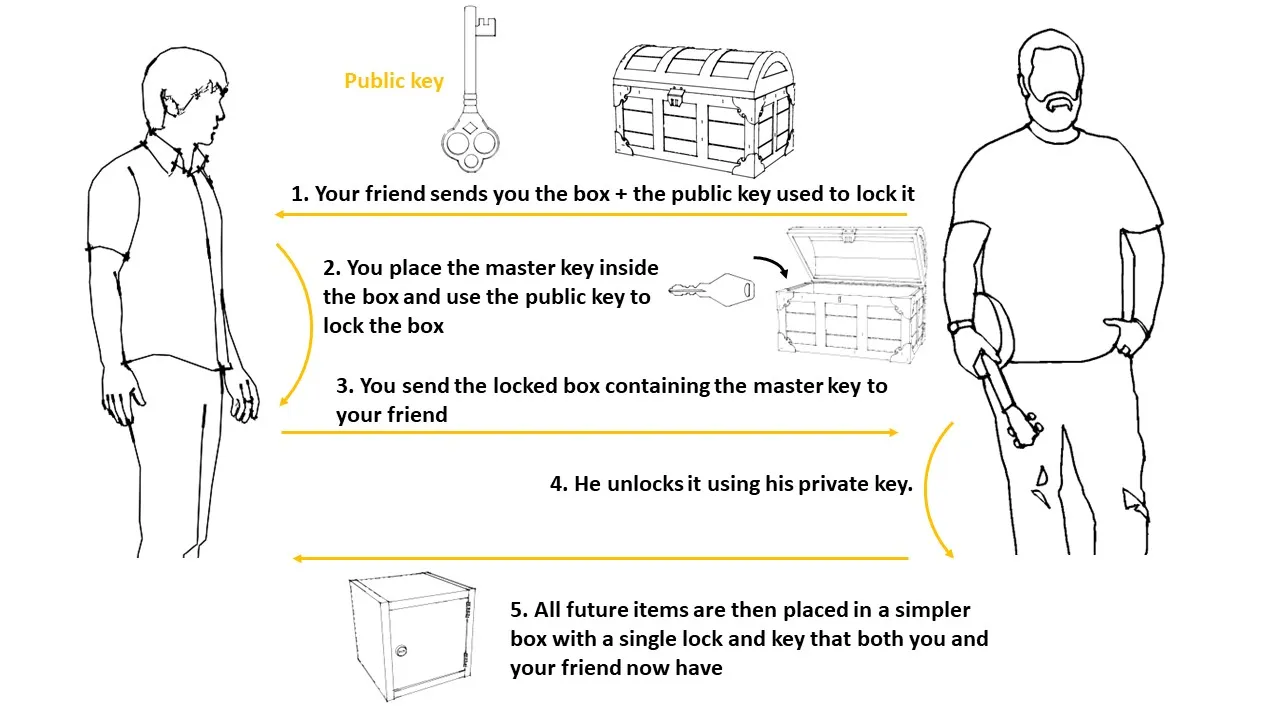
- First, your friend sends the box with the two locks plus the public key used to lock it. But you don’t want to keep using this box. You will only use this box once – to transfer the key for another simpler box that you will use for future exchanges.
- You place the master key that will be used in future exchanges inside this box and lock it with the public key sent by your friend.
- You send the locked box which contains a copy of the master key inside back to your friend.
- Your friend uses his private key to open the box. Now you both have the master key and can be sure no one else has it since it was sent in a secure box
- All future items are then placed in this simpler box with a single lock and key which can be opened and locked using the master key you just sent to your friend.
TLS/SSL Encryption Sequence
The analogy in the previous section neatly maps to how TLS/SSL encryption actually works. But there are some prerequisite steps which I ignored in this analogy, like creating a TCP connection and the server sending its certificate (Steps 1 and 2 below).
Also, Step 6 is a simplification of the process. In reality, the master key is used to generate a further set of keys that the client and server will use to encrypt and decrypt messages and also to authenticate that the messages were indeed sent by the client and server.
To read more about the low level detail, I’d recommend Chapter 8 of " Computer Networking " by Kurose & Ross.
But, at a high level, the sequence is as follows:
- Client establishes TCP connection with the server
- Client verifies that the server is who it says it is – server sends certificate which has the public key. The accompanying private key remains with the server.
- Client creates a master secret key and uses the server's public key to encrypt it. This master secret key is a symmetric key so the same key is used for encryption and decryption.
- Client sends the encrypted master secret key to the server.
- Server decrypts the encrypted master key using its private key.
- All future messages between client and server now use the symmetric master key to encrypt and decrypt messages.
Best of Both Worlds
Using both symmetric and asymmetric key encryption gives you the speed of symmetric key encryption without compromising on the extra security provided by asymmetric key encryption.
But nothing comes for free, of course. With TLS, there is an added layer of complexity since you need to first use asymmetric keys to establish a secure connection before exchanging the symmetric key for future communication.
So by using both symmetric and asymmetric encryption, TLS/SSL gets the best of both worlds with limited downsides.
Read more posts .
If you read this far, thank the author to show them you care. Say Thanks
Learn to code for free. freeCodeCamp's open source curriculum has helped more than 40,000 people get jobs as developers. Get started
What Is Encryption?
Learn about the types of encryption, along with the benefits and challenges.
- Get a Threat Assessment
- Read the Outbreak Alerts Report

