Types of Network Protocols Explained with Functions
This tutorial explains network protocols types and their functions. Learn the most common types of network protocols and how they work in a computer network.

TCP and UDP protocols
TCP stands for Transmission Control Protocol. UDP stands for User Datagram Protocol. Both protocols allow network applications to exchange data between nodes. The main difference between both is that TCP is a connection-oriented protocol while UDP is a connectionless protocol.
When the TCP protocol is used, a special connection is opened up between two network devices, and the channel remains open to transmit data until it is closed. On the other hand, a UDP transmission does not make a proper connection and merely broadcasts its data to the specified network address without any verification of receipt.
To learn more about TCP and UDP, you can check the following tutorial.
TCP features and functions
IP protocol
IP stands for Internet Protocol. This protocol works with TCP and UDP protocols. It provides a unique identity to each node on the computer network. This identity is known as an IP address. An IP address is a software address of the node on a computer network. There are two versions of IP protocol: IPv4 and IPv6. IPv4 uses 32 bits to create an IP address while IPv6 uses 128 bits to create an IP address.
To learn how IP protocol creates and manages IP addresses, you can check the following tutorial.
>IP address classes explained
DNS stands for Domain Name Service. This service allows us to access a node by its name. By default, nodes use IP addresses to identify each other on the network. DNS service allows us to map a name to an IP address. When we access a node by its name, the DNS service translates the name into the IP address. Let's take an example.
Suppose you want to access the home page of Yahoo's site. For this, you enter the following address in your web browser.
https://www.yahoo.com
Your web browser connects the configured DNS server and sends a request to convert the entered address into the IP address. DNS server translates the address into the IP address and sends the IP address of Yahoo's site. Your browser accesses Yahoo's site and displays it on the viewport. Without DNS service, your browser will not be able to access Yahoo's site.
NAT stands for Network Address Translation. This protocol translates one IP address to another. This can be a source address or a destination address. Two basic implementations of NAT can be used: static and dynamic. In the static NAT, a manual translation is performed. In the dynamic NAT, an automatic address translation is performed by an address translation device. Static NAT is used to translate destination IP addresses in packets as they come into your network, but you can translate source addresses also. Dynamic NAT is used to translate source IP addresses in packets as they go out of your network. In dynamic NAT, the global address assigned to the internal user isn’t that important, since outside devices don’t directly connect to your internal users—they just return traffic to them that the inside user requested.
To learn more about NAT, you can check the following tutorial.
> Basic Concepts of NAT Explained in Easy Language
SNMP (Simple Network Management Protocol)
Simple Network Management Protocol is a TCP/IP protocol for monitoring networks and network components. SNMP uses small utility programs called agents to monitor behavior and traffic on the network. These agents can be loaded onto managed devices such as hubs, NIC's, servers, routers, and bridges. The gathered data is stored in a MIB (management information base). To collect the information in a usable form, a management program console polls these agents and downloads the information from their MIBs, which then can be displayed as graphs, charts and sent to a database program to be analyzed.
SMB (Server Message Block)
SMB is a file-sharing protocol. It allows networked computers to transparently access files that reside on remote systems over a variety of networks. The SMB protocol defines a series of commands that pass information between computers. It is mainly used by Microsoft Windows-equipped computers. SMB works through a client-server approach, where a client makes specific requests and the server responds accordingly.
FTP (File Transfer Protocol)
One of the earliest uses of the Internet, long before Web browsing came along, was transferring files between computers. The File Transfer Protocol (FTP) is used to connect to remote computers, list shared files, and either upload or download files between local and remote computers.
FTP runs over TCP, which provides a connection-oriented, guaranteed data-delivery service. FTP is a character-based command interface, although many FTP applications have graphical interfaces. FTP is still used for file transfer purposes, most commonly as a central FTP server with files available for download. Web browsers can make FTP requests to download programs from links selected on a Web page.
TFTP (Trivial File Transfer Protocol)
TFTP is used when a file transfer does not require an acknowledgment packet during file transfer. TFTP is used often in the router configuration. TFTP is similar in operation to FTP. TFTP is also a command-line-based utility.
One of the two primary differences between TFTP and FTP is speed and authentication. Because TFTP is used without acknowledgment packets, it is usually faster than FTP. TFTP does not provide user authentication like FTP and therefore the user must be logged on to the client and the files on the remote computer must be writable. TFTP supports only unidirectional data transfer (unlike FTP, which supports bi-directional transfer). TFTP is operated over port 69.
HTTP (Hypertext Transfer Protocol)
HTTP is often called the protocol of the Internet. HTTP received this designation because most Internet traffic is based on HTTP. When a user requests a Web resource, it is requested using HTTP. The following is a Web request:
http://www.example.com
When a client enters this address into a Web browser, DNS is called to resolve the Fully Qualified Domain Name (FQDN) to an IP address. When the address is resolved, an HTTP get request is sent to the Web server. The Web server responds with an HTTP send response. Such communication is done several times throughout a single session to a Web site. HTTP uses TCP for communication between clients and servers. HTTP operates on port 80.
HTTPS (Hypertext Transfer Protocol Secure)
HTTPS is for Web sites using additional security features such as certificates. HTTPS is used when Web transactions are required to be secure. HTTPS uses a certificate-based technology such as VeriSign.
Certificate-based transactions offer mutual authentication between the client and the server. Mutual authentication ensures the server of the client identity and ensures the client of the server identity. HTTPS, in addition to using certificate-based authentication, encrypts all data packets sent during a session.
SMTP (Simple Mail Transfer Protocol)
SMTP is a standard electronic-mail protocol that handles the sending of mail from one SMTP to another SMTP server. To accomplish the transport, the SMTP server has its MX (mail exchanger) record in the DNS database that corresponds to the domain for which it is configured to receive mail.
When equipped for two-way communication, mail clients are configured with the address of a POP3 server to receive mail and the address of an SMTP server to send mail. The clients can configure server parameters in the properties sheets of the mail client, basing the choices on an FQDN or an IP address.
POP3 / IMAP4 (Post Office Protocol version 3 / Internet Message Access Protocol version 4)
Post Office Protocol 3 (POP3) and Internet Message Access Protocol 4 (IMAP4) are two application-layer protocols used for electronic messaging across the Internet. POP3 is a protocol that involves both a server and a client. A POP3 server receives an e-mail message and holds it for the user. A POP3 client application periodically checks the mailbox on the server to download mail. POP3 does not allow a client to send mail, only to receive it. POP3 transfers e-mail messages over TCP port 110.
IMAP4 is an alternate e-mail protocol. IMAP4 works in the same way as POP3. In this, an e-mail message is held on a server and then downloaded to an e-mail client application. Users can read their e-mail messages locally in their e-mail client application, but they can't send an e-mail message using IMAP4. When users access e-mail messages via IMAP4, they have the option to view just the message header, including its title and the sender's name, before downloading the body of the message. Users can create, change, or delete folders on the server, as well as search for messages and delete them from the server.
Telnet stands for Telecommunication Network. It is a virtual terminal protocol. It allows a user to access a system remotely. In remote control, a session appears in which the user can manage the files on the remote computer, although the session appears to be functioning locally. Telnet is an early version of a remote control application.
Telnet is very basic; it offers solely character-based access to another computer. You can often use Telnet to manage equipment that lacks a monitor. For example, most routers have Telnet enabled so that the administrator can log in and manage the router. Telnet also provides a quick check to make certain that network connectivity is functioning. Because Telnet sits at the application layer, if it can connect to a remote host, you can be certain that network connectivity between the two hosts is operational, as well as all lower-layer protocols.
SSH (Secure Shell)
SSH is a program for logging in to and executing commands on a remote machine. It provides secure encrypted communications between two untrusted hosts over an insecure network. When SSH connects and logs in to a specified computer, the user must prove his/her identity to the remote machine which is transmitted across the connection using data encryption. This process makes SSH impervious to Internet eavesdroppers who might otherwise steal account information.
ICMP (Internet Control Message Protocol)
ICMP provides network diagnostic functions and error reporting. ICMP also provides a little network help for routers. When a router is being overloaded with route requests, the router sends a source quench message to all clients on the network, instructing them to slow their data requests to the router.
To learn ICMP protocol in detail, you can check the following tutorial.
ARP (Address Resolution Protocol)
The Address Resolution Protocol (ARP) is an Internet layer protocol that helps TCP/IP network components find other devices in the same broadcast domain. ARP uses a local broadcast (255.255.255.255) at layer 3 and FF:FF:FF:FF:FF:FF at layer 2 to discover neighboring devices.
RARP (Reverse Address Resolution Protocol)
RARP is sort of the reverse of an ARP. In an ARP, the device knows the layer 3 address, but not the data link-layer address. With a RARP, the device doesn’t have an IP address and wants to acquire one. The only address that this device has is a MAC address. Common protocols that use RARP are BOOTP and DHCP
NTP (Network Time Protocol)
The Network Time Protocol is used to synchronize the time of a computer client or server to another server or reference time source, such as a radio or satellite receiver or modem. It provides accuracy's typically within a millisecond on LANs and up to a few tens of milliseconds on WANs.
SCP (Secure Copy Protocol)
Secure Copy or SCP is a means of securely transferring computer files between a local and a remote host or between two remote hosts, using the Secure Shell (SSH) protocol. The protocol itself does not provide authentication and security; it expects the underlying protocol, SSH, to secure this. The SCP protocol implements file transfers only. It does so by connecting to the host using SSH and there executes an SCP server (SCP). SCP server connects with SCP client and transfers files securely.
LDAP (Lightweight Directory Access Protocol)
Lightweight Directory Access Protocol, or LDAP, is a networking protocol for querying and modifying directory services running over TCP/IP. A directory is a set of information with similar attributes organized logically and hierarchically. The most common example is the telephone directory, which consists of a series of names organized alphabetically, with an address and phone number attached.
IGMP (Internet Group Multicast Protocol)
The Internet Group Management Protocol is a communications protocol used to manage the membership of Internet Protocol multicast groups. IGMP is used by IP hosts and adjacent multicast routers to establish multicast group memberships. It is an integral part of the IP multicast specification, like ICMP for unicast connections. IGMP can be used for online video and gaming and allows more efficient use of resources when supporting these uses.
LPD (Line Printer Daemon) /LPR (Line Printer Remote)
The Line Printer Daemon protocol/Line Printer Remote protocol (or LPD, LPR) also known as the Berkeley printing system, is a set of programs that provide printer spooling and network print server functionality for Unix-like systems.
The most common implementations of LPD are the official BSD UNIX operating system and the LPRng project. The Common Unix Printing System (or CUPS), which is more common on modern Linux distributions, borrows heavily from LPD.
That's all for this tutorial. In this tutorial, we discussed some most common networking protocols and their functions. If you have suggestions or feedback about this tutorial, you can mail us or comment on our Facebook page.
By ComputerNetworkingNotes Updated on 2024-06-09
ComputerNetworkingNotes Networking Tutorials Types of Network Protocols Explained with Functions
- Basic Networking Terms and Definitions
- Anonymous user and Authentication Method
- AAA Security in Computer Network
- Access Control Type Explained
- SCSI, PATA, SATA, and NVMe Explained
- Why Do Hard Disks use Serial Transmission?
- Differences between Hard disks and SSDs Explained
- Megabytes (MB) V/s Mebibytes (MiB) Differences Explained
- GUID Partition Table (GPT) Explained
- BIOS v/s UEFI Explained
We do not accept any kind of Guest Post. Except Guest post submission, for any other query (such as adverting opportunity, product advertisement, feedback, suggestion, error reporting and technical issue) or simply just say to hello mail us [email protected]
All Common Network Protocols Explained

