A Systematic Literature Review on Cloud Computing Security: Threats and Mitigation Strategies
Ieee account.
- Change Username/Password
- Update Address

Purchase Details
- Payment Options
- Order History
- View Purchased Documents
Profile Information
- Communications Preferences
- Profession and Education
- Technical Interests
- US & Canada: +1 800 678 4333
- Worldwide: +1 732 981 0060
- Contact & Support
- About IEEE Xplore
- Accessibility
- Terms of Use
- Nondiscrimination Policy
- Privacy & Opting Out of Cookies
A not-for-profit organization, IEEE is the world's largest technical professional organization dedicated to advancing technology for the benefit of humanity. © Copyright 2024 IEEE - All rights reserved. Use of this web site signifies your agreement to the terms and conditions.
- Our Promise
- Our Achievements
- Our Mission
- Proposal Writing
- System Development
- Paper Writing
- Paper Publish
- Synopsis Writing
- Thesis Writing
- Assignments
- Survey Paper
- Conference Paper
- Journal Paper
- Empirical Paper
- Journal Support
- CLOUD COMPUTING SECURITY RESEARCH PROPOSAL
Cloud security is the mechanism to prevent cyber-attacks in the cloud. It is similar to cybersecurity. Servers and data centres play the roles of upload and download data to the cloud. It is the server that enables the usage of data for any user from any place and time. With the spread of cloud usage among individuals, Cloud computing security research proposal are gaining huge importance these days. In the following section, we will give you the complete picture of cloud computing and its security.
We are guiding cloud computing research projects for about 15 years . So we have enough knowledge and experience in cloud computing security research. First, let us start with an understanding of cloud computing.
HOW SECURE IS CLOUD COMPUTING?
- First of all, we should remember that cloud servers are hosted remotely.
- So we may think the cloud is insecure.
- But it is surprisingly proven by multiple projects that cloud servers are safer than on-site service providers.
The security in cloud computing is not more vulnerable but still certain activities on the cloud which require two or more levels of security. We are working on methods and functions to enhance security in the cloud. There are some existing techniques that we are working upon to scrutinize them and prove to the customers that cloud security is more stringent.
Only by understanding the risks in cloud computing security , you can choose the best topic for your cloud computing security research proposal. This is because, any research that aims at rectifying the present-day issues in cloud computing security or for that matter, issues in any field, can gain you tremendous success in your research career.
WHAT ARE THE MAIN CLOUD SECURITY RISKS?
The major categories of risks in cloud security are as follows
- Leakage of data
- Malware and DDoS attacks
- Threat from internal users(unlimited access)
- Data being accessed by unauthorized people
Cloud security must protect the data and network from these types of risks. You can now find the issues that lead to the most irrevocable damages to the security system and content . Then you can apply your knowledge to design systems that can improve the existing issues of cloud computing security.
Experts and engineers with us have huge experience in the field of designing security systems for cloud computing . So you can reach out to us and get their guidance if needed. Now let us talk more about issues related to cloud computing security.
RESEARCH ISSUES IN CLOUD SECURITY
The following are the issues associated with cloud security . Our team of experts is highly skilled in solving these issues. We have almost two decades of expertise in providing real-time solutions to problems of cloud security . So you can contact us for any solving any types of issues in the cloud and its security. The following are the research issues in cloud security
- Controlling the access to data
- Personal and corporate data must be separated
- Network Security in the transfer of data must be ensured
- The data in the cloud storage must be properly encrypted for protection
- The safe interface is to be provided
Further, the issues in cloud computing can be extended to the following aspects.
- Vulnerability
- Insider threats
- Hijacking of service
- Hypervisor viruses
- Denial of service
- IP spoofing
- Minimized control
- Confidentiality of data
- Malware attacks
- Data intrusion
- Availability
- Injection attack
- Man-in-the-middle attack
We have delivered many projects related to these attacks and the solutions that our experts prescribed always exceeded the expectations of our customers. You can look into those projects and their performances once you get connected with our experts. Our technical team is updating themselves and they are always capable of providing solutions to any sort of problems that you may encounter during your research in cloud computing security.
RESEARCH OBJECTIVES IN CLOUD SECURITY
The following are the main aims of any research in cloud security . You can write your cloud computing security research proposal in any of these objectives.
- Reducing the costs of hardware and backup
- Lowering the costs
- Increasing the efficiency of storage
- Easily recoverable at times of disaster
- Enhancing the efficiency of network
With these objectives, we have guided lots of cloud security projects . You can talk to our experts and gain their experience and then start your research. We insist upon this because lots of lessons can be learned from the experiences of others, especially in research. We will now brief you on attacks on cloud security
CLOUD COMPUTING SECURITY ATTACKS
As we said before, there are many issues associated with security in cloud computing . We have successfully delivered all projects by rectifying cloud computing security attacks . Refer to the following attacks in cloud computing.
- Man-in-the-middle attacks
- Side-channel threats
- DNS amplification
- Registrar hijacking
- Spoofing of IP address
- Authentication threats
- Denial of service attacks
- Cache poisoning
Our engineers are world-class certified. We have writers and developers with us who gained expertise in writing cloud computing security proposal . We have highly trained and skilled experts. You can rely on them for your project support. The following are some of the advanced topics in cloud computing security.
ADVANCED TOPICS IN CLOUD COMPUTING SECURITY RESEARCH PROPOSAL
You can refer to the following topics on security in cloud computing . These are the trending topics in the field.
- Anomaly Classification in Multi-Cloud
- Dynamic Programming and VM Scheduling in Cloud
- Secure Multi-Party Computation by Agent
- Cyber Security T hreats Detection
- Secure Data Storage
- Data Modernization
- DDoS Attacks Detection
- Secure Data Access Control
- Dynamic Encrypted Data Distribution
- Proxy-based Hybrid Cloud Network
- Hybrid Bayesian Network Organization
- Secure Data Offloading and Data Access Control
- IDPS Proof Design, Distributed Offloading
- Misbehaving Sources Identify
- Smart Grid and Cloud-based Attacks Mitigation
We guide all these topics. You can either choose from this list or come up with your own topic. We are happy to lend support for any kind of topic in the security in cloud computing . As we have been in the research of cloud security for a long, we are potential enough to project future advancements in cloud computing security . In the following section, we have given the future of cloud computing security.
THE FUTURE OF CLOUD COMPUTING SECURITY
The advancements in cloud security can be attributed to the following.
- IoT applications to smart cities
- Monitor (trusted)
- Computing between machines
- Big data analytics in the cloud
- Information that is self-protected
From this, you can now clearly understand that there are huge scopes for future research in cloud computing security . We are ready to offer guidance for cloud security projects from basics to future advancements. So you can rely on us for your complete research support. Following are the major points to be included in your cloud computing security research proposal .
The research proposal for a topic like “security in data deduplication” should consist of the major threats to data deduplication. This is because your research aim in itself is to overcome these threats.
The threats to users in cases of data deduplication are as follows
- Cloud storage server (data encryption and decryption)
- A malicious user (retrieval of critical data from source)
These threats can be overcome very easily with our expert guidance. You can enhance your potential resource base with the massive reliable resources that we provide. As we have huge experience in guiding cloud security research projects , we can give you ample ideas, resources, and advice for your research. We will now let you know more about the research gaps in cloud security.
RESEARCH GAPS IN CLOUD SECURITY
The following are the gaps existing in cloud security research. We help you bridge these gaps. Our experts are very famous for their attempts in building the research gaps in cloud security.
- Threats to privacy
- Increased time for search and retrieval of data (centralized index table)
- Less demand meeting capabilities of present schemes for data depulication
- Loopholes in accessing large data in data deduplication
- Duplicate elimination ratio (efficiency must be increased for file blocking)
- Strengthened algorithms for security based on the criticality of data
These research gaps are not a big issue for our experts. Your knowledge accompanied by our experience can fetch you wonderful results. Now we will take you through the importance of research design in cloud computing .
WHAT IS RESEARCH DESIGN AND ITS IMPORTANCE?
Research design includes the following
- Techniques for data collection
- Analyzing methods
The necessity of research design can be understood from the following.
- Accuracy is enhanced
- Reliability is increased
- Enhancing efficiency
- Research is guided in the correct way
You can connect with us to know more about the role played by research design in the execution of cloud computing security projects . Now let us see about the necessary qualities for a good research proposal.
WHAT ARE THE QUALITIES OF A GOOD RESEARCH PROPOSAL?
You might be already aware of producing a quality research proposal. We want you to remember these points so that you can surely produce a very good quality research proposal.
- Clearly states the objective of the study
- It must attract the readers (innovations must be included)
- Gives projections of aims (measurable and achievable)
- The significance of the research is well addressed
- Gives the benefits of the study
- Proves the importance of the research (like conducting the study)
Hope you are now convinced to continue your research in cloud security . Reach out to us and get more ideas on cloud computing security research proposal . We are very much happy to render you all types of research support.
MILESTONE 1: Research Proposal
Finalize journal (indexing).
Before sit down to research proposal writing, we need to decide exact journals. For e.g. SCI, SCI-E, ISI, SCOPUS.
Research Subject Selection
As a doctoral student, subject selection is a big problem. Phdservices.org has the team of world class experts who experience in assisting all subjects. When you decide to work in networking, we assign our experts in your specific area for assistance.
Research Topic Selection
We helping you with right and perfect topic selection, which sound interesting to the other fellows of your committee. For e.g. if your interest in networking, the research topic is VANET / MANET / any other
Literature Survey Writing
To ensure the novelty of research, we find research gaps in 50+ latest benchmark papers (IEEE, Springer, Elsevier, MDPI, Hindawi, etc.)
Case Study Writing
After literature survey, we get the main issue/problem that your research topic will aim to resolve and elegant writing support to identify relevance of the issue.
Problem Statement
Based on the research gaps finding and importance of your research, we conclude the appropriate and specific problem statement.
Writing Research Proposal
Writing a good research proposal has need of lot of time. We only span a few to cover all major aspects (reference papers collection, deficiency finding, drawing system architecture, highlights novelty)
MILESTONE 2: System Development
Fix implementation plan.
We prepare a clear project implementation plan that narrates your proposal in step-by step and it contains Software and OS specification. We recommend you very suitable tools/software that fit for your concept.
Tools/Plan Approval
We get the approval for implementation tool, software, programing language and finally implementation plan to start development process.
Pseudocode Description
Our source code is original since we write the code after pseudocodes, algorithm writing and mathematical equation derivations.
Develop Proposal Idea
We implement our novel idea in step-by-step process that given in implementation plan. We can help scholars in implementation.
Comparison/Experiments
We perform the comparison between proposed and existing schemes in both quantitative and qualitative manner since it is most crucial part of any journal paper.
Graphs, Results, Analysis Table
We evaluate and analyze the project results by plotting graphs, numerical results computation, and broader discussion of quantitative results in table.
Project Deliverables
For every project order, we deliver the following: reference papers, source codes screenshots, project video, installation and running procedures.
MILESTONE 3: Paper Writing
Choosing right format.
We intend to write a paper in customized layout. If you are interesting in any specific journal, we ready to support you. Otherwise we prepare in IEEE transaction level.
Collecting Reliable Resources
Before paper writing, we collect reliable resources such as 50+ journal papers, magazines, news, encyclopedia (books), benchmark datasets, and online resources.
Writing Rough Draft
We create an outline of a paper at first and then writing under each heading and sub-headings. It consists of novel idea and resources
Proofreading & Formatting
We must proofread and formatting a paper to fix typesetting errors, and avoiding misspelled words, misplaced punctuation marks, and so on
Native English Writing
We check the communication of a paper by rewriting with native English writers who accomplish their English literature in University of Oxford.
Scrutinizing Paper Quality
We examine the paper quality by top-experts who can easily fix the issues in journal paper writing and also confirm the level of journal paper (SCI, Scopus or Normal).
Plagiarism Checking
We at phdservices.org is 100% guarantee for original journal paper writing. We never use previously published works.
MILESTONE 4: Paper Publication
Finding apt journal.
We play crucial role in this step since this is very important for scholar’s future. Our experts will help you in choosing high Impact Factor (SJR) journals for publishing.
Lay Paper to Submit
We organize your paper for journal submission, which covers the preparation of Authors Biography, Cover Letter, Highlights of Novelty, and Suggested Reviewers.
Paper Submission
We upload paper with submit all prerequisites that are required in journal. We completely remove frustration in paper publishing.
Paper Status Tracking
We track your paper status and answering the questions raise before review process and also we giving you frequent updates for your paper received from journal.
Revising Paper Precisely
When we receive decision for revising paper, we get ready to prepare the point-point response to address all reviewers query and resubmit it to catch final acceptance.
Get Accept & e-Proofing
We receive final mail for acceptance confirmation letter and editors send e-proofing and licensing to ensure the originality.
Publishing Paper
Paper published in online and we inform you with paper title, authors information, journal name volume, issue number, page number, and DOI link
MILESTONE 5: Thesis Writing
Identifying university format.
We pay special attention for your thesis writing and our 100+ thesis writers are proficient and clear in writing thesis for all university formats.
Gathering Adequate Resources
We collect primary and adequate resources for writing well-structured thesis using published research articles, 150+ reputed reference papers, writing plan, and so on.
Writing Thesis (Preliminary)
We write thesis in chapter-by-chapter without any empirical mistakes and we completely provide plagiarism-free thesis.
Skimming & Reading
Skimming involve reading the thesis and looking abstract, conclusions, sections, & sub-sections, paragraphs, sentences & words and writing thesis chorological order of papers.
Fixing Crosscutting Issues
This step is tricky when write thesis by amateurs. Proofreading and formatting is made by our world class thesis writers who avoid verbose, and brainstorming for significant writing.
Organize Thesis Chapters
We organize thesis chapters by completing the following: elaborate chapter, structuring chapters, flow of writing, citations correction, etc.
Writing Thesis (Final Version)
We attention to details of importance of thesis contribution, well-illustrated literature review, sharp and broad results and discussion and relevant applications study.
How PhDservices.org deal with significant issues ?
1. novel ideas.
Novelty is essential for a PhD degree. Our experts are bringing quality of being novel ideas in the particular research area. It can be only determined by after thorough literature search (state-of-the-art works published in IEEE, Springer, Elsevier, ACM, ScienceDirect, Inderscience, and so on). SCI and SCOPUS journals reviewers and editors will always demand “Novelty” for each publishing work. Our experts have in-depth knowledge in all major and sub-research fields to introduce New Methods and Ideas. MAKING NOVEL IDEAS IS THE ONLY WAY OF WINNING PHD.
2. Plagiarism-Free
To improve the quality and originality of works, we are strictly avoiding plagiarism since plagiarism is not allowed and acceptable for any type journals (SCI, SCI-E, or Scopus) in editorial and reviewer point of view. We have software named as “Anti-Plagiarism Software” that examines the similarity score for documents with good accuracy. We consist of various plagiarism tools like Viper, Turnitin, Students and scholars can get your work in Zero Tolerance to Plagiarism. DONT WORRY ABOUT PHD, WE WILL TAKE CARE OF EVERYTHING.
3. Confidential Info
We intended to keep your personal and technical information in secret and it is a basic worry for all scholars.
- Technical Info: We never share your technical details to any other scholar since we know the importance of time and resources that are giving us by scholars.
- Personal Info: We restricted to access scholars personal details by our experts. Our organization leading team will have your basic and necessary info for scholars.
CONFIDENTIALITY AND PRIVACY OF INFORMATION HELD IS OF VITAL IMPORTANCE AT PHDSERVICES.ORG. WE HONEST FOR ALL CUSTOMERS.
4. Publication
Most of the PhD consultancy services will end their services in Paper Writing, but our PhDservices.org is different from others by giving guarantee for both paper writing and publication in reputed journals. With our 18+ year of experience in delivering PhD services, we meet all requirements of journals (reviewers, editors, and editor-in-chief) for rapid publications. From the beginning of paper writing, we lay our smart works. PUBLICATION IS A ROOT FOR PHD DEGREE. WE LIKE A FRUIT FOR GIVING SWEET FEELING FOR ALL SCHOLARS.
5. No Duplication
After completion of your work, it does not available in our library i.e. we erased after completion of your PhD work so we avoid of giving duplicate contents for scholars. This step makes our experts to bringing new ideas, applications, methodologies and algorithms. Our work is more standard, quality and universal. Everything we make it as a new for all scholars. INNOVATION IS THE ABILITY TO SEE THE ORIGINALITY. EXPLORATION IS OUR ENGINE THAT DRIVES INNOVATION SO LET’S ALL GO EXPLORING.
Client Reviews
I ordered a research proposal in the research area of Wireless Communications and it was as very good as I can catch it.
I had wishes to complete implementation using latest software/tools and I had no idea of where to order it. My friend suggested this place and it delivers what I expect.
It really good platform to get all PhD services and I have used it many times because of reasonable price, best customer services, and high quality.
My colleague recommended this service to me and I’m delighted their services. They guide me a lot and given worthy contents for my research paper.
I’m never disappointed at any kind of service. Till I’m work with professional writers and getting lot of opportunities.
- Christopher
Once I am entered this organization I was just felt relax because lots of my colleagues and family relations were suggested to use this service and I received best thesis writing.
I recommend phdservices.org. They have professional writers for all type of writing (proposal, paper, thesis, assignment) support at affordable price.
You guys did a great job saved more money and time. I will keep working with you and I recommend to others also.
These experts are fast, knowledgeable, and dedicated to work under a short deadline. I had get good conference paper in short span.
Guys! You are the great and real experts for paper writing since it exactly matches with my demand. I will approach again.
I am fully satisfied with thesis writing. Thank you for your faultless service and soon I come back again.
Trusted customer service that you offer for me. I don’t have any cons to say.
I was at the edge of my doctorate graduation since my thesis is totally unconnected chapters. You people did a magic and I get my complete thesis!!!
- Abdul Mohammed
Good family environment with collaboration, and lot of hardworking team who actually share their knowledge by offering PhD Services.
I enjoyed huge when working with PhD services. I was asked several questions about my system development and I had wondered of smooth, dedication and caring.
I had not provided any specific requirements for my proposal work, but you guys are very awesome because I’m received proper proposal. Thank you!
- Bhanuprasad
I was read my entire research proposal and I liked concept suits for my research issues. Thank you so much for your efforts.
- Ghulam Nabi
I am extremely happy with your project development support and source codes are easily understanding and executed.
Hi!!! You guys supported me a lot. Thank you and I am 100% satisfied with publication service.
- Abhimanyu
I had found this as a wonderful platform for scholars so I highly recommend this service to all. I ordered thesis proposal and they covered everything. Thank you so much!!!
Related Pages
Academia.edu no longer supports Internet Explorer.
To browse Academia.edu and the wider internet faster and more securely, please take a few seconds to upgrade your browser .
Enter the email address you signed up with and we'll email you a reset link.
- We're Hiring!
- Help Center