Encryption Definition
Encryption is a form of data security in which information is converted to ciphertext. Only authorized people who have the key can decipher the code and access the original plaintext information.
In even simpler terms, encryption is a way to render data unreadable to an unauthorized party. This serves to thwart cybercriminals, who may have used quite sophisticated means to gain access to a corporate network—only to find out that the data is unreadable and therefore useless.
Encryption not only ensures the confidentiality of data or messages but it also provides authentication and integrity, proving that the underlying data or messages have not been altered in any way from their original state.
How Encryption Works
Original information, or plain text, might be something as simple as "Hello, world!" As cipher text, this might appear as something confusing like 7*#0+gvU2x—something seemingly random or unrelated to the original plaintext.
Encryption, however, is a logical process, whereby the party receiving the encrypted data—but also in possession of the key—can simply decrypt the data and turn it back into plaintext.
For decades, attackers have tried by brute force—essentially, by trying over and over again—to figure out such keys. Cybercriminals increasingly have access to stronger computing power such that sometimes, when vulnerabilities exist, they are able to gain access.
Data needs to be encrypted when it is in two different states: "at rest," when it is stored, such as in a database; or "in transit," while it is being accessed or transmitted between parties.
An encryption algorithm is a mathematical formula used to transform plaintext (data) into ciphertext. An algorithm will use the key to alter the data in a predictable way. Even though the encrypted data appears to be random, it can actually be turned back into plaintext by using the key again. Some commonly used encryption algorithms include Blowfish, Advanced Encryption Standard (AES), Rivest Cipher 4 (RC4), RC5, RC6, Data Encryption Standard (DES), and Twofish.
Encryption has evolved over time, from a protocol that was used only by governments for top-secret operations to an everyday must-have for organizations to ensure the security and privacy of their data.
Get a Cybersecurity Threat Assessment
Know your vulnerabilities - get the facts about your security risk and at no cost.
Types of Encryption
There are many different types of encryption, each with its own benefit and use case.
Symmetric encryption
In this simple encryption method, only one secret key is used to both cipher and decipher information. While the oldest and best-known encryption technique, the main drawback is that both parties need to have the key used to encrypt the data before they can decrypt it. Symmetric encryption algorithms include AES-128, AES-192, and AES-256. Because it is less complex and executes faster, symmetric encryption is the preferred method for transmitting data in bulk.
Asymmetric encryption
Also known as public key cryptography , asymmetric encryption is a relatively new method that uses two different but related keys to encrypt and decrypt data. One key is secret and one key is public. The public key is used to encrypt data, and the private key is used to decrypt (and vice versa). Security of the public key is not needed because it is publicly available and can be shared over the internet.
Asymmetric encryption presents a much stronger option for ensuring the security of information transmitted over the internet. Websites are secured using Secure Socket Layer (SSL) or Transport Layer Security (TLS) certificates. A query to a web server sends back a copy of the digital certificate, and a public key can be extracted from that certificate, while the private key stays private.
Data Encryption Standard (DES)
DES is a deprecated symmetric key method of data encryption. DES works by using the same key to encrypt and decrypt a message, so both the sender and the receiver must have access to the same private key. DES has been superseded by the more secure AES algorithm. It was adopted by the U.S. government as an official standard in 1977 for the encryption of government computer data. It can be said that DES was the impetus for the modern cryptography and encryption industry.
Triple Data Encryption Standard (3DES)
The Triple Data Encryption Standard involved running the DES algorithm three times, with three separate keys. 3DES was largely seen as a stopgap measure, as the single DES algorithm was increasingly becoming seen as too weak to stand up to brute force attacks and the stronger AES was still under evaluation.
Rivest-Shamir-Adleman (RSA) is an algorithm and the basis of a cryptosystem—a suite of cryptographic algorithms used for specific security services or purposes. This enables public key encryption and is often used by browsers to connect to websites and by virtual private networks (VPNs). RSA is asymmetric, in which two different keys are used for encryption: one public and one private. If decryption is carried out with the public key, encryption is performed with the private key, or vice versa.
Advanced Encryption Standard (AES)
Developed in 1997 by the National Institute of Standards and Technology (NIST) as an alternative to the Data Encryption Standard, the Advanced Encryption Standard is a cipher chosen by the U.S. government to protect sensitive information. AES has three different key lengths to encrypt and decrypt a block of messages: 128-bit, 192-bit, and 256-bit. AES is widely used for protecting data at rest in such applications as databases and hard drives.
Encryption in the cloud
Cloud encryption is a service offered by cloud storage providers in which data is first encrypted using algorithms before being pushed to a storage cloud. Customers of a cloud storage provider must be aware of and comfortable with the level of depth of the provider's policies and procedures for encryption and encryption key management.
Because encryption consumes more bandwidth, many cloud providers only offer basic encryption on a few database fields, such as passwords and account numbers. This is often not enough for some organizations. So they rely on a Bring Your Own Encryption (BYOE) model in which they use their own encryption software and manage their own encryption keys to ensure a level of cloud computing security they are comfortable with.
As an opposite approach, Encryption as a Service (EaaS) has emerged as a simple, pay-as-you-go service customers can purchase from a cloud provider, managing encryption themselves in a multi-tenant environment.
End-to-End encryption
End-to-end encryption (E2EE) ensures that only the two users communicating with one another can read the messages. Even the intermediary, such as the telecom or internet service provider, cannot decrypt the messages. E2EE is generally seen as the most secure way to communicate privately and securely online. Examples of E2EE in use include the WhatsApp messaging service , which famously asserts that users' messages are secured with "locks."
The Benefits of Encryption
Privacy and security.
Encryption can prevent data breaches. Even if an attacker maliciously gains access to a network, if a device is encrypted, the device will still be secure, rendering attempts by the attacker to consume the data useless. Encryption ensures no one can read communications or data except the intended recipient or data owner. This prevents attackers from intercepting and accessing sensitive data.
Regulations
Encrypting data allows organizations to protect data and maintain privacy in accordance with industry regulations and government policy. Many industries, especially those in financial services and healthcare, have explicit rules on data protection. For example, the Gramm-Leach-Bliley Act requires financial institutions to let customers know how their data is being shared and also how their data is remaining protected. Encryption helps financial institutions comply with this act.
Secure internet browsing
Encryption also keeps users safe while browsing the internet. Earlier in the internet's history, attackers found ways to steal unencrypted information sent between users and web services over the Hypertext Transfer Protocol (HTTP). The standard to encrypt web content by running HTTP over the Secure Socket Layer protocol emerged, soon to be replaced with the Transport Layer Security protocol, enabling enterprises, publishers, and e-commerce providers to offer a secure experience for users.
With encryption, users feel safer entering personal information into webpages and carrying out financial or e-commerce transactions.
Encryption keeps sensitive data safe
Encryption will continue to be a core security feature in everything from video chats to e-commerce to social media. Basically, if it can be shared or stored, it will be encrypted. Both organizations and individual users would benefit from keeping on top of encryption standards to ensure that both their personal and professional data is safe from misuse or compromise.
Encrypt Data with a FortiGate Next-Generation Firewall
Encryption Challenges
Attackers will still attack even when they know that data or devices are encrypted. They figure that with some effort, they might get through. For many years, weak passwords served as the impetus for attackers to keep trying, as some sophisticated software could sooner or later figure out passwords.
Such brute force attacks have become more sophisticated, as attackers hope that by making thousands or even millions of guesses, they will figure out the key for decryption. However, most modern encryption methods, coupled with multi-factor authentication (MFA), are helping organizations to become more resistant to brute force attacks.
Cybersecurity Resources
- Cybersecurity
- Types of Cyber Attacks
- IT vs OT Cybersecurity
- AI Cybersecurity
- Cyber Threat Intelligence
- Cybersecurity Management
- Network Security
- Data Security
- Email Security
- Endpoint Security
- Web Security
- Enterprise Security
- Cybersecurity Mesh
Quick Links
- Fortinet Products
- Fortinet Demos
- Analyst Reports
- Editor's Choice: Tech Gifts for Mom
- New! iPad Air 6 Details
How to Apply Security in PowerPoint Presentations
Prevent your presentations from being viewed or changed by others
- Brock University
In This Article
Jump to a Section
Why Add Security
- Encrypt Your Presentations
- Save as Graphic Images
- Save as PDF
- Mark as Final Feature
What to Know
- Use the encryption feature in PowerPoint. Assign a password by going to Protect Presentation .
- Save the presentation as graphic images or a PDF file to keep the information visible but not easily editable.
- Use the Mark as Final feature to ensure that no further edits are made inadvertently.
This article explains several ways you can apply security in PowerPoint presentations. This information applies to PowerPoint 2019, 2016, 2013, 2010 and PowerPoint for Microsoft 365.
Security in PowerPoint is a concern when your presentation contains sensitive or confidential information or when you don't want anyone making changes to the presentation. Below are some of the methods used to secure presentations to avoid tampering with information or theft of your ideas.
Encrypt Your PowerPoint Presentations
Using the encryption feature in PowerPoint is a way to keep others from accessing your presentation. A password is assigned by you in the creation process of the presentation . The viewer must enter this password in order to open or modify your work.
Secure PowerPoint Slides by Saving as Graphic Images
Saving your completed slides as graphic images ensures that the information remains intact. This method takes a little more work, as you have to first create your slides, save them as pictures, and then reinsert them into new slides.
This method is one you would use if it is imperative that the content remains unchanged, as in the case of confidential financial data being presented to board members.
Save PowerPoint Presentations as a PDF File
Secure your PowerPoint presentation from any edits by saving, or publishing, it in PDF format . This retains all the formatting you applied, even when the viewing computer doesn't have those particular fonts, styles, or themes installed. This is a great option when you need to submit your work for review, but don't want the reader to make any changes.
Mark as Final Feature in PowerPoint
Once your presentation is complete and ready for prime time, use the Mark as Final feature to ensure that no further edits are made inadvertently.
Get the Latest Tech News Delivered Every Day
- How to Use Copilot in Powerpoint
- How to Make a PowerPoint Presentation
- How to Insert PDF Files Into PowerPoint Presentations
- Add Hyperlinks to PowerPoint Presentations
- How to Save PowerPoint Presentations as PDF Files
- Converting PowerPoint Presentations to Word Documents
- Tips for Solving Common PowerPoint Problems
- Print a PowerPoint Handout in PDF Format Without a Date
- How to Link to Other Slides or Websites in PowerPoint
- How to Do a Voiceover on PowerPoint
- Using Design Themes in PowerPoint
- How to Add an Excel Chart to a PowerPoint Presentation
- How to Merge PowerPoints
- Remove Slide Numbers From PowerPoint Slides
- PowerPoint Master Slide
- How to Use PowerPoint Slide Master Layouts

- Popular Categories
Powerpoint Templates
Icon Bundle
Kpi Dashboard
Professional
Business Plans
Swot Analysis
Gantt Chart
Business Proposal
Marketing Plan
Project Management
Business Case
Business Model
Cyber Security
Business PPT
Digital Marketing
Digital Transformation
Human Resources
Product Management
Artificial Intelligence
Company Profile
Acknowledgement PPT
PPT Presentation
Reports Brochures
One Page Pitch
Interview PPT
All Categories
Powerpoint Templates and Google slides for Encryption
Save your time and attract your audience with our fully editable ppt templates and slides..
Item 1 to 60 of 866 total items
- You're currently reading page 1

This slide represents the importance of data encryption in cloud security and what type of data should always be encrypted through private keys.Introducing Cloud Security Checklist Data Encryption Cloud Information Security to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Future Evaluation, Device Is Detected, Change Activities using this template. Grab it now to reap its full benefits.
This slide represents data encryption model for effective information security. It includes data encoding, data decoding, backup repository etc.Present the topic in a bit more detail with this Data Encryption Model For Effective Information Security Strategy SS. Use it as a tool for discussion and navigation on Backup Repository, Encrypted Data, Proper Decryption. This template is free to edit as deemed fit for your organization. Therefore download it now.
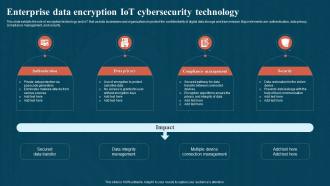
This slide exhibits the role of encryption technology and IoT that assists businesses and organizations to protect the confidentiality of digital data storage and transmission. Major elements are authentication, data privacy, compliance management, and security. Presenting our set of slides with Enterprise Data Encryption IoT Cybersecurity Technology. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Authentication, Privacy, Management.

This slide covers data protection and encryption framework in multi cloud with multi layer protection and data management. Deliver an outstanding presentation on the topic using this Data Protection Multi Cloud Data Encryption Cloud Architecture Review. Dispense information and present a thorough explanation of Object Store Appliance, Multi Cloud Data Encryption, Automated Encryption, Device Control using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
This colourful PowerPoint Illustration is perfect for illustrating the concept of cloud cryptography. It features a cloud with a lock and key, demonstrating the secure encryption of data stored in the cloud. Its a great way to visually explain the power of cloud cryptography.
Give your next presentation a sophisticated, yet modern look with this 100 percent editable Encryption key protection colored icon in powerpoint pptx png and editable eps format. Choose from a variety of customizable formats such as PPTx, png, eps. You can use these icons for your presentations, banners, templates, One-pagers that suit your business needs.
Presenting, internet of things encryption layout PowerPoint slide. Easily personalize this layout to choose the PPT layout, font, text, color, and design as per your way. This determined PPT design can be practiced by professionals for exhibiting their data modeling and banking applications related presentations. This template is well cooperative with Google Slides and can be easily saved into pdf or jpg formats. These pictures graphics do not pixelate when forecasted on a widescreen and are accessible in 16:9 fullscreen version.
Presenting our Symmetric Encryption Vs Asymmetric Encryption Ppt Powerpoint Presentation Example Cpb PowerPoint template design. This PowerPoint slide showcases four stages. It is useful to share insightful information on Symmetric Encryption VS Asymmetric Encryption This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
Presenting bitcoin encryption powerpoint slide icon. This is a bitcoin encryption powerpoint slide icon. This is a one stage process. The stages in this process are block chain, bitcoin wallet, list of record, cryptocurrency.

Presenting complete encryption powerpoint slide backgrounds. This is a complete encryption powerpoint slide backgrounds. This is a three stage process. The stages in this process are secure email, it security structure, cyber security policies, encrypted metadata.
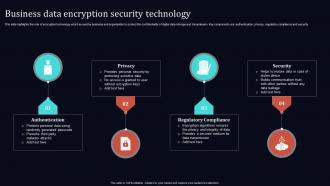
This slide highlights the role of encryption technology which is used by business and organisation to protect the confidentiality of digital data storage and transmission. Key components are authentication, privacy, regulatory compliance and security. Presenting our set of slides with name Business Data Encryption Security Technology. This exhibits information on four stages of the process. This is an easy-to-edit and innovatively designed PowerPoint template. So download immediately and highlight information on Privacy, Authentication, Regulatory Compliance, Security.

