An official website of the United States government
The .gov means it’s official. Federal government websites often end in .gov or .mil. Before sharing sensitive information, make sure you’re on a federal government site.
The site is secure. The https:// ensures that you are connecting to the official website and that any information you provide is encrypted and transmitted securely.
- Publications
- Account settings
Preview improvements coming to the PMC website in October 2024. Learn More or Try it out now .
- Advanced Search
- Journal List
- Front Public Health

Cyberbullying Among Adolescents and Children: A Comprehensive Review of the Global Situation, Risk Factors, and Preventive Measures
Chengyan zhu.
1 School of Political Science and Public Administration, Wuhan University, Wuhan, China
Shiqing Huang
2 School of Medicine and Health Management, Tongji Medical College, Huazhong University of Science and Technology, Wuhan, China
Richard Evans
3 College of Engineering, Design and Physical Sciences, Brunel University London, Uxbridge, United Kingdom
Associated Data
The original contributions presented in the study are included in the article/ Supplementary Material , further inquiries can be directed to the corresponding author/s.
Background: Cyberbullying is well-recognized as a severe public health issue which affects both adolescents and children. Most extant studies have focused on national and regional effects of cyberbullying, with few examining the global perspective of cyberbullying. This systematic review comprehensively examines the global situation, risk factors, and preventive measures taken worldwide to fight cyberbullying among adolescents and children.
Methods: A systematic review of available literature was completed following PRISMA guidelines using the search themes “cyberbullying” and “adolescent or children”; the time frame was from January 1st, 2015 to December 31st, 2019. Eight academic databases pertaining to public health, and communication and psychology were consulted, namely: Web of Science, Science Direct, PubMed, Google Scholar, ProQuest, Communication & Mass Media Complete, CINAHL, and PsycArticles. Additional records identified through other sources included the references of reviews and two websites, Cyberbullying Research Center and United Nations Children's Fund. A total of 63 studies out of 2070 were included in our final review focusing on cyberbullying prevalence and risk factors.
Results: The prevalence rates of cyberbullying preparation ranged from 6.0 to 46.3%, while the rates of cyberbullying victimization ranged from 13.99 to 57.5%, based on 63 references. Verbal violence was the most common type of cyberbullying. Fourteen risk factors and three protective factors were revealed in this study. At the personal level, variables associated with cyberbullying including age, gender, online behavior, race, health condition, past experience of victimization, and impulsiveness were reviewed as risk factors. Likewise, at the situational level, parent-child relationship, interpersonal relationships, and geographical location were also reviewed in relation to cyberbullying. As for protective factors, empathy and emotional intelligence, parent-child relationship, and school climate were frequently mentioned.
Conclusion: The prevalence rate of cyberbullying has increased significantly in the observed 5-year period, and it is imperative that researchers from low and middle income countries focus sufficient attention on cyberbullying of children and adolescents. Despite a lack of scientific intervention research on cyberbullying, the review also identified several promising strategies for its prevention from the perspectives of youths, parents and schools. More research on cyberbullying is needed, especially on the issue of cross-national cyberbullying. International cooperation, multi-pronged and systematic approaches are highly encouraged to deal with cyberbullying.
Introduction
Childhood and adolescence are not only periods of growth, but also of emerging risk taking. Young people during these periods are particularly vulnerable and cannot fully understand the connection between behaviors and consequences ( 1 ). With peer pressures, the heat of passion, children and adolescents usually perform worse than adults when people are required to maintain self-discipline to achieve good results in unfamiliar situations. Impulsiveness, sensation seeking, thrill seeking, and other individual differences cause adolescents to risk rejecting standardized risk interventions ( 2 ).
About one-third of Internet users in the world are children and adolescents under the age of 18 ( 3 ). Digital technology provide a new form of interpersonal communication ( 4 ). However, surveys and news reports also show another picture in the Internet Age. The dark side of young people's internet usage is that they may bully or suffer from others' bullying in cyberspace. This behavior is also acknowledged as cyberbullying ( 5 ). Based on Olweus's definition, cyberbullying is usually regarded as bullying implemented through electronic media ( 6 , 7 ). Specifically, cyberbullying among children and adolescents can be summarized as the intentional and repeated harm from one or more peers that occurs in cyberspace caused by the use of computers, smartphones and other devices ( 4 , 8 – 12 ). In recent years, new forms of cyberbullying behaviors have emerged, such as cyberstalking and online dating abuse ( 13 – 15 ).
Although cyberbullying is still a relatively new field of research, cyberbullying among adolescents is considered to be a serious public health issue that is closely related to adolescents' behavior, mental health and development ( 16 , 17 ). The increasing rate of Internet adoption worldwide and the popularity of social media platforms among the young people have worsened this situation with most children and adolescents experiencing cyberbullying or online victimization during their lives. The confines of space and time are alleviated for bullies in virtual environments, creating new venues for cyberbullying with no geographical boundaries ( 6 ). Cyberbullying exerts negative effects on many aspects of young people's lives, including personal privacy invasion and psychological disorders. The influence of cyberbullying may be worse than traditional bullying as perpetrators can act anonymously and connect easily with children and adolescents at any time ( 18 ). In comparison with traditional victims, those bullied online show greater levels of depression, anxiety and loneliness ( 19 ). Self-esteem problems and school absenteeism have also proven to be related to cyberbullying ( 20 ).
Due to changes in use and behavioral patterns among the youth on social media, the manifestations and risk factors of cyberbullying have faced significant transformation. Further, as the boundaries of cyberbullying are not limited by geography, cyberbullying may not be a problem contained within a single country. In this sense, cyberbullying is a global problem and tackling it requires greater international collaboration. The adverse effects caused by cyberbullying, including reduced safety, lower educational attainment, poorer mental health and greater unhappiness, led UNICEF to state that “no child is absolutely safe in the digital world” ( 3 ).
Extant research has examined the prevalence and risk factors of cyberbullying to unravel the complexity of cyberbullying across different countries and their corresponding causes. However, due to variations in cyberbullying measurement and methodologies, no consistent conclusions have been drawn ( 21 ). Studies into inconsistencies in prevalence rates of cyberbullying, measured in the same country during the same time period, occur frequently. Selkie et al. systematically reviewed cyberbullying among American middle and high school students aged 10–19 years old in 2015, and revealed that the prevalence of cyberbullying victimization ranged from 3 to 72%, while perpetration ranged from 1 to 41% ( 22 ). Risk and protective factors have also been broadly studied, but confirmation is still needed of those factors which have more significant effects on cyberbullying among young people. Clarification of these issues would be useful to allow further research to recognize cyberbullying more accurately.
This review aims to extend prior contributions and provide a comprehensive review of cyberbullying of children and adolescents from a global perspective, with the focus being on prevalence, associated risk factors and protective factors across countries. It is necessary to provide a global panorama based on research syntheses to fill the gaps in knowledge on this topic.
Search Strategies
This study strictly employed Preferred Reporting Items for Systematic Reviews and Meta-Analyses (PRISMA) guidelines. We consulted eight academic databases pertaining to public health, and communication and psychology, namely: Web of Science, Science Direct, PubMed, Google Scholar, ProQuest, Communication & Mass Media Complete, CINAHL, and PsycArticles. Additional records identified through other sources included the references of reviews and two websites, Cyberbullying Research Center and United Nations Children's Fund. With regard to the duration of our review, since most studies on cyberbullying arose around 2015 ( 9 , 21 ), this study highlights the complementary aspects of the available information about cyberbullying during the recent 5 year period from January 1st, 2015 to December 31st, 2019.
One researcher extracted keywords and two researchers proposed modifications. We used two sets of subject terms to review articles, “cyberbullying” and “child OR adolescent.” Some keywords that refer to cyberbullying behaviors and young people are also included, such as threat, harass, intimidate, abuse, insult, humiliate, condemn, isolate, embarrass, forgery, slander, flame, stalk, manhunt, as well as teen, youth, young people and student. The search formula is (cyberbullying OR cyber-bullying OR cyber-aggression OR ((cyber OR online OR electronic OR Internet) AND (bully * OR aggres * OR violence OR perpetrat * OR victim * OR threat * OR harass * OR intimidat * OR * OR insult * OR humiliate * OR condemn * OR isolate * OR embarrass * OR forgery OR slander * OR flame OR stalk * OR manhunt))) AND (adolescen * OR child OR children OR teen? OR teenager? OR youth? OR “young people” OR “elementary school student * ” OR “middle school student * ” OR “high school student * ”). The main search approach is title search. Search strategies varied according to the database consulted, and we did not limit the type of literature for inclusion. Journals, conference papers and dissertations are all available.
Specifically, the inclusion criteria for our study were as follows: (a). reported or evaluated the prevalence and possible risk factors associated with cyberbullying, (b). respondents were students under the age of 18 or in primary, junior or senior high schools, and (c). studies were written in English. Exclusion criteria were: (a). respondents came from specific groups, such as clinical samples, children with disabilities, sexual minorities, specific ethnic groups, specific faith groups or samples with cross-national background, (b). review studies, qualitative studies, conceptual studies, book reviews, news reports or abstracts of meetings, and (c). studies focused solely on preventive measures that were usually meta-analytic and qualitative in nature. Figure 1 presents the details of the employed screening process, showing that a total of 63 studies out of 2070 were included in our final review.

PRISMA flow chart diagram showing the process of study selection for inclusion in the systematic review on children and adolescents cyberbullying.
Meta-analysis was not conducted as the limited research published within the 5 years revealed little research which reported odds ratio. On the other hand, due to the inconsistency of concepts, measuring instruments and recall periods, considerable variation could be found in research quality ( 23 ). Meta-analysis is not a preferred method.
Coding Scheme
For coding, we created a comprehensive code scheme to include the characteristics. For cyberbullying, we coded five types proposed by Willard ( 24 – 26 ), which included verbal violence, group violence, visual violence, impersonating and account forgery, and other behaviors. Among them, verbal violence is considered one of the most common types of cyberbullying and refers to the behavior of offensive responses, insults, mocking, threats, slander, and harassment. Group violence is associated with preventing others from joining certain groups or isolating others, forcing others to leave the group. Visual violence relates to the release and sharing of embarrassing photos and information without the owners' consent. Impersonating and account forgery refers to identity theft, stealing passwords, violating accounts and the creation of fake accounts to fraudulently present the behavior of others. Other behaviors include disclosure of privacy, sexual harassment, and cyberstalking. To comprehensively examine cyberbullying, we coded cyberbullying behaviors from both the perspectives of cyberbullying perpetrators and victims, if mentioned in the studies.
In relation to risk factors, we drew insights from the general aggression model, which contributes to the understanding of personal and situational factors in the cyberbullying of children and adolescents. We chose the general aggression model because (a) it contains more situational factors than other models (e.g., social ecological models) - such as school climate ( 9 ), and (b) we believe that the general aggression model is more suitable for helping researchers conduct a systematic review of cyberbullying risk and protective factors. This model provides a comprehensive framework that integrates domain specific theories of aggression, and has been widely applied in cyberbullying research ( 27 ). For instance, Kowalski and colleagues proposed a cyberbullying encounter through the general aggression model to understand the formation and development process of youth cyberbullying related to both victimization and perpetration ( 9 ). Victims and perpetrators enter the cyberbullying encounter with various individual characteristics, experiences, attitudes, desires, personalities, and motives that intersect to determine the course of the interaction. Correspondingly, the antecedents pertaining to cyberbullying are divided into two broad categories, personal factors and situational factors. Personal factors refer to individual characteristics, such as gender, age, motivation, personality, psychological states, socioeconomic status and technology use, values and perceptions, and other maladaptive behaviors. Situational factors focus on the provocation/support, parental involvement, school climate, and perceived anonymity. Consequently, our coders related to risk factors consisting of personal factors and situational factors from the perspectives of both cyberbullying perpetrators and victims.
We extracted information relating to individual papers and sample characteristics, including authors, year of publication, country, article type, sampling procedures, sample characteristics, measures of cyberbullying, and prevalence and risk factors from both cyberbullying perpetration and victimization perspectives. The key words extraction and coding work were performed twice by two trained research assistants in health informatics. The consistency test results are as follows: the Kappa value with “personal factors” was 0.932, and the Kappa value with “situational factors” was 0.807. The result shows that the coding consistency was high enough and acceptable. Disagreements were resolved through discussion with other authors.
Quality Assessment of Studies
The quality assessment of the studies is based on the recommended tool for assessing risk of bias, Cochrane Collaboration. This quality assessment tool focused on seven items: random sequence generation, allocation concealment, blinding of participants and personnel, blinding of outcome assessment, incomplete outcome data, selective reporting, and other sources of bias ( 28 ). We assessed each item as “low risk,” “high risk,” and “unclear” for included studies. A study is considered of “high quality” when it meets three or more “low risk” requirements. When one or more main flaw of a study may affect the research results, the study is considered as “low quality.” When a lack of information leads to a difficult judgement, the quality is considered to be “unclear.” Please refer to Appendix 1 for more details.
This comprehensive systematic review comprised a total of 63 studies. Appendices 2 , 3 show the descriptive information of the studies included. Among them, 58 (92%) studies measured two or more cyberbullying behavior types. The sample sizes of the youths range from several hundred to tens of thousands, with one thousand to five thousand being the most common. As for study distribution, the United States of America, Spain and China were most frequently mentioned. Table 1 presents the detail.
Descriptive information of studies included (2015–2019).
Prevalence of Global Cyberbullying
Prevalence across countries.
Among the 63 studies included, 22 studies reported on cyberbullying prevalence and 20 studies reported on prevalence from victimization and perpetration perspectives, respectively. Among the 20 studies, 11 national studies indicated that the prevalence of cyberbullying victimization and cyberbullying perpetration ranged from 14.6 to 52.2% and 6.3 to 32%, respectively. These studies were conducted in the United States of America ( N = 4) ( 29 – 32 ), South Korea ( N = 3) ( 33 – 35 ), Singapore ( N = 1) ( 36 ), Malaysia ( N = 1) ( 37 ), Israel ( N = 1) ( 38 ), and Canada ( N = 1) ( 39 ). Only one of these 11 national studies is from an upper middle income country, and the rest are from highincome countries identified by the World Bank ( 40 ). By combining regional and community-level studies, the prevalence of cyberbullying victimization and cyberbullying perpetration ranged from 13.99 to 57.5% and 6.0 to 46.3%, respectively. Spain reported the highest prevalence of cyberbullying victimization (57.5%) ( 41 ), followed by Malaysia (52.2%) ( 37 ), Israel (45%) ( 42 ), and China (44.5%) ( 43 ). The lowest reported victim rates were observed in Canada (13.99%) and South Korea (14.6%) ( 34 , 39 ). The reported prevalence of cyberbullying victimization in the United States of America ranged from 15.5 to 31.4% ( 29 , 44 ), while in Israel, rates ranged from 30 to 45% ( 26 , 42 ). In China, rates ranged from 6 to 46.3% with the country showing the highest prevalence of cyberbullying perpetration (46.30%) ( 15 , 43 , 45 , 46 ). Canadian and South Korean studies reported the lowest prevalence of cyberbullying perpetration at 7.99 and 6.3%, respectively ( 34 , 39 ).
A total of 10 studies were assessed as high quality studies. Among them, six studies came from high income countries, including Canada, Germany, Italy, Portugal, and South Korea ( 13 , 34 , 39 , 46 – 48 ). Three studies were from upper middle income countries, including Malaysia and China ( 37 , 43 ) and one from a lower middle income country, Nigeria ( 49 ). Figures 2 , ,3 3 describe the prevalence of cyberbullying victimization and perpetration respectively among high quality studies.

The prevalence of cyberbullying victimization of high quality studies.

The prevalence of cyberbullying perpetration of high quality studies.
Prevalence of Various Cyberbullying Behaviors
For the prevalence of cyberbullying victimization and perpetration, the data were reported in 18 and 14 studies, respectively. Figure 4 shows the distribution characteristics of the estimated value of prevalence of different cyberbullying behaviors with box plots. The longer the box, the greater the degree of variation of the numerical data and vice versa. The rate of victimization and crime of verbal violence, as well as the rate of victimization of other behaviors, such as cyberstalking and digital dating abuse, has a large degree of variation. Among the four specified types of cyberbullying behaviors, verbal violence was regarded as the most commonly reported behaviors in both perpetration and victimization rates, with a wide range of prevalence, ranging from 5 to 18%. Fewer studies reported the prevalence data for visual violence and group violence. Studies also showed that the prevalence of impersonation and account forgery were within a comparatively small scale. Specific results were as follows.