Network protocol is a set of rules that devices use to communicate with each other over a network.
It’s similar to how people follow certain behaviors and procedures when talking to each other.
They specify things like how data packets should be structured, how devices should identify themselves, and how errors & conflicts should be handled.
Network protocols can be categorized into these three main types: Communication , Security , and Management .

#1. Communication Protocols
These protocols focus on enabling the exchange of data & information between devices on a network. They determine how data is formatted, transmitted, and received, which ensures effective communication. Examples are HTTP/HTTPS, FTP, TCP, and UDP.
#2. Security Protocols
Security protocols are designed to protect the confidentiality & authenticity of data as it traverses a network. They establish secure channels for communication and make sure that sensitive information is not vulnerable to interception or tampering.
Examples include SSL/TLS for encryption, SSH for secure remote access, and secure variants of email protocols like SMTPS and POP3S.
#3. Management Protocols
Management protocols are used for the administration, monitoring, and control of network devices/resources. They help network administrators configure and troubleshoot network components efficiently.
Some examples are DHCP for dynamic IP address allocation, SNMP for network device management, ICMP for diagnostic purposes, and BGP for routing & reachability information.
Let’s discuss some common protocols from each category.
Communication Protocols
HTTP stands for Hypertext Transfer Protocol.
It is a fundamental protocol used for communication between a web browser and a server.
It is an application layer protocol that operates on top of the OSI model .
When you enter a URL in your web browser and press enter, it sends an HTTP request to a web server which then processes the request & sends back an HTTP response containing the requested information.
This could be a web page, an image, a video, or any other resource hosted on the server.

HTTP is a stateless protocol. It means each request from a client to a server is treated as an independent & isolated transaction.
The server does not maintain any information about previous requests from the same client. This simplicity is one of the reasons why HTTP is so widely used.
HTTP defines several request methods, including GET (retrieve data), POST (send data to be processed), PUT (update a resource), DELETE (remove a resource), and others. These methods determine the type of operation the client wants to perform on the server.
Generally, HTTP responses include a status code that indicates the outcome of the request.
For example – A status code of 200 indicates a successful request, while 404 indicates that the requested resource was not found.
And HTTP has seen several versions over the years, with HTTP/1.1 being one of the most widely used versions for a long time.
HTTP/2 and HTTP/3 (also known as QUIC) were developed to improve the performance.
HTTPS stands for Hypertext Transfer Protocol Secure.
It is an extension of the HTTP protocol used for secure communication over computer networks.
It adds a layer of security to standard HTTP by encrypting the data exchanged between a browser & web server using cryptographic protocols like SSL/TLS . Even if someone intercepts the data being transmitted, they cannot easily read or decipher it.
HTTPS includes a form of server authentication.
When a browser connects to a website over HTTPS, the website presents a digital certificate which is issued by a trusted Certificate Authority (CA).
This certificate verifies the identity of the website, which makes sure that the client is connecting to the intended server and not a malicious one.

Websites that use HTTPS are identified by “https://” at the beginning of their URLs. The use of this prefix indicates that the website is using a secure connection.
HTTPS generally uses port 443 for communication – whereas HTTP uses port 80. Web servers can easily differentiate between secure & non-secure connections using this distinction.
Search engines like Google prioritize websites that use HTTPS in their search rankings.
Browsers can also warn users when a secure HTTPS webpage contains elements ( images or scripts) served over an unsecured HTTP connection. This is known as “mixed content” and can compromise security.
Here is a detailed article on how to get an SSL Certificate for a Website . Feel free to visit this page.
File Transfer Protocol (FTP) is a standard network protocol used for transferring files between a client and a server on a computer network.
FTP operates on the client-server model. That means the client initiates a connection to another computer (the server) to request & transfer files.
FTP uses two ports for communication and can operate in two modes: Active mode and Passive mode.
Port 21 is used for the control connection where commands & responses are sent between the client and server.
Active mode is the traditional mode that works on the principle of the client-server model. An additional port (usually in the range of 1024-65535) is opened for data transfer here.
On the other hand, Passive mode is often used when the client is behind a firewall or NAT device and the server opens a random high-numbered port for data transfer.