Cloud Computing Security Vulnerabilities and Integrity Research Proposal

Related Papers
Web of Deceit - June 2022 - Creative Research Publishers - Open Access
Justin O N Y A R I N Ogala , Mughele, S.E
Cloud computing is one of the most popular terms in the computer industry right now. Virtualization enables resource sharing, which includes software, platform, and infrastructure. The underlying technology underpinning cloud resource sharing is virtualization. This environment aspires to be dynamic, dependable, and configurable, with a high level of service assurance. Security is just as important in the cloud as it is everywhere else. Various people have different perspectives on cloud computing. Some people feel that using the cloud is risky. Cloud providers go to great lengths to assure security. This study looks at a few important security vulnerabilities with cloud computing, as well as available remedies to those security issues in the cloud computing sector.
Journal of Interdisciplinary Cycle Research
Shailesh Gahane
Cloud computing allows you to share advantages over the Internet with the use of Internet composites, group of jobs, extra room and various programming initiatives. Cloud master associations can lease different benefits to customer needs and companies can pay for cloud client businesses. Nonetheless, the various security issues related to all cloud benefits, programming, virtualization, hardware, architectures, multitenant data and master associations are a fundamental barrier to cloud allocation in the IT business. 3 depicts security responses to prevent these risks, 4 Finishing the paper.
International Journal of Innovative Research in Computer and Communication Engineering
ILLANDULA SWATHI
Inside the ongoing decade, significant developments in technology have arisen that possibly add more accommodation to everyday life rehearses on an enterprise-level as well as on a singular level also. Cloud Computing technology has seen huge advances in its execution and becomes broadly received by one or the other private or public areas. It was clear as of late that many associations and enterprises are moving their outstanding tasks at hand to the cloud. In any case, Security is a significant worry for the cloud computing administrations, which depends on the Internet association that makes it powerless against numerous kinds of attacks. Despite the fact that that the security estimates executed over cloud computing are building up each spending year, Security still a test. In this paper, we led a review concentrate on cloud computing and tended to various kinds of attacks and potential dangers to this arising technology, just as assurance strategies and existing answers for such attacks.
IAEME PUBLICATION
IAEME Publication
Cloud Computing is a recent technology paradigm that enables organizations or individuals to share various services in a seamless, flexible and cost-effective manner. In the modern era of business operation, the technical adoption of cloud services are high on rise by the large scale to small scale business establishment on various products and services. Despite the potential gains achieved from the cloud computing, the organizations are slow in accepting it. Organizations which consider adopting cloud based services must also understand the many major problems of information policy including issues of privacy, security, reliability, access and regulation. There are various means by which introducing a malicious program inside the cloud is not that complicated task for attacker. The various services providers as well as past researcher have introduced some of the potential security features which is claimed to be highly effective. However, accomplishing fail-proof security systems in cloud is never witnessed nor reported by any user or researcher, which clearly specifies that security problems do persist and are on exponential rise. Therefore, this paper discusses about the security issues in cloud supported by brief description of standard security models currently available in cloud.
Dr. N. Jeyanthi
International Journal of Computer Science & Information Technology (IJCSIT)
Clouds provide a powerful computing platform that enables individuals and organizations to perform variety levels of tasks such as: use of online storage space, adoption of business applications, development of customized computer software, and creation of a “realistic” network environment. In previous years, the number of people using cloud services has dramatically increased and lots of data has been stored in cloud computing environments. In the meantime, data breaches to cloud services are also increasing every year due to hackers who are always trying to exploit the security vulnerabilities of the architecture of cloud. In this paper, three cloud service models were compared; cloud security risks and threats were investigated based on the nature of the cloud service models. Real world cloud attacks were included to demonstrate the techniques that hackers used against cloud computing systems. In addition, countermeasures to cloud security breaches are presented.
(IJIERT) International Journal of Innovations in Engineering Research and Technology IJIERT
This paper explores security challenges faced by cloud computing. It discusses the prevailing protection tactics to secure the cloud infrastructure, programs and drawbacks. Cloud computing started in the mid 90’s and one of its earlier users are Amazon and Ali Baba. It is growing really fast in the field of computer science. People nowadays are using cloud computing at a very vast level. Cloud computing is basically based on the Internet and has the most powerful architecture of computation. After a particular has deployed his/her cloud based platform, the biggest fear is its security. A cloud as mentioned earlier is all web-based which means that retrieving data from a particular cloud isn’t something impossible. As the use of cloud computing is growing, so are the security challenges. More people are getting aware of the technology which is making it easier for them to break into different clouds and retrieve their desired information. Many organizations have started offering cloud based solutions to their customers which has made security a major aim in their projects. On the other hand, many security experts are working on finding better security solutions. Even though security is getting better day by day but still hackers are finding ways to exploit a particular cloud. The Cloud security concern becomes more complex below the cloud model as many other fields continuously enter the Cloud computing industry
2012 IEEE International Conference on Systems, Man, and Cybernetics (SMC)
Nilima Dongre
TEMPAT MAGANG DI MALANG
"WA:0852-5756-6933, Apakah Anda Membutuhkan Info Tentang Daftar Tempat Prakerin Multimedia Di Malang,Daftar Tempat Prakerin Rpl,Daftar Tempat Prakerin Rpl Di Malang,Daftar Tempat Prakerin Smk Multimedia,Daftar Tempat Prakerin Tkj,Daftar Tempat Prakerin Tkj,Daftar Tempat Prakerin Tkj Di Malang,Daftar Tempat Prakerin Tkj Di Malang,Daftar Tempat Prakerin Tkj Di Malang,Dibuka Lowongan Magang 2020. Magang, OJT, PSG, Prakerin ataupun PKL adalah kurikulum wajib bagi Anda anak SMK, Akademi, Politeknik, Sekolah Tinggi ataupun Universitas. Dimana salah satu tujuannya buat Anda adalah Melatih Anda dalam dunia Kerja dan memperkenalkan ke dunia usaha ataupun Industri yang akan Anda terjuni nantinya setelah Anda Lulus Nantinya. IM-Pro Digital adalah sebuah perusahaan yang bergerak di bidang Internet Marketingmembuka kesempatan seluas-luasnya bagi anda Mahasiswa ataupun Anda siswa-siswi SMK jurusan Multimedia — RPL — TKJ untuk berkesempatan Magang ditempat kami. Keuntungan Magang, OJT, PSG, Prakerin ataupun PKL di IM-Pro Digital adalah : 1. Diajari materi marketing online ( FREE ) seperti : Video Marketing — Blog Marketing — Social Media marketing 2. Bisa jadi bekal setelah lulus sekolah untuk bisa mandiri, wiraswasta ataupun pengusaha dalam bidang Bisnis Online. 3. Mendapat Sertifikat Magang setelah Lulus Syarat untuk peserta Magang 1. Membawa Surat Pengantar dari Sekolah, Lembaga ataupun Universitas. 2. Membawa Laptop selama kegiatan Magang 3. Berkelakuan baik selama Masa Magang dan mengikuti aturan yang diberikan. Lokasi Magang: IM-Pro Digital - Taman Bandra Regency Blok F4 (daerah Bandara Abdul Rahman Saleh) Upek-Upek, Asrikaton, Pakis, Malang, Jawa Timur 65154 Informasi Hubungi: Bp Andrian Firmanto Telp/WA: 0852-5756-6933 (TELKOMSEL) Website: https://magangdi.improduk.com Note: Peserta dibatasi 10 orang setiap kelasnya. BURUAN DAFTAR SEBELUM PENUH!! "
Ailen Laconi
LEY ARTICULO 1°: Apruébase el Estatuto del Docente abarcativo del personal que se desempeña en todos los niveles, modalidades y especialidades de la Enseñanza y Organismos de Apoyo, cuyo texto como Anexo Unico forma parte de la presente ley. ARTICULO 2°: Derógase el Decreto-Ley 19.885/57. ARTICULO 3°: Comuníquese al Poder Ejecutivo. NOTA: Por Ley 11.612 (Ley de Educación) La Dirección General de Escuelas y Cultura, pasó a denominarse Dirección General de Cultura y Educación. ANEXO UNICO ESTATUTO DEL DOCENTE DE LA PROVINCIA DE BUENOS AIRES CAPITULO I DISPOSICIONES GENERALES ARTICULO 1°: El presente estatuto determina los deberes y derechos del personal docente que ejerce funciones en los establecimientos de enseñanza estatal, dependientes de la Dirección General de Escuelas y Cultura de la Provincia de Buenos Aires o en sus organismos, y cuyos cargos se encuentran comprendidos en el escalafón general que fija el estatuto. DE LA SITUACION DOCENTE ARTICULO 2°: Revistan en situación docente a los efectos de este estatuto quienes habilitados por títulos competentes: a) Imparten y guían la educación de los alumnos. b) Dirigen, supervisan u orientan la enseñanza en cualquiera de sus niveles, modalidades y especialidades. c) Colaboran directamente con las anteriores funciones. d) Realizar tareas de investigación y especialización técnico-docente. ARTICULO 3°: El personal docente contrae las obligaciones y adquiere los derechos establecidos en el presente estatuto, desde el momento en que se hace cargo de la función para la que es designado en carácter de titular, titular interino, provisional o suplente, con las limitaciones que en cada caso se determinen. ARTICULO 4°: La situación de revista del personal docente será:
RELATED PAPERS
Journal of Global Oncology
Prakash Gupta
Oncology Nursing Forum
Domanic Smith
Pediatric Research
Timothy Antonius
Mahmoud Abdel-Dayem
Turkiye Klinikleri Journal of Medical Ethics-Law and History
NÜKET BÜKEN
Journal of Geographical Systems
Lucien Benguigui
Modeling Control and Information Technologies
Dmytro Vinnichenko
Thiago Dutra de Araújo
Cynthia Bulley
Petra Grell
Scientia Agricola
Sarita LEONEL
Gelson Silva
Rheumatology International
ahmad fahmy mohamed
Journal of Weed Science and Technology
Mitsuhiro MATSUO
Cristina Mataloni
Journal of Food Science
Spectrochimica Acta Part A: Molecular and Biomolecular Spectroscopy
SACHIN MITTAL
Personal Care Magazine
Kelly Dobos
Sabina mason
Vasiliki Takou
Nabilla Nabilla
See More Documents Like This
RELATED TOPICS
- We're Hiring!
- Help Center
- Find new research papers in:
- Health Sciences
- Earth Sciences
- Cognitive Science
- Mathematics
- Computer Science
- Academia ©2024
Advances, Systems and Applications
- Open access
- Published: 12 July 2012
A quantitative analysis of current security concerns and solutions for cloud computing
- Nelson Gonzalez 1 ,
- Charles Miers 1 , 4 ,
- Fernando Redígolo 1 ,
- Marcos Simplício 1 ,
- Tereza Carvalho 1 ,
- Mats Näslund 2 &
- Makan Pourzandi 3
Journal of Cloud Computing: Advances, Systems and Applications volume 1 , Article number: 11 ( 2012 ) Cite this article
110k Accesses
122 Citations
10 Altmetric
Metrics details
The development of cloud computing services is speeding up the rate in which the organizations outsource their computational services or sell their idle computational resources. Even though migrating to the cloud remains a tempting trend from a financial perspective, there are several other aspects that must be taken into account by companies before they decide to do so. One of the most important aspect refers to security: while some cloud computing security issues are inherited from the solutions adopted to create such services, many new security questions that are particular to these solutions also arise, including those related to how the services are organized and which kind of service/data can be placed in the cloud. Aiming to give a better understanding of this complex scenario, in this article we identify and classify the main security concerns and solutions in cloud computing, and propose a taxonomy of security in cloud computing, giving an overview of the current status of security in this emerging technology.
Introduction
Security is considered a key requirement for cloud computing consolidation as a robust and feasible multi-purpose solution [ 1 ]. This viewpoint is shared by many distinct groups, including academia researchers [ 2 , 3 ], business decision makers [ 4 ] and government organizations [ 5 , 6 ]. The many similarities in these perspectives indicate a grave concern on crucial security and legal obstacles for cloud computing, including service availability, data confidentiality, provider lock-in and reputation fate sharing [ 7 ]. These concerns have their origin not only on existing problems, directly inherited from the adopted technologies, but are also related to new issues derived from the composition of essential cloud computing features like scalability, resource sharing and virtualization (e.g., data leakage and hypervisor vulnerabilities) [ 8 ]. The distinction between these classes is more easily identifiable by analyzing the definition of the essential cloud computing characteristics proposed by the NIST (National Institute of Standards and Technology) in [ 9 ], which also introduces the SPI model for services (SaaS, PaaS, and IaaS) and deployment (private, public, community, and hybrid).
Due to the ever growing interest in cloud computing, there is an explicit and constant effort to evaluate the current trends in security for such technology, considering both problems already identified and possible solutions [ 10 ]. An authoritative reference in the area is the risk assessment developed by ENISA (European Network and Information Security Agency) [ 5 ]. Not only does it list risks and vulnerabilities, but it also offers a survey of related works and research recommendations. A similarly work is the security guidance provided by the Cloud Security Alliance (CSA) [ 6 ], which defines security domains congregating specific functional aspects, from governance and compliance to virtualization and identity management. Both documents present a plethora of security concerns, best practices and recommendations regarding all types of services in NIST’s SPI model, as well as possible problems related to cloud computing, encompassing from data privacy to infrastructural configuration. Albeit valuable, these studies do not focus on quantifying their observations, something important for developing a comprehensive understanding of the challenges still undermining the potential of cloud computing.
The main goal of this article is to identify, classify, organize and quantify the main security concerns and solutions associated to cloud computing, helping in the task of pinpointing the concerns that remain unanswered. Aiming to organize this information into a useful tool for comparing, relating and classifying already identified concerns and solutions as well as future ones, we also present a taxonomy proposal for cloud computing security. We focus on issues that are specific to cloud computing, without losing sight of important issues that also exist in other distributed systems. This article extends our previous work presented in [ 11 ], providing an enhanced review of the cloud computing security taxonomy previously presented, as well as a deeper analysis of the related work by discussing the main security frameworks currently available; in addition, we discuss further the security aspects related to virtualization in cloud computing, a fundamental yet still underserved field of research.
Cloud computing security
Key references such as CSA’s security guidance [ 6 ] and top threats analysis [ 12 ], ENISA’s security assessment [ 5 ] and the cloud computing definitions from NIST [ 9 ] highlight different security issues related to cloud computing that require further studies for being appropriately handled and, consequently, for enhancing technology acceptance and adoption. Emphasis is given to the distinction between services in the form of software (SaaS), platform (PaaS) and infrastructure (IaaS), which are commonly used as the fundamental basis for cloud service classification. However, no other methods are standardized or even employed to organize cloud computing security aspects apart from cloud deployment models, service types or traditional security models.
Aiming to concentrate and organize information related to cloud security and to facilitate future studies, in this section we identify the main problems in the area and group them into a model composed of seven categories, based on the aforementioned references . Namely, the categories are: network security, interfaces, data security, virtualization, governance, compliance and legal issues. Each category includes several potential security problems, resulting in a classification with subdivisions that highlights the main issues identified in the base references:
Network security: Problems associated with network communications and configurations regarding cloud computing infrastructures. The ideal network security solution is to have cloud services as an extension of customers’ existing internal networks [ 13 ], adopting the same protection measures and security precautions that are locally implemented and allowing them to extend local strategies to any remote resource or process [ 14 ].
Transfer security: Distributed architectures, massive resource sharing and virtual machine (VM) instances synchronization imply more data in transit in the cloud, thus requiring VPN mechanisms for protecting the system against sniffing, spoofing, man-in-the-middle and side-channel attacks.
Firewalling: Firewalls protect the provider’s internal cloud infrastructure against insiders and outsiders [ 15 ]. They also enable VM isolation, fine-grained filtering for addresses and ports, prevention of Denial-of-Service (DoS) and detection of external security assessment procedures. Efforts for developing consistent firewall and similar security measures specific for cloud environments [ 16 , 17 ] reveal the urge for adapting existing solutions for this new computing paradigm.
Security configuration: Configuration of protocols, systems and technologies to provide the required levels of security and privacy without compromising performance or efficiency [ 18 ].
Interfaces: Concentrates all issues related to user, administrative and programming interfaces for using and controlling clouds.
API: Programming interfaces (essential to IaaS and PaaS) for accessing virtualized resources and systems must be protected in order to prevent malicious use [ 19 – 23 ].
Administrative interface: Enables remote control of resources in an IaaS (VM management), development for PaaS (coding, deploying, testing) and application tools for SaaS (user access control, configurations).
User interface: End-user interface for exploring provided resources and tools (the service itself), implying the need of adopting measures for securing the environment [ 24 – 27 ].
Authentication: Mechanisms required to enable access to the cloud [ 28 ]. Most services rely on regular accounts [ 20 , 29 , 30 ] consequently being susceptible to a plethora of attacks [ 31 – 35 ] whose consequences are boosted by multi-tenancy and resource sharing.
Data security: Protection of data in terms of confidentiality, availability and integrity (which can be applied not only to cloud environments, but any solution requiring basic security levels) [ 36 ].
Cryptography: Most employed practice to secure sensitive data [ 37 ], thoroughly required by industry, state and federal regulations [ 38 ].
Redundancy: Essential to avoid data loss. Most business models rely on information technology for its core functionalities and processes [ 39 , 40 ] and, thus, mission-critical data integrity and availability must be ensured.
Disposal: Elementary data disposal techniques are insufficient and commonly referred as deletion [ 41 ].In the cloud, the complete destruction of data, including log references and hidden backup registries, is an important requirement [ 42 ].
Virtualization: Isolation between VMs, hypervisor vulnerabilities and other problems associated to the use of virtualization technologies [ 43 ].
Isolation: Although logically isolated, all VMs share the same hardware and consequently the same resources, allowing malicious entities to exploit data leaks and cross-VM attacks [ 44 ]. The concept of isolation can also be applied to more fine-grained assets, such as computational resources, storage and memory.
Hypervisor vulnerabilities: The hypervisor is the main software component of virtualization. Even though there are known security vulnerabilities for hypervisors, solutions are still scarce and often proprietary, demanding further studies to harden these security aspects.
Data leakage: Exploit hypervisor vulnerabilities and lack of isolation controls in order to leak data from virtualized infrastructures, obtaining sensitive customer data and affecting confidentiality and integrity.
VM identification: Lack of controls for identifying virtual machines that are being used for executing a specific process or for storing files.
Cross-VM attacks: Includes attempts to estimate provider traffic rates in order to steal cryptographic keys and increase chances of VM placement attacks. One example consists in overlapping memory and storage regions initially dedicated to a single virtual machine, which also enables other isolation-related attacks.
Governance: Issues related to (losing) administrative and security controls in cloud computing solutions [ 45 , 46 ].
Data control: Moving data to the cloud means losing control over redundancy, location, file systems and other relevant configurations.
Security control: Loss of governance over security mechanisms and policies, as terms of use prohibit customer-side vulnerability assessment and penetration tests while insufficient Service Level Agreements (SLA) lead to security gaps.
Lock-in: User potential dependency on a particular service provider due to lack of well-established standards (protocols and data formats), consequently becoming particularly vulnerable to migrations and service termination.
Compliance: Includes requirements related to service availability and audit capabilities [ 47 , 48 ].
Service Level Agreements (SLA): Mechanisms to ensure the required service availability and the basic security procedures to be adopted [ 49 ].
Loss of service: Service outages are not exclusive to cloud environments but are more serious in this context due to the interconnections between services (e.g., a SaaS using virtualized infrastructures provided by an IaaS), as shown in many examples [ 50 – 52 ]. This leads to the need of strong disaster recovery policies and provider recommendations to implement customer-side redundancy if applicable.
Audit: Allows security and availability assessments to be performed by customers, providers and third-party participants. Transparent and efficient methodologies are necessary for continuously analyzing service conditions [ 53 ] and are usually required by contracts or legal regulations. There are solutions being developed to address this problem by offering a transparent API for automated auditing and other useful functionalities [ 54 ].
Service conformity: Related to how contractual obligations and overall service requirements are respected and offered based on the SLAs predefined and basic service and customer needs.
Legal issues: Aspects related to judicial requirements and law, such as multiple data locations and privilege management.
Data location: Customer data held in multiple jurisdictions depending on geographic location [ 55 ] are affected, directly or indirectly, by subpoena law-enforcement measures.
E-discovery: As a result of a law-enforcement measures, hardware might be confiscated for investigations related to a particular customer, affecting all customers whose data were stored in the same hardware [ 56 – 58 ]. Data disclosure is critical in this case.
Provider privilege: Malicious activities of provider insiders are potential threats to confidentiality, availability and integrity of customers’ data and processes’ information [ 59 , 60 ].
legislation: Juridical concerns related to new concepts introduced by cloud computing [ 61 ].
Cloud computing security taxonomy
The analysis of security concerns in the context of cloud computing solutions shows that each issue brings different impacts on distinct assets. Aiming to create a security model both for studying security aspects in this context and for supporting decision making, in this section we consider the risks and vulnerabilities previously presented and arrange them in hierarchical categories, thus creating a cloud security taxonomy. The main structure of the proposed taxonomy, along with its first classification levels, are depicted in Figure 1 .

Cloud computing security taxonomy. Top level overview of the security taxonomy proposed, highlighting the three main categories: security related to privacy, architecture and compliance.
The three first groups correspond to fundamental (and often related) security principles [ 7 ] (Chapters 3-8).
The architecture dimension is subdivided into network security, interfaces and virtualization issues, comprising both user and administrative interfaces to access the cloud. It also comprises security during transferences of data and virtual machines, as well as other virtualization related issues, such as isolation and cross-VM attacks. This organization is depicted in Figure 2 . The architecture group allows a clearer division of responsibilities between providers and customers, and also an analysis of their security roles depending on the type of service offered (Software, Platform or Infrastructure). This suggests that the security mechanisms used must be clearly stated before the service is contracted, defining which role is responsible for providing firewalling capabilities, access control features and technology-specific requirements (such as those related to virtualization).
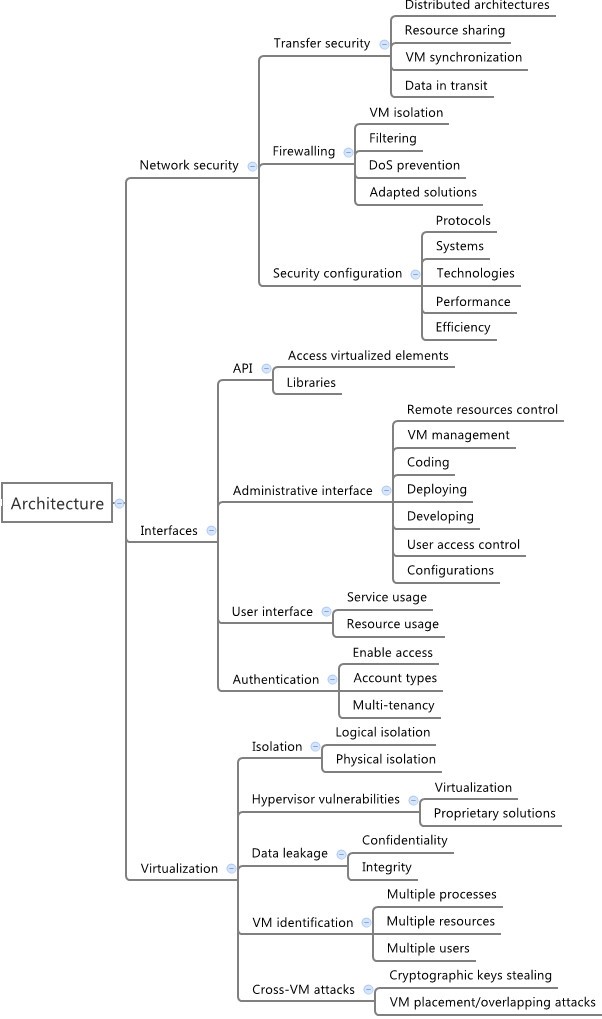
Security taxonomy - architecture. Details from architecture category, which is divided in network, host, application, data (security and storage), security management, and identity and access controls – all these elements are directly connected to the infrastructure and architecture adopted to implement or use a cloud solution.
The compliance dimension introduces responsibilities toward services and providers. The former includes SLA concerns, loss of service based on outages and chain failures, and auditing capabilities as well as transparency and security assessments. The latter refers to loss of control over data and security policies and configurations, and also lock-in issues resulting from lack of standards, migrations and service terminations. The complete scenario is presented in Figure 3 .
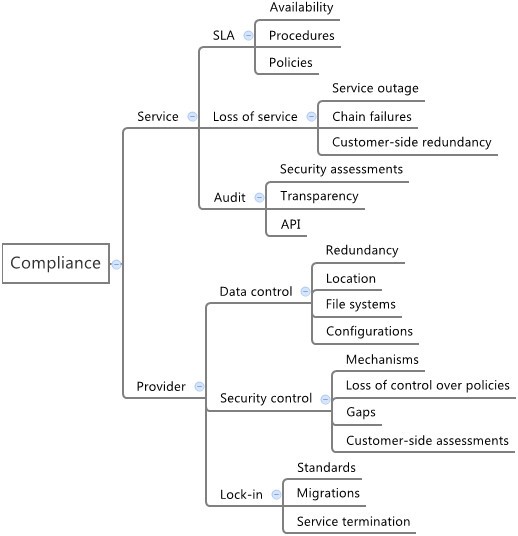
Security taxonomy - compliance. Details from compliance category, divided in lifecycle controls and governance, risk and other compliance related issues (such as continuous improvement policies).
The privacy dimension includes data security itself (from sensitive data, regulations and data loss to disposal and redundancy) and legal issues (related to multiple jurisdictions derived from different locations where data and services are hosted). The expansion of this group is represented in Figure 4 . We note that the concerns in this dimension cover the complete information lifecycle (i.e., generation, use, transfer, transformation, storage, archiving, and destruction ) inside the provider perimeter and in its immediate boundaries (or interfaces) to the users.
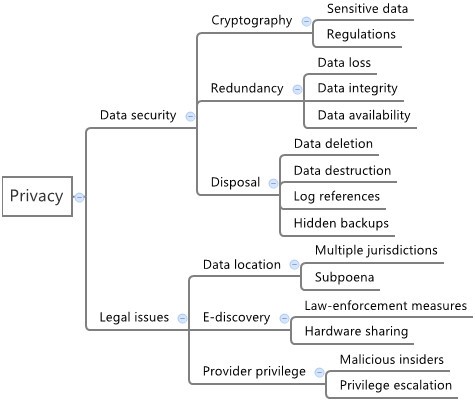
Security taxonomy - privacy. Details from privacy category, initially divided in concerns and principles. Concerns are related to the complete data lifecycle, from generation, use and transfer to transformation, storage, archival and destruction. Principles are guidelines related to privacy in the cloud.
A common point between all groups is the intrinsic connection to data and service lifecycles. Both privacy and compliance must be ensured through all states of data, including application information or customer assets, while security in this case is more oriented towards how the underlying elements (e.g., infrastructural hardware and software) are protected.
Current status of cloud security
A clear perspective of the main security problems regarding cloud computing and on how they can be organized to ease decision making is the primary step for having a comprehensive overview of the current status of cloud security. In this section, we analyze industry and academia viewpoints focusing on strategic study areas that need to be further developed. This study is based on more than two hundred different references including white papers, technical reports, scientific papers and other relevant publications. They were analyzed in terms of security problems and solutions by evaluating the number of citations for each case. We used a quantitative approach to identify the amount of references related to each category of concerns or solutions. Our goal is not to determine if the presented solutions completely solve an identified concern, since most of the referenced authors agree that this is an involved task. Nonetheless, we identify the number of references dealing with each concern, providing some useful insight on which are the concerns that have received more attention from the research community and which have not been so extensively analyzed. Some observations about the analysis method:
The references consulted came from different research segments, including academia, organizations, and companies. Due to the article’s length limitations, we did not include all the consulted references in the References section. In the following we present some of the main sources of consultation:
Academia: conference papers and journals published by IEEE, ACM, Springer, Webscience, and Scipress.
Organizations: reports, white papers, and interviews from SANS Institute, CSA, NIST, ENISA, Gartner Group, KVM.org, OpenGrid, OpenStack, and OpenNebula.
Companies: white papers, manuals, interviews, and web content from ERICSSON, IBM, XEROX, Cisco, VMWare, XEN, CITRIX, EMC, Microsoft, and Salesforce.
Each reference was analyzed aiming to identify all the mentioned concerns covered and solutions provided. Therefore, one reference can produce more than one entry on each specified category.
Some security perspectives were not covered in this paper, as each security/concern category can be sub-divided in finer-grained aspects such as: authentication, integrity, network communications, etc.
We present the security concerns and solutions using pie charts in order to show the representativeness of each category/group in the total amount of references identified. The comparison between areas is presented using radar graphs to identify how many solutions address each concern category/group.
Security concerns
The results obtained for the number of citations on security issues is shown in Figure 5 . The three major problems identified in these references are legal issues, compliance and loss of control over data. These legal- and governance-related concerns are followed by the first technical issue, isolation, with 7% of citations. The least cited problems are related to security configuration concerns, loss of service (albeit this is also related to compliance, which is a major problem), firewalling and interfaces.
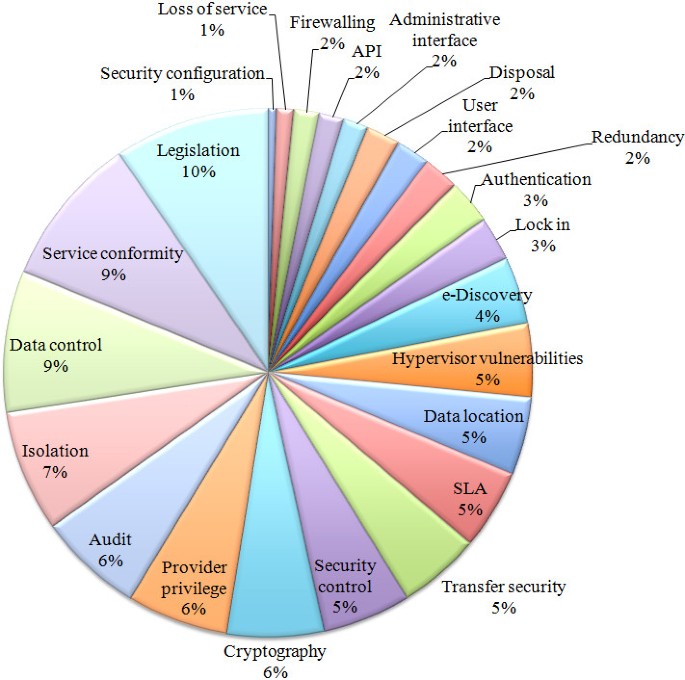
Security problems. Pie chart for security concerns.
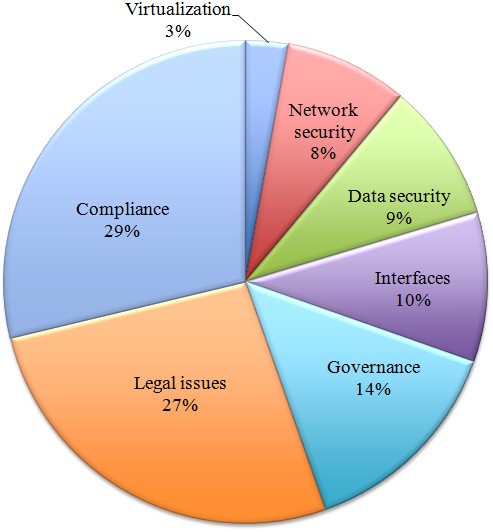
Grouping the concerns using the categories presented in section “Cloud computing security” leads to the construction of Figure 6 . This figure shows that legal and governance issues represent a clear majority with 73% of concern citations, showing a deep consideration of legal issues such as data location and e-discovery, or governance ones like loss of control over security and data. The technical issue more intensively evaluated (12%) is virtualization, followed by data security, interfaces and network security.