Cyberbullying prevalence across types (2015–2019).
Verbal Violence
A total of 13 studies reported verbal violence prevalence data ( 15 , 26 , 34 , 37 – 39 , 42 , 43 , 47 , 48 , 50 , 51 ). Ten studies reported the prevalence of verbal violence victimization ranging from 2.8 to 47.5%, while seven studies claimed perpetration prevalence ranging from 1.5 to 31.8%. Malaysia reported the highest prevalence of verbal violence victimization (47.5%) ( 37 ), followed by China (32%) ( 43 ). China reported that the prevalence of verbal violence victimization ranged from 5.1 to 32% ( 15 , 43 ). Israel reported that the prevalence of verbal violence victimization ranged from 3.4 to 18% ( 26 , 38 , 42 ). For perpetration rate, Malaysia reported the highest level at 31.8% ( 37 ), while a study for Spain reported the lowest, ranging from 3.2 to 6.4% ( 51 ).
Group Violence
The prevalence of group violence victimization was explored within 4 studies and ranged from 5 to 17.8% ( 26 , 34 , 42 , 43 ), while perpetration prevalence was reported in three studies, ranging from 10.1 to 19.07% ( 34 , 43 , 47 ). An Israeli study suggested that 9.8% of respondents had been excluded from the Internet, while 8.9% had been refused entry to a group or team ( 26 ). A study in South Korea argued that the perpetration prevalence of group violence was 10.1% ( 34 ), while a study in Italy reported that the rate of online group violence against others was 19.07% ( 47 ).
Visual Violence
The prevalence of visual violence victimization was explored within three studies and ranged from 2.6 to 12.1% ( 26 , 34 , 43 ), while the perpetration prevalence reported in four studies ranged from 1.7 to 6% ( 34 , 43 , 47 , 48 ). For victimization prevalence, a South Korean study found that 12.1% of respondents reported that their personal information was leaked online ( 34 ). An Israel study reported that the prevalence of outing the picture was 2.6% ( 26 ). For perpetration prevalence, a South Korean study found that 1.7% of respondents had reported that they had disclosed someone's personal information online ( 34 ). A German study reported that 6% of respondents had written a message (e.g., an email) to somebody using a fake identity ( 48 ).
Impersonating and Account Forgery
Four studies reported on the victimization prevalence of impersonating and account forgery, ranging from 1.1 to 10% ( 15 , 42 , 43 ), while five studies reported on perpetration prevalence, with the range being from 1.3 to 9.31% ( 15 , 43 , 47 , 48 , 51 ). In a Spanish study, 10% of respondents reported that their accounts had been infringed by others or that they could not access their account due to stolen passwords. In contrast, 4.5% of respondents reported that they had infringed other people's accounts or stolen passwords, with 2.5% stating that they had forged other people's accounts ( 51 ). An Israeli study reported that the prevalence of being impersonated was 7% ( 42 ), while in China, a study reported this to be 8.6% ( 43 ). Another study from China found that 1.1% of respondents had been impersonated to send dating-for-money messages ( 15 ).
Other Behaviors
The prevalence of disclosure of privacy, sexual harassment, and cyberstalking were also explored by scholars. Six studies reported the victimization prevalence of other cyberbullying behaviors ( 13 , 15 , 34 , 37 , 42 , 43 ), and four studies reported on perpetration prevalence ( 34 , 37 , 43 , 48 ). A study in China found that 1.2% of respondents reported that their privacy had been compromised without permission due to disputes ( 15 ). A study from China reported the prevalence of cyberstalking victimization was 11.9% ( 43 ), while a Portuguese study reported that this was 62% ( 13 ). In terms of perpetration prevalence, a Malaysian study reported 2.7% for sexual harassment ( 37 ).
Risk and Protective Factors of Cyberbullying
In terms of the risk factors associated with cyberbullying among children and adolescents, this comprehensive review highlighted both personal and situational factors. Personal factors referred to age, gender, online behavior, race, health conditions, past experiences of victimization, and impulsiveness, while situational factors consisted of parent-child relationship, interpersonal relationships, and geographical location. In addition, protective factors against cyberbullying included: empathy and emotional intelligence, parent-child relationship, and school climate. Table 2 shows the risk and protective factors for child and adolescent cyberbullying.
Risk and protective factors of cyberbullying among children and adolescents.
In terms of the risk factors associated with cyberbullying victimization at the personal level, many studies evidenced that females were more likely to be cyberbullied than males ( 13 , 26 , 29 , 38 , 43 , 52 , 54 , 55 , 58 ). Meanwhile, adolescents with mental health problems ( 61 ), such as depression ( 33 , 62 ), borderline personality disorder ( 63 ), eating disorders ( 41 ), sleep deprivation ( 56 ), and suicidal thoughts and suicide plans ( 64 ), were more likely to be associated with cyberbullying victimization. As for Internet usage, researchers agreed that youth victims were probably those that spent more time online than their counterparts ( 32 , 36 , 43 , 45 , 48 , 49 , 60 ). For situational risk factors, some studies have proven the relationship between cyberbullying victims and parental abuse, parental neglect, family dysfunction, inadequate monitoring, and parents' inconsistency in mediation, as well as communication issues ( 33 , 64 , 68 , 73 ). In terms of geographical location, some studies have reported that youths residing in city locations are more likely to be victims of cyberbullying than their peers from suburban areas ( 61 ).
Regarding the risk factors of cyberbullying perpetration at the personal level, it is generally believed that older teenagers, especially those aged over 15 years, are at greater risk of becoming cyberbullying perpetrators ( 55 , 67 ). When considering prior cyberbullying experiences, evidence showed that individuals who had experienced cyberbullying or face-to-face bullying tended to be aggressors in cyberbullying ( 35 , 42 , 49 , 51 , 55 ); in addition, the relationship between impulsiveness and cyberbullying perpetration was also explored by several pioneering scholars ( 55 , 72 , 80 ). The situational factors highlight the role of parents and teachers in cyberbullying experiences. For example, over-control and authoritarian parenting styles, as well as inharmonious teacher-student relationships ( 61 ) are perceived to lead to cyberbullying behaviors ( 74 , 75 ). In terms of differences in geographical locations, students residing in cities have a higher rate of online harassment than students living in more rural locations ( 49 ).
In terms of the protective factors in child and adolescent cyberbullying, scholars have focused on youths who have limited experiences of cyberbullying. At the personal level, high emotional intelligence, an ability for emotional self-control and empathy, such as cognitive empathy ability ( 44 , 55 ), were associated with lower rates of cyberbullying ( 57 ). At the situational level, a parent's role is seen as critical. For example, intimate parent-child relationships ( 46 ) and open active communication ( 19 ) were demonstrated to be related to lower experiences of cyberbullying and perpetration. Some scholars argued that parental supervision and monitoring of children's online activities can reduce their tendency to participate in some negative activities associated with cyberbullying ( 31 , 46 , 73 ). They further claimed that an authoritative parental style protects youths against cyberbullying ( 43 ). Conversely, another string of studies evidenced that parents' supervision of Internet usage was meaningless ( 45 ). In addition to conflicting roles of parental supervision, researchers have also looked into the role of schools, and posited that positive school climates contribute to less cyberbullying experiences ( 61 , 79 ).
Some risk factors may be protective factors under another condition. Some studies suggest that parental aggressive communication is related to severe cyberbullying victims, while open communication is a potential protective factor ( 19 ). Parental neglect, parental abuse, parental inconsistency in supervision of adolescents' online behavior, and family dysfunction are related to the direct or indirect harm of cyberbullying ( 33 , 68 ). Parental participation, a good parental-children relationship, communication and dialogue can enhance children's school adaptability and prevent cyberbullying behaviors ( 31 , 74 ). When parental monitoring reaches a balance between control and openness, it could become a protective factor against cyberbullying, and it could be a risk factor, if parental monitoring is too low or over-controlled ( 47 ).
Despite frequent discussion about the risk factors associated with cyberbullying among children and adolescents, some are still deemed controversial factors, such as age, race, gender, and the frequency of suffering on the internet. For cyberbullying victims, some studies claim that older teenagers are more vulnerable to cyberbullying ( 15 , 38 , 52 , 53 ), while other studies found conflicting results ( 26 , 33 ). As for student race, Alhajji et al. argued that non-white students were less likely to report cyberbullying ( 29 ), while Morin et al. observed no significant correlation between race and cyberbullying ( 52 ). For cyberbullying perpetration, Alvarez-Garcia found that gender differences may have indirect effects on cyberbullying perpetration ( 55 ), while others disagreed ( 42 , 61 , 68 – 70 ). Specifically, some studies revealed that males were more likely to become cyberbullying perpetrators ( 34 , 39 , 56 ), while Khurana et al. presented an opposite point of view, proposing that females were more likely to attack others ( 71 ). In terms of time spent on the Internet, some claimed that students who frequently surf the Internet had a higher chance of becoming perpetrators ( 49 ), while others stated that there was no clear and direct association between Internet usage and cyberbullying perpetration ( 55 ).
In addition to personal and situational factors, scholars have also explored other specific factors pertaining to cyberbullying risk and protection. For instance, mindfulness and depression were found to be significantly related to cyber perpetration ( 76 ), while eating disorder psychopathology in adolescents was associated with cyber victimization ( 41 ). For males who were familiar with their victims, such as family members, friends and acquaintances, they were more likely to be cyberstalking perpetrators than females or strangers, while pursuing desired closer relationships ( 13 ). In the school context, a lower social likability in class was identified as an indirect factor for cyberbullying ( 48 ).
This comprehensive review has established that the prevalence of global childhood and adolescent victimization from cyberbullying ranges from 13.99 to 57.5%, and that the perpetration prevalence ranges from 6.0 to 46.3%. Across the studies included in our research, verbal violence is observed as one of the most common acts of cyberbullying, including verbal offensive responses, insults, mocking, threats, slander, and harassment. The victimization prevalence of verbal violence is reported to be between 5 and 47.5%, and the perpetration prevalence is between 3.2 and 26.1%. Personal factors, such as gender, frequent use of social media platforms, depression, borderline personality disorder, eating disorders, sleep deprivation, and suicidal tendencies, were generally considered to be related to becoming a cyberbullying victim. Personal factors, such as high school students, past experiences, impulse, improperly controlled family education, poor teacher-student relationships, and the urban environment, were considered risk factors for cyberbullying perpetration. Situational factors, including parental abuse and neglect, improper monitoring, communication barriers between parents and children, as well as the urban environment, were also seen to potentially contribute to higher risks of both cyberbullying victimization and perpetration.
Increasing Prevalence of Global Cyberbullying With Changing Social Media Landscape and Measurement Alterations
This comprehensive review suggests that global cyberbullying rates, in terms of victimization and perpetration, were on the rise during the 5 year period, from 2015 to 2019. For example, in an earlier study conducted by Modecki et al. the average cyberbullying involvement rate was 15% ( 81 ). Similar observations were made by Hamm et al. who found that the median rates of youth having experienced bullying or who had bullied others online, was 23 and 15.2%, respectively ( 82 ). However, our systematic review summarized global children and adolescents cyberbullying in the last 5 years and revealed an average cyberbullying perpetration rate of 25.03%, ranging from 6.0 to 46.3%, while the average victimization was 33.08%, ranging from 13.99 to 57.5%. The underlying reason for increases may be attributed to the rapid changing landscape of social media and, in recent years, the drastic increase in Internet penetration rates. With the rise in Internet access, youths have greater opportunities to participate in online activities, provided by emerging social media platforms.
Although our review aims to provide a broader picture of cyberbullying, it is well-noted in extant research that difficulties exist in accurately estimating variations in prevalence in different countries ( 23 , 83 ). Many reasons exist to explain this. The first largely relates poor or unclear definition of the term cyberbullying; this hinders the determination of cyberbullying victimization and perpetration ( 84 ). Although traditional bullying behavior is well-defined, the definition cannot directly be applied to the virtual environment due to the complexity in changing online interactions. Without consensus on definitions, measurement and cyberbullying types may vary noticeably ( 83 , 85 ). Secondly, the estimation of prevalence of cyberbullying is heavily affected by research methods, such as recall period (lifetime, last year, last 6 months, last month, or last week etc.), demographic characteristics of the survey sample (age, gender, race, etc.), perspectives of cyberbullying experiences (victims, perpetrators, or both victim and perpetrator), and instruments (scales, study-specific questions) ( 23 , 84 , 86 ). The variety in research tools and instruments used to assess the prevalence of cyberbullying can cause confusion on this issue ( 84 ). Thirdly, variations in economic development, cultural backgrounds, human values, internet penetration rates, and frequency of using social media may lead to different conclusions across countries ( 87 ).
Acknowledging the Conflicting Role of the Identified Risk Factors With More Research Needed to Establish the Causality
Although this review has identified many personal and situational factors associated with cyberbullying, the majority of studies adopted a cross-sectional design and failed to reveal the causality ( 21 ). Nevertheless, knowledge on these correlational relationships provide valuable insights for understanding and preventing cyberbullying incidents. In terms of gender differences, females are believed to be at a higher risk of cyberbullying victimization compared to males. Two reasons may help to explain this. First, the preferred violence behaviors between two genders. females prefer indirect harassment, such as the spreading of rumors, while males tend toward direct bullying (e.g., assault) ( 29 ) and second, the cultural factors. From the traditional gender perspective, females tended to perceive a greater risk of communicating with others on the Internet, while males were more reluctant to express fear, vulnerability and insecurity when asked about their cyberbullying experiences ( 46 ). Females were more intolerant when experiencing cyberstalking and were more likely to report victimization experiences than males ( 13 ). Meanwhile, many researchers suggested that females are frequent users of emerging digital communication platforms, which increases their risk of unpleasant interpersonal contact and violence. From the perspective of cultural norms and masculinity, the reporting of cyberbullying is also widely acknowledged ( 37 ). For example, in addition, engaging in online activities is also regarded as a critical predictor for cyberbullying victimization. Enabled by the Internet, youths can easily find potential victims and start harassment at any time ( 49 ). Participating in online activities directly increases the chance of experiencing cyberbullying victimization and the possibility of becoming a victim ( 36 , 45 ). As for age, earlier involvement on social media and instant messaging tools may increase the chances of experiencing cyberbullying. For example, in Spain, these tools cannot be used without parental permission before the age of 14 ( 55 ). Besides, senior students were more likely to be more impulsive and less sympathetic. They may portray more aggressive and anti-social behaviors ( 55 , 72 ); hence senior students and students with higher impulsivity were usually more likely to become cyberbullying perpetrators.
Past experiences of victimization and family-related factors are another risk for cyberbullying crime. As for past experiences, one possible explanation is that young people who had experienced online or traditional school bullying may commit cyberbullying using e-mails, instant messages, and text messages for revenge, self-protection, or improving their social status ( 35 , 42 , 49 , 55 ). In becoming a cyberbullying perpetrator, the student may feel more powerful and superior, externalizing angry feelings and relieving the feelings of helplessness and sadness produced by past victimization experiences ( 51 ). As for family related factors, parenting styles are proven to be highly correlated to cyberbullying. In authoritative families, parents focus on rational behavioral control with clear rules and a high component of supervision and parental warmth, which have beneficial effects on children's lifestyles ( 43 ). Conversely, in indulgent families, children's behaviors are not heavily restricted and parents guide and encourage their children to adapt to society. The characteristics of this indulgent style, including parental support, positive communication, low imposition, and emotional expressiveness, possibly contribute to more parent-child trust and less misunderstanding ( 75 ). The protective role of warmth/affection and appropriate supervision, which are common features of authoritative or indulgent parenting styles, mitigate youth engagement in cyberbullying. On the contrary, authoritarian and neglectful styles, whether with excessive or insufficient control, are both proven to be risk factors for being a target of cyberbullying ( 33 , 76 ). In terms of geographical location, although several studies found that children residing in urban areas were more likely to be cyberbullying victims than those living in rural or suburban areas, we cannot draw a quick conclusion here, since whether this difference attributes to macro-level differences, such as community safety or socioeconomic status, or micro-level differences, such as teacher intervention in the classroom, courses provided, teacher-student ratio, is unclear across studies ( 61 ). An alternative explanation for this is the higher internet usage rate in urban areas ( 49 ).
