Cyber Terrorism: Research Review: Research Report of the Australian National University Cybercrime Observatory for the Korean Institute of Criminology
129 Pages Posted: 12 Jun 2017 Last revised: 4 Jul 2017

Roderic Broadhurst
School of Regulation & Global Governance (RegNet); Australian National University (ANU) - Cybercrime Observatory
Hannah Woodford-Smith
Anu cybercrime observatory, donald maxim.
(ANU) - Cybercrime Observatory
Bianca Sabol
Stephanie orlando.
(ANU) - Cybercrime Observatory ; Australian National University (ANU), Students
Ben Chapman-Schmidt
Australian National University (ANU) - School of Social Sciences
Mamoun Alazab
Cyber Security
Date Written: June 30, 2017
This review of cyber-terrorism outlines the main trends and challenges presented by the convergence of the exceptional reach, speed and scale of the Internet and the political ambitions of violent extremists. Chapters on cyber weapons, critical infrastructure, attribution, Internet of Things, recruitment and propaganda, financing, legislation and counter measures, and cyberwar. Each chapter provides a brief summary of a key aspect of the cyber terror phenomenon, an analysis of emerging trends or perspectives, and other relevant information or examples identified during the research. At the end of each chapter a brief annotated bibliography is included to assist future research and give readers more information about the sources used. The report has drawn on a broad range of sources including government documents (e.g. law enforcement and security agencies), web/blog posts, academic articles, information security websites and online news articles about cyber terrorism. The final chapter concludes with a discussion on the likelihood of a cyber terrorist attack. At present a sophisticated large-scale cyber terrorist attack with a kinetic element appears to be unlikely. However, this may change in the next five years because of the increasing capacity of many nation states (including proxy actors) to undertake offensive measures in the cyber domain. Moreover, one notes the increasing risk that sophisticated weaponised software may enter the ‘wild’ and into the criminal underworld, and potentially into the hands of capable violent extremists. A serious cyber terrorist kinetic event (for example, the interruption of power supply or transport services with death or injury as one of the outcomes) is therefore currently unlikely, but high volume/low value or impact events are on the rise (e.g. the routine use of ransomware to finance a terrorist group, the distribution of deceptive or ‘fake’ news, and the mounting of distributed denial of service [DDoS] attacks to undermine confidence in e-commerce). The risk of a cyber terrorism attack should therefore not be understated as an emerging threat, and consequently, preventative and response capabilities should be maintained and advanced. Contemporary society, in short, is coming to realise that violent extremism, albeit relatively rare, is the ‘new normal’. Though it may be difficult to predict each specific event, we can be reasonably certain that at some future point, they will occur.
Keywords: cyber terrorism, cybercrime, cyber warfare, critical infrastructure, terrorist recruitment
Suggested Citation: Suggested Citation
Roderic Broadhurst (Contact Author)
School of regulation & global governance (regnet) ( email ).
Canberra, Australian Capital Territory 0200 Australia
Australian National University (ANU) - Cybercrime Observatory ( email )
Anu cybercrime observatory ( email ).
Canberra, Australian Capital Territory 2601 Australia
(ANU) - Cybercrime Observatory ( email )
Acton, ACT 2601 Australia
Australian National University (ANU), Students ( email )
Canberra Australia
Australian National University (ANU) - School of Social Sciences ( email )
Cyber security ( email ).
HOME PAGE: http://https://sites.google.com/view/alazabm
Do you have a job opening that you would like to promote on SSRN?
Paper statistics, related ejournals, innovation law & policy ejournal.
Subscribe to this fee journal for more curated articles on this topic
Types of Offending eJournal
Conflict studies: terrorism ejournal.
- Search Menu
- Sign in through your institution
- Editor's Choice
- Author Guidelines
- Submission Site
- Open Access
- About Journal of Cybersecurity
- Editorial Board
- Advertising and Corporate Services
- Journals Career Network
- Self-Archiving Policy
- Journals on Oxford Academic
- Books on Oxford Academic