This colourful PowerPoint Illustration is perfect for data security presentations. It features a padlock in the centre of a blue and green circle, symbolizing the protection of confidential information. Use it to emphasize the importance of data security in your presentation.
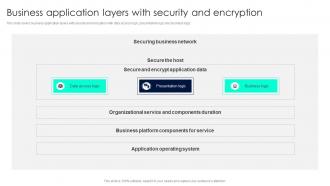
This slide covers business application layers with security and encryption with data access logic, presentation logic and business logic. Presenting our well structured Business Application Layers With Security And Encryption. The topics discussed in this slide are Business Application, Layers Security, Encryption. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
Introducing our premium set of slides with Data Encryption And Protection Standards Icon. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Data Encryption And Protection, Standards Icon. So download instantly and tailor it with your information.
This coloured powerpoint Illustration is perfect for any presentation on cyber security safety. It features a bright, eye catching design that will attract attention and help you illustrate your message. Ideal for use in educational and business settings.
This coloured PowerPoint Illustration depicts a data security concept, with a padlock and a key to represent secure data protection. It is ideal for presentations on data protection, cyber security, and other related topics.
This coloured PowerPoint Illustration provides a visually appealing representation of global data security. It is perfect for presentations and other documents to illustrate the importance of protecting data across the world.
This coloured PowerPoint Illustration is designed to represent healthcare cyber security. It features a blue shield with a white cross in the center, symbolizing protection against malicious cyber threats. It is a perfect visual aid for any presentation on the importance of cyber security in healthcare.
Presenting this set of slides with name Difference Compression Encryption Ppt Powerpoint Presentation Ideas Graphics Example Cpb. This is an editable Powerpoint five stages graphic that deals with topics like Difference Compression Encryption to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Presenting this set of slides with name Email Encryption Ppt Powerpoint Presentation Pictures Background Designs Cpb. This is an editable Powerpoint four stages graphic that deals with topics like Email Encryption to help convey your message better graphically. This product is a premium product available for immediate download, and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Presenting our set of slides with Blockchain Security Icon With Encryption Symbol. This exhibits information on one stage of the process. This is an easy-to-edit and innovatively designed PowerPoint template. So download immediately and highlight information on Blockchain Security Icon With Encryption Symbol.

Enthrall your audience with this Encryption For Data Privacy In Digital Age IT Powerpoint Presentation Slides. Increase your presentation threshold by deploying this well-crafted template. It acts as a great communication tool due to its well-researched content. It also contains stylized icons, graphics, visuals etc, which make it an immediate attention-grabber. Comprising two hundred fourty one slides, this complete deck is all you need to get noticed. All the slides and their content can be altered to suit your unique business setting. Not only that, other components and graphics can also be modified to add personal touches to this prefabricated set.

This complete deck covers various topics and highlights important concepts. It has PPT slides which cater to your business needs. This complete deck presentation emphasizes Encryption Implementation Strategies Powerpoint Presentation Slides and has templates with professional background images and relevant content. This deck consists of total of one hundred eight slides. Our designers have created customizable templates, keeping your convenience in mind. You can edit the color, text and font size with ease. Not just this, you can also add or delete the content if needed. Get access to this fully editable complete presentation by clicking the download button below.

Enthrall your audience with this Cloud Data Encryption Implementation Plan Powerpoint Presentation Slides. Increase your presentation threshold by deploying this well-crafted template. It acts as a great communication tool due to its well-researched content. It also contains stylized icons, graphics, visuals etc, which make it an immediate attention-grabber. Comprising sixty eight slides, this complete deck is all you need to get noticed. All the slides and their content can be altered to suit your unique business setting. Not only that, other components and graphics can also be modified to add personal touches to this prefabricated set.

If your company needs to submit a Encryption Framework Upgradation Proposal Powerpoint Presentation Slides look no further. Our researchers have analyzed thousands of proposals on this topic for effectiveness and conversion. Just download our template add your company data and submit to your client for a positive response.
Deliver a lucid presentation by utilizing this End To End Encryption Powerpoint PPT Template Bundles. Use it to present an overview of the topic with the right visuals, themes, shapes, and graphics. This is an expertly designed complete deck that reinforces positive thoughts and actions. Use it to provide visual cues to your audience and help them make informed decisions. A wide variety of discussion topics can be covered with this creative bundle such as End-To-End Encryption, Chat Privacy, Whatsapp Encryption, Encryption Challenges Solutions, Business Trends Encryption, Encryption Backup Systems. All the Twenty slides are available for immediate download and use. They can be edited and modified to add a personal touch to the presentation. This helps in creating a unique presentation every time. Not only that, with a host of editable features, this presentation can be used by any industry or business vertical depending on their needs and requirements. The compatibility with Google Slides is another feature to look out for in the PPT slideshow.

Engage buyer personas and boost brand awareness by pitching yourself using this prefabricated set. This Encryption Powerpoint PPT Template Bundles is a great tool to connect with your audience as it contains high-quality content and graphics. This helps in conveying your thoughts in a well-structured manner. It also helps you attain a competitive advantage because of its unique design and aesthetics. In addition to this, you can use this PPT design to portray information and educate your audience on various topics. With fourteen slides, this is a great design to use for your upcoming presentations. Not only is it cost-effective but also easily pliable depending on your needs and requirements. As such color, font, or any other design component can be altered. It is also available for immediate download in different formats such as PNG, JPG, etc. So, without any further ado, download it now.
Presenting Data Encryption in Ransomware Attacks. This PPT presentation is thoroughly researched by the experts, and every slide consists of appropriate content. It is well crafted and designed by our PowerPoint specialists. Suitable for use by managers, employees, and organizations. You can edit the color, text, icon, and font size to suit your requirements. The PPT also supports Google Slides. Even Premium Customer Support is also available. Download now and present with confidence.

Presenting Lack of Encryption as an Information Security Threat. This PPT presentation is thoroughly researched and each slide consists of appropriate content. Designed by PowerPoint specialists, this PPT is fully customizable alter the colors, text, icons, and font size to meet your needs. Compatible with Google Slides and backed by superior customer support. Download today to deliver your presentation confidently.

Presenting Encryption as a Type of Application Security. This PPT presentation is meticulously researched and each slide consists of relevant content. Designed by SlideTeams PowerPoint experts, this PPT is fully customizable alter the colors, text, icons, and font size to meet your requirements. Compatible with Google Slides and backed by excellent customer support. Download to present with poise and assurance.
Engage buyer personas and boost brand awareness by pitching yourself using this prefabricated set. This Blockchain Icon Symbol Circle Computers Encryption Security Technology is a great tool to connect with your audience as it contains high-quality content and graphics. This helps in conveying your thoughts in a well-structured manner. It also helps you attain a competitive advantage because of its unique design and aesthetics. In addition to this, you can use this PPT design to portray information and educate your audience on various topics. With twelve slides, this is a great design to use for your upcoming presentations. Not only is it cost-effective but also easily pliable depending on your needs and requirements. As such color, font, or any other design component can be altered. It is also available for immediate download in different formats such as PNG, JPG, etc. So, without any further ado, download it now.