Security problems with grouped categories. Pie chart for security concerns with grouped categories (seven altogether: legal issues, compliance, governance, virtualization, data security, interfaces and network security).
Virtualization is one of the main novelties employed by cloud computing in terms of technologies employed, considering virtual infrastructures, scalability and resource sharing, and its related problems represent the first major technical concern.
Security solutions
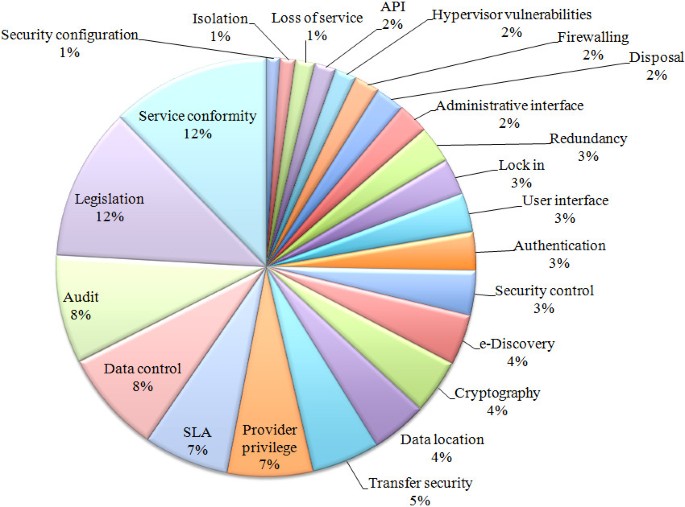
When analyzing citations for solutions, we used the same approach described in the beginning of this section. The results are presented in Figure 7 , which shows the percentage of solutions in each category defined in section “Cloud computing security”, and also in Figure 8 , which highlights the contribution of each individual sub-category.
Security solutions with grouped categories. Pie chart for solutions with grouped categories, showing a clear lack for virtualization security mechanisms in comparison to its importance in terms of concerns citations.
Security solutions. Pie chart for solutions citations.
When we compare Figures 6 and 7 , it is easy to observe that the number of citations covering security problems related to legal issues, compliance and governance is high (respectively 24%, 22%, and 17%); however, the same also happens when we consider the number of references proposing solutions for those issues (which represent respectively 29%, 27%, and 14% of the total number of citations). In other words, these concerns are higly relevant but a large number solutions are already available for tackling them.
The situation is completely different when we analyze technical aspects such as virtualization, isolation and data leakage. Indeed, virtualization amounts for 12% of problem references and only 3% for solutions. Isolation is a perfect example of such discrepancy as the number of citations for such problems represents 7% in Figure 5 , while solutions correspond to only 1% of the graph from Figure 8 . We note that, for this specific issue, special care has been taken when assessing the most popular virtual machine solution providers (e.g., XEN, VMWARE, and KVM) aiming to verify their concerns and available solutions. A conclusion that can be drawn from this situation is that such concerns are also significant but yet little is available in terms of solutions. This indicates the need of evaluating potential areas still to be developed in order to provide better security conditions when migrating data and processes in the cloud.
The differences between problem and solution citations presented in the previous sections can be observed in Figure 9 .
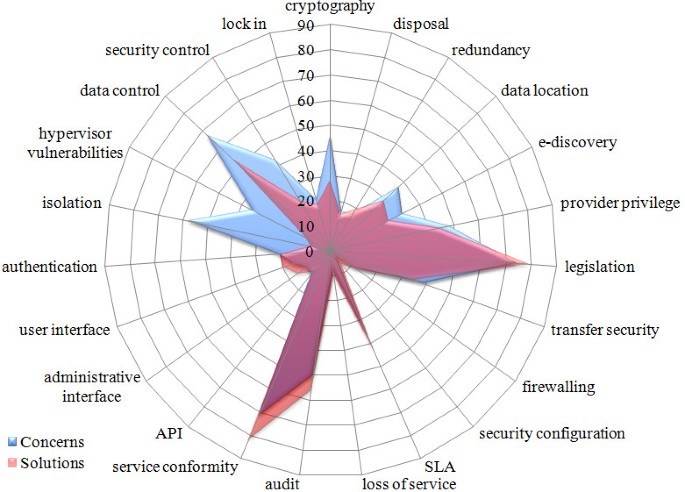
Comparison between citations. Radar chart comparing citations related to concerns and solutions, showing the disparities for each security category adopted.
Axis values correspond to the number of citations found among the references studied. Blue areas represent concern citations and lighter red indicates solutions, while darker red shows where those areas overlap. In other words, light red areas are problems with more citations for solutions than problems – they might be meaningful problems, but there are many solutions already addressing them – while blue areas represent potential subjects that have received little attention so far, indicating the need for further studies.
Figure 9 clearly shows the lack of development regarding data control mechanisms, hypervisor vulnerabilities assessment and isolation solutions for virtualized environments. On the other hand, areas such as legal concerns, SLAs, compliance and audit policies have a quite satisfactory coverage. The results for grouped categories (presented in section 4) are depicted in Figure 10 .
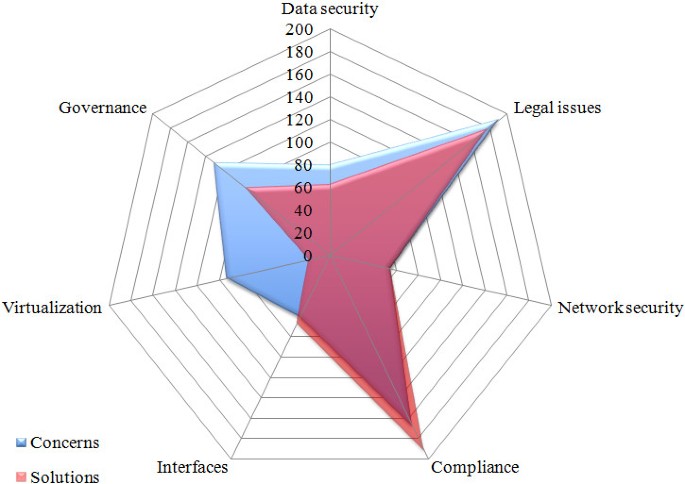
Comparison between citations with grouped categories. Radar chart grouping the categories, showing the difference between citations about concerns and solutions regarding each category.
Figure 10 shows that virtualization problems represent an area that requires studies for addressing issues such as isolation, data leakage and cross-VM attacks; on the other hand, areas such as compliance and network security encompass concerns for which there are already a considerable number of solutions or that are not considered highly relevant.
Finally, Considering virtualization as key element for future studies, Figure 11 presents a comparison focusing on five virtualization-related problems: isolation (of computational resources, such as memory and storage capabilities), hypervisor vulnerabilities, data leakage, cross-VM attacks and VM identification. The contrast related to isolation and cross-VM attacks is more evident than for the other issues. However, the number of solution citations for all issues is notably low if compared to any other security concern, reaffirming the need for further researches in those areas.