Regarding health conditions, especially mental health, some scholars believe that young people with health problems are more likely to be identified as victims than people without health problems. They perceive health condition as a risk factor for cyberbullying ( 61 , 63 ). On the other hand, another group of scholars believe that cyberbullying has an important impact on the mental health of adolescents which can cause psychological distress consequences, such as post-traumatic stress mental disorder, depression, suicidal ideation, and drug abuse ( 70 , 87 ). It is highly possible that mental health could be risk factors, consequences of cyberbullying or both. Mental health cannot be used as standards, requirements, or decisive responses in cyberbullying research ( 13 ).
The Joint Effort Between Youth, Parents, Schools, and Communities to Form a Cyberbullying-Free Environment
This comprehensive review suggests that protecting children and adolescents from cyberbullying requires joint efforts between individuals, parents, schools, and communities, to form a cyberbullying-free environment. For individuals, young people are expected to improve their digital technology capabilities, especially in the use of social media platforms and instant messaging tools ( 55 ). To reduce the number of cyberbullying perpetrators, it is necessary to cultivate emotional self-regulation ability through appropriate emotional management training. Moreover, teachers, counselors, and parents are required to be armed with sufficient knowledge of emotional management and to develop emotional management capabilities and skills. In this way, they can be alert to the aggressive or angry emotions expressed by young people, and help them mediate any negative emotions ( 45 ), and avoid further anti-social behaviors ( 57 ).
For parents, styles of parenting involving a high level of parental involvement, care and support, are desirable in reducing the possibility of children's engagement in cyberbullying ( 74 , 75 ). If difficulties are encountered, open communication can contribute to enhancing the sense of security ( 73 ). In this vein, parents should be aware of the importance of caring, communicating and supervising their children, and participate actively in their children's lives ( 71 ). In order to keep a balance between control and openness ( 47 ), parents can engage in unbiased open communication with their children, and reach an agreement on the usage of computers and smart phones ( 34 , 35 , 55 ). Similarly, it is of vital importance to establish a positive communication channel with children ( 19 ).
For schools, a higher priority is needed to create a safe and positive campus environment, providing students with learning opportunities and ensuring that every student is treated equally. With a youth-friendly environment, students are able to focus more on their academic performance and develop a strong sense of belonging to the school ( 79 ). For countries recognizing collectivist cultural values, such as China and India, emphasizing peer attachment and a sense of collectivism can reduce the risk of cyberbullying perpetration and victimization ( 78 ). Besides, schools can cooperate with mental health agencies and neighboring communities to develop preventive programs, such as extracurricular activities and training ( 44 , 53 , 62 ). Specifically, school-based preventive measures against cyberbullying are expected to be sensitive to the characteristics of young people at different ages, and the intersection of race and school diversity ( 29 , 76 ). It is recommended that school policies that aim to embrace diversity and embody mutual respect among students are created ( 26 ). Considering the high prevalence of cyberbullying and a series of serious consequences, it is suggested that intervention against cyberbullying starts from an early stage, at about 10 years old ( 54 ). Schools can organize seminars to strengthen communication between teachers and students so that they can better understand the needs of students ( 61 ). In addition, schools should encourage cyberbullying victims to seek help and provide students with opportunities to report cyberbullying behaviors, such as creating online anonymous calls.
Conclusions and Limitations
The comprehensive study has reviewed related research on children and adolescents cyberbullying across different countries and regions, providing a positive understanding of the current situation of cyberbullying. The number of studies on cyberbullying has surged in the last 5 years, especially those related to risk factors and protective factors of cyberbullying. However, research on effective prevention is insufficient and evaluation of policy tools for cyberbullying intervention is a nascent research field. Our comprehensive review concludes with possible strategies for cyberbullying prevention, including personal emotion management, digital ability training, policy applicability, and interpersonal skills. We highlight the important role of parental control in cyberbullying prevention. As for the role of parental control, it depends on whether children believe their parents are capable of adequately supporting them, rather than simply interfering in their lives, restricting their online behavior, and controlling or removing their devices ( 50 ). In general, cyberbullying is on the rise, with the effectiveness of interventions to meet this problem still requiring further development and exploration ( 83 ).
Considering the overlaps between cyberbullying and traditional offline bullying, future research can explore the unique risk and protective factors that are distinguishable from traditional bullying ( 86 ). To further reveal the variations, researchers can compare the outcomes of interventions conducted in cyberbullying and traditional bullying preventions simultaneously, and the same interventions only targeting cyberbullying ( 88 ). In addition, cyberbullying also reflects a series of other social issues, such as personal privacy and security, public opinion monitoring, multinational perpetration and group crimes. To address this problem, efforts from multiple disciplines and novel analytical methods in the digital era are required. As the Internet provides enormous opportunities to connect young people from all over the world, cyberbullying perpetrators may come from transnational networks. Hence, cyberbullying of children and adolescents, involving multiple countries, is worth further attention.
Our study has several limitations. First, national representative studies are scarce, while few studies from middle and low income countries were included in our research due to language restrictions. Many of the studies included were conducted in schools, communities, provinces, and cities in high income countries. Meanwhile, our review only focused on victimization and perpetration. Future studies should consider more perspectives, such as bystanders and those with the dual identity of victim/perpetrator, to comprehensively analyze the risk and protective factors of cyberbullying.
Data Availability Statement
Author contributions.
SH, CZ, RE, and WZ conceived the study and developed the design. WZ analyzed the result and supervised the study. CZ and SH wrote the first draft. All authors contributed to the article and approved the submitted version.
Conflict of Interest
The authors declare that the research was conducted in the absence of any commercial or financial relationships that could be construed as a potential conflict of interest.
Supplementary Material
The Supplementary Material for this article can be found online at: https://www.frontiersin.org/articles/10.3389/fpubh.2021.634909/full#supplementary-material
Qualitative Methods in School Bullying and Cyberbullying Research: An Introduction to the Special Issue
- Published: 12 August 2022
- Volume 4 , pages 175–179, ( 2022 )
Cite this article

- Paul Horton 1 &
- Selma Therese Lyng 2
9700 Accesses
12 Altmetric
Explore all metrics
Avoid common mistakes on your manuscript.
Introduction
School bullying research has a long history, stretching all the way back to a questionnaire study undertaken in the USA in the late 1800s (Burk, 1897 ). However, systematic school bullying research began in earnest in Scandinavia in the early 1970s with the work of Heinemann ( 1972 ) and Olweus ( 1978 ). Highlighting the extent to which research on bullying has grown exponentially since then, Smith et al. ( 2021 ) found that there were only 83 articles with the term “bully” in the title or abstract published in the Web of Science database prior to 1989. The numbers of articles found in the following decades were 458 (1990–1999), 1,996 (2000–2009), and 9,333 (2010–2019). Considering cyberbullying more specifically, Smith and Berkkun ( 2017 , cited in Smith et al., 2021 ) conducted a search of Web of Science with the terms “cyber* and bully*; cyber and victim*; electronic bullying; Internet bullying; and online harassment” until the year 2015 and found that while there were no articles published prior to 2000, 538 articles were published between 2000 and 2015, with the number of articles increasing every year (p. 49).
Numerous authors have pointed out that research into school bullying and cyberbullying has predominantly been conducted using quantitative methods, with much less use of qualitative or mixed methods (Hong & Espelage, 2012 ; Hutson, 2018 ; Maran & Begotti, 2021 ; Smith et al., 2021 ). In their recent analysis of articles published between 1976 and 2019 (in WoS, with the search terms “bully*; victim*; cyberbullying; electronic bullying; internet bullying; and online harassment”), Smith et al. ( 2021 , pp. 50–51) found that of the empirical articles selected, more than three-quarters (76.3%) were based on quantitative data, 15.4% were based on a combination of quantitative and qualitative data, and less than one-tenth (8.4%) were based on qualitative data alone. What is more, they found that the proportion of articles based on qualitative or mixed methods has been decreasing over the past 15 years (Smith et al., 2021 ). While the search criteria excluded certain types of qualitative studies (e.g., those published in books, doctoral theses, and non-English languages), this nonetheless highlights the extent to which qualitative research findings risk being overlooked in the vast sea of quantitative research.
School bullying and cyberbullying are complex phenomena, and a range of methodological approaches is thus needed to understand their complexity (Pellegrini & Bartini, 2000 ; Thornberg, 2011 ). Indeed, over-relying on quantitative methods limits understanding of the contexts and experiences of bullying (Hong & Espelage, 2012 ; Patton et al., 2017 ). Qualitative methods are particularly useful for better understanding the social contexts, processes, interactions, experiences, motivations, and perspectives of those involved (Hutson, 2018 ; Patton et al., 2017 ; Thornberg, 2011 ; Torrance, 2000 ).
Smith et al. ( 2021 ) suggest that the “continued emphasis on quantitative studies may be due to increasingly sophisticated methods such as structural equation modeling … network analysis … time trend analyses … latent profile analyses … and multi-polygenic score approaches” (p. 56). However, the authors make no mention of the range or sophistication of methods used in qualitative studies. Although there are still proportionately few qualitative studies of school bullying and cyberbullying in relation to quantitative studies, and this gap appears to be increasing, qualitative studies have utilized a range of qualitative data collection methods. These methods have included but are not limited to ethnographic fieldwork and participant observations (e.g., Eriksen & Lyng, 2018 ; Gumpel et al., 2014 ; Horton, 2019 ), digital ethnography (e.g., Rachoene & Oyedemi, 2015 ; Sylwander, 2019 ), meta-ethnography (e.g., Dennehy et al., 2020 ; Moretti & Herkovits, 2021 ), focus group interviews (e.g., Odenbring, 2022 ; Oliver & Candappa, 2007 ; Ybarra et al., 2019 ), semi-structured group and individual interviews (e.g., Forsberg & Thornberg, 2016 ; Lyng, 2018 ; Mishna et al., 2005 ; Varjas et al., 2013 ), vignettes (e.g., Jennifer & Cowie, 2012 ; Khanolainen & Semenova, 2020 ; Strindberg et al., 2020 ), memory work (e.g., Johnson et al., 2014 ; Malaby, 2009 ), literature studies (e.g., Lopez-Ropero, 2012 ; Wiseman et al., 2019 ), photo elicitation (e.g., Ganbaatar et al., 2021 ; Newman et al., 2006 ; Walton & Niblett, 2013 ), photostory method (e.g., Skrzypiec et al., 2015 ), and other visual works produced by children and young people (e.g., Bosacki et al., 2006 ; Gillies-Rezo & Bosacki, 2003 ).
This body of research has also included a variety of qualitative data analysis methods, such as grounded theory (e.g., Allen, 2015 ; Bjereld, 2018 ; Thornberg, 2018 ), thematic analysis (e.g., Cunningham et al., 2016 ; Forsberg & Horton, 2022 ), content analysis (e.g., Temko, 2019 ; Wiseman & Jones, 2018 ), conversation analysis (e.g., Evaldsson & Svahn, 2012 ; Tholander, 2019 ), narrative analysis (e.g., Haines-Saah et al., 2018 ), interpretative phenomenological analysis (e.g., Hutchinson, 2012 ; Tholander et al., 2020 ), various forms of discourse analysis (e.g., Ellwood & Davies, 2010 ; Hepburn, 1997 ; Ringrose & Renold, 2010 ), including discursive psychological analysis (e.g., Clarke et al., 2004 ), and critical discourse analysis (e.g., Barrett & Bound, 2015 ; Bethune & Gonick, 2017 ; Horton, 2021 ), as well as theoretically informed analyses from an array of research traditions (e.g., Davies, 2011 ; Jacobson, 2010 ; Søndergaard, 2012 ; Walton, 2005 ).
In light of the growing volume and variety of qualitative studies during the past two decades, we invited researchers to discuss and explore methodological issues related to their qualitative school bullying and cyberbullying research. The articles included in this special issue of the International Journal of Bullying Prevention discuss different qualitative methods, reflect on strengths and limitations — possibilities and challenges, and suggest implications for future qualitative and mixed-methods research.
Included Articles
Qualitative studies — focusing on social, relational, contextual, processual, structural, and/or societal factors and mechanisms — have formed the basis for several contributions during the last two decades that have sought to expand approaches to understanding and theorizing the causes of cyber/bullying. Some have also argued the need for expanding the commonly used definition of bullying, based on Olweus ( 1993 ) (e.g., Allen, 2015 ; Ellwood & Davies, 2010 Goldsmid & Howie, 2014 ; Ringrose & Rawlings, 2015 ; Søndergaard, 2012 ; Walton, 2011 ). In the first article of the special issue, Using qualitative methods to measure and understand key features of adolescent bullying: A call to action , Natalie Spadafora, Anthony Volk, and Andrew Dane instead discuss the usefulness of qualitative methods for improving measures and bettering our understanding of three specific key definitional features of bullying. Focusing on the definition put forward by Volk et al. ( 2014 ), they discuss the definitional features of power imbalance , goal directedness (replacing “intent to harm” in order not to assume conscious awareness, and to include a wide spectrum of goals that are intentionally and strategically pursued by bullies), and harmful impact (replacing “negative actions” in order to focus on the consequences for the victim, as well as circumventing difficult issues related to “repetition” in the traditional definition).
Acknowledging that these three features are challenging to capture using quantitative methods, Spadafora, Volk, and Dane point to existing qualitative studies that shed light on the features of power imbalance, goal directedness and harmful impact in bullying interactions — and put forward suggestions for future qualitative studies. More specifically, the authors argue that qualitative methods, such as focus groups, can be used to investigate the complexity of power relations at not only individual, but also social levels. They also highlight how qualitative methods, such as diaries and autoethnography, may help researchers gain a better understanding of the motives behind bullying behavior; from the perspectives of those engaging in it. Finally, the authors demonstrate how qualitative methods, such as ethnographic fieldwork and semi-structured interviews, can provide important insights into the harmful impact of bullying and how, for example, perceived harmfulness may be connected to perceived intention.
In the second article, Understanding bullying and cyberbullying through an ecological systems framework: The value of qualitative interviewing in a mixed methods approach , Faye Mishna, Arija Birze, and Andrea Greenblatt discuss the ways in which utilizing qualitative interviewing in mixed method approaches can facilitate greater understanding of bullying and cyberbullying. Based on a longitudinal and multi-perspective mixed methods study of cyberbullying, the authors demonstrate not only how qualitative interviewing can augment quantitative findings by examining process, context and meaning for those involved, but also how qualitative interviewing can lead to new insights and new areas of research. They also show how qualitative interviewing can help to capture nuances and complexity by allowing young people to express their perspectives and elaborate on their answers to questions. In line with this, the authors also raise the importance of qualitative interviewing for providing young people with space for self-reflection and learning.
In the third article, Q methodology as an innovative addition to bullying researchers’ methodological repertoire , Adrian Lundberg and Lisa Hellström focus on Q methodology as an inherently mixed methods approach, producing quantitative data from subjective viewpoints, and thus supplementing more mainstream quantitative and qualitative approaches. The authors outline and exemplify Q methodology as a research technique, focusing on the central feature of Q sorting. The authors further discuss the contribution of Q methodology to bullying research, highlighting the potential of Q methodology to address challenges related to gaining the perspectives of hard-to-reach populations who may either be unwilling or unable to share their personal experiences of bullying. As the authors point out, the use of card sorting activities allows participants to put forward their subjective perspectives, in less-intrusive settings for data collection and without disclosing their own personal experiences. The authors also illustrate how the flexibility of Q sorting can facilitate the participation of participants with limited verbal literacy and/or cognitive function through the use of images, objects or symbols. In the final part of the paper, Lundberg and Hellström discuss implications for practice and suggest future directions for using Q methodology in bullying and cyberbullying research, particularly with hard-to-reach populations.
In the fourth article, The importance of being attentive to social processes in school bullying research: Adopting a constructivist grounded theory approach , Camilla Forsberg discusses the use of constructivist grounded theory (CGT) in her research, focusing on social structures, norms, and processes. Forsberg first outlines CGT as a theory-methods package that is well suited to meet the call for more qualitative research on participants’ experiences and the social processes involved in school bullying. Forsberg emphasizes three key focal aspects of CGT, namely focus on participants’ main concerns; focus on meaning, actions, and processes; and focus on symbolic interactionism. She then provides examples and reflections from her own ethnographic and interview-based research, from different stages of the research process. In the last part of the article, Forsberg argues that prioritizing the perspectives of participants is an ethical stance, but one which comes with a number of ethical challenges, and points to ways in which CGT is helpful in dealing with these challenges.
