Virtual Private Network’s Impact on Network Performance
Ieee account.
- Change Username/Password
- Update Address

Purchase Details
- Payment Options
- Order History
- View Purchased Documents
Profile Information
- Communications Preferences
- Profession and Education
- Technical Interests
- US & Canada: +1 800 678 4333
- Worldwide: +1 732 981 0060
- Contact & Support
- About IEEE Xplore
- Accessibility
- Terms of Use
- Nondiscrimination Policy
- Privacy & Opting Out of Cookies
A not-for-profit organization, IEEE is the world's largest technical professional organization dedicated to advancing technology for the benefit of humanity. © Copyright 2024 IEEE - All rights reserved. Use of this web site signifies your agreement to the terms and conditions.
Secured Communication Using Virtual Private Network (VPN)
- Conference paper
- First Online: 02 October 2021
- Cite this conference paper

- Paul Joan Ezra 5 ,
- Sanjay Misra 5 ,
- Akshat Agrawal 6 ,
- Jonathan Oluranti 5 ,
- Rytis Maskeliunas 7 &
- Robertas Damasevicius 7
Part of the book series: Lecture Notes on Data Engineering and Communications Technologies ((LNDECT,volume 73))
2692 Accesses
11 Citations
The evolution and era of the latest programs and services, collectively with the enlargement of encrypted communications, make it difficult for site visitors within a safety enterprise. Virtual private networks (VPNs) are an instance of encrypted communique provider that is becoming famous, as a way for bypassing censorship in addition to gaining access to offerings which are geographically locked. This paper reviews the layout of an IP security, VPN. The Cisco Packet lines platform is used for the simulation, evaluation and verification. It uses a virtual connection to carry the records packets from a non-public network to remote places.
- Virtual private network
- Authentication
- Confidentiality
This is a preview of subscription content, log in via an institution to check access.
Access this chapter
- Available as PDF
- Read on any device
- Instant download
- Own it forever
- Available as EPUB and PDF
- Compact, lightweight edition
- Dispatched in 3 to 5 business days
- Free shipping worldwide - see info
Tax calculation will be finalised at checkout
Purchases are for personal use only
Institutional subscriptions
Odusami, M., Misra, S., Adetiba, E., Abayomi-Alli, O., Damasevicius, R., Ahuja, R.: An improved model for alleviating layer seven distributed denial of service intrusion on webserver. J. Phys.: Conf. Ser. 1235 (1), 012020 (2019)
Google Scholar
Odusami, M., Misra, S., Abayomi‐Alli, O., Abayomi‐Alli, A., Fernandez‐Sanz, L.:. A survey and meta‐analysis of application‐layer distributed denial‐of‐service attack. Int. J. Commun. Syst. 33 (18), e4603 (2020)
Draper-gil, G., Lashkari, A.H., Saiful, M., Mamun, I., Ghorbani, A.A.: Characterization of encrypted and VPN traffic using time-related features. In: Proceedings of the 2nd International Conference on Information Systems Security And Privacy (ICISSP), pp. 407–414, 2016
Busschbach, P.B.: ♦ Toward QoS-capable virtual private networks. Bell Labs Tech. J. 3 (4), 161–175 (1998)
Article Google Scholar
Deshmukh, D., Iyer, B.: Design of IPSec virtual private network for remote access. In: 2017 International Conference on Computing, Communication and Automation (ICCCA), pp. 716–719. IEEE, 2017
Nawej, M.C., Technologiae, M.: Evaluation of virtual private network impact on network performance (2016)
Liyanage, M., Gurtov, A.: Secured VPN models for LTE backhaul networks. In: 2012 IEEE Vehicular Technology Conference (VTC Fall), Sept 2015, pp. 1–5. IEEE
Jaha, A.A., Ben Shatwan, F., Ashibani, M.: Proper virtual private network (VPN) solution. In: Proceedings of 2nd International Conference on Next Generation Mobile Applications, Services, and Technologies, NGMAST 2008, pp. 309–314, 2008
Azhar, M.A., Saudi, M.M., Ahmad, A., Bakar, A.A.: Detection of social media exploitation via SMS and Camera. IJIM 13 (4), 61–78 (2019). Last accessed 01 Mar 21. https://www.learntechlib.org/p/208525/paper_208525.pdf
Chze, P.L.R., Leong, K.S.: A secure multi-hop routing for IoT communication. In: 2014 IEEE World Forum on Internet of Things, WF-IoT 2014
Das, A., Islam, M.M.: SecuredTrust: a dynamic trust computation model for secured communication in multiagent systems. 9 (2), (2012)
Sarika, S., Pravin, A., Vijayakumar, A., Selvamani, K.: Security issues in mobile ad hoc networks. Proc. Comput. Sci. 3 (5), 1022–1024 (2014)
Wu, B., Chen, J., Wu, J., Cardei, M.: COUNTERMEASURES IN
Dinesh, D., Kumar, A., Singh, J.: Security attacks in mobile adhoc networks (MANET): a literature survey. Int. J. Comput. Appl. 122 (20), 31–35 (2015)
Zhou, L., Haas, Z.J.: Securing ad hoc networks. IEEE Netw. 13 (6), 24–30 (1999)
Manvi, S.S., Tangade, S.: A survey on authentication schemes in VANETs for secured communication. Veh. Commun . (2017)
Assadhan, B., Moura, J.M.F., Lapsley, D., Jones, C., Strayer, W.T.: Detecting botnets using command and control traffic, 4, 156–162 (2009)
Lan, J., Zhou, J., Liu, X.: An area-efficient implementation of a message authentication code (MAC) algorithm for cryptographic systems. In: IEEE Reg. 10 Annual International Conference Proceedings/TENCON, pp. 1977–1979, 2017
Liu, Z., Lallie, H.S., Liu, L., Zhan, Y., Wu, K.: A hash-based secure interface on plain connection, 1236–1239 (2011)
Padmavathi, G., Subashini, P., Aruna, M.D.D.: ZRP with WTLS key management technique to secure transport and network layers in mobile adhoc networks. Int. J. Wirel. Mob. Netw. 4 (1), 129–138 (2012)
Liang, Y., Poor, H.V., Shamai, S.: Secure communication over fading channels. IEEE Trans. Inf. Theory 54 (6), 2470–2492 (2008)
Article MathSciNet Google Scholar
Kobayashi, M., Shitz, S.S.: Secured communication over frequency-selective fading channels : a practical vandermonde precoding, 2009 (2009)
Azeez, N.A., Salaudeen, B.B., Misra, S., Damaševičius, R., Maskeliūnas, R.: Identifying phishing attacks in communication networks using URL consistency features. Int. J. Electron. Secur. Digit. Forensics 12 (2), 200–213 (2020)
Osho, O., Musa, F.A., Misra, S., Uduimoh, A.A., Adewunmi, A., Ahuja, R.: AbsoluteSecure: a tri-layered data security system. Commun. Comput. Inf. Sci. 1078 , 243–255
Download references
Acknowledgements
The authors appreciate the sponsorship from Covenant University through its Center for Research, Innovation and Discovery, Covenant University, Ota Nigeria.
Author information
Authors and affiliations.
Center of ICT/ICE Research, Covenant University, Ota, Nigeria
Paul Joan Ezra, Sanjay Misra & Jonathan Oluranti
Amity University, Gurgaon, Haryana, India
Akshat Agrawal
Silesian University of Technology, Gliwice, Poland
Rytis Maskeliunas & Robertas Damasevicius
You can also search for this author in PubMed Google Scholar
Corresponding author
Correspondence to Sanjay Misra .
Editor information
Editors and affiliations.
The NorthCap University, Gurugram, India
Kavita Khanna
Departamento of Telecommunications (TET), Universidade Federal Fluminese, Duque de Caxias, Rio de Janeiro, Brazil
Vania Vieira Estrela
Av. Ministro Petrônio Portela, Universidade Federal Do Piauí, Teresina, Piauí, Brazil
Joel José Puga Coelho Rodrigues
Rights and permissions
Reprints and permissions
Copyright information
© 2022 The Author(s), under exclusive license to Springer Nature Singapore Pte Ltd.
About this paper
Cite this paper.
Ezra, P.J., Misra, S., Agrawal, A., Oluranti, J., Maskeliunas, R., Damasevicius, R. (2022). Secured Communication Using Virtual Private Network (VPN). In: Khanna, K., Estrela, V.V., Rodrigues, J.J.P.C. (eds) Cyber Security and Digital Forensics . Lecture Notes on Data Engineering and Communications Technologies, vol 73. Springer, Singapore. https://doi.org/10.1007/978-981-16-3961-6_27
Download citation
DOI : https://doi.org/10.1007/978-981-16-3961-6_27
Published : 02 October 2021
Publisher Name : Springer, Singapore
Print ISBN : 978-981-16-3960-9
Online ISBN : 978-981-16-3961-6
eBook Packages : Engineering Engineering (R0)
Share this paper
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
- Publish with us
Policies and ethics
- Find a journal
- Track your research
VPNoverview.com Editorial Guidelines How We Review VPNs
How We Review VPNs
At VPNOverview, our team of experts conducts a series of rigorous tests when reviewing and researching a VPN. As a trusted authority on cybersecurity and VPNs for millions of users, we strive to provide our readers with accurate, up-to-date information . That’s why we update the VPN reviews on our site whenever new information comes to light or when test results change significantly.
Every VPN review is segmented into four primary sections. During testing, each of them is assigned a score on a scale of 1 to 10:
Server Network
These partial scores are then combined to form an average score, which can be seen in our reviews. The final scores awarded to each VPN determines our official VPN ranking.
As an example, lets take a look at Surfshark VPN’s scores:
When combined, these scores give us the following average final score:
Here’s some more information about what each section includes and the factors we consider during testing and scoring.
Speed is a critical factor to consider when evaluating any VPN, as it can have a massive impact on your overall browsing experience. A VPN that throttles your browsing speeds might make simple tasks difficult, such as streaming HD content, browsing in multiple tabs, or playing online games.
When reviewing each VPN, we first test our connection speeds without a VPN . We use this as a benchmark to determine the speed drop-off after connecting to the VPN. Due to nature of VPNs (they redirect your traffic) it isn’t unusual to find small speed drop-offs. However, the VPN shouldn’t deter you from going about your usual business.

When testing any VPN for speed, we always test on both near and distant servers , including locations in Asia, Europe, and North America.
Tests are often conducted several times throughout the day , as performance usually varies depending upon demand. This allows us to provide a more accurate result.

The speed results are presented in a table, which shows:
- Download speeds : The rate (in megabits per second) at which information is downloaded from a server
- Upload speeds : The speeds (in megabits per second) at which information is sent, or uploaded, to a server
- Ping (Packet Internet) : A network tool to check the connectivity performance between our host computer and different servers
It’s important to note that other factors, such as the type of encryption, the VPN protocol, or additional security features, may reduce speeds further.
The top VPNs have the lowest speed drop-off , often no more than 10% on closer servers and under 35% on distant servers, and as such, receive a higher score. Take a look at the speed tests of our top 5 VPN providers below, both for servers close to the testing facility, as well as servers far away.
Our experts test the VPN’s performance and speed themselves , using it for everyday activities like downloading, streaming, gaming, and browsing, to ensure that the performance numbers hold up in performance too.
VPNs play an important role in keeping users safe. In every review we do, we analyze the security features offered by the VPN , including:
- The type of encryption
- The different VPN protocols supported
- Logging and privacy policy
- Security infrastructure improvements made by the VPN provider
- DNS/IP leak protection
- Kill switch
- Obfuscation
- Split tunneling
AES-256 is the most robust encryption available today, and many leading VPNs offer that. This is military grade encryption that is used by security agencies around the globe to encrypt privileged information.

If a VPN we’re reviewing uses AES-256 encryption, it’s already off to a good start in terms of security performance. However, that’s not the only factor we take into account.
We also evaluate the different VPN protocols available. The safest VPN protocols today are WireGuard, OpenVPN (UDP/TCP), and IKEv2 . Some VPNs also have their own proprietary protocols, often built on open-source technologies like WireGuard. VPNs that use older protocols, like SSTP or L2TP/IPSec, generally receive a lower security score compared to those that support more modern choices. We also check whether the listed protocols are working or not, and outline our experience in the review.

We rigorously check every VPN provider’s logging policy to ensure they don’t keep any logs. The best VPNs are certified no-logs, ensuring that no data regarding your online activity is stored on their servers.
Other safety and security features that we test include the kill switch and split tunneling, as they are incredibly important for almost any VPN use case. Of course, if a VPN’s package includes other security-related tools like a password manager, those will be tested as well.
We use highly reliable third-party tools such as ipleak.net to determine whether a VPN is reliably concealing your IP address. If the VPN doesn’t leak your IP address and all security features work, our experts will give it a higher rating.
We also pay attention to any security infrastructure improvements made by the VPN provider, as that indicates that the company is concerned about providing a superior, more secure service.
Usability, or user-friendliness, is another important factor we pay close attention to. Some VPNs are easier to use and can be installed right out of the box. They also have mobile apps available, offering protection on multiple devices with the same account. However, not all VPNs are the same . Some, like custom VPNs for Linux, require technical expertise.
We start by evaluating just how easy it is to download, install, and use the VPN on different platforms. This includes Android, iOS, macOS, Windows, and, if available, smart TVs and other devices, such as Roku, the Amazon Fire TV Stick, and even routers. We also provide screenshots to give users a better understanding. These are updated regularly when we update our reviews.
We carefully analyze the interface of the app. Poorly designed or outdated apps are often difficult to use, and as such, receive a lower rating. We also review the settings to determine how easily a person can set up the VPN according to their needs.

Customer support is another key factor we consider in this section. If a user runs into a problem with their VPN, they should have the option of contacting customer service.
Our team of experts at VPNOverview reaches out to customer support as regular customers , often asking technical questions. We then evaluate the quality of responses to determine if they can help readers in case they run into an issue.
We consider different support channels offered by the VPN, such as email, an FAQ, and live chat. The top VPNs usually offer support through all of these channels, and thus, may receive a higher rating.
We also review additional tools , if available, such as dedicated IPs or (business) security solutions, and include information about those in this rating.
A VPN that offers an expansive network of servers around the globe allows users to unblock more content. In our reviews, we provide details about the major locations where servers are available , including the total number of servers on the network. Of course, during our research, we don’t just look at the number of servers on offer, but also use randomized testing to determine how they perform .
For instance, we test if the VPN is capable of unblocking different streaming platforms , including US Netflix, Hulu, Disney+, and Amazon Prime Video. The experts at VPNOverview have subscriptions to all of these streaming platforms, so we can provide our readers with accurate, up-to-date results. If a VPN is able to unblock major streaming platforms and offer a lag-free streaming experience, it gets a higher score.
If a VPN offers specialized servers , including dedicated obfuscation servers or P2P servers for torrenting, we also test those to ensure they actually add value, as well as ensure they don’t compromise user security.

We test key features like split tunneling and setting up port forwarding for seamless torrenting as well. Some VPNs also offer dedicated IP addresses in specific locations. If available, we test those too.
We understand that many of our readers want reliable information about VPNs that can unblock certain websites, especially in countries that enforce strict censorship. In such cases, we test the VPNs locally, from within the region , to provide a more accurate account of our experience and test results.
Other Writing and Reviewing Processes
On VPNOverview, we also review other cybersecurity software. You can read more about our writing guidelines and how we test these other tools down below:
- How We Review Antivirus Software
- How We Review Password Managers
- Our Editorial Guidelines

Priscilla Sherman Author
Chief editor.
Priscilla is VPNOverview’s chief editor and has several years of experience in VPNs and product reviews. She helps coordinate the team and ensures that all content on our website is honest and accessible.
Share this article
Looking for a vpn.
Take a look at our overview of the most trustworthy, fast, and safe VPN services. Extensively tested by our experts.

Ask a question from expert
Virtual Private Network (VPN) | Literature Review
Review existing literatures on VPN technologies and issues, and write a report. Also, install a demo on virtual box or laptop to demonstrate the concept.
Added on 2022-09-18
Added on 2022-09-18

End of preview
Want to access all the pages? Upload your documents or become a member.
Types of VPN and Encryption Techniques lg ...
Ssl/tls vpn technologies: significance, role, advantages, and security lg ..., security in cryptography | assignment lg ..., report on virtual private network 2022 lg ..., vpn: virtual private network - categories, types, topology, advantages, disadvantages, components, protocols, and benefits lg ..., report on virtual private network lg ....
- Skip to main content
- Skip to header right navigation
- Skip to site footer

RestorePrivacy
Resources to stay safe and secure online
VPN Reviews: Honest Analysis and In-Depth Testing
For some people, finding a good VPN can be frustrating. That’s because many of the websites that recommend and “review” VPNs do not base their recommendations on testing results, but instead on questionable marketing claims.
Even worse, many of these websites are often paid to promote inferior and untrustworthy services. This may sound strange, but it’s quite common. Consequently, people waste time and money as they search for a safe and secure VPN service.
All of the VPN reviews on RestorePrivacy are based on extensive testing to see how well the VPN protects your privacy and security. Every VPN is tested for IP address leaks (both IPv4 and IPv6), DNS leaks, reliability, speed, and how well the features work. Other considerations include privacy jurisdiction, company policies, trustworthiness, and the track record (background) of the provider.
We have been personally using and testing VPN services for the past eight years, even before RestorePrivacy.com was started.
Is there a published review of every VPN that was tested?
The answer is no. Writing up a detailed VPN review is extremely time-intensive, which is why there aren’t too many reviews published here on RestorePrivacy. Here’s what takes up time:
- Purchasing, downloading, and setting up the VPN clients
- Testing the VPN on different operating systems
- Taking screenshots of the test results
- Compressing and resizing images to be used in the VPN review
- Writing the VPN review and describing the test results and findings (over 2,000 words)
- Responding to VPN companies when they have complaints, concerns, or feedback with my VPN reviews
- Responding to VPN users who have general questions
- Keeping the VPN review updated to reflect changes, such as with company policies, features, and VPN client updates
Over the past few years, doing all of the above with about a dozen VPN reviews has taken up lots of time, in addition to writing and updating other privacy guides for the site. However, our small team is expanding to cover more privacy topics, which also includes doing more VPN Reviews.
VPN reviews on RestorePrivacy
Here are all the VPNs we have reviewed on RestorePrivacy:
ExpressVPN Review NordVPN Review Surfshark Review VPN.ac Review Perfect Privacy Review ProtonVPN Review IPVanish Review Avast VPN Review Trust.Zone Review VPNArea Review Windscribe Review Hotspot Shield VPN Review Norton VPN Review VyprVPN Review Private Internet Access Review PureVPN Review HideMyAss HMA VPN Review CyberGhost Review Opera VPN Review Namecheap VPN Review TunnelBear VPN Review Betternet Review TorGuard Review Mullvad VPN Review AVG Secure VPN Review Atlas VPN review PrivadoVPN review PrivateVPN Review
VPN review updates
Right now our focus is on updating old VPN reviews, rather than adding new reviews to our list of content. Updating old reviews with new information and test results is a time-intensive task, but we’re doing our best to keep all content updated and relevant.
This VPN reviews page was last updated on October 27, 2023.