Introduce your topic and host expert discussion sessions with this Firewall Enterprise Protection Security Installation Encryption. This template is designed using high-quality visuals, images, graphics, etc, that can be used to showcase your expertise. Different topics can be tackled using the twelve slides included in this template. You can present each topic on a different slide to help your audience interpret the information more effectively. Apart from this, this PPT slideshow is available in two screen sizes, standard and widescreen making its delivery more impactful. This will not only help in presenting a birds-eye view of the topic but also keep your audience engaged. Since this PPT slideshow utilizes well-researched content, it induces strategic thinking and helps you convey your message in the best possible manner. The biggest feature of this design is that it comes with a host of editable features like color, font, background, etc. So, grab it now to deliver a unique presentation every time.
This slide represents the dashboard which can be utilized by organization to monitor cloud security. It includes overall progress, number of critical risks identified, initiatives, incident management, compliance, patches, highest number of critical incidents, etc. Deliver an outstanding presentation on the topic using this Data Encryption Performance Tracking Dashboard Cloud Data Encryption. Dispense information and present a thorough explanation of Progress, Critital Risks Identified using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
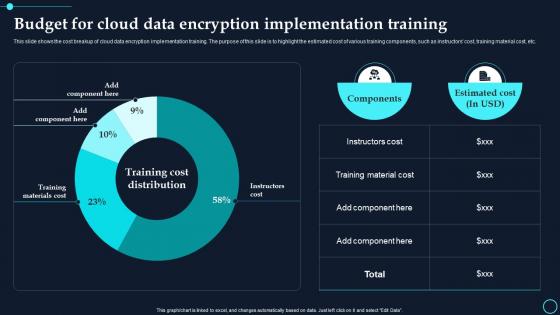
This slide shows the cost breakup of cloud data encryption implementation training. The purpose of this slide is to highlight the estimated cost of various training components, such as instructors cost, training material cost, etc. Deliver an outstanding presentation on the topic using this Budget For Cloud Data Encryption Implementation Training Cloud Data Encryption. Dispense information and present a thorough explanation of Components, Estimated Cost using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
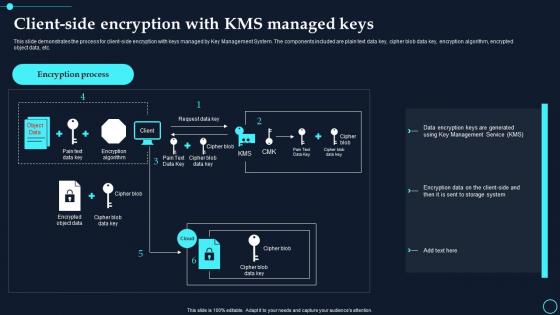
This slide demonstrates the process for client side encryption with keys managed by Key Management System. The components included are plain text data key, cipher blob data key, encryption algorithm, encrypted object data, etc. Deliver an outstanding presentation on the topic using this Client Side Encryption With Kms Managed Keys Cloud Data Encryption. Dispense information and present a thorough explanation of Encryption Process, Encryption Algorithm using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
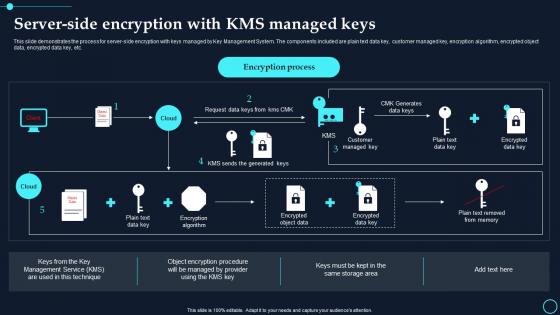
This slide demonstrates the process for server side encryption with keys managed by Key Management System. The components included are plain text data key, customer managed key, encryption algorithm, encrypted object data, encrypted data key, etc. Present the topic in a bit more detail with this Server Side Encryption With Kms Managed Keys Cloud Data Encryption. Use it as a tool for discussion and navigation on Encryption Process, Customer Managed Key. This template is free to edit as deemed fit for your organization. Therefore download it now.
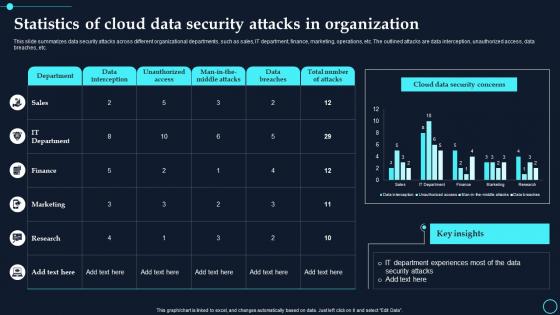
This slide summarizes data security attacks across different organizational departments, such as sales, IT department, finance, marketing, operations, etc. The outlined attacks are data interception, unauthorized access, data breaches, etc. Deliver an outstanding presentation on the topic using this Statistics Of Cloud Data Security Attacks In Organization Cloud Data Encryption. Dispense information and present a thorough explanation of Data Interception, Unauthorized Access using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
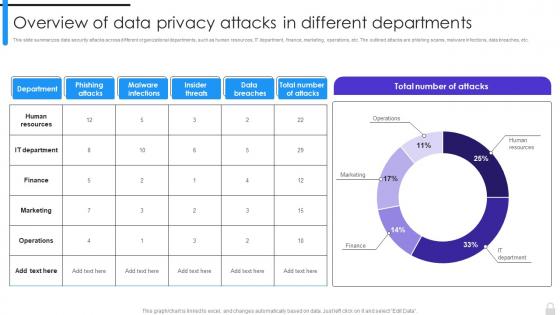
This slide summarizes data security attacks across different organizational departments, such as human resources, IT department, finance, marketing, operations, etc. The outlined attacks are phishing scams, malware infections, data breaches, etc. Present the topic in a bit more detail with this Encryption Implementation Strategies Overview Of Data Privacy Attacks In Different Departments. Use it as a tool for discussion and navigation on Human Resources, IT Department, Finance, Marketing, Operations. This template is free to edit as deemed fit for your organization. Therefore download it now.
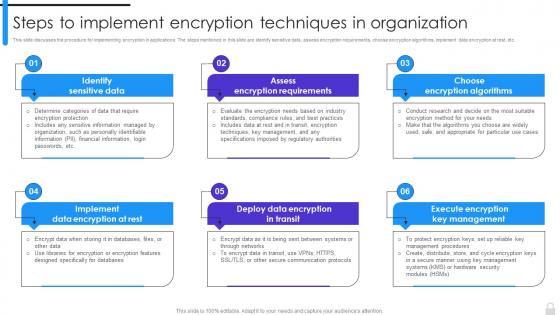
This slide discusses the procedure for implementing encryption in applications. The steps mentioned in this slide are identify sensitive data, assess encryption requirements, choose encryption algorithms, implement data encryption at rest, etc. Introducing Encryption Implementation Strategies Steps To Implement Encryption Techniques In Organization to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Implement Data Encryption At Rest, Deploy Data Encryption In Transit, Assess Encryption Requirements, Choose Encryption Algorithms, using this template. Grab it now to reap its full benefits.
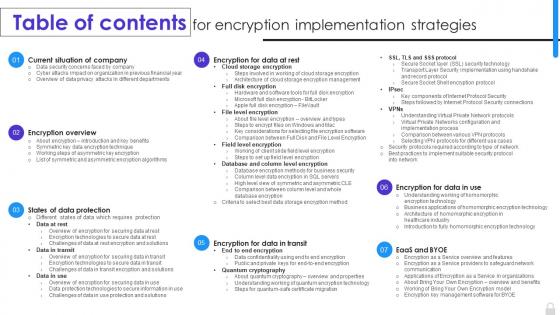
Introducing Table Of Contents For Encryption Implementation Strategies Ppt Ideas Examples to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Encryption Overview, States Of Data Protection, Current Situation Of Company, Encryption Implementation Strategies, using this template. Grab it now to reap its full benefits.
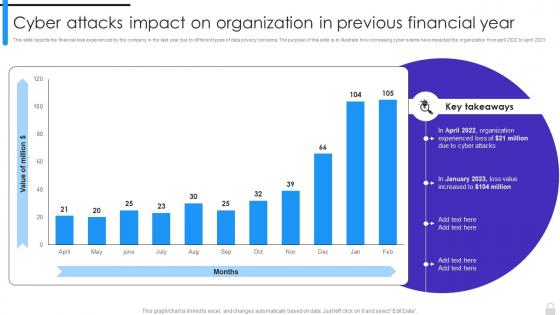
This slide depicts the financial loss experienced by the company in the last year due to different types of data privacy concerns. The purpose of this slide is to illustrate how increasing cyber scams have impacted the organization from april 2022 to april 2023. Present the topic in a bit more detail with this Encryption Implementation Strategies Cyber Attacks Impact On Organization In Previous Financial Year. Use it as a tool for discussion and navigation on Cyber Attacks, Financial Loss, Organization Experienced Loss, Data Privacy Concerns. This template is free to edit as deemed fit for your organization. Therefore download it now.
This slide represents the dashboard which can be utilized by organization to monitor cryptographic security. It includes overall progress, number of critical risks identified, initiatives, incident management, compliance, patches, highest number of critical incidents, etc. Present the topic in a bit more detail with this Encryption Implementation Strategies Data Encryption Performance Tracking Dashboard. Use it as a tool for discussion and navigation on Data Encryption Performance, Tracking Dashboard, Critical Incidents, Incident Management. This template is free to edit as deemed fit for your organization. Therefore download it now.

This slide showcases a collection of customer testimonials received from multiple clients who have graciously shared their feedback with the organization. It highlights the names and designations of the clients. Introducing Client Testimonials For Encryption Framework Upgradation Proposal to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Client Testimonials, Encryption Framework, Customer Testimonials, using this template. Grab it now to reap its full benefits.
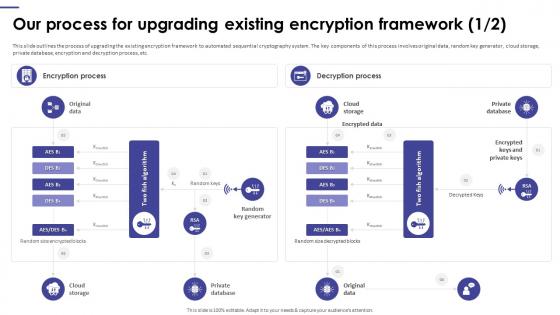
This slide outlines the process of upgrading the existing encryption framework to automated sequential cryptography system. The key components of this process involves original data, random key generator, cloud storage, private database, encryption and decryption process, etc. Present the topic in a bit more detail with this Our Process For Upgrading Existing Encryption Framework Upgradation Proposal. Use it as a tool for discussion and navigation on Encryption Framework, Cloud Storage, Private Database, Encryption And Decryption Process. This template is free to edit as deemed fit for your organization. Therefore download it now.
This slide represents an overview of the team structure for the encryption framework upgradation proposal. It highlights the names and designations of each team member in accordance with their position within the hierarchy. Increase audience engagement and knowledge by dispensing information using Our Team For Encryption Framework Upgradation Proposal. This template helps you present information on three stages. You can also present information on Our Team, Encryption Framework, Upgradation Proposal, Expertise And Achievements using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.

This slide showcases the cost of the encryption upgradation proposal. It includes the different costs related to hardware, software, professional services, total service costs, software licenses, key management solutions, and contingency budgets. Present the topic in a bit more detail with this Pricing Summary For Encryption Framework Upgradation Proposal. Use it as a tool for discussion and navigation on Encryption Framework, Upgradation Proposal, Key Management Solutions, Contingency Budgets. This template is free to edit as deemed fit for your organization. Therefore download it now.

The purpose of this slide is to outline the major uses of Encryption-as-Service method in different domains. The key applications discussed in this slide are all-time security assurance, secure sensitive information and maintaining regulatory compliance. Introducing Applications As A Service In Organizations Encryption For Data Privacy In Digital Age It to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Maintaining Regulatory Compliance, Secure Sensitive Information, Security Assurance, using this template. Grab it now to reap its full benefits.