In the fifth article, A qualitative meta-study of youth voice and co-participatory research practices: Informing cyber/bullying research methodologies , Deborah Green, Carmel Taddeo, Deborah Price, Foteini Pasenidou, and Barbara Spears discuss how qualitative meta-studies can be used to inform research methodologies for studying school bullying and cyberbullying. Drawing on the findings of five previous qualitative studies, and with a transdisciplinary and transformative approach, the authors illustrate and exemplify how previous qualitative research can be analyzed to gain a better understanding of the studies’ collective strengths and thus consider the findings and methods beyond the original settings where the research was conducted. In doing so, the authors highlight the progression of youth voice and co-participatory research practices, the centrality of children and young people to the research process and the enabling effect of technology — and discuss challenges related to ethical issues, resource and time demands, the role of gatekeepers, and common limitations of qualitative studies on youth voice and co-participatory research practices.
Taken together, the five articles illustrate the diversity of qualitative methods used to study school bullying and cyberbullying and highlight the need for further qualitative research. We hope that readers will find the collection of articles engaging and that the special issue not only gives impetus to increased qualitative focus on the complex phenomena of school bullying and cyberbullying but also to further discussions on both methodological and analytical approaches.
Allen, K. A. (2015). “We don’t have bullying, but we have drama”: Understandings of bullying and related constructs within the school milieu of a U.S. high school. Journal of Human Behavior in the Social Environment , 25 (3), 159–181.
Barrett, B., & Bound, A. M. (2015). A critical discourse analysis of No Promo Homo policies in US schools. Educational Studies, 51 (4), 267–283.
Article Google Scholar
Bethune, J., & Gonick, M. (2017). Schooling the mean girl: A critical discourse analysis of teacher resource materials. Gender and Education, 29 (3), 389–404.
Bjereld, Y. (2018). The challenging process of disclosing bullying victimization: A grounded theory study from the victim’s point of view. Journal of Health Psychology, 23 (8), 1110–1118.
Article PubMed Google Scholar
Bosacki, S. L., Marini, Z. A., & Dane, A. V. (2006). Voices from the classroom: Pictorial and narrative representations of children’s bullying experiences. Journal of Moral Education, 35 (2), 231–245.
Burk, F. L. (1897). Teasing and Bullying. Pedagogical Seminary, 4 (3), 336–371.
Clarke, V., Kitzinger, C., & Potter, J. (2004). ‘Kids are just cruel anyway’: Lesbian and gay parents’ talk about homophobic bullying. British Journal of Social Psychology, 43 (4), 531–550.
Cunningham, C. E., Mapp, C., Rimas, H., Cunningham, S. M., Vaillancourt, T., & Marcus, M. (2016). What limits the effectiveness of antibullying programs? A thematic analysis of the perspective of students. Psychology of Violence, 6 (4), 596–606.
Davies, B. (2011). Bullies as guardians of the moral order or an ethic of truths? Children & Society, 25 , 278–286.
Dennehy, R., Meaney, S., Walsh, K. A., Sinnott, C., Cronin, M., & Arensman, E. (2020). Young people’s conceptualizations of the nature of cyberbullying: A systematic review and synthesis of qualitative research. Aggression and Violent Behavior, 51 , 101379.
Ellwood, C., & Davies, B. (2010). Violence and the moral order in contemporary schooling: A discursive analysis. Qualitative Research in Psychology, 7 (2), 85–98.
Eriksen, I. M., & Lyng, S. T. (2018). Relational aggression among boys: Blind spots and hidden dramas. Gender and Education, 30 (3), 396–409.
Evaldsson, A. -C., Svahn, J. (2012). School bullying and the micro-politics of girls’ gossip disputes. In S. Danby & M. Theobald (Eds.). Disputes in everyday life: Social and moral orders of children and young people (Sociological Studies of Children and Youth, Vol. 15) (pp. 297–323). Bingley: Emerald Group Publishing.
Forsberg, C., & Horton, P. (2022). ‘Because I am me’: School bullying and the presentation of self in everyday school life. Journal of Youth Studies, 25 (2), 136–150.
Forsberg, C., & Thornberg, R. (2016). The social ordering of belonging: Children’s perspectives on bullying. International Journal of Educational Research, 78 , 13–23.
Ganbaatar, D., Vaughan, C., Akter, S., & Bohren, M. A. (2021). Exploring the identities and experiences of young queer people in Mongolia using visual research methods. Culture, Health & Sexuality . Advance Online Publication: https://doi.org/10.1080/13691058.2021.1998631
Gillies-Rezo, S., & Bosacki, S. (2003). Invisible bruises: Kindergartners’ perceptions of bullying. International Journal of Children’s Spirituality, 8 (2), 163–177.
Goldsmid, S., & Howie, P. (2014). Bullying by definition: An examination of definitional components of bullying. Emotional and Behavioural Difficulties, 19 (2), 210–225.
Gumpel, T. P., Zioni-Koren, V., & Bekerman, Z. (2014). An ethnographic study of participant roles in school bullying. Aggressive Behavior, 40 (3), 214–228.
Haines-Saah, R. J., Hilario, C. T., Jenkins, E. K., Ng, C. K. Y., & Johnson, J. L. (2018). Understanding adolescent narratives about “bullying” through an intersectional lens: Implications for youth mental health interventions. Youth & Society, 50 (5), 636–658.
Heinemann, P. -P. (1972). Mobbning – gruppvåld bland barn och vuxna [Bullying – group violence amongst children and adults]. Stockholm: Natur och Kultur.
Hepburn, A. (1997). Discursive strategies in bullying talk. Education and Society, 15 (1), 13–31.
Hong, J. S., & Espelage, D. L. (2012). A review of mixed methods research on bullying and peer victimization in school. Educational Review, 64 (1), 115–126.
Horton, P. (2019). The bullied boy: Masculinity, embodiment, and the gendered social-ecology of Vietnamese school bullying. Gender and Education, 31 (3), 394–407.
Horton, P. (2021). Building walls: Trump election rhetoric, bullying and harassment in US schools. Confero: Essays on Education, Philosophy and Politics , 8 (1), 7–32.
Hutchinson, M. (2012). Exploring the impact of bullying on young bystanders. Educational Psychology in Practice, 28 (4), 425–442.
Hutson, E. (2018). Integrative review of qualitative research on the emotional experience of bullying victimization in youth. The Journal of School Nursing, 34 (1), 51–59.
Jacobson, R. B. (2010). A place to stand: Intersubjectivity and the desire to dominate. Studies in Philosophy and Education, 29 , 35–51.
Jennifer, D., & Cowie, H. (2012). Listening to children’s voices: Moral emotional attributions in relation to primary school bullying. Emotional and Behavioural Difficulties, 17 (3–4), 229–241.
Johnson, C. W., Singh, A. A., & Gonzalez, M. (2014). “It’s complicated”: Collective memories of transgender, queer, and questioning youth in high school. Journal of Homosexuality, 61 (3), 419–434.
Khanolainen, D., & Semenova, E. (2020). School bullying through graphic vignettes: Developing a new arts-based method to study a sensitive topic. International Journal of Qualitative Methods, 19 , 1–15.
Lopez-Ropero, L. (2012). ‘You are a flaw in the pattern’: Difference, autonomy and bullying in YA fiction. Children’s Literature in Education, 43 , 145–157.
Lyng, S. T. (2018). The social production of bullying: Expanding the repertoire of approaches to group dynamics. Children & Society, 32 (6), 492–502.
Malaby, M. (2009). Public and secret agents: Personal power and reflective agency in male memories of childhood violence and bullying. Gender and Education, 21 (4), 371–386.
Maran, D. A., & Begotti, T. (2021). Measurement issues relevant to qualitative studies. In P. K. Smith & J. O’Higgins Norman (Eds.). The Wiley handbook of bullying (pp. 233–249). John Wiley & Sons.
Mishna, F., Scarcello, I., Pepler, D., & Wiener, J. (2005). Teachers’ understandings of bullying. Canadian Journal of Education, 28 (4), 718–738.
Moretti, C., & Herkovits, D. (2021). Victims, perpetrators, and bystanders: A meta-ethnography of roles in cyberbullying. Cad. Saúde Pública, 37 (4), e00097120.
Newman, M., Woodcock, A., & Dunham, P. (2006). ‘Playtime in the borderlands’: Children’s representations of school, gender and bullying through photographs and interviews. Children’s Geographies, 4 (3), 289–302.
Odenbring, Y. (2022). Standing alone: Sexual minority status and victimisation in a rural lower secondary school. International Journal of Inclusive Education, 26 (5), 480–494.
Oliver, C., & Candappa, M. (2007). Bullying and the politics of ‘telling.’ Oxford Review of Education, 33 (1), 71–86.
Olweus, D. (1978). Aggression in the schools – Bullies and the whipping boys . Wiley.
Google Scholar
Olweus, D. (1993). Bullying in school: What we know and what we can do . Blackwell.
Patton, D. U., Hong, J. S., Patel, S., & Kral, M. J. (2017). A systematic review of research strategies used in qualitative studies on school bullying and victimization. Trauma, Violence, & Abuse, 18 (1), 3–16.
Pellegrini, A. D., & Bartini, M. (2000). A longitudinal study of bullying, victimization, and peer affiliation during the transition from primary school to middle school. American Educational Research Journal, 37 (3), 699–725.
Rachoene, M., & Oyedemi, T. (2015). From self-expression to social aggression: Cyberbullying culture among South African youth on Facebook. Communicatio: South African Journal for Communication Theory and Research , 41 (3), 302–319.
Ringrose, J., & Rawlings, V. (2015). Posthuman performativity, gender and ‘school bullying’: Exploring the material-discursive intra-actions of skirts, hair, sluts, and poofs. Confero: Essays on Education, Philosophy and Politics , 3 (2), 80–119.
Ringrose, J., & Renold, E. (2010). Normative cruelties and gender deviants: The performative effects of bully discourses for girls and boys in school. British Educational Research Journal, 36 (4), 573–596.
Skrzypiec, G., Slee, P., & Sandhu, D. (2015). Using the PhotoStory method to understand the cultural context of youth victimization in the Punjab. The International Journal of Emotional Education, 7 (1), 52–68.
Smith, P., Robinson, S., & Slonje, R. (2021). The school bullying research program: Why and how it has developed. In P. K. Smith & J. O’Higgins Norman (Eds.). The Wiley handbook of bullying (pp. 42–59). John Wiley & Sons.
Smith, P. K., & Berkkun, F. (2017). How research on school bullying has developed. In C. McGuckin & L. Corcoran (Eds.), Bullying and cyberbullying: Prevalence, psychological impacts and intervention strategies (pp. 11–27). Hauppage, NY: Nova Science.
Strindberg, J., Horton, P., & Thornberg, R. (2020). The fear of being singled out: Pupils’ perspectives on victimization and bystanding in bullying situations. British Journal of Sociology of Education, 41 (7), 942–957.
Sylwander, K. R. (2019). Affective atmospheres of sexualized hate among youth online: A contribution to bullying and cyberbullying research on social atmosphere. International Journal of Bullying Prevention, 1 , 269–284.
Søndergaard, D. M. (2012). Bullying and social exclusion anxiety in schools. British Journal of Sociology of Education, 33 (3), 355–372.
Temko, E. (2019). Missing structure: A critical content analysis of the Olweus Bullying Prevention Program. Children & Society, 33 (1), 1–12.
Tholander, M. (2019). The making and unmaking of a bullying victim. Interchange, 50 , 1–23.
Tholander, M., Lindberg, A., & Svensson, D. (2020). “A freak that no one can love”: Difficult knowledge in testimonials on school bullying. Research Papers in Education, 35 (3), 359–377.
Thornberg, R. (2011). ‘She’s weird!’ – The social construction of bullying in school: A review of qualitative research. Children & Society, 25 , 258–267.
Thornberg, R. (2018). School bullying and fitting into the peer landscape: A grounded theory field study. British Journal of Sociology of Education, 39 (1), 144–158.
Torrance, D. A. (2000). Qualitative studies into bullying within special schools. British Journal of Special Education, 27 (1), 16–21.
Varjas, K., Meyers, J., Kiperman, S., & Howard, A. (2013). Technology hurts? Lesbian, gay, and bisexual youth perspectives of technology and cyberbullying. Journal of School Violence, 12 (1), 27–44.
Volk, A. A., Dane, A. V., & Marini, Z. A. (2014). What is bullying? A Theoretical Redefinition, Developmental Review, 34 (4), 327–343.
Walton, G. (2005). Bullying widespread. Journal of School Violence, 4 (1), 91–118.
Walton, G. (2011). Spinning our wheels: Reconceptualizing bullying beyond behaviour-focused Approaches. Discourse: Studies in the Cultural Politics of Education , 32 (1), 131–144.
Walton, G., & Niblett, B. (2013). Investigating the problem of bullying through photo elicitation. Journal of Youth Studies, 16 (5), 646–662.
Wiseman, A. M., & Jones, J. S. (2018). Examining depictions of bullying in children’s picturebooks: A content analysis from 1997 to 2017. Journal of Research in Childhood Education, 32 (2), 190–201.
Wiseman, A. M., Vehabovic, N., & Jones, J. S. (2019). Intersections of race and bullying in children’s literature: Transitions, racism, and counternarratives. Early Childhood Education Journal, 47 , 465–474.
Ybarra, M. L., Espelage, D. L., Valido, A., Hong, J. S., & Prescott, T. L. (2019). Perceptions of middle school youth about school bullying. Journal of Adolescence, 75 , 175–187.
Download references
Acknowledgements
We would like to thank the authors for sharing their work; Angela Mazzone, James O’Higgins Norman, and Sameer Hinduja for their editorial assistance; and Dorte Marie Søndergaard on the editorial board for suggesting a special issue on qualitative research in the journal.
Author information
Authors and affiliations.
Department of Behavioural Sciences and Learning (IBL), Linköping University, Linköping, Sweden
Paul Horton
Work Research Institute (WRI), Oslo Metropolitan University, Oslo, Norway
Selma Therese Lyng
You can also search for this author in PubMed Google Scholar
Corresponding author
Correspondence to Paul Horton .
Rights and permissions
Reprints and permissions
About this article
Horton, P., Lyng, S.T. Qualitative Methods in School Bullying and Cyberbullying Research: An Introduction to the Special Issue. Int Journal of Bullying Prevention 4 , 175–179 (2022). https://doi.org/10.1007/s42380-022-00139-5
Download citation
Published : 12 August 2022
Issue Date : September 2022
DOI : https://doi.org/10.1007/s42380-022-00139-5
Share this article
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
- Find a journal
- Publish with us
- Track your research
- Open access
- Published: 22 December 2021
Cyberbullying detection: advanced preprocessing techniques & deep learning architecture for Roman Urdu data
- Amirita Dewani ORCID: orcid.org/0000-0002-3816-3644 1 ,
- Mohsin Ali Memon ORCID: orcid.org/0000-0003-2638-4252 1 &
- Sania Bhatti ORCID: orcid.org/0000-0002-0887-8083 1
Journal of Big Data volume 8 , Article number: 160 ( 2021 ) Cite this article
10k Accesses
28 Citations
1 Altmetric
Metrics details
Social media have become a very viable medium for communication, collaboration, exchange of information, knowledge, and ideas. However, due to anonymity preservation, the incidents of hate speech and cyberbullying have been diversified across the globe. This intimidating problem has recently sought the attention of researchers and scholars worldwide and studies have been undertaken to formulate solution strategies for automatic detection of cyberaggression and hate speech, varying from machine learning models with vast features to more complex deep neural network models and different SN platforms. However, the existing research is directed towards mature languages and highlights a huge gap in newly embraced resource poor languages. One such language that has been recently adopted worldwide and more specifically by south Asian countries for communication on social media is Roman Urdu i-e Urdu language written using Roman scripting. To address this research gap, we have performed extensive preprocessing on Roman Urdu microtext. This typically involves formation of Roman Urdu slang- phrase dictionary and mapping slangs after tokenization. We have also eliminated cyberbullying domain specific stop words for dimensionality reduction of corpus. The unstructured data were further processed to handle encoded text formats and metadata/non-linguistic features. Furthermore, we performed extensive experiments by implementing RNN-LSTM, RNN-BiLSTM and CNN models varying epochs executions, model layers and tuning hyperparameters to analyze and uncover cyberbullying textual patterns in Roman Urdu. The efficiency and performance of models were evaluated using different metrics to present the comparative analysis. Results highlight that RNN-LSTM and RNN-BiLSTM performed best and achieved validation accuracy of 85.5 and 85% whereas F1 score was 0.7 and 0.67 respectively over aggression class.