About Sven Taylor
Sven Taylor is the lead editor and founder of RestorePrivacy, a digital privacy advocacy group. With a passion for digital privacy and accessible information, he created RestorePrivacy to provide you with honest, useful, and up-to-date information about online privacy, security, and related topics.
Have a language expert improve your writing
Run a free plagiarism check in 10 minutes, generate accurate citations for free.
- Knowledge Base
Methodology
- How to Write a Literature Review | Guide, Examples, & Templates
How to Write a Literature Review | Guide, Examples, & Templates
Published on January 2, 2023 by Shona McCombes . Revised on September 11, 2023.
What is a literature review? A literature review is a survey of scholarly sources on a specific topic. It provides an overview of current knowledge, allowing you to identify relevant theories, methods, and gaps in the existing research that you can later apply to your paper, thesis, or dissertation topic .
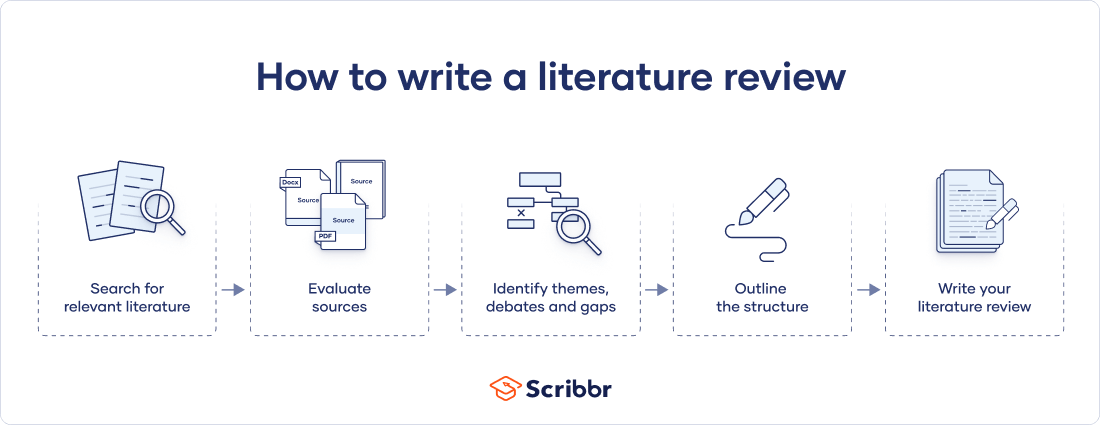
There are five key steps to writing a literature review:
- Search for relevant literature
- Evaluate sources
- Identify themes, debates, and gaps
- Outline the structure
- Write your literature review
A good literature review doesn’t just summarize sources—it analyzes, synthesizes , and critically evaluates to give a clear picture of the state of knowledge on the subject.
Instantly correct all language mistakes in your text
Upload your document to correct all your mistakes in minutes
Table of contents
What is the purpose of a literature review, examples of literature reviews, step 1 – search for relevant literature, step 2 – evaluate and select sources, step 3 – identify themes, debates, and gaps, step 4 – outline your literature review’s structure, step 5 – write your literature review, free lecture slides, other interesting articles, frequently asked questions, introduction.
- Quick Run-through
- Step 1 & 2
When you write a thesis , dissertation , or research paper , you will likely have to conduct a literature review to situate your research within existing knowledge. The literature review gives you a chance to:
- Demonstrate your familiarity with the topic and its scholarly context
- Develop a theoretical framework and methodology for your research
- Position your work in relation to other researchers and theorists
- Show how your research addresses a gap or contributes to a debate
- Evaluate the current state of research and demonstrate your knowledge of the scholarly debates around your topic.
Writing literature reviews is a particularly important skill if you want to apply for graduate school or pursue a career in research. We’ve written a step-by-step guide that you can follow below.
Here's why students love Scribbr's proofreading services
Discover proofreading & editing
Writing literature reviews can be quite challenging! A good starting point could be to look at some examples, depending on what kind of literature review you’d like to write.
- Example literature review #1: “Why Do People Migrate? A Review of the Theoretical Literature” ( Theoretical literature review about the development of economic migration theory from the 1950s to today.)
- Example literature review #2: “Literature review as a research methodology: An overview and guidelines” ( Methodological literature review about interdisciplinary knowledge acquisition and production.)
- Example literature review #3: “The Use of Technology in English Language Learning: A Literature Review” ( Thematic literature review about the effects of technology on language acquisition.)
- Example literature review #4: “Learners’ Listening Comprehension Difficulties in English Language Learning: A Literature Review” ( Chronological literature review about how the concept of listening skills has changed over time.)
You can also check out our templates with literature review examples and sample outlines at the links below.
Download Word doc Download Google doc
Before you begin searching for literature, you need a clearly defined topic .
If you are writing the literature review section of a dissertation or research paper, you will search for literature related to your research problem and questions .
Make a list of keywords
Start by creating a list of keywords related to your research question. Include each of the key concepts or variables you’re interested in, and list any synonyms and related terms. You can add to this list as you discover new keywords in the process of your literature search.
- Social media, Facebook, Instagram, Twitter, Snapchat, TikTok
- Body image, self-perception, self-esteem, mental health
- Generation Z, teenagers, adolescents, youth
Search for relevant sources
Use your keywords to begin searching for sources. Some useful databases to search for journals and articles include:
- Your university’s library catalogue
- Google Scholar
- Project Muse (humanities and social sciences)
- Medline (life sciences and biomedicine)
- EconLit (economics)
- Inspec (physics, engineering and computer science)
You can also use boolean operators to help narrow down your search.
Make sure to read the abstract to find out whether an article is relevant to your question. When you find a useful book or article, you can check the bibliography to find other relevant sources.
You likely won’t be able to read absolutely everything that has been written on your topic, so it will be necessary to evaluate which sources are most relevant to your research question.
For each publication, ask yourself:
- What question or problem is the author addressing?
- What are the key concepts and how are they defined?
- What are the key theories, models, and methods?
- Does the research use established frameworks or take an innovative approach?
- What are the results and conclusions of the study?
- How does the publication relate to other literature in the field? Does it confirm, add to, or challenge established knowledge?
- What are the strengths and weaknesses of the research?
Make sure the sources you use are credible , and make sure you read any landmark studies and major theories in your field of research.
You can use our template to summarize and evaluate sources you’re thinking about using. Click on either button below to download.
Take notes and cite your sources
As you read, you should also begin the writing process. Take notes that you can later incorporate into the text of your literature review.
It is important to keep track of your sources with citations to avoid plagiarism . It can be helpful to make an annotated bibliography , where you compile full citation information and write a paragraph of summary and analysis for each source. This helps you remember what you read and saves time later in the process.
Prevent plagiarism. Run a free check.
To begin organizing your literature review’s argument and structure, be sure you understand the connections and relationships between the sources you’ve read. Based on your reading and notes, you can look for:
- Trends and patterns (in theory, method or results): do certain approaches become more or less popular over time?
- Themes: what questions or concepts recur across the literature?
- Debates, conflicts and contradictions: where do sources disagree?
- Pivotal publications: are there any influential theories or studies that changed the direction of the field?
- Gaps: what is missing from the literature? Are there weaknesses that need to be addressed?
This step will help you work out the structure of your literature review and (if applicable) show how your own research will contribute to existing knowledge.
- Most research has focused on young women.
- There is an increasing interest in the visual aspects of social media.
- But there is still a lack of robust research on highly visual platforms like Instagram and Snapchat—this is a gap that you could address in your own research.
There are various approaches to organizing the body of a literature review. Depending on the length of your literature review, you can combine several of these strategies (for example, your overall structure might be thematic, but each theme is discussed chronologically).
Chronological
The simplest approach is to trace the development of the topic over time. However, if you choose this strategy, be careful to avoid simply listing and summarizing sources in order.
Try to analyze patterns, turning points and key debates that have shaped the direction of the field. Give your interpretation of how and why certain developments occurred.
If you have found some recurring central themes, you can organize your literature review into subsections that address different aspects of the topic.
For example, if you are reviewing literature about inequalities in migrant health outcomes, key themes might include healthcare policy, language barriers, cultural attitudes, legal status, and economic access.
Methodological
If you draw your sources from different disciplines or fields that use a variety of research methods , you might want to compare the results and conclusions that emerge from different approaches. For example:
- Look at what results have emerged in qualitative versus quantitative research
- Discuss how the topic has been approached by empirical versus theoretical scholarship
- Divide the literature into sociological, historical, and cultural sources
Theoretical
A literature review is often the foundation for a theoretical framework . You can use it to discuss various theories, models, and definitions of key concepts.
You might argue for the relevance of a specific theoretical approach, or combine various theoretical concepts to create a framework for your research.
Like any other academic text , your literature review should have an introduction , a main body, and a conclusion . What you include in each depends on the objective of your literature review.
The introduction should clearly establish the focus and purpose of the literature review.
Depending on the length of your literature review, you might want to divide the body into subsections. You can use a subheading for each theme, time period, or methodological approach.
As you write, you can follow these tips:
- Summarize and synthesize: give an overview of the main points of each source and combine them into a coherent whole
- Analyze and interpret: don’t just paraphrase other researchers — add your own interpretations where possible, discussing the significance of findings in relation to the literature as a whole
- Critically evaluate: mention the strengths and weaknesses of your sources
- Write in well-structured paragraphs: use transition words and topic sentences to draw connections, comparisons and contrasts
In the conclusion, you should summarize the key findings you have taken from the literature and emphasize their significance.
When you’ve finished writing and revising your literature review, don’t forget to proofread thoroughly before submitting. Not a language expert? Check out Scribbr’s professional proofreading services !
This article has been adapted into lecture slides that you can use to teach your students about writing a literature review.
Scribbr slides are free to use, customize, and distribute for educational purposes.
Open Google Slides Download PowerPoint
If you want to know more about the research process , methodology , research bias , or statistics , make sure to check out some of our other articles with explanations and examples.
- Sampling methods
- Simple random sampling
- Stratified sampling
- Cluster sampling
- Likert scales
- Reproducibility
Statistics
- Null hypothesis
- Statistical power
- Probability distribution
- Effect size
- Poisson distribution
Research bias
- Optimism bias
- Cognitive bias
- Implicit bias
- Hawthorne effect
- Anchoring bias
- Explicit bias
A literature review is a survey of scholarly sources (such as books, journal articles, and theses) related to a specific topic or research question .
It is often written as part of a thesis, dissertation , or research paper , in order to situate your work in relation to existing knowledge.
There are several reasons to conduct a literature review at the beginning of a research project:
- To familiarize yourself with the current state of knowledge on your topic
- To ensure that you’re not just repeating what others have already done
- To identify gaps in knowledge and unresolved problems that your research can address
- To develop your theoretical framework and methodology
- To provide an overview of the key findings and debates on the topic
Writing the literature review shows your reader how your work relates to existing research and what new insights it will contribute.
The literature review usually comes near the beginning of your thesis or dissertation . After the introduction , it grounds your research in a scholarly field and leads directly to your theoretical framework or methodology .
A literature review is a survey of credible sources on a topic, often used in dissertations , theses, and research papers . Literature reviews give an overview of knowledge on a subject, helping you identify relevant theories and methods, as well as gaps in existing research. Literature reviews are set up similarly to other academic texts , with an introduction , a main body, and a conclusion .
An annotated bibliography is a list of source references that has a short description (called an annotation ) for each of the sources. It is often assigned as part of the research process for a paper .
Cite this Scribbr article
If you want to cite this source, you can copy and paste the citation or click the “Cite this Scribbr article” button to automatically add the citation to our free Citation Generator.
McCombes, S. (2023, September 11). How to Write a Literature Review | Guide, Examples, & Templates. Scribbr. Retrieved April 8, 2024, from https://www.scribbr.com/dissertation/literature-review/
Is this article helpful?
Shona McCombes
Other students also liked, what is a theoretical framework | guide to organizing, what is a research methodology | steps & tips, how to write a research proposal | examples & templates, what is your plagiarism score.
VPN Glossary: key terms explained
Kill switches, DNS, geo-spoofing – what does it all mean?

Advanced Encryption Standard (AES)
Catapult hydra, deep packet inspection (dpi), domain name system (dns), eavesdropping attack, encryption key, five eyes alliance, geo-blocking, jurisdiction, key exchange, kill switch, man-in-the-middle attacks, no logs policy, obfuscation, perfect forward secrecy, public wi-fi, split tunneling, vpn service, warrant canary.
Virtual Private Networks (VPNs) are, undeniably, handy pieces of kit for anyone who values their digital privacy. They can put a stop to snooping cybercriminals, invasive ads, and ISP (internet service provider) throttling that can grind your streaming sessions to a halt. Unfortunately, the language used on provider sites can be super-techy and obscure.
If you've ever wondered just what encryption is, exactly, or the difference between a DNS leak and an IP leak, you’re not alone – and I'm here to help.
I've picked out the terms you're likely to come across when shopping around for the best VPN in the business. I've summed up each one with a jargon-free explanation that'll help you wrap your head around the key VPN concepts – whether you're totally new to the tech or have some experience under your belt.
Advanced Encryption Standard (AES) is an encryption cipher that determines how data is encrypted and decrypted.
AES is the industry's gold standard, and you'll often find it described alongside the key length. AES-128 uses a 128-bit key, for example, whereas AES-256 encryption uses a 256-bit key. The more bits, the stronger the encryption, and AES encryption is virtually uncrackable (even when tested by brute force attacks).
Auditors use a "black box" testing technique to check out VPN services from the point of view of an everyday user – like you and me. While black box testing lets the auditor install and run the VPN, it doesn't allow them to comb through the service's app and server source code. That requires a "white box" test .
A VPN protocol developed by Hotspot Shield . It uses TLS 1.2-based security, but additional details on how the protocol works haven't been shared by the provider.
Sign up to get the BEST of Tom’s Guide direct to your inbox.
Upgrade your life with a daily dose of the biggest tech news, lifestyle hacks and our curated analysis. Be the first to know about cutting-edge gadgets and the hottest deals.
Ciphers contain rules for data encryption and decryption – and there are all sorts of ciphers available. Blowfish is an enduring favorite, developed in 1993, and still widely used today. Advanced Encryption Standard (AES) is tougher, however, and has become the VPN industry's gold standard.
Web content that lives on darknets, which are only accessible to savvy users with specific software. The TOR network is the most popular of these.
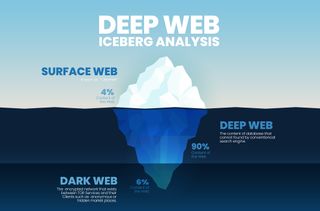
Similar (but not the same as) the dark web , the deep web is any site that isn't indexed by search engines – think Google, Bing , etc. You can access these deep web sites via a direct URL or IP address, but you might need an additional password to view content.
Deep web sites are used for online banking, email providers, and forums where you'll need an account to join the conversation and check out content.
Firmware you can use to improve your wireless router's performance: better speed, more features, and extended functionality. You'll need to "flash" your router to do this, however, which can be risky. Lots of VPNs are compatible with DD-WRT (including ExpressVPN and NordVPN ), meaning you can set them up on a range of wireless routers.
"DD" is a reference to Dresden, in Germany, where DD-WRT firmware was initially developed. "WRT" means wireless router.
Filtering technologies that inspect network traffic to understand its purpose. DPI uses pre-defined criteria to check out traffic, find viruses, malware, hackers, spam, and other threats, and block them. Unfortunately, DPI can also be used by repressive government regimes to monitor its citizens' online activity.
When you connect to a VPN, your traffic is encrypted and much harder for snoopers to inspect with DPI. That means you can go about your browsing with added peace of mind. DPI isn't a rock-solid guarantee of privacy, however, as it can be used to sniff out and prevent VPN usage.
DNS takes the URL you type into your browser's address bar and turns it into a numeric IP address that your device uses to find the webpage and load it up. DNS is often thought of as the translation of human inputs (like URLs and domain names) into computer-friendly numeric codes.
Your default DNS provider is usually your ISP (Internet Service Provider). However, connect to a VPN, and your DNS will be provided by the VPN service provider.
A form of hacking that targets information as it is transmitted over unencrypted wireless internet connections. Often, these are free Wi-Fi hotspots you find in cafes and airports, and they typically don't require a password.
Eavesdropping attacks are sometimes called "sniffing attacks" or "spoofing attacks".
Encryption encodes data, turning it into a random string of unintelligible characters, and prevents it from being read by snoopers and hackers. An algorithm encrypts your data, and a cipher is used to subsequently decrypt it once it reaches its destination.
Today's best secure VPNs use a variety of encryption protocols to protect your data, but AES (Advanced Encryption Standard) is the most widely used and secure.
Encryption keys are made up of random sets of information used to encrypt and decrypt data. You'll often see keys described alongside their size – like 1024 and 2048. The bigger the number, the more variations there are in the encryption process, and the harder it is for attacks to crack the code.
An intelligence network made up of the UK, the US, Canada, Australia, and New Zealand. The existence of the Five Eyes Alliance (and the extent of its data harvesting) was unveiled in 2013, by Edward Snowden, and now we recommend sticking to VPN providers who are headquartered outside of the countries listed above.
Extended alliances exist, too – including the Nine Eyes and Fourteen Eyes.
Geo-blocks prevent you from accessing web content – and can limit certain sites, services, and apps to specific countries.
Streaming VPNs can help you get around geo-blocking measures, however, which is vital for folks trying to check out international Netflix libraries. So, if you're on vacation, traveling for work, or simply interested in what other regions have to offer, a VPN is your best bet.
An IP address is like a digital street name and house number – every device has one, just like physical houses, and they use them to communicate. Any gadget that can connect to the internet has a unique IP address that contains approximate location information and makes sure that the correct data gets routed to the correct computer.