This slide outlines the differences between symmetric and asymmetric encryption methods. The purpose of this slide is to compare the two main data encryption techniques known as symmetric key cryptography and asymmetric key cryptography. Present the topic in a bit more detail with this Comparison Symmetric And Asymmetric Encryption Encryption For Data Privacy In Digital Age It. Use it as a tool for discussion and navigation on Asymmetric, Encryption, Comparison. This template is free to edit as deemed fit for your organization. Therefore download it now.
This slide represents the dashboard which can be utilized by organization to monitor cryptographic security. It includes overall progress, number of critical risks identified, initiatives, incident management, compliance, patches, highest number of critical incidents, etc. Deliver an outstanding presentation on the topic using this Data Encryption Performance Tracking Dashboard Encryption For Data Privacy In Digital Age It. Dispense information and present a thorough explanation of Encryption, Performance, Dashboard using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
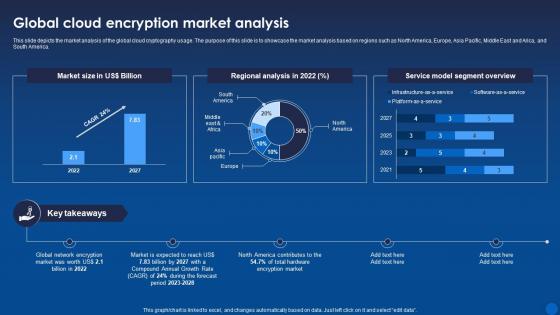
This slide depicts the market analysis of the global cloud cryptography usage. The purpose of this slide is to showcase the market analysis based on regions such as North America, Europe, Asia Pacific, Middle East and Arica, and South America. Present the topic in a bit more detail with this Global Cloud Encryption Market Analysis Encryption For Data Privacy In Digital Age It. Use it as a tool for discussion and navigation on Regional Analysis, Segment Overview, Encryption. This template is free to edit as deemed fit for your organization. Therefore download it now.
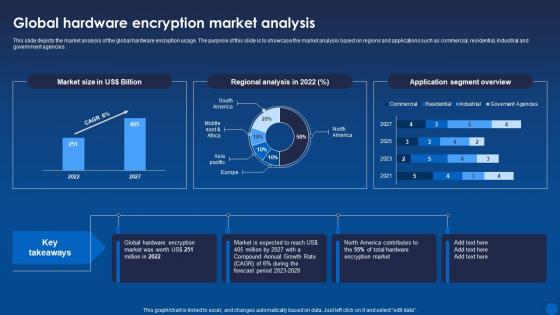
This slide depicts the market analysis of the global hardware encryption usage. The purpose of this slide is to showcase the market analysis based on regions and applications such as commercial, residential, industrial and government agencies. Deliver an outstanding presentation on the topic using this Global Hardware Encryption Market Analysis Encryption For Data Privacy In Digital Age It. Dispense information and present a thorough explanation of Hardware, Encryption, Analysisusing the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
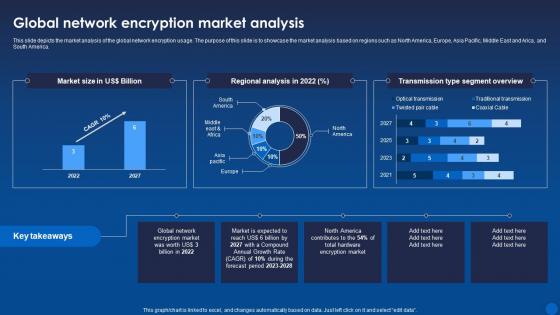
This slide depicts the market analysis of the global network encryption usage. The purpose of this slide is to showcase the market analysis based on regions such as North America, Europe, Asia Pacific, Middle East and Arica, and South America. Present the topic in a bit more detail with this Global Network Encryption Market Analysis Encryption For Data Privacy In Digital Age It. Use it as a tool for discussion and navigation on Global Network, Encryption, Market Analysis. This template is free to edit as deemed fit for your organization. Therefore download it now.
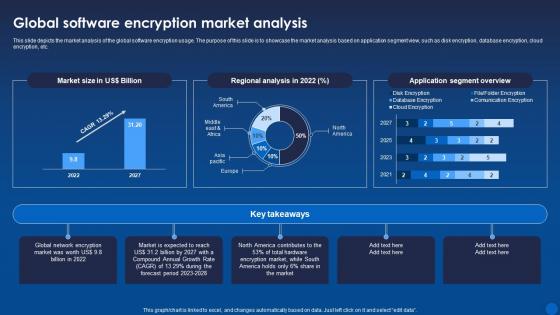
This slide depicts the market analysis of the global software encryption usage. The purpose of this slide is to showcase the market analysis based on application segment view, such as disk encryption, database encryption, cloud encryption, etc. Deliver an outstanding presentation on the topic using this Global Software Encryption Market Analysis Encryption For Data Privacy In Digital Age It. Dispense information and present a thorough explanation of Software, Encryption, Market Analysis using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
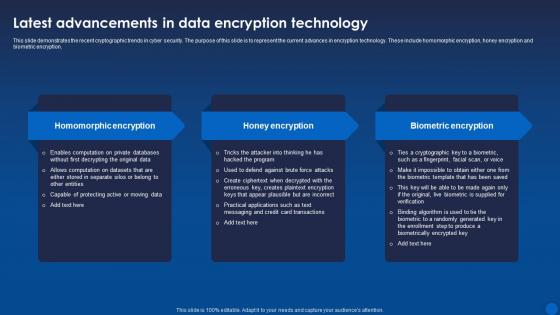
This slide demonstrates the recent cryptographic trends in cyber security. The purpose of this slide is to represent the current advances in encryption technology. These include homomorphic encryption, honey encryption and biometric encryption. Increase audience engagement and knowledge by dispensing information using Latest Advancements In Data Encryption Technology Encryption For Data Privacy In Digital Age It. This template helps you present information on three stages. You can also present information on Homomorphic Encryption, Honey Encryption, Biometric Encryption using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
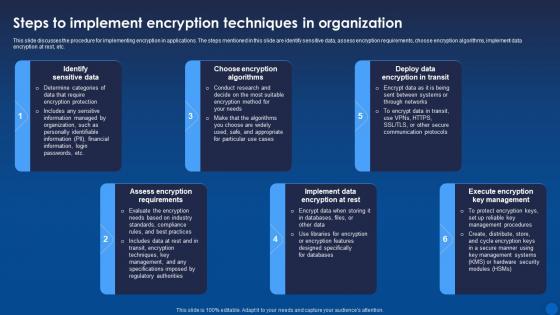
This slide discusses the procedure for implementing encryption in applications. The steps mentioned in this slide are identify sensitive data, assess encryption requirements, choose encryption algorithms, implement data encryption at rest, etc. Introducing Steps To Implement Encryption Techniques In Organization Encryption For Data Privacy In Digital Age It to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Identify Sensitive Data, Choose Encryption Algorithms, Deploy Data Encryption In Transit, using this template. Grab it now to reap its full benefits.

Deliver an outstanding presentation on the topic using this Table Of Contents For Encryption For Data Privacy In Digital Age. Dispense information and present a thorough explanation of Encryption Overview, Importance Of Encryption, Encryption Market And Trends using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
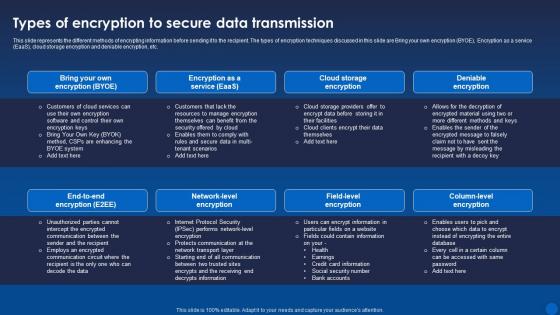
This slide represents the different methods of encrypting information before sending it to the recipient. The types of encryption techniques discussed in this slide are Bring your own encryption BYOE, Encryption as a service EaaS, cloud storage encryption and deniable encryption, etc. Present the topic in a bit more detail with this Types Of Encryption To Secure Data Transmission Encryption For Data Privacy In Digital Age It. Use it as a tool for discussion and navigation on Data Transmission, Encryption, Deniable Encryption. This template is free to edit as deemed fit for your organization. Therefore download it now.
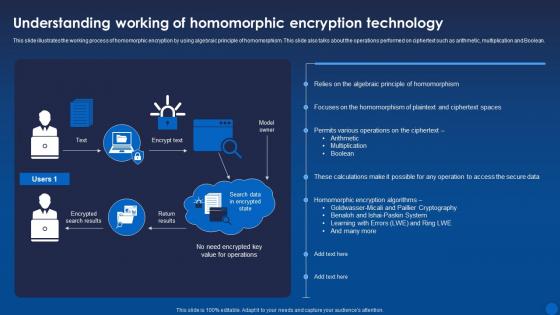
This slide illustrates the working process of homomorphic encryption by using algebraic principle of homomorphism. This slide also talks about the operations performed on ciphertext such as arithmetic, multiplication and Boolean. Present the topic in a bit more detail with this Understanding Homomorphic Encryption Technology Encryption For Data Privacy In Digital Age It. Use it as a tool for discussion and navigation on Homomorphic, Encryption, Technology. This template is free to edit as deemed fit for your organization. Therefore download it now.
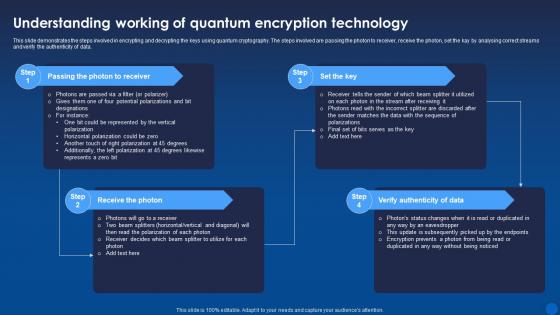
This slide demonstrates the steps involved in encrypting and decrypting the keys using quantum cryptography. The steps involved are passing the photon to receiver, receive the photon, set the kay by analysing correct streams and verify the authenticity of data. Increase audience engagement and knowledge by dispensing information using Understanding Working Of Quantum Encryption Technology Encryption For Data Privacy In Digital Age It. This template helps you present information on four stages. You can also present information on Passing The Photon To Receiver, Receive The Photon, Verify Authenticity Of Data using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
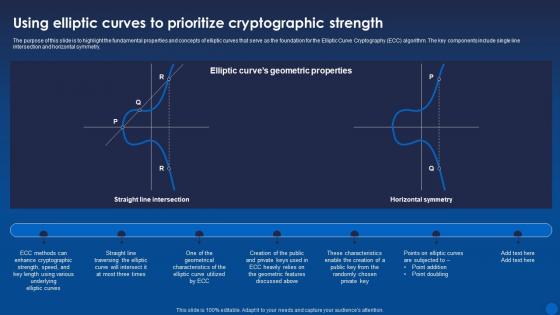
The purpose of this slide is to highlight the fundamental properties and concepts of elliptic curves that serve as the foundation for the Elliptic Curve Cryptography ECC algorithm. The key components include single line intersection and horizontal symmetry. Present the topic in a bit more detail with this Using Elliptic Curves To Prioritize Cryptographic Strength Encryption For Data Privacy In Digital Age It. Use it as a tool for discussion and navigation on Prioritize, Cryptographic, Strength. This template is free to edit as deemed fit for your organization. Therefore download it now.
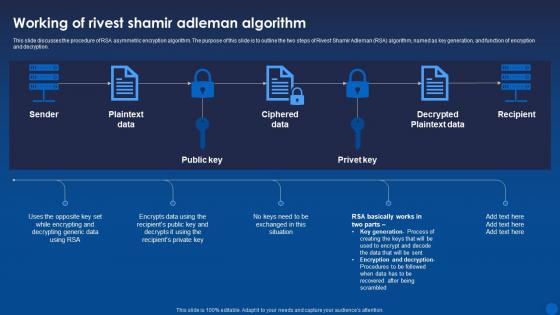
This slide discusses the procedure of RSA asymmetric encryption algorithm. The purpose of this slide is to outline the two steps of Rivest Shamir Adleman RSA algorithm, named as key generation, and function of encryption and decryption. Deliver an outstanding presentation on the topic using this Working Of Rivest Shamir Adleman Algorithm Encryption For Data Privacy In Digital Age It. Dispense information and present a thorough explanation of Algorithm, Ciphered Data, Decrypted Plaintext Data using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
Introducing our Encryption Techniques Icon For Securing Big Data Analytics set of slides. The topics discussed in these slides are Encryption Techniques, Securing Big Data Analytics. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
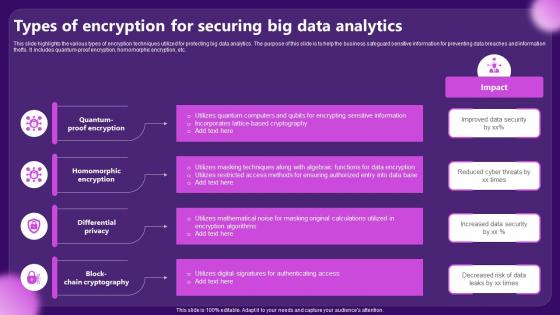
This slide highlights the various types of encryption techniques utilized for protecting big data analytics. The purpose of this slide is to help the business safeguard sensitive information for preventing data breaches and information thefts. It includes quantum proof encryption, homomorphic encryption, etc. Introducing our premium set of slides with Types Of Encryption For Securing Big Data Analytics. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Homomorphic Encryption, Differential Privacy. So download instantly and tailor it with your information.
This PowerPoint icon features a colourful illustration of a lock, symbolizing the security of a wireless network. It is perfect for presentations on WIFI security, data protection, and cyber safety. Use this icon to emphasize the importance of secure networks and data privacy.
This Monotone powerpoint icon is perfect for any presentation on WIFI security. It features a classic black and white design with a laptop and a router, making it ideal for any modern business presentation. It is easy to use and can be used to illustrate the importance of secure WIFI connections.
This cheerful coloured powerpoint icon is perfect for illustrating file sharing. It features a cloud with an arrow pointing up and down, representing the transfer of files between two sources.
This Monotone Powerpoint Icon is perfect for representing File Sharing. It features a folder with an arrow pointing to the right, symbolizing the sharing of files from one device to another. It is simple, yet effective and can be used in any presentation.
This coloured powerpoint icon features a broken shield with a distressed texture. It is perfect for conveying a sense of vulnerability, fragility, or failure in presentations. It is available in a range of vibrant colours and can be used to highlight key points or draw attention to important concepts.
This Monotone Powerpoint icon depicts a broken shield, representing a lack of protection or security. It is perfect for conveying a sense of vulnerability, fragility, or danger in presentations. It can also be used to illustrate a lack of trust or loyalty.
Presenting Sales force Encrypted Fields Limitations In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase four stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Salesforce Encrypted Fields Limitations. This well-structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
Presenting Shield Encryption Salesforce Limitations In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase five stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Shield Encryption Salesforce Limitations. This well-structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
This is a coloured powerpoint icon of a WIFI symbol with a red cross over it, indicating the WIFI is off. Ideal for presentations or documents related to technology, networks and internet security.
This Monotone PowerPoint icon is perfect for presentations that need to communicate the concept of WIFI Off. It features a simple, minimalistic design that is easy to recognize and eye catching. The icon is available in both vector and raster formats for easy use.
This coloured powerpoint icon is perfect for illustrating the concept of digital signature. It is a high-resolution, vector-based graphic with a vibrant and eye-catching colour palette. It is an ideal choice for presentations, infographics, and other visuals.
This Monotone Powerpoint Icon on Digital Signature is a modern and stylish way to represent the concept of digital signature. It is a simple yet powerful graphic that will add a professional touch to any presentation. It is easy to customize and can be used for a variety of purposes.
This coloured powerpoint icon is perfect for presentations and displays. It features a modern, sleek design and is available in a range of vibrant colours. It is easy to use and adds a professional touch to your work.
This Monotone powerpoint icon on Scan WIFI is a simple yet effective way to add a professional look to your presentation. It is easy to customize and can be used to illustrate any concept related to scanning a wireless network. It is an ideal choice for any business or educational presentation.
This coloured powerpoint icon is perfect for making your presentation stand out. It features a login symbol in bright and vivid colours that will draw the attention of your audience. It is easy to use and can be resized to fit your needs. Get creative and make your presentation memorable with this powerpoint icon.
Monotone Powerpoint Icon on Login is a high-quality vector icon designed to be used in presentations, websites, and other digital projects. It features a simple, minimalistic design with a monotone color palette, making it perfect for modern and professional designs.
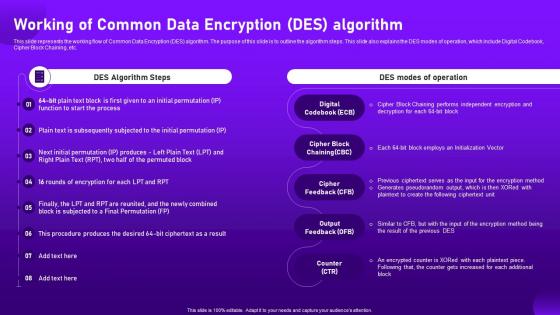
This slide represents the working flow of Common Data Encryption DES algorithm. The purpose of this slide is to outline the algorithm steps. This slide also explains the DES modes of operation, which include Digital Codebook, Cipher Block Chaining, etc. Deliver an outstanding presentation on the topic using this Working Of Common Data Encryption Des Algorithm Cloud Cryptography. Dispense information and present a thorough explanation of Pseudorandom, Initialization, Independent using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
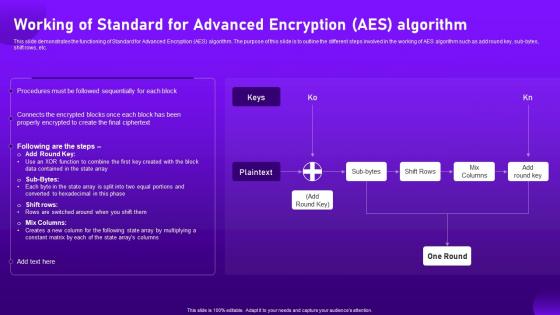
This slide demonstrates the functioning of Standard for Advanced Encryption AES algorithm. The purpose of this slide is to outline the different steps involved in the working of AES algorithm such as add round key, sub-bytes, shift rows, etc. Present the topic in a bit more detail with this Working Of Standard For Advanced Encryption Aes Algorithm Cloud Cryptography. Use it as a tool for discussion and navigation on Demonstrates, Encryption, Algorithm. This template is free to edit as deemed fit for your organization. Therefore download it now.