Comparison for virtualization. Radar chart only for virtualization issues.
Related work
An abundant number of related works and publications exist in the literature, emphasizing the importance and demand of security solutions for cloud computing. However, we did not identify any full taxonomy that addresses directly the security aspects related to cloud computing. We only identified some simplified models that were developed to cover specific security aspects such as authentication. We were able to recognize two main types of works: (1) security frameworks, which aim to aggregate information about security and also to offer sets of best practices and guidelines when using cloud solutions, and (2) publications that identify future trends and propose solutions or areas of interest for research. Each category and corresponding references are further analyzed in the following subsections.
Security frameworks
Security frameworks concentrate information on security and privacy aiming to provide a compilation of risks, vulnerabilities and best practices to avoid or mitigate them. There are several entities that are constantly publishing material related to cloud computing security, including ENISA, CSA, NIST, CPNI (Centre for the Protection of National Infrastructure from UK government) and ISACA (the Information Systems Audit and Control Association). In this paper we focus on the first three entities, which by themselves provide a quite comprehensive overview of issues and solutions and, thus, allowing a broad understanding of the current status of cloud security.
ENISA is an agency responsible for achieving high and effective level of network and information security within the European Union [ 62 ]. In the context of cloud computing, they published an extensive study covering benefits and risks related to its use [ 5 ]. In this study, the security risks are divided in four categories:
• Policy and organizational: issues related Policy and organizational: issues related to governance, compliance and reputation;
• Technical: issues derived from technologies used to implement cloud services and infrastructures, such as isolation, data leakage and interception, denial of service attacks, encryption and disposal;
• Legal: risks regarding jurisdictions, subpoena and e-discovery;
• Not cloud specific: other risks that are not unique to cloud environments, such as network management, privilege escalation and logging;
As a top recommendation for security in cloud computing, ENISA suggests that providers must ensure some security practices to customers and also a clear contract to avoid legal problems. Key points to be developed include breach reporting, better logging mechanisms and engineering of large scale computer systems, which encompass the isolation of virtual machines, resources and information. Their analysis is based not only on what is currently observed, but also on what can be improved through the adoption of existing best practices or by means of solutions that are already used in non-cloud environments. This article aims at taking one step further by transforming these observations into numbers – a quantitative approach.
CSA is an organization led by a coalition of industry practitioners, corporations, associations and other stakeholders [ 63 ], such as Dell, HP and eBay. One of its main goals is to promote the adoption of best practices for providing security within cloud computing environments.
Three CSA documents are analyzed in this paper – the security guidance [ 6 ], the top threats in cloud computing [ 12 ] and the Trusted Cloud Initiative (TCI) architecture [ 64 ] – as they comprise most of the concepts and guidelines researched and published by CSA.
The latest CSA security guidance (version 3.0 [ 65 ]) denotes multi-tenancy as the essential cloud characteristic while virtualization can be avoided when implementing cloud infrastructures – multi-tenancy only implies the use of shared resources by multiple consumers, possibly from different organizations or with different objectives. They discuss that, even if virtualization-related issues can be circumvented, segmentation and isolated policies for addressing proper management and privacy are still required. The document also establishes thirteen security domains:
Governance and risk management: ability to measure the risk introduced by adopting cloud computing solutions, such as legal issues, protection of sensitive data and their relation to international boundaries;
Legal issues: disclosure laws, shared infrastructures and interference between different users;
Compliance and audit: the relationship between cloud computing and internal security policies;
Information management and data security: identification and control of stored data, loss of physical control of data and related policies to minimize risks and possible damages;
Portability and interoperability: ability to change providers, services or bringing back data to local premises without major impacts;
Traditional security, business continuity and disaster recovery: the influence of cloud solutions on traditional processes applied for addressing security needs;
Data center operations: analyzing architecture and operations from data centers and identifying essential characteristics for ensuring stability;
Incident response, notification and remediation: policies for handling incidents;
Application security: aims to identify the possible security issues raised from migrating a specific solution to the cloud and which platform (among SPI model) is more adequate;
Encryption and key management: how higher scalability via infrastructure sharing affects encryption and other mechanisms used for protecting resources and data;
Identity and access management: enabling authentication for cloud solutions while maintaining security levels and availability for customers and organizations;
Virtualization: risks related to multi-tenancy, isolation, virtual machine co-residence and hypervisor vulnerabilities, all introduced by virtualization technologies;
Security as a service: third party security mechanisms, delegating security responsibilities to a trusted third party provider;
CSA also published a document focusing on identifying top threats, aiming to aid risk management strategies when cloud solutions are adopted [ 12 ]. As a complete list of threats and pertinent issues is countless, the document targets those that are specific or intensified by fundamental characteristics of the cloud, such as shared infrastructures and greater flexibility. As a result, seven threats were selected:
Abuse and nefarious used of cloud computing: while providing flexible and powerful resources and tools, IaaS and PaaS solutions also unveil critical exploitation possibilities built on anonymity. This leads to abuse and misuse of the provided infrastructure for conducting distributed denial of service attacks, hosting malicious data, controlling botnets or sending spam;
Insecure application programming interfaces: cloud services provide APIs for management, storage, virtual machine allocation and other service-specific operations. The interfaces provided must implement security methods to identify, authenticate and protect against accidental or malicious use, which can introduce additional complexities to the system such as the need for third-party authorities and services;
Malicious insiders: although not specific to cloud computing, its effects are amplified by the concentration and interaction of services and management domains;
Shared technology vulnerabilities: scalability provided by cloud solutions are based on hardware and software components which are not originally designed to provide isolation. Even though hypervisors offer an extra granularity layer, they still exhibit flaws which are exploited for privilege escalation;
Data loss and leakage: insufficient controls concerning user access and data security (including privacy and integrity), as well as disposal and even legal issues;
Account, service and traffic hijacking: phishing and related frauds are not a novelty to computing security. However, not only an attacker is able to manipulate data and transactions, but also to use stolen credentials to perform other attacks that compromise customer and provider reputation.
Unknown risk profile: delegation of control over data and infrastructure allows companies to better concentrate on their core business, possibly maximizing profit and efficiency. On the other hand, the consequent loss of governance leads to obscurity [ 66 ]: information about other customers sharing the same infrastructure or regarding patching and updating policies is limited. This situation creates uncertainty concerning the exact risk levels that are inherent to the cloud solution;
It is interesting to notice the choice for cloud-specific issues as it allows the identification of central points for further development. Moreover, this compilation of threats is closely related to CSA security guidance, composing a solid framework for security and risk analysis assessments while providing recommendations and best practices to achieve acceptable security levels.
Another approach adopted by CSA for organizing information related to cloud security and governance is the TCI Reference Architecture Model [ 64 ]. This document focuses on defining guidelines for enabling trust in the cloud while establishing open standards and capabilities for all cloud-based operations. The architecture defines different organization levels by combining frameworks like the SPI model, ISO 27002, COBIT, PCI, SOX and architectures such as SABSA, TOGAF, ITIL and Jericho. A wide range of aspects are then covered: SABSA defines business operation support services, such as compliance, data governance, operational risk management, human resources security, security monitoring services, legal services and internal investigations; TOGAF defines the types of services covered (presentation, application, information and infrastructure; ITIL is used for information technology operation and support, from IT operation to service delivery, support and management of incidents, changes and resources; finally, Jericho covers security and risk management, including information security management, authorization, threat and vulnerability management, policies and standards. The result is a tri-dimensional relationship between cloud delivery, trust and operation that aims to be easily consumed and applied in a security-oriented design.
NIST has recently published a taxonomy for security in cloud computing [ 67 ] that is comparable to the taxonomy introduced in section “Cloud computing security taxonomy”. This taxonomy’s first level encompass typical roles in the cloud environment: cloud service provider, responsible for making the service itself available; cloud service consumer, who uses the service and maintains a business relationship with the provider; cloud carrier, which provides communication interfaces between providers and consumers; cloud broker, that manages use, performance and delivery of services and intermediates negotiations between providers and consumers; and cloud auditor, which performs assessment of services, operations and security. Each role is associated to their respective activities and decomposed on their components and subcomponents. The clearest difference from our taxonomy is the hierarchy adopted, as our proposal primarily focuses on security principles in its higher level perspective, while the cloud roles are explored in deeper levels. The concepts presented here extend NIST’s initial definition for cloud computing [ 9 ], incorporating a division of roles and responsibilities that can be directly applied to security assessments. On the other hand, NIST’s taxonomy incorporates concepts such as deployment models, service types and activities related to cloud management (portability, interoperability, provisioning), most of them largely employed in publications related to cloud computing – including this one.
Frameworks summary
Tables 1 and 2 summarize the information about each framework.
Books, papers and other publications
Rimal, Choi and Lumb [ 3 ] present a cloud taxonomy created from the perspective of the academia, developers and researchers, instead of the usual point of view related to vendors. Whilst they do provide definitions and concepts such as cloud architecture (based on SPI model), virtualization management, service types, fault tolerance policies and security, no further studies are developed focusing on cloud specific security aspects. This characteristic is also observed in other cloud taxonomies [ 68 – 70 ] whose efforts converge to the definition of service models and types rather than to more technical aspects such as security, privacy or compliance concerns – which are the focus of this paper.
In [ 7 ], Mather, Kumaraswamy and Latif discuss the current status of cloud security and what is predicted for the future. The result is a compilation of security-related subjects to be developed in topics like infrastructure, data security and storage, identity and access management, security management, privacy, audit and compliance. They also explore the unquestionable urge for more transparency regarding which party (customer or cloud provider) provides each security capability, as well as the need for standardization and for the creation of legal agreements reflecting operational SLAs. Other issues discussed are the inadequate encryption and key management capabilities currently offered, as well as the need for multi-entity key management.
Many publications also state the need for better security mechanisms for cloud environments. Doelitzscher et al. [ 71 ] emphasize security as a major research area in cloud computing. They also highlight the lack of flexibility of classic intrusion detection mechanisms to handle virtualized environments, suggesting the use of special security audit tools associated to business flow modeling through security SLAs. In addition, they identify abuse of cloud resources, lack of security monitoring in cloud infrastructure and defective isolation of shared resources as focal points to be managed. Their analysis of top security concerns is also based on publications from CSA, ENISA and others, but after a quick evaluation of issues their focus switch to their security auditing solution, without offering a deeper quantitative compilation of security risks and areas of concern.
Associations such as the Enterprise Strategy Group [ 72 ] emphasize the need for hypervisor security, shrinking hypervisor footprints, defining the security perimeter virtualization, and linking security and VM provisioning for better resource management. Aiming to address these requirements, they suggest the use of increased automation for security controls, VM identity management (built on top of Public Key Infrastructure and Open Virtualization Format) and data encryption (tightly connected to state-of-art key management practices). Wallom et al. [ 73 ] emphasize the need of guaranteeing virtual machines’ trustworthiness (regarding origin and identity) to perform security-critical computations and to handle sensitive data, therefore presenting a solution which integrates Trusted Computing technologies and available cloud infrastructures. Dabrowski and Mills [ 74 ] used simulation to demonstrate virtual machine leakage and resource exhaustion scenarios leading to degraded performance and crashes; they also propose the addition of orphan controls to enable the virtualized cloud environment to offer higher availability levels while keeping overhead costs under control. Ristenpart et al. [ 44 ] also explore virtual machine exploitation focusing on information leakage, specially sensitive data at rest or in transit. Finally, Chadwick and Casenove [ 75 ] describe a security API for federated access to cloud resources and authority delegation while setting fine-grained controls and guaranteeing the required levels of assurance inside cloud environments. These publications highlight the need of security improvements related to virtual machines and virtualization techniques, concern that this paper demonstrates to be valid and urgent.
Considering the points raised in the previous section, a straightforward conclusion is that cloud security includes old and well-known issues – such as network and other infrastructural vulnerabilities, user access, authentication and privacy – and also novel concerns derived from new technologies adopted to offer the adequate resources (mainly virtualized ones), services and auxiliary tools. These problems are summarized by isolation and hypervisor vulnerabilities (the main technical concerns according to the studies and graphics presented), data location and e-discovery (legal aspects), and loss of governance over data, security and even decision making (in which the cloud must be strategically and financially considered as a decisive factor).
Another point observed is that, even though adopting a cloud service or provider may be easy, migrating to another is not [ 76 ]. After moving local data and processes to the cloud, the lack of standards for protocols and formats directly affects attempts to migrate to a different provider even if this is motivated by legitimate reasons such as non-fulfillment of SLAs, outages or provider bankruptcy [ 77 ]. Consequently, the first choice must be carefully made, as SLAs are not perfect and services outages happen at the same pace that resource sharing, multi-tenancy and scalability are not fail proof. After a decision is made, future migrations between services can be extremely onerous in terms of time and costs; most likely, this task will require an extensive work for bringing all data and resources to a local infrastructure before redeploying them into the cloud.
Finally, the analysis of current trends for cloud computing reveals that there is a considerable number of well-studied security concerns, for which plenty solutions and best practices have been developed, such as those related to legal and administrative concerns. On the other hand, many issues still require further research effort, especially those related to secure virtualization.
Considerations and future work
Security is a crucial aspect for providing a reliable environment and then enable the use of applications in the cloud and for moving data and business processes to virtualized infrastructures. Many of the security issues identified are observed in other computing environments: authentication, network security and legal requirements, for example, are not a novelty. However, the impact of such issues is intensified in cloud computing due to characteristics such as multi-tenancy and resource sharing, since actions from a single customer can affect all other users that inevitably share the same resources and interfaces. On the other hand, efficient and secure virtualization represents a new challenge in such a context with high distribution of complex services and web-based applications, thus requiring more sophisticated approaches. At the same time, our quantitative analysis indicates that virtualization remains an underserved area regarding the number of solutions provided to identified concerns.
It is strategic to develop new mechanisms that provide the required security level by isolating virtual machines and the associated resources while following best practices in terms of legal regulations and compliance to SLAs. Among other requirements, such solutions should employ virtual machine identification, provide an adequate separation of dedicated resources combined with a constant observation of shared ones, and examine any attempt of exploiting cross-VM and data leakage.
A secure cloud computing environment depends on several security solutions working harmoniously together. However, in our studies we did not identify any security solutions provider owning the facilities necessary to get high levels of security conformity for clouds. Thus, cloud providers need to orchestrate / harmonize security solutions from different places in order to achieve the desired security level.
In order to verify these conclusions in practice, we deployed testbeds using OpenNebula (based on KVM and XEN) and analyzed its security aspects; we also analyzed virtualized servers based on VMWARE using our testbed networks. This investigation lead to a wide research of PaaS solutions, and allowed us to verify that most of them use virtual machines based on virtualization technologies such as VMWARE, XEN, and KVM, which often lack security aspects We also learned that Amazon changed the XEN source code in order to include security features, but unfortunately the modified code is not publicly available and there appears to be no article detailing the changes introduced. Given these limitations, a deeper study on current security solutions to manage cloud computing virtual machines inside the cloud providers should be a focus of future work in the area. We are also working on a testbed based on OpenStack for researches related to identity and credentials management in the cloud environment. This work should address basic needs for better security mechanisms in virtualized and distributed architectures, guiding other future researches in the security area.
IDC: Cloud Computing 2010 – An IDC Update. 2009. slideshare.net/JorFigOr/cloud-computing-2010-an-idc-update
Google Scholar
Armbrust M, Fox A, Griffith R, Joseph AD, Katz RH, Konwinski A, Lee G, Patterson DA, Rabkin A, Stoica I, Zaharia M: Above the Clouds: A Berkeley View of Cloud Computing. 2009. Technical Report UCB/EECS-2009-28, University of California at Berkeley, eecs.berkeley.edu/Pubs/TechRpts/2009/EECS-2009-28.html
Rimal BP, Choi E, Lumb I: A Taxonomy and, Survey of Cloud Computing Systems. Fifth International Joint Conference on INC, IMSand IDC, NCM '09, CPS 2009. pp 44–51 pp 44–51
Shankland S: HP’s Hurd dings cloud computing, IBM. 2009. CNET News
Catteddu D, Hogben G: Benefits, risks and recommendations for information security. 2009. Tech. rep., European Network and Information Security Agency, enisa.europa.eu/act/rm/files/deliverables/cloud-computing-risk-assessment
CSA: Security Guidance for Critical Areas of Focus in Cloud Computing. 2009. Tech. rep., Cloud Security Alliance
Mather T, Kumaraswamy S: Cloud Security and privacy: An Enterprise Perspective on Risks and Compliance . 1st edition. 2009. O’Reilly Media O’Reilly Media
Chen Y, Paxson V, Katz RH: What’s New About Cloud Computing Security? 2010. Technical Report UCB/EECS-2010-5, University of California at Berkeley, eecs.berkeley.edu/Pubs/TechRpts/2010/EECS-2010-5.html
Mell P, Grance T: The NIST Definition of Cloud Computing. 2009. http://www.nist.gov/itl/cloud/upload/cloud-def-v15.pdf Technical Report 15, National Institute of Standards and Technology,
Ibrahim AS, Hamlyn-Harris J, Grundy J: Emerging Security Challenges of Cloud Virtual Infrastructure. Proceedings of APSEC 2010Cloud Workshop, APSEC '10 2010.
Gonzalez N, Miers C, Redígolo F, Carvalho T, Simplício M, Naslund M, Pourzandi M: A quantitative analysis of current security concerns and solutions for cloud computing. In Proceedings of 3rd IEEECloudCom . Athens/Greece: IEEE Computer Society; 2011.
Hubbard D, Jr LJH, Sutton M: Top Threats to Cloud Computing. 2010. Tech. rep., Cloud Security Alliance. cloudsecurityalliance.org/research/projects/top-threats-to-cloud-computing/
Tompkins D: Security for Cloud-based Enterprise Applications. 2009. http://blog.dt.org/index.php/2009/02/security-for-cloud-based-enterprise-applications/
Jensen M, Schwenk J, Gruschka N, Iacono LL: On Technical Security Issues in Cloud Computing. IEEE Internation Conference on CloudComputing 2009. pp 109–116 pp 109–116
TrendMicro: Cloud Computing Security - Making Virtual Machines Cloud-Ready. 2010. Trend Micro White Paper
Genovese S: Akamai Introduces Cloud-Based Firewall. 2009. http://cloudcomputing.sys-con.com/node/1219023
Hulme GV: CloudPassage aims to ease cloud server security management. 2011. http://www.csoonline.com/article/658121/cloudpassage-aims-to-ease-cloud-server-security-management
Oleshchuk VA, Køien GM: Security and Privacy in the Cloud - A Long-Term View. Security and Privacy in the Cloud - ALong-Term View. In: 2nd International Conference on WirelessCommunications, Vehicular Technology, Information Theory andAerospace and Electronic Systems Technology (Wireless VITAE), WIRELESSVITAE '11 2011.pp 1–5, pp 1–5, 10.1109/WIRELESSVITAE.2011.5940876
Google: Google App Engine. 2011. code.google.com/appengine/
Google: Google Query Language (GQL). 2011. code.google.com/intl/en/appengine/docs/python/overview.html
StackOverflow: Does using non-SQL databases obviate the need for guarding against SQL injection? 2011. stackoverflow.com/questions/1823536/does-using-non-sql-databases-obvia te-the-need-for-guarding-against-sql-injection
Rose J: Cloudy with a chance of zero day. 2011. www.owasp.org/images/1/12/Cloudy_with_a_chance_of_0_day_Jon_Rose-Tom_Leavey.pdf
Balkan A: Why Google App Engine is broken and what Google must do to fix it. 2011. aralbalkan.com/1504
Salesforce: Salesforce Security Statement. 2011. salesforce.com/company/privacy/security.jsp
Espiner T: Salesforce tight-lipped after phishing attack. 2007. zdnet.co.uk/news/security-threats/2007/11/07/salesforce-tight-lipped-a fter-phishing-attack-39290616/
Yee A: Implications of Salesforce Phishing Incident. 2007. ebizq.net/blogs/security_insider/2007/11/-implications_of_salesforce_phi.php
Salesforce: Security Implementation Guide. 2011. login.salesforce.com/help/doc/en/salesforce_security_impl_guide.pdf
Li H, Dai Y, Tian L, Yang H: Identity-Based Authentication for Cloud Computing. Proceedings of the 1st International Conference on CloudComputing, CloudCom '09 2009.
Amazon: Elastic Compute Cloud (EC2). 2011. aws.amazon.com/ec2/
Kaufman C, Venkatapathy R: Windows Azure Security Overview. 2010. go.microsoft.com/?linkid=9740388, [August]
McMillan R: Google Attack Part of Widespread Spying Effort. 2010. PCWorld
Mills E: Behind the China attacks on Google. 2010. CNET News
Arrington M: Google Defends Against Large Scale Chinese Cyber Attack: May Cease Chinese Operations. 2010. TechCrunch
Bosch J: Google Accounts Attacked by Phishing Scam. 2009. BrickHouse Security Blog
Telegraph T: Facebook Users Targeted By Phishing Attack. 2009. The Telegraph
Pearson S: Taking account of privacy when designing cloud computing services. Proceedings of the 2009 ICSE Workshop onSoftware Engineering Challenges of Cloud Computing, CLOUD '09 2009.
Musthaler L: Cost-effective data encryption in the cloud. Network World 2009.
Yan L, Rong C, Zhao G: Strengthen Cloud Computing Security with Federal Identity Management Using Hierarchical Identity-Based Cryptography. Proceedings of the 1st International Conference onCloud Computing, CloudCom '09 2009.
Tech C: Examining Redundancy in the Data Center Powered by the Cloud and Disaster Recovery. 2010. Consonus Tech
Lyle M: Redundancy in Data Storage. 2011. Define the Cloud
Dorion P: Data destruction services: When data deletion is not enough. 2010. SearchDataBackup.com
Mogull R: Cloud Data Security: Archive and Delete (Rough Cut). 2009. securosis.com/blog/cloud-data-security-archive-and-delete-rough-cut/
Messmer E: Gartner: New security demands arising for virtualization, cloud computing. 2011. http://www.networkworld.com/news/2011/062311-security-summit.html
Ristenpart T, Tromer E, Shacham H, Savage S: Hey, you, get off of my cloud: exploring information leakage in third-party compute clouds. In Proceedings of the 16th ACM conference on Computer andcommunications security, CCS '09 . New York, NY, USA, ACM, ; 2009. pp 199–212, pp 199–212, 10.1145/1653662.1653687
Chow R, Golle P, Jakobsson M, Shi E, Staddon J, Masuoka R, Molina J: Controlling data in the cloud: outsourcing computation without outsourcing control. In Proceedings of the 2009 ACM workshop on,Cloud computing security, CCSW '09 . New York, NY, USA, ACM,; 2009. pp 85–90, pp 85–90, 10.1145/1655008.1655020
Sadeghi AR, Schneider T, Winandy M: Token-Based Cloud Computing - Secure Outsourcing of Data and Arbitrary Computations with Lower Latency. Proceedings of the 3rd international conferenceon Trust and trustworthy computing, TRUST '10 2010.
Brandic I, Dustdar S, Anstett T, Schumm D, Leymann F: Compliant Cloud Computing (C3): Architecture and Language Support for User-driven Compliance Management in Clouds. 2010 IEEE 3rdInternational Conference on Cloud Computing 2010. pp 244–251, pp 244–251, 10.1109/CLOUD.2010.42
Brodkin J: Gartner: Seven cloud computing security risks. 2008. http://www.infoworld.com/d/security-central/gartner-seven-cloud-computing-security-risks-853
Kandukuri BR, Paturi R, Rakshit A: Cloud Security Issues. Proceedings of the 2009 IEEE International Conference on ServicesComputing, SCC '09 2009.
Winterford B: Amazon EC2 suffers huge outage. 2011. http://www.crn.com.au/News/255586,amazon-ec2-suffers-huge-outage.aspx
Clarke G: Microsoft BPOS cloud outage burns Exchange converts. 2011. http://www.theregister.co.uk/2011/05/13/
Shankland S: Amazon cloud outage derails Reddit, Quora. 2011.
Young E: Cloud Computing - The role of internal audit. 2009.
CloudAudit: A6 - The automated audit, assertion, assessment and assurance API. 2011. http://cloudaudit.org/
Anand N: The legal issues around cloud computing. 2010. http://www.labnol.org/internet/cloud-computing-legal-issues/14120/
Hunter S: Ascending to the cloud creates negligible e-discovery risk. 2011. http://ediscovery.quarles.com/2011/07/articles/information-technology/ascending-to-the-cloud-creates-negligible-ediscovery-risk/
Sharon D, Nelson JWS: Virtualization and Cloud Computing: benefits and e-discovery implications. 2011. http://www.slaw.ca/2011/07/19/virtualization-and-cloud-computing-benefits-and-e-discovery-implications/
Bentley L: E-discovery in the cloud presents promise and problems. 2009. http://www.itbusinessedge.com/cm/community/features/interviews/blog/e-discovery-in-the-cloud-presents-promise-and-problems/?cs=31698
Zierick J: The special case of privileged users in the sloud. 2011. http://blog.beyondtrust.com/bid/63894/The-Special-Case-of-Privileged-Users-in-the-Cloud
Dinoor S: Got Privilege? Ten Steps to Securing a Cloud-Based Enterprise. 2010. http://cloudcomputing.sys-con.com/node/1571649
Pavolotsky J: Top five legal issues for the cloud. 2010. http://www.forbes.com/2010/04/12/cloud-computing-enterprise-technology-cio-network-legal.html
ENISA: About ENISA. 2011. http://www.enisa.europa.eu/about-enisa
CSA: About. 2011. https://cloudsecurityalliance.org/about/
CSA: CSA TCI Reference Architecture. 2011. https://cloudsecurityalliance.org/wp-content/uploads/2011/11/TCI-Reference-Architecture-1.1.pdf
CSA: Security Guidance for Critical Areas of Focus in Cloud Computing V3.0. 2011. http://www.cloudsecurityalliance.org/guidance/csaguide.v3.0.pdf Tech. rep., Cloud Security Alliance.
Ramireddy S, Chakraborthy R, Raghu TS, Rao HR: Privacy and Security Practices in the Arena of Cloud Computing - A Research in Progress. AMCIS 2010 Proceedings, AMCIS '10; 2010. http://aisel.aisnet.org/amcis2010/574
NIST: NIST Cloud Computing Reference Architecture: SP 500–292. 2011. http://collaborate.nist.gov/twiki-cloud-computing/pub/CloudComputing/ReferenceArchitectureTaxonomy/NIST ∖ _SP ∖ _500-292 ∖ _- ∖ _090611.pdf
Youseff L, Butrico M, Silva DD: Toward a Unified Ontology of Cloud Computing. Grid Computing Environments Workshop, 2008. GCE '08; 2008. pp 10, 1, pp 10, 1, 10.1109/GCE.2008.4738443
Chapter Google Scholar
Johnston S: Sam Johnston: taxonomy: the 6 layer cloud computing stack. 2008. http://samj.net/2008/09/taxonomy-6-layer-cloud-computing-stack.html []
Linthicum D: Defining the cloud computing framework. 2009. http://cloudcomputing.sys-con.com/node/811519
Doelitzscher F, Reich C, Knahl M, Clarke N: An autonomous agent based incident detection system for cloud environments. Third IEEEInternational Conference on Cloud Computing Technology and Science,CloudCom 2011, CPS; 2011. http://dx.doi.org/10.1109/CloudCom.2011.35 pp 197–204,
Oltsik J: Information security, virtualization, and the journey to the cloud. 2010. Tech. rep., Cloud Security Alliance
Wallom D, Turilli M, Taylor G, Hargreaves N, Martin A, Raun A, McMoran A: myTrustedCloud: Trusted Cloud Infrastructure for Security-critical Computation and Data Managment. Third IEEE InternationalConference on Cloud Computing Technology and Science, CloudCom, CPS; 2011. pp 247–254
Dabrowski C, Mills K: VM Leakage and Orphan Control in Open-Source Clouds. Third IEEE International Conference on CloudComputing Technology and Science, CloudCom, CPS; 2011. pp 554–559
Chadwick DW, Casenove M: Security APIs for My Private Cloud. Third IEEE International Conference on Cloud Computing Technologyand Science, CloudCom, CPS; 2011. pp 792–798
Claybrook B: How providers affect cloud application migration. 2011. http://searchcloudcomputing.techtarget.com/tutorial/How-providers-affect-cloud-application-migration
CSA: Interoperability and portability. 2011.
Download references
Acknowledgements
This work was supported by the Innovation Center, Ericsson Telecomunicações S.A., Brazil.
Author details
1 Escola Polit´ecnica at the University of S˜ao Paulo (EPUSP), S˜ao Paulo, Brazil. 2 Ericsson Research, Stockholm, Sweden. 3 Ericsson Research, Ville Mont-Royal, Canada. 4 State University of Santa Catarina, Joinville, Brazil.
Author information
Authors and affiliations.
Escola Politécnica at the University of São Paulo (EPUSP), São Paulo, Brazil
Nelson Gonzalez, Charles Miers, Fernando Redígolo, Marcos Simplício & Tereza Carvalho
Ericsson Research, Stockholm, Sweden
Mats Näslund
Ericsson Research, Ville Mont-Royal, Canada
Makan Pourzandi
State University of Santa Catarina, Joinville, Brazil
Charles Miers
You can also search for this author in PubMed Google Scholar
Corresponding author
Correspondence to Nelson Gonzalez .
Additional information
Competing interests.
The authors declare that they have no competing interests.
Author’s contributions
NG carried out the security research, including the prospecting for information and references, categorization, results analysis, taxonomy creation and analysis of related work. CM participated in the drafting of the manuscript as well as in the analysis of references, creation of the taxonomy and revisions of the text. MS, FR, MN and MP participated in the critical and technical revisions of the paper including the final one, also helping with the details for preparing the paper to be published. TC coordinated the project related to the paper and also gave the final approval of the version to be published. All authors read and approved the final manuscript.
Authors’ original submitted files for images
Below are the links to the authors’ original submitted files for images.
Authors’ original file for figure 1
Authors’ original file for figure 2, authors’ original file for figure 3, authors’ original file for figure 4, authors’ original file for figure 5, authors’ original file for figure 6, authors’ original file for figure 7, authors’ original file for figure 8, authors’ original file for figure 9, authors’ original file for figure 10, authors’ original file for figure 11, rights and permissions.
Open Access This article is distributed under the terms of the Creative Commons Attribution 2.0 International License ( https://creativecommons.org/licenses/by/2.0 ), which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.
Reprints and permissions
About this article
Cite this article.
Gonzalez, N., Miers, C., Redígolo, F. et al. A quantitative analysis of current security concerns and solutions for cloud computing. J Cloud Comp 1 , 11 (2012). https://doi.org/10.1186/2192-113X-1-11
Download citation
Received : 30 January 2012
Accepted : 05 June 2012
Published : 12 July 2012
DOI : https://doi.org/10.1186/2192-113X-1-11
Share this article
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
- Cloud Computing
- Virtual Machine
- Cloud Service
- Service Level Agreement
- Cloud Provider
Cybersecurity management in cloud computing: semantic literature review and conceptual framework proposal
- Published: 19 October 2020
- Volume 7 , pages 69–84, ( 2021 )
Cite this article
- Najat Tissir 1 , 2 ,
- Said El Kafhali ORCID: orcid.org/0000-0001-9282-5154 3 &
- Noureddine Aboutabit 1 , 2
2928 Accesses
34 Citations
Explore all metrics
Cloud Computing is an emerging paradigm that is based on the concept of distributed computing. Its definition is related to the use of computer resources which are offered as a service. As with any novel technology, Cloud Computing is subject to security threats, vulnerabilities, and attacks. Recently, the studies on security impact include the interaction of software, people and services on the Internet and that is called cyber-security or cyberspace security. In spite of various studies, we still fail to define the needs of cybersecurity management in Cloud Computing. This paper principally focuses on a comprehensive study of Cloud Computing concerns, security, cybersecurity differences, ISO, and NIST standards. It aims at identifying the policies and the guidelines included in these standards as well as it provides a comprehensive Framework proposal to manage and prevent cyber risks in Cloud Computing taking into consideration the ISO 27,032, ISO 27,001, ISO 27,017 and NIST cybersecurity Framework CSF. In addition to that, our study pinpoints at the criteria that concern measuring the maturity of organizations that implement the framework. Our objective is to provide guidance to organizations on how to establish their proper approach of cybersecurity risk management in Cloud Computing or to complement their ‘already have’ processes.
This is a preview of subscription content, log in via an institution to check access.
Access this article
Price includes VAT (Russian Federation)
Instant access to the full article PDF.
Rent this article via DeepDyve
Institutional subscriptions
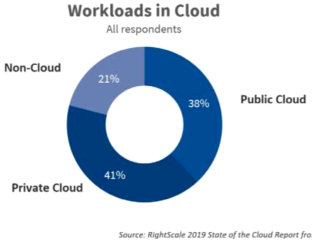
Similar content being viewed by others

Cyber risk and cybersecurity: a systematic review of data availability
Frank Cremer, Barry Sheehan, … Stefan Materne

Cyber Security Threats and Vulnerabilities: A Systematic Mapping Study
Mamoona Humayun, Mahmood Niazi, … Sajjad Mahmood