FTP generally requires authentication to access files on the server. Users has to provide a username and password to log in.
Some FTP servers also support anonymous access. So, users can log in with a generic username like “anonymous” or “FTP” and use their email address as a password.
FTP supports two data transfer modes: ASCII mode & binary mode.
ASCII mode is used for text files and Binary mode is used for non-text files like images and executables. The mode is set based on the type of file being transferred.
Traditional FTP is not a secure protocol as it transmits data including usernames and passwords in plain text.
Secure FTP (SFTP) and FTP over SSL/TLS (FTPS) are more secure alternatives that encrypt the data transfer to protect sensitive information.
Here is a detailed article on SFTP vs FTPS and which protocol to use.
Transmission Control Protocol (TCP) is one of the main transport layer protocols in the IP suite.
It plays a major role in providing reliable and ordered data transmission between devices over IP networks.
TCP establishes a connection between the sender and receiver before any data transfer begins. This connection setup involves a three-way handshake (SYN, SYN-ACK, ACK) and a connection termination process when the data exchange is complete.
It also supports full-duplex communication that allows data to be sent and received simultaneously in both directions within the established connection.

Generally, TCP monitors network conditions & adjusts its transmission rate to avoid network congestion.
This protocol includes error-checking mechanisms to detect and correct data corruption during transmission. If a data segment is found to be corrupted, the receiver requests retransmission.
TCP uses port numbers to identify specific services or applications on a device. Port numbers help route incoming data to the correct application.
The receiver in a TCP connection sends acknowledgments (ACKs) to confirm the receipt of data segments. If the sender doesn’t receive an ACK within a certain time – it retransmits the data segment.
TCP maintains connection state information on both the sender and receiver sides. This information helps keep track of the sequence of data segments & manage the connection.
IP stands for Internet Protocol.
It is a core protocol that enables communication & data exchange in computer networks, including the global network we know as the Internet.
IP uses a numerical addressing system to identify devices on a network. These numerical addresses are called IP addresses, and they can be either IPv4 or IPv6.
IPv4 addresses are typically in the form of four sets of decimal numbers (e.g., 192.168.1.1), while IPv6 addresses are longer and use hexadecimal notation.

IP routes the data packets between devices on different networks.
Routers & switches play a major role in directing these packets to their intended destinations based on their IP addresses.
Generally, IP uses a packet-switching methodology. That means data is broken into smaller packets for transmission across the network. Each packet contains a source and destination IP address that allows routers to make forwarding decisions.
IP is considered a connectionless protocol. It does not establish a dedicated connection between the sender & receiver before transmitting data.
Each packet is treated independently and can take different routes to reach its destination.
UDP stands for User Datagram Protocol.
It is a connectionless & lightweight protocol that provides a way to send data over a network without establishing a formal connection.
Unlike the TCP protocol, UDP does not establish a connection before sending data. It simply packages the data into datagrams and sends them to the destination.
It does not guarantee the delivery of data and it doesn’t implement mechanisms for error detection and correction. If a packet is lost or arrives out of order, it is up to the application layer to handle this.

UDP has less overhead than TCP because it doesn’t include features like flow control, error correction, or acknowledgments. This makes it faster but less reliable.
It also doesn’t have built-in congestion control mechanisms, so it’s possible to flood a network with UDP traffic which potentially causes congestion.
UDP is commonly used in situations where low latency and high-speed data transmission are more critical than guaranteed delivery. Some common examples are real-time audio and video streaming, online gaming, DNS , and some IoT applications.
The best thing about UDP is its multiplexing feature. It allows multiple applications on the same device to use the same UDP port which differentiates the data streams using port numbers.
let’s understand UDP with a simple example.
Imagine you want to send a message to your friend across a noisy playground using a bouncy ball. You decide to use UDP, which is like throwing the ball without any formal conversation. Here’s how it works:
- You write your message on a piece of paper and wrap it around the ball.
- You throw the ball in the direction of your friend. You don’t wait for your friend to catch it or acknowledge that they received it; you just throw it and hope they catch it.
- The ball bounces and reaches your friend, who tries to catch it. But sometimes, because of the noise it might bounce off their hands or arrive out of order.
- Your friend reads the message on the paper, and if they caught the ball successfully – they get the message. If not, they might miss it, and you won’t know because you didn’t have a way to check.
So, in this example:
The ball represents the UDP protocol which sends data without establishing a formal connection.
You sending the ball without waiting for a response is like UDP being connectionless and not ensuring delivery.
The possibility of the ball bouncing or getting lost symbolizes the lack of reliability in UDP.
Your friend reading the message is like the application layer handling the data received through UDP, which possibly deals with any missing data.
Security Protocols
SSH stands for Secure Shell.
It is a network protocol used for secure communication between a client and a server over an unsecured network. It provides a way to remotely access & manage devices over a command-line interface with a high level of security.
SSH uses cryptographic techniques to authenticate both the client and the server. This makes sure that you are connecting to the correct server and that the server can verify your identity before allowing access.
All data transmitted over an SSH connection is encrypted, which makes it difficult for anyone intercepting the communication to eavesdrop on the data being exchanged.
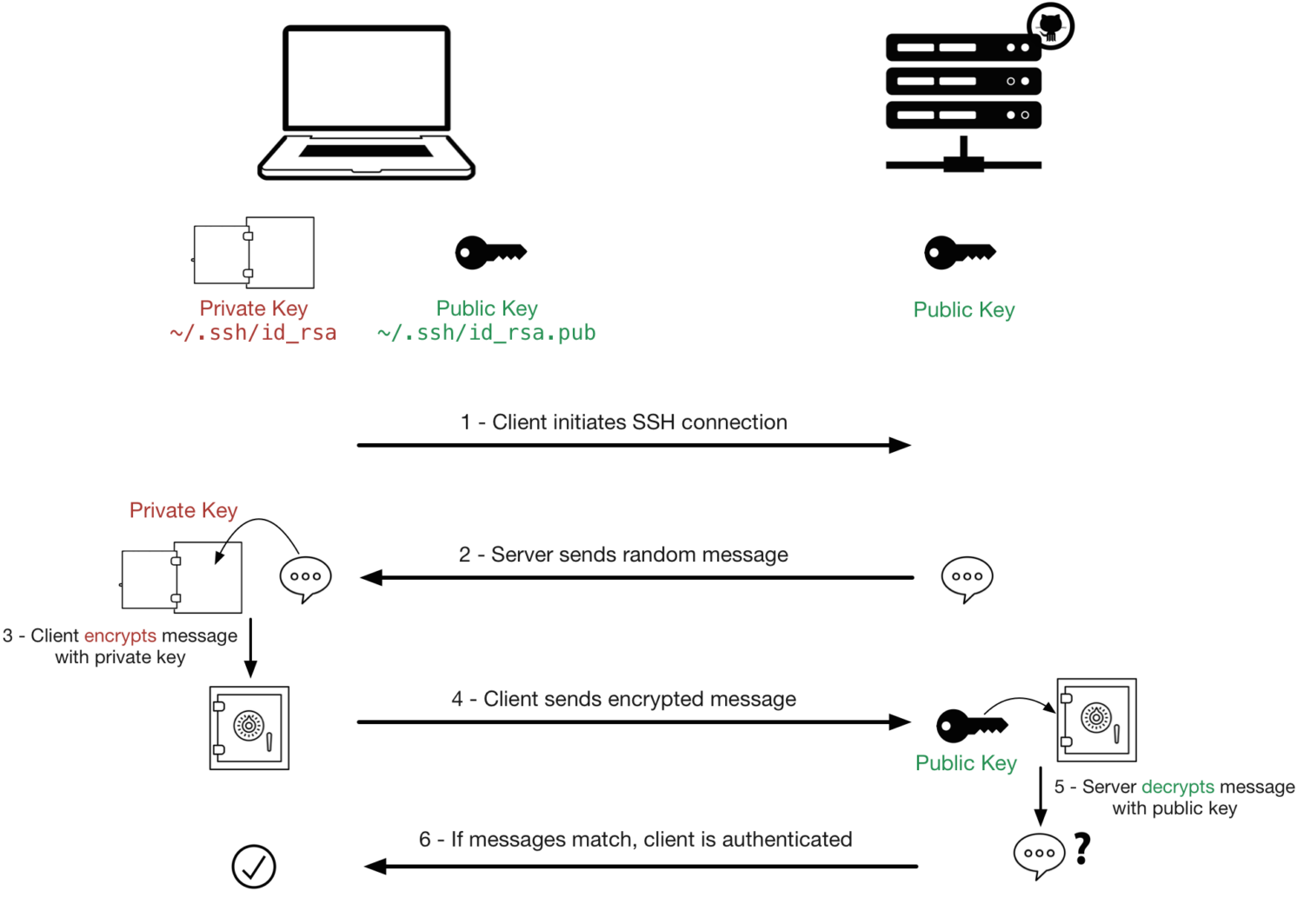
SSH uses a key pair for authentication. The key pair consists of a public key (which is shared with the server) and a private key (which you keep secret).
Here is an article on how it works – SSH Passwordless Login
When you connect to an SSH server, your client uses your private key to prove your identity.
Along with this, It also supports traditional username & password authentication. However, this is less secure and is often discouraged, especially for internet-facing servers.
SSH uses port 22 for communication by default – but this can be changed for security reasons. Changing the port number can help reduce automated attacks.
SSH is commonly used for remote server administration, file transfer (with tools like SCP and SFTP), and secure access to remote command-line interfaces.
It’s widely used in the administration of Unix-like operating systems and is also available on Windows through various software solutions.
SMTP stands for Simple Mail Transfer Protocol.
It is a standard protocol responsible for sending outgoing email messages from a client or email server to an email server on the recipient’s end.
SMTP is a fundamental part of email communication, and it works in conjunction with other email protocols like IMAP/POP3 to enable the complete email lifecycle, including sending, receiving, and storing email messages.
When you compose an email and click “send” in your email client, it uses SMTP to relay the message to your email provider’s server.