Microsoft 365 Life Hacks > Presentations > How to password protect your PowerPoint presentations
How to password protect your PowerPoint presentations
Learn how to password protect a PowerPoint presentation and get additional tips for keeping your online files safe even as you share them with your colleagues and contributors.

As the most versatile and widely used presentation software, Microsoft PowerPoint presentations often contain valuable content that requires protection. From company earnings results to trade secrets, students’ projects, or the questions and answers to a quiz, it’s essential for PowerPoint users to safeguard their sensitive data and confidential information, so that they won’t be easily accessed by hackers or unauthorized parties in general.
Why should you add password protection to your PowerPoint files?
A password is the easiest way to add a layer of protection to any of your files, and it’s an effective deterrent to ward off those who aren’t supposed to access them. If you’re sharing sensitive information at your work, or delivering a confidential presentation, a password will reduce the chance of a data breach or the misuse of your presentation’s contents.

Tell your story with captivating presentations
Powerpoint empowers you to develop well-designed content across all your devices
There are many ways in which your files can fall into the wrong hands: whether you store them on a removable USB drive, which can be easily lost, or email an unencrypted file to a compromised account, adding a password adds an extra layer of security. If you’re sharing a PowerPoint presentation online with multiple collaborators, consider using secure cloud storage like Microsoft OneDrive .
By taking a few minutes to implement password protection, you gain peace of mind knowing that your data is safeguarded. Be sure to share your file access with only the people who are authorized to see it.
How to add a password to your PowerPoint presentation
Adding a password to protect your PowerPoint file is easy! Follow these steps to password protect your presentation :
- Open your PowerPoint presentation and select File , then Info .
- Select Protect Presentation . Here, you have multiple options on who can access, view, or edit your presentation.
- Always Open Read-Only prevents viewers from accidentally making changes. Restrict Access allows you to select who can read, copy, or edit. Add a Digital Signature secures your file with proof that someone has opened it. Mark as Final lets your viewers know that they’re looking at the final draft of your presentation.
- To add a password, select Encrypt with Password , the second option in the drop-down menu.
- A dialog box will open. Enter your password and select OK .
Be sure to remember what your password is, as PowerPoint’s powerful encryption abilities will lock you out if you’re not able to remember your own password. You can use any word or combination of letters and numbers to secure your file and remember that all passwords are case-sensitive. When sharing your password-protected PowerPoint files via email, use encrypted emailing ( which Outlook offers ) for an added layer of security.
Taking a few moments to easily add this security layer can save you from unauthorized access and the potentially damaging impact of a data breach. Whether it’s a presentation in a corporate environment, an academic project, or some personal content, adding password protection ensures that your files will remain confidential and secure.
But don’t just stop there: PowerPoint’s advanced presentation features are effective for all subjects and audiences! If you’re looking to get the most out of conveying information, read these additional tips and tricks on how to ace your upcoming presentation , whether you’re looking to dazzle your audience , improving your public speaking skills , or you’re curious about the 30+year history of PowerPoint .
Get started with Microsoft 365
It’s the Office you know, plus the tools to help you work better together, so you can get more done—anytime, anywhere.
Topics in this article
More articles like this one.

How to create an educational presentation
Use PowerPoint to create dynamic and engaging presentations that foster effective learning.

Five tips for choosing the right PowerPoint template
Choose an appropriate PowerPoint template to elevate your presentation’s storytelling. Consider time length, audience and other presentation elements when selecting a template.

How you can use AI to help you make the perfect presentation handouts
Learn how AI can help you organize and create handouts for your next presentation.

How to use AI to help improve your presentations
Your PowerPoint presentations are about to get a boost when you use AI to improve a PowerPoint presentation.

Everything you need to achieve more in less time
Get powerful productivity and security apps with Microsoft 365


Explore Other Categories

Password protection for presentations in PowerPoint
A password helps to prevent other people from opening or modifying a presentation.
Caution: When you create a password for a presentation, record the password and keep it in a secure place. If you lose the password, it can't be retrieved and you won't be able open or gain access to the presentation.
Add password protection to a file
Select File > Info .
Select Protect Presentation > Encrypt with Password .
In the Password box, enter the password you'd like to use. Select OK .
PowerPoint prompts you to confirm the password by entering it once more.
Save the file to ensure the password takes effect.
Password protection isn't supported in PowerPoint for ODP (Open Document Presentation) files.
Remove a password from a file
Removing a password from a document is a simple process, but you have to know the original password.
Open the presentation whose password you want to remove.
Clear the password in the Password box, and then click OK .
Co-authoring a password-protected file
If you attempt to open a password-protected file that someone else is currently working on, you'll be able to open it, but you won't be able to edit it. You'll see the file in read-only mode.
Add or remove protection in your document, workbook, or presentation
Require a password to open a presentation
Click File > Passwords .
Under Password to open , select the Encrypt this presentation and require a password to open check box.
In the New password box, type a password.
Note: To create a strong password, use at least seven characters and include a combination of uppercase and lowercase letters, numbers, and non-alphabetic characters such as !,$, #, and %. Do not include your account name or other personal information.
In the Verify box, type the password again, and then click Set Password .
Click OK , and then save your presentation.
Tip: To remove the password, clear the Encrypt this presentation and require a password to open check box, click OK , and then save your presentation.
Require a password to modify a presentation
You can add a password so that only authorized users can modify a presentation. Unauthorized users can still open the presentation and then save it by using a different file name.
Under Password to modify , select the Require a password to modify the presentation check box.
Tip: To remove the password, clear the Require a password to modify the presentation check box, click OK , and then save your presentation.
Change a password to open or modify a presentation
Under Password to open or Password to modify , click Change Password .
In the New password box, type the new password.
To open a password-protected presentation: Enter the password for the file in the box.
Passwords are case-sensitive. Make sure you don't accidentally have Caps Lock turned on.
You can try again if you enter an incorrect password.
The file can't be opened without the password. If you don't know the password, you'll have to check with the person that encrypted the file.
For ODP (Open Document Presentation) files, password protection isn't supported in PowerPoint for the web.