IPv4 is what we call the 4th version of the internet's standard protocol, Internet Protocol (IP). IPv4 assigns a unique IP address to every internet-enabled device, allowing them to communicate and connect to the web.
We're rapidly running out of usable IPv4 addresses, however. The protocol is so popular, and there are so many devices connected to the internet, that it became necessary to develop a new standard protocol – IPv6 .
Internet Protocol version 6 (IPv6 for short) is the newer version of IPv4 . Like its predecessor, it defines how IP addresses are dished out to our gadgets and computers, and how they communicate.
IPv6 isn’t as widespread as IPv4, but it's certainly better . It's much quicker, simpler, and has 1,028 times more IP addresses than IPv4. That's good news, too, because we're quickly running out of IPv4 addresses.
IP leaks occur when your IP address is visible – even though you're using a VPN.
If you're using your original DNS server, and not the one provided by your VPN, your ISP (internet service provider) can see everything you get up to online. Naturally, this is the last thing you want when using a VPN.
You can visit IPLeak.net , IPLeak.org , or BrowserLeaks.com to check for DNS leaks. Alternatively, lots of VPN providers have their own DNS leak tools – including ExpressVPN's excellent page .
The country where a VPN provider's headquarters are located. A VPN provider has to stick to the laws of the jurisdiction – which can vary from country to country.
Generally, we'd advise you to use a VPN headquartered in a country that isn't a part of the Five Eyes alliance – and one without invasive data retention laws.
A process where two parties securely swap cryptographic keys that can be used to share encrypted data. Anyone who isn't an involved party will be unable to get their hands on a key (or a copy of the key) and, as a result, unable to decrypt the shared data.
Diffie-Hellman is a popular method of key exchange, along with Internet Key Exchange (which you might recognize from the IKEv2 protocol).
One of a VPN's most must-have features. A kill switch cuts your connection to the internet if your VPN connection drops out, and ensures that you don't suffer an IP leak . Without a kill switch, your identifiable information could become visible to snoopers, and your data could be left unprotected.
How long it takes for data to journey across a network from its source (usually your device) to its ultimate destination (like a website).
When you connect to a VPN, data leaves the source and is routed through the VPN server before it makes it to its destination. This is an extra step in the process – but an important one, as this is where your data is encrypted – that can increase latency.

Whenever a VPN fails to keep your personal information secure and out of the hands of onlookers (including your internet service provider, the website you're on, other network users, or cybercriminals) it's known as a leak.
Common leaks include: IPv4, IPv6, DNS, and WebRTC.
A proprietary protocol created by ExpressVPN – and based on WireGuard. Like WireGuard, Lightway is more lightweight than OpenVPN, consisting of fewer lines of code. This means that it won't drain your device’s battery as fast or demand as many CPU requirements.
Lightway is quicker, connects faster, and is designed to handle common mobile networking hangups – like surprise signal dropouts. Most proprietary VPN protocols are closed-source, but Lightway bucks the trend, and you can comb through its source code yourself if you want to check that it's working as it should.

<a href="https://go.expressvpn.com/c/4550836/1330033/16063?subId1=hawk-custom-tracking&sharedId=hawk&u=https%3A%2F%2Fwww.expressvpn.com%2Foffer%2Frecommended-deal%3Foffer%3D3monthsfree" data-link-merchant="expressvpn.com"" target="_blank" rel="nofollow"> Looking in the Lightway: ExpressVPN If Lightway has piqued your interest, you'll want to check out ExpressVPN. It's an awesome newbie VPN, thanks to a bevy of handy automations that handle all the complicated configurations for you, and it can unblock more content than you'll know what to do with. Take this super-fast service for a test drive with a 30-day money-back guarantee .
Generally, VPN logs are split into two categories: connection logs and usage logs. Connection logs are usually anonymized, and contain information about which server you're using, how long you've been connected to it, and the device you're using the VPN with. Connection logs help VPN services maintain their server networks and troubleshoot issues as they crop up.
Usage logs, on the other hand, are far more insidious. They can reveal your IP address, the websites and services you've visited, and your download history, which is a massive violation of your digital privacy. The Tom's Guide team doesn't recommend VPNs known to keep usage logs.
A cyberattack that allows a snooper to listen in to conversations between a user device and the sites they visit – and record login details, financial information, and even credit card numbers. Armed with this information, the snooper can go on to impersonate the victim or empty their bank account.
A no-logs policy states that a VPN won't keep a record of a user's browsing history, download history, real IP address, DNS queries, or bandwidth usage. Today's top VPNs submit to independent audits of their no-log policies in the name of transparency.
Obfuscation makes encrypted VPN traffic look just like ordinary web traffic – so the websites you visit can't tell that you’re using a VPN at all. Obfuscation can help you access streaming platforms and blocked services, and nullify VPN bans imposed by certain websites or oppressive governments.

<a href="http://go.nordvpn.net/aff_c?offer_id=564&url_id=10992&aff_id=3013&aff_click_id=hawk-custom-tracking&aff_sub2=hawk-article-url" data-link-merchant="go.nordvpn.net"" target="_blank" rel="nofollow"> The best VPN with obfuscated servers: NordVPN NordVPN is my top pick overall when it comes to obfuscation. The provider has obfuscated servers you can connect to with just a click and get around those pesky VPN bans and check out content that might otherwise be unavailable in your current location. Check out NordVPN today with a handy 30-day money-back guarantee .
A massively popular VPN protocol. OpenVPN is secure, configurable, and open-source – which means you could take a look at its source code (and pick out potential bugs or weaknesses) if you wanted.
OpenVPN's security and versatility have made the protocol a mainstay in the VPN world, but the WireGuard protocol (and proprietary protocols, like Lightway and NordLynx) are quicker.
A method of encryption that frequently swaps the encryption keys that a VPN uses to encrypt and decrypt data. The constant switch-ups ensure that only a small percentage of data is exposed if a bad actor hacks a key.
A measurement of latency; how long it takes for data to travel along a network, from one device to the next, and come back with a response.
When you connect to a VPN, your traffic is routed through a VPN server after it leaves your device and before it reaches its ultimate destination. This extra step can result in increased ping.
Rules that dictate how data is transmitted between a VPN server and a user device, and how the VPN creates a secure connection between the two parties.
The protocols you'll see most often include OpenVPN , WireGuard , and IKEv2.
Proxies can help bypass geo-restrictions that block access to region-specific services or websites. By masking your original IP address and replacing it with one of the proxy's IP addresses, you can avoid restrictions.
However, proxies aren't usually encrypted, so they're often thought of as unblocking tools rather than a full privacy-enhancing security suite (like a VPN).
The free wireless connections offered by hotels, airports, cafes, and other public places. Anyone can connect to these public Wi-Fi hotspots – you won't need a password. However, because of this (and because public Wi-Fi hotspots are unencrypted), they're a notorious hotspot for hackers. Users are at risk unless they have a VPN to encrypt data transmitted to and from their devices.
A feature offered by some VPNs that dictates whether traffic is routed through an encrypted VPN tunnel (for improved digital security) or the regular internet connection (in order to access websites and services restricted to your current location).
If an app isn't working properly with your VPN (a streaming service that blocks access if it detects that you're connected to a VPN server overseas, for example), you can set up split tunneling and direct app traffic through your original internet connection to avoid the problem in the future.
An open-source VPN app. You can use it on Windows, Mac, Android, and iOS, and it's compatible with most VPNs on the market.
Although strongSwan isn't packed with features, you can use it in place of a VPN provider's app if you're having trouble with it.
Internet throttling is a mode of digital traffic management that reduces connection speeds. Your internet service provider (ISP) might decide to throttle your connection if you're in the middle of a data-intensive activity (think HD streaming, online gaming, torrenting) to alleviate bandwidth demand.
A VPN prevents throttling by hiding your activity from your ISP – meaning it won't know what you're up to and won't know to throttle you.
The Tor Network (also known as The Onion Router) is an open-source project that enables secure and anonymous online communication. Tor achieves this by encrypting data multiple times and passing it through randomly selected volunteer-run services (or "nodes").
Although Tor and VPNs aren't the same, they can both mask your IP address and boost your digital privacy – and some VPNs are compatible with Tor.
The encrypted connection that links your device and another network. A VPN, for example, creates a secure tunnel between your device and the internet.
The VPN client is the device owned (or used) by you, the VPN user. This device connects to the VPN server via the encrypted tunne l and can be a PC, laptop, smartphone, tablet, games console, TV, or even a router.
Servers run and maintained by the VPN provider that connect to the internet. VPN end users connect their devices to a VPN server of their choice via the encrypted tunnel. Most of today's top VPNs have hundreds (sometimes thousands) of servers dotted around the globe – talk about being spoiled for choice.
A service or company that provides VPN servers . These servers are scattered around the world and enable VPN users to connect to the internet via the secure encrypted tunnel.
A document that subtly informs VPN users that a VPN provider has been ordered to reveal identifiable information about its users. Warrant canaries let users know that a VPN provider hasn't been lumped with a warrant or subpoena, up to a certain date. So, if the warrant canary is wildly out of date or removed altogether, VPN users can typically assume that the provider has come under investigation.
Created by Google, Web Real-Time Communications (WebRTC) is an open-source technology allowing web browsers (and other apps) to support audio, video, and other communications.
However, WebRTC can inform websites about the original IP address of a user, even if they have a VPN, which is known as a WebRTC leak.
An in-depth method of software testing where auditors have access to apps and their source code.
White box VPN audits result in more detailed findings than black box tests , where auditors only have access to the same information as end users – meaning they can test apps, but can’t comb through the source code.
The next generation of VPN encryption – and the successor to OpenVPN in terms of popularity. WireGuard is easy to set up by design, contains fewer lines of code than OpenVPN, and often results in improved speed – making it a favorite of avid streamers and gamers.

<a href="http://get.surfshark.net/aff_c?offer_id=61&aff_id=1691&aff_click_id=hawk-custom-tracking&aff_sub2=hawk-article-url" data-link-merchant="get.surfshark.net"" target="_blank" rel="nofollow"> Blazing fast WireGuard implementation: Surfshark Surfshark is all-in when it comes to WireGuard, and is wickedly quick as a result. I often recommend Surfshark as a Netflix VPN, seeing as it can handle HD and 4K streaming without buffering hiccups, as well as your day-to-day browsing. You'll also get unlimited simultaneous connections, budget-friendly prices, and a handy 30-day money-back guarantee.
We test and review VPN services in the context of legal recreational uses. For example: 1. Accessing a service from another country (subject to the terms and conditions of that service). 2. Protecting your online security and strengthening your online privacy when abroad. We do not support or condone the illegal or malicious use of VPN services. Consuming pirated content that is paid-for is neither endorsed nor approved by Future Publishing.

River is a Tech Software Editor and VPN expert at Tom’s Guide—helping take care of VPN and cybersecurity content, publish breaking news stories, and ensure all of our VPN testing is as accurate as possible. When they’re not following the ins and outs of the VPN world, River can be found plugged into their PS5 or trekking through the Welsh countryside in a very practical, but unfortunately unfashionable, waterproof jacket.
VPNs aren't a silver bullet – but I still use one every day
Our latest VPN testing results
Save 30% on Brooklyn Bedding’s best cooling mattress for hot sleepers
Most Popular
By Christian de Looper April 07, 2024
By John Velasco April 07, 2024
By Sam Hopes April 07, 2024
By Jessica Downey April 06, 2024
By Mo Harber-Lamond April 06, 2024
By Jason England April 06, 2024
By Sam Hopes April 06, 2024
By Mo Harber-Lamond April 05, 2024
By Ryan Morrison April 05, 2024
By Nick Pino April 05, 2024
- 2 KitchenAid just launched its new Espresso Collection — and it's impressive
- 3 How to photograph the April 2024 solar eclipse with your smartphone
- 4 What running shoes were the Paris Marathon 2024 winners wearing?
- 5 Apple has licensed millions of Shutterstock images to train its AI — what this means for the iPhone
ExpressVPN Review (2024)
Shift into the express lane to unrestricted entertainment..
Founded in 2009, ExpressVPN is one of the oldest VPN providers. Known for its fast speeds and ability to unblock popular streaming platforms, it’s long been ranked among the best VPN services available. We wanted to find out if ExpressVPN is proactive in staying ahead of the competition, or if it’s now relying on its reputation. To do this, we put it under the microscope: measuring server speeds, studying the small print, and even testing its money-back guarantee.
ExpressVPN – Server Network and Coverage
A growing number of VPNs, ExpressVPN included, are becoming less transparent about just how many servers it offers. There may be an element of strategy behind this in not wanting to provide rival VPNs with a competitive edge. Of course, it may be that ExpressVPN’s server count fluctuates too much to provide an accurate number, or that its focus is more on the quality of servers it’s providing.
Before removing its server count, ExpressVPN’s network exceeded 3,000 servers and it’s likely that’s still the case. This is a high number of servers for a VPN, although there are some VPNs that offer more. NordVPN now claims to offer over 5,000 servers globally, while CyberGhost recently surpassed 10,000 servers although, like ExpressVPN, it has since removed its server count.
How often do you use a VPN?
What we do know is that ExpressVPN’s network covers 105 countries, which is double that of many VPNs. The biggest difference between ExpressVPN’s network and that of many rival VPNs is that it covers more countries in Africa and Asia. Although ExpressVPN doesn’t state how many servers it has in each country, it’s safe to say there’s a healthy number in the US where it covers a dozen cities in all.
Given the scale of ExpressVPN’s server network, you’ll likely be able to find a server in your preferred country or, at the very least, in a nearby location. If ExpressVPN’s server speeds are anything to go by, there are plenty of servers to go around. I rarely encountered a server that was obviously suffering heavy load.

ExpressVPN – Speed and Performance
I first used ExpressVPN more than five years ago and found it to be one of the faster VPNs I’d tested. The good news is that, based on my recent speed tests, this is still very much the case. As expected from any paid VPN service, ExpressVPN provides unlimited bandwidth, so there’s no limit to the amount of browsing, streaming, or online gaming you can do.
Unlike many of the top VPN providers nowadays, ExpressVPN hasn’t implemented the very popular WireGuard protocol. Instead, it has a proprietary protocol called Lightway. While both VPN protocols are designed for fast connections, Lightway’s codebase is even more lightweight, with just 2,000 lines of code (compared to the 4,000 lines of WireGuard).
In order to test ExpressVPN’s server speeds, I connected to three server locations nine times each (three mornings, afternoons, and evenings). The aim was to generate an average global speed for ExpressVPN by trying servers at varying distances from my location during both peak and off-peak hours.

The closest ExpressVPN server to home is Barcelona, Spain (100 miles). I also connected to a server in New York (3,700 miles), as well as one in Tokyo (6,200 miles). As expected, my internet speed when not connected to the VPN, at 286 Mbps, was much better. This is due to the fact that a VPN adds extra steps to the process with encryption and data routing.
What’s particularly curious however, is that I achieved faster speeds when connecting to a server in New York (139 Mbps) than in Barcelona (108 Mbps). This is despite the 3,600 mile difference between those servers and my location. Stranger still, I recorded the same speeds on ExpressVPN’s servers in Barcelona and Tokyo (108 Mbps) even though there’s a more than 6,000 mile difference between them and where I’m based.
Of course, there’s more to a VPN’s speed than the distance between the server and a user’s physical location. However, these tests were conducted on the same Wi-Fi network, using the same VPN protocol (Lightway). ExpressVPN’s support assured me that all servers have been optimized but it’s quite possible that server quality varies by location or that, at the very least, the ratio of servers to number of users isn’t as generous in some locations.
Still, ExpressVPN’s global average speed was 118 Mbps, which is very respectable. Keep in mind that the speeds you experience will almost certainly vary. For example, you’re more likely to experience faster VPN speeds with a higher baseline internet speed. The speeds ExpressVPN offers should still be more than fast enough regardless of whether you’re just using your VPN for simple browsing or for more bandwidth-intensive activities.
ExpressVPN Speed Test Results

ExpressVPN – Unblocking and Streaming Capabilities
ExpressVPN is one of the stronger unblocking VPNs for streaming . It has long been one of the most consistent VPNs you can use with Netflix, allowing you to access many different country versions including the US, UK, Canada, and Japan. This is impressive considering how many VPNs fail to work with Netflix due to its very stringent VPN IP address blocking.
I also tested ExpressVPN with streaming services including Amazon Prime Video, BBC iPlayer, Disney+, Hulu, ITVX, and Paramount Plus and had no issues with any of them. If you are having trouble with accessing a particular website or service, it’s worth trying more than one server. Clearing your browser’s cache and cookies between each new attempt ensures the website in question forgets your previous IP address.

ExpressVPN even works in China despite the strict restrictions on not only online content, but VPNs themselves (the Great Firewall blocks VPN traffic and VPN websites). ExpressVPN is able to bypass this through obfuscated servers which make encrypted traffic appear unencrypted. You won’t find these servers in ExpressVPN’s apps though as this all happens automatically when connecting from China.
As mentioned further above, ExpressVPN offers impressive speeds so you can expect seamless streaming. Indeed, I was able to stream in 4K resolution without lag or buffering, even when connected to servers further afield.
ExpressVPN – Security Features
As with any quality VPN service that takes user security seriously, ExpressVPN protects data with 256-bit AES encryption. As long as you’re connected, your ISP and other third parties will no longer be able to read your online activity. This is particularly important if you live in (or are traveling in) a country in which citizens have limited internet freedom and may face legal repercussions for their online actions.
You can connect to the following VPN protocols when you use ExpressVPN:
- Lightway (ExpressVPN’s proprietary protocol)
In the case of both Lightway and OpenVPN, you can toggle between TCP and UDP (you’ll want to opt for UDP if your priority is speed) By default, ExpressVPN automatically selects the protocol that’s most appropriate for your network.
ExpressVPN claims to protect users from DNS and IPv6 leaks and this was apparent in the leak tests I ran in which no DNS or IP leaks were observed. ExpressVPN also has a kill switch feature (referred to as “Network Lock”). If your VPN connection drops unexpectedly due to a power outage or when switching Wi-Fi networks, it stops your internet traffic and reduces the risk of data leaks.