Article Contents
Introduction, conventional and cyber terror: mirror images, research design, cyberterrorism and public confidence, cyberterrorism and political attitudes: security, civil liberties, government regulation and military retaliation, cyberterrorism and risk perception, discussion: the psychological effects of cyberterrorism, acknowledgements.
- < Previous
Cyberterrorism: its effects on psychological well-being, public confidence and political attitudes
- Article contents
- Figures & tables
- Supplementary Data
Michael L. Gross, Daphna Canetti, Dana R. Vashdi, Cyberterrorism: its effects on psychological well-being, public confidence and political attitudes, Journal of Cybersecurity , Volume 3, Issue 1, March 2017, Pages 49–58, https://doi.org/10.1093/cybsec/tyw018
- Permissions Icon Permissions
Does exposure to lethal and non-lethal cyberterrorism affect psychological well-being, public confidence and political attitudes? By what mechanisms do they do so? While cyberterrorism most often raises concerns about national security, its effects on individuals’ psyche and cognition are overlooked. To address these questions we carried out three studies between 2013 and 2016 ( n = 1124, 909 and 592). Utilizing experimental manipulations (video clips) subjects were exposed to simulated lethal and non-lethal cyberterrorism. Our findings demonstrate a stress-based ‘cyber terrorism effect’. Exposure to cyberterrorism is not benign and shares many traits with conventional terrorism: stress, anxiety, insecurity, a preference for security over liberty, a reevaluation of confidence in public institutions, a heightened perception of risk and support for forceful government policies. In the cyber realm, this translates into support for such policies as Internet surveillance, government regulation of the Internet and a forceful military response to cyberterrorism (including conventional, kinetic retaliation). These attitudes may impinge upon the tolerance and confidence necessary for a vibrant civil society. This effect is associated with non-lethal cyberterrorism that causes economic loss as well as with cyberterrorism that causes death and injury.
A primary goal of conventional terrorism is to undermine civilians’ resilience by instilling a sense of fear and vulnerability that erodes confidence in the ability of the government and law enforcement agencies to protect citizens against future attacks [ 1 ]. What about cyberterrorism? Are the psychological ramifications of conventional and cyberterrorism identical? Does the threat of conventional or cyberterrorism affect confidence in government and support for forceful security policies in the same way? To address these questions, we advanced three multiple scenario-based empirical studies for testing what happens when the public experiences cyberterrorism that causes mass casualties and/or severe economic losses with the avowed goal of undermining the public’s morale and its confidence in economic and political institutions.
Our findings draw on three large n studies conducted from 2013 to 2016 and suggest that cyberterrorism aggravates stress and anxiety, intensifies feelings of vulnerability and hardens political attitudes. In these ways, we demonstrate that cyberterrorism causes responses similar to conventional terrorism. These responses highlight the human dimension of cyberterrorism that is often neglected as policymakers focus on national security interests and the protection of frontiers, critical infrastructures and military capabilities. Both are important and as the threat of cyberterrorism grows, policymakers will have to direct their attention to the emotional distress that cyberterrorism causes just as they strive to bolster deterrent and offensive cyber capabilities. In the sections below, we draw out the similarities between the psychology of conventional and cyberterrorism that inform our empirical research, present the details of our findings and discuss their implications for public policy.
Conventional terrorism employs kinetic means (e.g. suicide bombers or improvised explosive devices) and works in many ways. Accompanied by death, injury and property destruction, terrorism generates fear and anxiety in the target population. Terrorists may, therefore, use terrorism to demoralize a civilian population to pressure their government to undertake or refrain from a specific policy. Sometimes terrorists are effective. Witness the sudden departure of Spanish troops from Iraq following terror bombings in Madrid that killed 191 people in 2004. More commonly, however, the civilian population proves exceptionally resilient [ 2–4 ]. Terrorism hardens their hearts as they demand and often receive a forceful response from their government. Armed groups, such as Hamas, may also resort to terrorism to scuttle prospects of peace [ 5 ]. Alternatively, terrorism is theater, specifically designed to seize centre stage and provoke a disproportionate response from the government of terror victims with the hopes of turning world opinion. For nearly a decade, Israel avoided any massive response to Hamas’ crude missile attacks on Southern Israel. Although the attacks disrupted everyday life, few people lost their lives. Eventually, though, security concerns and domestic pressure led to a full-scale invasion of the Gaza Strip in 2008 and again in 2014. Apart from achieving a short and fragile ceasefire, Israel faced a storm of international condemnation following the deaths of more than 1000 Palestinians in each encounter. In this way, terrorism sometimes creates a no-win situation for states [ 6 ]. Finally, terrorism may produce relatively few immediate casualties but undermine public confidence more broadly. Airplane hijackings such as those of 9/11, undermined faith in the air transportation system until governments introduced rigid controls [ 7 ]. Generally, however, conventional terrorism does not regularly affect confidence in major government institutions. This is attributable to a ‘rally around the flag’ effect and to the growing dependence on government institutions to provide security ([ 8–12 ], but see Baldwin et al. [ 13 ] and Berry et al. [ 14 ] for contrary data).
In contrast to conventional terrorism, cyberterrorism employs malicious computer technology rather than kinetic force. But like conventional terrorism, cyberterrorism aims to further political, religious, or ideological goals by harming civilians physically or psychologically. By contrast, ‘cyberwar’ uses malware and viruses to disable military targets while ‘cybercrime’ aims for pecuniary gain or personally motivated harm to others (e.g. revenge, bullying) unrelated to political conflict. Sometimes these categories overlap and the differences are difficult to discern. Cyber-terrorists and nation states may, like criminals, steal money, data or identities or, like hacktivists, mount DDoS strikes to shut down major systems. Much depends upon the intention and identity of the actors that are not always known. In our cases, Hamas and Anonymous are the perpetrators and each publically announced its intent to terrorize Israeli citizens. In Europe and the USA, on the other hand, attribution may be more difficult as ISIS and proxy hacktivists have reason to sometimes conceal their identities.
Despite its growth, cyberterrorism unlike conventional terrorism does not currently threaten life and limb. As a result, very little attention is paid to the effects of cyberterrorism on civilians [ 15 ]. The Tallinn Manual on the International Law Applicable to Cyber Warfare [ 16 ], for example, describes how cyber operations may rise to the level of an armed attack by threatening widespread loss of life or destruction of property. However, the Manual considers operations that block email throughout the country (section 30.12), involve ‘mere economic coercion’ (section 11.2), transmit tweets to cause panic by ‘falsely indicating that a highly contagious and deadly disease is spreading through the population’ (section 36.3) or comprise cyber psychological operations intended solely to undermine confidence in a government or economy (section 11.3) as insufficiently severe to constitute terror. We ask whether current events do not belie this equanimity. Claiming, ‘The internet is not indispensable to the survival of the civilian population’ (section 81.5) the framers of the Tallinn Manual seem unaware of the effects cyberterrorism may pose. As cyberattacks grow in frequency and intensity, they push beyond criminal acts to concerted attempts to disrupt airport and utility services in the Ukraine [ 17 ], perpetrate an electronic Holocaust in Israel (below), cripple DynDNS servers across important sectors of the USA and interfere with and possibly compromise the recent US elections. While not all the perpetrators or their goals are immediately obvious, they do not appear motivated by monetary gain. Rather it seems that they aim to impair public confidence, disrupt civil society and seed anxiety and insecurity by crippling digital and financial resources, undermining the institutions of governance and disrupting social networks. Given the growing threat of cyberterrorism, the question, ‘How does non-lethal and lethal cyberterrorism affect individuals psychologically?’ is pressing. In an attempt to shed some light on this question, we examined the effects of different kinds of cyberattacks on a person’s sense of security and confidence.
Experimental overview
To evaluate the effects of different kinds of cyberattacks on a person’s sense of security and confidence, we utilized two platforms: experimental manipulations and self-reported past exposure to cyberattacks. Focusing on emotional and political responses to cyberattacks and using original video clips, we conducted three online and panel studies.
Our experimental designs enabled randomization and full control of the researchers. While online surveys—particularly non-probability ones—may be slightly skewed towards the younger and the technology savvy, phone surveys tend towards older respondents, women and left leaning individuals. Because we were not conducting a correlational study seeking precise estimates of population values, we followed the recommendations of Baker et al. [ 18 ] that support the use of online studies for the purposes described in our studies [ 19 ]. Each study received University Institutional Review Board (IRB) approval. Participants signed a consent form at the beginning of the survey and we made provisions for psychological support with the survey company if needed. None was requested. Participants were debriefed and informed post-study that all the scenarios were simulated and not actual attacks.
Study 1 (September 2015)
This is an online survey experiment in which Israeli adults were randomly assigned to three treatments after which they answered a series of psychological and political questions. The control group received no experimental stimulus. In the ‘high’ treatment group, subjects viewed a video clip depicting civilian and military deaths following cyberattacks on missile systems and the electric company. In the ‘low’ treatment group, they viewed a video clip reporting a non-lethal cyberattack accompanied by damage to hardware, loss of data and theft of funds ( n = 1124). In neither case was the perpetrator identified.
Study 2 (January 2016)
This was also an online survey. Here, subjects were randomly assigned to a news report describing a cyberattack on Israel’s water purification network by terrorists (Hamas). The news reports were identical with the exception of the losses suffered. In one clip, two people died and many were injured after terrorists released deadly amounts of chlorine into the water system. In the second clip, Hamas retrieved the financial information of the company’s customers and successfully transferred substantial funds to its coffers overseas. Alternative manipulations included a conventional terror attack, that depicts a kinetic attack on a water facility that, like the kinetic attack, kills two and injures many and a control group that viewed a benign clip depicting the dedication of a new water desalinization plant ( n = 909). Immediately after viewing the clip, subjects were asked to report risk perception, threat perception and confidence in government and to evaluate offensive cyber policies and cyber regulation practices.
Using a two-wave panel design, we administered two surveys to the same panel of 522 experimental subjects—10 days apart, leading up to and following Anonymous’ well-publicized ‘electronic Holocaust’ campaign against Israel in April 2015. Anonymous’ language was belligerent and menacing but did not threaten physical harm. Rather they warned that ‘elite cyber squadrons’ would ‘invade and attack your devices and personal data, take down your servers and erase Israel from cyber space’ [ 20 ]. Pre- and post-attack questionnaires focused on the emotional and cognitive responses to the attacks and related policy choices ranging from cyber to kinetic retaliation.
Independent variables
Type of terrorism.
This was manipulated in Studies 1 and 2 by the experimental condition as explained above. In Study 1, there were three conditions: (i) control, (ii) cyberterrorism, non-lethal and (iii) cyberterrorism, lethal. In Study 2, there was an additional condition: (iv) kinetic terrorism.
Previous exposure to a cyberattack
This was assessed in all three studies by asking subjects four questions on a scale of 1–6 regarding the extent to which they, their friends or their family suffered harm or loss from a cyberattack. An answer above 3 on any of these questions was regarded as previous exposure.
Dependent variables
Measures of well-being, stress and threat perception.
In ‘Study 1’ (unidentified perpetrator) and ‘Study 2’ (Hamas), we used a four-point scale State–Trait Anxiety Index (STAI) [ 21 ]. STAI measures two types of anxiety—state (extrinsic) and trait (intrinsic) anxiety. State anxiety aligns with temporary feelings of fear, nervousness and discomfort. Trait anxiety aligns with almost daily feelings of stress, worry and discomfort. The questionnaire includes six items describing various feelings and emotions. The experimental subjects were asked to rate on a scale of 1–4 (1 = not at all; 4 = very much so) the extent to which their feelings ‘at present’ (both pre- and post experimental treatment) correspond to different items. Half of the items represent negative feelings and emotions (e.g. ‘I feel upset’, ‘I feel nervous’) and the other half represent positive feelings and emotions (e.g. ‘I feel relaxed’, ‘I feel comfortable’). Because we were interested in negative affect, we created a variable constituting only the three negative emotions.
In addition to stress, perceptions of threat play a significant role in our understanding of the psychology of terrorism. Perceptions of threat reflect the extent to which thinking about a cyberattack undermines ones sense of personal security. Threat perception is an appraisal of the danger that an out-group poses to an individual and/or his/her political community [ 22–26 , 56 , 57 , 58 , 59 ]. To gauge threat perception in all three studies we asked ‘To what extent do cyberattacks undermine your sense of personal security?’ and ‘To what extent do you feel threatened by cyber terrorism?’ (Scale 1–5).
Measures of public confidence
1. ‘Following a cyber-attack on the water system, the authorities advised drinking bottled water. How soon would you drink tap water?’ 2. ‘Following a cyber-attack on the water system the authorities suggested waiting 3 days before showering: After 3 days, would you …?’ Following each question, subjects were asked to choose one of four modes of behavior that reflect various degrees of compliance (full responses are provided below).
Measures of attitudes towards government policies
In all three studies, we asked subjects to consider government surveillance of the Internet and emails, government regulation of the businesses and military retaliation in response to cyberattacks. Questions about government surveillance asked whether the government ought to read emails and monitor social networks for security threats. Regulation of the business sector reflected answers to ‘Should the government require businesses to maintain a mandated level of cyber security.’ Retaliatory policy offered four options: (i) a ‘limited cyberattack’ to disable enemy military cyber capabilities (servers, switches, computers, cables); (ii) a ‘large scale cyberattack’ to disable enemy military and civilian cyber capabilities; (iii) a ‘limited conventional attack’ (missiles or bombs) to disable enemy military cyber capabilities; and (iv) a ‘large scale, conventional attack’ (missiles or bombs) to disable enemy military and civilian cyber capabilities. All questions were rated on a scale of 1 (not at all) to 6 (most definitely).
Measures of risk perception
Following Slovic [ 27 ], we distinguish between risk assessment and risk perception: ‘Whereas technologically sophisticated analysts employ risk assessment to evaluate hazards, the majority of citizens rely on intuitive judgments typically called risk perceptions.’ To assess risk perception we posed 16 questions that asked the experimental subjects in Study 2 (Hamas) to assess the risk posed by a cyberterror attack (1 = no risk; 6 = a very high risk). Responses loaded on four factors: bodily harm (risk of injury or loss of life); material loss (credit card and bank fraud, data theft, theft of confidential medical information); damage to critical infrastructures (transportation, refineries, water) and damage to state facilities (military, stock exchange, government offices) Alpha Cronbach 0.70, 0.91, 0.81 and 0.94, respectively.
Demographic variables
We asked respondents about their political orientation on a scale ranging from very right-wing to very left-wing.
Our findings suggest that the effects of ‘non-lethal’ and ‘lethal’ cyberterrorism track those of conventional terrorism. Overall, experimental subjects exhibit marked signs of stress, personal insecurity and heightened perceptions of cyber threat. Heightened perceptions of threat, in turn, lend support for forceful cyber government policies, a finding consistent with the effects of kinetic terrorism [ 28–31 ].
Stress and anxiety
Stress/anxiety measures following experimental cyberterror attacks. Scale: 1 (low) to 4 (high)
| . | State/trait anxiety measure STAI | |
|---|---|---|
| Study 1 , = 1027 . | Study 2 , = 907 . | |
| PerpetratorTreatment group | Unidentified | Hamas |
| Control: no terrorism | 2.3 | 2.7 |
| Cyberterrorism, non-lethal: asset and data loss (Study 1); disclosure of account information, loss of funds (Study 2) | 3.5 | 3.4 |
| Cyberterrorism, lethal: deaths and injuries | 3.6 | 3.6 |
| Conventional (kinetic) terrorism, lethal: deaths and injuries | 4.0 | |
| Significance | < 0.001 | < 0.001 |
| ANOVA (Analysis of Variance) | = 139.65 | = 34.23 |
| . | State/trait anxiety measure STAI | |
|---|---|---|
| Study 1 , = 1027 . | Study 2 , = 907 . | |
| PerpetratorTreatment group | Unidentified | Hamas |
| Control: no terrorism | 2.3 | 2.7 |
| Cyberterrorism, non-lethal: asset and data loss (Study 1); disclosure of account information, loss of funds (Study 2) | 3.5 | 3.4 |
| Cyberterrorism, lethal: deaths and injuries | 3.6 | 3.6 |
| Conventional (kinetic) terrorism, lethal: deaths and injuries | 4.0 | |
| Significance | < 0.001 | < 0.001 |
| ANOVA (Analysis of Variance) | = 139.65 | = 34.23 |
In post hoc tests using the Tukey statistic there is a significant difference between all treatment groups except for the difference between non-lethal and lethal cyberterrorism that is not significant for any of the stress/anxiety measures.
Threat perception
Threat perception measures following experimental cyberterror attacks. Scale 1 (low) to 5 (high)
| Experiment . | Study 1 , = 1027 . | Study 2 , = 907 . |
|---|---|---|
| Perpetrator treatment group . | Unidentified . | Hamas . |
| Control: no terrorism | 2.9 | 3.1 |
| Cyberterrorism, non-lethal: disclosure of account information and loss of funds | 3.4 | |
| Cyberterrorism, non-lethal: asset and data loss | 3.4 | |
| Cyberterrorism, lethal: deaths and injuries | 3.5 | 3.6 |
| Conventional terrorism, lethal: deaths and injuries | 3.8 | |
| Significance | < 0.001 | < 0.001 |
| ANOVA | = 21.60 | = 11.12 |
| Experiment . | Study 1 , = 1027 . | Study 2 , = 907 . |
|---|---|---|
| Perpetrator treatment group . | Unidentified . | Hamas . |
| Control: no terrorism | 2.9 | 3.1 |
| Cyberterrorism, non-lethal: disclosure of account information and loss of funds | 3.4 | |
| Cyberterrorism, non-lethal: asset and data loss | 3.4 | |
| Cyberterrorism, lethal: deaths and injuries | 3.5 | 3.6 |
| Conventional terrorism, lethal: deaths and injuries | 3.8 | |
| Significance | < 0.001 | < 0.001 |
| ANOVA | = 21.60 | = 11.12 |
In post hoc tests using the Tukey statistic for the data of Study 1, there was no significant difference between non-lethal and lethal cyberterrorism, but both were significantly different than the control group.
In post hoc tests using the Tukey statistic for the data of Study 2, there was no significant difference between the control group and non-lethal cyberterrorism, no significant difference between non-lethal and lethal cyberterrorism and no significant difference between lethal cyberterrorism and conventional terrorism. Lethal cyberterrorism and conventional terrorism were significantly different than the control group and conventional terrorism was significantly different than non-lethal cyberterrorism.
Simulated exposure to lethal attacks, whether cyber or kinetic, evoked perceptions of threat 16–22% stronger than those unexposed to terrorism in the control group. Among those exposed to non-lethal cyberterrorism, perceptions of threat were 10–17% stronger than among those in the control group. These results varied relative to the nature of non-lethal cyberterrorism. Perceptions of cyber threat were strongest when non-lethal cyberattacks resulted in the loss of ‘assets and data’ (Study 1, unidentified perpetrator), rather than the loss of ‘funds’ (Study 2, Hamas). While loss of data and other digital assets might be irreplaceable or costly to replace, banks and other financial institutions usually reimburse customers for funds lost to hackers. Our results indicate that the fact that the perpetrator was Hamas, a hostile agent that one might expect to induce threat perception, did not change this assessment. Indeed, when non-lethal cyberterrorism is defined in terms of financial loss alone, its effects on threat perception were not statistically different than among those in the control group (see notes, Table 2 ). Further data are necessary to substantiate the relationship between perceptions of threat and non-lethal cyber-terrorist attacks.
The data in Tables 1 and 2 clearly suggest that cyberattacks, whether lethal or non-lethal, cause stress, anxiety and insecurity. In their wake, threat perception rises to a level very close to conventional terrorism when cyberterrorism turns deadly. These data demonstrate how cyberterrorism, like conventional terrorism, impairs psychological well-being and increase perceptions of threat. The fear stemming from threat perception may lead to incorrect assessments of risk and risk-averse attitudes that, in turn, impinge upon confidence in government institutions.
Confidence measures, Study 2 (Hamas). Scale 1 (not confident) to 6 (extremely confident) n = 907
| Condition confidence measure . | Control . | Cyberterrorism non-lethal . | Cyberterrorism lethal . | Conventional terrorism . | Sig. ANOVA . |
|---|---|---|---|---|---|
| Confidence in government to protect infrastructures (water, electric, transportation, stock exchange, classified military data) | 4.1 | 4.1 | 4.2 | 4.2 | NS |
| Confident in government to protect personal data | 3.6 | 3.6 | 3.5 | 3.5 | NS |
| Confidence in public/private institutions (army, scientific community, high-tech sector, government, police) to prevent a serious cyberterror attack | 4.4 | 4.6 | 4.5 | 4.5 | NS |
| Confidence in those responsible for cybersecurity to know what they are doing | 4.8 | 5.1 | 5.0 | 5.0 | 0.01 = 2.68 |
| Condition confidence measure . | Control . | Cyberterrorism non-lethal . | Cyberterrorism lethal . | Conventional terrorism . | Sig. ANOVA . |
|---|---|---|---|---|---|
| Confidence in government to protect infrastructures (water, electric, transportation, stock exchange, classified military data) | 4.1 | 4.1 | 4.2 | 4.2 | NS |
| Confident in government to protect personal data | 3.6 | 3.6 | 3.5 | 3.5 | NS |
| Confidence in public/private institutions (army, scientific community, high-tech sector, government, police) to prevent a serious cyberterror attack | 4.4 | 4.6 | 4.5 | 4.5 | NS |
| Confidence in those responsible for cybersecurity to know what they are doing | 4.8 | 5.1 | 5.0 | 5.0 | 0.01 = 2.68 |
In post hoc tests using the Tukey statistic the significant difference lies only in the difference between the control group and the non-lethal cyberterrorism (NS = not significant).
Two other questions posed behavioural choices to gauge confidence:
(1) Following a cyberattack on the water system, the authorities advised drinking bottled water: How soon would you drink tap water? ( n = 909)
(2) Following a cyberattack on the water system, the authorities suggested waiting 3 days before showering: After 3 days, would you? ( n = 909)
In each case, 30–37% of the respondents do not trust the authority’s instructions. Rather, they preferred to take additional measures to protect themselves. The answers to these two questions were unaffected by the manipulations.
Political action following cyberattack on selected facilities, n = 907
| Response (% agreeing) . | Electric Co. . | HMO . | Bank . |
|---|---|---|---|
| Complain to the facility | 30 | 25 | 22 |
| Find a different HMO/bank | 7 | 15 | |
| File a lawsuit | 12 | 14 | 18 |
| Complain to the city | 4 | ||
| Turn to the press | 4 | 3 | 3 |
| Participate in a demonstration | 14 | 4 | 4 |
| File a complaint with the ombudsman | 10 | 7 | |
| Complain to the police | 12 | 11 | |
| Other or none | 37 | 24 | 18 |
| Response (% agreeing) . | Electric Co. . | HMO . | Bank . |
|---|---|---|---|
| Complain to the facility | 30 | 25 | 22 |
| Find a different HMO/bank | 7 | 15 | |
| File a lawsuit | 12 | 14 | 18 |
| Complain to the city | 4 | ||
| Turn to the press | 4 | 3 | 3 |
| Participate in a demonstration | 14 | 4 | 4 |
| File a complaint with the ombudsman | 10 | 7 | |
| Complain to the police | 12 | 11 | |
| Other or none | 37 | 24 | 18 |
While these questions did not specify whether the attack on the facility was lethal or non-lethal, few people are sufficiently riled to take to the streets. A substantial minority (22–30%) would complain to the authorities and some would join a lawsuit (12–18%), but few would demonstrate. None of the attacks prompted outrage or lack of confidence in the government. On the contrary, the manipulations prompted support for greater government intervention to assure security. It is no surprise then, that confidence in the government is generally unaffected by cyberterrorism and may even increase in its wake.
Support for domestic and retaliatory cyber policy
| . | Study 1, = 1027 . | Study 2, = 907 . | Study 3, = 522 . |
|---|---|---|---|
| Perpetrator policy . | Unidentified (% agreeing ) . | Hamas (% agreeing ) . | Anonymous (% agreeing ) . |
| Domestic cyber policy | |||
| Surveillance | |||
| Monitor for suspicious expressions | 67 | 54 | |
| Read emails | 46 | 23 | |
| Monitor Facebook Twitter | 61 | 48 | |
| Regulation of business to maintain cybersecurity | 69 | 62 | 78 |
| Willingness to give up privacy for security | 54 | 44 | |
| Retaliatory policyfollowing a hostile cyber attack | |||
| Cyberattack on military facilities | 84 | 86 | |
| Cyberattack on military and civilian facilities | 78 | 69 | |
| Conventional attack on military facilities | 60 | 37 | |
| Conventional attack on military and civilian facilities | 65 | 31 |
| . | Study 1, = 1027 . | Study 2, = 907 . | Study 3, = 522 . |
|---|---|---|---|
| Perpetrator policy . | Unidentified (% agreeing ) . | Hamas (% agreeing ) . | Anonymous (% agreeing ) . |
| Domestic cyber policy | |||
| Surveillance | |||
| Monitor for suspicious expressions | 67 | 54 | |
| Read emails | 46 | 23 | |
| Monitor Facebook Twitter | 61 | 48 | |
| Regulation of business to maintain cybersecurity | 69 | 62 | 78 |
| Willingness to give up privacy for security | 54 | 44 | |
| Retaliatory policyfollowing a hostile cyber attack | |||
| Cyberattack on military facilities | 84 | 86 | |
| Cyberattack on military and civilian facilities | 78 | 69 | |
| Conventional attack on military facilities | 60 | 37 | |
| Conventional attack on military and civilian facilities | 65 | 31 |
% who agree, very much agree or absolutely agree
Overall, the high percentages of support reflect widespread backing for these policies. Well over 50% support government monitoring of emails for suspicious expressions and roughly 50% are willing to give up privacy for security and allow the government to monitor social media (Facebook, Twitter). At the same time, 23% will permit the government to read emails, a figure that doubles to 46% when the perpetrator is Hamas. These numbers are higher than in the USA where, in a recent PEW Survey [ 32 ] in the USA, 43% of the subjects said it is acceptable for the government to monitor the communications of US citizens (compare 48–67% in our survey).
Looking beyond surveillance to retaliatory policy we see how military strikes, particularly cybernetic but also kinetic, command significant support from the public. In response to cyberterrorism, the vast majority (69–89%) support retaliatory cyberattacks against military and civilian targets while a significant number (31–65%) support conventional, ‘kinetic’ counter attacks. These attitudes remain unstudied in the USA, but there is little doubt that they will play a significant role as public officials and scholars weigh the merit of responding to cyberwar and cyberterrorism with kinetic force [ 33 , 34 ].
To explain why individuals hold different attitudes about surveillance and military retaliation, we looked at a number of factors. The experimental manipulations within each study had no direct effect on political attitudes as they did on anxiety and did not affect the extent to which individuals supported different types of retaliation. That is, support for surveillance, regulation or military action was not affected by exposure to a simulated cyberattack (With the exception of Study 1, (unidentified perpetrator), where the willingness to give up privacy increased as the manipulation grew more severe.). Similarly, self-reported exposure to cyberattacks did not affect attitudes towards these policies. Instead, variables that explain greater support for government interference include political and religious conservatism, threat perception and the identity of the perpetrator. Support from right-wing religious conservatives is consistent with the right’s traditional demand for security and their support for the current right-wing government. Among our subjects, the odds that right-wing conservatives would support militant policies were up to two times higher than those on the left. Beyond the role of political orientation, however, lie the effects of threat perception. As threat perception (in contrast to direct exposure to cyber violence) grows, individuals demand greater security from their government. Here, the odds were 1.3–2.2 times higher that individuals with high levels of threat perception will support surveillance, government regulation and military retaliation compared to those with lower perceptions of threat.
Our data also suggest that the identity of the perpetrator matters. Note how support for government surveillance and, in particular, retaliatory ‘military’ strikes is appreciably greater when the manipulation focused on a known terrorist group, Hamas, (Study 2) rather than on a hacktivist group, Anonymous (Study 3). Our question was framed generally and asked whether subjects would support military retaliation following a cyberattack. We did not ask whether they would support an attack against Hamas or Anonymous or their sponsors. Nevertheless, and as Table 5 demonstrates, subjects participating in the Hamas experiment favoured government surveillance far more than those in Study 3 (Anonymous) and supported conventional military attacks of either sort (limited or large scale) by a margin of nearly 2:1. One reason may be that the manipulation triggered fears of Hamas and burgeoning Islamic radicalism. Another reason may be the recognition that Hamas, like ISIS, has infrastructures and territory vulnerable to conventional attack. Because our study found a relationship between threat perceptions and support for surveillance and military retaliation it seems that it is not Hamas’ material vulnerability but the fear related to threat perception that better explains why those exposed to Hamas cyberterrorism are more likely to support surveillance and military retaliation than those facing Anonymous. Nevertheless, this may change. In a phenomenon, George Lucas [ 35 ] describes as ‘state sponsored hacktivism’, nations recruit hacktivist groups to mount cyberattacks on their behalf. As they do, fears of such groups may grow accordingly as might the willingness to retaliate against their sponsors.
Researchers of risk perception have long noted how individuals’ perceptions of the risk of common hazards [ 27 ] or disease [ 36 ] are often markedly different from the assessments of experts. The result is to make it more difficult to manage risk effectively. How, then, does the public understand the risk of cyberterrorism? If cyberterrorism, unlike conventional terrorism, disease or natural disasters, has yet to harm anyone, there is good reason to suspect that the public does not understand the risk it poses. Experts are themselves divided [ 37 ]. Some remain sceptical about the capabilities of terrorist groups or violent hacktivists to mount offensive, catastrophic cyberattack [ 38–40 ] while others describe how cyberterrorism may seriously compromise electrical infrastructures [ 41 ], disable military defense systems [ 42 ] and, ultimately, ‘undermine conventional and nuclear stability’ [ 43 ]. Divisions among experts might only confound risk perceptions among the lay population.
Risk Assessment, Study 2(Hamas). Scale 1 (very low) to 6 (very high).
| What are the chances of a cyberattack causing: . | Control . | Cyber terror non-lethal . | Cyber terror lethal . | Conventional terrorism . | Sig. ANOVA . | Total average . |
|---|---|---|---|---|---|---|
| 1. Theft of data, assets, identity | 3.0 | 3.1 | 3.1 | 3.2 | NS | 3.1 |
| 2. Attacks on state facilities: military, stock exchange, government offices | 3.7 | 3.7 | 3.5 | 3.8 | NS | 3.6 |
| 3. Destruction/damage of critical infrastructures | 4.4 | 4.7 | 4.6 | 4.8 | <0.001 = 5.9 | 4.6 |
| 4. Loss of life or limb | 2.7 | 2.7 | 3.1 | 3.2 | <0.001 = 19.22 | 2.9 |
| What are the chances of a cyberattack causing: . | Control . | Cyber terror non-lethal . | Cyber terror lethal . | Conventional terrorism . | Sig. ANOVA . | Total average . |
|---|---|---|---|---|---|---|
| 1. Theft of data, assets, identity | 3.0 | 3.1 | 3.1 | 3.2 | NS | 3.1 |
| 2. Attacks on state facilities: military, stock exchange, government offices | 3.7 | 3.7 | 3.5 | 3.8 | NS | 3.6 |
| 3. Destruction/damage of critical infrastructures | 4.4 | 4.7 | 4.6 | 4.8 | <0.001 = 5.9 | 4.6 |
| 4. Loss of life or limb | 2.7 | 2.7 | 3.1 | 3.2 | <0.001 = 19.22 | 2.9 |
A repeated measures ANOVA with a Greenhouse-Geisser correction was statistically significant ( F 2.908, 2640.671 = 904.457, P < 0.001). All the mean scores between the all the different categories of risk assessment were significantly different from each other.
In post hoc tests using the Tukey statistic, there was no significant difference between the the non-lethal cyberterrorism group, the lethal cyberterrorism group and the conventional terrorism group. These three groups were all significantly different from the control group.
In post hoc tests using the Tukey statistic, there was no significant difference between the control group and the non-lethal cyberterrorism group and no significant difference between the lethal cyberterrorism group and the conventional terrorism group. Significant differences were found between lethal cyberterrorism and the control and non-lethal cyberterrorism and between the conventional terrorism and the control and non-lethal cyberterrorism.
| Option . | Percentage agreeing . |
|---|---|
| a. When the authorities say it is OK | 70 |
| b. 3 months after the authorities say it is OK | 24 |
| c. 1 year after the authorities say it is OK | 5 |
| d. Never | 6 |
| a. Shower? | 63 |
| b. Wait 1 week | 19 |
| c. Install a filter that doubled your water bill | 8 |
| d. Install a filter that tripled your water bill | 4 |
These data demonstrate how experimental manipulations exacerbate some assessments of risk from cyberterrorism. After viewing video clips of cyber or conventional terror attacks with lethal consequences, subjects’ perceptions of risk to life, limb and infrastructures were significantly greater than of those viewing the more benign clips (rows 3, 4). When asked to assess the chances of a cyberattack-causing destruction of critical infrastructures the average response rose from 4.4 in the control group to 4.8 in the conventional terrorism group. Similarly, when asked to assess the chances of a cyberattack-causing loss of life and limb the average response rose from 2.7 in the control group to 3.2 in the conventional terrorism group. On the other hand, the manipulations did not affect the risk associated with data theft or attacks on the stock exchange or government offices (rows 1, 2). These stayed constant across the manipulations. These attitudes reflect concerns about the future threat of cyberterrorism. The risk associated with identity theft, asset loss and attacks on the government offices is stable, while the risk associated with significant bodily or infrastructural harm is not. Individuals seem to think they understand the risks of non-lethal cyberterrorism but seem unsure about the risks of lethal cyberterrorism when, in fact, our data indicate much the opposite. They underestimate the danger of non-lethal cyberterrorism while often overestimating the danger of lethal terrorism particularly when the perpetrator is a known terrorist organization. As such, it is important to notice that the perception of threat, in part, contradicts reality. For many subjects, the risk of an attack that destroys or damages critical infrastructures, which has yet to materialize to any significant degree (average 4.6), is significantly ‘greater’ than the risk of an attack on stock exchanges, government offices, personal computers, banks and credit cards that are clear and present dangers (average 3.6). While these outcomes might be partially explained by a manipulation that primes subjects for threats to infrastructures, our control group viewed no attack and still assessed some risks unrealistically high. At the same time the average perception of risk associated with the theft of data, assets and identity (average 3.1) was little different from a risk that a cyberattack would bring death or injury (average 2.9). They perceive the risk of these hazards equally despite the fact that the former is relatively common and the latter non-existent.
Our results show that cyberterrorism, even when non-lethal, impacts the civilian population in several ways. First, cyberterrorism aggravates anxiety and personal insecurity. Secondly, lethal and non-lethal terrorism exacerbate perceptions of threat and personal insecurity. Thirdly, many people, particularly those with high levels of threat perception, are willing to support strong government policies. These policies split along two lines and include foreign policy (e.g. cyber and/or kinetic military responses to cyberattacks) and domestic policy (e.g. tolerance of government surveillance and control of the Internet). As threat perception increases, individuals take increasingly stringent political views. Like conventional terrorism, cyberterrorism hardens political attitudes as individuals are willing to exchange civil liberties and privacy for security and support government surveillance, greater regulation of the Internet and forceful military responses in response to cyberattacks. And while these measures are meant to ensure national security, such foreign and particularly domestic policies may adversely affect the unfettered discourse necessary for a vibrant and open democratic society [ 44 ].
Nevertheless, cyberterrorism does not significantly undermine confidence in the national government or its institutions any more than conventional terrorism does. This was evident from our confidence measures comparing a control group to those exposed to depictions of conventional and cyberterrorism. As noted at the head of this article, such broad measures of confidence are not always affected by terrorism or other traumatic events. On the contrary, such events often strengthen public confidence as occurred in the USA post 9/11 [ 11 , 9 ]. These findings about confidence go hand in hand with demands for greater security. As individuals, particularly those with heightened levels of threat perception, demand more government oversight, they cannot express a lack of confidence in the government without unease. Supporters of intrusive government regulation and surveillance must be confident that the authorities will do their jobs effectively and without abusing the greater authority they now enjoy.
This does not mean governments can remain quiescent. This is true for governments in Israel, whose population was the subject of these studies, and just as important for governments in the USA, Europe and elsewhere. Just as 20th-century studies of the psychology of terrorism in Israel informed post 9/11 research, the effects of cyberterrorism in Israel are equally relevant. Cyberterrorism is a transnational phenomenon and we see that agents like Anonymous are as equally prepared to disrupt American networks (as they did in Ferguson, MO in 2014 [ 46 ]) as they are Israeli systems. In fact, the effects of cyberterrorism may prove weaker in Israel than elsewhere as research develops. For Israelis, Hamas is a known quantity, a partner to a long simmering but, to date, manageable conflict that occasionally erupts into sustained violence. To pursue its goals Hamas must publicize its demands and attacks. Attribution is not an issue. For ISIS and the proxies of hostile nations, on the other hand, this is not necessarily true. Attacks are difficult to attribute with certainty and hacktivist demands are often unknown, thereby allowing foreign governments to conduct offensive cyber operations by proxy. Such attacks trade on uncertainty and disruption that may exacerbate anxiety, threat and risk perception in many Western nations to a greater extent than we have seen in Israel.
The outsized risk attributed to threats to life, limb and infrastructure track previous studies that ascribe relatively high levels of risk perception to hazards associated with uncertainty and dread risk, i.e. events ‘perceived by lack of control, dread, catastrophic potential and fatal consequences’ [ 27 ]. Lichtenstein et al. [ 36 ] describe how media exposure, particularly sensational media coverage, catastrophic outcomes and lack of direct experience skew assessments of risk. To some extent, cyberterrorism fits these models. Although there are only hypothetical lines between cyberattacks and mass casualties, the great risk attributable to infrastructure damage and loss of life and limb might be explained by their possible catastrophic effects, the benefits that they provide (thereby making them a likely target as well as a significant source of concern if threatened), the inability to always identify perpetrators or their motives, and the division of opinion among experts that only exacerbates uncertainty. The role of media coverage remains unstudied but may provide insight into the high risks that many people associate with cyberterrorism. Slovic [ 60 ] also reminds us that a kinetic terrorist attack comes with significant ‘signal value’, the perception that an event will reverberate in the future and generate further death, destruction and mayhem [ 47 ]. The result is to overestimate risk. On the other hand, and in contrast to the studies cited, cyberterrorism has never caused death or injury. As such, cyber risk, with is peculiar counterfactual (if we protect ourselves nothing will continue to happen), is likely to be the next frontier of risk perception theory.
Finally, our data suggest that threat perception and not only actual cyber events drive the cognitive effects of cyberterrorism. While individuals demand Internet surveillance and regulation, and forceful military responses to cyberattack following the experimental manipulations, many people are responding to their fears rather than to specific cyber events. In other words, it does not take exposure to actual events to trigger anxiety, rather the perception of threat alone. These results are consistent with studies that document how simply raising and lowering terror threat alerts can increase anxiety and depression and foster a willingness to ‘accept both restrictions on their personal freedoms … and violent actions against others’ [ 48 ]. Here, too, there is no actual attack in the offing, only the fear of an attack. Threat perception, not an actual attack is sufficient to unsettle individuals to the extent many terrorists desire. As a result, authorities will need to recognize that they cannot reduce fears of cyberterrorism and its pervasive effects solely by eliminating cyberattacks that will, quite possibly, only grow more severe. Rather, policymakers must think about ways to enhance resilience in much the way they have in the context of kinetic terrorism and other disasters.
Lessons gleaned from successful (and unsuccessful) efforts to improve disaster preparedness [ 49–53 ] suggest that the government, the private sector and the academic community should effectively communicate the risks of cyberterrorism and take steps that will help instill effective cybersecurity practices. Furthermore, if individuals feel they can communicate their concerns to their government and the authorities are attentive (i.e. citizens have a sense of political efficacy) then threat perceptions may be reduced (Canetti et al. , unpublished work [ 54 ]). These efforts are intertwined. Providing cybersecurity depends, in part, upon securing compliance with cybersecurity measures. Compliance, in turn, depends upon how accurately the public assesses the risk of cyberattacks and upon how successfully government and private agencies communicate cyber risks and the precautions that individuals must take.
To secure computer systems, we draw attention to the many programmes in schools and businesses to impart the knowledge and skills individuals need to maintain personal cybersecurity. Currently, it is our impression that the only evaluation tool is performative, i.e. how well end-users master and adopt the necessary skills to protect their online assets (e.g. recognizing malware, changing passwords, updating firewalls). To fully assess the benefits of these tools, further research is required to understand how these educational and intervention programmes might impart the fear/stress reducing skills to cope with cyberterrorism and to improve resiliency, i.e. withstand adverse psychological effects of cyberterrorism, overcome feelings of vulnerability and regain a sense of control. Experience with kinetic terrorism also points to the benefits of psychological intervention [ 55 ]. Mitigating the deleterious effects of cyberterrorism and strengthening resilience may diminish the impact of cyberterrorism and the chance it will spill over into militancy, kinetic war and protracted conflict.
This research was made possible, in part, by grants awarded to D.C. from the National Institute of Mental Health (R01 MH073687), from the Israel Science Foundation (594/15) and from the US-Israel Binational Science Foundation (2009460) and to M.L.G. from the Israel Science Foundation (156/13). An earlier version of this article was presented at Stanford University in March 2016 as part of the Cyber Policy Program Workshop on Strategic Uses of Offensive Cyber Operations. We wish to thank Herb Lin who organized the conference and provided valuable input during the early stages of this project and to the conference participants who commented on earlier drafts of this study during the workshop.
Sinclair SJ , Antonius D. The Political Psychology of Terrorism Fears . Oxford : Oxford University Press , 2013 .
Google Scholar
Google Preview
Luft B. We're not Leaving: 9/11 Responders Tell Their Stories of Courage, Sacrifice, and Renewal . New York : Greenpoint Press , 2011 .
Hobfoll SE , Palmieri PA , Johnson RJ et al. . Trajectories of resilience, resistance, and distress during ongoing terrorism: the case of Jews and Arabs in Israel . J Consult Clin Psychol 2009 ; 77 : 138 – 148 .
Norris FH , Tracy M , Galea S. Looking for resilience: understanding the longitudinal trajectories of responses to stress . Soc Sci Med 2009 ; 68 : 2190 – 98 .
De Mesquita EB . Conciliation, counterterrorism, and patterns of terrorist violence . International Organization 2005 ; 59 : 145 – 76 .
Gross ML. The Ethics of Insurgency: A Critical Guide to just Guerrilla Warfare . Cambridge : Cambridge University Press , 2015 .
Goodrich JN. September 11, 2001 attack on America: a record of the immediate impacts and reactions in the USA travel and tourism industry . Tourism Manage 2002 ; 23 : 573 – 80 .
Fierke KM. Terrorism and trust in Northern Ireland . Critic Stud Terror 2009 ; 2 : 497 – 511 .
Gross K , Brewer PR , Aday S. Confidence in government and emotional responses to terrorism after September 11, 2001 . Am Polit Res 2009 ; 37 : 107 – 28 .
Smith TW , Rasinski KA , Toce M. America Rebounds: A National Study of Public Response to the September 11th Terrorist Attacks . Chicago, IL : National Opinion Research Center, University of Chicago , 2001 .
Rasinski KA , Berktold J , Smith TW et al. . America Recovers: A Follow-up to a National Study of Public Response to the September 11th Terrorist Attacks . Chicago, IL : National Opinion Research Center, University of Chicago , 2002 .
Wollebæk D , Enjolras B , Steen-Johnsen K et al. . After Utøya: how a high-trust society reacts to terror—trust and civic engagement in the aftermath of July 22 . PS: Polit Sci Politic 2012 ; 45 : 32 – 37 .
Baldwin TE , Ramaprasad A , Samsa ME. Understanding public confidence in government to prevent terrorist attacks . J Homeland Secur Emerg Manage 2008 ; 5 : 18 – 30 .
Berry MS , Baldwin TE , Samsa ME et al. . The effect of terrorism on public confidence: an exploratory study. Argonne National Laboratory, ANL/DIS-08/6, 2008 .
Canetti D, Gross ML, Waismel-Manor I. Immune From Cyber-Fire? The Psychological & Physiological Effects of Cyberwar. In: Allhoff F, Henschke A, and Strawser BJ (eds). Binary Bullets: The Ethics of Cyberwarfare. Oxford: Oxford University Press, 2016, 157–76.
Schmitt MN (ed). Tallinn Manual on the International Law Applicable to Cyber Warfare . Cambridge : Cambridge University Press , 2013 .
Polityuk, P. 2016. Ukraine Sees Russian Hand in Cyber Attacks on Power Grid.Reuters 12 February. http://www.reuters.com/article/us-ukraine-cybersecurity-idUSKCN0VL18E
Baker R , Blumberg SJ , Brick JM et al. . Research synthesis AAPOR report on online panels . Public Opin Quart 2010 ; 74 : 711 – 81 .
Callegaro M , Baker R , Bethlehem J et al. . (eds). Online Panel Research: A Data Quality Perspective . West Sussex, UK : John Wiley and Sons , 2014 .
Deardon L. Anonymous vows to wreak ′electronic holocaust′ on Israel for ′crimes in the Palestinian territories′. The Independent , 31 March 2015 .
Marteau TM , Bekker H. The development of a Six-Item Short-Form of the State Scale of the Spielberger State—Trait Anxiety Inventory (STAI) . British Journal of Clinical Psychology 1992 ; 31 : 301 – 306 .
Canetti-Nisim D , Ariely G , Halperin E. Life, Pocketbook, or Culture: The Role of Perceived Security Threats in Promoting Exclusionist Political Attitudes towards Minorities in Israel . Political Research Quarterly 2008 ; 61 : 90 – 103 .
Canetti D , Lindner M. Exposure to political violence and political behavior. In: Reynolds K , Branscombe N (eds), Psychology of Change: Life Contexts, Experiences, and Identities . New York : Psychology Press , 2014 , 77 – 94 .
Raijman R , Semyonov M. Perceived threat and exclusionary attitudes towards foreign workers in Israel . Ethnic Racial Stud 2004 ; 27 : 780 – 99 .
Hobfoll SE , Canetti‐Nisim D , Johnson RJ et al. . The association of exposure, risk, and resiliency factors with PTSD among Jews and Arabs exposed to repeated acts of terrorism in Israel . J Trauma Stress 2008 ; 21 : 9 – 21 .
Huddy L , Feldman S , Capelos T et al. . The consequences of terrorism: disentangling the effects of personal and national threat . Polit Psychol 2002 ; 23 : 485 – 509 .
Slovic P. Perception of risk . Science 1987 ; 236 : 280 – 85 .
Davis DW , Silver BD. Civil liberties vs. security: public opinion in the context of the terrorist attacks on America . Am J Polit Sci 2004 ; 48 : 28 – 46 .
Echebarria‐Echabe A , Fernández‐Guede E. Effects of terrorism on attitudes and ideological orientation . Eur J Social Psychol 2006 ; 36 : 259 – 65 .
Getmansky A , Zeitzoff T. Terrorism and Voting: the effect of rocket threat on voting in Israeli elections . Am Polit Sci Rev 2014 ; 108 : 588 – 604 .
Lerner JS , Gonzalez RM , Small DA et al. . Effects of fear and anger on perceived risks of terrorism a national field experiment . Psychol Sci 2003 ; 14 : 144 – 50 .
PEW American's Privacy Strategies Post Snowden , 2015 http://www.pewinternet.org/files/2015/03/PI_AmericansPrivacyStrategies_0316151.pdf
Libicki, C. From the Tallinn Manual to Las Vegas rules. In: Cyberspace in Peace and War. Annapolis MD: Naval Institute Press, 2016, chapter 32, forthcoming.
Farell H , Glaser CL. An effects-based approach to escalation and deterrence in cyberspace. In: Stanford Cyber Policy Program Workshop on Strategic Uses of Offensive Cyber Operations. Stanford, CA : Stanford University , March 3-4, 2016 .
Lucas GR. State sponsored hacktivism. In: Gross ML, Meisels T. (eds), Soft War, the Ethics of Unarmed Conflict . Cambridge : Cambridge University Press , 2017 .
Lichtenstein S , Slovic P , Fischhoff B et al. . Judged frequency of lethal events . J Exp Psychol 1978 ; 4 : 551 – 578 .
Jarvis LS , Macdonald S , Nouri L. The cyberterrorism threat: findings from a survey of researchers . Stud Conflict Terror 2014 ; 37 : 68 – 90 .
Lewis JA. Assessing the Risks of Cyber Terrorism, Cyber War and Other Cyber Threats . Washington, DC: Center for Strategic and International Studies, 2002 .
Lucas GR. Cyber warfare. In: Johnson JT , Patterson ED (eds), The Ashgate Research Companion to Military Ethics . London : Ashgate , 2015 , 245 – 58 .
Valeriano B , Maness RC. The coming cyberspace: the normative argument against cyberwarfare . Foreign Affairs , 13 May 2015 .
Bronk C. Getting creative on what will do: cyber espionage, conflict and covert action. In: Stanford Cyber Policy Program Workshop on Strategic Uses of Offensive Cyber Operations . Stanford, CA : Stanford University , March 3-4, 2016 .
Aucsmith D. Disintermediation, counterinsurgency, and cyber defense. In: Stanford Cyber Policy Program Workshop on Strategic Uses of Offensive Cyber Operations . Stanford, CA : Stanford University , March 3–4, 2016 .
Gartzke E , Lindsay J. Cyberwar in a thermonuclear world. Stanford Cyber Policy Program Workshop on Strategic Uses of Offensive Cyber Operations . Stanford, CA : Stanford University , March 3-4, 2016 .
Gross ML , Canetti D , Vashdi DR. The psychological effects of cyber terrorism . Bull Atom Sci 2016 ; 72 : 284 – 91 .
Gross K , Brewer PR , Aday S. Confidence in government and emotional responses to terrorism after September 11, 2001 . American Politics Research 2009 ; 37 : 107 – 28 .
Kerr D , Ferguson M. Police site hit with DDoS attack . CNET , 15 August 2014 .
Jenkin CM. Risk perception and terrorism: applying the psychometric paradigm . Homeland Secur Affair 2006 ; ii : 1 – 14 .
McDermott R , Zimbardo PG. The psychological consequences of terrorist alerts. In: Bongar B , Brown LM , Beutler LE et al. . (eds), Psychology of Terrorism. Oxford : Oxford University Press , 2007 , 357 – 70 .
Barry MM , Sixsmith J , Infanti JJ. A Literature Review on Effective Risk Communication for the Prevention and Control of Communicable Diseases in Europe . Stockholm: ECDC, 2013 .
Basolo V , Steinberg LJ , Burby RJ et al. . The effects of confidence in government and information on perceived and actual preparedness for disasters . Environment and Behavior 2008 ; 43 : 338 – 64 .
Gray GM , Ropeik DP. Dealing with the dangers of fear: the role of risk communication . Health Affair 2002 ; 21 : 106 – 16 .
Fischhoff B , Gonzalez RM , Small DA et al. . Evaluating the success of terror risk communications . Biosecur Bioterror 2003 ; 1 : 255 – 58 .
Wood MM , Mileti DS , Kano M et al. . Communicating actionable risk for terrorism and other hazards . Risk Anal 2012 ; 32 : 601 – 15 .
Canetti D , Navot D , Vashdi D et al. . Political resources effect? Evidence from a longitudinal study on exposure to violence and psychological distress in Israel (unpublished manuscript).
Canetti D , Hall BJ , Rapaport C et al. . Exposure to terrorism and political extremism: a stress-based process . Eur Psychol 2013 ; 18 : 263 – 72 .
Canetti-Nisim D , Halperin E , Sharvit K et al. . A new stress-based model of political extremism personal exposure to terrorism, psychological distress, and exclusionist political attitudes . J Confl Resolut 2009 ; 53 : 363 – 89 .
Hirsch-Hoefler S , Canetti D , Rapaport C et al. . Conflict will harden your heart: exposure to violence, psychological distress and peace barriers in Israel and Palestine . Brit J Polit Sci 2014 ; 44 : 1 – 15 .
Huddy L , Feldman S. Americans respond politically to 9/11: understanding the impact of the terrorist attacks and their aftermath . Am Psychol 2011 ; 66 : 455 – 67 .
Rubin GJ , Brewin CR , Greenberg N et al. . Enduring consequences of terrorism: 7-month follow-up survey of reactions to the bombings in London on 7 July 2005 . Brit J Psychiat 2007 ; 190 : 350 – 56 .
Slovic P. The perception of risk. In: Sternberg RJ , Fiske ST , Foss DJ (eds), Scientists Making a Difference , Cambridge : Cambridge University Press , 2016 , 179 – 82 .
| Month: | Total Views: |
|---|---|
| February 2017 | 44 |
| March 2017 | 73 |
| April 2017 | 50 |
| May 2017 | 54 |
| June 2017 | 87 |
| July 2017 | 48 |
| August 2017 | 38 |
| September 2017 | 78 |
| October 2017 | 172 |
| November 2017 | 141 |
| December 2017 | 1,014 |
| January 2018 | 929 |
| February 2018 | 727 |
| March 2018 | 877 |
| April 2018 | 1,528 |
| May 2018 | 1,501 |
| June 2018 | 1,139 |
| July 2018 | 824 |
| August 2018 | 1,082 |
| September 2018 | 1,301 |
| October 2018 | 1,665 |
| November 2018 | 1,861 |
| December 2018 | 1,404 |
| January 2019 | 998 |
| February 2019 | 1,367 |
| March 2019 | 1,825 |
| April 2019 | 1,942 |
| May 2019 | 1,710 |
| June 2019 | 1,183 |
| July 2019 | 1,100 |
| August 2019 | 1,098 |
| September 2019 | 1,228 |
| October 2019 | 1,004 |
| November 2019 | 921 |
| December 2019 | 556 |
| January 2020 | 475 |
| February 2020 | 542 |
| March 2020 | 446 |
| April 2020 | 676 |
| May 2020 | 405 |
| June 2020 | 393 |
| July 2020 | 334 |
| August 2020 | 322 |
| September 2020 | 405 |
| October 2020 | 561 |
| November 2020 | 544 |
| December 2020 | 482 |
| January 2021 | 450 |
| February 2021 | 450 |
| March 2021 | 601 |
| April 2021 | 571 |
| May 2021 | 813 |
| June 2021 | 619 |
| July 2021 | 453 |
| August 2021 | 439 |
| September 2021 | 619 |
| October 2021 | 790 |
| November 2021 | 805 |
| December 2021 | 692 |
| January 2022 | 595 |
| February 2022 | 804 |
| March 2022 | 681 |
| April 2022 | 742 |
| May 2022 | 839 |
| June 2022 | 481 |
| July 2022 | 477 |
| August 2022 | 404 |
| September 2022 | 452 |
| October 2022 | 583 |
| November 2022 | 448 |
| December 2022 | 423 |
| January 2023 | 414 |
| February 2023 | 341 |
| March 2023 | 518 |
| April 2023 | 532 |
| May 2023 | 527 |
| June 2023 | 373 |
| July 2023 | 256 |
| August 2023 | 237 |
| September 2023 | 310 |
| October 2023 | 394 |
| November 2023 | 329 |
| December 2023 | 346 |
| January 2024 | 319 |
| February 2024 | 340 |
| March 2024 | 398 |
| April 2024 | 422 |
| May 2024 | 369 |
| June 2024 | 177 |
| July 2024 | 189 |
| August 2024 | 175 |
Email alerts
Citing articles via, affiliations.
- Online ISSN 2057-2093
- Print ISSN 2057-2085
- Copyright © 2024 Oxford University Press
- About Oxford Academic
- Publish journals with us
- University press partners
- What we publish
- New features
- Open access
- Institutional account management
- Rights and permissions
- Get help with access
- Accessibility
- Advertising
- Media enquiries
- Oxford University Press
- Oxford Languages
- University of Oxford
Oxford University Press is a department of the University of Oxford. It furthers the University's objective of excellence in research, scholarship, and education by publishing worldwide
- Copyright © 2024 Oxford University Press
- Cookie settings
- Cookie policy
- Privacy policy
- Legal notice
This Feature Is Available To Subscribers Only
Sign In or Create an Account
This PDF is available to Subscribers Only
For full access to this pdf, sign in to an existing account, or purchase an annual subscription.
Advertisement
An Explorative Study into the Importance of Defining and Classifying Cyber Terrorism in the United Kingdom
- Original Research
- Open access
- Published: 24 November 2021
- Volume 3 , article number 84 , ( 2022 )
Cite this article
You have full access to this open access article