Need more help?
Want more options.
Explore subscription benefits, browse training courses, learn how to secure your device, and more.

Microsoft 365 subscription benefits

Microsoft 365 training

Microsoft security

Accessibility center
Communities help you ask and answer questions, give feedback, and hear from experts with rich knowledge.

Ask the Microsoft Community

Microsoft Tech Community

Windows Insiders
Microsoft 365 Insiders
Was this information helpful?
Thank you for your feedback.
Got any suggestions?
We want to hear from you! Send us a message and help improve Slidesgo
Top searches
Trending searches

teacher appreciation
11 templates

memorial day
12 templates

9 templates

rain forest
23 templates

55 templates
Cryptography Thesis
Cryptography thesis presentation, free google slides theme and powerpoint template.
Once again, Slidesgo reminds you that we live in the era of information and technology. This means we move lots of data every day... but we must ensure that the data is secure! Our templates are, just like this one for thesis defenses. If you've finished a study on cryptography, use this colorful design and its translucent shapes! Explain the methodology, the analysis of the results, the conclusions, the bibliographical references and other main points from your dissertation. It's the "safest" way to an A+!
Features of this template
- 100% editable and easy to modify
- 25 different slides to impress your audience
- Contains easy-to-edit graphics such as graphs, maps, tables, timelines and mockups
- Includes 500+ icons and Flaticon’s extension for customizing your slides
- Designed to be used in Google Slides and Microsoft PowerPoint
- 16:9 widescreen format suitable for all types of screens
- Includes information about fonts, colors, and credits of the resources used
How can I use the template?
Am I free to use the templates?
How to attribute?
Attribution required If you are a free user, you must attribute Slidesgo by keeping the slide where the credits appear. How to attribute?
Related posts on our blog.

How to Add, Duplicate, Move, Delete or Hide Slides in Google Slides
How to Change Layouts in PowerPoint
How to Change the Slide Size in Google Slides
Related presentations.

Premium template
Unlock this template and gain unlimited access
Register for free and start editing online
- Ultimate Combo

- Sign Out Sign Out Sign In
19 Best Encryption-Themed Templates for PowerPoint & Google Slides
With over 6 million presentation templates available for you to choose from, crystalgraphics is the award-winning provider of the world’s largest collection of templates for powerpoint and google slides. so, take your time and look around. you’ll like what you see whether you want 1 great template or an ongoing subscription, we've got affordable purchasing options and 24/7 download access to fit your needs. thanks to our unbeatable combination of quality, selection and unique customization options, crystalgraphics is the company you can count on for your presentation enhancement needs. just ask any of our thousands of satisfied customers from virtually every leading company around the world. they love our products. we think you will, too" id="category_description">crystalgraphics creates templates designed to make even average presentations look incredible. below you’ll see thumbnail sized previews of the title slides of a few of our 19 best encryption templates for powerpoint and google slides. the text you’ll see in in those slides is just example text. the encryption-related image or video you’ll see in the background of each title slide is designed to help you set the stage for your encryption-related topics and it is included with that template. in addition to the title slides, each of our templates comes with 17 additional slide layouts that you can use to create an unlimited number of presentation slides with your own added text and images. and every template is available in both widescreen and standard formats. with over 6 million presentation templates available for you to choose from, crystalgraphics is the award-winning provider of the world’s largest collection of templates for powerpoint and google slides. so, take your time and look around. you’ll like what you see whether you want 1 great template or an ongoing subscription, we've got affordable purchasing options and 24/7 download access to fit your needs. thanks to our unbeatable combination of quality, selection and unique customization options, crystalgraphics is the company you can count on for your presentation enhancement needs. just ask any of our thousands of satisfied customers from virtually every leading company around the world. they love our products. we think you will, too.
Widescreen (16:9) Presentation Templates. Change size...

PPT layouts having computer hacker silhouette of hooded man reaching and stealing network password to steal confidential data concept for security encryption crime and virus protection

Presentation design having composite of programming language and padlock over network server room circuit board security protection data storage password encryption and technology concept

Presentation theme featuring composite of multiple words programming language and padlock over network server room circuit board security protection data storage password encryption and technology concept

Slide deck with encryption concept - red decrypted letters in middle of digital code

Presentation theme having cyber safety or security encryption concept code numbers pad lock on laptop computer

Slide deck having ssl secure sockets layer for security and encryption random alphabets with letters in background

Slides with correct key security and encryption concept image

Slides enhanced with code numbers pad lock on hard disk security encryption concept

PPT theme having security and encryption random alphabets with letters of authentication on top

Slide deck featuring security and encryption random alphabets with letters of security on top

PPT layouts enhanced with encryption and other random alphabets

Slides with encryption - computer network security concept - isolated text in vintage wood letterpress printing blocks stained by color inks

Slide set with many keys in the dark security and encryption concept image

Slide set consisting of encryption concept - red laser decrypting letters in middle of digital code

Theme with computer keyboard background

Slides featuring malware security and encryption random alphabets in background

PPT layouts with image of an external hard drive with the text hardware encryption

Slide set consisting of phishing security and encryption random alphabets in background
More encryption presentation templates.

Company Info
- File Formats
- Presentation
Security in Presentation
19 Sep 2023 11 minutes to read
Encrypting with password
You can protect a PowerPoint Presentation by encrypting the document by using a password. This prevents unauthorized users to access or make changes in the Presentation.
The following code example demonstrates how to encrypt a PowerPoint Presentation with password.
- C# [Cross-platform]
- C# [Windows-specific]
- VB.NET [Windows-specific]
You can download a complete working sample from GitHub .
Decrypting the PowerPoint Presentation
Essential Presentation provides ability to remove the encryption from the PowerPoint Presentation. You can decrypt a PowerPoint Presentation by opening it with the password.
Opening the Encrypted PowerPoint Presentation
The following code example demonstrates opening the encrypted PowerPoint Presentation.
Removing the encryption from Presentation
The following code example demonstrates removing the encryption from a PowerPoint Presentation.
Write Protection
You can set write protection for a PowerPoint Presentation and remove protection from the write protected PowerPoint presentation.
Protect PowerPoint Presentation
You can protect a PowerPoint Presentation with password to restrict unauthorized editing.
The following code example shows how to set write protection for a PowerPoint Presentation.
Remove Protection
You can check whether a PowerPoint Presentation is write protected and remove protection from the write protected PowerPoint Presentation.
The following code example shows how to remove restriction protection from the write protected PowerPoint Presentation
NOTE In Xamarin applications, Encryption, Decryption and Write Protection features are supported from the target framework .NET Standard 2.0 version onwards. For ASP.NET Core, Encryption, Decryption and Write Protection features are supported from the .NET Core 2.0 version onwards.
Layer 6 Presentation Layer
De/Encryption, Encoding, String representation
The presentation layer (data presentation layer, data provision level) sets the system-dependent representation of the data (for example, ASCII, EBCDIC) into an independent form, enabling the syntactically correct data exchange between different systems. Also, functions such as data compression and encryption are guaranteed that data to be sent by the application layer of a system that can be read by the application layer of another system to the layer 6. The presentation layer. If necessary, the presentation layer acts as a translator between different data formats, by making an understandable for both systems data format, the ASN.1 (Abstract Syntax Notation One) used.
OSI Layer 6 - Presentation Layer
The presentation layer is responsible for the delivery and formatting of information to the application layer for further processing or display. It relieves the application layer of concern regarding syntactical differences in data representation within the end-user systems. An example of a presentation service would be the conversion of an EBCDIC-coded text computer file to an ASCII-coded file. The presentation layer is the lowest layer at which application programmers consider data structure and presentation, instead of simply sending data in the form of datagrams or packets between hosts. This layer deals with issues of string representation - whether they use the Pascal method (an integer length field followed by the specified amount of bytes) or the C/C++ method (null-terminated strings, e.g. "thisisastring\0"). The idea is that the application layer should be able to point at the data to be moved, and the presentation layer will deal with the rest. Serialization of complex data structures into flat byte-strings (using mechanisms such as TLV or XML) can be thought of as the key functionality of the presentation layer. Encryption is typically done at this level too, although it can be done on the application, session, transport, or network layers, each having its own advantages and disadvantages. Decryption is also handled at the presentation layer. For example, when logging on to bank account sites the presentation layer will decrypt the data as it is received.[1] Another example is representing structure, which is normally standardized at this level, often by using XML. As well as simple pieces of data, like strings, more complicated things are standardized in this layer. Two common examples are 'objects' in object-oriented programming, and the exact way that streaming video is transmitted. In many widely used applications and protocols, no distinction is made between the presentation and application layers. For example, HyperText Transfer Protocol (HTTP), generally regarded as an application-layer protocol, has presentation-layer aspects such as the ability to identify character encoding for proper conversion, which is then done in the application layer. Within the service layering semantics of the OSI network architecture, the presentation layer responds to service requests from the application layer and issues service requests to the session layer. In the OSI model: the presentation layer ensures the information that the application layer of one system sends out is readable by the application layer of another system. For example, a PC program communicates with another computer, one using extended binary coded decimal interchange code (EBCDIC) and the other using ASCII to represent the same characters. If necessary, the presentation layer might be able to translate between multiple data formats by using a common format. Wikipedia
- Data conversion
- Character code translation
- Compression
- Encryption and Decryption
The Presentation OSI Layer is usually composed of 2 sublayers that are:
CASE common application service element
Sase specific application service element, layer 7 application layer, layer 6 presentation layer, layer 5 session layer, layer 4 transport layer, layer 3 network layer, layer 2 data link layer, layer 1 physical layer.
ETSI Security Conference 2024
Call for presentations, programme committee, venue & travel.
ETSI’s annual flagship event on Cyber Security, the ETSI Security Conference, will take place face-to-face from 14 to 17 October 2024, in ETSI, Sophia Antipolis, France . Save the date in your calendar not to miss this opportunity to Meet and Network with the Community!
This exclusive face-to-face event will provide an exceptional opportunity for the security community to come together to exchange with experts, network with peers, and share facts and opinions around the most relevant subjects of cybersecurity standardization. The intensive 4-day programme will gather speakers from government agencies, other standards bodies, academia and various industry sectors.
This year's event will address AI - Impacts of Regulation on Zero Trust and Consumer devices - Societal Impact of Technology- Fraud, Security and Standards Convergence - 5G to 6G - Privacy and Considerations of Employing Encryption Technologies -Transport, Public safety and Critical Communications - Consumer verticals.
You may want to give a talk or present a poster during the ETSI Security Conference! Currently the Programme Committee is calling for Presentations/ Posters: d o not miss the deadline: 26 May! Please check here the submission modalities and submit your proposal .
The event stable programme and the registration opening will be announced in the course of July. Subscribe to this mailing list to be kept informed of its launch.
Venue: ETSI Headquarters 650 Route des Lucioles 06560 Valbonne - Sophia Antipolis
FRANCE Tel: +33 4 92 94 42 00
The Programme Committee is now calling for Presentations / Posters. Should you want to send a presentation or poster proposal, please SUBMIT YOUR PROPOSAL by 26 May ..
Note : Due to the high number of presentation proposals expected, we recommend to strictly submit your proposal within the announced deadline, as no extension will be granted. Marketing / commercial speeches are not welcome.
Proposal status will be provided by the end of June, as it is intended to publish a stable event programme in the course of July.
The presentations proposed should fit within the following sessions objectives:
- Impacts of Regulation - Capturing European values in Technologies : The session will focus on impacts of regulation on products, innovation and technology. It will consider how EU regulation (e.g. AI Act, e-IDAS, RED, CRA, NIS2) and other regional regulations have shaped the global technology landscape. The session will also consider points of friction and gaps between aims of regulation and actual security improvements for products placed on the market.
- AI as a Technology / Platform : The session will consider AI security from the perspective of securing AI as a generic platform capability. The session will discuss latest challenges, threats, legislation and approaches to providing secure AI.
- AI "Verticals" / End Applications : The session will consider AI security from the perspective of securing AI as deployed in specific vertical applications. The session will discuss latest challenges, threats, legislation and approaches to implementing AI in specific vertical / end applications.
- Societal Impacts of Technology : This session will explore the societal impact of technology on end users and society. Topics including coercive control avoidance, Metaverse, protection of children, disinformation and protection vulnerable citizens will be discussed.
- Impact of Regulation - Zero Trust : The session will explore latest developments, regulatory landscape and best practice for zero trust.
- Impact of Regulation - Consumer Devices: :The session will explore impacts of regulation on consumer products and devices. It will particularly explore successes, failures, best practice and gaps. Focus areas to include IoT and automotive.
- Quantum Session: The session explore latest developments in quantum algorithm selection, migration strategy, best practice, agility and other cryptography.
- Fraud, Security and Standards Convergence: This session will explore where standards are being driven by fraud and where fraud is driving standards. The session will discuss how security and fraud prevention / detection can work more closely. Focus areas to include; 5G, PSD2, eSignature and e-payments.
- 5G to 6G Evolution or Revolution? In early 2024 3GPP, ETSI and GSMA started the multi-year process of developing standards for 6G. While 6G won’t reach the market until ~2030, 2024 to 2026 with be the key years in which 6G architecture is standardised. This session will explore 6G challenges and opportunities from a security perspective.
- Privacy and Considerations of Employing Encryption Technologies: Privacy by design has become a corner stone of all new information communication technology systems, devices and applications. However this and zero trust can also have negative consequences for security. The session will explore the interplay between encryption technologies to support privacy requirements, versus the need to detect and mitigate threats, malware and other malicious attacks. This will include consideration for limiting the spread of disinformation.
- Transport, Public safety and Critical communications: The session will explore security for Transport, Public Safety, Critical Industries and Critical Communications. Topics to include; Tetra replacement, FRMCS Rail, 3GPP SA6 work.
- Consumer Verticals: The session will explore latest security best practice, challenges and gaps for consumer IoT and other smart devices.
The ETSI Security Conference 2024 programme will be built by the following people:
- Samim Ahmadi, EY
- Charles Brookson, ZEATA Security
- Alex Cadzow, C3L
- Scott Cadzow, C3L
- Matt Campagna, Amazon Web Services
- Peter C, NCSC
- Mirko Cano Soveri, ETSI/3GPP
- Slawomir Gorniak, ENISA
- Alan Hayward, NCSC
- Holie Hennessy, OMDIA
- Alex Leadbeater,GSMA, Programme Committee Chair
- Tieyan Li, Huawei
- Gerry McQuaid, Ofcom
- Mats Naslund, NDRE
- Kim Nordstrom , ETSI
- Jean-Pierre Quémard, KAT
- Davide Pratone, Huawei
- Tony Rutkowski, CIS
- George Sharkov, European DIGITAL SME Alliance & SBS
- Nataliya Stanetsky, Google Ireland Limited
- Colin Whorlow, NCSC
- Alf Zugenmaier, NTT Docomo
ETSI Newsletter Notification Service
You are leaving the ETSI website and will be directed to the ETSI Member Portal.