Introduction
Cyberbullying (aka hate speech, cyberaggression and toxic speech) is a critical social problem plaguing today’s Internet users typically youth and lead to severe consequences like low self-esteem, anxiety, depression, hopelessness and in some cases causes lack of motivation to be alive, ultimately resulting in death of a victim [ 1 ]. Cyberbullying incidents can occur via various modalities. For example, it can take the form of sharing/ posting offensive video content or uploading violent images or sharing the pictures without permission of the owner etc. However, cyberbullying via textual content is far more common [ 2 ]. In Pakistan, the usage of internet, smartphones and social media has increasingly become prevalent these days and the very frequent users are youngsters. According to a report, more than 65% of all the users lie between 18 and 29, and typically women are more susceptible and unprotected. People often use offensive language, use hate speech, and become aggressive to bully celebrities, leaders, women and an individual [ 3 ]. In Pakistan, victims have reported life disturbing and annoying experiences and most of the victims are educated youngsters (age group of 21–30 years) [ 4 ]. The traffic in cyberspace has escalated significantly during covid-19 pandemic. A report “COVID 19 and Cyber Harassment”, released by DRF in 2020 highlights a great rise in the number of cyberbullying and harassment cases during the pandemic. The complaints registered with DRF’s Cyber Harassment Helpline were surged by 189% [ 5 ].
Recently, Roman Urdu language has been a contemporary trend and a viable language for communication on different social networking platforms. Urdu is national and official language of Pakistan and predominant among most communities across different regions. A survey statistic in [ 6 ] affirms that 300 million people are speaking Urdu language and approximately 11 million speakers are in Pakistan from which maximum users switched to Roman Urdu language for the textual communication, typically on social media. It is linguistically rich and morphologically complex language [ 7 ]. Roman Urdu language is highly variant with respect to word structures, writing styles, irregularities, and grammatical compositions. It is deficit of standard lexicon and available resources and hence become extremely challenging when performing NLP tasks.
An elaboration of script of Urdu instances and Roman Urdu is given in Table 1 . Instances highlighted are describing anti-social behavior.
This paper addresses toxicity/cyberbullying detection problem in Roman Urdu language using deep learning techniques and advanced preprocessing methods including usage of lexicons/resource that are typically developed to accomplish this work. Intricacies in analyzing the structure and patterns behind these typical aggressive behaviors, typically in a newly adopted language, and forming it as a comprehensive computational task is very complicated. The major contributions of this study are formation of a slang and contraction mapping procedure along with slang lexicon for Roman Urdu language and development of hybrid deep neural network models to capture complex aggression and bullying patterns.
The rest of the paper is organized as follows: Review of existing literature is presented in " Related Work " Section. " Problem statement " Section states research gap and gives formal definition of the addressed problem. " Methodology " Section describes the steps of research methodology and techniques and models used for the experimentations. Advanced preprocessing steps applied on Roman Urdu data are elaborated in " Data Preprocessing on Roman Urdu microtext " section. Implementation of proposed model architecture and hyperparameter settings are discussed in " Experimental Setup " section. " Results and Discussion " Section highlights and discusses study results and finally " Conlusion " Section concludes the research work and provides future research directions.
Related work
Due to the accretion of social media communication and adverse effects arising from its darker side on users, the field of automatic cyberbullying detection has become an emerging and evolving research trend [ 8 ]. Research work in [ 9 ] presents cyberbullying detection algorithm for textual data in English language. It is considered as one of the pioneers and highly cited research. They divided the task in text-classification sub problems related to sensitive topics and collected 4500 textual comments on controversial YouTube videos. This study implemented Naive Bayes, SVM and J48 binary and multiclass classifiers using general and specific feature sets. Study contributed in [ 10 ] applied deep learning architectures on Kaggle dataset and conducted experimental analysis to determine the effectiveness and performance of deep learning algorithms LSTM, BiLSTM, RNN and GRU in detecting antisocial behavior. Authors in [ 11 ] extracted data from four platforms i-e Twitter, YouTube, Wikipedia, and Reddit for developing an online hate classifier in English language using different classification techniques. Research carried out in [ 12 ] developed an automated approach to detect toxicity and unethical behavior in online communication using word embeddings and varying neural network layers. They suggested that LSTM layers and mimicked word embedding can uncover such behavior with good accuracy level.
Few of the studies in recent years has been contributed by researchers on other languages apart from English. Research work in [ 13 ] is unique and has gathered textual data from Instagram and twitter in Turkish language. They have implemented Naïve Bayes Multinomial, SVM, KNN and decision trees for cyberbullying detection along with Chi-square and information gain (IG) for feature selection. Work accomplished in [ 14 ] also addresses the problem of cyberaggression in Turkish language. The work extends comparison of different machine learning algorithms and found optimal results using Light Gradient Boosting Model. Van Hee, Cynthia, et al. in [ 15 ] proposed cyberbullying detection scheme for Dutch language. This is the first study on Dutch social media. Data was collected from ASKfm where users can ask and answer questions. The research uses default parameter settings for un-optimized linear kernel SVM based on n-grams and keyword system to identify bullying traces. F1 score for Dutch language was 61%. Problem of Arabic language cyberbullying detection was addressed and accomplished in [ 16 ]. This study used Dataiku DSS and WEKA for ML tasks. The data was scrapped from facebook and twitter. The study concluded that even though the detection approach was not comparable with the other studies in English language but overall Naive Bayes and SVM yield reasonable performance. Research work in [ 17 ] by Gomez-Adorno, Helena, et al. proposed automatic aggression detection for Spanish tweets. Several types of n-grams and linguistically motivated patterns were used but the best run could only achieve F1 score of 42.85%. Studies presented in [ 18 , 19 , 20 ] are based on automatic detection of cyberbullying content in German language. Research conducted in [ 18 ] proposed an approach based on SVM, CNN and ensemble model using unigram, bigrams and character N-grams for categorizing offensive tweets in German language. Research presented in [ 21 ] attempted for the very first time to identify bullying traces in Indonesian language. Association Rule mining and FP growth text mining were used to identify trends for bullying patterns in Jakarta and Surabaya cities using social media text. This baseline study on Indonesian language was further extended by Nurrahmi, Hani et al. in [ 22 ]. Study in [ 23 ] made first attempt to develop a corpus of code-mixed data considering Hindi and English language. They proposed a scheme for hate speech detection using N-grams and lexical features. An ensemble approach by combining the predictions of Convolutional Neural Network (CNN) and SVM algorithms were used for identifying such patterns. The weighted F1 score for Hindi language ranged between 0.37 and 0.55 for different experiments [ 24 ]. In the year 2019, Association for computational linguistics initiated the project for automatic detection of cyberbullying in Polish language [ 25 ]. Research conducted in [ 26 ] attempted to uncover cyberbullying patterns in Bengali language implementing passive aggressive, SVM and logistic regression. The optimum accuracy achieved was 78.1%. Recently, work contributed in [ 27 ] presented first study in Roman Urdu using lexicon based approach. The dataset was highly skewed comprising of only 2.2% toxic data. As according to [ 28 ], biased sampling and measurement errors are highly prone to classification errors when working on such datasets. Moreover, pattern detection based on predefined bullying and non-bullying lexicons were shortcomings of this study.
For automated detection of complex cyberbullying patterns, studies contributed by different scholars employ supervised, unsupervised, hybrid and deep learning models, vast feature engineering techniques, corpora, and social media platforms. However, the existing literature is mainly oriented towards unstructured data in English language. Some recent studies and projects have been initiated in other languages as discussed previously. To the best of our knowledge and literature review, no detailed work has been contributed in Roman Urdu to systematically analyze cyberbullying detection phenomenon using advanced preprocessing techniques (involving the usage of Roman Urdu resources) and deep learning approaches under different configurations.
Problem statement
The escalated usage of social networking sites and freedom of speech has given optimal ground to individuals across all demographics for cyberbullying and cyberaggression. This leaves drastic and noticeable impacts on behavior of a victim, ranging from disturbance in emotional wellbeing and isolation from society to more severe and deadly consequences [ 29 ]. Automatic Cyberbullying detection has remained very challenging task since social media content is in natural language and is usually posted in unstructured free-text form leaving behind the language norms, rules, and standards. Evidently, there exists a substantial number of research studies which primarily focus on discovering cyberbullying textual patterns over diverse social media platforms as discussed previously in literature review section. However, most of the detection schemes and automated approaches formulated are for resource-rich and mature languages spoken worldwide. Roman Urdu is typically spoken in South Asia and is a highly resource deficient language. Hence this research puts novel efforts to propose data pre-processing techniques on Roman Urdu scripting and develop deep learning-based hybrid models for automated cyberbullying detection in Roman Urdu language. The outcomes of this study, if implemented, will assist cybercrime centers and investigation agencies for monitoring social media contents and in making cyberspace secure and safer place for all segments of society.
Methodology
The research methodology is depicted in Fig. 1 .
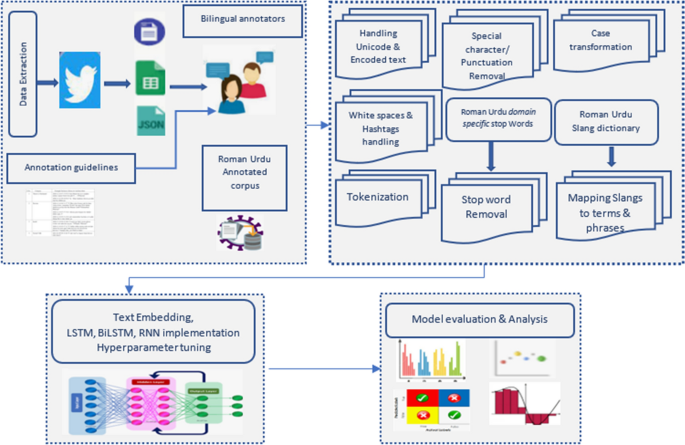
Proposed research methodology
The development of hate speech/cyberbullying corpus with minor skew and automated development of domain specific roman Urdu stop words is published in our previous work [ 30 ]. The work details formation of computational linguist resources. Further steps of methodology are discussed in subsequent sections. The Deep Neural Network (DNN) based techniques and models used for the experimentations are detailed below.
Model description
Recurrent neural networks (rnn).
RNN [ 31 ] has been applied in literature for successive time series applications with temporal dependencies. An unfolded RNN can handle processing of current data by utilizing past data. Meanwhile, RNN has the issue of training long-term dependencies. This has been addressed by one of the RNN variant.
Long short-term memory networks (LSTM)
LSTM has been employed as an advanced version of RNN network. It resolves the shortcoming of RNN by applying memory cells also known as hidden layer units. Memory cells are controlled through three gates named as: input gate, output gate and forget gate. They have the self-connections which store the temporal state of network [ 31 ]. Input and output gates address and control the flow of information from memory cell input and output to rest of the network. The forget gate, usually called as a remember vector, transfers the information with higher weights from previous neuron to the next neuron. The forget gate is added to the memory cell. The information resides in memory depending upon the high activation results; the information will be stored in memory cell iff the input unit has high activation. However, the information will be transferred to next neuron if the output unit has high activation. Otherwise, input information with high weights resides in memory cell [ 31 ].
Mathematically, LSTM network can be described as [ 32 ]:
where W h ∈ R m × d and U h ∈ R m × m indicates weight matrices, x t denotes the current word embedding, b h ∈ R m refers to bias term, whereas f(x ) is a non-linear function.
LSTM has more complex architecture including hidden states and tends to remember information for either short or long term. The hidden state [ 33 ] of LSTM is computed as follows:
where f t denotes the forget gate, i t refers to the input gate, c t denotes the cell state, o t is the output gate, h t is the regular hidden state, σ indicates sigmoid function, and ◦ is the Hadamard product.
Bidirectional Long short-term memory networks (BiLSTM)
In the traditional recurrent neural network model and LSTM model, the propagation of information is only in forward direction. This results in computation of an output vector only based on the current input at time t and the output of the previous unit. The back propagation of information in network is achieved by merging two bidirectional recurrent neural network (BiRNN) and LSTM units, one for forward direction and one for backward direction. This helps in capturing contextual information and enhances learning ability [ 34 ].
In bidirectional LSTM, outputs of two LSTM networks are stacked together. The first LSTM is a regular sequence starting from the starting of the paragraph, while the second LSTM is a standard sequence, and the series of inputs are fed in the opposite order. The first hidden state is denoted by ht forward whereas second LSTM unit’s hidden state is denoted by ht backward . After processing data, the final state ht Bilstm is computed by concatenating the two hidden states as given in Eq. 3 .
where ⊕ denotes a concatenation operator.
Convolutional neural networks (CNN)
Convolution neural networks (aka CNN), originally incorporated for image processing tasks, have become very efficacious in different NLP and text classification applications. The network identifies correlations and patterns of data via their feature maps. Information about local structure of data is extracted by applying multiple filters with different dimensions [ 35 ].
Data preprocessing on Roman Urdu microtext
Big social media data in Roman Urdu language is inconsistent, incomplete, or precise, missing in certain behaviors or trends, and is likely to incorporate many errors. Roman Urdu users highly deviate language norms while communicating on social media. Hence data preprocessing is immensely significant. Some major data preprocessing steps applied on Roman Urdu microtext are detailed below.
Handling Unicode and encoded text formats
Unicode scheme provides every character in natural language text a unique code from 0 to 0 × 10FFFF. The uncleaned Roman Urdu data comprised of special symbols, emojis, and other typical stray characters represented using Unicode. We used Unicode transformation type 8 encoding to convert the data. This data was converted and handled using re and string modules in python.
Text cleaning
Text cleaning is essential step to eliminate or at least reduce noise from Microtext. This step comprised of case transformation, removal of punctuations and URLs, elimination of additional white spaces, exclusion of hashtags, digits & special character removal and removal of metadata/non-linguistic features.
Tokenization
Tokenization is immensely essential phase of text processing. It is the process of generating tokens by splitting textual content into words, phrases, or other meaningful parts. It is generally a form of text segmentation [ 36 ]. Tokenization was performed using Keras tokenizer to prepare the text for implementing deep learning networks.
Filtering stop words
Stop words are non-semantic division of text in natural language. The necessity that stop words should be eliminated from text is that they make the text higher dimensional with redundant features which are less significant for analysts. Removing stop words reduces the dimensionality of term space [ 37 ]. Development of domain specific stop words in Roman Urdu language automatically using statistical techniques and bilingual experts’ input, comprising of 173 words is detailed in our previous work [ 30 ]. Insignificant Roman Urdu words were typically articles such as ek (ایک), conjunctions and pronouns such as tum (تم), tumhara (تمھارا), us (اُس), wo/who (وہ), usko (اُسکو), preposition such as main (میں), pe (پے), par (پر), demonstratives such as ye (یے), inko (انکو), yahan(یہاں), and interrogatives such as kahan (کہاں), kab (کب), kisko (کس کو), kiski (کس کی) etc. Stop words were removed from Roman Urdu corpus, leaving behind the index terms which are important.
Mapping slangs and contractions
Existing libraries, APIs and toolkits in python language primarily support preprocessing functions for English and other mature languages. They can be partially used for Roman Urdu language. Moreover, most of the communication in Roman Urdu comprises of bully terms being used as slangs. High dimensional textual data also suppress significant features. Hence contraction mapping is mandatory for dimensionality reduction and to capture complex bullying patterns. Currently, Pycontractions Library [ 38 ] only supports English contraction mapping process. To address this problem, the study developed data slang mapping process. To map slangs to original terms and phrases in Roman Urdu language, we created Slang lexicon in Roman Urdu (SLRU) which also included Roman Urdu abuses and offensive terms used as a norm by Roman Urdu users. SLRU is in the form of a dictionary. It comprises of the key: value pairs, where key is the slang and value is its equivalent Roman Urdu phrase/term such as “AFIK”: “Jahan tak mujhay pata hai”, ASAP: “Jitna jaldi ho sakay”, “tbh”: “Sach main” and so on. The process of slang mapping is detailed in Fig. 2 .