- Victoria Jangada Correia ORCID: orcid.org/0000-0002-0305-3381 1
8227 Accesses
8 Citations
1 Altmetric
Explore all metrics
Terrorism, crime, and war are all familiar notions; however, the way in which these have been altered through cyberspace is not yet fully, nor unanimously, understood through definitions, theories, and approaches. Although the threat level of terrorism in the UK has lowered to moderate, the threat posed by cyber terrorism has nonetheless heightened throughout the COVID pandemic due to the greater necessity and presence of technology in our lives. This research aimed to highlight the necessity for a unanimous cyber terrorism definition and framework and further aimed to determine what perceptions are held by the general public regarding cyber terrorism through a mixed methods approach. The literature review confirms that there is an absence of a unanimously agreed upon definition of cyber terrorism, and furthermore that the existing academic definitions are not compatible with UK legislation. In addition, the literature review highlights an absence of a cyber terrorism framework that classifies what kind of terrorist activity is cyber enabled or cyber dependent. Quantitative data from the online survey find a couple of significant effects implying the necessity for greater diversity amongst stakeholders which could potentially enhance the detection and prevention of terrorism in the UK. The qualitative data find that although there is some agreement amongst the sample population in views held towards cyber terrorism, some misconceptions are nonetheless present which could have implications on the general public’s ability to identify and report cyber terrorist activity. Overall, the findings from the literature review and the primary data collection aid in developing a cyber terrorism definition that is compatible with UK legislative definitions, and further aids in developing a terrorist activity framework that succinctly highlights the inextricable links between traditional, cyber enabled, and cyber-dependent terrorism.
Similar content being viewed by others