It uses port 25 for unencrypted communication & port 587 for encrypted communication (using STARTTLS). Port 465 was also used for encrypted SMTP communication but is less common.
Many SMTP servers require authentication to send emails to prevent unauthorized use. Authentication methods like username and password or more secure methods like OAuth are used.
These SMTP servers are often used as relays, which means they accept outgoing emails from clients (e.g., your email app) and forward them to the recipient’s email server. This helps route emails across the Internet.
Communication can be secured using encryption via TLS or SSL – especially when sending sensitive or confidential information via email.
Management Protocols
POP3 stands for Post Office Protocol version 3.
It is one of the most common email retrieval protocols used for fetching email messages from a mail server to an email client application.
POP3 is designed to work in a “store-and-forward” manner. It retrieves emails from the server and then typically deletes them from the server after storing a copy on the client’s device.
Some email clients provide an option to leave a copy of the email on the server – but this is not the default behavior.
It uses port 110 for unencrypted communication. Port 995 is commonly used for secure POP3 communication using TLS/SSL .
POP3 is a stateless protocol. That means it does not keep track of the emails you’ve already downloaded. Each time you connect to the server, it retrieves all unread messages. This can lead to synchronization issues if you access your email from multiple devices.

POP3 is primarily designed to retrieve emails from the inbox. It may not support the retrieval of emails from other folders on the server, such as sent items or drafts.
Since POP3 doesn’t synchronize email folders between the server and the client – Actions taken on one device (e.g., deleting an email) won’t be reflected on other devices.
It’s recommended to use the secure version of POP3 (POP3S or POP3 over SSL/TLS), which encrypts the communication between the email client and server to improve security.
POP3 is less commonly used today compared to IMAP (Internet Message Access Protocol). It provides more advanced features like folder synchronization & allows multiple devices to manage the same mailbox more effectively.
BGP stands for Border Gateway Protocol.
It is a standardized exterior gateway protocol used in networking to exchange routing & reachability information between autonomous systems (ASes).
An autonomous system is a collection of IP networks and routers under the control of a single organization that presents a common routing policy to the Internet.
BGP is a path vector protocol. That means it keeps track of the path (list of autonomous systems) that data packets take to reach their destination. This information helps BGP routers make routing decisions based on policies & path attributes.

It’s primarily used to determine the best path for data to traverse when crossing multiple networks operated by different organizations or ISPs.
Also supports route aggregation that helps reduce the size of the global routing table by summarizing multiple IP prefixes into a single route announcement.
BGP protocol uses various mechanisms to prevent routing loops, including the use of the AS path attribute & the split-horizon rule.
It is used in both the public internet and private networks.
In the public internet, it’s used to exchange routing information between ISPs and large networks. In private networks, it’s used for internal routing and connecting to the internet through a border router.
DHCP stands for Dynamic Host Configuration Protocol.
It is used to automatically assign IP addresses & other network configuration settings to devices on a TCP/IP network.
The DHCP process generally involves four main stages:
DHCP Discover
When a device joins a network – it sends out a DHCP Discover broadcast message to find available DHCP servers.
DHCP servers on the network respond to the DHCP Discover message with a DHCP Offer. Each server provides an IP address and related configuration options.
DHCP Request
The device selects one of the DHCP Offers & sends a DHCP Request message to the chosen server that requests the offered IP address.
DHCP Acknowledge
The DHCP server acknowledges the request by sending a DHCP Acknowledgment message that confirms the IP address assignment.

Let’s understand the DHCP working principle with a simple example.
Imagine you have a home Wi-Fi network and you want your devices (like phones and laptops) to connect to it without manually setting up each device’s network settings. That’s where DHCP comes in:
- Let’s say your smartphone just joined your home Wi-Fi network.
- The smartphone sends out a message saying, “Hey, I’m new here. Can someone give me an IP address and other network details?”
- Your Wi-Fi router acting as a DHCP server hears the request. It says, “Sure, I have an available IP address, and here are the other network settings you need – like the subnet mask, default gateway, and DNS server.”
- The smartphone receives this information and automatically sets itself up with the provided IP address & network settings.
Smartphone is now ready to use the internet and communicate with other devices on your home network.
Internet Control Message Protocol (ICMP) is a network layer protocol that is used in the IP suite to enable communication & provide feedback about the status of network operations.
ICMP is mainly used for reporting errors and providing diagnostic information related to IP packet processing.
For example, if a router encounters a problem while forwarding an IP packet – it generates an ICMP error message and sends it back to the source of the packet.
Common ICMP error messages include “Destination Unreachable,” “Time Exceeded,” and “Parameter Problem.”
One of the most well-known uses of ICMP is the “ ping ” command (used to check the reachability of a host).
This ping command sends ICMP Echo Request messages to a destination host, and if the host is reachable, it should respond with an ICMP Echo Reply message. This is a simple way to test network connectivity.