Mapping process for slangs in Roman Urdu
The results of mapping process are highlighted in Fig. 3 .

Mapping on Roman Urdu Data
Experimental setup
This section discusses implementation of proposed neural network architecture and all hyper-parameter settings. All the experiments were performed on 11 Gen, core i7, 4 cores, 8 logical microprocessors, with 2.8 GHz processor speed, 256 GB Solid State Drive and python version 3.8, 64 bits.
Proposed model implementation and hyper-parameter settings
All models were implemented and trained in Keras; a high-level neural network API that works with open-source machine learning framework called TensorFlow [ 39 ]. All the implementation was accomplished using PyCharm. The optimal parameters and results were achieved through repeated experimentations.
Data was split into training and testing datasets. The data split was 0.8 for training and 0.2 for testing i-e 80% of data instances were used for training and 20% were holdout for testing and validation purpose. The sets were made using shuffled array. This allows model to learn over different data instances. Moreover, it helps to uncover reliability of model and consistency of results over repeated executions. Random state is also generated using numpy.random [ 40 ] for random sampling during splitting of data to ensure reproducible splits.
Textual input data must be integer encoded. In RNN-LSTM architecture, a sequential model was created. Initially an Embedding layer was added to the network and textual Roman Urdu data was provided as an input. Embedding layer embedded high dimensional text data in low dimensional vector space for generating dense vector representation of data. Embedding was formed using 2000 features and 128 embed dimensions. The experiment was initially executed on 20 epochs and 50 batch size. The batch size was based on the fact that model was having single lstm layer, and comparatively took lower training and validation time per step. The execution time for each epoch was approximately 10 ms. SpatialDropout1D was used with rate of 0.3. It helped to regularize the activations and maintain effective learning rate of the model. For updating network weights iteratively, this work uses binary cross entropy loss function and Adam optimizer. Sigmoid activation function was also implemented. It is denoted by f(x) and is defined as:
The Spatial Dropout layer was implemented instead of a simple Dropout. The major reason being was to retain the context of textual data established by neighboring words. Dropping random words (except for stop words, which were already removed during preprocessing step) can highly affect the context of uttered sentences and ultimately the performance of model. We incorporated two hidden dense layers denoted by D 1 and D 2 . The output of each hidden layer was computed to get the final output for cyberbullying text detection.
Keras tokenizer was used to accomplish pre-tokenization of all the data required for the implementation of RNN-biLSTM model. We created a sequential model with Embedding layer having 2000 maximum features. Subsequently a biLSTM layer comprising of two LSTM layers, one to read sequence in forward direction and other in backward direction, each with 64 units was added. Hidden layer (H 1 ) was formed using sigmoid activation function. For down sampling the feature maps, Dropout layer was added with 0.2 dropout rate. Moreover, we used 128 batch size to utilize low to moderate computational resources while still not slowing down the training process. Batch size highlights number of samples processed by model before updating of internal parameters. To combat overfitting, we added second dropout layer with rate of 0.25. Adam optimization was used with learning rate of 0.01 since batch size was not too small. For this model, we used binary cross entropy loss function. As the Epochs increase, the generalization ability of the model improves. However, too many epochs also lead to the problem of overfitting. The model was executed over different number of Epochs and average execution time for each epoch was 13 to 15 ms. The performance of model stabilized over 20 Epochs, above which the improvement was almost negligible.
In CNN model, initially the sentence was transformed into matrix where each row of matrix represented word vectors representation of data. We used 1000 features and 32 dimensions. Two convolutional filters were applied with 8 and 16 filters and 3 kernel size. Each filter was used to perform one dimensional convolution on word embeddings. Both Layers were 1D in nature. We set two dropout layers with dropout rate of 0.25 to improve generalization ability of developed model. Hidden layers with Relu and sigmoid activation functions were used. To extract most salient and prominent features, global maximum pooling layers were used with pool size = 2. Flatten layer was created after convolutional layers to flatten the output of the previous layer to a single long feature vector. The experiment was simulated over different Epochs. However, results got stable at 30 epochs.
Results and discussion
Empirical evaluation of cyberbullying detection scheme performance in Roman Urdu and experimental setups is accomplished via accuracy, precision, recall, and f1 measure metrics.
All the implemented models were executed several times over number of epochs to get consistency in evaluation parameters until it was a minor difference of ± 0.1. The results for LSTM are depicted in Fig. 4 . To ensure results validity and reliability, for a comparatively less skewed dataset, F1 measure (i-e a harmonic mean of precision and recall) is used as an evaluation metric. Furthermore, we have also reported macro and weighted average scores across all the classes. The evaluation results of RNN-LSTM are given in Fig. 4 .
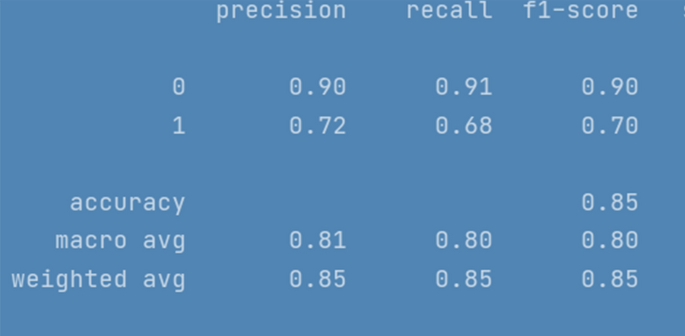
RNN-LSTM evaluation Results
F1 score for RNN-LSTM over cyberbullying class was only 70%, however for non-cyberbullying class, score was 90%. We observed that nearly all the instances of majority class of non-cyber bullying are correctly classified by this model. The experimental simulation depicting model accuracy and validation accuracy during training and validation phases, before and after stabilization of evaluation parameters is represented in Figs. 5 and 6 respectively.
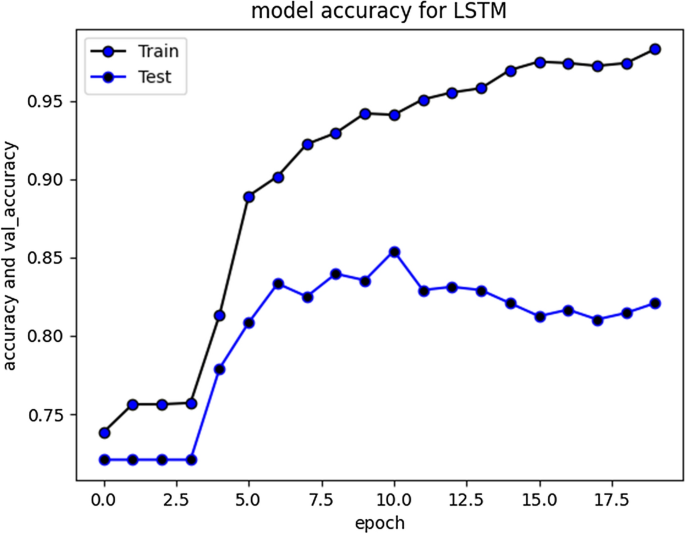
RNN-LSTM Model accuracy graph for 20 epochs
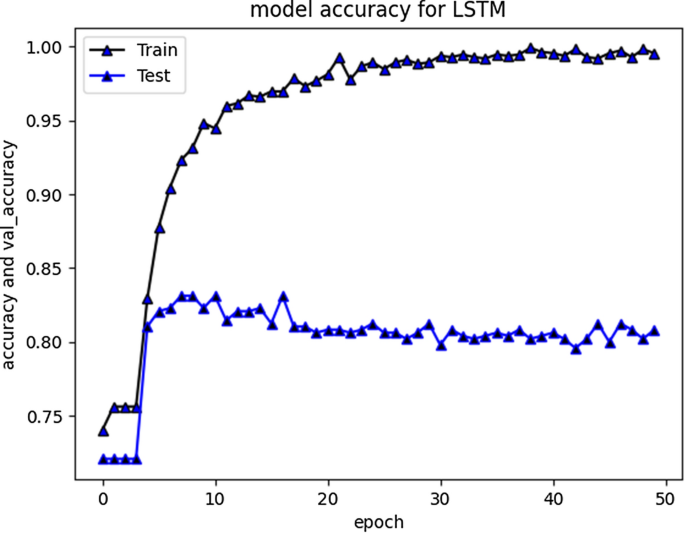
RNN-LSTM Model accuracy graph for 50 epochs
The accuracy improved over subsequent epochs. However, after 20 epochs it got stabilized. The average accuracy produced by this model was 93.5% during training and 85.5% during validation. Overall curve variation is indicating that no overfitting problem arise. The model loss during training and validation loss during testing over 20 and 50 epochs is shown in Figs. 7 and 8 respectively. The cross-entropy loss considered during configuration over different epochs converged well, thus indicating optimal model performance.
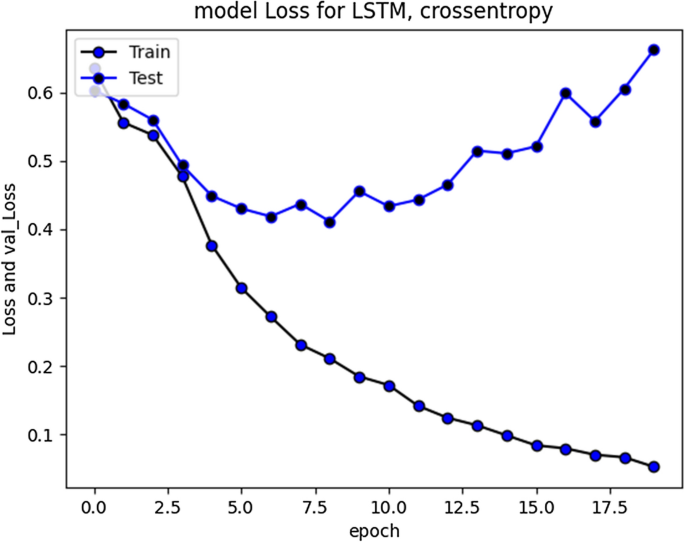
RNN-LSTM Model loss plot- Binary Cross entropy for 20 epochs
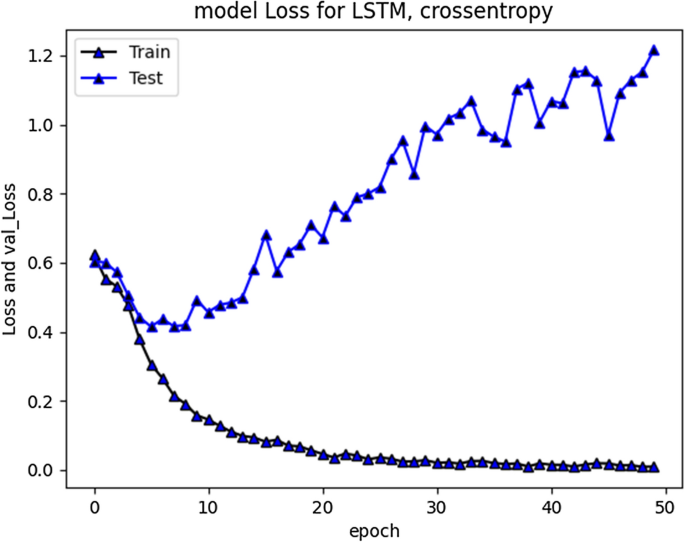
RNN-LSTM Model loss plot- Binary Cross entropy for 50 epochs
The evaluation results of RNN-BILSTM model over 20 epochs are given in Fig. 9 .
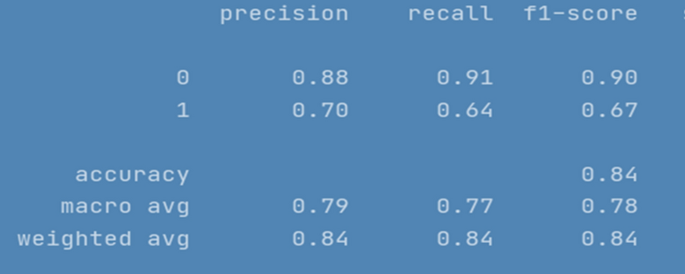
RNN-BiLSTM evaluation Results
RNN-LSTM also performed reasonably well for cyberbullying detection task on Roman Urdu data. F1 score for non-cyberbullying content prediction was 90% whereas for cyberbullying content, the score was 67% only. This indicates that model erroneously classified/misclassified some of the aggressive class instances and TN rate was at average. Figs. 10 and 11 are depicting model accuracy and validation accuracy for RNN-BiLSTM.
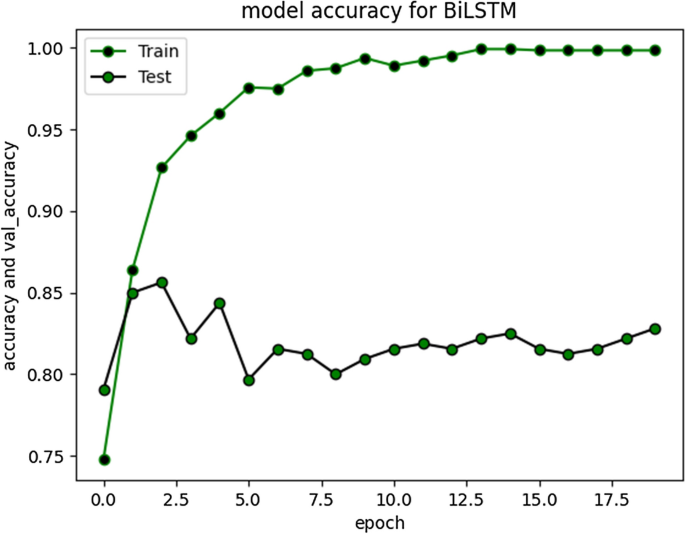
RNN-biLSTM Model accuracy plot for 20 epochs
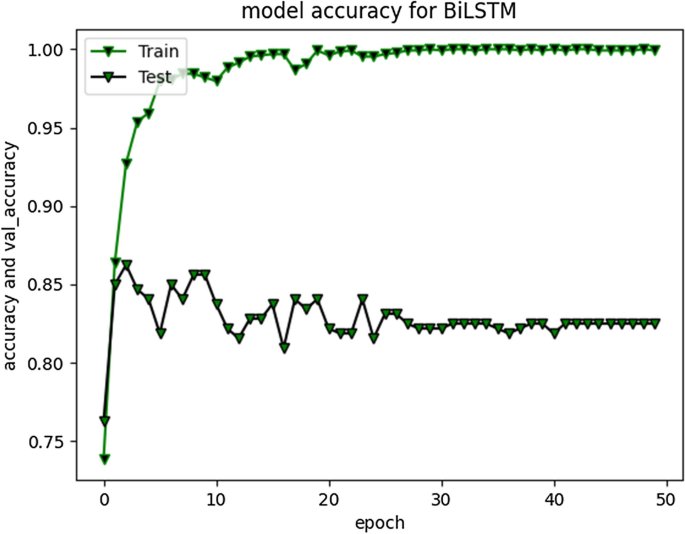
RNN-biLSTM Model accuracy plot for 50 epochs
The accuracy improved highly during training process up to 20 epochs. Overall average accuracy was 97% in training and 85% on validation set. 20% of the data was used for as a validation set, as stated earlier. During experimentation, we identified that accuracy of our model is not improving after a specific point i-e after 20 Epochs. The trivial variations can be clearly visualized from the graph in Fig. 9 . Model loss and validation loss during training and testing process for RNN-BiLSTM over 20 and 50 epochs is given in Figs. 12 and 13 respectively.