Understanding, Locating and Constructing Cyberterrorism

Learning Lessons from Countering Terrorism: the UK Experience 2017–2020

Cyber Terrorism: A Growing Threat to India’s Cyber Security
Explore related subjects.
- Artificial Intelligence
Avoid common mistakes on your manuscript.
Introduction
Overview of research.
For almost up to 2 decades, the search for defining cyber terrorism has been described as the ‘Holy Grail’ for scholars and policy makers [ 1 ]. This has been escalated during the recent COVID pandemic where life has made a remarkable shift towards online activity, placing individuals at a much higher risk of being vulnerable to cyber terrorist activities [ 2 ]. Although there has been considerable research focusing on how cyber capabilities facilitate terrorism [ 3 , 4 , 5 ], there is nonetheless significant disagreement surrounding what definitions and approaches should be used unanimously to facilitate in preventing, detecting, investigating, and prosecuting cyber terrorist threats by key stakeholders in the United Kingdom (UK) such as the police, prosecution services and policy makers and international stakeholders too.
This disagreement could be due to the notion that cyber terrorism as a term, houses a wide range of illicit behaviours including hacking and phishing, to sharing online propaganda, radicalising and recruiting individuals. Therefore, attempting to define everything under the term ‘cyber terrorism’ can become challenging due to legal contexts, objectives of the illicit behaviour, and intent [ 6 ]. The lack of a unanimous definition has further delayed a framework for cyber terrorism being developed. McGuire and Dowling [ 7 ] coined the cyber-dependant and cyber-enabled cybercrime classification; however, cyber terrorism was outside the scope at the time, and this has not been further reviewed to date.
As at financial year end on March 2020, 261 arrests of terrorism-related activity were recorded [ 8 ]. However, as at financial year end on March 2021, there was a 37% reduction in terrorism-related arrests [ 9 ]. Not only are these statistics potentially reflective of the three national lockdowns and restrictions put in place for the COVID pandemic but are also potentially indicative of terrorist activity transitioning further into online platforms and not being regulated effectively. It was found that in the middle of the pandemic, terrorist groups had been altering their methods of sharing their beliefs through a plethora of online platforms, from disseminating propaganda to spreading misinformation and conspiracies to attain further support [ 2 ]. These findings highlight a socio-technical perspective in which the inextricable links between terrorist technological use and its impacts on society are evident. This perspective highlights the need for a more collaborative approach from stakeholders to create greater security for society from terrorism.
Interestingly, the aforementioned issues are also prevalent and long-standing in the taxonomy of cybercrime and the crimes which are included under this term [ 10 , 11 , 12 ]. This alludes to widespread conflict in the foundational understanding of cybercrime as a whole which inevitably affects the approach to counter cyber terrorism. Therefore, the rationale for this research highlights the importance of law enforcement, policy makers and prosecuting services having a clear definition and framework for cyber terrorism and its links to traditional terrorism, allowing them to combat the threat collaboratively. However, it is perhaps important to note that recent research found that the use of nonspecific interventions to deter terrorist activity could in fact lead to an increase in terrorist attacks [ 13 ]. In light of this, more specific interventions and a clearer understanding of underlying criminal behaviours are necessary to effectively combat the threat of terrorism, further highlighting the need for a more unanimous and concise definition and approach from relevant stakeholders in countering cyber terrorism.
Research Aims and Objectives
This research primarily aims to establish a concise definition of cyber terrorism and a suitable framework that clearly elaborates on terrorist and cyber terrorist activity to be considered by UK stakeholders. In order to achieve this primary aim, this research’s research will investigate and critically analyse the etymology of the words so to better understand the term ‘cyber terrorism’. Furthermore, current definitions of terrorism and cyber terrorism will be reviewed and analysed to determine the strengths and weakness of viewing cyber terrorism in certain ways. Additionally, Space Transition Theory [ 14 ] and Routine Activity Theory [ 15 ] will be analysed to inform a discussion on cyber terrorist behaviours and processes. Lastly, the Smith et al. terrorist group activity process [ 16 ] will be analysed alongside the McGuire and Dowling [ 7 ] dual binary classification, to support the development of a proposed framework.
This research then aims to determine what the public’s perceptions are towards cyber terrorism as this could be representative of bigger issues regarding misconceptions on the topic. To conduct a reasonable investigation, this research will collect quantitative and qualitative primary data by means of an online survey. The data will first be statistically analysed to determine any significance between participant demographics and opinions. The data will then be thematically analysed to determine any strong themes which relate to participant opinions and identify common views held by the sample population in context of the findings from the literature review.
Article Layout
The structure which this research will follow includes a literature review where relevant literature, definitions, and frameworks will be evaluated to present a clear outline on what the current state of defining cyber terrorism is. This will be followed by a methodology chapter which will discuss and analyse the mixed methods approach adopted for this research’s primary data collection. Subsequently, the quantitative and qualitative results will be interpreted in the context of the findings from the literature review, with analysis of the implications and limitations of the data. Within the results and findings chapter, a new cyber terrorism definition and framework will be proposed and analysed. Finally, the research will offer conclusions and recommendations highlighting how the study could be improved and further researched.
Literature Review
Modern day understanding of terrorism.
Defining terrorism is a subject matter undergoing much discourse [ 17 , 18 , 19 ]. This struggle in defining terrorism could be attributed to the difficulty in reflecting ideological, philosophical, political and religious normative differences under a single term. As a result of this, further confusion can become apparent in justifying the legality or illegality of suspected terrorist activity. Terrorism has been depicted as a social construct as the meaning of it is shaped by the views held by the person categorising what terrorism means to them [ 20 , 21 ].
According to Hewer and Taylor, the term terrorism is merely a marker used by governments to legitimise or delegitimise politically motivated violence occurring in their country [ 22 ]. A good example of this is the paradoxical nature between the Middle East and the West in their characterisation of terrorism. In the Middle East there is an amalgamation between religious identity and politics which influences societal and cultural concepts directly [ 23 , 24 ], whereas in the west there is a strong distinction between religion and politics resulting in a democratic society which enables an array of societal and cultural ideals to cohabit [ 22 , 25 ]. The beliefs and ideologies held by the West and the Middle East see one another as a threat to their respective core norms and values which is potentially where the notion of terrorism emerges [ 26 , 27 ]. Overall, this information emphasises the belief that different countries may have different meanings of what qualifies as a terrorist act or not depending on their political and religious alignment. In light of this, it is important to acknowledge that the prosecution of a terrorist who is not based in the UK may be troublesome due to these differing aspects, especially with cyber terrorism where threats or acts of violence and disruption can be communicated or committed through cyber capabilities off British soil.
The Terrorism Act 2006 [ 28 ] and The Counter-Terrorism Act 2008 [ 29 ] are amongst some of the acts which detail illicit behaviours within terrorist activity. More specifically, The Terrorism Act 2006 defines terrorism as an act, or threat of act of violence against the public and/or property, to intimidate the public and/or property, or to advance political or religious ideologies. This definition has been criticised due to its implications on principles of legality and its lack of clarity in defining what actions are ascribed as ‘terrorist’ which may mislead public and political perceptions regarding terrorism [ 18 , 21 ]. This vagueness could be attributed to confusing wording within legislation, which could further cause individuals engaging in terrorist activity to not be aware of the illegality behind their behaviour. Regardless of these downfalls, it is important to consider the UK’s legislative definition of terrorism in this literature review as it is pertinent that any future cyber terrorism definition be compatible with already existing legislation.
Media coverage has also contributed massively to the way in which terrorism is defined and understood and have blurred the lines between victims and perpetrators of terrorist acts [ 30 ]. The media’s use of terms such as ‘freedom fighting’, ‘insurgency’ and ‘extremism’ has caused the foundational meaning of terrorism to be replaced and misunderstood [ 18 ]. As a result, the original understanding of the term terrorism has been modified to suit the many political and religious terrorist organisations operating in modern society. This could potentially result in news media outlets shaping and promoting misconceptions amongst public opinion.
This can be better understood through Gatekeeping Theory which explores the way in which information is selected and disseminated to a group of people by news media outlets [ 31 , 32 , 33 ]. Shoemaker and Vos [ 32 ] further developed the theory, specifically investigating the way in which information of an event is passed through a series of ‘gatekeepers’ who determine what information will be disseminated, how and to whom. This theory challenges one to consider how the gatekeeping process may potentially wittingly or unwittingly distort the general public’s understanding of terrorism and terrorist activity according to the differing political, religious, or societal alignments held by news media outlets. In light of these findings, it is clear that a unanimous understanding of terrorism should be shared across the various stakeholders to improve the accuracy of the information being shared to the public.
Understanding the ‘Cyber’ Prefix
The term ‘cyber’ as we know it today originates back to kebernetes which was an ancient Greek phrase which translates to ‘the art of steering’ [ 34 ]. It was not until mathematician Norbert Wiener used the word cybernetics in the 1940s that the term came to be known as a study of the systems within living beings and artificial machines [ 35 ]. This term was further influenced by pop culture in the 1980s during the cyberpunk movement which was inspired by William Gibson’s novel Neuromancer [ 36 ], which further associated the ‘cyber’ term with dystopian and futuristic concepts. At a similar time to this, there had also been a shifting approach and understanding within the US military with regard to information warfare and the changing nature of the modern battlefield [ 37 ].
Flutter argues that the cyber prefix is nothing but a catchall phrase which has resulted in a term that has been overly ill-defined due to the various range of factors which it tries to explain [ 38 ]. In his article, Flutter suggests that returning the terms ‘Information Warfare’, ‘Information Operations’ and ‘Computer Network Operations’ instead of the cyber prefix would be more beneficial as this would clearly classify crimes which are dependent to technology. Conversely to this view, it has been argued that a definition of cyberspace should not be solely categorised under the technological components as “cyberspace allows the exercise of power” [ 39 ]. Although Computer Network Operations as a term has mostly been used in warfare, there have yet been implications to push this into the broader scope of cybercrimes.
It could be useful to apply the above terms to terrorism rather than the cyber prefix as this could more clearly define terrorist activity which is fully dependent on technological capabilities such as denial of service attacks. This approach to focus on the computer and information operations has been adopted by a few academics in their definitions of cyber terrorism [ 40 , 41 ]. However, such an approach is arguably limited as it excludes other types of terrorist activities which are being enabled by other aspects of technology such as the dissemination of terrorist propaganda and recruitment. Although separate terms could be designed to distinguish between these differing approaches to terrorist activity, the cyber prefix has become a synonymous catch all phrase distinguishing between traditional crimes and more modern crimes being committed through technological capabilities. In light of this, a term such as ‘computer network operations’ or ‘information warfare’ may not be suitable to further explore and define cyber terrorism as these terms overlook other types of terrorist activity. In turn, this would reject the inextricable links between technology, terrorism, and their impacts on communities, not just computer networks. Therefore, this literature review proposes that the use of the cyber prefix is pertinent for a clear and synonymous categorisation between traditional terrorism and cyber terrorism.
Current Definitional Interpretations of Cyber Terrorism
Cyber terrorism definitions are mostly based upon traditional terrorism definitions such as the aforementioned. It has been suggested that attacks can qualify as cyber terrorism if there is intent to impede on the political, social, or economic functioning of a group, organisation or country, or to provoke/perpetrate acts of physical violence [ 42 ]. Holt further supports this definition by suggesting that the term cyber terrorism should encapsulate the behaviour leading to the act, without necessarily resulting in physical disruption or damage [ 43 ]. Both these definitions put emphasis on the intent and motivations behind cyber terrorist activity instead of narrowly focusing on the physical impacts.
Conversely, other academics have taken a different stance on the matter and have argued that to qualify an attack under cyber terrorism, physical damage and/or disruption against a computer or network must occur [ 40 , 41 ]. Despite efforts made by academics to define cyber terrorism, some have further argued that the cyber prefix to terrorism only elaborates on the method employed in committing terrorism and therefore ‘cyber terrorism’ does not require its own category [ 44 ]. As technology continues to evolve and becomes more accessible, viewing cyber terrorism as proposed by Gordon and Ford [ 44 ] and Denning [ 41 ], could pose a greater risk to public safety, as well as impact law enforcement’s understanding and approaches in preventing, detecting, and investigating cyber terrorist activity.
These cyber terrorism definitions offer differing insights into what may and may not qualify as cyber terrorism, but it is important to acknowledge the dates when these definitions were conceived. As technology has significantly evolved since the conception of these definitions, it has become necessary to agree upon an up-to-date cyber terrorism definition that incorporates all aspects of modern technology. A more recent study was conducted identifying the key characteristics present in an array of cyber terrorism definitions to establish a new definition based off of these components and the study concluded that [ 45 ]:
“Cyber terrorism is the premeditated attack or threat thereof by non-state actors with the intent to use cyberspace to cause real world consequences in order to influence fear or coerce civilian, government, or non-government targets in pursuit of social or ideological objectives. Real-world consequences include physical, psychological, political, economic, ecological, or otherwise that occur outside of cyber space.”
This definition emphasises the actor, motivation, intent, means, effects and targets of cyber terrorism. Comparing this definition to those by Foltz [ 42 ] and Holt [ 43 ], there are some similarities; however, this definition puts further emphasis on the effect of the cyber terrorist activity which is pertinent to better understand what kind of acts actually encapsulate cyber terrorism. In comparison to the definitions proposed by Denning [ 41 ] and Conway [ 40 ], the Plotnek and Slay [ 45 ] definition does not only focus on cyber terrorist activity which may have physical impacts, but also focuses on other effects such as psychological and economic. This is an important aspect in defining the cyber terrorism term as it acknowledges all impacts which technological platforms are having on terrorism and subsequently on communities, rather than just a singular aspect. Although important points are covered in this explanation of cyber terrorism, it is nonetheless a long-winded definition with many different clauses which may not be simply understood. Furthermore, Plotnek and Slay are Australian based researchers and therefore the applicability of their definition to UK legislation is perhaps dubious due to its lack of compatibility with the current definition of terrorism outlined in The Terrorism Act 2006 [ 28 ]. A more suitable approach to defining cyber terrorism more succinctly, could be to divide it into clearer themes and shorter sentences.
Realistically, cyber terrorism is a very broad topic, and a definition which may endeavour to cover all the characteristics which fall under this term is seemingly challenging. Therefore, the attempt to encapsulate every aspect of cyber terrorism under one singular definition may be counter-productive and may potentially be the very notion preventing a unanimously agreed upon definition. Furthermore, there seems to be a lack of compatibility of the above definitions with the UK legislative definition of terrorism, therefore, a cyber terrorism definition could be designed in the context of UK law.
Theoretical Underpinnings of Cyber Terrorism
Terrorists use cyber space for an array of activities including hate speech, propaganda, recruitment and communication [ 46 ]. This literature review found that Routine Activity Theory [ 15 ] and Space Transition Theory [ 14 ] can be applied to cyber terrorism to support a clearer understanding behind the motivations of cyber terrorist offenders, in turn aiding stakeholders in the prevention, detection, investigation and prosecution of cyber terrorism.
Routine Activity Theory
Routine Activity Theory was developed by Cohen and Felson in 1979 and proposed that in order for there to be an occurrence of victimisation, three confluent factors were necessary: first, a motivated offender; secondly, a suitable target; and thirdly, the absence of a capable guardian. When this theory is applied to cybercrime, the notion of physical space is modified into cyberspace [ 47 , 48 , 49 ]. A study was conducted into the relationship between university students and their computers, and it was found that students who had a greater tendency to disregard their computer-oriented lifestyles and/or neglected security software on their computers, were more likely to be victims of computer crimes [ 47 ]. This study highlights a moderation to the original routine activity theory by which the absence of a guardian may not only be a physical person but could also be the lack of security software on a victim’s technological device.
Although this study was specifically about hacking, the cyber routine activity theory has nonetheless been applied to other forms of cybercrimes [ 50 ] and these findings can be applied to cyber terrorism to better illuminate the three confluent factors in relation to online terrorist activity. For example, if there is no computer security or blocked websites, this could enable the motivated offender to carry out a threat or act of terrorist violence against a suitable target.
Space Transition Theory
Space Transition Theory, created by Jaishankar [ 14 ], was developed to better explain the transitioning of cyber-criminal behaviour between physical space, to cyber space and vice versa. This theory explores seven main tenets: (1) propensity to commit cybercrime as a result of repressed offline criminal tendencies; (2) flexible identity within cyber environments; (3) freedom to transition between physical and cyber spaces; (4) criminal opportunity with little regulation and chance of being caught; (5) offenders’ social connections; (6) reduced threat to offenders; and (7) the blurred lines between norms and values within cyber environments. The principles within Jaishankar’s [ 14 ] theory provide greater comprehension in the paradoxical characteristics between traditional and cybercrimes, and three of these can specifically contribute to better understanding cyber terrorism.
Firstly, due to the anonymous nature of cyberspace, there is a straightforward opportunity for cyber terrorists to disguise their identity, previously referred to as dissociative anonymity [ 50 , 51 ]. This anonymity enables terrorists to hide their identity as a way to bypass existing regulations within cyber environments. Second, due to the anonymous nature of cyber environments, this not only impacts how actions can be regulated, but also allows offenders to continue their criminal behaviour with little to no consequences. This is further supported by cognitive inhibition effect in which, due to lack of deterrence, dissociation between the action and the end result encourages the continual terrorist behaviour [ 50 ]. Third, the ability to interchange between physical space and cyber space, alludes to the notion that terrorist activity may potentially manifest in cyber space where there are limited constraints to disseminate propaganda and recruit, prior to moving into physical space where offline impacts may be seen [ 52 ]. This available interchangeability is financially advantageous to terrorist groups as they can achieve their aims and objectives to further their terrorist ideology with reduced monetary costs.
Lastly, if terrorist behaviour is repressed in physical environments, this may encourage terrorists to modify their approaches into cyberspace where activities can be hidden from regulatory bodies and stakeholders involved in combatting terrorism [ 53 ]. Although this was an already advantageous aspect for terrorists, this has become even more significant due to the global COVID pandemic and lockdown restrictions [ 2 ]. Due to a greater increase in terrorist use of cyber space and its dynamic spatial -temporal characteristic, there is a lower risk of being caught due to the vastness of cyber environments [ 52 ]. Overall, the tenets highlighted in Space Transition Theory [ 14 ] simplify the advantageous elements which are enabling terrorist activity to continue mostly uninterrupted.
Categorisation of Cyber Terrorist Activity
According to the Crown Prosecution Service [ 54 ], in order for an action to qualify as terrorism, there needs to be evidence of terrorist motivations. Wilkinson identifies four types of terrorist groups: ethno-nationalist groups; ideological groups; religio-political groups; and single-issue groups [ 55 ]. This identification can be used to inform the types of motivations which can influence terrorist offences. The current legislations for countering the threat of terrorism in the UK are The Terrorism Act 2000 [ 56 ]; The Terrorism Act 2006 [ 28 ]; The Counter-Terrorism Act 2008 [ 29 ]; and The Counter-Terrorism and Border Security Act 2019 [ 57 ].
According to the Crown Prosecution Service [ 54 ], some examples of substantive terrorist offences include preparing terrorist attacks; collecting terrorist information; disseminating terrorist publications with intent of encouraging terrorism; aiding in covering up terrorist activity online; supporting a proscribed organisation; attending a place for terrorist training; and financially aiding terrorist activity. In the context of the above offences, one could question the effectiveness of current UK legislation in preventing, detecting, investigating and prosecuting cyber terrorist activity. For example, the offence of ‘attending a place for terrorist training’ under The Terrorism Act 2006 [ 28 ] may be challenging to apply to terrorist virtual training as there is no geographic “place” due to the boundaryless characteristic of a cyber environment. Both pinpointing the virtual location of training and determining the IP addresses of each individual attending the training session, could make it difficult for stakeholders to detect and prosecute [ 58 , 59 ]. However, as explored in Space Transition Theory [ 14 ], this is an advantageous notion for cyber terrorism due to the anonymity factor. In addition, it is important to note that terrorist activities, such as training and recruitment, have become more reliant on online platforms, especially throughout the COVID pandemic due to restrictions.
Recently, The Department for Digital, Cultural, Media and Sport [ 60 ], released a Draft Online Safety Bill which aims to set out principles for service providers in regulating their services and making them safe for users. It directly highlights principles which should be used to combat online terrorist activity. The draft bill has been under scrutiny for the risk it poses to freedom of speech, privacy and the way in which it will regulate risks to the public [ 61 , 62 ], however, it is nonetheless a step in the right direction to continue combatting the threat posed by terrorism in the UK. Although UK laws can be a beneficial tool in understanding what offences can be prosecuted, it is limited in clearly categorising terrorist offences and their processes in a framework approach.
Smith et al. [ 16 ] conducted a study into the spatial and temporal patterns of terrorist group activity, and although classifying terrorist activity was not a main aim, this was nonetheless achieved and can be used to better understand terrorist processes. This study breaks down terrorist activity into four main categories: (1) recruitment; (2) preliminary organisation and planning; (3) preparatory conduct; and (4) terrorist act. This framework can be useful in gaining a clearer understanding of what general types of terrorist activity occur and, furthermore, how one act can lead to another. This could be a beneficial tool for stakeholders involved in the prevention, detection, investigation, and prosecution of traditional and cyber terrorism as there would be a clearer understanding of the entailed processes.
McGuire and Dowling developed a dual-binary framework approach which classifies cybercrimes based off their dependence to cyber capabilities [ 7 ]. Cyber-enabled crimes, such as disseminating terrorist propaganda or theft, are traditional crimes which can increase in scale due to technology. On the other hand, cyber-dependent crimes, such as denial of service attacks or hacking, are acts which can only be committed through technological means. This dual binary approach is beneficial as it encourages a clear classification which can be easily understood by direct stakeholders such as law enforcement and prosecution services. However, this approach is limited as it does not apply this model to cyber terrorism [ 7 ]. Considering this approach has been adopted by the Crown Prosecution Service [ 63 ] to better explain the prosecution of cybercrimes, this could be indicative of a lack of understanding towards cyber terrorism from the criminal justice system in the UK. This raises a critical question of whether the criminal justice system is suitably equipped with knowledge in securing the UK against the threat posed by cyber terrorism. Considering the rise of online based terrorism throughout the pandemic [ 2 ], a dual binary approach may not be sufficient, but rather a ternary approach which incorporates traditional, cyber enabled and cyber dependent terrorism, could instead be considered to enhance the understanding of varying terrorist activities and their correlations.
Methodology
Research design.
In order to determine what perceptions were held by the public towards cyber terrorism, a mixed methods approach was chosen over a single method approach as mixed methods enable the researcher to find comparisons and contradictions within the quantitative and qualitative data which overall strengthens the discussion to better understand something, which as highlighted in the literature review, is not yet well understood [ 64 , 65 ]. By utilising a mixed methods approach, quantitative and qualitative data were collected and analysed simultaneously using positivist (quantitative) and post-positivist (qualitative) paradigms to observe and measure the responses [ 66 , 67 ].
Research Materials
The research material used was a mixed methods questionnaire which consisted of both quantitative and qualitative questions in the form of an online survey which was open to the public. Some benefits of utilising surveys to collect data are that participants are able to answer questions in their own time, and furthermore can answer truthfully without a fear of being judged as they are in a familiar environment [ 68 , 69 ]. Also, online surveys have been found to be beneficial as they are simple to implement and inexpensive compared to traditional questionnaire characteristics such as printing, postage, location and time [ 70 , 71 ].
The online survey was created through Jisc Online Surveys [ 72 ] which was used to create and host the survey for participants to complete the questions using a link. It was important to the research that the survey be made simple for ease of participants to navigate through it themselves and, therefore, where needed, explanations were put in place to aid participants throughout the survey. The survey used a range of demographic questions, dichotomous questions, Likert scale questions, and open questions. Every question gave respondents the opportunity to elaborate on their responses with free text boxes which fed in to the qualitative data.
Participants were specifically asked questions regarding their beliefs towards the way in which cyberspace is enabling terrorism. Participants were asked to share what threat level they believe the UK currently faces from terrorism and were also asked their opinion on the importance of stakeholder’s understanding to improve the UK’s approach to counter cyber terrorism. The questions under this section made up an important part of this research as they directly correlated to the aims and objectives. This enabled the analysis against the demographic groups to be done to ascertain what the sample populations’ perceptions were towards cyber terrorism.
Research Sampling and Procedure
The sampling techniques which were dedicated to this research were convenience sampling and snowball sampling. The convenience sampling method does not rely on probability and takes a sample from a group of people who meet a certain criterion [ 73 , 74 ], where for this research the criteria were easy to reach; availability; and over the age of 18. A limitation of convenience sampling is that it encourages biased results due to the potential proximity of the researcher and the respondents and therefore, opinions in the data may not have the ability to be fairly applied to the general population [ 74 , 75 ]. In light of this limitation, the snowball sampling method was then also utilised by encouraging respondents to share the survey once they had completed it to at least one other person is this would increase the sample size and generalisability of the data [ 76 ]. This would ensure that the sample was more diverse.
The online survey was distributed through a web link which was shared via the researcher’s social media accounts with a short explanation of the research so that participants could make an informed decision of whether they wished to participate or not. The social media sites used included LinkedIn; Facebook; Twitter; and Instagram. The survey was open to the public for 76 days between March and May of 2021, and every Thursday of the week, the survey was reshared on the social media sites to generate a larger sample population. Overall, this achieved a sample size of 83 respondents. As respondents answered questions on topics which they may not have put much thought into prior to completing the survey, this may have hindered their ability to make decent thought-out conclusions in their answers [ 77 , 78 ], potentially making a catalyst of unreliable data.