ICMP is also used for Path Maximum Transmission Unit (PMTU) discovery. PMTU is the maximum size of an IP packet that can be transmitted without fragmentation along a path.
ICMP messages such as “Fragmentation Needed” and “Packet Too Big” are used to determine the appropriate MTU for a given path which helps to avoid fragmentation and optimize data transfer.
Also, These messages can be used to track the time it takes for packets to travel from the source to the destination and back. The “Time Exceeded” message is used for this purpose.
SNMP stands for Simple Network Management Protocol.
It is an application layer protocol for managing and monitoring network devices/systems.
SNMP operates using a manager-agent model. There are two main components.
SNMP Manager
The manager is responsible for making requests and collecting information from SNMP agents. It can also set configuration parameters on agents.
The agent is a software module or process running on network devices. It stores information about the device’s configuration & performance. The agent responds to requests from SNMP managers.
MIB (Management Information Base) is a hierarchical database that defines the structure and organization of managed objects on a network device. It serves as a reference for both SNMP managers and agents, which makes sure that they understand each other’s data.

There are three versions of SNMP that are being used widely.
SNMPv1: The original version of SNMP that uses community strings for authentication. It lacks security features and is considered less secure.
SNMPv2c: An improvement over SNMPv1 with support for additional data types & improved error handling.
SNMPv3: The most secure version of SNMP, which offers encryption, authentication, and access control. It addresses many of the security concerns of earlier versions.
SNMP is used for various network management tasks such as monitoring bandwidth utilization, tracking device uptime, configuring network devices remotely, and receiving alerts when specific events occur (e.g., system failures or threshold breaches).
Conclusion✍️
I hope you found this article very useful in learning about the various network protocols. You may also be interested in learning about network segmentation and how to implement it.

- Communication Technologies
- Introduction
- History of Networking
- Terminologies
- Switching Techniques
- Transmission Media
- Network Devices
- Network Topologies
- Types of Networks
Network Protocols
- Mobile Communication Protocols
- Mobile Communication Technologies
- Email Protocols
- Wireless Technologies
- Network Security
- Security Acts & Laws
- Web Services
- Useful Resources
- Quick Guide
- Selected Reading
- UPSC IAS Exams Notes
- Developer's Best Practices
- Questions and Answers
- Effective Resume Writing
- HR Interview Questions
- Computer Glossary
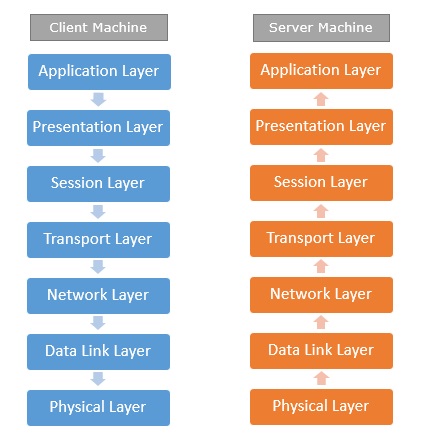
Network Protocols are a set of rules governing exchange of information in an easy, reliable and secure way. Before we discuss the most common protocols used to transmit and receive data over a network, we need to understand how a network is logically organized or designed. The most popular model used to establish open communication between two systems is the Open Systems Interface (OSI) model proposed by ISO.
OSI model is not a network architecture because it does not specify the exact services and protocols for each layer. It simply tells what each layer should do by defining its input and output data. It is up to network architects to implement the layers according to their needs and resources available.
These are the seven layers of the OSI model −
Physical layer −It is the first layer that physically connects the two systems that need to communicate. It transmits data in bits and manages simplex or duplex transmission by modem. It also manages Network Interface Card’s hardware interface to the network, like cabling, cable terminators, topography, voltage levels, etc.
Data link layer − It is the firmware layer of Network Interface Card. It assembles datagrams into frames and adds start and stop flags to each frame. It also resolves problems caused by damaged, lost or duplicate frames.
Network layer − It is concerned with routing, switching and controlling flow of information between the workstations. It also breaks down transport layer datagrams into smaller datagrams.
Transport layer − Till the session layer, file is in its own form. Transport layer breaks it down into data frames, provides error checking at network segment level and prevents a fast host from overrunning a slower one. Transport layer isolates the upper layers from network hardware.
Session layer − This layer is responsible for establishing a session between two workstations that want to exchange data.
Presentation layer − This layer is concerned with correct representation of data, i.e. syntax and semantics of information. It controls file level security and is also responsible for converting data to network standards.
Application layer − It is the topmost layer of the network that is responsible for sending application requests by the user to the lower levels. Typical applications include file transfer, E-mail, remote logon, data entry, etc.
It is not necessary for every network to have all the layers. For example, network layer is not there in broadcast networks.
When a system wants to share data with another workstation or send a request over the network, it is received by the application layer. Data then proceeds to lower layers after processing till it reaches the physical layer.
At the physical layer, the data is actually transferred and received by the physical layer of the destination workstation. There, the data proceeds to upper layers after processing till it reaches application layer.
At the application layer, data or request is shared with the workstation. So each layer has opposite functions for source and destination workstations. For example, data link layer of the source workstation adds start and stop flags to the frames but the same layer of the destination workstation will remove the start and stop flags from the frames.
Let us now see some of the protocols used by different layers to accomplish user requests.
TCP/IP stands for Transmission Control Protocol/Internet Protocol . TCP/IP is a set of layered protocols used for communication over the Internet. The communication model of this suite is client-server model. A computer that sends a request is the client and a computer to which the request is sent is the server.
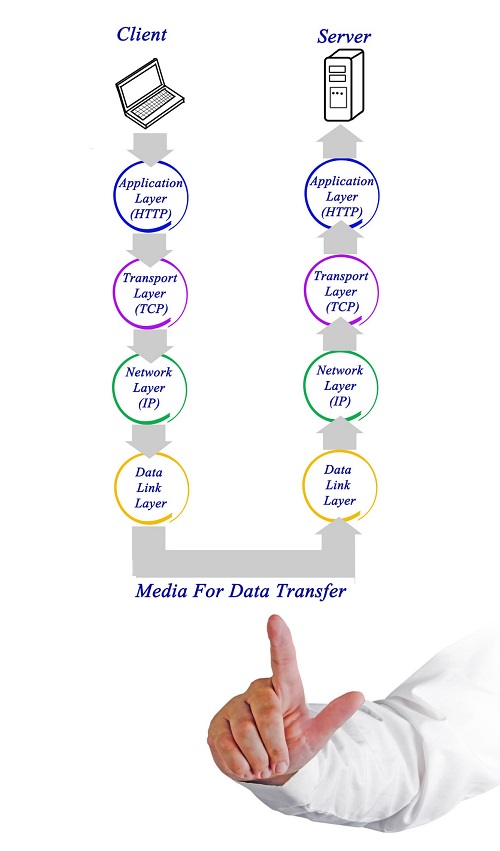
TCP/IP has four layers −
Application layer − Application layer protocols like HTTP and FTP are used.
Transport layer − Data is transmitted in form of datagrams using the Transmission Control Protocol (TCP). TCP is responsible for breaking up data at the client side and then reassembling it on the server side.
Network layer − Network layer connection is established using Internet Protocol (IP) at the network layer. Every machine connected to the Internet is assigned an address called IP address by the protocol to easily identify source and destination machines.
Data link layer − Actual data transmission in bits occurs at the data link layer using the destination address provided by network layer.
TCP/IP is widely used in many communication networks other than the Internet.
As we have seen, the need for network came up primarily to facilitate sharing of files between researchers. And to this day, file transfer remains one of the most used facilities.The protocol that handles these requests is File Transfer Protocol or FTP .

Using FTP to transfer files is helpful in these ways −
Easily transfers files between two different networks
Can resume file transfer sessions even if connection is dropped, if protocol is configure appropriately
Enables collaboration between geographically separated teams
Point to Point Protocol or PPP is a data link layer protocol that enables transmission of TCP/IP traffic over serial connection, like telephone line.