A survey on security challenges in cloud computing: issues, threats, and solutions
Hamed Tabrizchi & Marjan Kuchaki Rafsanjani
Hayes B (2008) Cloud computing. Commun ACM 51(7):9–11
Article Google Scholar
Zaharia-Rădulescu AM, Radu I (2017) Cloud computing and public administration: approaches in several European countries. Proc Int Conf Business Excellence 11(1):739–749
Al Etawi NA (2018) A comparison between cluster, grid, and cloud computing. Int J Comput Appl 179(32):37–42
Google Scholar
Yeo CS, Buyya R, Pourreza H, Eskicioglu R, Graham P, Sommers Cluster Computing: high-performance, high-availability, and high-throughput processing on a network of computers, vol. 29(6), Springer Science+Business Media Inc., New York, USA (2006) pp. 521–551
Chellappa R (1997) Intermediaries in cloud-computing. INFORMS Meeting. Talk. Dallas, Texas
Grossman RL, Gu Y, Sabala M, Zhang W (2009) Compute and storage clouds using wide area high performance networks. Future Generation Computer Systems 25(2):179–183
RightScale 2019 State of the cloud report from Flexera, 2019. [Online]. https://info.flexerasoftware.com/SLO-WP-State-of-the-Cloud-2019 . Accessed 7 Aug 2019
Ghorbel A, Ghorbel M, Jmaiel M (2017) Privacy in cloud computing environments: a survey and research challenges. J Supercomput 73(6):2763–2800
World Economic Forum, The Global Risks Report 2019, 14th Edition, 2019. https://wef.ch/risks2019 , ISBN: 978–1–944835–15- 6.Accessed: 15 Sept 2019
EUROPEAN UNION AGENCY FOR CYBERSECURITY. About ENISA. [Online]. https://www.enisa.europa.eu/ . Accessed: 21 Sept 2019
Senyo PK, Addae E, Boateng R (2018) Cloud computing research: a review of research themes, frameworks, methods and future research directions. Int J Inf Manage 38(1):128–139
Tanzim Khorshed MD, Shawkat Ali ABM, Wasimi SA (2012) A survey on gaps, threat remediation challenges and some thoughts for proactive attack detection in cloud computing. Future Generation Comput Syst 28(6):833–851
Mell P, Grance T (2011) The NIST definition of cloud computing: recommendations of the national institute of standards and technology. NIST Spec Publ 800–145:1–7
Liu F, Tong J, Mao J, Bohn R, Messina J, Badger L, Leaf D (2012) NIST cloud computing reference architecture: recommendations of the national institute of standards and technology. NIST Spec Publ 500–292:1–35
Rittinghouse J.W, Ransome JF Cloud Computing Implementation, Management, and Security, Version Date: 2013 11 21, Taylor & Francis, Boca Raton, FL, USA:CRC Press, ISBN:978-1-4398-0681-4
Cloud Security Alliance. “Security Guidance for critical areas of focus in Cloud Computing V3.0”, 2011. [Online]. https://cloudsecurityalliance.org/artifacts/security-guidance-for-critical-areas-of-focus-in-cloud-computing-v3/ . 29 July 2019
Varghese B, Buyya R (2018) Next generation cloud computing: new trends and research directions. Future Generation Comput Syst 79:849–861
Wailly A (2014) End-to-end security architecture for cloud computing environments. Doctoral thesis in Networking and Internet Architecture. National Institute of Telecommunications, (2014). English. p.180. <NNT: 2014TELE0020 >.
Meye. PO (2016) Dependability in cloud storage. Doctoral thesis in Distributed, Parallel, and Cluster Computing. Rennes University. 2016. English. P.130. < 10 NNT: 2016REN1S091 >.
Becker JD,Bailey E (2014) A comparison of IT Governance and control frameworks in cloud computing. In: Proceedings of twentieth americas conference on information systems, Savannah, pp 1–16.
Bulla CM, Bhojannavar SS, Danawade VM (2013) Cloud computing: research activities and challenges. Int J Emerging Trends Technol Comput Sci (IJETTCS) 2(5):206–214
Victor ICC (2020) A proposed framework for cloud computing adoption. In: Sustainable business: concepts, methodologies, tools, and applications, 2020, pp 978–1003. IGI Global.
Ko RK, Jagadpramana P, Mowbray M, Pearson S, Kirchberg M, Liang Q, Lee BS, TrustCloud: a framework for accountability and trust in cloud computing. In: 2011 IEEE World Congress on Services, SERVICES, July, 2011, pp 584–588.
ISO/IEC 27032:2012(E) information technology e security techniques e guidelines for Cyber Security, Geneva, Switzerland: ISO/IEC, 2012.
Hasrouny H, Samhat AE, Bassil C, Laouiti A (2017) VANet security challenges and solutions: a survey. Vehicular Commun 7:7–20
Rowe and Barry Lunt DC (2012) Mapping the cyber security terrain in a research context. In: Proceedings of the 1st annual conference on research in information technology, pp 7–12, Calgary, Alberta, Canada—October 11–13
Public Safety Canada, “National Cyber Security Strategy: Canada’s vision for security and prosperity in the digital age”. (2018). [Online]. https://www.publicsafety.gc.ca/cnt/rsrcs/pblctns/ntnl-cbr-scrt-strtg/ntnl-cbr-scrt-strtg-en.pdf
Von Solms B, von Solms R (2018) Cyber Security and information security—What goes where? Inform Comput Security 26(1):2–9
International Telecommunications Union (ITU). “Overview of Cybersecurity: Recommendation ITU-T X.1205, Geneva: International Telecommunication Union (ITU)”. (2009). https://www.itu.int/rec/T-REC-X.1205-200804-I/en
Bahuguna A, Bisht RK, Pande J (2018) Roadmap amid chaos: cyber security management for organisations. In: Proceedings of the ninth international conference on computing communication and networking technologies (ICCCNT), pp 1–6
Disterer G (2013) ISO/IEC 27000, 27001 and 27002 for information security management. J Inform Security 4(2):92–100
Humphreys E (2011) Information security management system standards. Datenschutz und Datensicherheit 35(1):7–11
ISO/IEC. 27017:2015, “Information technology—Security techniques—Code of practice for information security controls based on ISO/IEC 27002 for cloud services”, 2015.
ISO/IEC. 27001:2013, “International standard ISO/IEC Information technology—Security techniques—Information security management systems—Requirements”, vol. 2013, 2013.
ISO/IEC. 27000:2018, “Information technology—Security techniques—Information security management systems—Overview and vocabulary”, 2018.
ISO/IEC. 27002:2013, “Information technology—Security techniques—Code of practice for Information security controls”, 2013.
NIST, “Framework for Improving Critical Infrastructure Cybersecurity”. Version 1.0. (2014). [Online]. Available at https://www.nist.gov/document-3766
NIST, “Glossary of Key Information Security Terms”. NISTIR 7298 Rev.3. (2019). [Online]. https://doi.org/10.6028/NIST.IR.7298r3
Krumay B, Bernroider EWN, Walser R (2018) Evaluation of cybersecurity management controls and metrics of critical infrastructures: a literature review considering the NIST Cybersecurity Framework. In: Gruschka N. (ed) NordSec. Lecture Notes in Computer Science, vol 11252, pp 369–384.
NIST, “Framework for improving critical infrastructure cybersecurity”, Version1.1, (2018). [Online]. https://doi.org/10.6028/NIST.CSWP.04162018
Mbanaso UM, Abrahams L, Apene OZ (2019) Conceptual design of a cybersecurity resilience maturity measurement (CRMM) framework. African J Inform Commun 23:1–26
Chang V, Kuo YH, Ramachandran M (2016) a Cloud computing adoption framework: a security framework for business clouds. Future Generation Comput Syst 57:24–41
Chang V, Ramachandran M, Yao Y (2016) Chung-Sheng Li, A resiliency framework for an enterprise cloud. Int J Inf Manage 36(1):155–166
Wendler R (2012) The maturity of maturity model research: a systematic mapping study. Inf Softw Technol 54(12):1317–1339
Almuhammadi S, Majeed A (2017) Information Security maturity model for NIST cyber security framework. Comput Sci Inform Technol 51:51–62
Le NT, Hoang DB (2017) Capability maturity model and metrics framework for cyber cloud security. Scalable Comput 4:277–290
Abdel-Basset M, Mohamed M, Chang V (2018) NMCDA: a framework for evaluating cloud computing services. Future Generation Comput Syst 86:12–29
Download references
Author information
Authors and affiliations.
Process Engineering, Computer Science and Mathematics Laboratory, National School of Applied Sciences, Sultan Moulay Slimane University, 25000, Khouribga, Morocco
Najat Tissir & Noureddine Aboutabit
Sultan Moulay Slimane University, Beni Mellal, Morocco
Hassan First University of Settat, Faculty of Sciences and Techniques, Computer, Networks, Mobility and Modeling Laboratory: IR2M, 26000, Settat, Morocco
Said El Kafhali
You can also search for this author in PubMed Google Scholar
Corresponding author
Correspondence to Said El Kafhali .
Additional information
Publisher's note.
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Reprints and permissions
About this article
Tissir, N., El Kafhali, S. & Aboutabit, N. Cybersecurity management in cloud computing: semantic literature review and conceptual framework proposal. J Reliable Intell Environ 7 , 69–84 (2021). https://doi.org/10.1007/s40860-020-00115-0
Download citation
Received : 28 April 2020
Accepted : 30 September 2020
Published : 19 October 2020
Issue Date : June 2021
DOI : https://doi.org/10.1007/s40860-020-00115-0
Share this article
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
- Cloud computing
- Cybersecurity
- Cybersecurity management
- Find a journal
- Publish with us
- Track your research
- Cloud Security
We’re working on building the most secure cloud infrastructure platforms. Our research focuses on ensuring the integrity of everything in the stack, reducing the attack surface of cloud systems, and advancing the use of confidential computing and hardware security modules.
Simplifying cloud security policies with AI
- Data and AI Security
How do you measure innovation?

- Semiconductors

The ultimate tool for data privacy: Fully homomorphic encryption
- Fully Homomorphic Encryption
Extending server integrity across space and time with Durable Attestation
Strengthening cloud security with confidential computing.

Confidential Computing
What is confidential computing.
- Cryptography
- Hybrid Cloud
- See more of our work on Cloud Security
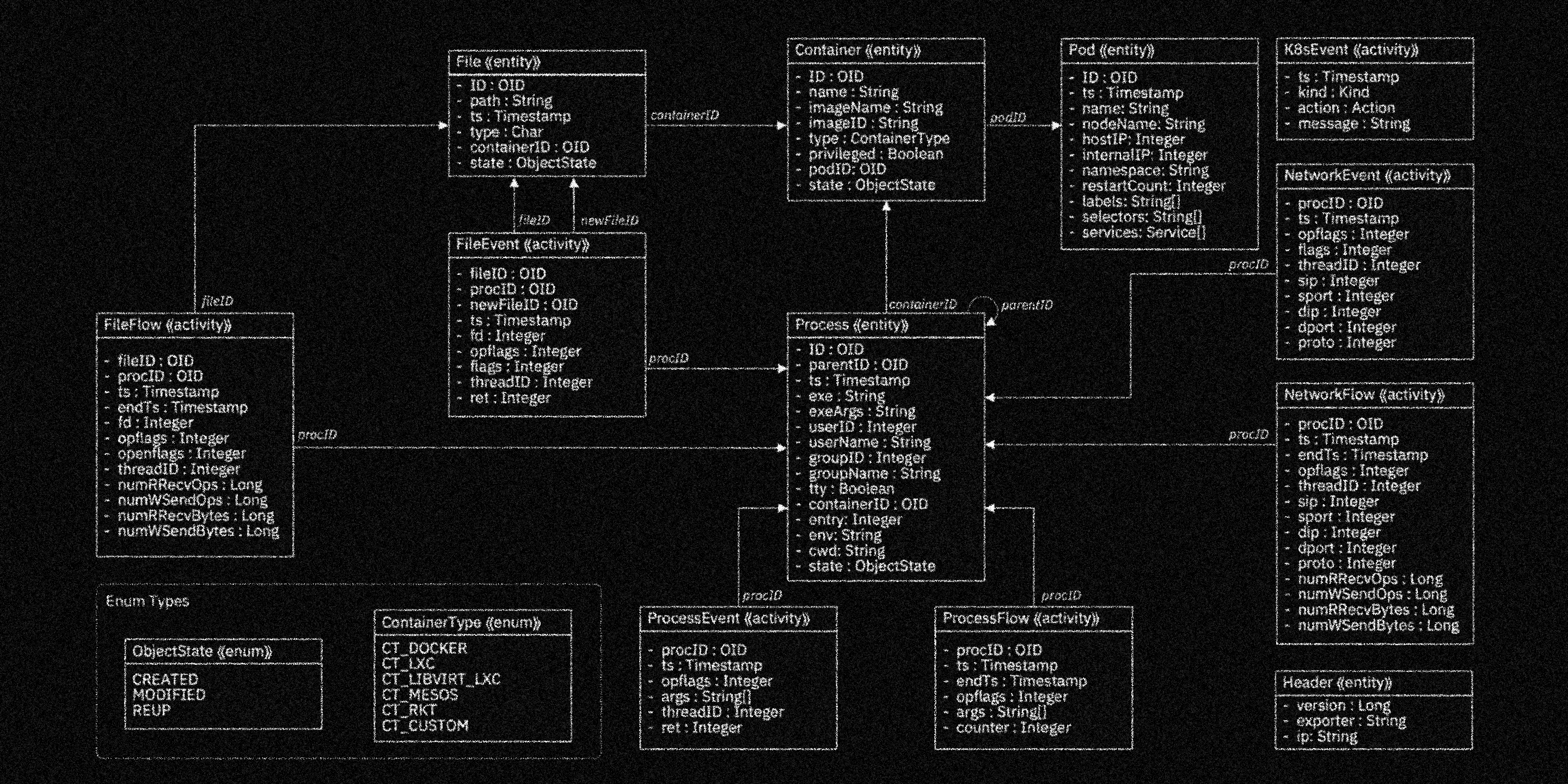
- Security Analysis
Threat Management
Publications.
- Vikram Narayanan
- Claudio Siqueira de Carvalho
- Pradip Bose
- Jennifer Dworak
- Wojciech Ozga
- Guerney Hunt
- Sahil Suneja
- Yufan Zhuang
- Francesco Fusco
- FiCloud 2023
- Michael V. Le
- Salman Ahmed
- ASIA CCS 2023
Related topics
Security analysis at scale, hybrid cloud infrastructure, hybrid cloud platform.
cloud security Recently Published Documents
Total documents.
- Latest Documents
- Most Cited Documents
- Contributed Authors
- Related Sources
- Related Keywords
A Review on AWS - Cloud Computing Technology
Abstract: Cloud computing is something simple we can define as maintaining data centers and data servers and also u can access technology services by computing power, storage, and database using cloud computing technology AWS(Amazon Web Services). It is an emerged model which is already popular among almost all enterprises. It provides us the concept of ondemand services where we are using and scaling cloud resources on demand and as per demand respectively. AWS Cloud computing is a cost-effective model. The major concern in this model is Security and Storage in the cloud. This is one of the major reasons many enterprises of choosing AWS cloud computing. This paper provides a review of security research in the field of cloud security and storage services of the AWS cloud platform. After security and storage, we have presented the working of AWS (Amazon Web Service) cloud computing. AWS is the most trusted provider of cloud computing which not only provides excellent cloud security but also provides excellent cloud storage services. The main aim of this paper is to make cloud computing storage and security a core operation and not an add-on operation. As per the increase in the Service provider and related companies, this AWS Cloud Platform plays a vital role in service industries by giving its best web services, so, therefore, choosing the cloud service providers wisely is the basic need of the industry. Therefore we are going to see how AWS fulfills all these specific needs. Keywords: Trusted Computing, AWS, Information-Centric Security, Cloud Storage, S3, EC2, Cloud Computing
Deep Learning Approaches to Cloud Security
Genetic algorithm-based pseudo random number generation for cloud security, cloud security service for identifying unauthorized user behaviour, qos based cloud security evaluation using neuro fuzzy model, azure cloud security for absolute beginners, mitigating theft-of-service attack - ensuring cloud security on virtual machines, cloud computing security requirements: a review.
Abstract Cloud computing is a new technology that is undergoing tremendous development today. People who use it are not able to separate the reasonable from the unreasonable arguments that come with the security requirements in the cloud. The claim that cloud computing is hereditarily insecure is as absurd as the claim that cloud computing does not create new security problems. Cloud computing is a way to dynamically increase resources without the need for in-depth knowledge of a brand new infrastructure, without training new workers or designing new software solutions. The article aims to analyse the different cloud security issues and models of cloud architectures. Some of the main problems with security in virtualization, concerns about storing data in the cloud and the assessment of risk tolerance in cloud computing are presented. Legal and regulatory issues for the protection of personal data are addressed.
The Vulnerabilities of Cloud Computing : A Review
A Cloud is a type of analogous and scattered system consisting of a collection of inter-connected and virtualized computers that are dynamically provisioned and presented as one or more unified computing resources “ . cloud computing is the dynamic provisioning of IT capabilities (hardware, software, or services) from third parties over a network. However this technology is still in its initial stages of development, as it suffers from threats and vulnerabilities that prevent the users from trusting it. Various malicious activities from illegal users have threatened this technology such as data misuse, inflexible access control and limited monitoring. The occurrence of these threats may result into damaging or illegal access of critical and confidential data of users. This article is in order to describe the impact of those vulnerabilities and threats to create awareness among organisations and users so that they can Adopt this technology with trust And form a trusted provider Who has trusted security policies. Here we have defined cloud-specific vulnerabilities, cloud feature vulnerabilities and propose a reference vulnerabilities architecture of cloud computing and threats related cloud computing. Cloud security and privacy plays an important role to avoid cloud threats .Cloud Privacy Concerns the expression of or devotion to various legal and non- legal norms regarding the right to private life. Cloud Security Concerns the confidentiality, ease of use and reliability of data or information. As the development of cloud computing, issue of security has become a top priority. In this article we are going to discuss about the Characteristics of vulnerabilities , cloud vulnerabilities and cloud threats , Also how we can overcome or avoid them and keep our data safe.
Security and Privacy in Cloud Computing: Technical Review
Advances in the usage of information and communication technologies (ICT) has given rise to the popularity and success of cloud computing. Cloud computing offers advantages and opportunities for business users to migrate and leverage the scalability of the pay-as-you-go price model. However, outsourcing information and business applications to the cloud or a third party raises security and privacy concerns, which have become critical in adopting cloud implementation and services. Researchers and affected organisations have proposed different security approaches in the literature to tackle the present security flaws. The literature also provides an extensive review of security and privacy issues in cloud computing. Unfortunately, the works provided in the literature lack the flexibility in mitigating multiple threats without conflicting with cloud security objectives. The literature has further focused on only highlighting security and privacy issues without providing adequate technical approaches to mitigate such security and privacy threats. Conversely, studies that offer technical solutions to security threats have failed to explain how such security threats exist. This paper aims to introduce security and privacy issues that demand an adaptive solution approach without conflicting with existing or future cloud security. This paper reviews different works in the literature, taking into account its adaptiveness in mitigating against future reoccurring threats and showing how cloud security conflicts have invalidated their proposed models. The article further presents the security threats surrounding cloud computing from a user perspective using the STRIDE approach. Additionally, it provides an analysis of different inefficient solutions in the literature and offers recommendations in terms of implementing a secure, adaptive cloud environment.
Export Citation Format
Share document.
An official website of the United States government
The .gov means it’s official. Federal government websites often end in .gov or .mil. Before sharing sensitive information, make sure you’re on a federal government site.
The site is secure. The https:// ensures that you are connecting to the official website and that any information you provide is encrypted and transmitted securely.
- Publications
- Account settings
Preview improvements coming to the PMC website in October 2024. Learn More or Try it out now .
- Advanced Search
- Journal List
- Comput Intell Neurosci
- v.2022; 2022

This article has been retracted.
The rise of cloud computing: data protection, privacy, and open research challenges—a systematic literature review (slr), junaid hassan.
1 Department of Computer Science, National University of Computer and Emerging Sciences, Islamabad, Chiniot-Faisalabad Campus, Chiniot 35400, Pakistan
Danish Shehzad
2 Department of Computer Science, Superior University, Lahore 54000, Pakistan
Usman Habib
3 Faculty of Computer Sciences and Engineering, GIK Institute of Engineering Sciences and Technology, Topi, Swabi 23640, Khyber Pakhtunkhwa, Pakistan
Muhammad Umar Aftab
Muhammad ahmad, ramil kuleev.
4 Institute of Software Development and Engineering, Innopolis University, Innopolis 420500, Russia
Manuel Mazzara
Associated data.
The data used to support the findings of this study are provided in this article.
Cloud computing is a long-standing dream of computing as a utility, where users can store their data remotely in the cloud to enjoy on-demand services and high-quality applications from a shared pool of configurable computing resources. Thus, the privacy and security of data are of utmost importance to all of its users regardless of the nature of the data being stored. In cloud computing environments, it is especially critical because data is stored in various locations, even around the world, and users do not have any physical access to their sensitive data. Therefore, we need certain data protection techniques to protect the sensitive data that is outsourced over the cloud. In this paper, we conduct a systematic literature review (SLR) to illustrate all the data protection techniques that protect sensitive data outsourced over cloud storage. Therefore, the main objective of this research is to synthesize, classify, and identify important studies in the field of study. Accordingly, an evidence-based approach is used in this study. Preliminary results are based on answers to four research questions. Out of 493 research articles, 52 studies were selected. 52 papers use different data protection techniques, which can be divided into two main categories, namely noncryptographic techniques and cryptographic techniques. Noncryptographic techniques consist of data splitting, data anonymization, and steganographic techniques, whereas cryptographic techniques consist of encryption, searchable encryption, homomorphic encryption, and signcryption. In this work, we compare all of these techniques in terms of data protection accuracy, overhead, and operations on masked data. Finally, we discuss the future research challenges facing the implementation of these techniques.
1. Introduction
Recent advances have given rise to the popularity and success of cloud computing. It is a new computing and business model that provides on-demand storage and computing resources. The main objective of cloud computing is to gain financial benefits as cloud computing offers an effective way to reduce operational and capital costs. Cloud storage is a basic service of cloud computing architecture that allows users to store and share data over the internet. Some of the advantages of cloud storage are offsite backup, efficient and secure file access, unlimited data storage space, and low cost of use. Generally, cloud storage is divided into five categories: (1) private cloud storage, (2) personal cloud storage, (3) public cloud storage, (4) community cloud storage, and (5) hybrid cloud storage.
However, when we outsource data and business applications to a third party, security and privacy issues become a major concern [ 1 ]. Before outsourcing private data to the cloud, there is a need to protect private data by applying different data protection techniques, which we will discuss later in this SLR. After outsourcing the private data to the cloud, sometimes the user wants to perform certain operations on their data, such as secure search. Therefore, while performing such operations on private data, the data needs to be protected from intruders so that intruders cannot hack or steal their sensitive information.
Cloud computing has many advantages because of many other technical resources. For example, it has made it possible to store large amounts of data, perform computation on data, and many other various services. In addition, the cloud computing platform reduces the cost of services and also solves the problem of limited resources by sharing important resources among different users. Performance and resource reliability requires that the platform should be able to tackle the security threats [ 2 ]. In recent years, cloud computing has become one of the most important topics in security research. These pieces of research include software security, network security, and data storage security.
The National Institute of Standards and Technology (NIST) defines cloud computing as [ 3 ] “a model for easy access, ubiquitous, resource integration, and on-demand access that can be easily delivered through various types of service providers. The Pay as You Go (PAYG) mechanism is followed by cloud computing, in which users pay only for the services they use. The PAYG model gives users the ability to develop platforms, storage, and customize the software according to the needs of the end-user or client. These advantages are the reason that the research community has put so much effort into this modern concept [ 4 ].
Security is gained by achieving confidentiality, integrity, and data availability. Cloud users want assurance that their data must be saved while using cloud services. There are various types of attacks that launch on a user's private data, such as intrusion attacks, hacking, stealing the user's private data, and denial of service attacks. 57% of companies report security breaches using cloud services [ 5 ]. Data privacy is more important than data security because cloud service providers (CSPs) have full access to all cloud user's data and can monitor their activities, because of which the cloud user privacy is compromised. For example, a user is a diabetic, and the CSP is analyzing their activities, such as what he is searching for more and what kind of medicine he is using the most. Because of this access, CSP can get all the sensitive information about an individual user and can also share this information with a medicine company or an insurance company [ 6 ]. Another problem is that the user cannot fully trust CSP. Because of this reason, there are many legal issues. Users cannot store their sensitive data on unreliable cloud services because of this mistrust. As a result, many users cannot use cloud services to store their personal or sensitive data in the cloud. There are two ways to solve this problem. One is that the user installs a proxy on his side, and this proxy takes the user's data, encrypts and saves their data using some data protection techniques, and then sends it to the untrusted CSP [ 7 ].
The recent Google privacy policy is that any user can use any Google service free of cost; however, Google monitors their activity by monitoring their data to improve their services [ 8 ]. In this paper, we compare different types of data protection techniques that provide privacy and security over the data stored on the cloud. Many papers discuss outsourcing data storage on the cloud [ 9 , 10 ], however, we also discuss how we can secure the outsourced data on the cloud. Most of the paper describes the data security on the cloud vs the external intruder attacks [ 11 , 12 ]. This paper not only discusses the security attacks from outside intruders and securing mechanisms but also inner attacks from the CSP itself. Many surveys cover data privacy by applying cryptographic techniques [ 13 , 14 ]. These cryptographic techniques are very powerful for the protection of data and also provide a very significant result. However, there is a problem as these cryptographic techniques require key management, and some of the cloud functionalities are not working on these cryptographic techniques. In this paper, we also discuss some steganographic techniques. To the best of our knowledge, no study discusses all the conventional and nonconventional security techniques. Therefore, all the data protection techniques need to be combined in one paper.
The rest of this paper is organized as follows: Section 3 of the paper describes the research methodology that consists of inclusion, exclusion criteria, quality assessment criteria, study selection process, research questions, and data extraction process. Also, we discuss assumptions and requirements for data protection in the cloud. Section 4 presents all the cryptographic and also noncryptographic techniques that are used for data protection over the cloud. Also, we discuss the demographic characteristics of the relevant studies by considering the following four aspects: (i) publication trend, (ii) publication venues (proceeding and journals), (iii) number of citations, and (iv) author information. Section 4 also compares all these data protection techniques. Lastly, in Section 5 , we discuss results and present conclusion and future work.
2. Related Work
The first access control mechanism and data integrity in the provable data possession (PDP) model is proposed in the paper [ 15 ], and it provides two mobile applications based on the RSA algorithm. Like the PDP, the author in the paper [ 16 ] proposed a proof of retrievability (PoR) scheme that is used to ensure the integrity of remote data. PoR scheme efficiency is improved using a shorter authentication tag that is integrated with the PoR system [ 17 ]. A more flexible PDP scheme is proposed by the author of the paper [ 18 ] that uses symmetric key encryption techniques to support dynamic operations. A PDP protocol with some flexible functionality is developed, in which, we can add some blocks at run time [ 19 ]. A new PDP system with a different data structure is introduced, and it improves flexibility performance [ 20 ]. Similarly, another PDP model with a different data structure is designed to handle its data functionality [ 21 ]. To improve the accuracy of the data, the author of the paper [ 22 ] designed a multireplicas data verification scheme that fully supports dynamic data updates.
A unique data integration protocol [ 23 ] for multicloud servers is developed. The author of the paper [ 24 ] also considers the complex area where multiple copies are stored in multiple CSPs and builds a solid system to ensure the integrity of all copies at once. A proxy PDP scheme [ 25 ] is proposed, which supports the delegation of data checking that uses concessions to verify auditor consent. In addition, the restrictions of the verifier are removed that strengthened the scheme, and it proposes a separate PDP certification system [ 26 ]. To maintain the security of information, a concept for information security is proposed and a PDP protocol for public research is developed [ 27 ]. To resolve the certification management issue, the PDP system with data protection is introduced [ 28 ].
Identity-based cryptography is developed, in which a user's unique identity is used as input to generate a secret key [ 29 ]. Another PDP protocol is recommended to ensure confidentiality [ 30 ]. The author of the paper [ 31 ] proposed a scheme, in which tags are generated through the ring signature technique for group-based data sharing that supports public auditing and maintains user privacy. A new PDP system is introduced for data sharing over the cloud while maintaining user privacy [ 32 ]. Additionally, it supports the dynamic group system and allows users to exit or join the group at any time. Another PDP system [ 33 ] that is based on broadcast encryption and supports dynamic groups [ 34 ] is introduced. The issue of user revocation has been raised [ 35 ], and to address this issue, a PDP scheme has been proposed, which removes the user from the CSP using the proxy signature method. A PDP-based group data protocol was developed to track user privacy and identity [ 36 ]. A PDP system [ 37 ] is proposed for data sharing between multiple senders. The author of the paper [ 38 ] provides SEPDP systems while maintaining data protection. However, the author of the paper [ 39 ] proved that the scheme proposed in [ 38 ] is vulnerable to malicious counterfeiting by the CSP. A collision-resistant user revocable public auditing (CRUPA) system [ 40 ] is introduced for managing the data that is shared in groups. Another scheme [ 41 ] is introduced as a way to ensure the integrity of mobile data terminals in cloud computing.
To address the PKI issue, identity-based encryption [ 42 ] is designed to enhance the PDP protocol and maintain user privacy in a dynamic community. Before sharing user-sensitive data with third parties or researchers, data owners ensure that the privacy of user-sensitive data is protected. We can do this using data anonymization techniques [ 43 ]. In recent years, the research community has focused on the PPDP search area and developed several approaches for tabular data and SN [ 44 – 49 ]. There are two popular settings in PPDP: one is interactive, and the other is noninteractive [ 50 ]. The K-anonymity model [ 51 ] and its effects are most commonly used in the noninteractive setting of PPDP [ 52 – 56 ]. Differential privacy (DP) [ 57 ] and an interactive configuration of PPDP make extensive use of DP-based methods [ 58 – 60 ]. Meanwhile, several studies for a noninteractive setting reported a PD-dependent approach [ 61 ]. Researchers have expanded the concepts used to anonymize tabular data to protect the privacy of SN users [ 62 – 64 ].
Most images on the internet are in a compressed form. Hence, various studies design some techniques for AMBTC-compressed images. Data concealment has become an active research area. We can hide the data by adding confidential information to the cover image, and as a result, we get the stego image. There are two types of data hiding schemes: one is irreversible [ 65 – 68 ], and the other is a reversible data hiding scheme [ 69 – 71 ]. A cipher text designated for data collection can be re-encrypted as designated for another by a semitrusted proxy without decryption [ 72 ]. The first concrete construction of collusion-resistant unidirectional identity-based proxy re-encryption scheme, for both selective and adaptive identity, is proposed in the paper [ 73 ]. One of the data hiding schemes is the histogram shifting scheme [ 74 – 76 ], and it is the most widely used. A histogram-shifting data hiding scheme [ 77 ] that detects pixel histograms in the cover image is introduced. When big and diverse data are distributed everywhere, we cannot control the vicious attacks. Therefore, we need a cryptosystem to protect our data [ 78 – 80 ].
Some identity-based signature (IBS) schemes [ 81 – 84 ] are introduced that are based on bilinear pairing. However, the authentication schemes based on bilinear pairing over elliptic curve are more efficient and safer than traditional public key infrastructure [ 85 , 86 ]. The paper [ 87 ] proposed a preserving proxy re-encryption scheme for public cloud access control. A differential attack is performed on one-to-many order preserving encryption OPE by exploiting the differences of the ordered ciphertexts in [ 88 ]. Another scheme is proposed, which consists of a cancelable biometric template protection scheme that is based on the format-preserving encryption and Bloom filters [ 89 ]. Some of the researchers also use the concept of paring free identity-based signature schemes [ 90 – 93 ]. A lightweight proxy re-encryption scheme with certificate-based and incremental cryptography for fog-enabled e-healthcare is proposed in [ 94 ].
3. Research Methodology
The objective of this SLR is to evaluate, investigate, and identify the existing research in the context of data storage security in cloud computing to find and evaluate all the existing techniques. SLR is a fair and unbiased way of evaluating all the existing techniques. This way provides a complete and evidence-based search related to a specific topic. At this time, there is no SLR conducted on data storage security techniques that explains all the cryptographic and noncryptographic techniques. Hence, this SLR fulfills the gap by conducting itself. This SLR aims to provide a systematic method using the guidelines of an SLR provided by Kitchenham [ 95 ]. Furthermore, to increase the intensity of our evidence, we follow another study that is provided by [ 96 ]. Our SLR consists of three phases, namely planning, conducting, and reporting. By following these three phases, we conduct our SLR, as shown in Figure 1 .