Data Analysis Techniques
The quantitative data collected from the online survey were analysed using IBM SPSS. This software was chosen for the quantitative analysis as it has been used for research in social sciences due to the straightforward approach it offers for a range of analyses and the researcher does not need any mathematical expertise to use this software [ 79 , 80 ]. Additionally, SPSS allowed for comparative investigation between the data sets to be undertaken to analyse whether there were any strong attitudinal relationships [ 81 ]. More specifically, t tests and ANOVA (Analysis of Variance) tests were carried out using SPSS to determine whether there were any strong relationships between demographics and the topical questions.
The qualitative data collected from the online survey were thematically analysed utilising Microsoft Word. This software was chosen for the qualitative analysis as it enabled the researcher to see all the qualitative data together and go through the process of thematic analysis using the highlight feature to colour codes and themes, and further use the control find feature to search for particular words or phrases [ 82 ]. In order to ensure that important data were not missed, the researcher initially became comfortable with the data taking simple notes on opinions which become apparent prior to beginning the coding and thematic categorising stage [ 82 ]. Analysis and interpretation of the qualitative results were conducted in tandem to ensure that any final conclusions were reached following in-depth analysis [ 83 , 84 ].
Ethical Considerations
The British Society of Criminology’s Ethics Statement ensures that within any primary research, safety should be practiced, and ethics should be considered [ 85 ]. Prior to the survey being shared, a number of ethical considerations had to be considered to ensure that the researcher and participants were not placed at risk, and if so that the mitigation strategies were made available. The main ethical considerations which related directly to this research’s research were consent, confidentiality, anonymity, autonomy and debriefing. Steps were taken to ensure that respondents were aware of their rights as a participant when they agreed to take part in the research.
Online Surveys is fully compliant with the Data Protection Act 2018 [ 86 ] and does not record IP addresses to ensure that complete anonymity is maintained. Furthermore, to ensure the data were kept safe and private, only the researcher had access to the raw data which were stored on a password protected account with Online Surveys on a password protected laptop belonging to the researcher. In accordance with the School of Criminology and Criminal Justice Ethics Committee guidelines, the data were stored in the researchers N drive, and after 10 years it will be destroyed. Before the survey could be disseminated, an ethical review was completed by the SCCJ Ethics Committee of the proposed research, and the ethics were approved.
In order to ensure that participants had informed consent and participation was voluntary, an information sheet was included on the first page of the survey. Participants were informed of their rights throughout the survey process and the data collection process and participants were only able to progress to the questions for the survey once they had confirmed they were over the age of 18 and that they consented to everything in the information sheet. A section on debriefing was placed at the end of the survey upon completion which thanked respondents for their participation in the research. Additionally, as the topic of the research was of sensitive nature and could have affected individuals, three helplines and support websites were provided for participants. Finally, the details of the researcher and supervisor were provided in case any respondents had complaints and/or queries regarding the survey.
Results and Discussion
Overall findings from the literature review highlighted that there is a lack of a widely accepted definition and framework for cyber terrorism in the UK. Findings further discovered that theory can be used to better understand cyber terrorist behaviour, thus aiding in a better understanding of what cyber terrorism is. The literature review, paired with this research’s primary data collection, aimed to establish a current definition of cyber terrorism and framework approach which can be utilised by direct stakeholders involved in the prevention, detection, investigation, and prosecution of cyber terrorism within the UK. The research hypotheses were as follows:
This research hypothesised that misconceptions may be held amongst the general public, especially in the qualitative data, and that this could be a representation of misconceptions held amongst direct stakeholders as they are disseminating this information to the general public
This research also hypothesised that, based on the demographic characteristics of the sample population, significant effects would be found between the gender demographic and the topical questions where females may have been more concerned with the psychological effects of terrorism and males more so with the physical effects. This hypothesis is influenced by research that has found females to hold greater empathic concerns towards individuals’ situations than males [ 87 , 88 ].
In addition, it was hypothesised that significant effects would be found in respondents’ occupations, assuming that occupations from within technology and/or law enforcement categories may hold a more experiential understanding of cyber terrorism within the survey.
Quantitative findings are presented through the use of tables, and qualitative findings are explored through themes supported by quotations from the sample population. Subsequently, the results are discussed, exploring interpretations and implications of the findings in light of the learnt literature. This chapter ultimately develops a definition and framework for cyber terrorism informed by available literature presented in the literature review, and the outcomes of the primary data collection.
Demographics of Sample Population
The primary data were collected from 83 respondents overall. Of the sample population, 45% were male respondents and 55% were female respondents. In context of the age demographic, the highest rate of respondents being amongst the ‘18–24’ group and the lowest number of respondents being from the ‘65 or above’ group. As the survey was distributed amongst the researcher’s social media accounts, this turnout was expected due to the researcher’s connections. The main limitation is the lack of results retrieved from the 65 and above age group, although had this age group been more targeted in the distribution of the survey this would have rejected anonymity and confidentiality of the participants.
The survey offered a total of 25 occupation categories which participants could choose from. Four of these occupations were not selected by any individuals and in addition, some occupations had two or less respondents which implicated the data analysis. Therefore, once all data had been collected, the 21 occupation categories were funnelled down in to nine categories and the data for occupations were recoded in SPSS. The new categories can be seen below in Table 1 . The total sample population for occupation is 81 in contrast to the overall population of 83 as two participants did not disclose their occupation.
Quantitative Results
The quantitative results in this primary data collection aimed to investigate whether demographic characteristics from the sample population had any significant effects on the topical questions from the survey. Further to the hypotheses of this primary data collection, the quantitative results further aimed to establish whether there were any trends or patterns which could be used to better understand what perceptions are held by the public and whether there is a trend leaning towards unanimity or not. A range of t tests and ANOVA tests were used to conduct an overall of 66 basic statistical tests using SPSS to initially investigate significant findings in the data. Overall, 97% of the data were found to have no significant effects, indicating only 2 out of 66 tests had a significant effect.
Gender Findings and Interpretations
Independent t tests were conducted to investigate whether or not gender played a significant role in the way the topical questions were answered. The overall results for the t test can be found in Table 2 where data can be tracked as significant or insignificant in the p value column. As can be seen, the results which found gender to have a significant effect were Q9d and Q13. Although significant results are important to note and interpret, it should be acknowledged that these significant findings merely highlight notions which appear worthy of further investigation and replication [ 89 , 90 ].
The recruitment and mobilisation question asked participants to rank what they felt were ways in which terrorism was being enabled by cyber capabilities from a list of options. Participants were able to choose 3 options with 1 being the most important and 3 being not as important. As there were more than 3 options for participants to choose from in this question, it cannot be assumed what 3 meant to people – it could have meant ‘least important’ to some or ‘not as important’ to others.
Results showed that male participants ( M = 1.57, SD = 0.746) ranked recruitment and mobilisation higher than females ( M = 2.04, SD = 0.676) and an independent t-test found this pattern to be significant, t (44) = − 2.23, p < 0.05. First, these data suggest that males are more likely to include recruitment and mobilisation as an enabled form of cyber terrorism than females. Second, these data also allude to the notion that males are potentially more concerned with the concept of recruiting and mobilising new terrorists. As no effect size was calculated due to an outdated version of SPSS, these data cannot be generalised to a larger population.
Some assumptions can be made based on the implications of these findings regarding gender perception on recruitment and mobilisation within terrorist activity. Due to terrorist groups use of online capabilities, the ability to recruit and mobilise individuals has increased through a greater ease in disseminating information to followers [ 14 , 91 ]. This has especially increased during the pandemic where more individuals have felt anxious, disempowered and alone and have found a sense of community and solace in like-minded groups where inciting violence either in a virtual or physical environment, has been more so attractive than possibly before the pandemic [ 92 ].
As discussed in this research’s literature review, recruitment is one of the first steps in the process of terrorist group activity [ 16 ]. This information, coupled with the male gender effect on ‘recruitment and mobilisation’, could indicate that males are more concerned with terrorist group actions which have a long-term effect such as recruiting individuals, who may play a direct or indirect role in threatening or causing harm to individuals virtually or physically, further down the process of terrorist group activity. This interpretation could be broadened onto a wider scale looking at stakeholders within cyber terrorism where male police officers make up 69% of the police force [ 93 ]. For example, if male police officers are more concerned with the long-term effects of cyber terrorism and are more likely to acknowledge recruitment as a first step in terrorist group activity, there may be a greater interest to detect and combat the terrorist activity being enabled by cyber space before the threat of harm to a community or nation increases. Overall, this could indicate there being a greater ambition to deter terrorism from happening through observing recruitment activity online. In light of these findings, there is a potential for hypothesis 2 to be met on the condition that the study be replicated to calculate the generalisability of these findings.
The final question in the survey, asked participants how strongly they agreed that stakeholders’ understanding of the term cyber terrorism is important in detecting and preventing terrorism in the UK. Zero participants selected the answers ‘disagree’ and ‘strongly disagree’, and only eight participants selected ‘neutral’ which suggests that there is generally overall agreement amongst the sample population that stakeholder understanding is important. However, results showed that female participants ( M = 1.40, SD = 0.580) were more likely to strongly agree with the stakeholder statement than males ( M = 1.89, SD = 0.658), and an independent t-test confirmed a pattern of significance, t (72.508) = 3.553, p ≤ 0.05. These data suggest that females are more likely to acknowledge the influence that stakeholders’ understanding of cyber terrorism can have on the detection and prevention of terrorism. It also highlights that male participants are potentially more inclined to take a more ‘neutral’ standpoint towards the statement. These data challenge one to consider the impact which stakeholders lacking in gender diversity may have on the understanding, and subsequently the detection and prevention of cyber terrorism.
In light of this finding, it is important to consider gender diversity within agencies and stakeholders who are associated in tackling cyber terrorism, including policy makers and law enforcement. Research regarding gender diversity has found that more diverse work environments can result in broader perspectives within decision-making and greater effectiveness in work delivery [ 94 , 95 , 96 ]. In addition, one study showed an inclination from female leadership roles in focusing on preventing and resolving matters [ 97 ]. As highlighted, the police work force is 69% males [ 93 ] and potentially making this environment more gender diverse may mean a greater emphasis for broader perspectives in understanding cyber terrorism to prevent, detect, and investigate terrorism effectively. Furthermore, recent statistics indicated that 34% of the MPs in the House of Commons are female [ 98 ]. Although this statistic has been referred to as record high, this nonetheless indicates a disparity in gender diversity within parliament which could be contributing to the difficulties in developing a unanimous definition of cyber terrorism to enable greater prevention strategies against terrorism. Overall, this finding alludes to the necessity for more gender diversity within stakeholders directly involved in detecting and preventing terrorist activity in the UK.
Age and Occupation Findings and Interpretations
ANOVA tests were carried out to establish whether or not age and occupation played a significant role in determining respondent answers. The overall results for age can be found in Table 3 , and the overall results for occupation can be found in Table 4 . Where the M or SD display ‘n/a’, this is indicative of results where respondents from a specific category did not respond to a specific question. This is most probably due to the rank questions only allowing three options to be chosen by each participant to rank in questions 9 and 11. In both these tables, the F value column displays that there were no significant findings with age or occupation. The non-significant results were analysed and the implications of these highlighted.
Discussion on Non-significant Results
The reporting of non-significant results has been much debated amongst academics, with various and differing approaches being encouraged [ 99 , 100 ]. However, it has been strongly posited that non-significant results should not be assumed to represent homogeneity amongst the sample population [ 101 , 102 ]. This is due to the fact that a non-significant result merely highlights what population parameter is unlikely, rather than what it is likely to be [ 103 ].
It can be assumed that the non-significant findings from this primary research were unable to present evidence for all the hypotheses. In order to determine whether a type I or type II error has occurred, replication of the study and re-analysis of the data would need to be carried out to better understand the non-significant results [ 103 ].
In the case of a type II error, it is important to discuss potential influential factors apart from gender, age, and occupation which could have influenced the sample population’s beliefs towards the survey questions, thus resulting in non-significant results. Most pertinent to this primary research is the impact which media outlets have potentially had in shaping perceptions surrounding cyber terrorism. In a contemporary society, the news has become more easily accessible through news media websites and social media platforms, which has increased the way in which public opinion is shaped due to the news’s gatekeeping process [ 32 , 104 , 105 ].
Although news media outlets are beneficial in making the public aware of current events, the implications could potentially be detrimental for stakeholders involved in detecting and preventing cyber terrorism. If public opinion has been shaped to believe that cyber terrorism mainly involves cyber dependent acts such as denial of service attacks, then this may be what the public look out for and subsequently report to the police (recent news examples include [ 106 , 107 , 108 ]). This leaves a gap in which cyber enabled acts of terrorism, such as online terrorist propaganda, may not be as reported by the public due to misconceptions. In turn, this potentially impacts the ability for police to prevent terrorist attacks due to online terrorist activity not being as reported. If a unanimous definition of cyber terrorism could be agreed upon, policy-makers and police could share this through news media outlets to enable the public to have a greater understanding of cyber terrorism, in turn encouraging individuals to identify and report both cyber enabled and cyber-dependent terrorism.
Qualitative Results
Analysis of the qualitative data from the online survey revealed important themes which were evident amongst the majority of the sample population. The qualitative analysis aimed to establish a more in depth understanding of what the public’s perceptions are towards cyber terrorism. Analysis highlighted that the majority of participants were generally in agreement, with only a small number of participants expressing more opposing views.
Among the 83 participants and across all the topical questions there were a total of 198 qualitative responses. Qualitative responses appeared to decline as the survey progressed, with the highest response rate to a single question being 75 responses and the lowest at 3 responses. This has the potential to lessen the validity and generalisability of all the qualitative responses; however, coupled with the quantitative data and the findings from the literature review, it may contribute in the justification for developing a cyber terrorism definition and framework. Figure 1 displays codes and themes from the qualitative analysis. In the discussion of the qualitative data, responses will be displayed as ‘PX’ where ‘P’ indicates ‘Participant’ and ‘X’ an identification number.
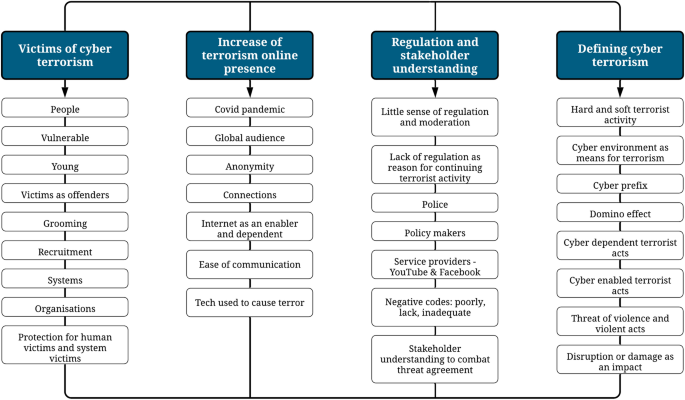
Thematic analysis codes and themes from qualitative data. This figure displays the themes and codes which came to light throughout the qualitative analysis of the primary data collected. These themes and codes are reflective of the views and opinions held by the sample population, which are supported further with quotations in the analysis below
Victims of Cyber Terrorism
The first theme which emerged from the qualitative analysis of this research’s primary data collection was the distinction between the two victims of cyber terrorism. On the one hand, the ‘people’ victims of cyber terrorism were highlighted with concerns about “vulnerable” and “young” people raised by P1, P2 and P3, and “uninformed users” raised by P4 and P5. These groups were highlighted as victims of being groomed and recruited in to the terrorist group activity process, but also be victims of virtual and physical verbal attacks from cyber terrorists and extremists. On the other hand, there were also concerns highlighted towards the ‘system’ victims of cyber terrorism where participants included examples such as “data and resources” (P6), “power grids” (P7), and “interfaces” (P8 & P9). One individual (P10) referred to these more physical impacts of cyber terrorism as being “more traditionally what the term [terrorism] is associated with”.
The theme of cyber terrorist victims can be one which encourages confusion as there are different types of victims which could be encapsulated under the cyber terrorism umbrella. McGuire and Dowling’s [ 7 ] cyber enabled and cyber-dependent classification can be used to categorise victims of cyber terrorism which can further aid in developing a more concise classification. ‘Human victims’ of cyber terrorism can be victims of both cyber enabled and cyber dependent actions, which has been broken down further into ‘human victims of cyber dependent terrorism’ (for example, data theft) and ‘human victims of cyber-enabled terrorism’ (for example, verbal abuse on a social media platform). Systems who are victims of cyber terrorism can only be victims to cyber-dependent actions and, therefore, have been classed just as ‘system victims’ (for example, Ransomware attacks on national infrastructure for political gain). These classifications contribute to the development of a framework in this research.
However, it became apparent from the qualitative analysis that there is a blurred line between victims and offenders of terrorist activity with P11, P12 and P13 referring to there being an “ease for terrorists to recruit people” and “alter people’s way of thinking”. These qualitative findings are supported by the findings from the literature review highlighting the complexity in sometimes distinguishing between victim and perpetrator as a result of misconceptions from stakeholders affecting news media outlets [ 30 ]. Interestingly, although the individuals being recruited and groomed are in fact victims, in some cases they too become the offenders for the very things they were once victims of. This paradoxical concept can be better understood through the story of Shamima Begum who left the UK at the age of 15 after being recruited to join ISIS. Since the age of 19, she has been trying to return to the UK as she claims she did not expect to go through everything she did, despite her engaging in known terrorist activity [ 109 , 110 ]. The supreme court recently ruled that they could not allow Begum to return to the UK as this would create a significant national security risk [ 111 ].
As highlighted in Jaishankar’s Space Transition Theory [ 14 ], the anonymous nature of cyber environments allows individuals to hide their true identities which could enable individuals to transition from victim to perpetrator with more ease, either intentionally or inadvertently, further accentuated by cognitive inhibition effect and dissociative anonymity [ 50 , 51 ]. Understanding victims of cyber enabled and cyber dependent terrorist activity could also provide a clearer interpretation of motivated terrorist offenders. Overall, this thematic finding highlights disparities amongst respondents regarding cyber terrorist victims which could be due to the absence of an agreed upon definition and framework detailing what qualifies as a cyber terrorist act. Having a unanimous definition would, therefore, make a clearer distinction between victims and offenders of cyber terrorism.
Increase of Terrorist Online Presence
Another theme which emerged from the qualitative analysis was the way in which respondents emphasised how online capabilities have aided in expanding terrorist activity. P14 alluded to the notion that online platforms “help build a sense of community between members, assist in recruitment, and launch attacks”. Additionally, P15 highlighted the ability which terrorists have “to reach a global audience and form groups which reinforce each other”. There were concerns raised specifically regarding the impact which the COVID pandemic has had on terrorist activity. Although some participants highlighted the risk of terrorism as “lower than before due to COVID” (P16), others seemed to emphasise the advantageous aspects of COVID for terrorist activity as there being “more time to plan” (P17), and one participant nodded at cyber terrorism being “underreported” with the “true scale now being unknown but severe” (P18) due to its greater shift online.
It became evident throughout the qualitative data, that much of the sample population appeared to be mostly in agreement that the threat of terrorism posed through online capabilities is apparent. This is supported by the quantitative findings in Q10 and Q12 where ≥ 80% participants were in agreement that the cyber enabled and cyber dependent acts listed were classed as cyber terrorism. These results also support the findings from the literature review which found that terrorist activity is a process by which the smaller and perhaps less impactful activities are seen to have a domino effect on larger terrorist attacks [ 16 ]. For example, recruitment was identified by 12 participants throughout the qualitative responses which is a positive finding as it indicates that individuals are aware of its impact in the process of terrorist activity. In addition, this links back to the significant effect found on gender where males were more likely to rank recruitment and mobilisation higher than females in the quantitative results. Controversially to these findings, P19 stated that “terrorism, the act, is an offensive action, just recruitment and fundraising themselves are not terrorist acts” which was an opinion also raised by P20, P21 and P22. These qualitative findings highlight the presence of common misconceptions held by some individuals regarding cyber terrorism, which is supported by the findings from the literature review. The UK law in fact deems ‘Encouragement of Terrorism’ under The Terrorism Act 2006 [ 28 ] and ‘Finance and Money Laundering in relation to terrorism acts’ under The Terrorism Act 2000 [ 56 ], as common offences. Although it is positive that respondents appeared to mostly agree on cyber enabled and cyber dependent terrorist offences, the minority of people who did not agree could be only a small representation of the wider public.
In light of the aforementioned theme, the misunderstanding around terrorism offences could also be an attributing factor in causing the general public’s confusion around who is a victim or a perpetrator of cyber terrorism [ 18 , 30 ]. The public has a responsibility to report observed criminal activity, and if there is not enough awareness of cyber enabled and cyber dependent terrorism offences, this could have detrimental implications on the investigation and prosecution of cyber terrorist activity in the UK in line with the Action Counters Terrorism (ACT) campaign [ 112 ]. Understanding these detrimental effects of misconceptions amongst the general public, could suggest an urgent need for cyber terrorism to be unanimously defined incorporating both cyber enabled and cyber dependent aspects. Overall, these findings allude to the potential misconceptions held amongst the public regarding cyber terrorist activity; however, these cannot be generalised without replicating the study with the aim of gathering data from a larger sample population.
Regulation and Stakeholder Understanding
The qualitative analysis further highlighted a theme regarding the regulation of the internet and stakeholders’ involvement in this. The theme of regulation was not introduced to participants within the survey questions, unlike the previous themes, which perhaps highlights the importance of regulatory processes to the survey respondents, in the context of cyber terrorism. P23, in the context of online platforms, stated that these are “too free a space with little to no sense of regulation”, which was a popular opinion with other respondents using words such as moderation, monitor, and regulation on 19 occasions in the qualitative responses. The issue with the lack of regulation on online platforms was further identified by P24 stating “online platforms provide unchecked means of sharing material” and P25 further suggesting the notion of “rumoured safety measures in place”. Interestingly, positive connotations were not associated with regulation in the qualitative responses potentially indicating dissatisfaction regarding the current approaches to regulating online terrorist activity. This dissatisfaction could be a result of ambiguous guidelines on social media and online platform such as those referred to in qualitative responses—“Facebook” (P26 & P27) and “YouTube” (P28, P29, & P30).
YouTube guidelines state that terrorist organisations are not permitted to utilise their services to conduct a range of terrorist activity, for example, “praising or justifying violent acts carried out by a terrorist organisation” [ 113 ]. Facebook states that any entities, such as terrorist organisations, who engage in “serious offline harms” will be condemned alongside any content which praises, supports or represents terrorist organisations [ 114 ]. Problematically, these online platforms do not define the term ‘terrorism’. This means that when it comes to regulating and removing certain online content, the service providers can decide what is deemed terrorist or not according to their own perceptions. Looking at the recent conflict between Israel and Palestine, Hamas, a proscribed terrorist organisation [ 115 ], fired rockets into Israel from the Gaza strip due to political and religious differences [ 116 , 117 ]. At the time of these events, there was justification and condoning across online platforms for the violent actions directed at Israel from Hamas despite Hamas’ recognition as a terrorist organisation. Furthermore, media platforms such as YouTube and Facebook condemned Israel’s actions, and justification for their retaliation was taken down as ‘misinformation’. A more recent example is the Plymouth shooting. Jake Davison, who practiced hate speech against women, incited violence and spoke about his ‘incel’ (involuntary celibate) alignment on YouTube, killed five innocent individuals [ 118 , 119 ]. Davison had just short of 100 subscribers on his YouTube channel, and these were 100 missed opportunities to detect this terrorist activity prior to his online terrorist behaviour becoming a physical attack.
These unclear guidelines which are used to regulate online terrorist activity are evidently biased and counterproductive, which may be the reason for the dissatisfaction towards regulating cyber terrorism highlighted from some of the survey respondents. Furthermore, with repressed behaviour in physical environments due to the COVID pandemic [ 2 , 14 , 53 ], this may encourage online terrorist activity alongside the lack of collaborative regulation. The implications of this are that direct stakeholders involved in combatting online terrorist activity, including online platform providers and law enforcement, are perhaps not able to do so effectively due to the absence of a unanimously agreed upon definition. Perhaps a collaborative approach could ensure clearer regulatory guidelines and may further enable the future instalment of the draft Online Safety Bill [ 60 ] to be more effective.
Q13 from the survey found that 90% of respondents overall agreed that a definition could enable stakeholders to better understand cyber terrorism, in turn aiding in the detection and prevention of terrorist activity. Although this question only received 10 qualitative responses, ‘stakeholders’ were referred to in qualitative responses from other questions, with direct mentions being made of the police, policy makers, and online platforms. P31 stated that “If you don’t consider something a crime or a precursor to a crime, you won’t be looking for it” indicating that unless something is defined as a crime, it will not be identified and reported as such. Furthermore, P32 claimed that there is a need for stakeholders to “understand the objectives of the terrorist and the means used to execute their plans”. As discussed in the literature review, pre-curser crimes could include recruitment, training, or disseminating propaganda which are initial phases in the terrorist activity process [ 16 ]. Therefore, P31 and P32 could be implying that these pre-cursor terms are not clearly defined under cyber terrorism which perhaps indicates an absence of these activities not being policed effectively due to a lack of understanding of terrorist motivations. However, much of the regulation of the internet is controlled by the service providers, and therefore, a more collaborative approach from various stakeholders would perhaps be the most effective way to combat online terrorist activity. This collaborative approach would also ensure that public users of online platforms are safer and more aware of what they can report as terrorist activity, in turn countering future threats posed by terrorism.