That’s not all ExpressVPN offers in terms of security features however. Towards the back end of 2023, ExpressVPN introduced its Advanced Protection feature which blocks ads, trackers, and malicious content. This is available for Windows, Mac, Android, iOS, and Linux. That said, these advanced protection features are disabled by default so you’ll need to enable them manually in settings.

Not content to assume that ExpressVPN’s Advanced Protection does its job, I decided to try it out. Using an online ad block test, I found that my desktop browser (Brave) with shields down blocked just 4 of 140 ads. With shields up, it blocked 138. Meanwhile, ExpressVPN’s Advanced Protection blocked 121 of 140 ads, which is pretty impressive for such a new feature. Still, there’s some room for improvement.

Another very new ExpressVPN feature is ExpressVPN Keys, ExpressVPN’s built-in password manager. This allows unlimited password (as well as credit card details and notes) storage. It uses zero-knowledge encryption, ensuring your privacy is very much protected because nobody else can see or access it – ExpressVPN included. It has been independently audited by Cure53, and even includes a feature that alerts you to data breaches and vulnerable passwords.
ExpressVPN – Privacy and Logging Policies
ExpressVPN is headquartered in the British Virgin Islands which has no data retention laws. It’s also not part of an international intelligence alliance such as Five Eyes (or 14 Eyes). A concerning fact is that ExpressVPN is owned by Kape Technologies, formerly known as Crossrider, which was previously involved in distributing malware.
Signup with ExpressVPN requires you to provide an email address although ExpressVPN provides a “privacy guarantee” stating that this isn’t shared with anyone. Unfortunately, ExpressVPN doesn’t offer anonymous payment methods. You can pay in Bitcoin although it’s not anonymous unless you use a mixing service. There are a small number of VPNs that accept cash or gift cards so it would be good to see ExpressVPN do the same.
ExpressVPN doesn’t keep any identifying logs of users. This means no logging of your browsing activity or IP address (VPN or original IP address). It also doesn’t log connection timestamps or session duration. ExpressVPN states that it can’t be compelled by authorities to provide such information because it simply doesn’t have it to give.

Note that ExpressVPN does collect some usage data. This includes:
- Apps and app versions you’ve activated
- Successful connections to the VPN
- Connected server location (and from which country and ISP)
- Total sum of data transferred
Although ExpressVPN can also collect app diagnostic data, this is on an opt-in basis only. It’s good to see that ExpressVPN’s no-logs policy has been independently audited by PwC (June 2019) as well as KPMG (September 2022). Another positive is that ExpressVPN has introduced biannual transparency reports which detail information requests its legal department receives.
ExpressVPN – Signup and Setup
An increasing number of VPNs are introducing different subscription tiers, letting users choose which additional features they’d like alongside their VPN. While this provides greater flexibility, it can be overwhelming, particularly for first-time VPN users. ExpressVPN keeps things simple with just one subscription tier. You’ll receive access to all of ExpressVPN’s features, regardless of whether you sign up for one month, six months, or a year.
Once subscribed, you’ll be taken to a page to create the password for your new ExpressVPN account. ExpressVPN provides a randomly generated password made up of letters (lower and uppercase) and numbers although you can create your own password if you prefer. After this, you’ll be able to download the ExpressVPN app. It lets you connect up to eight devices at once which is above average for a VPN (and more than both NordVPN and CyberGhost).

Installation took less than a minute on both desktop and mobile, and upon logging in for the first time, I was prompted to enter my activation code from the app download page (you can also find this via your ExpressVPN account dashboard). Following a quick tour of what’s new in the app, you’re in and can connect to a server.
ExpressVPN – Apps and Compatibility
ExpressVPN provides more apps than most VPNs so you can use it with most of your devices:
- Linux (CLI app)
- Amazon Fire TV
Not all VPNs have an app for Linux so that’s a definite plus for ExpressVPN. It’s also one of the few apps to offer an Apple TV app although this is starting to change since the tvOS update that allows the downloading of VPN apps.
What’s unique about ExpressVPN though is its custom firmware for routers. This is pre-configured with ExpressVPN’s servers and replaces a router’s existing firmware. An even easier option is ExpressVPN’s AirCove, a router with ExpressVPN already built-in. One advantage of using a VPN with a router is that devices connected to the router don’t count against the simultaneous connection limit.

Last but not least, ExpressVPN has browser extensions for Chrome, Firefox, Edge, and Brave. Just keep in mind that although extensions offer a high level of convenience, they only secure browser traffic.
Having had plenty of time with ExpressVPN’s apps, I think they can best be described as functional. There’s nothing flashy about them, but that’s no bad thing. The home view is the same across the desktop and mobile apps, and in both cases you can connect to a server in a single click. ExpressVPN’s Smart Location feature automatically picks the fastest server while a shortcut takes you to your most recent location.

ExpressVPN lets you favorite specific server locations although it’s not immediately obvious how to do this on Android or iOS (swipe right to add a location to the list). In just a couple of clicks in the desktop and mobile apps, you’ll get to ExpressVPN’s Settings page. This is all very neatly laid out with different features and VPN protocols clearly explained, making it very accessible.
ExpressVPN – Customer Support
Having interacted with many VPNs over the years, I can safely say that ExpressVPN is one of the best when it comes to customer support. Live chat is available 24 hours a day and, whenever I’ve used it, I’ve received prompt, helpful replies.
ExpressVPN’s email support is also excellent, and I was surprised to find that it was only slightly slower than its live chat. I sent three emails to test its response times. The first email contained a straightforward request, the second required more detailed information, and the third sought more advanced technical details. With an average response time of just 6 minutes and 40 seconds, it’s the fastest I’ve tested.
Here are the questions I sent to ExpressVPN, their response times, and quality of answer:

Of course, it’s not just about the speed of replies. It’s little good if a VPN answers quickly only to fail to answer the question! Fortunately, ExpressVPN provided three relevant replies, two of which were good and answered my question, while the other was a little too generic for my liking, failing to provide specific instructions for optimizing the VPN for gaming as I’d requested.
As an alternative to ExpressVPN’s live chat and email support, ExpressVPN provides setup tutorials, troubleshooting guides, and FAQs. The setup guides are particularly useful as they take you through the process step-by-step, providing screenshots along the way so it’s difficult to get lost. In many cases, a video tutorial is also linked and ExpressVPN has a very active YouTube channel with dozens of videos uploaded in recent weeks.
ExpressVPN is a very strong all-rounder, providing fast speeds, powerful unblocking, and an impressive set of security features. It also has excellent 24/7 support which offers prompt answers via live chat and email. However, it’s lacking a truly anonymous payment option. Still, this is a small criticism and is easily outweighed by the many benefits ExpressVPN provides.
In This Article

More Reviews by Mark Gill
Ign recommends.