Review procedure.
3.1. Research Questions
The primary research question of this systematic literature review is “What types of data protection techniques have been proposed in cloud computing?” This primary research question is further divided into four RQs. All these four questions are enlisted below.
- RQ1: what types of data protection techniques have been proposed in cloud computing?
- RQ2: what are the demographic characteristics of the relevant studies?
- RQ3: which data protection technique provides more data protection among all the techniques?
- RQ4: what are the primary findings, research challenges, and directions for future research in the field of data privacy in cloud computing?
3.2. Electronic Databases
Six electronic databases were selected to collect primary search articles. All these six electronic databases are well-reputed in the domain of cloud computing. Most of the relevant articles are taken from two electronic databases, namely IEEE and Elsevier. All the electronic databases that we use in this research process are given in Table 1 .
Databases sources.
3.3. Research Terms
First of all, the title base search is done on the different electronic databases, which are given in Table 1 . After that, most related studies/articles are taken. Search is done using the string (p1 OR p2. . . . . .OR pn.) AND (t1 OR t2. . . . . . OR tn.). This string/query is constructed using a population, intervention, control, and outcomes (PICO) structure that consists of population, intervention, and outcome. Database search queries are given in Table 2 .
- Population : “cloud computing”
- Intervention : “data security,” “data privacy,” “data integrity”
- Using the PICO structure, we construct a general query for the electronic database. Generic: ((“Document Title”: cloud∗) AND (“Document Title”: data AND (privacy OR protect∗ OR secure∗ OR integrity∗))).
Databases search query.
3.4. Procedure of Study Selection
The procedure of study selection is described in Figure 2 . This procedure has three phases: the first one is exclusion based on the title, in which articles are excluded based on the title, and the relevant titles are included. The second is exclusion based on the abstract in which articles are excluded. By reading the abstract of the articles, the most relevant abstract is included, and the last one is exclusion based on a full text that also includes quality assessment criteria.

Study selection procedure.
3.5. Eligibility Control
In this phase, all the selected papers are fully readied, and relevant papers are selected to process our SLR further. Table 3 shows the final selected papers from each database based on inclusion and exclusion criteria. The related papers are selected based on inclusion and exclusion criteria, which are given in Table 4 .
Results from electronic databases.
Inclusion and exclusion criteria.
3.6. Inclusion and Exclusion Criteria
We can use the inclusion and exclusion criteria to define eligibility for basic study selection. We apply the inclusion and exclusion criteria to those studies that are selected after reading the abstract of the papers. The criteria for inclusion and exclusion are set out in Table 4. Table 4 outlines some of the conditions that we have applied to the articles. After applying the inclusion and exclusion criteria, we get relevant articles, which we finally added to our SLR. The search period is from 2010 to 2021, and most of the papers included in our SLR are from 2015 to onward.
We apply inclusion and exclusion criteria in the third phase of the study selection process, and we get 139 results. After that, we also apply quality criteria, and finally, we get 52 articles, which are included in this SLR. Most of the articles are taken from Elsevier and IEEE electronic databases. IEEE is the largest Venus for data storage security in cloud computing. The ratio of the selected articles from different electronic databases is shown in Figure 3 .

Percentage of selected studies.
3.7. Quality Assessment Criteria
Quality checking/assessment is done in the 3 rd phase of the study selection process. A scale of 0-1 is used for the quality assessment (QA) of the articles.
Poor-quality articles get 0 points on the scale, and good-quality articles get 1 point on the scale. The articles with 1 point on the scale are included in this SLR. Hence, by applying the quality checking/assessment criteria on all the articles, we finally get 52 articles. All the selected papers have validity and novelty for different data protection techniques, and also, we find the relevance of the articles in the quality assessment criteria, which ensures that all the articles are related to the SLR (data storage protection and privacy in cloud computing). The quality checking (QC) criteria are given in Table 5 .
Quality checking criteria.
3.8. Taxonomy of the Data Protection Techniques
In this section, all the data protection techniques are depicted in Figure 4 . All the data protection techniques are arranged and classified in their related categories. The purpose of the taxonomy is to give a presentational view of all the data protection techniques. The data protection techniques are mainly divided into two categories, namely (1) noncryptographic techniques and (2) cryptographic techniques.

Taxonomy of the data protection techniques.
4. Results and Discussions
Data protection on the cloud is done by developing a third-party proxy that is trusted by the user. The trusted proxy is not a physical entity. It is a logical entity that can be developed on the user end (like on the user's personal computer) or at that location on which the user can trust. Mostly, all the local proxies are used as an additional service or as an additional module (like browser plugins). To fulfill the objective of data protection by proxies, some requirements are needed to fulfill necessarily. The requirements are given below:
- User privilege. There are several objectives of user privilege or user empowerment, however, the main objective is to increase the trust of the users in data protection proxies used by the cloud.
- Transparency. Another important objective is that when users outsource their sensitive data to trusted proxies, their data should remain the same and should not be altered.
- Cloud computing provides large computing power and cost saving resources. However, one concern is that if we increase data security, computation overhead should not increase. We want to minimize the computation overhead over the proxies.
- Cloud functionalities preservation. Cloud functionalities preservation is the most important objective. The users encrypt their sensitive data on their personal computers by applying different encryption techniques to increase the protection of their data, however, by applying these different encryption techniques, they are not able to avail some of the cloud functionalities because of compatibility issues [ 97 ]. Hence, it is the main issue.
Figure 5 provides a data workflow for protecting sensitive data on the cloud using a local proxy. There are different types of the assumption that are made for data protection, and some of them are discussed below.
- Curious CSPs, the most commonly used model in cloud computing, is given in the literature [ 98 ]. The cloud service provider honestly fulfills the responsibilities, i.e., they do not interfere in the user activities, and they only follow the stander protocols. The CSP is honest, however, sometimes, it is curious to analyze the users' queries and analyze their sensitive data, which is not good because it is against the protocol. Also, by this, the privacy of the user is compromised. Hence, we can avoid these things by applying some data protection techniques on the user end to protect the users' sensitive data from the CSPs.
- In some cases, CSPs may collaborate with data protection proxies that are present on the users' sides to increase the level of trust between the users and CSPs because better trust can motivate more users to move to the cloud. This collaboration can be done if CSPs provide some services to the users with a stable interface for storing, searching, and computing their data.
- A multicloud approach to cloud computing infrastructure has also been proposed to improve their performance. In this regard, multiple cloud computing services are provided in the same heterogeneous architecture [ 19 ]. A multicloud gives the user multiple different places to store their data at their desired location. There are several benefits to use a multicloud, e.g., it reduces reliance on a single CSP, which increases flexibility.

Data workflow on cloud using local proxy.
4.1. RQ1: What Type of Data Protection Techniques has Been Proposed in Cloud Computing?
In this session, we will discuss all the techniques for data storage security over the cloud. All these techniques are divided into two main categories, namely (i) cryptographic techniques and (ii) noncryptographic techniques. The local proxy uses different techniques to protect data that are stored on the cloud. Because of this reason, we cannot gain all the advantages of cloud services. Therefore, we analyze and compare all these techniques based on different criteria. These different criteria are as follows: (i) the data accuracy of all the techniques, (ii) the data protection level of all the techniques, (iii) all the functionalities these schemes allow on masked and unmasked data, and (iv) the overhead to encrypt and decrypt data over the cloud.
4.1.1. Noncryptographic Techniques
There are some noncryptographic techniques, and we discuss them in this paper as follows:
(1) Data Anonymization . Data anonymization is a data privacy technique used to protect a user's personal information. This technique hides the person's personal information by hiding the person's identifier or attributes that could reveal a person's identity. Data anonymization can be done by applying various mechanisms, for example, by removing or hiding identifiers or attributes. It can also be done by encrypting the user's personal information. The main purpose of performing data anonymization is that we can hide the identity of the person in any way. Data anonymity can be defined as the user's personal data being altered in such a way that we cannot directly or indirectly identify that person, and the CSP cannot retrieve any person's personal information. Data anonymization techniques have been developed in the field of statistical control disclosure. These techniques are most often used when we want to outsource sensitive data for testing purposes. Data anonymization is graphically represented in Figure 6 .

Data anonymization flow diagram.
Data anonymization techniques are most often used when we want to outsource sensitive data for testing purposes. For example, if some doctors want to diagnose certain diseases, some details of these diseases are required for this purpose. This information is obtained from the patients that suffer from these diseases, but it is illegal to share or disclose anyone's personal information. However, for this purpose, we use data anonymization technique to hide or conceal the person's personal information before outsourcing the data. In some cases, however, the CSP wants to analyze the user's masked data. In the data anonymization technique, attributes are the most important part. Attributes can include name, age, gender, address, salary, etc. Table 6 shows the identifiers classification.
Identifiers classification.
Data anonymization can be performed horizontally or vertically on this table and also on the record or group of records. The attributes are further classified into the following categories.
- Sensitive Attributes: sensitive attributes possess sensitive information of the person, such as salary, disease information, phone number, etc. These attributes are strongly protected by applying some protection techniques.
- Nonsensitive Attributes: these types of attributes do not belong to any type of category. Hence, they do not disclose the identity of a person.
- Identifiers: identifier belongs to the identity of a person, such as Id card, name, social security number, etc. Because of the presence of these identifiers, the relationship between different attributes can be detected. Hence, these identifiers must be replaced or anonymized.
- Quasi-Identifiers: quasi-identifiers are the group of identifiers that are available publicly, such as zip-code, designation, gender, etc. Separately, these identifiers cannot reveal the personal identity, however, by combining them, they may reveal the identity of the person. Hence, we want to separate these quasi-identifiers to avoid the discloser.
There are two main categories of data masking: (1) perturbative masking and (2) nonperturbative masking.
- (1) Perturbative Masking
- In perturbation, masking data is altered or masked with dummy datasets. Original data is replaced with dummy data, however, this data looks like the original data with some noise addition. The statistical properties of the original data are present in the masked data, however, nonperturbative masking does not contain the statistical properties of original data, because in perturbation masking, data is altered or masked with physically same but dummy data.
- Data swapping
- In data swapping, the data is randomly changed with the same but dummy data between different records [ 99 ]. However, if the numerical values are present in the dataset, then in certain limits, the values can be changed. Otherwise, the meaning of the data is changed. The masked data cannot look like the original data. For those attributes that can be ranked, the attribute is replaced with the nearby ranked attributes, and a very large difference between ranks is not suitable [ 100 ]. In data swapping, higher-level attributes are swapped [ 101 ] and individual values are not changed.
- Noise Addition
- In this mechanism, some noise is added to the original dataset to alter the original data. Noise is only added to the data that is continuous and divided into categories [ 102 ]. The noise is added into all the attributes that are present in the original dataset, such as sensitive attributes and also quasi-attributes.
- Microaggregation
- In this technique, all the relevant data is stored into different groups, and these different groups release average values from each record [ 103 ]. If a large number of similar records is present in different groups, then more data utility is done. We can cluster the data in many ways, e.g., in categorical versions [ 104 ]. Microaggregation is done on a quasi-attribute to protect these attributes from reidentification, and the quasi-attributes protect all the other attributes from reidentification. We can also minimize reidentification by data clustering [ 105 ].
- Pseudonymization
- In this method, the original data is replaced with artificial datasets [ 106 ]. In this technique, each attribute present in the original data is a pseudonym, and by doing this, data is less identifiable.
- (2) Nonperturbative Masking
- Nonperturbative masking does not change or alter the original data, however, it changes the statistical properties of the original data. Mask data is created by the reduction of the original data or suppressions of the original data [ 107 ].
- Bucketization
- In this method, original data is stored in different buckets, and these buckets are protected through encryption [ 108 ]. We can protect the sensitive attributes through bucketization.
- Data slicing is a method in which a larger group of data is divided into smaller slices or segments [ 109 ]. Hence, we can slice the data, and in this way, the sensitive attribute and the quasi-attributes are divided into different slices. By identifying the individual slice, the identity of the person cannot be disclosed.
- Sampling is a technique in which the population and sample concept is present. The entire data is called population, and the masked data is called a sample. In this technique, we make different samples of the original data. A smaller data sample provides more protection [ 110 ].
- Generalization
- It is a technique in which some additional attributes are added to the record. If the number of quasi-attributes is less rare, then some dummy attributes are added into the record, which look like the quasi-attributes. Hence, by doing this, reidentification becomes more difficult [ 111 ]. By applying generalization on data, we can protect the identity of a person because it hides the relationship between the quasi-attributes.
The summary of data anonymization techniques is given in Table 7 .
The summary of data anonymization techniques.
(2) Data Splitting . Data splitting is a technique in which sensitive data is divided into different fragments [ 112 ] to protect it from unauthorized access. In this technique, we first split the data into different fragments, then these fragments are randomly stored on different clouds. Even if the intruder gains access to a single fragment in any way, still the intruder will not be able to identify the person. For example, if an intruder gets a fragment from the cloud that contains the salary information of an organization, it is useless until he knows which salary belongs to which person. Hence, data splitting is a very useful technique for protecting data stored on the cloud.
Local proxies outsource data to the cloud without splitting the data, and they can also split the data first and then outsource to the same cloud using different accounts in the same CSP. It can also store data on different cloud platforms that run through different CSPs but provide some of the same services. Data is split before storing in different locations because even if some part or piece of data is known to an intruder, they will not be able to identify anyone.
Firstly, the local proxy retrieves sensitive data from the user and then calculates the risk factor for disclosure. In this method, the user can define the privacy level, and this privacy level provides information about all the sensitive attributes that can reveal someone's identity. These sensitive attributes are called quasi-attributes or quasi-identifiers. Next, the local proxy decides the number of pieces into which the sensitive data will be split and the number of locations that will be needed to store those pieces. Therefore, no one can reveal a person's identity, and all this information about the data splitting mechanism is stored at the local proxy. However, the system must be able to function properly and respond to the queries on time. After that, the local proxy stores these different data fragments in different cloud databases, and now, they are free from disclosure. The data-splitting mechanism supports almost all the functions of the cloud. Hence, we can use almost all the services provided by CSP using the data-splitting mechanism for storing data in the cloud.
When the users want to retrieve the original data, they process a query on a local proxy. The query is processed, and the data storage locations are retrieved from the local database. After that, the query is replicated as many times as the data is split into fragments, and these queries are forwarded to the relevant CSPs. As a result, each CSP provides a set of results that represent a partial view of the complete result. Finally, the proxy collects partial results according to the criteria used to split the data and provides the complete result to the user. Mostly, all these fragments are stored on different cloud databases in their original structure. Therefore, computation on these fragments can be performed easily. However, there is a problem if we want to perform computation separately on the individual fragment. Then, there is no algorithm that exists for this computation. Therefore, some algorithms are required to perform these types of computation as this computation requires communication between different CSPs. The redundancy of proxy metadata and backup policies must be essential to ensure the robustness of the mechanism. The data-splitting is graphically represented in Figure 7 .

Data-splitting flow diagram.
The summary of the data-splitting is given in Table 8 . Different data-splitting techniques are used for the protection of data stored on the cloud. Some of these are given below.
- Byte level splitting
- In this type, all the sensitive data is converted into bytes [ 113 ]. Then, these bytes are randomly shuffled with each other. After that, all the bytes are recombined. Fixed length fragments are made, and then, these fragments are stored on a different cloud.
- Privacy level splitting
- In this mechanism, the user chose the privacy level of each file [ 114 ] that is to be stored on a cloud database. Hence, a privacy level is attached with the file that is to be stored on the cloud. Using this privacy level, the user can decide that the higher privacy level files should be stored on the trusted cloud.
- Byte level splitting with replication
- Byte-level data splitting is combined with data replication to improve both performance and security. The author of the paper [ 115 ] proposed an algorithm to store the data fragments on different clouds, so that they are at a certain distance and by doing this; we can avoid confabulation attacks where the intruder can aggregate the split fragments.
- Byte level splitting with encryption
- Firstly, byte-level data splitting [ 116 , 117 ] is proposed. In this scheme, every fragment of data is encrypted to enhance the security of sensitive data. In this mechanism, the data is split into bytes, and these bytes are randomly shuffled and finally recombined. This type of data splitting is suitable for binary or multimedia files that are not processed through the cloud.
- Another problem is the length of a fragment in which we can say that the data cannot be reidentified or the identity of a person cannot be revealed. If the length is too short, then the probability of disclosure increases, and if the length is too long, then it is difficult to handle these fragments. Hence, it should have a certain length so that we can also protect the identity of a person.
- There is another type of data splitting in which we split data into attributes. The attribute level splitting is performed in two ways: one is horizontal splitting and the second is vertical splitting. These types of splitting are mostly done on structural databases, and they provide strong privacy.
- Vertical splitting
- In vertical data splitting [ 118 , 119 ], we divide quasi-identifiers or quasi-attributes in such a way that all the risky attributes are divided into different fragments to secure the reidentification. Some of the sensitive fragments required encryption on it. Hence, we can encrypt these fragments by applying some encryption algorithms or by applying some other privacy methods to increase the security level.
The summary of the data-splitting techniques.
A solution for sensitive data splitting without performing encryption on fragments is proposed [ 120 ]. This mechanism is suitable for data on which we want to perform some computation, because on encrypted data, we cannot perform computation directly. Another technique has been proposed [ 121 ], which demonstrates the redaction and sanitization of a document that identifies all sensitive attributes and protects the data in most documents.
The schemes that use vertical splitting to protect data are faster than other splitting techniques because data fragments consist of a single attribute or multiple attributes. It does not involve data masking or encryption. Hence, the computation is easy. There is another type of encryption in which we do not encrypt and decrypt every time to perform computation. It is called homomorphic encryption. In this case, all data modification is done on encrypted data, and actual data is not changed, however, the final result is preserved [ 122 ].
(3) Steganography . Steganography is the practice of concealing a message within another message or a physical object. In computing contexts, video, audio, image, message, or computer file is concealed within another image, message, or file. The steganography flow diagram is depicted in Figure 8 . There are two main types of steganography, namely (1) linguistic steganography and (2) technical steganography. These techniques are given as follows:
- (1) Linguistic Steganography
- It uses images and symbols alone to cover the data. There are two types of Semagrams [ 123 ]. The first is a visual Semagram. In this type, we can visualize the massage. The second type is a text Semagram. In this type, we change the font, color, or symbols of the text message.
- In this case, we hide the real message from the intruder by installing the original massage in an authorized carrier [ 124 ]. Open code technique is further divided into two types: one is jargon code, and the second is covered ciphers.
- (2) Technical Steganography
- Text steganography
- In this type, we change some textual characteristics of text, such as the font, color, or symbols of the text message [ 127 ]. Three coding techniques are used to change these textual features, which are as follows: (1) line-shift coding, (2) word-shift coding, and (3) feature coding.
- Image steganography
- It is the most popular type of steganography. Image steganography refers to the process of hiding sensitive data inside an image file [ 128 ]. The transformed image is expected to look very similar to the original image because the visible features of the stego image remain the same. The image steganography is divided into three parts, namely (1) least significant bits coding, (2) masking and filtering, and (3) transformations.
- Audio steganography
- Audio steganography is a technique that is used to transmit secret data by modifying a digitalized audio signal in an imperceptible manner [ 129 ]. Following types of audio steganography are given: (1) least significant bits coding, (2) phase coding, (3) spread spectrum, and (4) echo hiding.
- Video steganography
- In video steganography, both image and audio steganography are used [ 130 ]. A video consists of many frames. Hence, video steganography hides a large amount of data in carrier images. In this type of steganography, we select the specific frame in which we want to hide the sensitive data.
- (ii) Methods
- Frequency Domain
- A frequency-domain steganography technique is used for hiding a large amount of data with no loss of secret message, good invisibility, and high security [ 131 ]. In the frequency domain, we change the magnitude of all of the DCT coefficients of the cover image. There are two types of frequency domain: (1) discrete cosine transformation and (2) discrete wavelet transformation.
- Spatial Domain
- The spatial domain is based on the physical location of pixels in an image [ 132 ]. A spatial domain technique gives the idea of pixel regulation, which minimizes the progressions of a stego image created from the spread image. Some methods of the spatial domain are given as follows: (1) least significant bit, (2) pixel value differencing, (3) pixel indicator, (4) gray level modification, and (5) quantized indexed modulation.