To do this, PPP defines these three things −
A framing method to clearly define end of one frame and start of another, incorporating errors detection as well.
Link control protocol (LCP) for bringing communication lines up, authenticating and bringing them down when no longer needed.
Network control protocol (NCP) for each network layer protocol supported by other networks.
Using PPP, home users can avail Internet connection over telephone lines.
Open Access is an initiative that aims to make scientific research freely available to all. To date our community has made over 100 million downloads. It’s based on principles of collaboration, unobstructed discovery, and, most importantly, scientific progression. As PhD students, we found it difficult to access the research we needed, so we decided to create a new Open Access publisher that levels the playing field for scientists across the world. How? By making research easy to access, and puts the academic needs of the researchers before the business interests of publishers.
We are a community of more than 103,000 authors and editors from 3,291 institutions spanning 160 countries, including Nobel Prize winners and some of the world’s most-cited researchers. Publishing on IntechOpen allows authors to earn citations and find new collaborators, meaning more people see your work not only from your own field of study, but from other related fields too.
Brief introduction to this section that descibes Open Access especially from an IntechOpen perspective
Want to get in touch? Contact our London head office or media team here
Our team is growing all the time, so we’re always on the lookout for smart people who want to help us reshape the world of scientific publishing.
Home > Books > Telecommunication Systems - Principles and Applications of Wireless-Optical Technologies
Telecommunications Protocols Fundamentals
Submitted: 05 November 2018 Reviewed: 14 April 2019 Published: 11 June 2019
DOI: 10.5772/intechopen.86338
Cite this chapter
There are two ways to cite this chapter:
From the Edited Volume
Telecommunication Systems - Principles and Applications of Wireless-Optical Technologies
Edited by Isiaka A. Alimi, Paulo P. Monteiro and António L. Teixeira
To purchase hard copies of this book, please contact the representative in India: CBS Publishers & Distributors Pvt. Ltd. www.cbspd.com | [email protected]
Chapter metrics overview
1,743 Chapter Downloads
Impact of this chapter
Total Chapter Downloads on intechopen.com
Total Chapter Views on intechopen.com
The need for communication amongst people and electrical systems motivated the emergence of a large number of telecommunications protocols. The advances in digital networks and the internet have contributed to the evolution of telecommunications worldwide. The purpose of this chapter is to provide students and researchers with a clear presentation of telecommunications core protocols that are utilised in different research domains including telephony, brain-computer interface (BCI) and voice and digital telecommunications. Indeed, BCI involves different electrical signals, communications concepts and telecommunications protocols. This chapter introduces the reader to the core concepts in communications including analogue and digital telecommunications protocols that are utilised generally in communications and in particular in BCI systems. The topics covered in this chapter include telecommunications protocols, communications media, electrical signals, analogue and digital modulation techniques in digital communications, software-defined radio, overview on 10-Mbps Ethernet protocol and Session Initiation Protocol (SIP).
- analogue modulation
- digital modulation
Author Information
Amer al-canaan *.
- Department of Electrical Engineering, Islamic University of Al-Madinah, Al-Madinah Al-Munnawara, KSA
*Address all correspondence to: [email protected]
1. Introduction
Telecommunications protocols play an important role in the advanced modern communication systems that convey information, signals and messages over short and long distances. Telecommunications protocols were developed for data (digital) and voice (analogue) messages.
In a typical brain-computer interface (BCI) [ 1 ] application, the electroencephalography (EEG) [ 2 ] signals are acquired from the brain, encoded and sent over wireless protocols, such as Bluetooth or Wi-Fi data channels, to a control module. However, in a basic BCI system, signals may be sent through wires between signal acquisition and control modules through a certain serial data communications protocol. BCI is one of several vital engineering domains where researchers and students have to understand and deal with telecommunications protocols.
The need for data communications has inspired researchers and led to the emergence of digital communications, integration of Voice over Internet Protocol (VoIP) or IP telephony with multimedia services offered on IP networks over public switched telephone network (PSTN). Modern telecommunications through VoIP software are common on personal computers and portable devices including smart phones and handheld devices. VoIP systems employ packet switching protocols, which have numerous advantages over circuit switching upon which is based on the traditional PSTN.
VoIP applications for local area network (LAN), wide area networks (WAN), wireless local area network (WLAN) and mobile telephone networks offer better availability, scalability, flexibility, minimum hardware and low cost than PSTN. On the other hand, Internet-related problems such as delay and congestion causing jitter and packet loss are inherent in VoIP.
However, circuit switching is compelling in many applications where real-time, low delay and high QoS are desired, where each customer of modern PSTN profits from dedicated analogue or digital circuits. This implies that a communication channel is reserved during a call or a data session. Due to the limited number of circuits and control units in PSTN, only a fraction of customers can perform simultaneous calls within a switch.
One of the main protocols that has been developed for IP telephony is SIP, which is inspired from establishing and ending a call session and for changing parameters of an established session. The simplicity of SIP and the emergence of Java application interfaces for integrated networks (JAIN)-SIP which is a Java-based API for SIP have reinforced the development and implementation of platform-independent IP telephony services.
In this chapter, core concepts in telecommunications protocols, as well as other related topics including communications media, analogue and digital modulation techniques in digital communications, software-defined radio, overview on 10-Mbps Ethernet protocol and SIP protocol, are presented in an easy and simple style with a number of figures to explain the basic principles of telecommunications protocols.
1.1 Telecommunications core concepts
This section introduces the reader to selected core concepts in telecommunications including telecommunications media and digital encoding.
1.1.1 Twisted pair
Twisted pairs are utilised to carry analogue and digital signals. Depending on distance, analogue signals may be limited to 250 kHz, and digital signals are limited to 10 Mbps for distances around 100 m [ 3 ]. At the onset of electrical telecommunication systems, copper was the main transmission medium because of its electrical characteristics such as low resistivity to electric current.
1.1.2 Morse code
The Morse code is a variable-length code, where each character is given a series of dots and dashes. Some letters have one dot and others have one dash. The code length varies from 1 to 5, covering 36 symbols. The telegraph signals were carried using copper twisted pairs. Signal wires are twisted in order to cancel out unwanted noise and reduce the effective inductance of the transmission line. At the sending side, a switch is used to open and close the electric circuit in a certain pattern in order to produce Morse code at the receiving side.
1.1.3 Coaxial cable
A coaxial cable consists of a core wire and a cylindrical shield separated by insulation material. It provides better noise rejection and baud rate over longer distances than the twisted pair. Analogue signal frequency can exceed 500 MHz, and baud rate can reach 500 Mbps depending on distance.
1.1.4 Optical fibre
Optical fibre systems consist of a laser diode transmitter and receiver separated by transparent optical fibre. The signals are transmitted as light pulses that propagate inside the optical fibre. The optical fibre has small diameter and consists of three components: the core (pure glass or plastic), the cladding and the protective cover. The cladding material (glass or plastic) is less optically dense, which allows the light to travel easier through the core. The optical fibre can be used on longer distances with attenuation.
1.1.5 Wireless transmission
Radio and TV broadcasting was made possible through various modulation techniques of electrical signals over different carrier frequencies. For example, the short waves (SW) include frequencies from 3 up to 30 MHz, very high frequencies (VHF) range from 30 to 300 MHz and ultra-high frequency (UHF) cover frequency spectra from 0.3 to 3 GHz. Lower frequencies have longer propagation distances, while higher frequencies suffer from reflections and attenuation over long distances. On the other hand, radio frequency (RF) and high-frequency (HF) transmissions require small antennas since their wavelengths are much shorter.
1.1.6 Microwave transmission
With shorter wavelengths in the range 4–6 GHz, microwave signals travel in straight lines and do not penetrate solid objects. They are affected by clouds, rain and obstacles blocking the line of sight between the transmitter and receiver. Usually parabolic antennas are used for large systems. The received signal is focused at the focal point of the parabola.
1.1.7 Very small aperture terminal (VSAT)
In the 1980s, the very small aperture terminal devices made it possible to telecommunicate, utilising small dish dimensions between remote areas by means of highly directional parabolic antennas [ 4 ].
1.1.8 Telephone systems
The microphone in a telephone set converts sound into analogue electric signals that are conveyed traditionally through copper wires and reproduced back at the receiver into sound waves through the speaker. The first telephone systems were analogue, while today’s telephone systems are completely digital with tone dialling, voice and data services. Telephone networks have profited from advancements in wireless communications by the implementation of the mobile [ 5 , 6 ] communications. Old telephone networks were designed mainly to convey voice before the emergence of digital data networks and the Internet.
1.1.9 Analogue and digital signals
Digital signals are characterised by two discrete levels, high and low (1 or 0), while analogue signals have continuous forms. Digital and analogue signals are both utilised in modern telecommunications [ 7 ] systems and computer networks. Popular digital codes include American Standard Code for Information Interchange (ASCII) and binary-coded decimal (BCD). ASCII is used in basic character symbols for computer systems, while BCD is mainly used for seven-segment displays.
1.1.10 Non-return to zero (NRZ)
Non-return to zero is the simplest digital encoding as shown in Figure 1 , where a logic one corresponds to a positive high signal level and the logic zero is simply at ground potential or zero voltage. The NRZ encoding is inconvenient for data transmission specially when data contain a long series of zeros or ones.