Defining Cyber Terrorism
The survey asked participants to expand on how they would define cyber terrorism, and this question received the highest rate of responses from 75 participants. Some respondents classified cyber terrorism into binary models such as “hard and soft” (P33) and “enabled and dependent” (P34). Interestingly, of the 75 responses received for this question, only 40% incorporated terrorism that is both enabled by and dependent on cyber capabilities in their proposed definitions. The remaining 60% of respondents focussed on either cyber enabled or cyber dependent activity. This highlights the confusion that exists within the general public and could be reflective of the general misconceptions which exist, emphasising the need for a unanimous definition of cyber terrorism.
Respondents mostly used the ‘cyber’ prefix within their definitions, with fewer using terms such as ‘online’, ‘technology’, ‘internet’ and ‘virtual’. For example, P35 defined cyber terrorism as “terrorism that uses the cyber domain as a space to carry out its actions”, and P36 stated “cyber terrorism is when terrorist organisations enter cyber space and instrumentalise the internet to carry out violence”. However, P37 highlighted it as the “use of electronic interventions or resources to disrupt online systems or operations”. Despite Gordon and Ford’s [ 44 ] belief that the cyber prefix is not an effective term, the qualitative results find that this is a term which the respondents appear to be familiar with, which could be reflective of the general public’s views. Therefore, attempting to change the cyber prefix to something else, such as Computer Network Operations or Information Warfare [ 38 ], could potentially cause further confusion. These findings, coupled with the literature review, imply that a cyber terrorism definition could encapsulate a classification between enabled and dependent activity. The implications of a clearer definition, as discussed above in the aforementioned themes, would enable stakeholders including law enforcement, online platform providers, policy makers, and prosecution services to work collaboratively towards a unified goal. This may further enhance the public’s understanding of what they could be identifying and reporting in line with the ACT campaign [ 112 ].
Establishing a New Approach Towards Cyber Terrorism
In the context of the findings from the literature review and the collected primary data, this research posits a new definition and framework of cyber terrorism which could be utilised by stakeholders directly involved in preventing, detecting, investigating and prosecuting cyber terrorism.
Cyber Terrorism Definition
The development of a cyber terrorism definition aimed to gather the strengths of previously discussed definitions and incorporate them in a clear and more concise manner that can be easily understood. The most important factor which was considered for a cyber terrorism definition to be used by UK stakeholders, was the need for it to be compatible with the definition of Terrorism outlined in The Terrorism Act 2000 [ 56 ], The Terrorism Act 2006 [ 28 ], The Counter-Terrorism Act 2008 [ 29 ], and The Counter-Terrorism and Border Security Act 2019 [ 57 ]. In addition, themes from the Foltz [ 42 ], Holt [ 43 ], and Plotnek and Slay [ 45 ] definitions have been considered and prioritised for incorporation in this research’s proposed definition. Referring back to the literature review, terrorism as a concept evolves with the times, and henceforth, a cyber terrorism definition should be versatile to ensure its applicability to unpredictable future developments within terrorist techniques. Having identified the most critical components to develop a definition that is both concise and compatible with the legal definition of terrorism in the UK, (binary ‘means’ classification, motive, intent, and target) the following definition is proposed:
“Cyber terrorism encapsulates cyber enabled activity which intends to advance political, social, or religious ideologies against the public, and cyber dependent activity which further intends to threaten or facilitate damage against the public, properties, and/or systems. Cyber terrorism has the potential to coincide with traditional terrorism”.
As identified throughout this research, a clear definition of cyber terrorism could enable a more collaborative approach amongst stakeholders in preventing, detecting, investigating, and prosecuting cyber terrorism. Although this definition is not as lengthy and detailed as some of the other definitions analysed [ 41 , 43 , 45 ], the findings highlighted that a simpler definition with fewer clauses provides greater clarity, encouraging a more unanimous approach across various stakeholders. Overall, by having a clear definition outlined for those involved in detecting and preventing cyber terrorism, this could improve the way in which stakeholders combat the overall threat of terrorism, subsequently enabling the media to relay more accurate information to the public regarding cyber terrorist activity. This could in turn make the public more confident in identifying and reporting terrorist and cyber terrorist activity in line with ACT [ 112 ].
Cyber Terrorism Framework
The development of a framework for cyber terrorism aimed to clearly highlight what kind of terrorist activity occurs in cyber space, the process, and the links between traditional and cyber terrorism. Using the Smith et al. [ 16 ] categorisation of traditional terrorist activity, this research proposes a similar approach by incorporating McGuire and Dowling’s [ 7 ] cyber enabled and cyber dependent dual binary model. As this model has already been adopted by the Crown Prosecution Service to classify and prosecute cybercrimes, it is perhaps important that the same binary model be used to classify cyber terrorism for collaborative work amongst law enforcement and prosecuting services.
Based on this research’s proposed definition, a ternary approach is suggested as this highlights the inextricable links between traditional, cyber enabled and cyber dependent terrorism. A proposed ternary model can be seen in the Terrorist Activity Framework in Fig. 2 .
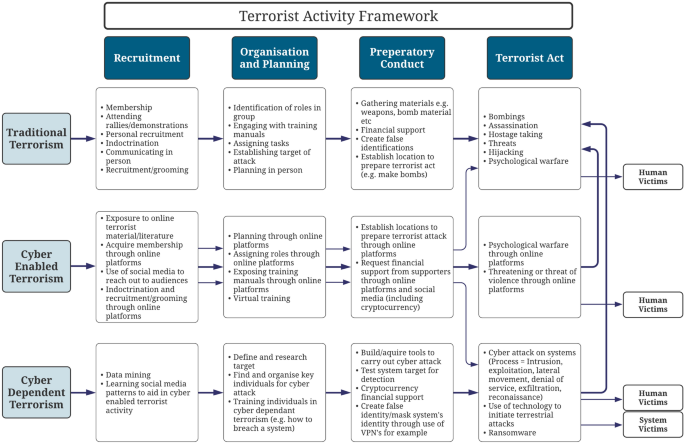
Terrorist activity framework entailing cyber terrorism—developed from [ 7 , 16 ]. This figure displays a framework which highlights cyber terrorist activity’s life cycle. It highlights cyber enabled terrorist activity, cyber-dependent terrorist activity and traditional terrorist activity with arrows to show the links between these three components. This framework is put forward from this paper’s findings to better aid stakeholders in more collaboratively tackling terrorism
This cyber terrorism framework highlights the similarities across the three identified types of terrorism and further accentuates how each of them link into one another with the use of arrows. The different pathways all lead to examples of ‘terrorist acts’, however, it is important to acknowledge that the first three stages leading up to the fourth stage all have the potential to be occurring simultaneously. In addition, the first three stages in the cyber-enabled pathway have the opportunity to branch out to the fourth stage in the traditional and cyber dependent pathways as much of cyber-enabled activity can be supporting activity for the other pathways. It is further important to highlight that the ‘recruitment’ stage in traditional terrorism and cyber-enabled terrorism has the ability to remain active throughout the whole process as these activities are not specific to a single terrorist attack. Therefore, stakeholders should consider these ongoing background processes when detecting traditional terrorism and cyber terrorism. Although this framework is limited as it does not list every single type of terrorist offence under each pathway, it nonetheless highlights a few examples which can better inform law enforcement of the intricate relations between each pathway to improve investigative practices in countering terrorism.
Recommendations and Conclusion
This paper, and the research within, intended to contribute to current academic and professional discussion regarding cyber terrorism and how it is defined and understood amongst UK stakeholders involved in preventing, detecting, investigating and prosecuting cyber terrorism. Through critically analysing currently established definitions, theories and frameworks related to cyber terrorism, this research highlighted the problematic nature in the lack of a unanimous understanding. In light of this, a new cyber terrorism definition was proposed which incorporates cyber enabled and cyber dependant activity. Furthermore, by developing Smith et al.’s [ 16 ] terrorist activity process, this research proposed a potential ternary framework which could be utilised by UK stakeholders to gain a better understanding of cyber terrorist behaviours and their inextricable links to traditional terrorism. Although the definition and framework concisely define and classify cyber terrorism in light of the findings from the literature review and the primary data collection, further editing from stakeholders would be recommended to ensure complete compatibility with UK legislation, and stakeholder procedures. Subsequently, this research recommends that specific legislation regarding cyber terrorism be developed to support UK stakeholders in preventing, detecting, investigating and prosecuting cyber terrorist activity. Furthermore, although this paper specifically analysed the necessity for a definition and framework in context of the United Kingdom, this proposed definition and framework are nonetheless generic and could, therefore, potentially be adopted for use by other nations. In doing so, a more collaborative international approach could be established to increase the efficacy of countering cyber terrorist activity, overall better securing society from the risk of terrorism.
The secondary aim of this research was to determine what the public’s perception of cyber terrorism was through a mixed methods primary data collection approach. The quantitative data highlighted a gender effect on questions regarding recruitment as a cyber-enabled terrorist act, and stakeholder understanding in the context of combatting cyber terrorism. However, the rest of the quantitative data were non-significant and as a result of this, there was not sufficient evidence to substantiate some of the hypotheses surrounding demographic effect on topical questions. In light of the non-significant data, this research further recommends that the primary research be replicated and shared out to a wider audience to generate a larger sample population and determine whether the non-significant results from the primary data collection are due to type I or type II errors [ 90 , 103 ]. By gathering a clearer and more generalised understanding of the public’s views, UK stakeholders can better identify what the general public’s perception is, which could better inform clearer campaigns to educate the public on identifying and reporting cyber terrorist activity.
The literature review highlighted that news media outlets can have an effect on the way in which the public understand a matter, and analysis of the non-significant findings suggested that in the case of a type II error, this could be due to news media outlets’ gatekeeping role in disseminating information regarding cyber terrorism to the public [ 32 , 104 ]. Therefore, this research recommends that further research be carried out regarding the correlation between news media outlets which individuals read/listen to, and their perceptions of traditional and cyber terrorism.
Overall, this research has offered an insight into how cyber terrorism could be defined and classified for UK stakeholders as part of the search for the ‘holy grail’ [ 1 ]. This research specifically highlighted the importance of correlating a new definition and framework with UK legislation for enhanced compatibility and effectiveness. In current times with the COVID pandemic enabling the evolution of terrorist activity [ 2 ], it is ever more important to clearly understand and adapt stakeholder procedures in countering cyber terrorism in the UK.
Availability of Data and Material
Raw data not available.
Code Availability
Not applicable.
Perry NJ. The numerous federal legal definitions of terrorism: the problem of too many grails. J Legis. 2004;30(2):249–74.
Google Scholar
Tony Blair Institute for Global Change. Snapshot: how extremist groups are responding to COVID-19. Tony Blair Institute for Global Change. 2020. https://institute.global/sites/default/files/2020-05/Snapshot%203%20COVID19%20V02.pdf
Bieda D, Halawi L. Cyberspace: a venue for terrorism. Issues Inf Syst. 2015;16(3):33–42.
Arora B. Exploring and analysing Internet crimes and their behaviours. Perspect Sci. 2016;8:540–2. https://doi.org/10.1016/j.pisc.2016.06.014 .
Article Google Scholar
Marsili M. The war on cyberterrorism. Democr Secur. 2018;15(2):172–99. https://doi.org/10.1080/17419166.2018.1496826 .
Luiifj E. Definitions of cyber terrorism. In: Staniforth A, Bosco F, editors. Cyber crime and cyber terrorism investigator’s handbook. Amsterdam: Elsevier Science; 2014. p. 11–7.
McGuire M, Dowling S. Cybercrime: a review of the evidence: summary of key findings and implications. Home Office Research Report 75. London: Home Office, October. 2013. https://assets.publishing.service.gov.uk/government/uploads/system/uploads/attachment_data/file/246749/horr75-summary.pdf
Home Office. Operation of police powers under the Terrorism Act 2000 and subsequent legislation: arrests, outcomes and stop and search Great Britain, financial year ending March 2020. Home Office National Statistics. 2020. https://assets.publishing.service.gov.uk/government/uploads/system/uploads/attachment_data/file/891341/police-powers-terrorism-mar2020-hosb1520.pdf
Home Office. Operation of police powers under the Terrorism Act 2000 and subsequent legislation: arrests, outcomes, and stop and search Great Britain, year ending March 2021. 2021. https://www.gov.uk/government/statistics/operation-of-police-powers-under-the-terrorism-act-2000-financial-year-ending-march-2021/operation-of-police-powers-under-the-terrorism-act-2000-and-subsequent-legislation-arrests-outcomes-and-stop-and-search-great-britain-year-ending#arrests-and-outcomes
Kshetri N. The global cybercrime industry. Berlin: Springer; 2010.
Book Google Scholar
Bernat F, Makin D. Cybercrime theory and discerning if there as a crime: the case of digital piracy. Int Rev Mod Sociol. 2014;40(2):99–119.
Yunos Z, Sulaman S. Understanding cyber terrorism from motivational perspectives. J Inf Warf. 2017;16(4):1–13.
Helbing D, Brockmann D, Chadefaux T, Donnay K, Blanke U, Woolley-Meza O, Moussaid M, Johansson A, Krause J, Schutte S, Perc M. Saving human lives: what complexity science and information systems can contribute. J Stat Phys. 2014;158:735–81. https://doi.org/10.1007/s10955-014-1024-9 .
Article MathSciNet MATH Google Scholar
Jaishankar K. Establishing a theory of cyber crimes. Int J Cyber Criminol. 2007;1(2):7–9. https://doi.org/10.5281/ZENODO.18792 .
Cohen LE, Felson M. Social change and crime rate trends: a routine activity approach. Am Sociol Rev. 1979;44(4):588–608. https://doi.org/10.2307/2094589 .
Smith BL, Cothren J, Roberts P, Damphousse KR. Geospatial analysis of terrorist activities: the identification of spatial and temporal patterns of preparatory behaviour of international and environmental terrorists. Terror Res Center Fulbright Coll. 2008;222909:14.
Enders W, Sandler T. The political economy of terrorism. 2nd ed. Cambridge: Cambridge University Press; 2012.
Hoffman B. Inside terrorism. 3rd ed. New York: Colombia University Press; 2017.
Sandler T. Terrorism and counterterrorism: an overview. Oxf Econ Pap. 2015;67(1):1–20. https://doi.org/10.1093/oep/gpu039 .
Anderson D. Shielding the compass: how to fight terrorism without defeating the law. SSRN Electron J. 2013. https://doi.org/10.2139/ssrn.2292950 .
Greene A. Defining terrorism: one size fits all? Int Comp Law Q. 2017;66(2):411–40. https://doi.org/10.1017/S0020589317000070 .
Hewer CJ, Taylor W. Deconstructing terrorism: Politics, language and social representation. In: Roberts R, editor. Just war: psychology and terrorism. London: PCCS Books; 2007. p. 199–212.
Monroe KR, Kreidie LH. The perspective of Islamic fundamentalists and the limits of rational choice theory. Polit Psychol. 2002;18(1):19–43. https://doi.org/10.1111/0162-895X.00043 .
Lee RD. Religion and politics in the Middle East. 2nd ed. New York: Routledge; 2013.
Fox J. Separation of religion and state and secularisation in theory and in practice. Relig State Soc. 2011;39(4):384–401. https://doi.org/10.1080/09637494.2011.621675 .
Nikfar J. Globalisation and future of power relations in the Arabic Middle-East: a case study of Egypt and Libya. Humanit Soc Sci Commun. 2020;7:134. https://doi.org/10.1057/s41599-020-00631-7 .
Stocchetti M. The politics of fear: A critical inquiry into the role of violence in 21st century politics. In: Hodges A, Nilep C, editors. Discourse, war and terrorism. Amsterdam: John Benjamin’s Publishing Company; 2007. p. 223–48.
Chapter Google Scholar
Terrorism Act 2006, c.11. 2006. https://www.legislation.gov.uk/ukpga/2006/11/contents
Counter-Terrorism Act 2008, c.28. 2008. https://www.legislation.gov.uk/ukpga/2008/28/contents
Fine J. Political and philological origins of the term ‘terrorism’ from the ancient near east to our times. Middle East Stud. 2010;46(2):271–88.
Lewin K. Frontiers in group dynamics: II. Channels of group life; social planning and action research. Hum Relat. 1947;1(2):143–53. https://doi.org/10.1177/001872674700100201 .
Shoemaker PJ, Vos T. Gatekeeping theory. 1st ed. Amsterdam: Routledge; 2009.
White DM. The “Gate Keeper”: a case study in the selection of news. Journal Mass Commun Q. 1950;27(4):383–90. https://doi.org/10.1177/107769905002700403 .
Tabansky L. Basic concepts in cyber warfare. Mil Strateg Aff. 2011;3(1):75–92.
Weiner N. Cybernetics or control and communication in the animal and the machine. London: MIT Press; 1948.
Gibson W. Neuromancer. London: Orion Publishing Co.; 1948.
Collin J, Flutter A. Reassessing the revolution in military affairs: transformation evolution and lessons learnt. London: Palgrave; 2015.
Flutter A. ‘Cyber’ semantics: why we should retire the latest buzzword in security studies. J Cyber Policy. 2018;3(2):201–16. https://doi.org/10.1080/23738871.2018.1514417 .
Lehto M, Huhtinen A, Jantunen S. The open definition of cyber: technology or a social construction? Int J Cyber Warf Terror. 2011;1(2):1–9. https://doi.org/10.4018/ijcwt.2011040101 .
Conway M. Reality check: assessing the (un)likelihood of cyberterrorism. In: Chen TM, Jarvis L, Macdonald S, editors. Cyberterrorism: understanding, assessment, and response. Berlin: Springer; 2014. p. 103–21.
Denning DE. A view of cyberterrorism 5 years later. In: Himma KE, editor. Internet security: hacking, counterhacking, and society. Burlington: Jones and Bartlett Publishers; 2006. p. 123–39.
Foltz BC. Cyberterrorism, computer crime, and reality. Inf Manag Comput Secur. 2004;12(2):154–66. https://doi.org/10.1108/09685220410530799 .
Holt TJ. Exploring the intersections of technology, crime, and terror. Terror Polit Violence. 2012;24(2):337–54. https://doi.org/10.1080/09546553.2011.648350 .
Gordon S, Ford R. Cyberterrorism? Comput Secur. 2002;21(7):636–47. https://doi.org/10.1016/S0167-4048(02)01116-1 .
Plotnek JJ, Slay J. Cyber terrorism: a homogenized taxonomy and definition. Comput Secur. 2021;102:1–9. https://doi.org/10.1016/j.cose.2020.102145 .
Choi KS, Lee CS. The present and future of cybercrime, cyberterrorism, and cybersecurity. Int J Cybersecur Intell Cybercrime. 2018;1(1):1–4.
Choi KS. Computer crime victimisation and integrated theory: an empirical assessment. Int J Cyber Criminol. 2008;2(1):308–33.
McQuade SC. Understanding and managing cybercrime. London: Pearson; 2006.
Choi KS, Scott TM, LeClair DP. Ransomware against police: diagnosis of risk factors via application of cyber-routine activities theory. Int J Forensic Sci Pathol. 2016;4(7):253–8. https://doi.org/10.19070/2332-287X-1600061 .
Suler J. The online disinhibition effect. Cyber Psychol Behav. 2004;7(3):321–6. https://doi.org/10.1089/1094931041291295 .
Agustina JR. Understanding cyber victimization: digital architectures and the disinhibition effect. Int J Cyber Criminol. 2015;9(1):35–54. https://doi.org/10.5281/zenodo.22239 .
Lee CS, Choi KS, Shandler R, Kayser C. Mapping global cyberterror networks: an empirical study of Al-Qaeda and ISIS cyberterrorism events. J Contemp Crim Justice. 2021;37(3):333–55. https://doi.org/10.1177/10439862211001606 .
Stalans LJ, Finn MA. Understanding how the internet facilitates crime and deviance. Vict Offenders. 2016;11(4):501–8. https://doi.org/10.1080/15564886.2016.1211404 .
Crown Prosecution Service. Terrorism. 2021. https://www.cps.gov.uk/crime-info/terrorism
Wilkinson P. Terrorism. In: Gill M, editor. The handbook of security. London: Palgrave; 2006.
Terrorism Act 2000, c.11. 2000. https://www.legislation.gov.uk/ukpga/2000/11/contents
Counter-Terrorism and Border Security Act 2019, c.3. 2019. https://www.legislation.gov.uk/ukpga/2019/3/contents/enacted
Bertram L. Terrorism, the internet and the social media advantage: Exploring how terrorist organisations exploit aspects of the internet, social media and how these same platforms could be used to counter-violent extremism. J Deradicalisation. 2016;7:225–52.
Holt TJ. Regulating cybercrime through law enforcement and industry mechanisms. Ann Am Acad Polit Soc Sci. 2018;679(1):140–57. https://doi.org/10.1177/0002716218783679 .
Department for Digital, Culture, Media and Sport. Draft Online Safety Bill (CP405). London. 2021. https://assets.publishing.service.gov.uk/government/uploads/system/uploads/attachment_data/file/985033/Draft_Online_Safety_Bill_Bookmarked.pdf
Wingfield R. First thoughts on the UK’s Draft Online Safety Bill. Global Partners Digital. 2021. https://www.gp-digital.org/first-thoughts-on-the-uks-draft-online-safety-bill/
Woods L, Perrin W. The Draft Online Safety Bill: Carnegie UK Trust initial analysis. Carnegie UK Trust. 2021. https://www.carnegieuktrust.org.uk/blog/the-draft-online-safety-bill-carnegie-uk-trust-initial-analysis/
Crown Prosecution Service. Cybercrime - Prosecution Guidance. 2019. https://www.cps.gov.uk/legal-guidance/cybercrime-prosecution-guidance
Archibald MM, Radil AI, Zhang X. Current mixed methods practices in qualitative research: a content analysis of leading journals. Int J Qual Methods. 2017;14(2):5–33. https://doi.org/10.1177/160940691501400205 .
Brannen J. Mixing methods the entry of qualitative and quantitative approaches into the research process. Int J Soc Res Methodol. 2007;8(3):173–84. https://doi.org/10.1080/13645570500154642 .
Guthrie G. Basic research methods: an entry to social science research. London: SAGE Publications; 2010.
Hatch MJ. Organisation theory: modern, symbolic and postmodern perspectives. Oxford: Oxford University Press; 2012.
Elmir R, Schmied V, Jackson D, Wilkes L. Interviewing people about potentially sensitive topics. Nurse Res. 2011;19(1):12–6. https://doi.org/10.7748/nr2011.10.19.1.12.c8766 .
Evans JR, Mathur A. The value of online surveys. Internet Res. 2005;15(2):195–219. https://doi.org/10.1108/10662240510590360 .
Lewis-Beck MS, Bryman A, Liao TF. The SAGE encyclopedia of social science research methods. London: SAGE Publications; 2004.
Sue VM, Ritter LA. Conducting online surveys. London: SAGE Publications; 2012.
Jisc Online Surveys. Jisc Online Survey Tool. 2021. https://www.onlinesurveys.ac.uk/
Etikan I, Musa SA, Alkassim RS. Comparison of convenience sampling and purposive sampling. Am J Theor Appl Stat. 2015;5(1):1–4. https://doi.org/10.11648/j.ajtas.20160501.11 .
Jager J, Putnick DL, Bornstein MH. More than just convenient: the scientific merits of homogeneous convenience samples. Monogr Soc Res Child Dev. 2017;82(2):13–30. https://doi.org/10.1111/mono.12296 .
Andrade C. The inconvenient truth about convenience and purposive samples. Indian J Psychol Med. 2020;43(1):86–8. https://doi.org/10.1177/0253717620977000 .
Balter F, Brunet I. Social research 2.0: virtual snowball sampling method using Facebook. Internet Res. 2012;22(1):57–74. https://doi.org/10.1108/10662241211199960 .
Andrade C. The limitations of online surveys. Indian J Psychol Med. 2020;42(6):575–6. https://doi.org/10.1177/0253717620957496 .
Brace I. Questionnaire design: how to plan, structure and write survey material for effective market research. 4th ed. London: Kogan Page; 2018.
Miller RL, Acton C, Fullerton DA, Maltby J. SPSS for social scientists. London: Palgrave Macmillan; 2002.
Ozgur C, Kleckner M, Li Y. Selection of statistical software for solving big data problems: a guide for businesses, students and universities. SAGE Open. 2015;5(2):1–12. https://doi.org/10.1177/2158244015584379 .
Stehlik-Barry K, Babinec AJ. Data analysis with IBM SPSS statistics. Birmingham: Packt Publishing; 2017.
Lester JN, Cho Y, Lochmiller CR. Learning to do qualitative data analysis: a starting point. Hum Resour Dev Rev. 2020;19(1):94–106. https://doi.org/10.1177/1534484320903890 .
Busetto L, Wick W, Gumbinger C. How to use and assess qualitative research methods. Neurol Res Pract. 2020;2(14):1–10. https://doi.org/10.1186/s42466-020-00059-z .
Fossey E, Harvey C, McDermott F, Davidson L. Understanding and evaluating qualitative research. Austral N Z J Psychiatry. 2002;36(6):717–32. https://doi.org/10.1046/j.1440-1614.2002.01100.x .
British Society of Criminology. Statement of ethics. British Society of Criminology. 2015. https://www.britsoccrim.org/documents/BSCEthics2015.pdf
Data Protection Act 2018, c.12. 2018. https://www.legislation.gov.uk/ukpga/2018/12/contents/enacted
Hoffman ML. Sex differences in empathy and related behaviours. Psychol Bull. 1977;84(4):712–22. https://doi.org/10.1037/0033-2909.84.4.712 .
Mestre MV, Samper P, Frías MD, Tur AM. Are women more empathetic than men? A longitudinal study in adolescence. Span J Psychol. 2013;12(1):76–83. https://doi.org/10.1017/S1138741600001499 .
Szucs D, Ioannidis JPA. Empirical assessment of published effect sizes and power in the recent cognitive neuroscience and psychology literature. PLoS Biol. 2021;15(3):1–18. https://doi.org/10.1371/journal.pbio.2000797 .
Goodman S. A dirty dozen: twelve p-value misconceptions. Semin Hematol. 2008;45(3):135–40. https://doi.org/10.1053/j.seminhematol.2008.04.003 .
Speckhard A, Ellenberg MD. ISIS in their own words: recruitment history, motivations for joining, travel, experiences in ISIS, and disillusionment over time – analysis of 220 in-depth interviews of ISIS returnees, defectors and prisoners. J Strateg Secur. 2020;13(1):82–127.
Kruglanski AW, Gunaratna R, Ellenberg M, Speckhard A. Terrorism in time of the pandemic: exploiting mayhem. Glob Secur. 2020;5(1):121–32. https://doi.org/10.1080/23779497.2020.1832903 .
Home Office. Police workforce, England and Wales, as at 31 March 2020 second edition. Home Office National Statistics. 2020. https://assets.publishing.service.gov.uk/government/uploads/system/uploads/attachment_data/file/955182/police-workforce-mar20-hosb2020.pdf
Profeta P. Gender equality in decision-making positions: the efficiency gains. Intereconomics. 2017;52:34–7. https://doi.org/10.1007/s10272-017-0640-4 .
Rose C. Does female board representation influence firm performance? The Danish Evidence. Corp Gov Int Rev. 2007;15(2):404–13. https://doi.org/10.1111/j.1467-8683.2007.00570.x .
Sarhan AA, Ntim CG, Al-Najjar B. Board diversity, corporate governance, corporate performance and executive pay. Int J Financ Econ. 2018;24(2):761–86. https://doi.org/10.1002/ijfe.1690 .
Van Der Walt N, Ingley C. Board dynamics and the influence of professional background, gender and ethnic diversity of directors. Corp Gov Int Rev. 2003;11(3):218–34. https://doi.org/10.1111/1467-8683.00320 .
Uberoi E, Watson C, Mutebi N, Danechi S, Bolton P. Women in politics and public life (Breifing Paper Number 01250). House of Commons Library. 2021. https://researchbriefings.files.parliament.uk/documents/SN01250/SN01250.pdf
Hartgerink CHJ, Wicherts JM, Van Assen MALM. Too good to be false: nonsignificant results revisited. Collabra. 2017;3(1):1–18. https://doi.org/10.1525/collabra.71 .
Visentin DC, Cleary M, Hunt GE. The earnestness of being important: reporting non-significant statistical results. J Adv Nurs. 2019;76(4):917–9. https://doi.org/10.1111/jan.14283 .
Greenland S, Senn SJ, Rothman KJ, Carlin JB, Poole C, Goodman SN, Altman DG. Statistical tests, P values, confidence intervals and power: a guide to misinterpretations. Eur J Epidemiol. 2016;31:337–50. https://doi.org/10.1007/s10654-016-0149-3 .
Higgins JPT, Thompson SG, Deeks JJ, Altman DG. Measuring inconsistency in meta-analysis. BMJ. 2003;327(557):557–60. https://doi.org/10.1136/bmj.327.7414.557 .
Aberson C. Interpreting null results: improving presentation and conclusions with confidence intervals. J Artic Supp Null Hypothesis. 2002;1(3):36–42.
Vermeer S, Trilling D, Kruikemeier S, Vreese C. Online news user journeys: the role of social media, news websites, and topics. Digit J. 2020;8(9):1114–41. https://doi.org/10.1080/21670811.2020.1767509 .
Welbers K, Opgenhaffen M. Social media gatekeeping: an analysis of the gatekeeping influence of newspapers’ public Facebook pages. New Media Soc. 2018;20(12):4728–47. https://doi.org/10.1177/1461444818784302 .
Boris T. Russian hackers target president Vladimir Putin’s Phone-In, Major Telco Confirms cyberattack. Tech Times. 2021. https://www.techtimes.com/articles/262260/20210701/hackers-cyber-attack-russian-president-putin-s-phone-in.htm
Robinson C. Northern’s ticket machines hit by ransomware cyber attack. BBC News. 2021. https://www.bbc.co.uk/news/uk-england-57892711
Russon M. US fuel pipeline hackers ‘didn’t mean to create problems’. BBC News. 2021. https://www.bbc.co.uk/news/business-57050690
BBC News.. Shamima Begum: ‘I didn’t want to be IS poster girl’. BBC News. 2021. https://www.bbc.co.uk/news/uk-47276572
Casciani D. Shamima Begum: What can the UK do about the IS teenager?. BBC News. 2019. https://www.bbc.co.uk/news/uk-47240100
BBC News. Shamima Begum cannot return to UK, Supreme Court rules. BBC News. 2021. https://www.bbc.co.uk/news/uk-56209007
Home Office. CONTEST the United Kingdom’s strategy for countering terrorism. 2018. https://assets.publishing.service.gov.uk/government/uploads/system/uploads/attachment_data/file/716907/140618_CCS207_CCS0218929798-1_CONTEST_3.0_WEB.pdf
YouTube. YouTube Policies Violent Criminal Organisations Policy. YouTube Help. 2021. https://support.google.com/youtube/answer/9229472?hl=en&ref_topic=9282436
Facebook. Community standards violence and criminal behaviour. Facebook Community Standards. 2021. https://www.facebook.com/communitystandards/violence_criminal_behavior
Home Office. Proscribed terrorist groups or organisations. Gov UK. 2021. https://www.gov.uk/government/publications/proscribed-terror-groups-or-organisations--2/proscribed-terrorist-groups-or-organisations-accessible-version
Holmes O, Beaumont P. Israel launches airstrike on Gaza Strip after Hamas rocket attacks. The Guardian. 2021. https://www.theguardian.com/world/2021/may/10/hamas-fires-rockets-into-israel-in-dispute-over-jerusalem-mosque
Srivastava M. Hamas rocket attacks provoke Israeli retaliation in Gaza. Financial Times. 2021. https://www.ft.com/content/887f0b34-1e08-428c-92c0-603e7830ba5b
Bancroft H, Mathers M, Tidman Z. Jake Davison named as Plymouth shooter: what we know so far. The Independent. 2021. https://www.independent.co.uk/news/uk/home-news/jake-davison-plymouth-shooting-b1901948.html
Hardy J, Gardner B, Lyons I. ‘I am a terminator’ boasted Plymouth gunman Jake Davison in final YouTube video before rampage. The Telegraph. 2021. https://www.telegraph.co.uk/news/2021/08/14/plymouth-shooting-gunman-said-terminator-final-youtube-video/?li_source=LI&li_medium=liftigniter-onward-journey
Download references
Author information
Authors and affiliations.
School of Criminology and Criminal Justice, University of Portsmouth, University House, Winston Churchill Avenue, Portsmouth, PO1 2UP, UK
Victoria Jangada Correia
You can also search for this author in PubMed Google Scholar