Help | Advanced Search
Computer Science > Machine Learning
Title: generative ai for architectural design: a literature review.
Abstract: Generative Artificial Intelligence (AI) has pioneered new methodological paradigms in architectural design, significantly expanding the innovative potential and efficiency of the design process. This paper explores the extensive applications of generative AI technologies in architectural design, a trend that has benefited from the rapid development of deep generative models. This article provides a comprehensive review of the basic principles of generative AI and large-scale models and highlights the applications in the generation of 2D images, videos, and 3D models. In addition, by reviewing the latest literature from 2020, this paper scrutinizes the impact of generative AI technologies at different stages of architectural design, from generating initial architectural 3D forms to producing final architectural imagery. The marked trend of research growth indicates an increasing inclination within the architectural design community towards embracing generative AI, thereby catalyzing a shared enthusiasm for research. These research cases and methodologies have not only proven to enhance efficiency and innovation significantly but have also posed challenges to the conventional boundaries of architectural creativity. Finally, we point out new directions for design innovation and articulate fresh trajectories for applying generative AI in the architectural domain. This article provides the first comprehensive literature review about generative AI for architectural design, and we believe this work can facilitate more research work on this significant topic in architecture.
Submission history
Access paper:.
- HTML (experimental)
- Other Formats
References & Citations
- Google Scholar
- Semantic Scholar
BibTeX formatted citation
Bibliographic and Citation Tools
Code, data and media associated with this article, recommenders and search tools.
- Institution
arXivLabs: experimental projects with community collaborators
arXivLabs is a framework that allows collaborators to develop and share new arXiv features directly on our website.
Both individuals and organizations that work with arXivLabs have embraced and accepted our values of openness, community, excellence, and user data privacy. arXiv is committed to these values and only works with partners that adhere to them.
Have an idea for a project that will add value for arXiv's community? Learn more about arXivLabs .
- Open access
- Published: 05 December 2023
A scoping review to identify and organize literature trends of bias research within medical student and resident education
- Brianne E. Lewis 1 &
- Akshata R. Naik 2
BMC Medical Education volume 23 , Article number: 919 ( 2023 ) Cite this article
816 Accesses
1 Citations
2 Altmetric
Metrics details
Physician bias refers to the unconscious negative perceptions that physicians have of patients or their conditions. Medical schools and residency programs often incorporate training to reduce biases among their trainees. In order to assess trends and organize available literature, we conducted a scoping review with a goal to categorize different biases that are studied within medical student (MS), resident (Res) and mixed populations (MS and Res). We also characterized these studies based on their research goal as either documenting evidence of bias (EOB), bias intervention (BI) or both. These findings will provide data which can be used to identify gaps and inform future work across these criteria.
Online databases (PubMed, PsycINFO, WebofScience) were searched for articles published between 1980 and 2021. All references were imported into Covidence for independent screening against inclusion criteria. Conflicts were resolved by deliberation. Studies were sorted by goal: ‘evidence of bias’ and/or ‘bias intervention’, and by population (MS or Res or mixed) andinto descriptive categories of bias.
Of the initial 806 unique papers identified, a total of 139 articles fit the inclusion criteria for data extraction. The included studies were sorted into 11 categories of bias and showed that bias against race/ethnicity, specific diseases/conditions, and weight were the most researched topics. Of the studies included, there was a higher ratio of EOB:BI studies at the MS level. While at the Res level, a lower ratio of EOB:BI was found.
Conclusions
This study will be of interest to institutions, program directors and medical educators who wish to specifically address a category of bias and identify where there is a dearth of research. This study also underscores the need to introduce bias interventions at the MS level.
Peer Review reports
Physician bias ultimately impacts patient care by eroding the physician–patient relationship [ 1 , 2 , 3 , 4 ]. To overcome this issue, certain states require physicians to report a varying number of hours of implicit bias training as part of their recurring licensing requirement [ 5 , 6 ]. Research efforts on the influence of implicit bias on clinical decision-making gained traction after the “Unequal Treatment: Confronting Racial and Ethnic Disparities in Health Care” report published in 2003 [ 7 ]. This report sparked a conversation about the impact of bias against women, people of color, and other marginalized groups within healthcare. Bias from a healthcare provider has been shown to affect provider-patient communication and may also influence treatment decisions [ 8 , 9 ]. Nevertheless, opportunities within medical education curriculum are created to evaluate biases at an earlier stage of physician-training and provide instruction to intervene them [ 10 , 11 , 12 ]. We aimed to identify trends and organize literature on bias training provided during medical school and residency programs since the meaning of ‘bias’ is broad and encompasses several types of attitudes and predispositions [ 13 ].
Several reviews, narrative or systematic in nature, have been published in the field of bias research in medicine and healthcare [ 14 , 15 , 16 ]. Many of these reviews have a broad focus on implicit bias and they often fail to define the patient’s specific attributes- such as age, weight, disease, or condition against which physicians hold their biases. However, two recently published reviews categorized implicit biases into various descriptive characteristics albeit with research goals different than this study [ 17 , 18 ]. The study by Fitzgerald et al. reviewed literature focused on bias among physicians and nurses to highlight its role in healthcare disparities [ 17 ]. While the study by Gonzalez et al. focused on bias curricular interventions across professions related to social determinants of health such as education, law, medicine and social work [ 18 ]. Our research goal was to identify the various bias characteristics that are studied within medical student and/or resident populations and categorize them. Further, we were interested in whether biases were merely identified or if they were intervened. To address these deficits in the field and provide clarity, we utilized a scoping review approach to categorize the literature based on a) the bias addressed and b) the study goal within medical students (MS), residents (Res) and a mixed population (MS and Res).
To date no literature review has organized bias research by specific categories held solely by medical trainees (medical students and/or residents) and quantified intervention studies. We did not perform a quality assessment or outcome evaluation of the bias intervention strategies, as it was not the goal of this work and is standard with a scoping review methodology [ 19 , 20 ]. By generating a comprehensive list of bias categories researched among medical trainee population, we highlight areas of opportunity for future implicit bias research specifically within the undergraduate and graduate medical education curriculum. We anticipate that the results from this scoping review will be useful for educators, administrators, and stakeholders seeking to implement active programs or workshops that intervene specific biases in pre-clinical medical education and prepare physicians-in-training for patient encounters. Additionally, behavioral scientists who seek to support clinicians, and develop debiasing theories [ 21 ] and models may also find our results informative.
We conducted an exhaustive and focused scoping review and followed the methodological framework for scoping reviews as previously described in the literature [ 20 , 22 ]. This study aligned with the four goals of a scoping review [ 20 ]. We followed the first five out of the six steps outlined by Arksey and O’Malley’s to ensure our review’s validity 1) identifying the research question 2) identifying relevant studies 3) selecting the studies 4) charting the data and 5) collating, summarizing and reporting the results [ 22 ]. We did not follow the optional sixth step of undertaking consultation with key stakeholders as it was not needed to address our research question it [ 23 ]. Furthermore, we used Covidence systematic review software (Veritas Health Innovation, Melbourne, Australia) that aided in managing steps 2–5 presented above.
Research question, search strategy and inclusion criteria
The purpose of this study was to identify trends in bias research at the medical school and residency level. Prior to conducting our literature search we developed our research question and detailed the inclusion criteria, and generated the search syntax with the assistance from a medical librarian. Search syntax was adjusted to the requirements of the database. We searched PubMed, Web of Science, and PsycINFO using MeSH terms shown below.
Bias* [ti] OR prejudice*[ti] OR racism[ti] OR homophobia[ti] OR mistreatment[ti] OR sexism[ti] OR ageism[ti]) AND (prejudice [mh] OR "Bias"[Mesh:NoExp]) AND (Education, Medical [mh] OR Schools, Medical [mh] OR students, medical [mh] OR Internship and Residency [mh] OR “undergraduate medical education” OR “graduate medical education” OR “medical resident” OR “medical residents” OR “medical residency” OR “medical residencies” OR “medical schools” OR “medical school” OR “medical students” OR “medical student”) AND (curriculum [mh] OR program evaluation [mh] OR program development [mh] OR language* OR teaching OR material* OR instruction* OR train* OR program* OR curricul* OR workshop*
Our inclusion criteria incorporated studies which were either original research articles, or review articles that synthesized new data. We excluded publications that were not peer-reviewed or supported with data such as narrative reviews, opinion pieces, editorials, perspectives and commentaries. We included studies outside of the U.S. since the purpose of this work was to generate a comprehensive list of biases. Physicians, regardless of their country of origin, can hold biases against specific patient attributes [ 17 ]. Furthermore, physicians may practice in a different country than where they trained [ 24 ]. Manuscripts were included if they were published in the English language for which full-texts were available. Since the goal of this scoping review was to assess trends, we accepted studies published from 1980–2021.
Our inclusion criteria also considered the goal and the population of the study. We defined the study goal as either that documented evidence of bias or a program directed bias intervention. Evidence of bias (EOB) had to originate from the medical trainee regarding a patient attribute. Bias intervention (BI) studies involved strategies to counter biases such as activities, workshops, seminars or curricular innovations. The population studied had to include medical students (MS) or residents (Res) or mixed. We defined the study population as ‘mixed’ when it consisted of both MS and Res. Studies conducted on other healthcare professionals were included if MS or Res were also studied. Our search criteria excluded studies that documented bias against medical professionals (students, residents and clinicians) either by patients, medical schools, healthcare administrators or others, and was focused on studies where the biases were solely held by medical trainees (MS and Res).
Data extraction and analysis
Following the initial database search, references were downloaded and bulk uploaded into Covidence and duplicates were removed. After the initial screening of title and abstracts, full-texts were reviewed. Authors independently completed title and abstract screening, and full text reviews. Any conflicts at the stage of abstract screening were moved to full-text screening. Conflicts during full-text screening were resolved by deliberation and referring to the inclusion and exclusion criteria detailed in the research protocol. The level of agreement between the two authors for full text reviews as measured by inter-rater reliability was 0.72 (Cohen’s Kappa).
A data extraction template was created in Covidence to extract data from included full texts. Data extraction template included the following variables; country in which the study was conducted, year of publication, goal of the study (EOB, BI or both), population of the study (MS, Res or mixed) and the type of bias studied. Final data was exported to Microsoft Excel for quantification. For charting our data and categorizing the included studies, we followed the Preferred Reporting Items for Systematic Reviews and Meta-Analyses extension for Scoping Reviews(PRISMA-ScR) guidelines [ 25 ]. Results from this scoping review study are meant to provide a visual synthesis of existing bias research and identify gaps in knowledge.
Study selection
Our search strategy yielded a total of 892 unique abstracts which were imported into ‘Covidence’ for screening. A total of 86 duplicate references were removed. Then, 806 titles and abstracts were screened for relevance independently by the authors and 519 studies were excluded at this stage. Any conflicts among the reviewers at this stage were resolved by discussion and referring to the inclusion and exclusion criteria. Then a full text review of the remaining 287 papers was completed by the authors against the inclusion criteria for eligibility. Full text review was also conducted independently by the authors and any conflicts were resolved upon discussion. Finally, we included 139 studies which were used for data extraction (Fig. 1 ).
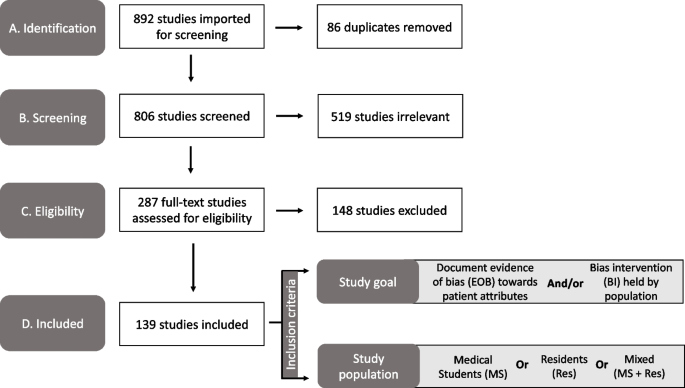
PRISMA diagram of the study selection process used in our scoping review to identify the bias categories that have been reported within medical education literature. Study took place from 2021–2022. Abbreviation: PRISMA, Preferred Reporting Items for Systematic Reviews and Meta-Analyses
Publication trends in bias research
First, we charted the studies to demonstrate the timeline of research focused on bias within the study population of our interest (MS or Res or mixed). Our analysis revealed an increase in publications with respect to time (Fig. 2 ). Of the 139 included studies, fewer studies were published prior to 2001, with a total of only eight papers being published from the years 1985–2000. A substantial increase in publications occurred after 2004, with 2019 being the peak year where most of the studies pertaining to bias were published (Fig. 2 ).
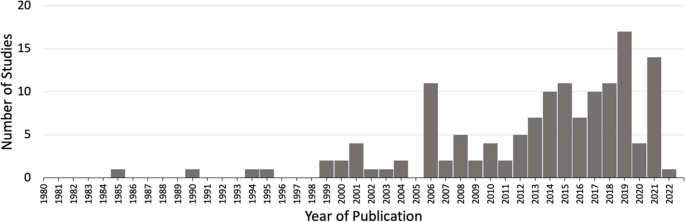
Studies matching inclusion criteria mapped by year of publication. Search criteria included studies addressing bias from 1980–2021 within medical students (MS) or residents (Res) or mixed (MS + Res) populations. * Publication in 2022 was published online ahead of print
Overview of included studies
We present a descriptive analysis of the 139 included studies in Table 1 based on the following parameters: study location, goal of the study, population of the study and the category of bias studied. All of the above parameters except the category of bias included a denominator of 139 studies. Several studies addressed more than one bias characteristic; therefore, we documented 163 biases sorted in 11 categories over the 139 papers. The bias categories that we generated and their respective occurrences are listed in Table 1 . Of the 139 studies that were included, most studies originated in the United States ( n = 89/139, 64%) and Europe ( n = 20/139, 20%).
Sorting of included research by bias category
We grouped the 139 included studies depending on the patient attribute or the descriptive characteristic against which the bias was studied (Table 1 ). By sorting the studies into different bias categories, we aimed to not only quantitate the amount of research addressing a particular topic of bias, but also reveal the biases that are understudied.
Through our analysis, we generated 11 descriptive categories against which bias was studied: Age, physical disability, education level, biological sex, disease or condition, LGBTQ + , non-specified, race/ethnicity, rural/urban, socio-economic status, and weight (Table 1 ). “Age” and “weight” categories included papers that studied bias against older population and higher weight individuals, respectively. The categories “education level” and “socio-economic status” included papers that studied bias against individuals with low education level and individuals belonging to low socioeconomic status, respectively. Within the bias category named ‘biological sex’, we included papers that studied bias against individuals perceived as women/females. Papers that studied bias against gender-identity or sexual orientation were included in its own category named, ‘LGBTQ + ’. The bias category, ‘disease or condition’ was broad and included research on bias against any patient with a specific disease, condition or lifestyle. Studies included in this category researched bias against any physical illnesses, mental illnesses, or sexually transmitted infections. It also included studies that addressed bias against a treatment such as transplant or pain management. It was not significant to report these as individual categories but rather as a whole with a common underlying theme. Rural/urban bias referred to bias that was held against a person based on their place of residence. Studies grouped together in the ‘non-specified bias’ category explored bias without specifying any descriptive characteristic in their methods. These studies did not address any specific bias characteristic in particular but consisted of a study population of our interest (MS or Res or mixed). Based on our analysis, the top five most studied bias categories in our included population within medical education literature were: racial or ethnic bias ( n = 39/163, 24%), disease or condition bias ( n = 29/163, 18%), weight bias ( n = 22/163, 13%), LGBTQ + bias ( n = 21/163, 13%), and age bias ( n = 16/163, 10%) which are presented in Table 1 .
Sorting of included research by population
In order to understand the distribution of bias research based on their populations examined, we sorted the included studies in one of the following: medical students (MS), residents (Res) or mixed (Table 1 ). The following distributions were observed: medical students only ( n = 105/139, 76%), residents only ( n = 19/139, 14%) or mixed which consisted of both medical students and residents ( n = 15/139, 11%). In combination, these results demonstrate that medical educators have focused bias research efforts primarily on medical student populations.
Sorting of included research by goal
A critical component of this scoping review was to quantify the research goal of the included studies within each of the bias categories. We defined the research goal as either to document evidence of bias (EOB) or to evaluate a bias intervention (BI) (see Fig. 1 for inclusion criteria). Some of the included studies focused on both, documenting evidence in addition to intervening biases and those studies were grouped separately. The analysis revealed that 69/139 (50%) of the included studies focused exclusively on documenting evidence of bias (EOB). There were fewer studies ( n = 51/139, 37%) which solely focused on bias interventions such as programs, seminars or curricular innovations. A small minority of the included studies were more comprehensive in that they documented EOB followed by an intervention strategy ( n = 19/139, 11%). These results demonstrate that most bias research is dedicated to documenting evidence of bias among these groups rather than evaluating a bias intervention strategy.
Research goal distribution
Our next objective was to calculate the distribution of studies with respect to the study goal (EOB, BI or both), within the 163 biases studied across the 139 papers as calculated in Table 1 . In general, the goal of the studies favors documenting evidence of bias with the exception of race/ethnic bias which is more focused on bias intervention (Fig. 3 ). Fewer studies were aimed at both, documenting evidence then providing an intervention, across all bias categories.
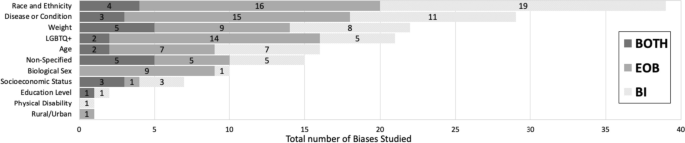
Sorting of total biases ( n = 163) within medical students or residents or a mixed population based on the bias category . Dark grey indicates studies with a dual goal, to document evidence of bias and to intervene bias. Medium grey bars indicate studies which focused on documenting evidence of bias. Light grey bars indicate studies focused on bias intervention within these populations. Numbers inside the bars indicate the total number of biases for the respective study goal. * Non-specified bias includes studies which focused on implicit bias but did not mention the type of bias investigated
Furthermore, we also calculated the ratio of EOB, BI and both (EOB + BI) within each of our population of interest (MS; n = 122, Res; n = 26 and mixed; n = 15) for the 163 biases observed in our included studies. Over half ( n = 64/122, 52%) of the total bias occurrences in MS were focused on documenting EOB (Fig. 4 ). Contrastingly, a shift was observed within resident populations where most biases addressed were aimed at intervention ( n = 12/26, 41%) rather than EOB ( n = 4/26, 14%) (Fig. 4 ). Studies which included both MS and Res (mixed) were primarily focused on documenting EOB ( n = 9/15, 60%), with 33% ( n = 5/15) aimed at bias intervention and 7% ( n = 1/15) which did both (Fig. 4 ). Although far fewer studies were documented in the Res population it is important to highlight that most of these studies were focused on bias intervention when compared to MS population where we documented a majority of studies focused on evidence of bias.
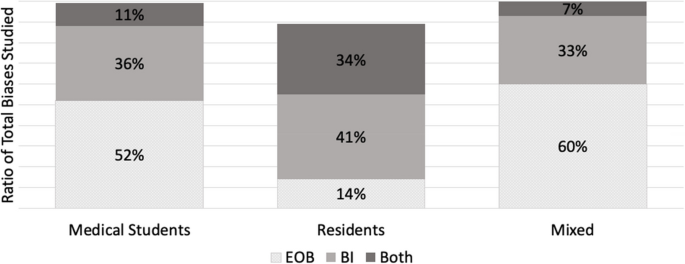
A ratio of the study goal for the total biases ( n = 163) mapped within each of the study population (MS, Res and Mixed). A study goal with a) documenting evidence of bias (EOB) is depicted in dotted grey, b) bias intervention (BI) in medium grey, and c) a dual focus (EOB + BI) is depicted in dark grey. * N = 122 for medical student studies. b N = 26 for residents. c N = 15 for mixed
Addressing biases at an earlier stage of medical career is critical for future physicians engaging with diverse patients, since it is established that bias negatively influences provider-patient interactions [ 171 ], clinical decision-making [ 172 ] and reduces favorable treatment outcomes [ 2 ]. We set out with an intention to explore how bias is addressed within the medical curriculum. Our research question was: how has the trend in bias research changed over time, more specifically a) what is the timeline of papers published? b) what bias characteristics have been studied in the physician-trainee population and c) how are these biases addressed? With the introduction of ‘standards of diversity’ by the Liaison Committee on Medical Education, along with the Association of American Medical Colleges (AAMC) and the American Medical Association (AMA) [ 173 , 174 ], we certainly expected and observed a sustained uptick in research pertaining to bias. As shown here, research addressing bias in the target population (MS and Res) is on the rise, however only 139 papers fit our inclusion criteria. Of these studies, nearly 90% have been published since 2005 after the “Unequal Treatment: Confronting Racial and Ethnic Disparities in Health Care” report was published in 2003 [ 7 ]. However, given the well documented effects of physician held bias, we anticipated significantly more number of studies focused on bias at the medical student or resident level.
A key component from this study was that we generated descriptive categories of biases. Sorting the biases into descriptive categories helps to identify a more targeted approach for a specific bias intervention, rather than to broadly intervene bias as a whole. In fact, our analysis found a number of publications (labeled “non-specified bias” in Table 1 ) which studied implicit bias without specifying the patient attribute or the characteristic that the bias was against. In total, we generated 11 descriptive categories of bias from our scoping review which are shown in Table 1 and Fig. 3 . Furthermore, our bias descriptors grouped similar kinds of biases within a single category. For example, the category, “disease or condition” included papers that studied bias against any type of disease (Mental illness, HIV stigma, diabetes), condition (Pain management), or lifestyle. We neither performed a qualitative assessment of the studies nor did we test the efficacy of the bias intervention studies and consider it a future direction of this work.
Evidence suggests that medical educators and healthcare professionals are struggling to find the appropriate approach to intervene biases [ 175 , 176 , 177 ] So far, bias reduction, bias reflection and bias management approaches have been proposed [ 26 , 27 , 178 ]. Previous implicit bias intervention strategies have been shown to be ineffective when biased attitudes of participants were assessed after a lag [ 179 ]. Understanding the descriptive categories of bias and previous existing research efforts, as we present here is only a fraction of the challenge. The theory of “cognitive bias” [ 180 ] and related branches of research [ 13 , 181 , 182 , 183 , 184 ] have been studied in the field of psychology for over three decades. It is only recently that cognitive bias theory has been applied to the field of medical education medicine, to explain its negative influence on clinical decision-making pertaining only to racial minorities [ 1 , 2 , 15 , 16 , 17 , 185 ]. In order to elicit meaningful changes with respect to targeted bias intervention, it is necessary to understand the psychological underpinnings (attitudes) leading to a certain descriptive category of bias (behaviors). The questions which medical educators need to ask are: a) Can these descriptive biases be identified under certain type/s of cognitive errors that elicits the bias and vice versa b) Are we working towards an attitude change which can elicit a sustained positive behavior change among healthcare professionals? And most importantly, c) are we creating a culture where participants voluntarily enroll themselves in bias interventions as opposed to being mandated to participate? Cognitive psychologists and behavioral scientists are well-positioned to help us find answers to these questions as they understand human behavior. Therefore, an interdisciplinary approach, a marriage between cognitive psychologists and medical educators, is key in targeting biases held by medical students, residents, and ultimately future physicians. This review may also be of interest to behavioral psychologists, keen on providing targeted intervening strategies to clinicians depending on the characteristics (age, weight, sex or race) the portrayed bias is against. Further, instead of an individualized approach, we need to strive for systemic changes and evidence-based strategies to intervene biases.
The next element in change is directing intervention strategies at the right stage in clinical education. Our study demonstrated that most of the research collected at the medical student level was focused on documenting evidence of bias. Although the overall number of studies at the resident level were fewer than at the medical student level, the ratio of research in favor of bias intervention was higher at the resident level (see Fig. 3 ). However, it could be helpful to focus on bias intervention earlier in learning, rather than at a later stage [ 186 ]. Additionally, educational resources such as textbooks, preparatory materials, and educators themselves are potential sources of propagating biases and therefore need constant evaluation against best practices [ 187 , 188 ].
This study has limitations. First, the list of the descriptive bias categories that we generated was not grounded in any particular theory so assigning a category was subjective. Additionally, there were studies that were categorized as “nonspecified” bias as the studies themselves did not mention the specific type of bias that they were addressing. Moreover, we had to exclude numerous publications solely because they were not evidence-based and were either perspectives, commentaries or opinion pieces. Finally, there were overall fewer studies focused on the resident population, so the calculated ratio of MS:Res studies did not compare similar sample sizes.
Future directions of our study include working with behavioral scientists to categorize these bias characteristics (Table 1 ) into cognitive error types [ 189 ]. Additionally, we aim to assess the effectiveness of the intervention strategies and categorize the approach of the intervention strategies.
The primary goal of our review was to organize, compare and quantify literature pertaining to bias within medical school curricula and residency programs. We neither performed a qualitative assessment of the studies nor did we test the efficacy of studies that were sorted into “bias intervention” as is typical of scoping reviews [ 22 ]. In summary, our research identified 11 descriptive categories of biases studied within medical students and resident populations with “race and ethnicity”, “disease or condition”, “weight”, “LGBTQ + ” and “age” being the top five most studied biases. Additionally, we found a greater number of studies conducted in medical students (105/139) when compared to residents (19/139). However, most of the studies in the resident population focused on bias intervention. The results from our review highlight the following gaps: a) bias categories where more research is needed, b) biases that are studied within medical school versus in residency programs and c) study focus in terms of demonstrating the presence of bias or working towards bias intervention.
This review provides a visual analysis of the known categories of bias addressed within the medical school curriculum and in residency programs in addition to providing a comparison of studies with respect to the study goal within medical education literature. The results from our review should be of interest to community organizations, institutions, program directors and medical educators interested in knowing and understanding the types of bias existing within healthcare populations. It might be of special interest to researchers who wish to explore other types of biases that have been understudied within medical school and resident populations, thus filling the gaps existing in bias research.
Despite the number of studies designed to provide bias intervention for MS and Res populations, and an overall cultural shift to be aware of one’s own biases, biases held by both medical students and residents still persist. Further, psychologists have recently demonstrated the ineffectiveness of some bias intervention efforts [ 179 , 190 ]. Therefore, it is perhaps unrealistic to expect these biases to be eliminated altogether. However, effective intervention strategies grounded in cognitive psychology should be implemented earlier on in medical training. Our focus should be on providing evidence-based approaches and safe spaces for an attitude and culture change, so as to induce actionable behavioral changes.
Availability of data and materials
The datasets used and/or analyzed during the current study are available from the corresponding author upon reasonable request.
Abbreviations
- Medical student
Evidence of bias
- Bias intervention
Hagiwara N, Mezuk B, Elston Lafata J, Vrana SR, Fetters MD. Study protocol for investigating physician communication behaviours that link physician implicit racial bias and patient outcomes in Black patients with type 2 diabetes using an exploratory sequential mixed methods design. BMJ Open. 2018;8(10):e022623.
Article Google Scholar
Haider AH, Schneider EB, Sriram N, Dossick DS, Scott VK, Swoboda SM, Losonczy L, Haut ER, Efron DT, Pronovost PJ, et al. Unconscious race and social class bias among acute care surgical clinicians and clinical treatment decisions. JAMA Surg. 2015;150(5):457–64.
Penner LA, Dovidio JF, Gonzalez R, Albrecht TL, Chapman R, Foster T, Harper FW, Hagiwara N, Hamel LM, Shields AF, et al. The effects of oncologist implicit racial bias in racially discordant oncology interactions. J Clin Oncol. 2016;34(24):2874–80.
Phelan SM, Burgess DJ, Yeazel MW, Hellerstedt WL, Griffin JM, van Ryn M. Impact of weight bias and stigma on quality of care and outcomes for patients with obesity. Obes Rev. 2015;16(4):319–26.
Garrett SB, Jones L, Montague A, Fa-Yusuf H, Harris-Taylor J, Powell B, Chan E, Zamarripa S, Hooper S, Chambers Butcher BD. Challenges and opportunities for clinician implicit bias training: insights from perinatal care stakeholders. Health Equity. 2023;7(1):506–19.
Shah HS, Bohlen J. Implicit bias. In: StatPearls. Treasure Island (FL): StatPearls Publishing; 2023. Copyright © 2023, StatPearls Publishing LLC.
Google Scholar
Institute of Medicine (US) Committee on Understanding and Eliminating Racial and Ethnic Disparities in Health Care. Unequal Treatment: Confronting Racial and Ethnic Disparities in Health Care. In: Smedley BD, Stith AY, Nelson AR, editors. Washington (DC): National Academies Press (US); 2003. PMID: 25032386.
Dehon E, Weiss N, Jones J, Faulconer W, Hinton E, Sterling S. A systematic review of the impact of physician implicit racial bias on clinical decision making. Acad Emerg Med. 2017;24(8):895–904.
Oliver MN, Wells KM, Joy-Gaba JA, Hawkins CB, Nosek BA. Do physicians’ implicit views of African Americans affect clinical decision making? J Am Board Fam Med. 2014;27(2):177–88.
Rincon-Subtirelu M. Education as a tool to modify anti-obesity bias among pediatric residents. Int J Med Educ. 2017;8:77–8.
Gustafsson Sendén M, Renström EA. Gender bias in assessment of future work ability among pain patients - an experimental vignette study of medical students’ assessment. Scand J Pain. 2019;19(2):407–14.
Hardeman RR, Burgess D, Phelan S, Yeazel M, Nelson D, van Ryn M. Medical student socio-demographic characteristics and attitudes toward patient centered care: do race, socioeconomic status and gender matter? A report from the medical student CHANGES study. Patient Educ Couns. 2015;98(3):350–5.
Greenwald AG, Banaji MR. Implicit social cognition: attitudes, self-esteem, and stereotypes. Psychol Rev. 1995;102(1):4–27.
Kruse JA, Collins JL, Vugrin M. Educational strategies used to improve the knowledge, skills, and attitudes of health care students and providers regarding implicit bias: an integrative review of the literature. Int J Nurs Stud Adv. 2022;4:100073.
Zestcott CA, Blair IV, Stone J. Examining the presence, consequences, and reduction of implicit bias in health care: a narrative review. Group Process Intergroup Relat. 2016;19(4):528–42.
Hall WJ, Chapman MV, Lee KM, Merino YM, Thomas TW, Payne BK, Eng E, Day SH, Coyne-Beasley T. Implicit racial/ethnic bias among health care professionals and its influence on health care outcomes: a systematic review. Am J Public Health. 2015;105(12):E60–76.
FitzGerald C, Hurst S. Implicit bias in healthcare professionals: a systematic review. BMC Med Ethics. 2017;18(1):19.