Unipolar non-return to zero (NRZ).
1.1.11 Return to zero (RZ)
Return to zero is an improved digital encoding over the NRZ encoding, where logic one signals return to zero as shown in Figure 2 . The RZ encoding is inconvenient for data transmission when data contain a long series of zeros.

Unipolar return to zero (RZ).
1.1.12 Manchester encoding
To assure reliable transmission of digital data (such as Ethernet and IP), the Manchester encoding (refers to Figures 3 and 4 with clock signal) is convenient to solve the issue of sending a long series of zeros or ones through a data communication line. The Manchester encoding encodes logic 1 as a transition from level high to low signal, while a 0 is a transition from low to high. The needed bandwidth is twice as the original signal, and there is always a change in the middle of each bit.

Manchester encoding.

Manchester encoding example.
An improved version of this encoding is called the differential Manchester encoding, where a 0 causes the signal to change at the start of the interval (refer to Figure 5 ). On the other hand, a 1 causes a change at the end of the interval. A 1 keeps the signal level unchanged as in the previous bit and changes to high at the middle. This is advantageous and permits interchanging the wiring of a differential pair without any issue.

Manchester differential encoding example.
1.1.13 Shannon’s theory
Shannon studied noisy channels, and his theory is based upon the fact that a signal has to have high signal-to-noise (S/N) ratio in order to be successfully distinguished. This influences the maximum bit rate that can be used as follows:
To increase the data rate, a channel with high S/N should be used. Other means that can increase the bit rate is data compression.
1.1.14 Sampling theory
To convert a continuous signal x ( t ) into a digital form [ 8 ], it is first sampled at equal intervals of time. To be able to reconstruct a sampled signal, x δ t is defined as
The sampling interval T s is 1/ f s , where the sampling frequency f s should be at least twice the highest frequency component f max of the original signal x ( t ). The frequency 2 f max is called the Nyquist frequency.
1.1.15 Analogue-to-digital (A/D) conversion
An analogue signal with a given frequency f 1 can be converted into a digital form by sampling it at a constant frequency f s , where f 1 < f s . A sampled signal has the form of pulses with different amplitudes called pulse amplitude modulation (PAM). The PAM signal is then quantised, and every level is given a binary code number. This process is called pulse-code modulation (PCM). The sampling frequency f s has to be at least twice as much as the signal frequency being sampled f 1 in order to produce a good approximation of the original signal that can be reproduced and converted back to analogue form. In telephony systems the 8-kHz frequency is used to sample voice that is encoded using 8-bit code. The bit rate in this case is 8000 × 8 = 64 kbps . In compact disc (CD) technology, the audio is sampled at 44.1 kHz .
1.1.16 Multiplexing
Frequency-division multiplexing (FDM). This type of multiplexing employs subcarriers to transmit different message signals.
Time-division multiplexing (TDM). This type of multiplexing employs time slots to transmit different message signals.
Quadrature multiplexing (QM). This type of multiplexing employs quadrature carriers to transmit different message signals. This type of multiplexing can be distinguished from FDM by the fact that they have overlapped frequency spectra. QM represents double-sideband (DSB) and single-sideband modulations (SSB).
2. Modulation techniques
In the past, digital networks were connected through telephone networks via the modem (modulation/demodulation). Modern telecommunications systems utilise optical fibres that carry many digital channels, which can be translated into voice signals in a telephone by using a codec (coder/decoder). This involves digital-to-analogue (D/A) and analogue-to-digital (A/D) conversions. When a signal m t = A m cos 2 π f m t + ϕ m t is transmitted, it is normally modulated using a carrier c t = A c sin 2 π f c t + ϕ c t signal, which can be changed or modulated in amplitude ( A c ), phase shift ( ϕ c ) or frequency ( f c ) [ 9 ]. The carrier signal can be generalised as c t = A c t [ sin ( 2 π f c t + ϕ c t ) ] .
2.1 Analogue modulation
To transmit analogue signals over long distances, analogue modulation techniques are used by changing either the amplitude, phase or frequency of analogue signals.
2.1.1 Amplitude modulation (AM)
Amplitude modulation (AM) takes place when A c t is linearly related to the modulating signals (message). In this modulation technique, the carrier frequency is kept constant, and its amplitude is varied according to the amplitude of the transmitted analogue signal as shown in Figure 6 . An AM signal y t is the result of multiplying the message m t and carrier c t functions. Assuming a sinusoidal carrier signal defined as c t = A c sin 2 π f c t is used to modulate the message signal m t = A m cos 2 π f m t + ϕ t :

AM modulation.
In the above equation, m is the modulation index, which is the ratio of the amplitude of the message signal A m to the amplitude A c of the carrier signal. To be able to recover the message, m should be less than 1, i.e., 1 < m > 0 . The resulting product function y t is composed of three frequencies:
The carrier frequency f c .
The sum of the carrier and modulated frequencies f c + f m + ϕ with the same phase shift of the message signal.
The difference between the carrier and modulated frequencies f c − f m − ϕ with the negative phase shift of the message signal.
2.1.2 Frequency modulation (FM)
Frequency modulation (FM) takes place when the time derivative of ϕ t is linearly related to the modulating signal. In this modulation technique, the amplitude of the carrier signal is kept constant, and its frequency is varied according to the amplitude of the transmitted analogue signal as shown in Figure 7 . Frequency and phase modulations are considered as special cases of angle modulation s t = A c cos 2 π f c t + ϕ t . The carrier frequency is changed such that the frequency f c depends on the message signal. Since the frequency is the derivative of the phase, the relation between the input signal and frequency can be written as [ 9 ] ϕ ′ t = m f m t . The FM signal y t can be written as

FM modulation.
In the above equation, A m is the amplitude of the message signal, f m is the frequency of the message signal and f Δ is the maximum frequency that corresponds to the maximum amplitude A m value. The frequency modulation index m f describes the variation in carrier frequency compared [ 10 ]:
The frequency modulation index can be less than 1 (for narrowband FM) or much greater than 1 (for wideband FM).
2.1.3 Phase modulation (PM)
Phase modulation (PM) takes place when ϕ t is linearly related to the modulating signal. In this modulation technique, the amplitude of the carrier signal is kept constant, and its phase is varied according to the amplitude of the transmitted analogue signal as shown in Figure 8 . The phase of the PM signal can be written in terms of the phase modulation index m p as ϕ t = m p m t .