Corresponding author
Correspondence to Victoria Jangada Correia .
Ethics declarations
Conflict of interest.
The corresponding author states that there are no conflicts of interest.
Ethical Approval
Favourable ethical opinion granted by the School of Criminology and Criminal Justice Ethics Committee from the University of Portsmouth on 05/03/2021.
Consent to Participate
Consent for publication, additional information, publisher's note.
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
This article is part of the topical collection “Cyber Security and Privacy in Communication Networks” guest-edited by Rajiv Misra, R K Shyamsunder, Alexiei Dingli, Natalie Denk, Omer Rana, Alexander Pfeiffer, Ashok Patel and Nishtha Kesswani.

Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution 4.0 International License, which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if changes were made. The images or other third party material in this article are included in the article's Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article's Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by/4.0/ .
Reprints and permissions
About this article
Jangada Correia, V. An Explorative Study into the Importance of Defining and Classifying Cyber Terrorism in the United Kingdom. SN COMPUT. SCI. 3 , 84 (2022). https://doi.org/10.1007/s42979-021-00962-5
Download citation
Received : 28 September 2021
Accepted : 04 November 2021
Published : 24 November 2021
DOI : https://doi.org/10.1007/s42979-021-00962-5
Share this article
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
- Cyber terrorism
- Counter terrorism
- Cyber crime
- Find a journal
- Publish with us
- Track your research
An official website of the United States government
The .gov means it’s official. Federal government websites often end in .gov or .mil. Before sharing sensitive information, make sure you’re on a federal government site.
The site is secure. The https:// ensures that you are connecting to the official website and that any information you provide is encrypted and transmitted securely.
- Publications
- Account settings
Preview improvements coming to the PMC website in October 2024. Learn More or Try it out now .
- Advanced Search
- Journal List
- HHS Author Manuscripts

The psychological effects of cyber terrorism
When ordinary citizens think of cyber threats, most are probably worried about their passwords and banking details, not a terrorist attack. The thought of a shooting in a mall or a bombing at an airport is probably more frightening than a cyber breach. Yet terrorists aim for mental as well as physical destruction, and our research has found that, depending on who the attackers and the victims are, the psychological effects of cyber threats can rival those of traditional terrorism.
Cyber aggression has become a daily fact of life in the 21st century, yet for most people it’s still only a reality in the form of cyber crime—hackers targeting financial information or other personal details. Politically motivated attacks might threaten them as well, but they tend to be the concern of governments and corporations rather than ordinary citizens. The thought of a terrorist shooting in a mall or bombing in an airport probably seems far more frightening to the average person than Russian hackers disrupting government networks in Estonia or Anonymous breaking into the police department of Ferguson, Missouri. Cyber terrorists, after all, have yet to actually kill or injure anyone. Yet our research has found this perception of cyber aggression might not be entirely accurate. The aim of terrorism, after all, is not just physical destruction, and depending on who the attackers and the victims are, the psychological effects of cyber terrorism can be just as powerful as the real thing.
Defining cyber terrorism
People face cyber aggression on an almost daily basis. Hackers appropriate, erase, or ransom data, defraud bank customers, steal identities, or plant malevolent viruses. In many cases, hackers are criminals out for pecuniary gain. But sometimes their motives are political. Some are “hacktivists,” or cyber activist groups, like Anonymous, others are terror groups like Hamas or Islamic State, and still others are agents of national states like Iran, North Korea, or Russia. They are not usually after money but pursue a political agenda to foment for social change, gain political concessions, or cripple an enemy. Sometimes their means are peaceful but other times they are vicious and violent. The lines often blur. Anonymous will hack the Ferguson police department just as it will initiate an “electronic Holocaust” against Israel in support of the Palestinian cause ( Rogers 2014 ). Islamic activists will not only use the Internet to recruit members and raise funds for social welfare projects but also to steal money for terrorist activities or disseminate information to stoke fear and demoralize a civilian population. States will pursue online espionage but also wreak havoc by crashing multiple systems—as did the Russians, allegedly, in Estonia in 2007, with mass denial-of-service attacks on government sites, and in Ukraine in 2016, with cyber attacks on the airport and power grid ( Polityuk 2016 ).
Underlying many of these attacks is terrorism: an attempt to extract political concessions by instilling fear in the civilian population. In this way, cyber terrorism is no different from conventional terrorism. Yet cyber terrorism is far more subtle. To date, cyber terrorists have neither killed nor injured anyone. Nor have cyber terrorists successfully destroyed any critical infrastructures. Whether this is due to the offensive inadequacies of the terrorists or the superior defensive capabilities of the United States and its allies, experts have yet to decide.
But as the war on cyber terrorism continues, it is increasingly clear that protecting vital national interests is only half the battle. Security experts rightly worry about defending transportation networks, refineries, dams, military installations, hospitals, banks, and government offices from cyber attack just as they worry about defending the same facilities from terrorist bombs or ballistic missiles ( Lewis 2002 ). Yet lost in the haze of cyber warfare is the human dimension. While scholars and policy makers raise concerns about the dangers that cyber terrorism holds for national security, we know little about its effects on human security.
Human security emphasizes the conditions necessary for a vibrant civil society ( Tadjbakhsh 2014 ). At the most basic level, people must be able to live free of undue fear, anxiety, and trepidation. At a more developed level, civil society requires energetic public discourse, judicious public policy, and respect for human dignity. Following 9/11, we now recognize that conventional terrorism undermines human security even more than national security. It is a common truism that terrorists want a lot of people watching, not a lot of people dead ( Jenkins 1975 ; Lerner et al. 2003 ). The dead are few; it is the living whose daily lives are transformed by the constant fear of impending doom. Conventional terrorism exacerbates feelings of insecurity and perceptions of threat that prompt public cries for protective and militant government policies that can short-circuit public discourse, intensify intolerance for dissident views, and infringe on human rights ( Boggs 2002 ; Hirsch-Hoefler et al., 2014 ). Does cyber terrorism cause similar effects?
At first glance, it seems that it cannot. In their attempts to formulate the law of cyber warfare, the framers of the Tallinn Manual on the International Law Applicable to Cyber Warfare remain unconvinced that cyber attacks that block e-mail, deny service, employ economic coercion, undermine confidence in the government or economy, or, in their example, “cause panic by falsely indicating that a highly contagious and deadly disease is spreading through the population” cause sufficient mental suffering to rise to the level of a terrorist attack ( Schmitt 2013 , §11.2, 3; 30.12; 36.3; 59.9). Unfortunately, these assumptions are untested and in a series of field experiments we studied how cyber terrorism affects psychological well-being and political attitudes that impinge upon human security by causing stress, anxiety, and fear—all of which radicalize political attitudes and push people to exchange privacy for security to prevent cyber terror in the future.
Simulating cyber terrorism
In our field survey experiments, we first interviewed 522 individuals following Anonymous’s well-publicized attempt to perpetrate an “electronic Holocaust” in April 2015, when the hacktivist group promised to take down servers and “erase Israel from cyber space.” In a second study, in January 2016, 907 subjects viewed various film clips describing hypothetical Hamas attacks on Israel’s national water company. In one scenario, cyber terrorism was fatal; terrorists poisoned the water supply with an overdose of chlorine that killed two and injured many more. In other scenarios, cyber terrorism was not lethal; no one suffered physical harm but hackers appropriated the bank account numbers of the company’s customers and successfully transferred money to Hamas. A third group of subjects viewed a fatal but conventional mass-casualty terrorist attack, while a control group viewed a neutral film depicting the dedication of a water treatment plant. Following these screenings, we surveyed respondents on measures fundamental to human security. These included stress, anxiety, insecurity and threat perception, political militancy, and a willingness to relinquish privacy and civil liberties in favor of security.
In some ways, Israelis are a unique population for such a study. The ongoing conflict between Israelis and Palestinians (and Palestinian allies like Hezbollah and Iran) is a constant feature of everyday life. Terrorism, too, simmers beneath the surface. Since January 2015, terrorists have taken 23 civilian lives in Israel. Yet Israelis know their enemy, know what they want and can imagine the way to peace. This puts terrorism and cyber terrorism in the context of a political struggle that has, in many ways, fixed and acceptable costs. Like a couple of wary boxers, each side circles the other, constantly poking and provoking. This leaves Israelis, who score very high on the UN’s world happiness index, weary but resilient.
In contrast, the West’s confrontation with radical Islam is enigmatic and exceptionally violent. In the same period since the start of last year, 67 Americans and 197 Europeans have lost their lives in terrorist attacks. Unlike Israelis, Americans and Europeans don’t know their enemy, have no clear idea what they want or how to confront their demands. Islamic State attacks are brutally violent for their own sake. Americans and especially Europeans will find resilience elusive as terrorism and cyber terrorism fuel an inescapable cycle of fear. Learning from the Israeli case and understanding the effects of cyber terrorism for other Western nations is crucially important.
Measuring stress and insecurity
Not surprisingly, exposure to cyber terrorism is stressful. Figure 1 uses the State-Trait Anxiety Inventory (STAI) to show how stress and anxiety grow as attacks become more deadly. With a score of 4.00, conventional mass-casualty terrorism (e.g., suicide bombings) evokes a level of anxiety at the top of the scale. The stress scores for lethal and non-lethal cyber terrorism are not far behind, and all the scores significantly surpass the control group. But the interesting point is this: Individuals were equally disturbed by lethal and non-lethal cyber terrorism, meaning there is no significant difference between the two when it comes to stress. Both cause significant panic and anxiety and both, it seems, are equally capable of cracking the foundations of personal wellbeing and human security.

Anxiety in the Wake of Terrorism
CONTROL: No terrorism
CYBER TERRORISM, NON-LETHAL: Disclosure of account information, loss of funds
CYBER TERRORISM, LETHAL: Deaths and injuries
CONVENTIONAL TERRORISM, LETHAL: Deaths and injuries
Cyber terrorism also left individuals insecure and wary of future cyber terrorist attacks. These judgments are measures of threat perception and gauged by such questions as: “To what extent do cyber attacks undermine your sense of personal security?” and “To what extent do you feel threatened by cyber terrorism?” Like stress, threat perception increased steadily as attacks grew more severe ( Figure 2 ). But even in our control group, Israelis are on edge and exposure to non-lethal cyber terrorism did not appreciably increase perceptions of threat. Lethal attacks, on the other hand, did trigger a significant jump in threat perception and it didn’t matter much whether they were cyber or conventional terrorist attacks. These findings show how stress and threat perception are two different phenomena. Stress is emotional while threat perception is cognitive. And while lethal and non-lethal cyber attacks evoke feelings of stress, only terrorism accompanied by injury and loss of life nurtures a serious preoccupation about the next attack. If a person’s reaction to cyber terrorism has both an emotional and cognitive dimension, it is also sensitive to circumstance and the identity of the perpetrator. After it was clear that Anonymous’s threat of an “electronic Holocaust” was empty, threat perception fell by 10 percent. People were still fearful, but not so much. But many Israelis do fear Hamas. and when that group, rather than Anonymous, was the perpetrator, threat perceptions increased by 20 percent, from a mean score of 2.9 to a score of 3.5. Hamas is a far more frightening adversary than Anonymous, even as they perpetrate similar attacks.

Threat Perception and Insecurity
Stress, anxiety, insecurity, and perceptions of threat do not stand alone. Instead, we know that studies of conventional terrorism show how stress, anxiety, and heightened perceptions of threat radicalize political attitudes and draw individuals away from concerns about civil liberties to worries about national security ( Verton and Brownlow 2003 ). In the wake of mass-casualty terrorism, individuals turn inward, disparage outgroups, move to the right on security and privacy issues, and call upon their government to take strong military action ( Canetti et al. 2013 ; McDermott 2010 ). The effects can have a chilling effect on civil society and political discourse in many democratic nations, as debates about torture, rendition, due process, military belligerency, and surveillance show. We were not surprised to see similar effects from cyber terrorism.
Political reactions
Figures 3 and and4 4 depict an array of political attitudes that harden in the wake of terrorism. As noted, individuals in our first survey confronted an ongoing cyber attack by Anonymous and in the second, a simulated attack by Hamas. In each case, we asked individuals about their support for internet surveillance, government regulation, and military retaliation in the context of an unspecified cyber terror attack. Questions centered on surveillance and civil liberties (“Should the government monitor emails and social networks for suspicious phrases?”; “Are you willing to let the government read emails to improve personal and national security?”), 1 government regulation (“Should the government require businesses to install cyber security systems?”), and military retaliation (“Following a cyber terrorism attack, should the government respond with a small-scale cyber attack against military targets, a large-scale cyber attack against military and civilian targets, a small-scale conventional (missiles, bombs, and artillery) attack against military targets, or a large-scale conventional attack attacks against military and civilian targets?”)

Percent Favoring Survelliance and Government Regulation

Percent Favoring Small-Scale and Large-Scale or Conventional Retaliation
CYBER RETALIATION SMALL SCALE: Cyber attacks against military targets
CYBER RETALIATION LARGE SCALE: Cyber attacks against military and civilian targets
CONVENTIONAL RETALIATION SMALL SCALE: Kinetic attacks against military targets
CONVENTIONAL RETALIATION LARGE SCALE: Kinetic attacks against military and civilian targets
Attitudes varied depending on the perpetrator. When Anonymous was the attacker, 54 percent of the respondents in our survey would allow the government to monitor e-mails for suspicious phrases, 48 percent would allow the government to monitor Facebook and Twitter, and 23 percent would allow the government to read e-mails. When the perpetrator was Hamas, support for government surveillance leaps to 67 percent in favor of monitoring e-mails, 46 percent in favor of monitoring social media, and 61 percent in favor of reading e-mails. Among Americans in general, by contrast, only 43% of the respondents would allow the US government to monitor the communications of US citizens ( Shelton et al. 2015 , 6). Among Israelis, support for surveillance depends on the identity of the perpetrator. And while the identity of the attacker did not affect calls for government regulation (74 percent of the respondents would require business to install cyber security software) fears of Islamic terrorism dominate the public’s demand for military responses. As Figure 4 demonstrates, individuals facing Hamas terrorism were considerably more militant and supported conventional retaliation by a margin of nearly 2:1 compared to those facing the hacktivist group Anonymous. One reason may be greater fear of Hamas but another may be the recognition that Hamas, like Islamic State, has infrastructures and territory vulnerable to conventional attack. On the other hand, it is fear of Hamas rather than its vulnerability that drives greater support for surveillance. These data highlight the public’s willingness to employ conventional military measures to quash cyber terrorism, strong attitudes that will no doubt influence political leaders as they weigh kinetic military responses to cyber threats ( Libicki 2014 ).
From a psychological perspective, the data offer a curious finding. We expected to find a clear connection between exposure to cyber terrorism and militant, hardline attitudes. The harsher the terrorist attack our subjects experienced, the greater their militancy. But this is not what we discovered. Instead, we found that the greater one’s perception of threat , the greater one’s militancy. The odds were more than twice as high that individuals with high levels of threat perception will support surveillance, government regulation, and military retaliation compared to those whose threat perception is lower. We cannot explain why some individuals are more fearful than others. Past exposure to cyber attacks explains only a small part of the variance. Other personality factors, beyond the scope of our study to examine, are also probably at work. Nevertheless, it is clear that the threat of terrorism and how one perceives it are better determinants of militancy and hardline attitudes than the experience of an actual attack. And, indeed, this is how terrorism works. One need not suffer direct harm to be terrorized; it is enough that one fear direct harm to suffer the ravages of contemporary terrorism, whether cyber terrorism or conventional terrorism.
From Anonymous and Hamas to Islamic State
These results offer tantalizing evidence that cyber terrorism mirrors conventional terrorism even when its victims do not suffer injury or loss of life. We found that cyber terrorism increases stress, anxiety, fear, hardline attitudes, and political militancy. But circumstances matter, because the identity of the perpetrator helps explain the political attitudes related to cyber terrorism. Hamas is more threatening than Anonymous. When Hamas is at the wheel, Israelis see a brutal terrorist organization and do not much distinguish between cyber and conventional terrorism. Anonymous, on the other hand, still carries some cachet as a rogue hacktivist group that is unwilling or unable to harm anyone physically. Hamas, for the most part, poses no threat to Americans and Europeans. But Islamic State certainly does, and it will not be long before the group gains the capabilities to mount cyber-terrorism attacks. And, as with Hamas, the fact that these attacks might cause little physical harm may be irrelevant. Islamic State, like Hamas, will trade on its ruthless terrorist image. Leveraging its success at conventional terrorism, it will move seamlessly and effectively to cyber terrorism to produce outsized fear and panic. Marrying conventional and cyber terrorism will have chilling effects: Islamic State and other terrorist groups will be able to achieve the dramatic effects of suicide attacks and mass casualties at the relatively low cost and risk of cyber terrorism. There will be no need for suicide cyber bombers. Cyber terrorism is a force multiplier that can magnify the effects of limited, sporadic, and even failed kinetic terrorist attacks. In tandem, conventional and cyber terrorism can undermine human security in a most fundamental way.
Restoring human security
Human security thrives when societies are open, tolerant, peaceful, and vibrant, and when they offer citizens the conditions necessary to flourish economically, intellectually, physically, and emotionally ( Tadjbakhsh and Chanoy 2007 ). Physical security is a necessary condition for human security but not sufficient if civil society fails to allow its members to thrive. To thrive, individuals must maintain tolerance and social discourse. By inducing stress and anxiety, cyber terrorism endangers psychological wellbeing and increases perceptions of threat even if individuals suffer no physical harm. Once cyber terrorism successfully breaches a critical infrastructure to kill and injure (as in our film clips), these effects are more pronounced. Threat perception is not all bad. Reasonable perceptions of threat are essential to protect individuals and their communities from dangerous surprises but become disabling when they foster insecurity and prompt visions of an inescapable cycle of violence ( Canetti-Nisim et al. 2009 ). It is the nature of cyber terrorism to target civilians ( Gross 2015 , 153–183). Some of this is mere efficiency: Civilian targets are softer than military targets or critical infrastructures, which states take great pains to protect. But part is strategic: Targeting civilians is a way to demoralize and terrorize. This is precisely what Anonymous, Hamas, and Islamic State promise to do.
In response, civilians are increasingly willing to jettison privacy and support military retaliation. Neither outcome bodes well for human security. Privacy embraces the right to keep secrets and preserves a domain for individuals to build their personal identities and communicate without interference or duress. Surveillance inhibits free speech, discourages political opposition, prevents dissenters from organizing or publishing anonymously, and disrupts the flow of information necessary for a well-functioning civil society. Surveillance threatens privacy but not without cause. Surveillance can strengthen physical security. Gaining access to the content of e-mails and social media may allow law enforcement authorities and intelligence agencies to co-opt and cripple hostile organizations. Physical security is as important for human security as privacy. Balancing the two will be exceptionally challenging in the shadow of cyber terrorism, and cyber security experts and policy makers cannot unilaterally fortify the former at the expense of the latter.
Political militancy is equally problematic. Facing cyber terrorism and the threat it poses to national and human security, governments consider a range of tempered policies that include criminal prosecution, counter espionage, and active cyber defenses. Because most offensive cyber attacks fall far short of war, each of these retaliatory responses is freighted with fears of escalation that the United States and other nations wish to avoid. Nations must be careful as they weigh their responses to hostile cyber operations ( Hathaway et al. 2012 ). Civilians, particularly those who already find themselves in the midst of an armed conflict, are less restrained and may push their governments in unwarranted and dangerous directions as they call for harsh military retaliation following cyber attacks. Human security does not demand pacifism but it thrives best in a society that is cautious about the use of armed force. Cyber terrorism, like conventional terrorism, upends judicious decision making.
Eliminating the toxic effects of cyber terrorism is not simply a matter of cyber security. It is not enough to thwart or reduce the incidence of cyber-terror attacks. Protecting facilities is only half the battle. Fear, insecurity, anxiety, and militancy are often the product of perceived, not actual, threats. Cyber terrorists lurk in the background, and individuals will not be mollified unless they are eliminated. Despite their best efforts, however, no government will ever eradicate cyber terrorism, and people will always be driven by their outsized fears. Mitigating these fears is as equally important as reducing the incidence of attack. But the means are entirely different. Perceptions depend crucially on information and, as a result, risk assessment and communication are of crucial importance is the war against cyber terrorism. Individuals who misunderstand the nature of cyber terrorism and the threat it poses are most likely inclined to greater fear, insecurity, and militancy than those whose assessment is sober. Experts, to be sure, remain divided over the risk of cyber terrorism. Nevertheless, the cyber security community must address the fears of everyday citizens by cogently assessing the danger of cyber terrorism and the protective measures necessary to maintain secure networks. Risk communication is sorely lacking; properly implemented, it can reduce insecurity and perceptions of threat. Finally, there is also room to think about psychological intervention and cognitive behavior therapy to treat cyber terrorism–induced anxieties, just as it is used to treat the effects of conventional terrorism. 2 Risk assessment and psychological treatment protocols address the human dimension of cyber terrorism and should not be neglected as nations work to fend off cyber terrorists of all stripes.
Cyber terrorism has many faces, as does the psychology of the masses. Our research demonstrates how even non-lethal, seemingly banal forms of cyber terrorism have a considerable impact on the attitudes of victimized populations. Our experiments show a “cyber terrorism effect” that enables terrorists to foster fears akin to kinetic terrorism and pursue similarly ideological goals. In this way, cyber terrorism pushes well beyond cyber crime even when its methods—identity theft, destruction of data, and disruption of service—are sometimes similar. When Anonymous threatens an electronic Holocaust by corrupting data or stealing identities, they are taking sides in violent, armed conflict, and their actions are far more than criminal. They are attacking innocent civilians, not bilking an easy mark. Victims know the difference. Under attack, they react with not only fear and trepidation, as do victims of crime, but with demands for protection from the enemies of the state via harsh military retaliation, surveillance, and strong government. This is the psychology of terrorism.
Acknowledgments
This research was made possible, in part, by grants awarded to Daphna Canetti from the US National Institute of Mental Health (R01 MH073687), from the Israel Science Foundation (594/15), and from the US-Israel Binational Science Foundation (2009460), and to Michael L. Gross from the Israel Science Foundation (156/13).
Biographies
Michael L. Gross is a professor in and the head of the School of Political Science at the University of Haifa, Israel. His recent books include The Ethics of Insurgency (Cambridge 2015) and Moral Dilemmas of Modern War (Cambridge 2010).
Daphna Canetti is a professor of political science at the University of Haifa and the director of the university’s graduate program in Democracy Studies. Canetti’s research examines the psychological challenges and policy implications of terrorism, warfare, and political violence. Her publications appear in political and psychological outlets including the Lancet , the American Journal of Political Science , the British Journal of Political Science , and Political Psychology . Her commentary has been featured in media outlets including NPR and the Washington Post .
Dana Vashdi is the head of the Division of Public Administration and Policy at the University of Haifa, Israel. Her research focuses on the well-being of citizens in general and of employees in particular as well as on teams in public organizations, organizational learning, and healthcare policy. She has published articles in a wide variety of academic journals including the Academy of Management Journal , the British Medical Journal, Human Resource Management , and Public Administration Review .
1 “Reading” and “monitoring” are different. “Monitoring” suggests either the collection of metadata or only reading e-mails that trigger security concerns, while “reading” suggest scrutinizing every e-mail.
2 For example, see Somer et al. 2005 .
Disclosure statement
No potential conflict of interest was reported by the authors.
- Boggs C. Militarism and Terrorism: The Deadly Cycle. Democracy & Nature. 2002; 8 (2):241–259. [ Google Scholar ]
- Canetti-Nisim D, Halperin E, Sharvit K, Hobfoll SE. A New Stress-Based Model of Political Extremism Personal Exposure to Terrorism, Psychological Distress, and Exclusionist Political Attitudes. Journal of Conflict Resolution. 2009; 53 (3):363–389. [ PMC free article ] [ PubMed ] [ Google Scholar ]
- Canetti D, Hall BJ, Rapaport C, Wayne C. Exposure to political violence and political extremism: A stress-based process. European Psychologist. 2013; 18 (4):263. [ Google Scholar ]
- Gross M. The Ethics of Insurgency: A Critical Guide to Just Guerrilla Warfare. Cambridge: Cambridge University Press; 2015. [ Google Scholar ]
- Hathaway OA, Crootof R, Levitz P, Nix H, Nowlan A, Perdue W, Spiegel J. The Law of Cyber-Attack. California Law Review. 2012; 100 (4):817–885. [ Google Scholar ]
- Hirsch-Hoefler S, Canetti D, Rapaport C, Hobfoll SE. Conflict will harden your heart: Exposure to violence, psychological distress and peace barriers in Israel and Palestine. British Journal of Political Science. 2014:1–15. [ Google Scholar ]
- Jenkins BM. Will terrorists go nuclear? Santa Monica, CA: The RAND Corporation; 1975. (P-5541 in the RAND Paper Series) [ Google Scholar ]
- Lerner JS, Gonzalez RM, Small DA, Fischhoff B. Effects of fear and anger on perceived risks of terrorism: A national field experiment. Psychological Science. 2003; 14 (2):144–150. [ PubMed ] [ Google Scholar ]
- Lewis JA. Assessing the Risks of Cyber Terrorism, Cyber War and Other Cyber Threats. Center for Strategic and International Studies. 2002 Dec [ Google Scholar ]
- Libicki MC. Cyberspace in Peace and War. Chap. 32. Annapolis, MD: Naval Institute Press; 2014. From the Tallinn Manual to Las Vegas rules. 2016 (forthcoming) [ Google Scholar ]
- McDermott R. Proceedings of a Workshop Deterring Cyberattacks: Informing Strategies and Developing Options for U.S. Policy, National Research Council. Washington, DC: The National Academies Press; 2010. Decision Making under Uncertainty; pp. 227–241. [ Google Scholar ]
- Polityuk P. Ukraine Sees Russian Hand in Cyber Attacks on Power Grid. Reuters. 2016 Feb 12; http://www.reuters.com/article/us-ukraine-cybersecurity-idUSKCN0VL18E . [ Google Scholar ]
- Schmitt MN, editor. Tallinn Manual on the International Law Applicable to Cyber Warfare. Cambridge: Cambridge University Press; 2013. [ Google Scholar ]
- Somer E, Tamir E, Maguen S, Litz BT. Brief cognitive behavioral phone-based intervention targeting anxiety about the threat of an attack: A pilot study. Behaviour Research and Therapy. 2005; 43 (5):669–679. [ PubMed ] [ Google Scholar ]
- Shelton M, Rainie L, Madden M. Americans’ Privacy Strategies Post-Snowden. Pew Research Center. 2015 Mar 15; http://www.pewinternet.org/files/2015/03/PI_AmericansPrivacyStrategies_0316151.pdf . [ Google Scholar ]
- Rogers A. What Anonymous is Doing in Ferguson. Time. 2014 Aug 21; http://time.com/3148925/ferguson-michael-brown-anonymous/ [ Google Scholar ]
- Tadjbakhsh S. Human security twenty years on. Norwegian Peacebuilding Resource Centre (NOREF) 2014 Jun; http://www.peacebuilding.no/var/ezflow_site/storage/original/application/540cb240aa84ac7133bce008adcde01f.pdf . [ Google Scholar ]
- Tadjbakhsh S, Chanoy AM. Human Security: Concepts and Implications. Abingdon, UK: Routledge; 2007. [ Google Scholar ]
- Verton D, Brownlow J, editors. Black Ice: The Invisible Threat of Cyber-Terrorism. Emeryville, CA: McGraw-Hill/Osborne; 2003. [ Google Scholar ]
IEEE Account
- Change Username/Password
- Update Address
Purchase Details
- Payment Options
- Order History
- View Purchased Documents
Profile Information
- Communications Preferences
- Profession and Education
- Technical Interests
- US & Canada: +1 800 678 4333
- Worldwide: +1 732 981 0060
- Contact & Support
- About IEEE Xplore
- Accessibility
- Terms of Use
- Nondiscrimination Policy
- Privacy & Opting Out of Cookies
A not-for-profit organization, IEEE is the world's largest technical professional organization dedicated to advancing technology for the benefit of humanity. © Copyright 2024 IEEE - All rights reserved. Use of this web site signifies your agreement to the terms and conditions.
CYBER-ATTACKS AND CYBER -TERRORISM: A WEAPON AND LATEST THREAT TO INTERNATIONAL PEACE AND SECURITY.
- Thesis for: Bachelor of Laws
- Advisor: Hafiza Amna Sadia