COMMENTS
Encryption ppt. Dec 28, 2015 • Download as PPTX, PDF •. 10 likes • 17,208 views. Anil Neupane. A ppt on Encryption. Technology. 1 of 11. Download now. Encryption ppt - Download as a PDF or view online for free.
Requirement for a modern encryption system: 1 It was evaluated assuming that the enemy knows the system. 2 Its security relies entirely on the key being secret. Note: IThe design and implementation of a secure communication system is a major investment and is not easily and quickly repeated. IRelying on the enemy not knowing the encryption ...
Encryption Presentation Jamie Roberts Encryption Defined: The process of converting messages, information, or data into a form unreadable by anyone except the intended recipient. Cryptography, Cryptanalysis, and Cryptology Cryptography is the art or science of secret writing Cryptanalysis is the practice of defeating attempts to hide ...
Lecture 22: Cryptography: Encryption Viewing videos requires an internet connection Description: In this lecture, Professor Devadas continues with cryptography, introducing encryption methods.
But there are, broadly speaking, two types of keys - symmetric and asymmetric keys. In symmetric key encryption, the same key used to encrypt the data is used to decrypt the data. In asymmetric key encryption, one key is used to only encrypt the data (the public key) and another key is used to decrypt (the private key).
Template 4: Internet of Things (IoT) Data Encryption PPT Template. This PPT Deck explains the role of data encryption in protecting sensitive information in IoT systems. Data encryption in IoT involves End-to-End security, increasing storage requirements, operating on encrypted data, authentication of devices, using secure communication ...
TLS (which underlies HTTPS) uses public key cryptography to ensure that we always maintain a secure channel of communication. An initial "handshake" that verifies the server's identity (e.g. that Facebook is Facebook) Generate session keys to use symmetric cryptography after the initial handshake. End-to-End Encryption (E2EE) is used for secure ...
Encryption is a way of scrambling data so that only authorized parties can understand the information. In technical terms, it is the process of converting human-readable plaintext to incomprehensible text, also known as ciphertext. In simpler terms, encryption takes readable data and alters it so that it appears random.
Encryption is a form of data security in which information is converted to ciphertext. Only authorized people who have the key can decipher the code and access the original plaintext information. In even simpler terms, encryption is a way to render data unreadable to an unauthorized party. This serves to thwart cybercriminals, who may have used ...
Get our attention-grabbing Data Encryption presentation template, compatible with MS PowerPoint and Google Slides, to describe the process of converting plain text or data into a different code or cipher text that is unreadable without the use of a secret key or specific decrypting software. You can further explain how it maintains the ...
How To Password Protect PowerPoint Files. On the PowerPoint ribbon, click on File. In the Info section, click on the first option, Protect Presentation. Then choose Encrypt with Password. The next step for you to do is to type in the password you'd like to assign for your PowerPoint file and click on the OK button.
Presenting this set of slides with name domain encryption ppt powerpoint presentation styles outline cpb pdf. This is an editable Powerpoint five stages graphic that deals with topics like domain encryption to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent ...
Use the encryption feature in PowerPoint. Assign a password by going to Protect Presentation. Save the presentation as graphic images or a PDF file to keep the information visible but not easily editable. Use the Mark as Final feature to ensure that no further edits are made inadvertently. This article explains several ways you can apply ...
Presenting this set of slides with name Email Encryption Ppt Powerpoint Presentation Pictures Background Designs Cpb. This is an editable Powerpoint four stages graphic that deals with topics like Email Encryption to help convey your message better graphically. This product is a premium product available for immediate download, and is 100 ...
Follow these steps to password protect your presentation: Open your PowerPoint presentation and select File, then Info. Select Protect Presentation. Here, you have multiple options on who can access, view, or edit your presentation. Always Open Read-Only prevents viewers from accidentally making changes. Restrict Access allows you to select who ...
Add password protection to a file. Select File > Info. Select Protect Presentation > Encrypt with Password. In the Password box, enter the password you'd like to use. Select OK. PowerPoint prompts you to confirm the password by entering it once more. Save the file to ensure the password takes effect. Password protection isn't supported in ...
PowerPoint offers encryption by giving you the ability to add a password to your presentation. Only those with the password can open the document. Let's take a closer look and see how it's done ...
Our templates are, just like this one for thesis defenses. If you've finished a study on cryptography, use this colorful design and its translucent shapes! Explain the methodology, the analysis of the results, the conclusions, the bibliographical references and other main points from your dissertation. It's the "safest" way to an A+!
Below you'll see thumbnail sized previews of the title slides of a few of our 19 best encryption templates for PowerPoint and Google Slides. The text you'll see in in those slides is just example text. The encryption-related image or video you'll see in the background of each title slide is designed to help you set the stage for your ...
The following code example demonstrates removing the encryption from a PowerPoint Presentation. C# [Cross-platform] C# [Windows-specific] VB.NET [Windows-specific] //Opens an existing Presentation from file system and it can be decrypted by using the provided password. using (FileStream inputStream = new FileStream ("Sample.pptx", FileMode.
The presentation layer is the lowest layer at which application programmers consider data structure and presentation, instead of simply sending data in the form of datagrams or packets between hosts. This layer deals with issues of string representation - whether they use the Pascal method (an integer length field followed by the specified ...
The presentations proposed should fit within the following sessions objectives: Impacts of Regulation - Capturing European values in Technologies: The session will focus on impacts of regulation on products, innovation and technology. It will consider how EU regulation (e.g. AI Act, e-IDAS, RED, CRA, NIS2) and other regional regulations have ...
To address a critical health care workforce shortage, HHSC has launched a free, virtual classroom course that is expected to increase the number of nurse aides providing direct care to residents in Texas nursing facilities. Under this initiative by the HHSC Long-Term Care Regulation (LTCR) team ...