Gonzalez CM, Onumah CM, Walker SA, Karp E, Schwartz R, Lypson ML. Implicit bias instruction across disciplines related to the social determinants of health: a scoping review. Adv Health Sci Educ. 2023;28(2):541–87.
Pham MT, Rajić A, Greig JD, Sargeant JM, Papadopoulos A, McEwen SA. A scoping review of scoping reviews: advancing the approach and enhancing the consistency. Res Synth Methods. 2014;5(4):371–85.
Levac D, Colquhoun H, O’Brien KK. Scoping studies: advancing the methodology. Implement Sci. 2010;5:69.
Pat C, Geeta S, Sílvia M. Cognitive debiasing 1: origins of bias and theory of debiasing. BMJ Qual Saf. 2013;22(Suppl 2):ii58.
Arksey H, O’Malley L. Scoping studies: towards a methodological framework. Int J Soc Res Methodol. 2005;8(1):19–32.
Thomas A, Lubarsky S, Durning SJ, Young ME. Knowledge syntheses in medical education: demystifying scoping reviews. Acad Med. 2017;92(2):161–6.
Hagopian A, Thompson MJ, Fordyce M, Johnson KE, Hart LG. The migration of physicians from sub-Saharan Africa to the United States of America: measures of the African brain drain. Hum Resour Health. 2004;2(1):17.
Tricco AC, Lillie E, Zarin W, O’Brien KK, Colquhoun H, Levac D, Moher D, Peters MDJ, Horsley T, Weeks L, et al. PRISMA Extension for Scoping Reviews (PRISMA-ScR): checklist and explanation. Ann Intern Med. 2018;169(7):467–73.
Teal CR, Shada RE, Gill AC, Thompson BM, Frugé E, Villarreal GB, Haidet P. When best intentions aren’t enough: Helping medical students develop strategies for managing bias about patients. J Gen Intern Med. 2010;25(Suppl 2):S115–8.
Gonzalez CM, Walker SA, Rodriguez N, Noah YS, Marantz PR. Implicit bias recognition and management in interpersonal encounters and the learning environment: a skills-based curriculum for medical students. MedEdPORTAL. 2021;17:11168.
Hoffman KM, Trawalter S, Axt JR, Oliver MN. Racial bias in pain assessment and treatment recommendations, and false beliefs about biological differences between blacks and whites. Proc Natl Acad Sci U S A. 2016;113(16):4296–301.
Mayfield JJ, Ball EM, Tillery KA, Crandall C, Dexter J, Winer JM, Bosshardt ZM, Welch JH, Dolan E, Fancovic ER, et al. Beyond men, women, or both: a comprehensive, LGBTQ-inclusive, implicit-bias-aware, standardized-patient-based sexual history taking curriculum. MedEdPORTAL. 2017;13:10634.
Morris M, Cooper RL, Ramesh A, Tabatabai M, Arcury TA, Shinn M, Im W, Juarez P, Matthews-Juarez P. Training to reduce LGBTQ-related bias among medical, nursing, and dental students and providers: a systematic review. BMC Med Educ. 2019;19(1):325.
Perdomo J, Tolliver D, Hsu H, He Y, Nash KA, Donatelli S, Mateo C, Akagbosu C, Alizadeh F, Power-Hays A, et al. Health equity rounds: an interdisciplinary case conference to address implicit bias and structural racism for faculty and trainees. MedEdPORTAL. 2019;15:10858.
Sherman MD, Ricco J, Nelson SC, Nezhad SJ, Prasad S. Implicit bias training in a residency program: aiming for enduring effects. Fam Med. 2019;51(8):677–81.
van Ryn M, Hardeman R, Phelan SM, Burgess DJ, Dovidio JF, Herrin J, Burke SE, Nelson DB, Perry S, Yeazel M, et al. Medical school experiences associated with change in implicit racial bias among 3547 students: a medical student CHANGES study report. J Gen Intern Med. 2015;30(12):1748–56.
Chary AN, Molina MF, Dadabhoy FZ, Manchanda EC. Addressing racism in medicine through a resident-led health equity retreat. West J Emerg Med. 2020;22(1):41–4.
DallaPiazza M, Padilla-Register M, Dwarakanath M, Obamedo E, Hill J, Soto-Greene ML. Exploring racism and health: an intensive interactive session for medical students. MedEdPORTAL. 2018;14:10783.
Dennis SN, Gold RS, Wen FK. Learner reactions to activities exploring racism as a social determinant of health. Fam Med. 2019;51(1):41–7.
Gonzalez CM, Walker SA, Rodriguez N, Karp E, Marantz PR. It can be done! a skills-based elective in implicit bias recognition and management for preclinical medical students. Acad Med. 2020;95(12S Addressing Harmful Bias and Eliminating Discrimination in Health Professions Learning Environments):S150–5.
Motzkus C, Wells RJ, Wang X, Chimienti S, Plummer D, Sabin J, Allison J, Cashman S. Pre-clinical medical student reflections on implicit bias: Implications for learning and teaching. PLoS ONE. 2019;14(11):e0225058.
Phelan SM, Burke SE, Cunningham BA, Perry SP, Hardeman RR, Dovidio JF, Herrin J, Dyrbye LN, White RO, Yeazel MW, et al. The effects of racism in medical education on students’ decisions to practice in underserved or minority communities. Acad Med. 2019;94(8):1178–89.
Zeidan A, Tiballi A, Woodward M, Di Bartolo IM. Targeting implicit bias in medicine: lessons from art and archaeology. West J Emerg Med. 2019;21(1):1–3.
Baker TK, Smith GS, Jacobs NN, Houmanfar R, Tolles R, Kuhls D, Piasecki M. A deeper look at implicit weight bias in medical students. Adv Health Sci Educ Theory Pract. 2017;22(4):889–900.
Eymard AS, Douglas DH. Ageism among health care providers and interventions to improve their attitudes toward older adults: an integrative review. J Gerontol Nurs. 2012;38(5):26–35.
Garrison CB, McKinney-Whitson V, Johnston B, Munroe A. Race matters: addressing racism as a health issue. Int J Psychiatry Med. 2018;53(5–6):436–44.
Geller G, Watkins PA. Addressing medical students’ negative bias toward patients with obesity through ethics education. AMA J Ethics. 2018;20(10):E948-959.
Onyeador IN, Wittlin NM, Burke SE, Dovidio JF, Perry SP, Hardeman RR, Dyrbye LN, Herrin J, Phelan SM, van Ryn M. The value of interracial contact for reducing anti-black bias among non-black physicians: a Cognitive Habits and Growth Evaluation (CHANGE) study report. Psychol Sci. 2020;31(1):18–30.
Poustchi Y, Saks NS, Piasecki AK, Hahn KA, Ferrante JM. Brief intervention effective in reducing weight bias in medical students. Fam Med. 2013;45(5):345–8.
Ruiz JG, Andrade AD, Anam R, Taldone S, Karanam C, Hogue C, Mintzer MJ. Group-based differences in anti-aging bias among medical students. Gerontol Geriatr Educ. 2015;36(1):58–78.
Simpson T, Evans J, Goepfert A, Elopre L. Implementing a graduate medical education anti-racism workshop at an academic university in the Southern USA. Med Educ Online. 2022;27(1):1981803.
Wittlin NM, Dovidio JF, Burke SE, Przedworski JM, Herrin J, Dyrbye L, Onyeador IN, Phelan SM, van Ryn M. Contact and role modeling predict bias against lesbian and gay individuals among early-career physicians: a longitudinal study. Soc Sci Med. 2019;238:112422.
Miller DP Jr, Spangler JG, Vitolins MZ, Davis SW, Ip EH, Marion GS, Crandall SJ. Are medical students aware of their anti-obesity bias? Acad Med. 2013;88(7):978–82.
Gonzalez CM, Deno ML, Kintzer E, Marantz PR, Lypson ML, McKee MD. A qualitative study of New York medical student views on implicit bias instruction: implications for curriculum development. J Gen Intern Med. 2019;34(5):692–8.
Gonzalez CM, Kim MY, Marantz PR. Implicit bias and its relation to health disparities: a teaching program and survey of medical students. Teach Learn Med. 2014;26(1):64–71.
Gonzalez CM, Nava S, List J, Liguori A, Marantz PR. How assumptions and preferences can affect patient care: an introduction to implicit bias for first-year medical students. MedEdPORTAL. 2021;17:11162.
Hernandez RA, Haidet P, Gill AC, Teal CR. Fostering students’ reflection about bias in healthcare: cognitive dissonance and the role of personal and normative standards. Med Teach. 2013;35(4):e1082-1089.
Kushner RF, Zeiss DM, Feinglass JM, Yelen M. An obesity educational intervention for medical students addressing weight bias and communication skills using standardized patients. BMC Med Educ. 2014;14:53.
Nazione S, Silk KJ. Patient race and perceived illness responsibility: effects on provider helping and bias. Med Educ. 2013;47(8):780–9.
Ogunyemi D. Defeating unconscious bias: the role of a structured, reflective, and interactive workshop. J Grad Med Educ. 2021;13(2):189–94.
Phelan SM, Burke SE, Hardeman RR, White RO, Przedworski J, Dovidio JF, Perry SP, Plankey M, A Cunningham B, Finstad D, et al. Medical school factors associated with changes in implicit and explicit bias against gay and lesbian people among 3492 graduating medical students. J Gen Intern Med. 2017;32(11):1193–201.
Phelan SM, Puhl RM, Burke SE, Hardeman R, Dovidio JF, Nelson DB, Przedworski J, Burgess DJ, Perry S, Yeazel MW, et al. The mixed impact of medical school on medical students’ implicit and explicit weight bias. Med Educ. 2015;49(10):983–92.
Barber Doucet H, Ward VL, Johnson TJ, Lee LK. Implicit bias and caring for diverse populations: pediatric trainee attitudes and gaps in training. Clin Pediatr (Phila). 2021;60(9–10):408–17.
Burke SE, Dovidio JF, Przedworski JM, Hardeman RR, Perry SP, Phelan SM, Nelson DB, Burgess DJ, Yeazel MW, van Ryn M. Do contact and empathy mitigate bias against gay and lesbian people among heterosexual first-year medical students? A report from the medical student CHANGE study. Acad Med. 2015;90(5):645–51.
Johnston B, McKinney-Whitson V, Garrison V. Race matters: addressing racism as a health issue. WMJ. 2021;120(S1):S74–7.
Kost A, Akande T, Jones R, Gabert R, Isaac M, Dettmar NS. Use of patient identifiers at the University of Washington School of Medicine: building institutional consensus to reduce bias and stigma. Fam Med. 2021;53(5):366–71.
Madan AK, Aliabadi-Wahle S, Beech DJ. Ageism in medical students’ treatment recommendations: the example of breast-conserving procedures. Acad Med. 2001;76(3):282–4.
Marbin J, Lewis L, Kuo AK, Schudel C, Gutierrez JR. The power of place: travel to explore structural racism and health disparities. Acad Med. 2021;96(11):1569–73.
Phelan SM, Dovidio JF, Puhl RM, Burgess DJ, Nelson DB, Yeazel MW, Hardeman R, Perry S, van Ryn M. Implicit and explicit weight bias in a national sample of 4,732 medical students: the medical student CHANGES study. Obesity (Silver Spring). 2014;22(4):1201–8.
Van J, Aloman C, Reau N. Potential bias and misconceptions in liver transplantation for alcohol- and obesity-related liver disease. Am J Gastroenterol. 2021;116(10):2089–97.
White-Means S, Zhiyong D, Hufstader M, Brown LT. Cultural competency, race, and skin tone bias among pharmacy, nursing, and medical students: implications for addressing health disparities. Med Care Res Rev. 2009;66(4):436–55.
Williams RL, Vasquez CE, Getrich CM, Kano M, Boursaw B, Krabbenhoft C, Sussman AL. Racial/gender biases in student clinical decision-making: a mixed-method study of medical school attributes associated with lower incidence of biases. J Gen Intern Med. 2018;33(12):2056–64.
Cohen RW, Persky S. Influence of weight etiology information and trainee characteristics on physician-trainees’ clinical and interpersonal communication. Patient Educ Couns. 2019;102(9):1644–9.
Haider AH, Sexton J, Sriram N, Cooper LA, Efron DT, Swoboda S, Villegas CV, Haut ER, Bonds M, Pronovost PJ, et al. Association of unconscious race and social class bias with vignette-based clinical assessments by medical students. JAMA. 2011;306(9):942–51.
Lewis R, Lamdan RM, Wald D, Curtis M. Gender bias in the diagnosis of a geriatric standardized patient: a potential confounding variable. Acad Psychiatry. 2006;30(5):392–6.
Matharu K, Shapiro JF, Hammer RR, Kravitz RL, Wilson MD, Fitzgerald FT. Reducing obesity prejudice in medical education. Educ Health. 2014;27(3):231–7.
McLean ME, McLean LE, McLean-Holden AC, Campbell LF, Horner AM, Kulkarni ML, Melville LD, Fernandez EA. Interphysician weight bias: a cross-sectional observational survey study to guide implicit bias training in the medical workplace. Acad Emerg Med. 2021;28(9):1024–34.
Meadows A, Higgs S, Burke SE, Dovidio JF, van Ryn M, Phelan SM. Social dominance orientation, dispositional empathy, and need for cognitive closure moderate the impact of empathy-skills training, but not patient contact, on medical students’ negative attitudes toward higher-weight patients. Front Psychol. 2017;8:15.
Stone J, Moskowitz GB, Zestcott CA, Wolsiefer KJ. Testing active learning workshops for reducing implicit stereotyping of Hispanics by majority and minority group medical students. Stigma Health. 2020;5(1):94–103.
Symons AB, Morley CP, McGuigan D, Akl EA. A curriculum on care for people with disabilities: effects on medical student self-reported attitudes and comfort level. Disabil Health J. 2014;7(1):88–95.
Ufomata E, Eckstrand KL, Hasley P, Jeong K, Rubio D, Spagnoletti C. Comprehensive internal medicine residency curriculum on primary care of patients who identify as LGBT. LGBT Health. 2018;5(6):375–80.
Aultman JM, Borges NJ. A clinical and ethical investigation of pre-medical and medical students’ attitudes, knowledge, and understanding of HIV. Med Educ Online. 2006;11:1–12.
Bates T, Cohan M, Bragg DS, Bedinghaus J. The Medical College of Wisconsin senior mentor program: experience of a lifetime. Gerontol Geriatr Educ. 2006;27(2):93–103.
Chiaramonte GR, Friend R. Medical students’ and residents’ gender bias in the diagnosis, treatment, and interpretation of coronary heart disease symptoms. Health Psychol. 2006;25(3):255–66.
Friedberg F, Sohl SJ, Halperin PJ. Teaching medical students about medically unexplained illnesses: a preliminary study. Med Teach. 2008;30(6):618–21.
Gonzales E, Morrow-Howell N, Gilbert P. Changing medical students’ attitudes toward older adults. Gerontol Geriatr Educ. 2010;31(3):220–34.
Hinners CK, Potter JF. A partnership between the University of Nebraska College of Medicine and the community: fostering positive attitudes towards the aged. Gerontol Geriatr Educ. 2006;27(2):83–91.
Lee M, Coulehan JL. Medical students’ perceptions of racial diversity and gender equality. Med Educ. 2006;40(7):691–6.
Schmetzer AD, Lafuze JE. Overcoming stigma: involving families in medical student and psychiatric residency education. Acad Psychiatry. 2008;32(2):127–31.
Willen SS, Bullon A, Good MJD. Opening up a huge can of worms: reflections on a “cultural sensitivity” course for psychiatry residents. Harv Rev Psychiatry. 2010;18(4):247–53.
Dogra N, Karnik N. First-year medical students’ attitudes toward diversity and its teaching: an investigation at one U.S. medical school. Acad Med. 2003;78(11):1191–200.
Fitzpatrick C, Musser A, Mosqueda L, Boker J, Prislin M. Student senior partnership program: University of California Irvine School of Medicine. Gerontol Geriatr Educ. 2006;27(2):25–35.
Hoffman KG, Gray P, Hosokawa MC, Zweig SC. Evaluating the effectiveness of a senior mentor program: the University of Missouri-Columbia School of Medicine. Gerontol Geriatr Educ. 2006;27(2):37–47.
Kantor BS, Myers MR. From aging…to saging-the Ohio State Senior Partners Program: longitudinal and experiential geriatrics education. Gerontol Geriatr Educ. 2006;27(2):69–74.
Klamen DL, Grossman LS, Kopacz DR. Medical student homophobia. J Homosex. 1999;37(1):53–63.
Kopacz DR, Grossman LS, Klamen DL. Medical students and AIDS: knowledge, attitudes and implications for education. Health Educ Res. 1999;14(1):1–6.
Leiblum SR. An established medical school human sexuality curriculum: description and evaluation. Sex Relatsh Ther. 2001;16(1):59–70.
Rastegar DA, Fingerhood MI, Jasinski DR. A resident clerkship that combines inpatient and outpatient training in substance abuse and HIV care. Subst Abuse. 2004;25(4):11–5.
Roberts E, Richeson NA, Thornhill JTIV, Corwin SJ, Eleazer GP. The senior mentor program at the University of South Carolina School of Medicine: an innovative geriatric longitudinal curriculum. Gerontol Geriatr Educ. 2006;27(2):11–23.
Burgess DJ, Burke SE, Cunningham BA, Dovidio JF, Hardeman RR, Hou YF, Nelson DB, Perry SP, Phelan SM, Yeazel MW, et al. Medical students’ learning orientation regarding interracial interactions affects preparedness to care for minority patients: a report from medical student CHANGES. BMC Med Educ. 2016;16:254.
Burgess DJ, Hardeman RR, Burke SE, Cunningham BA, Dovidio JF, Nelson DB, Perry SP, Phelan SM, Yeazel MW, Herrin J, et al. Incoming medical students’ political orientation affects outcomes related to care of marginalized groups: results from the medical student CHANGES study. J Health Pol Policy Law. 2019;44(1):113–46.
Kurtz ME, Johnson SM, Tomlinson T, Fiel NJ. Teaching medical students the effects of values and stereotyping on the doctor/patient relationship. Soc Sci Med. 1985;21(9):1043–7.
Matharu K, Kravitz RL, McMahon GT, Wilson MD, Fitzgerald FT. Medical students’ attitudes toward gay men. BMC Med Educ. 2012;12:71.
Pearl RL, Argueso D, Wadden TA. Effects of medical trainees’ weight-loss history on perceptions of patients with obesity. Med Educ. 2017;51(8):802–11.
Perry SP, Dovidio JF, Murphy MC, van Ryn M. The joint effect of bias awareness and self-reported prejudice on intergroup anxiety and intentions for intergroup contact. Cultur Divers Ethnic Minor Psychol. 2015;21(1):89–96.
Phelan SM, Burgess DJ, Burke SE, Przedworski JM, Dovidio JF, Hardeman R, Morris M, van Ryn M. Beliefs about the causes of obesity in a national sample of 4th year medical students. Patient Educ Couns. 2015;98(11):1446–9.
Phelan SM, Puhl RM, Burgess DJ, Natt N, Mundi M, Miller NE, Saha S, Fischer K, van Ryn M. The role of weight bias and role-modeling in medical students’ patient-centered communication with higher weight standardized patients. Patient Educ Couns. 2021;104(8):1962–9.
Polan HJ, Auerbach MI, Viederman M. AIDS as a paradigm of human behavior in disease: impact and implications of a course. Acad Psychiatry. 1990;14(4):197–203.
Reuben DB, Fullerton JT, Tschann JM, Croughan-Minihane M. Attitudes of beginning medical students toward older persons: a five-campus study. J Am Geriatr Soc. 1995;43(12):1430–6.
Tsai J. Building structural empathy to marshal critical education into compassionate practice: evaluation of a medical school critical race theory course. J Law Med Ethics. 2021;49(2):211–21.
Weyant RJ, Bennett ME, Simon M, Palaisa J. Desire to treat HIV-infected patients: similarities and differences across health-care professions. AIDS. 1994;8(1):117–21.
Ross PT, Lypson ML. Using artistic-narrative to stimulate reflection on physician bias. Teach Learn Med. 2014;26(4):344–9.
Calabrese SK, Earnshaw VA, Krakower DS, Underhill K, Vincent W, Magnus M, Hansen NB, Kershaw TS, Mayer KH, Betancourt JR, et al. A closer look at racism and heterosexism in medical students’ clinical decision-making related to HIV Pre-Exposure Prophylaxis (PrEP): implications for PrEP education. AIDS Behav. 2018;22(4):1122–38.
Fitterman-Harris HF, Vander Wal JS. Weight bias reduction among first-year medical students: a quasi-randomized, controlled trial. Clin Obes. 2021;11(6):e12479.
Madan AK, Cooper L, Gratzer A, Beech DJ. Ageism in breast cancer surgical options by medical students. Tenn Med. 2006;99(5):37–8, 41.
Bikmukhametov DA, Anokhin VA, Vinogradova AN, Triner WR, McNutt LA. Bias in medicine: a survey of medical student attitudes towards HIV-positive and marginalized patients in Russia, 2010. J Int AIDS Soc. 2012;15(2):17372.
Dijkstra AF, Verdonk P, Lagro-Janssen AL. Gender bias in medical textbooks: examples from coronary heart disease, depression, alcohol abuse and pharmacology. Med Educ. 2008;42(10):1021–8.
Dobrowolska B, Jędrzejkiewicz B, Pilewska-Kozak A, Zarzycka D, Ślusarska B, Deluga A, Kościołek A, Palese A. Age discrimination in healthcare institutions perceived by seniors and students. Nurs Ethics. 2019;26(2):443–59.
Hamberg K, Risberg G, Johansson EE, Westman G. Gender bias in physicians’ management of neck pain: a study of the answers in a Swedish national examination. J Womens Health Gend Based Med. 2002;11(7):653–66.
Magliano L, Read J, Sagliocchi A, Oliviero N, D’Ambrosio A, Campitiello F, Zaccaro A, Guizzaro L, Patalano M. “Social dangerousness and incurability in schizophrenia”: results of an educational intervention for medical and psychology students. Psychiatry Res. 2014;219(3):457–63.
Reis SP, Wald HS. Contemplating medicine during the Third Reich: scaffolding professional identity formation for medical students. Acad Med. 2015;90(6):770–3.
Schroyen S, Adam S, Marquet M, Jerusalem G, Thiel S, Giraudet AL, Missotten P. Communication of healthcare professionals: Is there ageism? Eur J Cancer Care (Engl). 2018;27(1):e12780.
Swift JA, Hanlon S, El-Redy L, Puhl RM, Glazebrook C. Weight bias among UK trainee dietitians, doctors, nurses and nutritionists. J Hum Nutr Diet. 2013;26(4):395–402.
Swift JA, Tischler V, Markham S, Gunning I, Glazebrook C, Beer C, Puhl R. Are anti-stigma films a useful strategy for reducing weight bias among trainee healthcare professionals? Results of a pilot randomized control trial. Obes Facts. 2013;6(1):91–102.
Yertutanol FDK, Candansayar S, Seydaoğlu G. Homophobia in health professionals in Ankara, Turkey: developing a scale. Transcult Psychiatry. 2019;56(6):1191–217.
Arnold O, Voracek M, Musalek M, Springer-Kremser M. Austrian medical students’ attitudes towards male and female homosexuality: a comparative survey. Wien Klin Wochenschr. 2004;116(21–22):730–6.
Arvaniti A, Samakouri M, Kalamara E, Bochtsou V, Bikos C, Livaditis M. Health service staff’s attitudes towards patients with mental illness. Soc Psychiatry Psychiatr Epidemiol. 2009;44(8):658–65.
Lopes L, Gato J, Esteves M. Portuguese medical students’ knowledge and attitudes towards homosexuality. Acta Med Port. 2016;29(11):684–93.
Papadaki V, Plotnikof K, Gioumidou M, Zisimou V, Papadaki E. A comparison of attitudes toward lesbians and gay men among students of helping professions in Crete, Greece: the cases of social work, psychology, medicine, and nursing. J Homosex. 2015;62(6):735–62.
Papaharitou S, Nakopoulou E, Moraitou M, Tsimtsiou Z, Konstantinidou E, Hatzichristou D. Exploring sexual attitudes of students in health professions. J Sex Med. 2008;5(6):1308–16.
Roberts JH, Sanders T, Mann K, Wass V. Institutional marginalisation and student resistance: barriers to learning about culture, race and ethnicity. Adv Health Sci Educ. 2010;15(4):559–71.
Wilhelmi L, Ingendae F, Steinhaeuser J. What leads to the subjective perception of a ‘rural area’? A qualitative study with undergraduate students and postgraduate trainees in Germany to tailor strategies against physician’s shortage. Rural Remote Health. 2018;18(4):4694.
Herrmann-Werner A, Loda T, Wiesner LM, Erschens RS, Junne F, Zipfel S. Is an obesity simulation suit in an undergraduate medical communication class a valuable teaching tool? A cross-sectional proof of concept study. BMJ Open. 2019;9(8):e029738.
Ahadinezhad B, Khosravizadeh O, Maleki A, Hashtroodi A. Implicit racial bias among medical graduates and students by an IAT measure: a systematic review and meta-analysis. Ir J Med Sci. 2022;191(4):1941–9. https://doi.org/10.1007/s11845-021-02756-3 .
Hsieh JG, Hsu M, Wang YW. An anthropological approach to teach and evaluate cultural competence in medical students - the application of mini-ethnography in medical history taking. Med Educ Online. 2016;21:32561.
Poreddi V, Thimmaiah R, Math SB. Attitudes toward people with mental illness among medical students. J Neurosci Rural Pract. 2015;6(3):349–54.
Mino Y, Yasuda N, Tsuda T, Shimodera S. Effects of a one-hour educational program on medical students’ attitudes to mental illness. Psychiatry Clin Neurosci. 2001;55(5):501–7.
Omori A, Tateno A, Ideno T, Takahashi H, Kawashima Y, Takemura K, Okubo Y. Influence of contact with schizophrenia on implicit attitudes towards schizophrenia patients held by clinical residents. BMC Psychiatry. 2012;12:8.
Banwari G, Mistry K, Soni A, Parikh N, Gandhi H. Medical students and interns’ knowledge about and attitude towards homosexuality. J Postgrad Med. 2015;61(2):95–100.
Lee SY. Obesity education in medical school curricula in Korea. J Obes Metab Syndr. 2018;27(1):35–8.
Aruna G, Mittal S, Yadiyal MB, Acharya C, Acharya S, Uppulari C. Perception, knowledge, and attitude toward mental disorders and psychiatry among medical undergraduates in Karnataka: a cross-sectional study. Indian J Psychiatry. 2016;58(1):70–6.
Wong YL. Review paper: gender competencies in the medical curriculum: addressing gender bias in medicine. Asia Pac J Public Health. 2009;21(4):359–76.
Earnshaw VA, Jin H, Wickersham JA, Kamarulzaman A, John J, Lim SH, Altice FL. Stigma toward men who have sex with men among future healthcare providers in Malaysia: would more interpersonal contact reduce prejudice? AIDS Behav. 2016;20(1):98–106.
Larson B, Herx L, Williamson T, Crowshoe L. Beyond the barriers: family medicine residents’ attitudes towards providing Aboriginal health care. Med Educ. 2011;45(4):400–6.
Wagner AC, Girard T, McShane KE, Margolese S, Hart TA. HIV-related stigma and overlapping stigmas towards people living with HIV among health care trainees in Canada. AIDS Educ Prev. 2017;29(4):364–76.
Tellier P-P, Bélanger E, Rodríguez C, Ware MA, Posel N. Improving undergraduate medical education about pain assessment and management: a qualitative descriptive study of stakeholders’ perceptions. Pain Res Manage. 2013;18(5):259–65.
Loignon C, Boudreault-Fournier A, Truchon K, Labrousse Y, Fortin B. Medical residents reflect on their prejudices toward poverty: a photovoice training project. BMC Med Educ. 2014;14:1050.
Phillips SP, Clarke M. More than an education: the hidden curriculum, professional attitudes and career choice. Med Educ. 2012;46(9):887–93.
Jaworsky D, Gardner S, Thorne JG, Sharma M, McNaughton N, Paddock S, Chew D, Lees R, Makuwaza T, Wagner A, et al. The role of people living with HIV as patient instructors—Reducing stigma and improving interest around HIV care among medical students. AIDS Care. 2017;29(4):524–31.
Sukhera J, Wodzinski M, Teunissen PW, Lingard L, Watling C. Striving while accepting: exploring the relationship between identity and implicit bias recognition and management. Acad Med. 2018;93(11S Association of American Medical Colleges Learn Serve Lead: Proceedings of the 57th Annual Research in Medical Education Sessions):S82-s88.
Harris R, Cormack D, Curtis E, Jones R, Stanley J, Lacey C. Development and testing of study tools and methods to examine ethnic bias and clinical decision-making among medical students in New Zealand: the Bias and Decision-Making in Medicine (BDMM) study. BMC Med Educ. 2016;16:173.
Cormack D, Harris R, Stanley J, Lacey C, Jones R, Curtis E. Ethnic bias amongst medical students in Aotearoa/New Zealand: findings from the Bias and Decision Making in Medicine (BDMM) study. PLoS ONE. 2018;13(8):e0201168.
Harris R, Cormack D, Stanley J, Curtis E, Jones R, Lacey C. Ethnic bias and clinical decision-making among New Zealand medical students: an observational study. BMC Med Educ. 2018;18(1):18.
Robinson EL, Ball LE, Leveritt MD. Obesity bias among health and non-health students attending an Australian university and their perceived obesity education. J Nutr Educ Behav. 2014;46(5):390–5.
Sopoaga F, Zaharic T, Kokaua J, Covello S. Training a medical workforce to meet the needs of diverse minority communities. BMC Med Educ. 2017;17:19.
Parker R, Larkin T, Cockburn J. A visual analysis of gender bias in contemporary anatomy textbooks. Soc Sci Med. 2017;180:106–13.
Gomes MdM. Doctors’ perspectives and practices regarding epilepsy. Arq Neuropsiquiatr. 2000;58(2):221–6.
Caixeta J, Fernandes PT, Bell GS, Sander JW, Li LM. Epilepsy perception amongst university students - A survey. Arq Neuropsiquiatr. 2007;65:43–8.
Tedrus GMAS, Fonseca LC, da Câmara Vieira AL. Knowledge and attitudes toward epilepsy amongst students in the health area: intervention aimed at enlightenment. Arq Neuropsiquiatr. 2007;65(4-B):1181–5.
Gomez-Moreno C, Verduzco-Aguirre H, Contreras-Garduño S, Perez-de-Acha A, Alcalde-Castro J, Chavarri-Guerra Y, García-Lara JMA, Navarrete-Reyes AP, Avila-Funes JA, Soto-Perez-de-Celis E. Perceptions of aging and ageism among Mexican physicians-in-training. Clin Transl Oncol. 2019;21(12):1730–5.
Campbell MH, Gromer J, Emmanuel MK, Harvey A. Attitudes Toward Transgender People Among Future Caribbean Doctors. Arch Sex Behav. 2022;51(4):1903-11. https://doi.org/10.1007/s10508-021-02205-3 .
Hatala R, Case SM. Examining the influence of gender on medical students’ decision making. J Womens Health Gend Based Med. 2000;9(6):617–23.
Deb T, Lempp H, Bakolis I, et al. Responding to experienced and anticipated discrimination (READ): anti -stigma training for medical students towards patients with mental illness – study protocol for an international multisite non-randomised controlled study. BMC Med Educ. 2019;19:41. https://doi.org/10.1186/s12909-019-1472-7 .
Morgan S, Plaisant O, Lignier B, Moxham BJ. Sexism and anatomy, as discerned in textbooks and as perceived by medical students at Cardiff University and University of Paris Descartes. J Anat. 2014;224(3):352–65.
Alford CL, Miles T, Palmer R, Espino D. An introduction to geriatrics for first-year medical students. J Am Geriatr Soc. 2001;49(6):782–7.
Stone J, Moskowitz GB. Non-conscious bias in medical decision making: what can be done to reduce it? Med Educ. 2011;45(8):768–76.
Nazione S. Slimming down medical provider weight bias in an obese nation. Med Educ. 2015;49(10):954–5.
Dogra N, Connin S, Gill P, Spencer J, Turner M. Teaching of cultural diversity in medical schools in the United Kingdom and Republic of Ireland: cross sectional questionnaire survey. BMJ. 2005;330(7488):403–4.
Aultman JM, Borges NJ. A clinical and ethical investigation of pre-medical and medical students’ attitudes, knowledge, and understanding of HIV. Med Educ Online. 2006;11(1):4596.
Deb T, Lempp H, Bakolis I, Vince T, Waugh W, Henderson C, Thornicroft G, Ando S, Yamaguchi S, Matsunaga A, et al. Responding to experienced and anticipated discrimination (READ): anti -stigma training for medical students towards patients with mental illness – study protocol for an international multisite non-randomised controlled study. BMC Med Educ. 2019;19(1):41.
Gonzalez CM, Grochowalski JH, Garba RJ, Bonner S, Marantz PR. Validity evidence for a novel instrument assessing medical student attitudes toward instruction in implicit bias recognition and management. BMC Med Educ. 2021;21(1):205.
Ogunyemi D. A practical approach to implicit bias training. J Grad Med Educ. 2021;13(4):583–4.
Dennis GC. Racism in medicine: planning for the future. J Natl Med Assoc. 2001;93(3 Suppl):1S-5S.
Maina IW, Belton TD, Ginzberg S, Singh A, Johnson TJ. A decade of studying implicit racial/ethnic bias in healthcare providers using the implicit association test. Soc Sci Med. 2018;199:219–29.
Blair IV, Steiner JF, Hanratty R, Price DW, Fairclough DL, Daugherty SL, Bronsert M, Magid DJ, Havranek EP. An investigation of associations between clinicians’ ethnic or racial bias and hypertension treatment, medication adherence and blood pressure control. J Gen Intern Med. 2014;29(7):987–95.
Stanford FC. The importance of diversity and inclusion in the healthcare workforce. J Natl Med Assoc. 2020;112(3):247–9.
Education LCoM. Standards on diversity. 2009. https://health.usf.edu/~/media/Files/Medicine/MD%20Program/Diversity/LCMEStandardsonDiversity1.ashx?la=en .
Onyeador IN, Hudson STJ, Lewis NA. Moving beyond implicit bias training: policy insights for increasing organizational diversity. Policy Insights Behav Brain Sci. 2021;8(1):19–26.
Forscher PS, Mitamura C, Dix EL, Cox WTL, Devine PG. Breaking the prejudice habit: mechanisms, timecourse, and longevity. J Exp Soc Psychol. 2017;72:133–46.
Lai CK, Skinner AL, Cooley E, Murrar S, Brauer M, Devos T, Calanchini J, Xiao YJ, Pedram C, Marshburn CK, et al. Reducing implicit racial preferences: II. Intervention effectiveness across time. J Exp Psychol Gen. 2016;145(8):1001–16.
Sukhera J, Watling CJ, Gonzalez CM. Implicit bias in health professions: from recognition to transformation. Acad Med. 2020;95(5):717–23.
Vuletich HA, Payne BK. Stability and change in implicit bias. Psychol Sci. 2019;30(6):854–62.
Tversky A, Kahneman D. Judgment under uncertainty: Heuristics and biases. Science. 1974;185(4157):1124–31.
Miller DT, Ross M. Self-serving biases in the attribution of causality: fact or fiction? Psychol Bull. 1975;82(2):213–25.
Nickerson RS. Confirmation bias: a ubiquitous phenomenon in many guises. Rev Gen Psychol. 1998;2(2):175–220.
Suveren Y. Unconscious bias: definition and significance. Psikiyatride Guncel Yaklasimlar. 2022;14(3):414–26.
Dietrich D, Olson M. A demonstration of hindsight bias using the Thomas confirmation vote. Psychol Rep. 1993;72(2):377–8.
Green AR, Carney DR, Pallin DJ, Ngo LH, Raymond KL, Iezzoni LI, Banaji MR. Implicit bias among physicians and its prediction of thrombolysis decisions for black and white patients. J Gen Intern Med. 2007;22(9):1231–8.
Rushmer R, Davies HT. Unlearning in health care. Qual Saf Health Care. 2004;13 Suppl 2(Suppl 2):ii10-15.
Vu MT, Pham TTT. Gender, critical pedagogy, and textbooks: Understanding teachers’ (lack of) mediation of the hidden curriculum in the EFL classroom. Lang Teach Res. 2022;0(0). https://doi.org/10.1177/13621688221136937 .
Kalantari A, Alvarez A, Battaglioli N, Chung A, Cooney R, Boehmer SJ, Nwabueze A, Gottlieb M. Sex and race visual representation in emergency medicine textbooks and the hidden curriculum. AEM Educ Train. 2022;6(3):e10743.
Satya-Murti S, Lockhart J. Recognizing and reducing cognitive bias in clinical and forensic neurology. Neurol Clin Pract. 2015;5(5):389–96.
Chang EH, Milkman KL, Gromet DM, Rebele RW, Massey C, Duckworth AL, Grant AM. The mixed effects of online diversity training. Proc Natl Acad Sci U S A. 2019;116(16):7778–83.
Download references
Acknowledgements
The authors would like to thank Dr. Misa Mi, Professor and Medical Librarian at the Oakland University William Beaumont School of Medicine (OWUB) for her assistance with selection of databases and construction of literature search strategies for the scoping review. The authors also wish to thank Dr. Changiz Mohiyeddini, Professor in Behavioral Medicine and Psychopathology at Oakland University William Beaumont School of Medicine (OUWB) for his expertise and constructive feedback on our manuscript.
Author information
Authors and affiliations.
Department of Foundational Sciences, Central Michigan University College of Medicine, Mt. Pleasant, MI, 48859, USA
Brianne E. Lewis
Department of Foundational Medical Studies, Oakland University William Beaumont School of Medicine, 586 Pioneer Dr, Rochester, MI, 48309, USA
Akshata R. Naik
You can also search for this author in PubMed Google Scholar
Contributions
A.R.N and B.E.L were equally involved in study conception, design, collecting data and analyzing the data. B.E.L and A.R.N both contributed towards writing the manuscript. A.R.N and B.E.L are both senior authors on this paper. All authors reviewed the manuscript.
Corresponding author
Correspondence to Akshata R. Naik .
Ethics declarations
Ethics approval and consent to participate.
Not applicable.
Consent for publication
Competing interests.
The authors declare no competing interests.
Additional information
Publisher’s note.
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution 4.0 International License, which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if changes were made. The images or other third party material in this article are included in the article's Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article's Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by/4.0/ . The Creative Commons Public Domain Dedication waiver ( http://creativecommons.org/publicdomain/zero/1.0/ ) applies to the data made available in this article, unless otherwise stated in a credit line to the data.
Reprints and permissions
About this article
Cite this article.
Lewis, B.E., Naik, A.R. A scoping review to identify and organize literature trends of bias research within medical student and resident education. BMC Med Educ 23 , 919 (2023). https://doi.org/10.1186/s12909-023-04829-6
Download citation
Received : 14 March 2023
Accepted : 01 November 2023
Published : 05 December 2023
DOI : https://doi.org/10.1186/s12909-023-04829-6
Share this article
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
- Preclinical curriculum
- Evidence of bis
BMC Medical Education
ISSN: 1472-6920
- Submission enquiries: [email protected]
- General enquiries: [email protected]