- University of Minho
- This person is not on ResearchGate, or hasn't claimed this research yet.
Discover the world's research
- 25+ million members
- 160+ million publication pages
- 2.3+ billion citations

- Marc Weller
- Randall Lesaffer
- Daniele Archibugi
- Paolo Palchetti

- N Tsagourias
- Recruit researchers
- Join for free
- Login Email Tip: Most researchers use their institutional email address as their ResearchGate login Password Forgot password? Keep me logged in Log in or Continue with Google Welcome back! Please log in. Email · Hint Tip: Most researchers use their institutional email address as their ResearchGate login Password Forgot password? Keep me logged in Log in or Continue with Google No account? Sign up
From cybercrime to terrorism, FBI director says America faces many elevated threats 'all at once'
The head of the FBI says America is facing heightened threats from many corners at a time when law enforcement agencies are struggling
BROOKLYN CENTER, Minn. -- The country is facing heightened threats from many corners at a time when law enforcement agencies are struggling, FBI Director Christopher Wray said in an exclusive interview, adding that he is “hard pressed to think of a time in my career where so many different kinds of threats are all elevated at once.”
Wray spoke Wednesday with The Associated Press while visiting the Minneapolis field office to talk about partnerships between law enforcement agencies and also with other entities. His remarks come as the FBI confronts heightened concerns over terrorism, both domestic and international, as well as Chinese espionage and intellectual property theft and foreign election interference.
“I worry about the combination of that many threats being elevated at once, with the challenges facing the men and women in law enforcement more generally,” Wray said at the office in the suburb of Brooklyn Center. “And the one thing that I think helps bridge those two challenges is partnerships. That’s how we get through. It is by all working together.”
Wray’s assessment of an elevated threat landscape is consistent with alarm bells he has sounded for months. Soon after the Oct. 7 attack by Hamas in Israel, Wray began warning that the rampage could serve as an inspiration to militants, “the likes of which we haven’t seen since ISIS launched its so-called caliphate years ago.”
The FBI has also scrambled to deal with security concerns related to the United States' southern border, with officials revealing in June that eight people from Tajikistan with suspected ties to the Islamic State group were arrested and were being held on immigration violations.
Officials are also dealing with the specter of foreign election interference. The FBI and other federal agencies announced Monday that Iran was responsible for a hack targeting the Trump campaign and for an attempted breach of the Biden-Harris campaign, part of what officials portrayed as a brazen and aggressive effort to interfere in American politics.
Wray declined to talk about any specific investigation or threat but said investigations into cyberattacks, including against election infrastructure, candidates or campaigns, require help from the private sector.
“One of the things that we have been doubling down on with every passing day is, is on partnerships, because ultimately you’re talking about the ability to connect the dots, whether it’s against some kind of election influence threat or some other kind of threat,” Wray said. “You need to have partners sharing information with each other to put the two pieces together to see the bigger picture.”
Law enforcement officers are being killed in the line of duty at a rate of about one every five days, Wray said, noting that four first responders have died in Minnesota alone in 2024. They include a Minneapolis officer killed in May while trying to help someone, and two officers and a paramedic who died in Burnsville in February when a heavily armed man opened fire.
Such violence “breaks my heart every single time,” the director said.
The FBI has not been spared such attacks: Days after agents searched Donald Trump’s Florida estate, Mar-a-Lago, to recover classified documents, a gunman who called on social media for federal agents to be killed “on sight” died in a shootout after trying to get inside the FBI’s Cincinnati office.
Wray said the FBI has been working to beef up traditional partnerships with state and local law enforcement, while also creating other ones with business and academia to help counter threats against cybersecurity or intellectual property. In Minneapolis and other offices, he said, authorities are cooperating with the likes of school resource officers and mental health professionals to help at-risk teenagers in hopes of heading off future threats.
Working with industry is important for protecting innovation and artificial intelligence from foreign threats, Wray added.
“AI is in many ways the most effective tool against the bad guys' use of AI,” he said. “So we need to work closely with industry to try to help make sure that American AI can be used to help protect American people from AI-enabled threats coming the other way.”
Associated Press writer Eric Tucker in Washington contributed to this report.
Trending Reader Picks

PBS' Judy Woodruff apologizes for an on-air remark about peace talks in Israel
- Aug 21, 9:37 PM

Remains found confirmed to be from missing woman
- Aug 21, 7:45 PM

US government indicts Guatemalan national on smuggling charges over deaths of 53 migrants in trailer
- Aug 22, 12:03 AM

FAA sent 43 cases of unruly passengers to FBI
- Aug 21, 11:48 AM

Mexico to bring charges against capo, not for drugs, but for turning over another drug lord to US
- Aug 21, 11:16 PM
ABC News Live
24/7 coverage of breaking news and live events
- Election 2024
- Entertainment
- Newsletters
- Photography
- AP Buyline Personal Finance
- AP Buyline Shopping
- Press Releases
- Israel-Hamas War
- Russia-Ukraine War
- Global elections
- Asia Pacific
- Latin America
- Middle East
- Delegate Tracker
- AP & Elections
- 2024 Paris Olympic Games
- Auto Racing
- Movie reviews
- Book reviews
- Financial Markets
- Business Highlights
- Financial wellness
- Artificial Intelligence
- Social Media
From cybercrime to terrorism, FBI director says America faces many elevated threats ‘all at once’
FBI Director Christopher Wray answers questions during an interview, Wednesday, Aug. 21, 2024, in Brooklyn Center, Minn. (AP Photo/Abbie Parr)
- Copy Link copied

BROOKLYN CENTER, Minn. (AP) — The country is facing heightened threats from many corners at a time when law enforcement agencies are struggling, FBI Director Christopher Wray said in an exclusive interview, adding that he is “hard pressed to think of a time in my career where so many different kinds of threats are all elevated at once.”
Wray spoke Wednesday with The Associated Press while visiting the Minneapolis field office to talk about partnerships between law enforcement agencies and also with other entities. His remarks come as the FBI confronts heightened concerns over terrorism, both domestic and international, as well as Chinese espionage and intellectual property theft and foreign election interference.
“I worry about the combination of that many threats being elevated at once, with the challenges facing the men and women in law enforcement more generally,” Wray said at the office in the suburb of Brooklyn Center. “And the one thing that I think helps bridge those two challenges is partnerships. That’s how we get through. It is by all working together.”
Wray’s assessment of an elevated threat landscape is consistent with alarm bells he has sounded for months. Soon after the Oct. 7 attack by Hamas in Israel, Wray began warning that the rampage could serve as an inspiration to militants, “the likes of which we haven’t seen since ISIS launched its so-called caliphate years ago.”
The FBI has also scrambled to deal with security concerns related to the United States’ southern border, with officials revealing in June that eight people from Tajikistan with suspected ties to the Islamic State group were arrested and were being held on immigration violations.
Officials are also dealing with the specter of foreign election interference. The FBI and other federal agencies announced Monday that Iran was responsible for a hack targeting the Trump campaign and for an attempted breach of the Biden-Harris campaign, part of what officials portrayed as a brazen and aggressive effort to interfere in American politics.
Wray declined to talk about any specific investigation or threat but said investigations into cyberattacks, including against election infrastructure, candidates or campaigns, require help from the private sector.
“One of the things that we have been doubling down on with every passing day is, is on partnerships, because ultimately you’re talking about the ability to connect the dots, whether it’s against some kind of election influence threat or some other kind of threat,” Wray said. “You need to have partners sharing information with each other to put the two pieces together to see the bigger picture.”
Law enforcement officers are being killed in the line of duty at a rate of about one every five days, Wray said, noting that four first responders have died in Minnesota alone in 2024. They include a Minneapolis officer killed in May while trying to help someone, and two officers and a paramedic who died in Burnsville in February when a heavily armed man opened fire.
Such violence “breaks my heart every single time,” the director said.
The FBI has not been spared such attacks: Days after agents searched Donald Trump’s Florida estate, Mar-a-Lago, to recover classified documents, a gunman who called on social media for federal agents to be killed “on sight” died in a shootout after trying to get inside the FBI’s Cincinnati office.
Wray said the FBI has been working to beef up traditional partnerships with state and local law enforcement, while also creating other ones with business and academia to help counter threats against cybersecurity or intellectual property. In Minneapolis and other offices, he said, authorities are cooperating with the likes of school resource officers and mental health professionals to help at-risk teenagers in hopes of heading off future threats.
Working with industry is important for protecting innovation and artificial intelligence from foreign threats, Wray added.
“AI is in many ways the most effective tool against the bad guys’ use of AI,” he said. “So we need to work closely with industry to try to help make sure that American AI can be used to help protect American people from AI-enabled threats coming the other way.”
Associated Press writer Eric Tucker in Washington contributed to this report.

Read The Diplomat , Know The Asia-Pacific
- Central Asia
- Southeast Asia
- Environment
- Asia Defense
- China Power
- Crossroads Asia
- Flashpoints
- Pacific Money
- Tokyo Report
- Trans-Pacific View
Photo Essays
- Write for Us
- Subscriptions
Pakistan Authorities Charge Man With Cyber Terrorism Over Misinformation That Sparked Riots in UK
Recent features.

Trump 2.0 Would Get Mixed Responses in the Indo-Pacific

Why Thaksin Could Help Hasten a Middle-Class Revolution in Thailand

Can the Bangladesh Police Recover?

The Lingering Economic Consequences of Sri Lanka’s Civil War

What’s Driving Lithuania’s Challenge to China?

Hun Manet: In His Father’s Long Shadow

Afghanistan: A Nation Deprived, a Future Denied

In Photos: Life of IDPs in Myanmar’s Rakhine State

Indian Government’s Intensifying Attack on Scientific Temperament Worries Scientists

Beyond Tariffs: Unveiling the Geopolitics of Electric Vehicles Through Supply Chains

In Photos: Bangladesh After Hasina Fled

First Known Survivor of China’s Forced Organ Harvesting Speaks Out
The pulse | society | south asia.
A Pakistan web developer is accused of spreading misinformation about the British suspect in a stabbing attack, leading to anti-Muslim and anti-migrant violence in the U.K.

A van on fire during riots in Southport, the U.K., July 30, 2024.
Authorities in Pakistan on Wednesday arrested and charged a man with cyber terrorism for his alleged role in spreading misinformation that led to widespread rioting in the United Kingdom earlier this month.
The suspect was identified as freelance web developer Farhan Asif, 32, said Imran Kishwar, deputy inspector general of investigations in Lahore, the capital of eastern Punjab province.
The man is accused of spreading misinformation from YouTube and Facebook about the British teenage suspect in a stabbing attack that killed three girls and injured 10 other people July 29 at a dance class in Northwest England.
The false information claimed that the suspect was a recently arrived asylum-seeker and had a name that suggested he was Muslim.
After the misinformation led to a violent mob attacking a mosque near the site of the stabbing the next day, police took the unusual step of clarifying that the suspect was born in the U.K. It’s been widely reported in British media that his parents are from Rwanda and said to have Christian beliefs.
Channel3 Now, an account on the X social media platform that purports to be a news channel, was one of the first outlets to report the false name, Ali Al-Shakati. A Facebook account for the channel said it is managed by people in Pakistan and the U.S.
The site’s editor-in-chief posted an apology July 31 for “the misleading information published in a recent article on our website, Channel3 NOW. We deeply regret any confusion or inconvenience this may have caused.”
But the false reports were widely disseminated and are blamed for fueling more than a week of rioting that broke out across the United Kingdom and has led to more than 1,000 arrests.
Authorities have blamed far-right agitators for stoking the violent unrest by continuing to spread misinformation and promoting the violent demonstrations online.
At a news conference in the eastern city of Lahore, the police official Kishwar said Asif was arrested at his house in the city for questioning.
He said Asif has claimed that he was not the source of the misinformation but that he reposted it from social media. Kishwar said Asif ran the Channel3 Now account, and alleged that he spread fake news to gain more viewers and income.
“He regretted over reposting fake news,” Kishwar told The Associated Press. “This act on the part of Asif amounts to cyber terrorism, for which he has been charged.”
Kishwar added that Asif’s arrest was a message for other YouTubers that they should verify facts before disseminating any information.
Police have handed over the case to the Federal Investigation Agency or FIA, which handles cases relating to cyber terrorism. FIA said the misinformation shared by Asif “created a sense of fear, insecurity” in England, and added that it also harmed Pakistan’s reputation.
It was unclear if Britain had requested his extradition. There is no extradition treaty between Pakistan and the U.K.
Federal investigators were granted permission by a court Wednesday to further question Asif for a day. Asif is expected to appear before a court again on Thursday when investigators are expected to seek more time to quiz him.

Activists in Balochistan Face a New Threat: Cyber Harassment
By arbaz shah.

Pakistan’s Government and Military Are Crushing Dissent on Social Media
By abdul rehman.

Pakistan’s Attempt to Tamper With the Internet Is Leading to Economic Turmoil
By manik aftab.

Pakistan Suffers Internet Slowdown as Government Denies Setting up a National Firewall
By babar dogar.

By Rajeev Bhattacharyya

Bangladesh’s New Democracy Under Threat From Flood of Misinformation
By farhana sultana.

An Aggressive China Is Pushing the Philippines and Vietnam Closer Than Ever
By vincent kyle parada.

Nuclear Shadows Over South Asia: Strategic Instabilities in the China-India-Pakistan Triad
By shawn rostker.

By Derek Grossman

By Jason Johnson

By Mehedi Hasan Marof and Saqlain Rizve

By Devana Senanayake
Pakistan authorities charge man with cyberterrorism over misinformation that sparked riots in U.K.

- Copy Link URL Copied!
Authorities in Pakistan on Wednesday arrested and charged a man with cyberterrorism for his alleged role in spreading misinformation that led to widespread rioting in the U.K. earlier this month.
The suspect was identified as freelance web developer Farhan Asif, 32, said Imran Kishwar, deputy inspector general of investigations in Lahore, the capital of eastern Punjab province.
The man is accused of spreading misinformation from YouTube and Facebook about the British teenage suspect in a stabbing attack that killed three girls and injured 10 other people July 29 at a dance class in North West England.
The false information claimed that the suspect was a recently arrived asylum-seeker and had a name that suggested he was Muslim.

World & Nation
U.K. police brace for more far-right violence as government warns of tough response
Suspects arrested in violent protests after the fatal stabbing of three children in northwest England appeared in court as officials braced for more clashes.
Aug. 2, 2024
After the misinformation led to a violent mob attacking a mosque near the site of the stabbing the next day, police took the unusual step of clarifying that the suspect was born in the U.K. It’s been widely reported in British media that his parents are from Rwanda and said to have Christian beliefs.
Channel3 Now, an account on the X social media platform that purports to be a news channel, was one of the first outlets to report the false name, Ali Al-Shakati. A Facebook account for the channel said it is managed by people in Pakistan and the U.S.
The site’s editor in chief posted an apology July 31 for “the misleading information published in a recent article on our website, Channel3 NOW. We deeply regret any confusion or inconvenience this may have caused.”
But the false reports were widely disseminated and are blamed for fueling more than a week of rioting that broke out across the United Kingdom and has led to more than 1,000 arrests.
Authorities have blamed far-right agitators for stoking the violent unrest by continuing to spread misinformation and promoting the violent demonstrations online.
At a news conference in the eastern city of Lahore, the police official Kishwar said Asif was arrested at his house in the city for questioning.

U.K. prime minister condemns attack on asylum-seeker hotel as far-right violence spreads
U.K. Prime Minister Keir Starmer condemned an attack on a hotel housing asylum seekers in north England, describing it as ‘far-right thuggery.’
Aug. 4, 2024
He said Asif has claimed that he was not the source of the misinformation but that he reposted it from social media. Kishwar said Asif ran the Channel3 Now account, and alleged that he spread fake news to gain more viewers and income.
“He regretted over reposting fake news,” Kishwar told the Associated Press. “This act on the part of Asif amounts to cyberterrorism for which he has been charged.”
Kishwar added that Asif’s arrest was a message for other YouTubers that they should verify facts before disseminating any information.
Police have handed over the case to the Federal Investigation Agency, or FIA, which handles cases relating to cyberterrorism. FIA said the misinformation shared by Asif “created a sense of fear, insecurity” in England, and added that it also harmed Pakistan’s reputation.
It was unclear if Britain had requested his extradition. There is no extradition treaty between Pakistan and the U.K.
Federal investigators were granted permission by a court Wednesday to further question Asif for a day. Asif is expected to appear before a court again Thursday when investigators are expected to seek more time to quiz him.
Dogar and Melley write for the Associated Press. Melley reported from London.
More to Read

Man stabs a girl and her mother in a London tourism hot spot before being arrested, police say
Aug. 12, 2024
Third person in custody after foiled plot targeting Taylor Swift shows in Vienna
Aug. 9, 2024

British prime minister announces police unit to deal with violent clashes after fatal stabbings
Aug. 1, 2024
Sign up for Essential California
The most important California stories and recommendations in your inbox every morning.
You may occasionally receive promotional content from the Los Angeles Times.
More From the Los Angeles Times

Body of British tech magnate Mike Lynch is among those recovered from yacht wreckage, officials say

Drug cartels’ turf war in Mexico’s Chiapas state sends villagers fleeing to Guatemala
Aug. 22, 2024

Tim Walz was a staunch LGBTQ+ ally, long before it was common

Entertainment & Arts
Hell hath no fury like a librarian scorned in the book banning wars

IMAGES
COMMENTS
Cyber terrorism is an elusive concept. Most definitions make a distinction between on the one hand politically motivated violent acts, or the threat thereof, using the internet, and on the other hand all the preparatory and supporting activities for terrorism done on or via the internet, such as recruitment, communication and financing.
Although cyber-terrorism may arise in the future, online crime, hacktivism, and cyber-warfare pose more immediate threats (Kenney, 2015). A striking feature of our understanding of cybercrime is the variety of terms used to describe it. Despite the wide range of terminology used, there is one common thread that stands out.
The risk of a cyber terrorism attack should therefore not be understated as an emerging threat, and consequently, preventative and response capabilities should be maintained and advanced. Contemporary society, in short, is coming to realise that violent extremism, albeit relatively rare, is the 'new normal'.
Our findings demonstrate a stress-based 'cyber terrorism effect'. Exposure to cyberterrorism is not benign and shares many traits with conventional terrorism: stress, anxiety, insecurity, a preference for security over liberty, a reevaluation of confidence in public institutions, a heightened perception of risk and support for forceful ...
This brings to the forefront a relatively new concept in the area of terrorism: cyberterrorism. This paper will look at the idea of cyberterrorism and analyze the preparedness of 12 North Carolina ...
Abstract. In the recent years, an alarming rise in the incidence of cyber attacks has made cyber security a major concern for nations across the globe. Given the current volatile socio-political environment and the massive increase in the incidence of terrorism, it is imperative that government agencies rapidly realize the possibility of cyber ...
Overview of Research. For almost up to 2 decades, the search for defining cyber terrorism has been described as the 'Holy Grail' for scholars and policy makers [].This has been escalated during the recent COVID pandemic where life has made a remarkable shift towards online activity, placing individuals at a much higher risk of being vulnerable to cyber terrorist activities [].
This paper examines the critical issues relevant to Cyber terrorism. A review of the literature indicates that incidences of computer crime and cyber terrorism are increasing. The cyber attacks on the U.S.'s critical infrastructure are no longer random, but rather are coordinated and precise. The types of attacks are discussed
However, the increase in cyber terrorism cases has increased the research interest in the domain. Researchers are focusing on improving the security of internet and IoT devices. The field is still in its infancy. A lot needs to be done to mitigate these attacks. Motivated to demystify the repercussions of the cyber terrorism, this paper ...
Abstract. This chapter discusses the threat of terrorism in cyberspace and examines the truth of the perceptions of this threat that have formed in recent years. It examines the capabilities that a non-state actor can achieve and whether this can constitute a real threat to the national security of states. For an analysis of the main threats ...
In addition, five scenarios can be considered for cyber warfare: (1) Government-sponsored cyber espionage to gather information to plan future cyber-attacks, (2) a cyber-attack aimed at laying the groundwork for any unrest and popular uprising, (3) Cyber-attack aimed at disabling equipment and facilitating physical aggression, (4) Cyber-attack as a complement to physical aggression, and (5 ...
Criminals, terrorists, and spies rely heavily on cyber-based technologies to support organizational objectives. Commonly recognized cyber-aggressors and representative examples of the harm they can inflict include the following: Cyberterrorists are state-sponsored and non-state actors who engage in cyberattacks to pursue their objectives.
Overall, the study narrowly defined cyber terrorism as "the unlawful destruction or disruption of digital property to intimidate or coerce governments or societies in the pursuit of goals that are political, religious or ideological." 3 For a study compiled in 1999, this was a well-rounded framework.
and legislative theories of counter-terrorism and cyberterrorism regulation.Based on the analysis of this thesis, the main weaknesses of the current international framework are the lack of a general definition of terrorism in both treaty and customary law and the politically sensitive issue of whether to include in the normative instruments the ...
an issue and a challenge in countering cyber-terrorism threats. To better understand why cyber terrorism acts are committed, this study examines cyber terrorism from motivational perspectives. Motivational forces behind cyber terrorism can be social, political, ideological, and economic. In this research, data analysed using a qualitative method.
Abstract. This article reports on a recent survey designed to capture understandings of cyberterrorism across the global research community. Specifically, it explores competing views, and the importance thereof, amongst 118 respondents on three definitional issues: (a) the need for a specific definition of cyberterrorism for either policymakers or researchers; (b) the core characteristics or ...
Hussein would not hesitate to use the cyber tool he has. . . . It is not a question of if but when. The entire United States is the front line," Alexander claimed. (See Ralf Bendrath's article "The American Cyber-Angst and the Real World," published in 2003 in Bombs and Bandwith, edited by Robert Latham.) Whatever the intentions of its ...
32 Countering Terrorism Online with Artificial Intelligence (New York: United Nations Office of Counter-Terrorism, United Nations ... started to trigger security warnings, which was not the case in March. However, no major differences when it comes to cyber security instructions or methods of avoiding detection from law enforcement agencies ...
The effects can have a chilling effect on civil society and political discourse in many democratic nations, as debates about torture, rendition, due process, military belligerency, and surveillance show. We were not surprised to see similar effects from cyber terrorism. Go to: Political reactions. Figures 3 and.
Cyber terrorism is a growing concern around the globe. The role of AI in countering cyber terrorism is another concern and challenge for national security agencies around the globe. This research explores the role of artificial intelligence in combating cyber terrorism and its potential advantages. In order to identify, prevent and respond to cyberattacks, the role of AI is explored in this ...
In this research paper we have discussed about the phenomenon of Cyber terrorism and its growing impact in the current scenario. We have reviewed the laws and acts in various countries like US, UK, Canada, Australia and in India. We have also tried to review the Cyber terrorism from the aspect of the Indian IT Act 2000. We have carried out a comparative review of the various laws made by these ...
The proposed research of this thesis will highlight what constitutes a cyber-attack and cyber-terrorism. It will further determine cyber-attacks and cyber-terrorism as armed attacks and a threat ...
to a long-term goal. With cyber-terrorism, the intent is generally to influence the behaviors and. decisions of a population and/or government toward a political, social, religious, or ideological. agenda. In contrast, the intent of cyber-crime is personal gain or gratification. Lastly, both.
From cybercrime to terrorism, FBI director says America faces many elevated threats 'all at once' The head of the FBI says America is facing heightened threats from many corners at a time when law ...
Authorities in Pakistan on Wednesday arrested and charged a man with cyber terrorism for his alleged role in spreading misinformation that led to widespread rioting in the U.K. earlier this month.
LAHORE, Pakistan (AP) — Authorities in Pakistan on Wednesday arrested and charged a man with cyber terrorism for his alleged role in spreading misinformation that led to widespread rioting in the U.K. earlier this month.. The suspect was identified as freelance web developer Farhan Asif, 32, said Imran Kishwar, deputy inspector general of investigations in Lahore, the capital of eastern ...
Such violence "breaks my heart every single time," the director said. The FBI has not been spared such attacks: Days after agents searched Donald Trump's Florida estate, Mar-a-Lago, to recover classified documents, a gunman who called on social media for federal agents to be killed "on sight" died in a shootout after trying to get inside the FBI's Cincinnati office.
Subscribe for ads-free reading. Authorities in Pakistan on Wednesday arrested and charged a man with cyber terrorism for his alleged role in spreading misinformation that led to widespread rioting ...
Authorities in Pakistan have arrested and charged a man with cyber terrorism for his alleged role in spreading misinformation that led to widespread rioting in the U.K. earlier this month
Wed 21 Aug 10.34pm • Pakistani police say money was the main motive of a man charged with cyberterrorism after he allegedly spread disinformation related to the Southport attack.