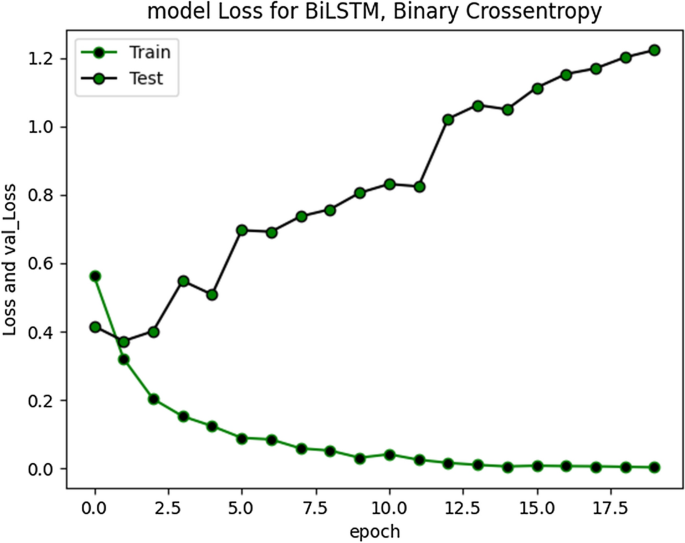
RNN-BiLSTM Model loss plot- Binary Cross entropy for 20 epochs
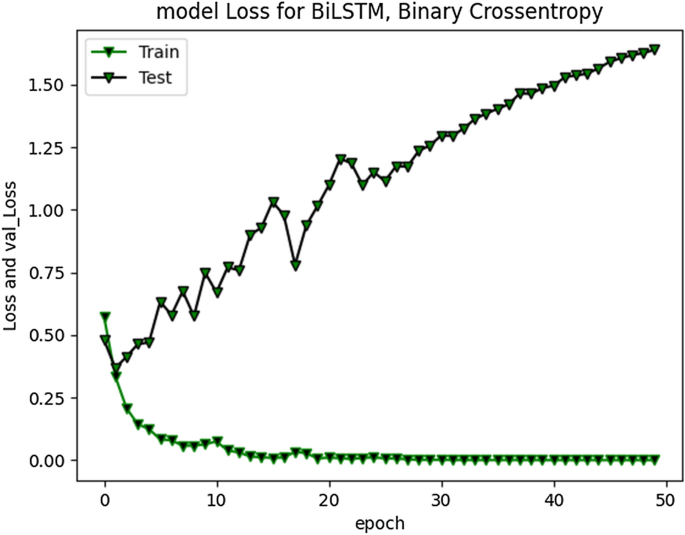
RNN-BiLSTM Model loss plot- Binary Cross entropy for 50 epochs
The cross-entropy loss was minimal (approximately 1.2), indicating good prediction capability of developed model.
Figure 14 represents the evaluation results for CNN model.
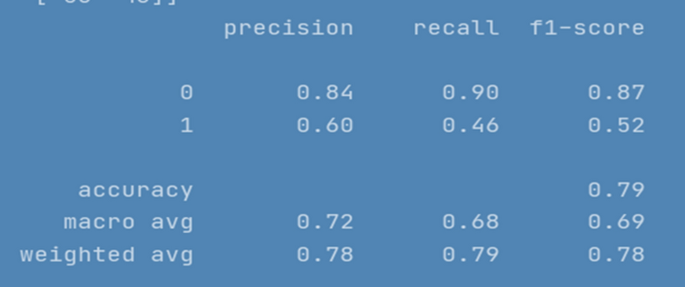
CNN model evaluation Results
CNN performed well for prediction of non-cyberbullying content, providing F1 score of 87%. However, model did not yield good efficiency for categorizing cyberbullying class, producing f1-score of 52%. The repeated experiments performed for CNN showed continuous improvements up to 30 Epochs. Figure 15 depicts model accuracy and validation accuracy. The experimental simulation over 50 epochs only shown minor improvements as represented in Fig. 16 . The average execution time for Epoch was 9 ms each. The training accuracy of 98% was achieved over different executions whereas model produced 85% validation accuracy.
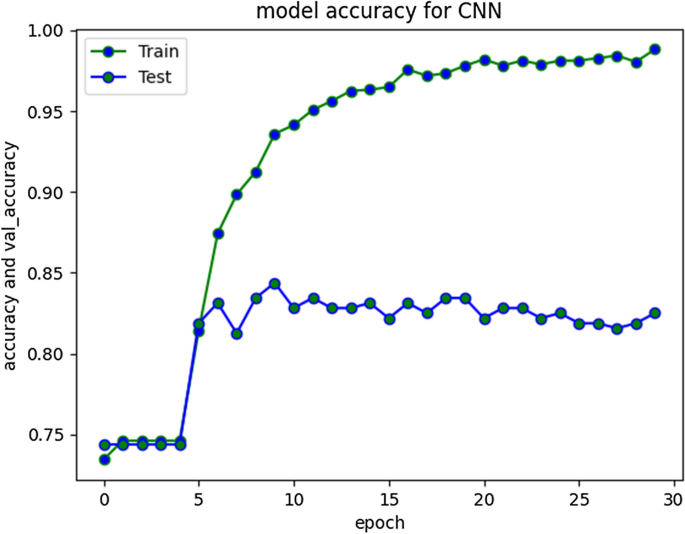
CNN Model accuracy plot for 30 epochs
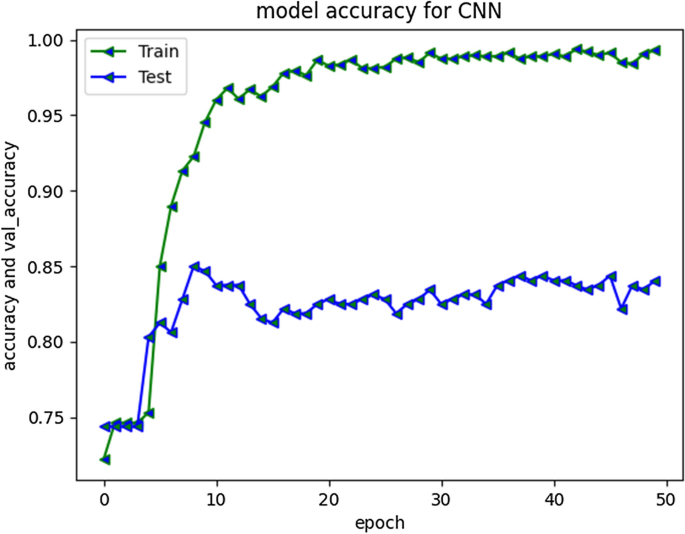
CNN Model accuracy plot for 50 epochs
CNN model loss and validation loss results at 30 and 50 epochs are presented in Fig. 17 and 18 respectively. The loss was minimal during training and converged. During validation the loss increased and diverged indicating only moderate performance over unseen instances typically from aggressive class.
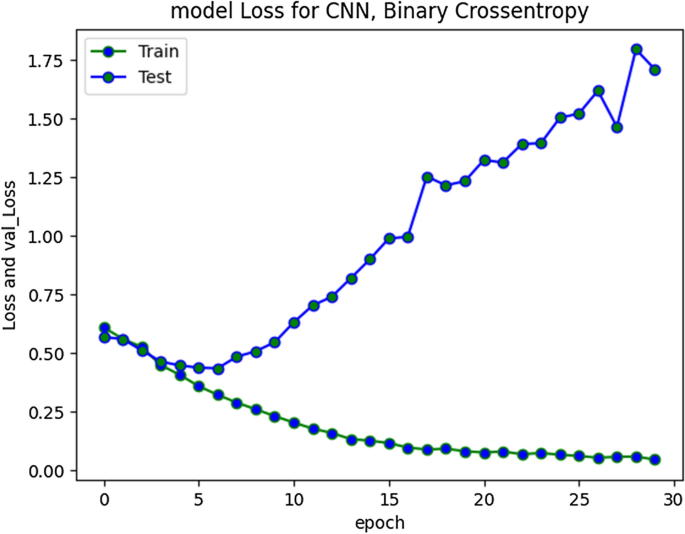
CNN Model loss plot- Binary Cross entropy for 30 epochs
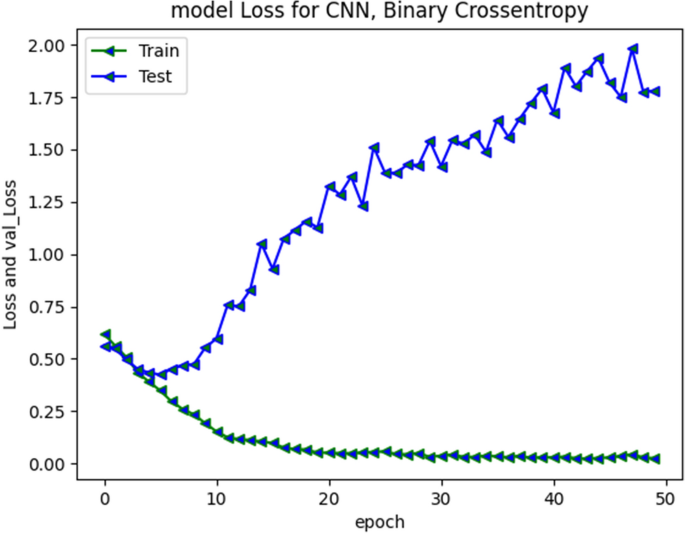
CNN Model loss plot- Binary Cross entropy for 50 epochs
The compiled model results indicating evaluation measures at stabilized epochs are depicted in Table 2 .
Cyberbullying has become an alarming social threat for today’s youth and has recently gained huge attention from research community. This research has addressed the problem of cyberbullying detection in Roman Urdu Language. Since Roman Urdu is highly resource deficient language, having different writing patterns, word structures, and irregularities thus making this work a challenging task. In this work we have presented advanced preprocessing techniques mainly a slang mapping mechanism, domain specific stop word removal, handling encoded formats and formulation of deep learning architecture to detect cyberbullying patterns in Roman Urdu language. We created experiments with vast parameters to build optimal classifier for cyberbullying tweets. The results highlighted that RNN-LSTM and RNN-BiLSTM with concatenation of forward and backward units provided better performance in 20 Epochs as compared to CNN. The existing work can be extended in numerous ways. The future studies can focus on development of ensemble models to uncover harassing and hate speech patterns. Moreover, the incorporation of context-specific features and handling of morphological variations might produce better results.
Availability of data and materials
The used raw dataset in this research is not publicly available. The data that support the findings of this research work are available from the corresponding author, on valid request due to privacy and ethical restrictions.
Abbreviations
Recurrent neural network
Long-short term memory
Bidirectional long-short term memory
Convolutional neural network
Social networking
Right to left
Left to right
True negative
Hellfeldt K, López-Romero L, Andershed H. Cyberbullying and psychological well-being in young adolescence: the potential protective mediation effects of social support from family, friends, and teachers. Int J Environ Res Public Health. 2020;17(1):45.
Article Google Scholar
Dadvar M. Experts and machines united against cyberbullying [PhD thesis]. University of Twente. 2014.
Magsi H, Agha N, Magsi I. Understanding cyber bullying in Pakistani context: causes and effects on young female university students in Sindh province. New Horiz. 2017;11(1):103.
Google Scholar
Qureshi SF, Abbasi M, Shahzad M. Cyber harassment and women of Pakistan: analysis of female victimization. J Bus Soc Rev Emerg Econ. 2020;6(2):503–10.
S. Irfan Ahmed, Cyber bullying doubles during pandemic. https://www.thenews.com.pk/tns/detail/671918-cyber-bullying-doubles-during-pandemic . Accessed 24 Aug 2020.
Shahroz M, Mushtaq MF, Mehmood A, Ullah S, Choi GS. RUTUT: roman Urdu to Urdu translator based on character substitution rules and unicode mapping. IEEE Access. 2020;8:189823–41.
Mehmood F, Ghani MU, Ibrahim MA, Shahzadi R, Mahmood W, Asim MN. A precisely xtreme-multi channel hybrid approach for roman urdu sentiment analysis. IEEE Access. 2020;8:192740–59.
Alotaibi M, Alotaibi B, Razaque A. A multichannel deep learning framework for cyberbullying detection on social media. Electronics. 2021;10(21):2664.
Dinakar K, Reichart R, Lieberman H. Modeling the detection of textual cyberbullying. In: 5th international AAAI conference on weblogs and social media. 2011.
Iwendi C, Srivastava G, Khan S, Maddikunta PKR. Cyberbullying detection solutions based on deep learning architectures. Multimed Syst. 2020. https://doi.org/10.1007/s00530-020-00701-5 .
Salminen J, Hopf M, Chowdhury SA, Jung S, Almerekhi H, Jansen BJ. Developing an online hate classifier for multiple social media platforms. Hum Cent Comput Inf Sci. 2020;10(1):1–34.
Dessì D, Recupero DR, Sack H. An assessment of deep learning models and word embeddings for toxicity detection within online textual comments. Electronics. 2021;10(7):779.
S. A. Özel, E. Saraç, S. Akdemir, and H. Aksu, Detection of cyberbullying on social media messages in Turkish, In: 2017 International Conference on Computer Science and Engineering (UBMK), 2017, pp. 366–370.
E. C. Ates, E. Bostanci, and M. S. Guzel, Comparative Performance of Machine Learning Algorithms in Cyberbullying Detection: Using Turkish Language Preprocessing Techniques, arXiv Prepr. arXiv2101.12718, 2021.
Van Hee C, et al. Automatic detection of cyberbullying in social media text. PLoS ONE. 2018;13(10):e0203794.
Haidar B, Chamoun M, Serhrouchni A. A multilingual system for cyberbullying detection: Arabic content detection using machine learning. Adv Sci Technol Eng Syst J. 2017;2(6):275–84.
Gómez-Adorno H, Bel-Enguix G, Sierra G, Sánchez O, Quezada D. A machine learning approach for detecting aggressive tweets in Spanish, In: IberEval@ SEPLN. 2018. pp. 102–107.
X. Bai, F. Merenda, C. Zaghi, T. Caselli, and M. Nissim, RuG at GermEval: Detecting Offensive Speech in German Social Media, in 14th Conference on Natural Language Processing KONVENS 2018, 2018, p. 63.
B. Birkeneder, J. Mitrovic, J. Niemeier, L. Teubert, and S. Handschuh, upInf—Offensive Language Detection in German Tweets, In: Proceedings of the GermEval 2018 Workshop, 2018, pp. 71–78.
J. M. Schneider, R. Roller, P. Bourgonje, S. Hegele, and G. Rehm, Towards the Automatic Classification of Offensive Language and Related Phenomena in German Tweets, In: 14th Conference on Natural Language Processing KONVENS 2018, 2018, p. 95.
H. Margono, X. Yi, and G. K. Raikundalia, Mining Indonesian cyber bullying patterns in social networks, In: Proceedings of the Thirty-Seventh Australasian Computer Science Conference-Volume 147, 2014, pp. 115–124.
H. Nurrahmi and D. Nurjanah, Indonesian Twitter Cyberbullying Detection using Text Classification and User Credibility, In: 2018 International Conference on Information and Communications Technology (ICOIACT), 2018, pp. 543–548.
A. Bohra, D. Vijay, V. Singh, S. S. Akhtar, and M. Shrivastava, A Dataset of Hindi-English Code-Mixed Social Media Text for Hate Speech Detection, In: Proceedings of the Second Workshop on Computational Modeling of People’s Opinions, Personality, and Emotions in Social Media, 2018, pp. 36–41.
A. Roy, P. Kapil, K. Basak, and A. Ekbal, An ensemble approach for aggression identification in english and hindi text, In: Proceedings of the First Workshop on Trolling, Aggression and Cyberbullying (TRAC-2018), 2018, pp. 66–73.
Association for Computational Linguistics. https://www.aclweb.org/portal/content/deadline-extension-first-task-automatic-cyberbullying-detection-polish-language . Accessed 09 May 2019.
Ghosh R, Nowal S, Manju G. Social media cyberbullying detection using machine learning in bengali language. Int J Eng Res Technol. 2021. https://doi.org/10.1109/ICECE.2018.8636797 .
Talpur KR, Yuhaniz SS, Sjarif NNBA, Ali B. Cyberbullying detection in Roman Urdu language using lexicon based approach. J Crit Rev. 2020;7(16):834–48. https://doi.org/10.31838/jcr.07.16.109 .
J. Brownlee, Imbalanced Classification, December 23, 2019. https://machinelearningmastery.com . Accessed 10 May 2021.
Arif M. A systematic review of machine learning algorithms in cyberbullying detection: future directions and challenges. J Inf Secur Cybercrimes Res. 2021;4(1):1–26.
A. Dewani, M. Ali Memon, and S. Bhatti, Development of Computational Linguistic Resources for Automated Detection of Textual Cyberbullying Threats in Roman Urdu Language, 3C TIC. Cuad. Desarro. Apl. a las TIC, 101–121., p. 17, 2021.