Mozilla VPN review: An easy-to-use VPN with Firefox compatibility
At a glance
Expert's Rating
・Approachable easy-to-use Windows application
・Split-tunneling and multi-hop features
・Trusted Mozilla brand
・Only comes with WireGuard protocol
・Issues with unblocking major streaming services
・Can get the same server network cheaper with Mullvad VPN
Our Verdict
Mozilla VPN is a solid service, but I can’t help feeling as if it hasn’t realized its full potential. Hardcore Mozilla fans will likely enjoy supporting the company’s free internet ideals and the integration with the Firefox browser. Outside of that, users might find that the service is lacking in features and server locations compared to other top VPNs.
Price When Reviewed
Best prices today: mozilla vpn.
Retailer Price Mozilla $9.99 View Deal Price comparison from over 24,000 stores worldwide Product Price Price comparison from Backmarket
Mozilla VPN in brief:
・P2P allowed: Yes
・Unlimited device connections: No, five simultaneous device connections
・Business location: California
・Number of servers: 500+
・Number of country locations: 30+
・Cost: $9.99 per month, or $59.88 for a year
Mozilla is one of the top players in the browser game along with Chrome and Safari. So when such a big name in the industry comes out with its own VPN, people take notice. What began as a Firefox browser extension more than five years ago has grown into a fully standalone application.
In the ensuing years, Mozilla has added support for more services such as MacOS and Linux, as well as boosting its server network and undergoing multiple independent security audits. So how does this internet browser giant’s VPN stack up against longtime players such as ExpressVPN and NordVPN? I put it to the test to find out.
Further reading: See our roundup of the best VPNs to learn about competing products.
What are Mozilla VPN’s features and services?
Since the launch of the service, Mozilla VPN has grown significantly. It now includes many of the same features as other top VPN services. Let’s look at what you’ll get for your money.
Mozilla VPN offers up to five simultaneous device connections. That isn’t bad, but the trend is towards removing these limitations, and many other services such as Surfshark , TunnelBear , and Private Internet Access are already offering unlimited connections.
Sam Singleton
When you first open the application you’re immediately confronted with a switch in the middle to turn on the VPN, a Select location option, and a few other settings features at the bottom. The whole design and layout of the app is incredibly clean and well thought out. Even the wording above the switch “Turn on to protect your privacy” is a nice touch that’s sure to make sense to even the most novice of users.
When you choose Select location, a drop-down menu will appear with all of the available server locations listed. You can choose to sort them by Recommended or All . As a whole, Mozilla VPN’s server network is unfortunately rather small compared to other services. At over 500 servers you’ll have options to choose from, but the fact that it only offers around 40 country locations is disappointing. This is an area that will hopefully be improved upon in the future.
The Mozilla VPN’s network is actually piggy-backing off of Mullvad VPN’s network. There isn’t a lot of advertisement for this, and in fact the only place it becomes apparent is when you check the server status on the website — it actually links to the Mullvad server status web page instead.
Mozilla VPN is more focused on user security and privacy than accessing geo-restricted content
Under the server list you’ll also find the option to switch to multi-hop connection. I was genuinely surprised that Mozilla VPN offers multi-hop. It’s a really nifty feature that not a lot of VPNs currently offer. With multi-hop you can pick your entry and exit server locations thereby allowing your traffic to be rerouted through more than just one VPN server. This further obfuscates your true IP location and makes your connection more private.
You can navigate to the settings menu by clicking the ever-present gear icon at the bottom of the page. Here you’ll be able to turn on ad-, tracker-, and malware-blocking under the Privacy features tab. These are all commonly included with most other VPNs nowadays, but still nice to have.
Mozilla VPN offers a split-tunneling feature, but it’s not labeled as such. Instead it’s nestled under App exclusions. Here you can pick and choose which particular apps you wish to be excluded from running through a VPN and rather just use your regular internet connection. This can be useful if you want to remain anonymous while browsing, but need your full internet speed while gaming.
The service also offers a kill switch that will suspend internet traffic should your VPN connection drop for any unexpected reason. This feature was deemed so important by Mozilla that the app doesn’t allow you to turn it off. This is a bit unique from other services which allow you to manually turn on or off the kill switch feature. From a privacy and security perspective I don’t mind this, but I see a case for having the option to change it. When I tested this feature it worked without a hitch.
Firefox users will also find that the VPN integrates to some degree with Mozilla’s browser. The best feature here is support for Multi-Account Containers. This allows you to connect different Firefox tabs to separate VPN servers. With this feature you no longer need to change servers should you wish to use different locations for different websites. It’s a quality-of-life feature that feels a bit niche, but I’m sure Firefox power users will appreciate it.
How is Mozilla VPN’s performance?
To test Mozilla VPN’s speeds I rated connection speeds across its servers in six different countries around the world and then compared them to my baseline internet speed. Mozilla VPN’s speeds were pretty average with the download speeds at 38 percent and upload speeds at 47 percent of base speeds.
That’s nowhere near our fastest VPNs such as Hotspot Shield , ExpressVPN , and NordVPN . All of these reached speeds upwards of 60 percent or more of baseline during our testing. Still, if you’re just looking for a VPN to keep you safe during casual browsing or streaming, Mozilla VPN should be just fine.
One notable perk with Mozilla VPN is that the actual connection time to a server is lightning fast. Sometimes VPNs can take a few moments to connect between servers, but Mozilla VPN was near instantaneous. It’s a rather trivial thing for most people, but combined with the Multi-Account Containers feature, users who need to change servers frequently will find it a nice quality-of-life fringe benefit.
When it comes to unblocking streaming content, however, much like my childhood aspirations to play in the MLB, Mozilla VPN falls flat on its face. The service wasn’t able to access any of the major streaming services such as Netflix, Amazon Prime, Disney Plus, or Hulu in any country that I tested. This just goes to show that Mozilla VPN is more focused on user security and privacy than accessing geo-restricted content.
How is Mozilla VPN’s security and privacy?
Mozilla VPN comes with the industry standard AES-256 bit encryption and only allows connections to be done over the WireGuard protocol. The reasoning behind this isn’t unsound as WireGuard is one of the newer protocols and offers excellent speed and security. But those who wish to tweak and customize their connections will feel a little hard done by.
That being said, the company did score well on our privacy checks. When checking for DNS leaks, the service came away with perfect marks, showing no leaks from any of our test sites.
In addition, the company’s privacy policy clearly states that it doesn’t store any online user activity logs. It does collect some data though, such as your IP address when you first register for the service as well as your operating system and hardware configuration. It does not, however, collect data on traffic, subsequent IP addresses, bandwidth usage, session times, or DNS requests.
To back up these claims, Mozilla VPN has undergone two separate independent security audits by third-party cybersecurity firm Cure53. The first audit was done in 2021 and the latest audit was completed in December of last year. The firm identified a few vulnerabilities, but Mozilla VPN was quick to address the issues and fix them.
Mentioned in this article
Read our review Price When Reviewed: $6.88 per month Best Prices Today: £5 at Amagicom AB
Much like Mullvad VPN, the service that underpins it, Mozilla VPN has strong overall privacy credentials. That’s to be expected though from a company like Mozilla who prioritizes a free and open internet. Privacy is definitely one of Mozilla VPN’s strong suits and depending on what you value in your VPN, may be a deciding factor.
Is Mozilla VPN worth it?
Is Mozilla VPN the best VPN I’ve ever used? In a nutshell, no. It lacks the widespread server network of other VPNs and there are some serious unblocking issues. That being said, fans of Mozilla and its free internet ideals will find that there is enough here to satisfy them.
The app is extremely easy to use and approachable for novices and the development team seems to be working hard to implement more features to appeal to power users. It also makes all of the right privacy promises. Still, in its current state, Mozilla VPN has some outstanding issues and its price is almost double that of Mullvad, the service it’s built around.
Editor’s note : Because online services are often iterative, gaining new features and performance improvements over time, this review is subject to change in order to accurately reflect the current state of the service. Any changes to text or our final review verdict will be noted at the top of this article.