Steganography flow diagram.
The summary of the steganographic techniques is given in Table 9 .
The summary of the steganographic techniques.
4.1.2. Cryptographic Techniques
Cryptography is the most important and most widely used technique for security purposes. In cryptography, the plain text is converted into ciphertext using a key and some encryption algorithms. Cryptographic techniques are the most secure techniques among all the other security techniques. Hence, these cryptography techniques are widely used in data storage security over the cloud. The present day's cryptography techniques are more realistic. We can achieve different objectives by applying these cryptographic techniques, for example, data confidentiality and data integrity. Because of an increase in the number of data breaches in the last few years, some cloud service provider companies are shifting toward cryptographic techniques to achieve more security. The most commonly used cryptographic technique is AES [ 133 ]. Key management is an important issue in cryptographic techniques because if the key is hacked by an intruder, then all the data will be hacked or stolen by this intruder. Hence, key protection or key management is a very important issue. Therefore, it is mostly the responsibility of CSP to manage the key and also provide the protection of key. Cryptographic techniques also protect the user from an untrusted CSP because sometimes the CSP outsources sensitive data without taking the permission of users, and it is an illegal activity. Hence, to avoid these things and protect our sensitive data from untrusted CSPs, we use cryptographic techniques, and it is the best option for users. However, there are some difficulties the user has to face while using cryptographic techniques, i.e., if a user wants to update a small amount of data, the user needs to decrypt the data and then perform this minor update. Hence, this work is very costly. Over time, implementing cryptographic techniques gives us a higher level of security, however, we compromise on performance or speed. It all depends on the user, the standard, the performance, or the high level of security the user wants to achieve. In this paper, we are focusing on the four main functionalities that are required or needed on cloud computing when using cryptographic techniques. Figure 9 shows the flow diagram of encryption.

Encryption flow diagram.
Some of the main functionalities of cryptographic functions are given below.
- Search on encrypted data
- If a user wants to retrieve their data stored in a cloud database, they generate a query and run the query on a local proxy server and search for the data they want. Searching for encrypted data is a very important part of cryptography because every user who stores their sensitive data in a cloud database wants to retrieve it, and it is done by searching their sensitive data through queries. Therefore, the procedure of retrieving their data is very difficult.
- Storage control
- Sometimes the user wants to store data in a desired location or trusted database. Hence, the user must have full control over the storage of data.
- Access control
- It is a very important control and is referred to as data access restriction. Sometimes, the user does not want to share a private file publicly. Hence, access control is an important functionality.
- Computation on data
- Data computation is the main functionality of cloud computing. Sometimes, the user wants to perform some computation on data that are stored on a cloud database. For example, if a user wants to perform computation on encrypted data that is stored on cloud databases, then there are two ways. One is that the user, firstly, decrypts the entire data, performs computation on the data, and finally, the user encrypts the entire data and stores on the cloud database. This process is very expensive in terms of computation.
Some of the cryptographic techniques are as follows:
(1) Homomorphic Encryption . Homomorphic encryption is a form of encryption that permits users to perform computations on encrypted data without decrypting it. These resulting computations are left in an encrypted form, which, when decrypted, result in an identical output to that produced had the operations been performed on the unencrypted data. There are some types of homomorphic encryption that are described below.
- Partial Homomorphic Encryption
- In partial homomorphic encryption, only one arithmetic function addition or multiplication is performed at one time. If the resultant ciphertext is the addition of the plain text, then it is called an additive homomorphic scheme, and if the resultant ciphertext is the multiplication of the plaintext, then it is called the multiplicative homomorphic scheme. Two multiplicative homomorphic schemes are given as in [ 134 , 135 ]. There is one additive homomorphic scheme that is called Paillier [ 136 ].
- Somewhat Homomorphic Encryption
- This technique allows the user to perform the multiplication and subtraction mathematical operations. However, this scheme allows a limited number of arithmetic operations, because if it allows a large number of arithmetic operations, then it produces noise. This noise changes the structure of the original data. Hence, limited numerical math operations are allowed. There is a somewhat homomorphic encryption scheme that is presented by the authors of the papers [ 137 , 138 ]. In this scheme, the time of encryption and decryption is increased when multiplication operations are increased. To avoid this increase in time, we allow only a limited number of mathematical operations.
- Fully Homomorphic Encryption
- This technique allows a large number of arithmetic operations, namely multiplication and subtraction. Multiplication and addition in this technique are performed in the form of XOR and AND gates [ 139 ]. Completely homomorphic encryption techniques require a higher computation time to encrypt and decrypt data. Therefore, this technique is not applicable in real-life applications for implementation. This technique uses a bootstrapping algorithm when a large number of multiplication operations is performed on data and also for the decryption of the data it is used. Homomorphic encryption, on the other hand, represents the trade-off between operations and speed performance. Only a limited number of arithmetic operations are allowed if someone wants low computation, and a large number of arithmetic operations are allowed if someone wants high security. It depends on the needs of the user.
(2) Searchable Encryption . A searchable encryption technique is proposed by the author of the paper [ 140 ]. In this technique, before storing data on a cloud database, encryption is performed, and after that, it is stored on the cloud. The advantage of this technique is that when we search for some data over the cloud database, this technique provides a secure search over the cloud database.
- Searchable Asymmetric Encryption
- Over the past two decades, we have focused on searchable encryption. Much of the work is related to the multiwriter and single-reader cases. Searchable encryption is also called public keyword search encryption along with keyword search (PEKS) [ 141 ].
- Searchable Symmetric Encryption
- Symmetric-key algorithms use the same key for massage encryption and ciphertext decryption. The keys can be the same, or there can be a simple transformation to go between the two keys. Verifiable searchable symmetric encryption, as a key cloud security technique, allows users to retrieve encrypted data from the cloud with keywords and verify the accuracy of the returned results. Another scheme is proposed for keyword search over dynamic encrypted cloud data with a symmetric-key-based verification scheme [ 142 ].
(3) Encryption . In cryptography, encryption is the process of encoding information. This process converts the original representation of the information, known as plaintext, into an alternative form known as ciphertext. Ideally, only authorized parties can decipher a ciphertext back to plaintext and access the original information.
- Symmetric Key Encryption
- Only one key is used in symmetric encryption to encrypt and decrypt the message. Two parties that communicate through symmetric encryption should exchange the key so that it can be used in the decryption process. This method of encryption differs from asymmetric encryption, where a pair of keys is used to encrypt and decrypt messages. A secure transmission method of network communication data based on symmetric key encryption algorithm is proposed in [ 143 ].
- Public Key Encryption
- The public-key encryption scheme is proposed by the author of the paper [ 144 ]. In this scheme, a public key pair is created by the receiver. This public key pair consists of two keys. One is called a public key, which is known publicly to everyone, and the second is the private key, which is kept a secret. Hence, in this scheme, the sender performs encryption on the data using the public key of the receiver and then sends this encrypted data to the receiver. After receiving this encrypted data, the receiver can decrypt this data using the private key. Hence, in this way, we can perform secure communication between two parties.
- Identity-Based Encryption
- Identity-based encryption is proposed by the author of the paper [ 145 ]. In this technique, a set of users is registered on the database and a unique identity is assigned to all the registered users by an admin that controls this scheme. The identity of the users can be represented by their name or their e-mail address. Just like in a public-key encryption, there is a public key pair that consists of one public key, which is the identity of the user, and one private key, which is a secret key. Just like in public-key encryption, the receiver cannot generate their public key in identity-based encryption. The identity cannot be generated by the user. There is a central authority that generates and manage the user's identity. The identity-based encryption is improved by the author [ 146 ]. The main advantage of identity-based encryption is that anyone can generate the public key of a given identity with the help of the central main authority.
- Attribute-Based Encryption
- The authors of the papers [ 147 , 148 ] propose a technique called attribute-based encryption. Similar to identity-based encryption, attribute-based encryption also depends on the central main authority. The central main authority generates the private key and distributes it to all the registered users. It can be encrypting the messages, however, if it does not have this designation, then it cannot be generating the messages. Attribute-based encryption is used when the number of registered users is very large. Then, the attribute-based encryption is useful. The attribute-based encryption consists of two schemes, which are key policy and ciphertext policy.
- Functional Encryption
- A functional encryption technique [ 149 , 150 ] consists of identity-based encryption, attribute-based encryption, and public-key encryption. All the functionalities of these three techniques combinedly make function encryption. In this technique, all the private keys are generated by the central main authority, which is associated with a specific function. Functional encryption is a very powerful encryption technique that holds all the functionalities of three encryption techniques. A functional encryption technique is used in many applications.
(4) Signcryption . Cryptography is publicly open-source, and it functions simultaneously as a digital signature and cipher. Cryptography and digital signatures are two basic encryption tools that can ensure confidentiality, integrity, and immutability. In [ 151 ], a new scheme called signature, encryption and encryption is proposed, based on effectively verifiable credentials. The system not only performs encryption and encryption but also provides an encryption or signature form only when needed [ 152 ]. The paper proposes lightweight certificate-based encryption using a proxy cipher scheme (CSS) for smart devices connected to an IoT network to reduce computing and communications costs. To ensure the security and efficiency of the proposed CBSS project, we used a cipher system encoded with 80 bit subparameters. Reference [ 153 ] proposes an input control scheme for the IoT environment using a cryptographic scheme corresponding to the efficiency and robustness of the UK security system. The proposed scheme shows that besides security services, such as protection against attacks, confidentiality, integrity, nonblocking, nondisclosure, and confidentiality, accounting and communication costs are low compared to the current scheme. Document [ 154 ] gives the informal and formal security proof of the proposed scheme. Automated Validation of Internet Security Protocols and Applications (AVISPA) tool is used for formal security analysis, which confirms that the proposed CB-PS scheme can potentially be implemented for resource-constrained low-computing electronic devices in E-prescription systems. The proposed scheme [ 155 ] introduced a new concept that does not require a reliable channel. The main production center sends a part of the private key to the public consumers. The summary of the cryptographic schemes is given in Table 10 .
The summary of the cryptographic techniques.
All data storage protection on cloud computing is discussed in session 3. There are a lot of data protection techniques, however, all these techniques are only divided into three main categories, namely (i) data splitting, (ii) data anonymization, and (iii) cryptography. From different points views, we discuss all these techniques, e.g., overhead on the local proxy, computation cost, search on encrypted data, data accuracy all these techniques retained, and data protection level all these techniques have, and all the masked data techniques have the functionalities. These are some different views, and by considering them, we can analyze all the data protection techniques. Cryptography provides high-level security but limited cloud functionalities and a high cost of performing computation on cloud data. Data splitting provide low computation cost but a low level of security. Data anonymization is of two types: one is perturbative masking, and the second is nonperturbative masking. Hence, in perturbative masking, data is altered with dummy data. Hence, security is high, however, we cannot perform some functionalities.
4.2. RQ2: What are the Demographic Characteristics of the Relevant Studies?
We answer this question by considering the four following aspects: (i) publication trend, (ii) publication venues (proceeding and journals), (iii) number of citations, and (iv) author information.
4.2.1. Publication Trend
From 2010 to 2021, we found 52 papers that were of top ranked journals and conferences. From 2010 to 2017, there is linear work in cloud computing, however, after 2017, a lot of work is done in cloud computing data security. From 2018 to 2021, 37 papers are published. After 2018, the trend about data security in cloud computing increased very vastly. Most of the work is done in 2021. High-ranked studies are published in 2021. Figure 10 shows all trends of all the publications from 2010. Most of the articles are published in journals venue, and the highest number of papers have been published in IEEE Access journal. 6 papers were published in this journal.

Number of publications per year.
4.2.2. Publication Venues
There are different types of publication venues, and some of them are book articles, conference proceedings, journals, workshop proceedings, and symposium proceedings. Hence, in our SLR, the number of publications in a different venue is given in Figure 11 . We have a total of 52 papers after applying the inclusion and exclusion criteria in Section 2 .

Publication venues.
Out of 52 papers, 0 papers are published in book chapters. 1 paper is published in workshop proceedings. 0 papers are published in symposium proceedings. 43 papers are published in journals. 8 papers are published in conference proceedings. There are some most active journals in cloud data security, which are enlisted in Table 11 .
Top 5 most active journals.
The most active journal is the IEEE Access. In this journal, 6 papers are published. Journal of Cryptology is the second most active journal in the field of data storage, security, and privacy in cloud computing. In this journal, 3 papers are published. In the third journal, i.e., in the Journal of Information Fusion, 3 papers are published. The fourth journal is the Information Science. In this journal, 2 papers are published. The fifth journal is IEEE Transactions on Knowledge and Data Engineering, and in this journal, 2 papers are published. Most active conferences are given in Table 12 .
Top 5 most active conferences.
4.2.3. Number of Citations
The number of citations of a paper also tells the quality of the paper. The more the number of citations, the higher the quality, and the fewer the number of citations of the paper, the lower the paper quality. Table 13 shows the most influential authors, and Figure 12 shows the number of citations of all the papers that we have used in this SLR. Few papers have citations of more than 100. Hence, it shows that papers have a very high quality, and hence, the citation of those papers is very high. These papers are [ 105 , 118 , 124 , 139 ].

Number of citations of the papers.
Top 10 most influential authors in data protection in cloud computing.
4.2.4. Author Information
Some authors are most active in their publication. To identify these authors, we enlist the names of the top 10 authors that are more active in the field of data protection and privacy in cloud computing. Hence, we enlist the names of the top 10 authors and also their numbers of publications in Table 13 .
4.3. RQ3: Which Data Protection Technique Provides More Data Protection among all the Techniques?
We answer this question by considering the following four aspects: (i) publication trend, (ii) publication venues (proceeding and journals), (iii) number of citations, and (iv) author information.
4.3.1. Comparison of Data Protection Techniques
In this section, we compare all the data protection techniques that are discussed in this SLR, and finally, we review which technique is better and provides more protection among all these data protection techniques. We compare these techniques based on different functionalities, which are given as (i) local proxy overhead, (ii) data accuracy retain, (iii) level of data protection, (iv) transparency, and (v) operation supported, and finally, we discuss RQ2. Table 14 depicts a comparison of all the data protection techniques and provides a brief comparison of all the data protection techniques discussed in this SLR. Now, we discuss all these five functionalities one by one in more detail.
- The overhead on the local proxy for encryption is very high because the data is encrypted. If the user wants to update the data, firstly, the user decrypts the data and then updates the data. After that, the user encrypts the data again. Hence, this operation requires a lot of time, and all this work is performed by the local proxy. It is the reason the overhead on the local proxy for encryption is very high for encryption.
- Data Splitting
- The overhead on a local proxy for data splitting is very low. The local proxy overhead remains constant while splitting data into fragments.
- Anonymization
- The overhead on a local proxy for anonymization is average because most of the anonymization methods require quasilinear computation in the number of records to generate the anonymized data set. Whenever the anonymized data is generated and stored in the cloud database, then there is no overhead on the local proxy.
- Homomorphic Encryption
- The overhead on local proxies for homomorphic encryption is very high because homomorphic encryption involves a large number of mathematical operations. Therefore, there is a lot of overhead on local proxies for homomorphic encryption.
- Steganography
- The overhead on the local proxy for steganography is not too much as the data is concealed inside the cover for secure communication. However, based on the complexity of the operation in the transformed domain technique, the local proxy overhead is more than the spatial domain technique.
- Signcryption
- The overhead on the local proxy for signcryption is high compared to the simple encryption because in signcryption, hashing and encryption are performed in a single logical step. Because of an extra operation in signcryption, the overhead on the local proxy is higher than the simple encryption.
- The data accuracy level for encryption is very high because data is encrypted by applying some algorithms. The sensitive data is encrypted by the sender, and this data is decrypted by the receiver using a key. This data cannot be read by anyone who does not have the secret key. Therefore, data accuracy is very high for encryption.
- The data accuracy level for data splitting is average because data-splitting data is present in the form of fragments. Therefore, CSP can easily access the fragments of data. Both encryption and data splitting are irreversible methods. Hence, we can retrieve the original data easily.
- The data accuracy level for data anonymization is very low because anonymization is not irreversible. In anonymization, data is replaced with dummy data, and it cannot be retrieved back. Therefore, anonymization has a very low level of data accuracy.
- The data accuracy level for homomorphic encryption is very high because data is encrypted by applying some algorithms.
- The data accuracy level for steganography is very low as compared to the other cryptographic techniques because data is embedded inside the cover of another medium. Any change in the cover during transmission results in the change of the concealed data. Therefore, it is hard to ensure a high accuracy level in steganography. The stego image contains the secrete data that is transmitted over the communication channel. Data concealed by the sender is extracted from the cover by the receiver. Therefore, the concealment of data results in accurate data transmission.
- The data accuracy level for signcryption is also very high, because in signcryption, confidentiality and authentication are achieved. Therefore, we can also verify the identity of the sender.
- The level of data protection is very high for encryption techniques, because in encryption, data is changed into ciphertext, which cannot be understood. Therefore, we can say that the identification of data is impossible without decryption using a secret key because encryption is a one-way function that is easy to execute in one direction, however, it is impossible to execute in the opposite direction.
- The level of data protection for data splitting is less high as compared to cryptographic techniques because data is split into different fragments, and these fragments contain original forms of data. Hence, if an intruder hacks or steal these fragments, then the untired data can be easily read. Hence, the data protection level is not high as compared to encrypted methods.
- The level of data protection for data anonymization is less high as compared to cryptographic techniques, because in anonymization techniques, quasi-identifiers are protected if the quasi-identifiers are not protected strongly. Then, there is a change in the reidentification of person-sensitive data.
- The level of data protection is very high for homomorphic encryption techniques because encryption data is changed into ciphertext, which cannot be understood.
- The data protection level for steganography is medium because data is embedded inside the cover of another medium. The stego image contains the secrete data that is transmitted over the communication channel. Data concealed by the sender is extracted from the cover by the receiver. Therefore, the concealment of data results in secure data transmission.
- The data protection level for signcryption is also very high, because in signcryption, both confidentiality and authentication are achieved. Therefore, we can also verify the identity of the sender.
- There is no transparency for the encrypted data, because in encryption, there is a need for key management. Hence, the local proxy needs to keep the records of all the keys and manage all these keys. Therefore, there is no transparency for the encrypted data.
- There is no transparency for the data-splitting mechanism, because in the data-splitting mechanism, data is split into different fragments, and the local proxy stores these fragments in different locations. Hence, there is a need to keep the record of the location of all the fragments that are stored on different locations.
- Anonymization is fully transparent, because in anonymization, there is no need to keep the record of data storage by the local proxy. In anonymization, data is statistically similar to the original data. Hence, CSP also performs computation and some analysis on the anonymized data.
- There is no transparency for the homomorphically encrypted data, because in encryption, there is a need for key management. Hence, the local proxy needs to keep the records of all the keys.
- In steganography, as compared to other data protection techniques, the main aim is to transmit data without letting the attacker know about the data transmission as it is concealed inside the cover of another medium. The data transmission in steganography is fully transparent. No key management is required, and there is no need to keep track of data storage.
- There is no transparency for the signcrypted data, because in signcryption, there is a need for key management. Hence, the local proxy needs to keep the records of all the keys and also manage all these keys.
- Only the data storage operation is supported on the encrypted data, because if the user wants to update some encrypted data that are stored on a cloud database, firstly, the user needs to decrypt this data, and then the user performs an update on this data. We cannot perform any modification operation on encrypted data.
- All the operations cloud be performed on data splitting, because in data splitting, the data is present in their original structure. Hence, we can perform data storage, search, data update, and also data computation.
- In anonymization, there are two types of data anonymization: one is data masking, and the second is data nonmasking. If data is nonmasked, then we can perform data storage and search on this data. Otherwise, we can only perform data storage.
- Only the data storage operation is supported on the encrypted data, because if the user wants to update some encrypted data that are stored on the cloud database, firstly, the user needs to decrypt this data, and then the user performs some updates on this data.
- A stego image only supports data storage operations because if the user wants to update the data hidden in a stego image, the user, firstly, retrieves that data from the stego image, and the user can perform any modification on this data.
- Only the data storage operation is supported on the signcrypted data, because if the user wants to update signcrypted data that are stored on the cloud database, firstly, the user needs to unsign this data, and then the user can perform any update on this data.
Comparison of data protection techniques.
5. Conclusion and Future Work
5.1. rq4: what are the primary findings, research challenges, and direction for future work in the field of data privacy in cloud computing, 5.1.1. conclusion and research challenges.
In this SLR, we have presented all the data privacy techniques related to data storage on cloud computing systematically, and we also present a comparison among all the protection techniques concerning the five finalities, which are the (i) local proxy overhead, (ii) data accuracy retains, (iii) level of data protection, (iv) transparency, and (v) operation supported. There are some research gaps we found in all these techniques of data splitting, anonymization, steganography, encryption, homomorphic encryption, and signcryption.
- There is a very strong need to develop some ad hoc protocols for the communication of data splitting fragments that are stored on different CSPs, and also, there is a strong need to develop some protocol for the communication between different CSPs. Noncryptographic techniques are faster on different CSPs but do not provide enough security. Hence, we can improve security by developing some methods for data-splitting techniques.
- Anonymity techniques work very effectively on a small amount of data but not for big data. Hence, there is a search gap in which we can develop some anonymity techniques to achieve more efficient performance. Therefore, some anonymous schemes need to be developed, which provide stronger protection to the quasi-identifier. Current anonymity techniques are very immature.
- One of the limitations of steganography is that one can only use it to defend against a third party who does not know steganography. If the third party knows steganography, it can extract the data in the same way that the recipient extracts it. Therefore, we always use encryption with steganography. Therefore, there is a need to develop such steganography techniques that can protect sensitive data from third parties.
- There is a need to develop some cryptographic techniques that can take less time than the existing cryptographic techniques to perform search and computation operation on encrypted data. Cryptographic techniques provide high security but low computational utility. Therefore, it is a search gap to develop some techniques that provide both high security with more efficiency.
- The complexity of homomorphic encryption and decryption is far greater than that of normal encryption and decryption, and it is not applicable to many applications, such as healthcare and time-sensitive applications. Therefore, there is an urgent need to develop such homomorphic encryption schemes that have low complexity and computation cost.
- Signcryption is used to verify and authenticate users. We can obtain confidentiality and authentication using signcryption, however, the main limitation of signcryption is that the calculation costs of the encryption algorithm used in signcryption are very high. Therefore, there is a need to develop such signcryption schemes that use such encryption algorithms, which have low computation cost.
Acknowledgments
This research was financially supported by The Analytical Center for the Government of the Russian Federation (Agreement nos. 70-2021- 00143 dd. 01.11.2021, IGK 000000D730321P5Q0002).
Data Availability
Conflicts of interest.
The authors declare that there are no conflicts of interest regarding the publication of this paper.
Need cloud computing? Get started now
Cloud Computing
Content Delivery
- All Products and Trials
Global Services
Build, release, and scale faster with VMs for every workload
Secure your network, balance traffic, control your infrastructure
Efficiently orchestrate containerized applications
Developer Tools
Get the most out of your applications with advanced management tools
Deploy dependable, easily accessible storage and management
Scale easily with simple and reliable managed databases
App and API Security
Api security.
Discover and monitor API behavior to respond to threats and abuse
App & API Protector
Protect web apps and APIs from DDoS, bots, and OWASP Top 10 exploits
Client-Side Protection & Compliance
Assist with PCI compliance and protect against client-side attacks
Zero Trust Security
Akamai guardicore segmentation.
Mitigate risk in your network with granular, flexible segmentation
Secure Internet Access
Proactively protect against zero-day malware and phishing
Stop the most evasive threats with proactive threat hunting
Enterprise Application Access
Granular application access based on identity and context
Harden against account takeovers and data breaches with phish-proof MFA
Abuse and fraud protection
Account protector.
Mitigate account abuse and grow your digital business
Content Protector
Stop scrapers, protect intellectual property, and increase conversion
Brand Protector
Detect and mitigate fraudulent representations of your brand
Bot Manager
Welcome the bots you want and mitigate those you don’t
Identity Cloud
Add secure, cloud-based identity management to your websites or apps
Audience Hijacking Protector
Retain site visitors, maximize conversions, and reduce affiliate fraud
INFRASTRUCTURE SECURITY
External authoritative solution for your DNS infrastructure
Protect your infrastructure from distributed denial-of-service attacks
APPLICATION PERFORMANCE
Improve the performance and reliability of your website at scale
API Acceleration
Improve the performance and reliability of your APIs at scale
MEDIA DELIVERY
Adaptive media delivery.
High-quality video delivery for any screen to global audiences
Download Delivery
Deliver large file downloads flawlessly, every time, at global scale
Dedicated Delivery
Deliver broadcast-quality video while maximizing network efficiency
EDGE APPLICATIONS
Edgeworkers.
Execute custom JavaScript at the edge, near users, to optimize UX
Distributed key-value store database at the edge
Image & Video Manager
Automatically optimize images and video for every user, on any device
Media Services Live
Reliably ingest and deliver low-latency live video at global scale
Predefined apps that run at the edge for specific business needs
Cloud Wrapper
Use an efficient caching layer to improve origin offload
Global Traffic Management
Optimize performance with intelligent load balancing
MONITORING, REPORTING, AND TESTING
Low-latency data feed for visibility and ingest into third-party tools
Measure the business impact of real user experiences in real time
Site and application load testing at global scale
Industry Solutions
Cloud computing.
Deliver an engaging, interactive video experience
Build with portability, performance, and efficiency from cloud to client
Improve the gamer experience with low latency and high availability
Apps and APIs
Protect your brand by securing apps and APIs from persistent threats
Deploy one platform for comprehensive coverage and deep visibility
DDoS Protection
Protect your infrastructure from DDoS and DNS attacks
Abuse and Fraud Protection
Stop account abuse, sophisticated bot attacks, and brand impersonation
CONTENT DELIVERY
App and api performance.
Improve user engagement through app & API optimization
Media Delivery
Deliver seamless streaming and download experiences to any device
Edge Compute
Build and deploy on the world’s most distributed edge platform
Media and Entertainment
Retail, travel, and hospitality, financial services, healthcare and life sciences, public sector, igaming and sports betting, network operator.
Discover how we power and protect life online
Our Platform
Explore Akamai Connected Cloud
- Security Research
- Developer Resources
Product Briefs
Reference architectures, customer stories, white papers, learning hub.
Educational resources and training for Akamai products and services
Key concepts in security, cloud computing, and content delivery
Akamai Security Research
Insights and intelligence from the Akamai Security Intelligence Group
State of the Internet Reports
In-depth analysis of the latest cybersecurity research and trends
Find a Partner
Become a partner.
- Cloud Computing Marketplace
Why Choose an Akamai Partner
Learn about our industry-leading ecosystem of partners
Channel Partners
Unlock more profit, focus on what matters, and deliver with confidence
Technology Partners
Create more value for joint customers with seamless integrations
Contact Sales
Have questions? We can help.
Customer Support
Need technical support? We are here 24/7.
XZ Utils Backdoor — Everything You Need to Know, and What You Can Do