Shahid F, Zameer A, Muneeb M. Predictions for COVID-19 with deep learning models of LSTM, GRU and Bi-LSTM. Chaos Solitons Fractals. 2020;140:110212.
M. Cliche, “BB_twtr at SemEval-2017 task 4: Twitter sentiment analysis with CNNs and LSTMs,” arXiv Prepr. arXiv1704.06125, 2017.
W. Zaremba, I. Sutskever, and O. Vinyals, Recurrent neural network regularization, arXiv Prepr. arXiv1409.2329, 2014.
Xu G, Meng Y, Qiu X, Yu Z, Wu X. Sentiment analysis of comment texts based on BiLSTM. Ieee Access. 2019;7:51522–32.
S. Minaee, E. Azimi, and A. Abdolrashidi, Deep-sentiment: Sentiment analysis using ensemble of cnn and bi-lstm models, arXiv Prepr. arXiv1904.04206, 2019.
Uysal AK, Gunal S. The impact of preprocessing on text classification. Inf Process Manag. 2014;50(1):104–12.
Vijayarani S, Ilamathi MJ, Nithya M. Preprocessing techniques for text mining-an overview. Int J Comput Sci Commun Networks. 2015;5(1):7–16.
Pycontractions 2.0.1. https://pypi.org/project/pycontractions/ . Accessed 17 Nov 2021.
API Documentation. https://www.tensorflow.org/api_docs . Accessed 21 Oct 2020.
NumPy. https://numpy.org/ . Accessed 18 Nov 2021.
Download references
Acknowledgements
We would like to thank Institute of Information and Communication Technology, Mehran University of Engineering & Technology, for providing resources and funding, necessary to accomplish this research work.
This research has been performed at Institute of Information and Communication Technology, Mehran University of Engineering and Technology, Pakistan and is fully funded under MUET funds for postgraduate students.
Author information
Authors and affiliations.
Institute of Information and Communication Technologies, Department of Software Engineering, Mehran University of Engineering & Technology, Jamshoro, Sindh, Pakistan
Amirita Dewani, Mohsin Ali Memon & Sania Bhatti
You can also search for this author in PubMed Google Scholar
Contributions
Corresponding author is the main contributor of this work from conception, drafting, algorithms development and implementation to analysis of results. Other authors are research supervisors who provided valuable guidance for work and content improvement. All authors read and approved the final manuscript.
Corresponding author
Correspondence to Amirita Dewani .
Ethics declarations
Ethics approval and consent to participate.
Not applicable.
Consent for publication
Competing interests.
The authors declare that they have no competing or conflicts of interest to report regarding the present study.
Additional information
Publisher's note.
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution 4.0 International License, which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if changes were made. The images or other third party material in this article are included in the article's Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article's Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by/4.0/ .
Reprints and permissions
About this article
Cite this article.
Dewani, A., Memon, M.A. & Bhatti, S. Cyberbullying detection: advanced preprocessing techniques & deep learning architecture for Roman Urdu data. J Big Data 8 , 160 (2021). https://doi.org/10.1186/s40537-021-00550-7
Download citation
Received : 03 September 2021
Accepted : 10 December 2021
Published : 22 December 2021
DOI : https://doi.org/10.1186/s40537-021-00550-7
Share this article
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
- Advanced preprocessing
- Deep learning
- Hate speech detection
- Cyberbullying

Internet use statistically associated with higher wellbeing, finds new global Oxford study
Links between internet adoption and wellbeing are likely to be positive, despite popular concerns to the contrary, according to a major new international study from researchers at the Oxford Internet Institute, part of the University of Oxford.
The study encompassed more than two million participants psychological wellbeing from 2006-2021 across 168 countries, in relation to internet use and psychological well-being across 33,792 different statistical models and subsets of data, 84.9% of associations between internet connectivity and wellbeing were positive and statistically significant.
The study analysed data from two million individuals aged 15 to 99 in 168 countries, including Latin America, Asia, and Africa and found internet access and use was consistently associated with positive wellbeing.
Assistant Professor Matti Vuorre, Tilburg University and Research Associate, Oxford Internet Institute and Professor Andrew Przybylski, Oxford Internet Institute carried out the study to assess how technology relates to wellbeing in parts of the world that are rarely studied.
Professor Przybylski said: 'Whilst internet technologies and platforms and their potential psychological consequences remain debated, research to date has been inconclusive and of limited geographic and demographic scope. The overwhelming majority of studies have focused on the Global North and younger people thereby ignoring the fact that the penetration of the internet has been, and continues to be, a global phenomenon'.
'We set out to address this gap by analysing how internet access, mobile internet access and active internet use might predict psychological wellbeing on a global level across the life stages. To our knowledge, no other research has directly grappled with these issues and addressed the worldwide scope of the debate.'
The researchers studied eight indicators of well-being: life satisfaction, daily negative and positive experiences, two indices of social well-being, physical wellbeing, community wellbeing and experiences of purpose.
Commenting on the findings, Professor Vuorre said, “We were surprised to find a positive correlation between well-being and internet use across the majority of the thousands of models we used for our analysis.”
Whilst the associations between internet access and use for the average country was very consistently positive, the researchers did find some variation by gender and wellbeing indicators: The researchers found that 4.9% of associations linking internet use and community well-being were negative, with most of those observed among young women aged 15-24yrs.
Whilst not identified by the researchers as a causal relation, the paper notes that this specific finding is consistent with previous reports of increased cyberbullying and more negative associations between social media use and depressive symptoms among young women.
Adds Przybylski, 'Overall we found that average associations were consistent across internet adoption predictors and wellbeing outcomes, with those who had access to or actively used the internet reporting meaningfully greater wellbeing than those who did not'.
'We hope our findings bring some greater context to the screentime debate however further work is still needed in this important area. We urge platform providers to share their detailed data on user behaviour with social scientists working in this field for transparent and independent scientific enquiry, to enable a more comprehensive understanding of internet technologies in our daily lives.'
In the study, the researchers examined data from the Gallup World Poll, from 2,414,294 individuals from 168 countries, from 2006-2021. The poll assessed well-being with face-to-face and phone surveys by local interviewers in the respondents’ native languages. The researchers applied statistical modelling techniques to the data using wellbeing indicators to test the association between internet adoption and wellbeing outcomes.
Watch the American Psychological Association (APA) video highlighting the key findings from the research.
Download the paper ‘ A multiverse analysis of the associations between internet use and well-being ’ published in the journal Technology, Mind and Behaviour, American Psychological Association.
DISCOVER MORE
- Support Oxford's research
- Partner with Oxford on research
- Study at Oxford
- Research jobs at Oxford
You can view all news or browse by category
Vanderbilt computer scientist shares personal story of resilience and strength in new book from the Women of Association for Computing Machinery
Brenda Ellis
May 13, 2024, 7:04 PM

Vanderbilt computer scientist Pamela Wisniewski has contributed significantly to the human-computer interaction research field and is a leading scholar in adolescent online safety. Her personal journey is prominently featured in a recently published book, “ Rendering History: The Women of ACM-W ” that celebrates the 30 th birthday of the Association for Computing Machinery’s Committee on Women in Computing (ACM-W).
“I am excited to share my personal story as a woman in computing. It is shared alongside other amazing and high-profile women—deans, directors, department chairs, authors and editors—in computing,” said Wisniewski, Flowers Family Fellow in Engineering and associate professor of computer science. “ I am extremely honored and humbled to be included in this compilation.”
Many of the 38 women profiled share intimate details of their personal and professional lives. They come from North and South America, Europe and Asia and reveal the motivations, struggles, and triumphs in their transformative work that has reshaped the computing landscape for women and young girls. The main theme of the book is the organization’s maturation from a US-centric organization to a global leader in supporting the advancement of women in computer science. Many of the women have been pioneers in computing and its roles in society, and in ACM-W.

“I built my research career around promoting the online safety and well-being of youth. This includes helping teens be more resilient against cyberbullying and sexual predation risks online,” said Wisniewski, who reflects that technology is a double-edged sword that can serve both to harm and protect young people.
Wisniewski’s work on adolescent online safety has been recognized nationally and internationally by the U.S. Federal Trade Commission, Netherland’s Down to Zero Alliance on combatting the online sexual exploitation of children, and most recently, by the White House’s Biden-Harris Task Force on Kids Online Health and Safety. She is an ACM Senior Member, Computing Research Association CCC Council Member, and a non-resident fellow of the Center for Democracy and Technology.
Wisniewski has authored more than 150 peer-reviewed publications and won multiple best papers (top 1%) and best paper honorable mentions (top 5%) at ACM SIGCHI conferences. Her research has been featured by popular news media outlets, including Scientific American , ABC News , NPR , Psychology Today , and U.S. News and World Report . She is the recipient of the National Science Foundation’s prestigious CAREER Award for her innovative, teen-centric approach to adolescent online safety, and was the first computer scientist to ever be selected as a William T. Grant Scholar for her work on reducing digital inequality in youth outcomes.
“Given my tumultuous childhood, resilience-based approaches that help youth thrive in the face of adversity are near and dear to my heart. I frame my research through a lens of social-ecological resilience—the support systems like family, friends, and community in which youth are embedded—rather than viewing resilience as an immutable trait of certain individuals.”
In that way, Wisniewski says if individuals fail to thrive, it isn’t necessarily a personal failure as much as a failure of the systems of support surrounding them. “Resilience is building stronger support systems and communities around people to protect and empower them.”
The book is edited by Gloria Townsend, an author, computer scientist, and DePauw University professor internationally known for her support of women in computing. The book was published April 10, 2024, by the Association for Computing Machinery, New York, NY.
Contact: [email protected]
Explore Story Topics
- Computer Science
- Uncategorized
- Association for Computing Machinery
- Pamela Wisniewski
- Rendering History: The Women of ACM-W

IMAGES
VIDEO
COMMENTS
Although cyberbullying is still a relatively new field of research, cyberbullying among adolescents is considered to be a serious public health issue that is closely related to adolescents' behavior, mental health and development (16, 17). The increasing rate of Internet adoption worldwide and the popularity of social media platforms among the ...
The nature of cyberbullying. Traditional face-to-face bullying has long been identified as a risk factor for the social and emotional adjustment of perpetrators, targets and bully victims during childhood and adolescence; Reference Almeida, Caurcel and Machado 1-Reference Sourander, Brunstein, Ikomen, Lindroos, Luntamo and Koskelainen 6 bystanders are also known to be negatively affected.
This paper presents an aggregation and summary of recent, primarily academic literature on youth (12-18-year-olds) and cyberbullying. It is important to note that this spotlight is not intended to stand alone. Rather, it seeks to serve as a brief update of a rich corpus of research literature on cyberbullying and is meant as an addendum to
1. DOI: 10.4018/978-1-7998-2360-5.ch001. ABSTRACT. Cyberbullying is t he usage of computerized transmission t o threat en an individual, typically by forwarding messages of an intimidating or ...
1. Introduction. Cyberbullying is an emerging societal issue in the digital era [1, 2].The Cyberbullying Research Centre [3] conducted a nationwide survey of 5700 adolescents in the US and found that 33.8 % of the respondents had been cyberbullied and 11.5 % had cyberbullied others.While cyberbullying occurs in different online channels and platforms, social networking sites (SNSs) are fertile ...
Addressing the second research question, women consistently led research in Cyberbullying, with primary authorship in over 62% of the papers analyzed as part of this study. Regarding quality, female authors contribute to over 50% of the papers in Top 500 publications and over 50% of the citations.
Recognized as complex and relational, researchers endorse a systems/social-ecological framework in examining bullying and cyberbullying. According to this framework, bullying and cyberbullying are examined across the nested social contexts in which youth live—encompassing individual features; relationships including family, peers, and educators; and ecological conditions such as digital ...
cyberbullying, in which individuals or groups of individuals use the media to inflict emotional distress on. other individuals (Bocij 2004). According to a rece nt study of 743 teenager s and ...
The system's view, therefore, extends the research into cyberbullying beyond examining the cyberbullying-victim interaction. Examining cyberbullying demands the exploration of the interaction among its components (e.g., cyberbullies, cybervictims, peers, teachers, and administrators) rather than simply focusing on any group in isolation.
entitled 'New bottle but old wine: A research of cyberbullying in schools', shows that 54% of. the 177 seventh grade students in Canada had been bullied offline, and 25% had been bullied ...
A review of literature is provided and results and analysis of the survey are discussed as well as recommendations for future research. Erdur-Baker's (2010) study revealed that 32% of the students were victims of both cyberbullying and traditional bullying, while 26% of the students bullied others in both cyberspace and physical environments ...
Cyberbullying victimization is becoming more prevalent and adversely affects mental health. This research explores the relationship between the two variables and the underlying mechanism, especially for children, as the impact of mental health in childhood might last a lifetime. Primary school students (N = 344; Mage = 9.90; 43.90% girls) completed self-report questionnaires regarding ...
School bullying research has a long history, stretching all the way back to a questionnaire study undertaken in the USA in the late 1800s (Burk, 1897).However, systematic school bullying research began in earnest in Scandinavia in the early 1970s with the work of Heinemann and Olweus ().Highlighting the extent to which research on bullying has grown exponentially since then, Smith et al. found ...
ABSTRACT. Bullying is a topic of international interest that attracts researchers from various disciplinary areas, including education. This bibliometric study aims to map out the landscape of educational research on bullying and cyberbullying, by performing analyses on a set of Web of Science Core Collection-indexed documents published between 1991-2020.
Running Head: CYBERBULLYING: IMPACTING TODAY'S YOUTH . Cyberbullying: Impacting Today's Youth. by Hillary Noll, B.A. MSW Clinical Research Paper Presented to the Faculty of the School of Social Work St. Catherine University and the University of St. Thomas St. Paul, Minnesota in Partial fulfillment of the Requirements for the Degree of
Cyber bullying is an online aggressive behaviour in the digital space. Bullying is a form of peer aggression which can be as damaging as any form of conventional aggression (Mickie, 2011). The problem investigated in this research concerns cyber bullying that disturbs university students psychologically and emotionally.
The MWU test provides insights into addressing research questions (RQ1) regarding the dimensions and patterns of cyberbullying (CB) and cyberstalking (CS), as well as RQ3, which examines how victims perceive CB and CS during the pandemic, and RQ4, which investigates the relationship between offenders and victims (full statistical details can be ...
Cyberbullying (aka hate speech, cyberaggression and toxic speech) is a critical social problem plaguing today's Internet users typically youth and lead to severe consequences like low self-esteem, anxiety, depression, hopelessness and in some cases causes lack of motivation to be alive, ultimately resulting in death of a victim [].Cyberbullying incidents can occur via various modalities.
DOI: 10.59585/ijhs.v2i1.325 Corpus ID: 269597967; The Relationship Between Cyberbullying And Self-Esteem In Adolescents At Global Edu High School @article{Maidartati2024TheRB, title={The Relationship Between Cyberbullying And Self-Esteem In Adolescents At Global Edu High School}, author={Maidartati Maidartati and Erna Irawan and Mery Tania and Anggi Saputra and Salsa Bila Firdaus}, journal ...
research. Cyberbullying can cause fear, low self-esteem, social isolation, bad academic performan ce. It can also cause difficulty in crea ting healthy relationships and most importantly, victims ...
Feature papers represent the most advanced research with significant potential for high impact in the field. A Feature Paper should be a substantial original Article that involves several techniques or approaches, provides an outlook for future research directions and describes possible research applications. ... - Cyberbullying victimization ...
Feature papers represent the most advanced research with significant potential for high impact in the field. A Feature Paper should be a substantial original Article that involves several techniques or approaches, provides an outlook for future research directions and describes possible research applications. ... "The Association between ...
The study encompassed more than two million participants psychological wellbeing from 2006-2021 across 168 countries, in relation to internet use and psychological well-being across 33,792 different statistical models and subsets of data, 84.9% of associations between internet connectivity and wellbeing were positive and statistically significant.
Abstract. This paper is an overview of cyberbullying which occurs mostly on social networking sites and issues and challenges in detecting cyberbullying. The topic presented in this paper starts ...
Pamela Wisniewski. Vanderbilt computer scientist Pamela Wisniewski has contributed significantly to the human-computer interaction research field and is a leading scholar in adolescent online safety. Her personal journey is prominently featured in a recently published book, "Rendering History: The Women of ACM-W" that celebrates the 30 th birthday of the Association for Computing Machinery ...