IMAGES
VIDEO
COMMENTS
This Literature review paper explains about Virtual Private Network(VPN), It's protocols and Security in VPN. ... VPN services are accessible for smart phones, PCs and tablets. It is a rising ...
Recently, there has been rapid development and deployment of virtual private network (VPN) services. There are wide varieties of IP-based VPNs and optical VPNs (OVPNs) proposed in the literature and readers could easily get confused with so many different types of VPNs. The purpose of this paper is to present a comprehensive overview of the VPN and discuss the main issues associated with the ...
This research comprehensively surveys VPN technologies, its features, working principles, and compliance principles that evolved over the last two decades. Based on it, this research presents a new methodology in the form of a feature-enriched template to comprehensively analyze a VPN solution.
Aside from using multiple services, users can also rely on Virtual Private Network (VPN) [48][49][50][51] [52] services or a custom-built service on the TOR [53] network to enhance user anonymity ...
IPSec VPN, as can be seen from the literal, is a VPN that realizes remote access through the IPSec protocol. It provides a tunnel over a public network for two private networks to transmit data. This tunnel is encrypted to ensure security. The advantage of IPSec.VPN is that it is a net-to-network networking method, which can establish ...
A virtual private network (VPN) can help resolve many of the issues associated with today's private networks. A VPN facilitates an agile IT infrastructure. Global VPNs enable connectivity to all locations anywhere in the world at a fraction of the cost of dedicated links. VPN services enable remote access to the intranet at significantly lower cost, thus enabling support for a mobile workforce ...
We categorized VPN's impact in to two different aspects; The affecting aspect, and the affected aspect. The affecting aspect of the impact encompasses factors such as security, algorithms, hardware, and software. Whereas the affected aspect is of the likes of network performance. While VPNs have managed to integrate security, one of the affecting aspect of the impact on one hand, on the other ...
Table 1 Summary of the literature review Summary of the literature review Authors Work done Result Liyanage and Gurtov [7] VPN architecture for LTE backhaul was addressed. The Internet key exchange model 2(IKEv2) and host identity protocol (HIP) were used as the safety key Provided secured backhaul traffic during DoS, DDoS and TCP reset ...
VPN is a virtual connection routed through the Internet on a public network, from the sender's private network to the receiver. VPN aims to initiate a secure communication path among different networks. It is usually created across the public network [ 3 ]. VPN tunnels are used to maintain the privacy of statistics shared over the physical ...
The study adopted investigative research design by use of empirical review on the security aspect of the current state VPN Remote Access methods. This necessitates the review of the research ...
An extensive literature review is given, providing the reader with insight into the key contributions in the area of VPN and VLAN implementations in static and dynamic networks; (b) Several details about the protocols and signaling used in VPN/VLAN systems are given, providing the reader with detailed information about security management in ...
Our experts test the VPN's performance and speed themselves, using it for everyday activities like downloading, streaming, gaming, and browsing, to ensure that the performance numbers hold up in performance too.. Security. VPNs play an important role in keeping users safe. In every review we do, we analyze the security features offered by the VPN, including:
The purpose of this study is to examine the use of a virtual private network (VPN) as an additional protective strategy for patrons using library computers.,This study is a literature review and commentary on this topic that has been addressed by professionals, researchers and practitioners.,Credit must be given to those libraries who have made ...
1 LITERATURE REVIEW Significance of VPN According to [1], the virtual private network (VPN) is mainly used for online communication. This uses the infrastructure of the public network to physically allow the connection in. This establishes the private messaging network instead of using the cables. The
to confirm that only authorized users can access the system and the data can be intercepted. This Literature review paper explains about Virtual Private Network (VPN), its protocols and Security in VPN. In this paper we have discussed about various protocol used in VPN. Key Words: VPN, Architecture of VPN, Protocol in VPN 1.
Keeping the VPN review updated to reflect changes, such as with company policies, features, and VPN client updates; Over the past few years, doing all of the above with about a dozen VPN reviews has taken up lots of time, in addition to writing and updating other privacy guides for the site. However, our small team is expanding to cover more ...
Examples of literature reviews. Step 1 - Search for relevant literature. Step 2 - Evaluate and select sources. Step 3 - Identify themes, debates, and gaps. Step 4 - Outline your literature review's structure. Step 5 - Write your literature review.
This section introduces the literature review in the area of t he opted domain of VPN security which is as follows: (Singh et al.,)[8], proposed an approach of VPN security.
II. LITERATURE REVIEW In 2000 John P. McGregor[et.al] presented a paper for VPN(Virtual Private Network) which connect two or more than two different clients to communicate securely over the network. For the securely communication cryptographic method is using so that VPN can provide the secure connection over the network.
We test and review VPN services in the context of legal recreational uses. For example: 1. Accessing a service from another country (subject to the terms and conditions of that service). 2.
ExpressVPN's one year plan costs $99.95 ($8.32 a month), a saving of 35 percent. Just keep in mind that you'll need to pay the total up front. Although the one month plan is more expensive at ...
In our January 2024 tests, CNET Labs clocked a best-in-class average speed loss of 11.1% when using NordVPN, earning it the accolade of CNET's. fastest VPN. For comparison, other top VPNs we ...
II. Literature Review This section introduces the literature review in the area of the opted domain of VPN security which is as follows: (Singh et al.,)[8], proposed an approach of VPN security. The proposed solution was applicable to the security of the user's data traveled in the form of a VPN Header. Moreover, it extends the
This systematic literature review presents an interdisciplinary overview of theories tested in experiments on the effects of communicating uncertainty. Using a machine learning-aided pipeline, we selected and manually coded 413 experimental studies. We discuss core assumptions and predictions of the main theories of uncertainty communication.
This article provides the first comprehensive literature review about generative AI for architectural design, and we believe this work can facilitate more research work on this significant topic in architecture. Comments: 32 pages, 20 figures. Subjects: Machine Learning (cs.LG); Artificial Intelligence (cs.AI) Cite as: arXiv:2404.01335 [cs.LG]
sol ution. Because of application agnostic nature of IPsec VPN, it can support cl ient/server application and number of legacy. protocols with minimal effort. However SSL VPNs have been. built ...
We conducted an exhaustive and focused scoping review and followed the methodological framework for scoping reviews as previously described in the literature [20, 22].This study aligned with the four goals of a scoping review [].We followed the first five out of the six steps outlined by Arksey and O'Malley's to ensure our review's validity 1) identifying the research question 2 ...
The firm identified a few vulnerabilities, but Mozilla VPN was quick to address the issues and fix them. Read our review. Price When Reviewed: $6.88 per month Best Prices Today: £5 at Amagicom AB ...
Microsoft committed a "cascade" of "avoidable errors" that allowed Chinese hackers to breach the tech giant's network and later the email accounts of senior US officials last year ...
processes and to create a competitive edge. One of the most useful technologies in that sense is virtual. privates networks (VPNs). It enables various secure connections through public networks ...