Akamai Security Intelligence Group
April 01, 2024

Executive summary
CVE-2024-3094 is a vulnerability discovered in the open-source library XZ Utils that stems from malicious code that was pushed into the library by one of its maintainers.
It was originally reported as an SSH authentication bypass backdoor, but further analysis indicates that the backdoor actually enables remote code execution (RCE).
The threat actor started contributing to the XZ project almost two years ago, slowly building credibility until they were given maintainer responsibilities. Such long-term operations are usually the realm of state-sponsored threat actors, but specific attribution does not currently exist.
Since the backdoor affects the latest XZ Utils releases, the recommended course of action is to downgrade to an uncompromised release. In this blog post, we offer other potential mitigations to limit the blast radius of the attack.
XZ Utils,, and its underlying library liblzma, are open-source projects that implement the lzma compression and decompression. They are included in many Linux distributions out of the box, are very popular with developers, and are used extensively throughout the Linux ecosystem.
Almost two years ago, a developer under the name of Jia Tan joined the project and started opening pull requests for various bug fixes or improvements. So far, nothing is out of the ordinary; this is how things work in the open-source world. Eventually, after building trust and credibility, Jia Tan began to receive permissions for the repository — first, commit permissions and, eventually, release manager rights.
It seems that as part of the effort to gain these permissions, Jia Tan used an interesting form of social engineering : They used fake accounts to send myriad feature requests and complaints about bugs to pressure the original maintainer, eventually causing the need to add another maintainer to the repository.
After contributing to the code for approximately two years, in 2023 Jia Tan introduced a few changes to XZ that were included as part of release 5.6.0. Among these changes was a sophisticated backdoor.
The backdoor
The backdoor is quite complex. For starters, you won’t find it in the xz GitHub repository (which is currently disabled, but that’s besides the point). In what seems like an attempt to avoid detection, instead of pushing parts of the backdoor to the public git repository, the malicious maintainer only included it in source code tarball releases. This caused parts of the backdoor to remain relatively hidden, while still being used during the build process of dependent projects .
The backdoor is composed of many parts introduced over multiple commits:
Using IFUNCs in the build process, which will be used to hijack the symbol resolve functions by the malware
Including an obfuscated shared object hidden in test files
Running a script set during the build process of the library that extracts the shared object (not included in the repository, only in releases, but added to .gitignore )
Disabling landlocking , which is a security feature to restrict process privileges
The execution chain also consists of multiple stages:
The malicious script build-to-host.m4 is run during the library’s build process and decodes the “test” file bad-3-corrupt_lzma2.xz into a bash script
The bash script then performs a more complicated decode process on another “test” file, good-large_compressed.lzma , decoding it into another script
That script then extracts a shared object liblzma_la-crc64-fast.o , which is added to the compilation process of liblzma
This process is admittedly hard to follow. We recommend Thomas Roccia ’s infographic for a great visual reference and in-depth analysis.
The shared object itself is compiled into liblzma, and replaces the regular function name resolution process. During (any) process loading, function names are resolved into actual pointers to the process memory, pointing at the binary code. The malicious library interferes with the function resolving process, so it could replace the function pointer for the OpenSSH function RSA_public_decrypt (Figure 1).
It then points that function to a malicious one of its own, which according to research published by Filippo Valsorda , extracts a command from the authenticating client’s certificate (after verifying that it is the threat actor) and passes it on to the system() function for execution, thereby achieving RCE prior to authentication.
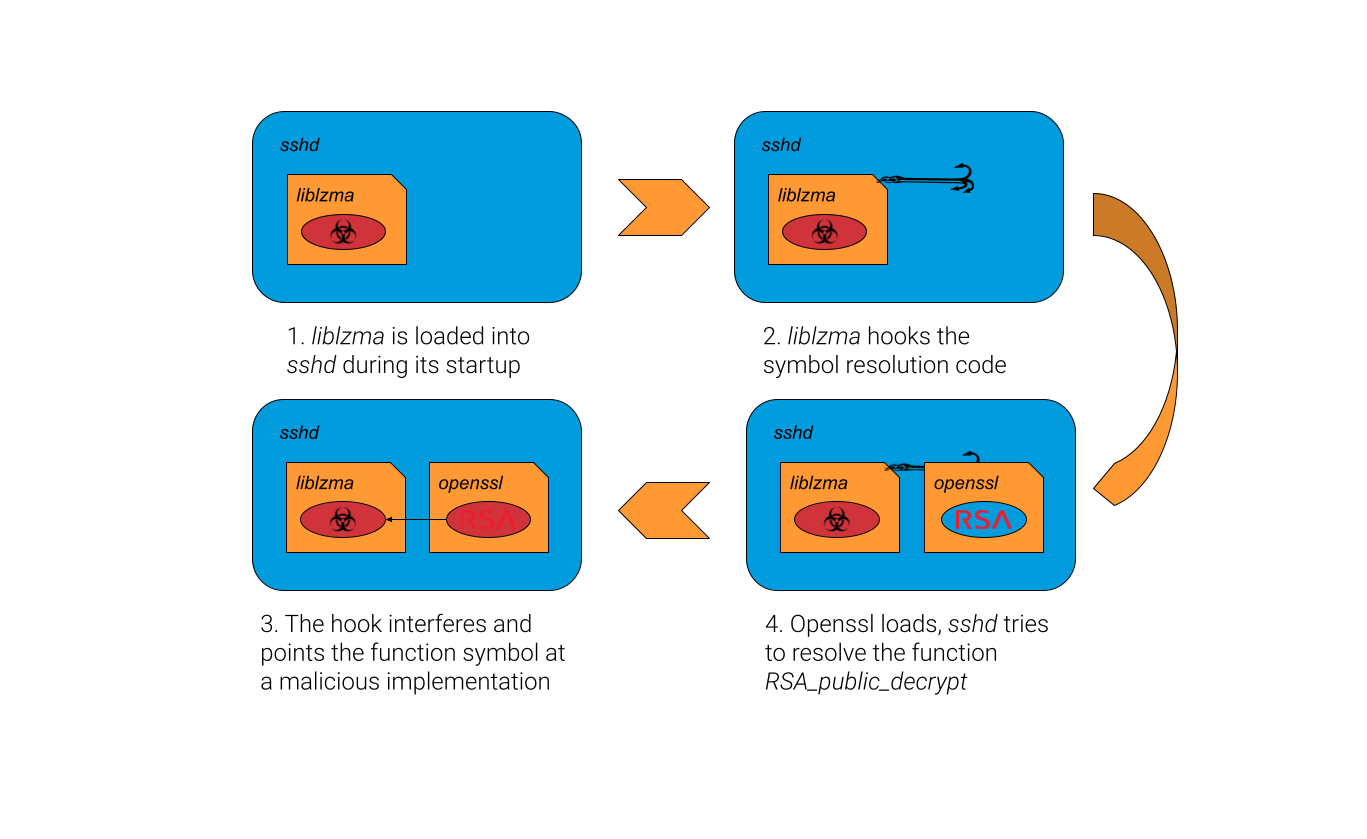
For a more detailed explanation of the backdoor parts, you can read Andres Freund 's post on openwall .
Potential impact
Currently, it appears as though the backdoor is added to the SSH daemon on the vulnerable machine, enabling a remote attacker to execute arbitrary code . This means that any machine with the vulnerable package that exposes SSH to the internet is potentially vulnerable.
This backdoor almost became one of the most significant intrusion enablers ever — one that would’ve dwarfed the SolarWinds backdoor. The attackers were almost able to gain immediate access to any Linux machine running an infected distro, which includes Fedora, Ubuntu, and Debian. Almost.
There was only one thing that stopped that from happening — Andres Freund. After investigating a 500 ms latency issue that was introduced after a software update, Andres was able to trace the issue back to the xz package and ultimately identify the backdoor.
This obviously raises a lot of concerns. We got lucky. If this backdoor was not detected by a curious engineer, how long would it have remained active?
And perhaps even more concerning: What if this has happened before?
Detection and mitigation
Version control.
The Cybersecurity and Infrastructure Security Agency (CISA) recommended course of action is to downgrade to an uncompromised version, such as 5.4.6.
To know which version of XZ Utils or liblzma you currently have on your systems, you can run the following query in Akamai Guardicore Segmentation Insight that will look for loaded instances of the liblzma library (Figure 2).
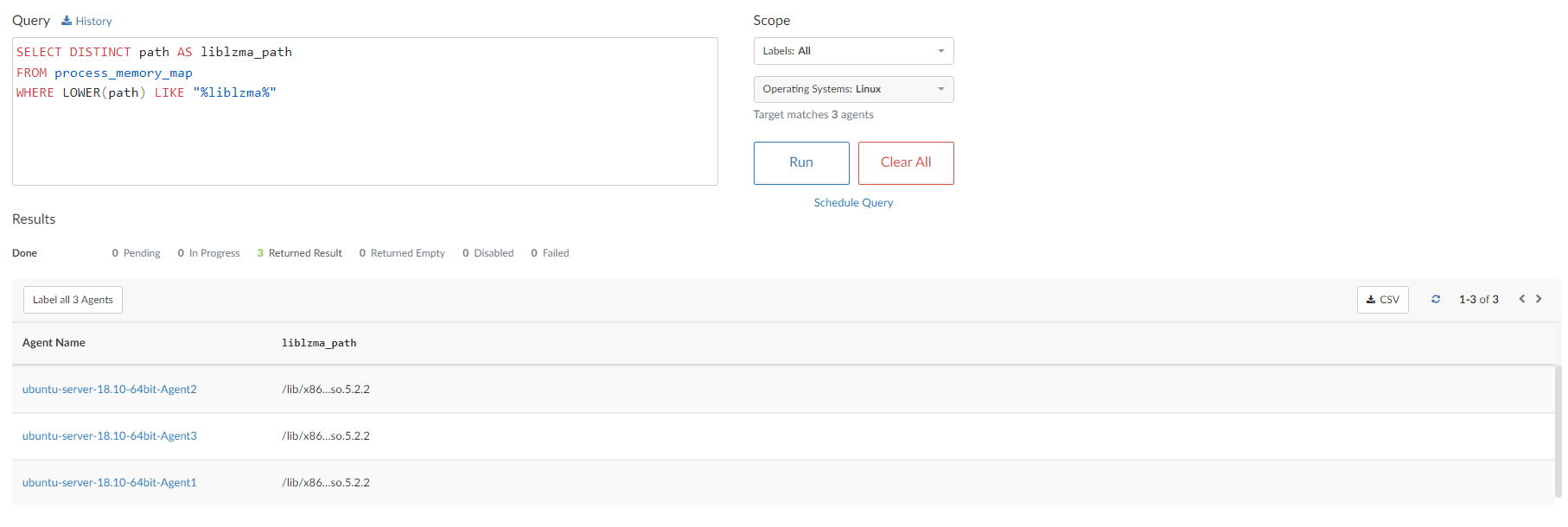
Alternatively, you can run the following query to find the package manager for the installed version.
Of course, you can also filter to show only vulnerable assets.
Threat hunting
Since the backdoor actually executes system commands, and isn’t just allowing authentication, it might be possible to detect this behavior via process tracking.
Usually, during logon, a new shell is created for the logging user, and runs the default shell process (like bash). However, with this backdoor, the malicious command is actually executed by the SSH daemon process, sshd , which could trigger an anomaly.
Our threat hunting service, Akamai Hunt , has methods in place to detect such anomalies; for example, by constantly tracking a baseline of process activity and their child processes.
Kill switch
According to some analyses of the backdoor , it appears to have an environment variable kill switch. Adding the key yolAbejyiejuvnup=Evjtgvsh5okmkAvj to the system’s environment variables may disable the backdoor.
Backdoor in upstream xz/liblzma leading to ssh server compromise
FAQ on the xz-utils backdoor
Filippo Valsorda on X
CISA advisory
- Cyber Security
- Threat Intelligence
- Segmentation
Related Blog Posts

Honey, I Lost My Credentials! Finding Plaintext Credentials on the Internet
Abusing the dhcp administrators group to escalate privileges in windows domains, akamai's perspective on march's patch tuesday.
All products and trials
Facts and Figures
Board of Directors
Investor Relations
Environmental, Social, and Governance
Working at Akamai
Students and Recent Grads
Workplace Diversity
Search Jobs
Culture Blog
Press Releases
In the News
Media Resources
Legal & compliance
Information Security Compliance
Privacy Trust Center
Cookie Settings
What Is Zero Trust?
What Is a CDN?
What Is Cloud Computing?
What Is Cybersecurity?
What Is a DDoS attack?
EMEA Legal Notice
Service Status
©2024 Akamai Technologies

IMAGES
VIDEO
COMMENTS
Cloud computing has become a widely exploited research area in academia and industry. Cloud computing benefits both cloud services providers (CSPs) and consumers. The security challenges associated with cloud computing have been widely studied in the literature. This systematic literature review (SLR) is aimed to review the existing research studies on cloud computing security, threats, and ...
associated with cloud computing have been widely studied in the literature. This systematic literature. review (SLR) is aimed to re view the existing research studies on cloud computing security ...
7.1. Challenges. Via analysis and contrast, we observe that cloud computing security protection work has achieved satisfactory research results. However, many problems remain, which prompt the consideration of a variety of security factors and continuous improvements in defense technology and security strategies. 1.
This research report systematically investigates various challenges and vulnerabilities in cloud computing, focusing on security and privacy issues. This study comprehensively examines potential ...
We will be concentrating majorly on cloud computing fraught with threats and how to overcome those threats. This paper is intended to introduce information about the most current attacks on cloud computing, just as safety efforts. The seriousness and impact of these attacks are talked about alongside genuine instances of these attacks.
With the idea of cloud computing, users and companies have access to a model that makes it easier to provision and release a variety of resources, including networks, servers, storage ...
The research evaluates and contrasts six security models of risk assessment methodologies: ISO27005, NIST SP 800-30, CRAMM, CORAS, OCTAVE Allegro, and COBIT 5. The evaluation of the models is based on their suitability, flexibility, and engagement in an approach to cloud-based hosting.
trust in cloud computing environment. Although, cloud computing is still in its advancement phase, there have been numbersof approaches and methodsproposed by researchers for the improvement of cloud computing security. In [4], the study proposed a novel risk identification framework for cloud computing security. The study also showed that the
Cloud security is the mechanism to prevent cyber-attacks in the cloud. It is similar to cybersecurity. Servers and data centres play the roles of upload and download data to the cloud. It is the server that enables the usage of data for any user from any place and time. With the spread of cloud usage among individuals, Cloud computing security ...
A STUDY ON CLOUD COMPUTING SECURITY VULNERABILITIES & INTEGRITY Widhia Kurnia Sukmono Aims This research aims to analyze the current security vulnerabilities in cloud computing, study and identify the current preventive measure used in cloud computing as well as to determine the possible areas for improvement in terms of security and integrity ...
Security is considered a key requirement for cloud computing consolidation as a robust and feasible multi-purpose solution [].This viewpoint is shared by many distinct groups, including academia researchers [2, 3], business decision makers [] and government organizations [5, 6].The many similarities in these perspectives indicate a grave concern on crucial security and legal obstacles for ...
Cloud Computing is an emerging paradigm that is based on the concept of distributed computing. Its definition is related to the use of computer resources which are offered as a service. As with any novel technology, Cloud Computing is subject to security threats, vulnerabilities, and attacks. Recently, the studies on security impact include the interaction of software, people and services on ...
The research will examine the issue of security risk assessment methods in migrating legacy systems into Cloud, using an action research methodology. The aim of utilising this particular approach is to provide a new perception to the issue, and will investigate whether formalised security risk assessment methods can be modified for the unique ...
Cloud Security. We're working on building the most secure cloud infrastructure platforms. Our research focuses on ensuring the integrity of everything in the stack, reducing the attack surface of cloud systems, and advancing the use of confidential computing and hardware security modules.
The findings of the proposed research include the following: we present a comprehensive survey of enabling cloud-based IoT architecture, services, configurations, and security models; the ...
The use of cloud computing has become a reliable information technology solution over the past decade by providing numerous services and resources on a pay-as-you-use basis and evolving from concept to reality. Despite increasing demand and popularity, the adoption of the cloud is hindered mainly by security concerns. Successful cloud adoption and uncomplicated operation are possible if users ...
This paper provides a review of security research in the field of cloud security and storage services of the AWS cloud platform. After security and storage, we have presented the working of AWS (Amazon Web Service) cloud computing. AWS is the most trusted provider of cloud computing which not only provides excellent cloud security but also ...
Cloud computing is actually one of the most popular themes of information systems research. Considering the nature of the processed information especially health care organizations need to assess and treat specific risks according to cloud computing in their information security management system. Therefore, in this paper we propose a framework that includes the most important security ...
Thus, creating a security architecture for cloud computing, and systematically perform research on cloud security main technologies such as firewall, security measures of architecture, and cloud ...
From 2010 to 2021, we found 52 papers that were of top ranked journals and conferences. From 2010 to 2017, there is linear work in cloud computing, however, after 2017, a lot of work is done in cloud computing data security. From 2018 to 2021, 37 papers are published. After 2018, the trend about data security in cloud computing increased very ...
about. Moreover, the general cloud security proposals are given. Key words: Cloud security, Cloud threats, Cyber-attacks, Security Tools. 1. Introduction Cloud computing simplifies and adapts everything, but cloud architecture is complicated, and resolving any security or network-related issue is difficult. In brief, there are three sorts
Since cloud computing is rest on internet, security issues like privacy, data security, confidentiality, and authentication is encountered. In order to get rid of the same, a variety of encryption ...
Executive summary. CVE-2024-3094 is a vulnerability discovered in the open-source library XZ Utils that stems from malicious code that was pushed into the library by one of its maintainers. It was originally reported as an SSH authentication bypass backdoor, but further analysis indicates that the backdoor actually enables remote code execution ...
The proposed security management framework was implemented based on the ISO 27000 family of standards. The ISMS was able to identify the most frequent cloud computing threats and the information ...