PM modulation.
2.2 Digital modulation
Transmission of digital signals involves modulation of amplitude, frequency or phase of carrier signals. The difference between analogue and digital modulation is that in digital modulation, the changes are at discrete intervals. For example, the amplitude of the carrier signal can be assigned to a maximum value or zero to represent the binary data 1 and 0.
2.2.1 Frequency-shift keying (FSK)
Frequency-shift keying is called also frequency modulation (FM). A bit 0 corresponds to low frequency, and a 1 corresponds to high frequency as shown in Figure 9 . An FSK signal s ( t ) can be written as

FSK modulation.
In the equation above, k is a constant shift in frequency. Obviously, the FSK uses two frequencies ( f c + k and f c − k ) for logic 0 and 1, respectively. This type of FSK is called binary FSK (BFSK).
In case k and 3 k are used to shift the carrier frequency, the resulting FSK signal has four different frequencies and can be utilised to encode the binary codes 00 , 01 , 10 and 11 , as follows:
2.2.2 Amplitude-shift keying (ASK)
Amplitude-shift keying is similar to amplitude modulation (AM) as shown in Figure 10 . Each signal amplitude is assigned to a sequence of bits. If four amplitudes are considered, the following bit code sequences can be defined as 00, 01, 10 and 11. A ASK signal s ( t ) can be written as

ASK modulation.
2.2.3 Phase-shift keying (PSK)
Phase-shift keying (PSK) is also called phase modulation (PM). The signal can have a variable phase as shown in Figure 11 . If the signal is compared with its predecessor, this technique is called differential phase-shift keying (DPSK). Each phase shift can be assigned to a given binary code [ 11 ]. A PSK signal s t can be written as

PSK modulation.
Since the above equation contains two distinct phases, this type is called binary phase-shift keying (BPSK). If the number of phase variations is increased to 4, the quadrature PSK (QPSK) ca be defined as follows:
2.2.4 Quadrature amplitude modulation (QAM)
Though the above three approaches can be used with any number of signals, they tend to be difficult to implement due to the fact that special hardware will be needed to distinguish between adjacent amplitudes, phases and frequencies. To overcome this limitation, a combination of bits can be assigned to groups of signals that can be different in amplitude and phase, for example. For example, using signals with two amplitudes and two phase shifts produces four different signals.
2.2.5 Analogue pulse modulation
Pulse amplitude modulation (PAM): The PAM signal (as shown in Figure 12 ) is similar to the sampled signal. The pulses in PAM can have a finite width unlike the sampling delta pulses. The PAM-modulated signal y t can be written as

PAM modulation.
Pulse width modulation (PWM): In PWM as shown in Figure 13 , the width of each pulse is related to the modulating signal. This type of modulation is used in DC motor control applications.
Pulse position modulation (PPM): In PPM as shown in Figure 14 , the position of each pulse is related to the modulating signal.

PWM modulation.

PPM modulation.
2.2.6 Digital pulse modulation
PCM: This modulation technique is achieved by sampling the message signal and assigning a digital code (quantisation) to each pulse. The level of the signal is not transmitted; instead the quantised code is assigned according to the available bits for encoding. For example, in 8-bit PCM (with n = 8 ), each level is assigned to a discrete value between 0 and 255. For a signal that has a bandwidth ( BW ) and a sampling rate of 2 BW , the number of transmitted pulses becomes 2 nBW .
Delta modulation: In delta modulation, only the difference between the previous and following codes is sent, as shown in Figure 15 . For a reference signal m s t and a message signal m t , the difference Δ t is computed and fed to a pulse generator in order to produce the delta-modulated signal to be transmitted:

Delta modulation.
In Figure 15 , the reference signal m s t is the signal with rectangular edges superimposed on the smooth sine wave message signal. The reference signal is obtained by integrating y t as follows [ 8 ]:
The difference value Δ nT s is calculated at the n th sampling instant. The reference signal m s t is a stair-step approximation of m t as shown in Figure 15 .
3. Session initiation protocol (SIP)
Modern telephony systems are based upon the Voice over IP (VoIP) protocols, such as SIP, which is a call control and signalling protocol adopted by the 3GPP in order to deliver IP multimedia services [ 12 ] to the mobile network [ 6 ]. The design of SIP was inspired from HTTP protocol and standardised by the Internet Engineering Task Force (IETF). The purpose of SIP is to enable initiating, terminating interactive call sessions and changing parameters of ongoing sessions. The simplicity of SIP and the emergence of JAIN-SIP [ 13 ] have facilitated the development and implementation of platform-independent IP telephony services. Multimedia sessions enable communicating via voice, video and text. SIP messages are either requests or responses and use Session Description Protocol (SDP) in order to determine and negotiate session parameters at either endpoint. SIP supports name mapping and redirection functionalities and, thus, permits user mobility. A typical SIP architecture consists of SIP user agents (UAs) and servers.
4. Software-defined radio (SDR)
Software-defined radio (SDR) [ 14 ] is a wireless communication device that employs software to perform most of the operations that are traditionally done by hardware in conventional radio circuits. Similar to the first radio receivers, SDR uses the same hardware for antenna and RF amplifiers. Unlike traditional radios that are based upon hardware to perform modulation and demodulation, software-defined radios are dependent on software to achieve filtering, modulation and demodulation. The IF signal is sampled and converted to digital signal that can be manipulated using software. Common modules between traditional radio and SDR include the antenna and the D/A and A/D converters. Some SDR implementations are freely available using field-programmable gate arrays (FPGA) [ 15 ].
5. Overview of 10-Mbps Ethernet
The core protocol of the Internet is the Ethernet protocol, which is based upon serial digital communications. This section provides an overview on the 10-Mbps Ethernet standard. The composition of Ethernet frames (at the MAC sub-layer) and the generation of differential signals at the physical interface (Phy) layer can be implemented on different hardware types as well as FPGA through hardware description language (HDL) code. For 10-Mbps Ethernet, Manchester encoding is utilised, where every bit of information is encoded as a transition from 1 to 0 or from 0 to 1.This is advantageous for the synchronisation between the sender and the receiver and for the recovery of the transmission clock. This encoding method prohibits sending consecutive zeros or ones, which appear as constant DC signal in a conventional RZ encoding. Since every bit of information is composed of two voltage levels, the reference clock is at 20 MHz (double the baud rate).
To identify the beginning of an Ethernet frame, a special pattern of bits is sent, which consists of preamble and a start of frame delimiter (SFD). The preamble and SFD are sent prior to the actual data. The pattern ‘10’ is repeatedly sent, such that a total of 62 bits of 101010 are followed by 11. The last byte (SFD) is 10101011. In hexadecimal, the preamble is 7 bytes of 0x55 followed by a single SFD byte of 0xD5. The first byte that is sent is 0x55, whereas the byte 0x D 5 is sent last. The leftmost bytes are sent first, of which the rightmost bits (LSB) are sent first. This is why the first byte in the preamble 10101010 is sent from right to left, as 0x55, i.e., the first bit to be transmitted, is 0. Data are usually transferred from an FPGA to the Ethernet port through a physical interface. Taking into consideration the media-independent interface (MII) standard, where the Phy interface communicates nibbles (4 bits) at a time, the SFD 10101011 byte is sent as 0xD and 0x5, since the lower nibble 0xD (in binary, 1011) is sent first starting by 1 (rightmost bit). The reference clocks are 2.5 and 25 MHz for 10-Mbps and 100-Mbps Ethernet, respectively. Reduced MII (RMII) and serial MII (SMII) are two reduced versions of MII, where 2-bit and 1-bit bus widths are used for the Phy, respectively. Compared to the 10-Mbps MII, the gigabit MII (GMII) communicates through 8-bit width bus with a reference clock of 125 MHz. However, the 10-Gbit MII (XGMII) standard deals with 32 bits of data at a time.
Some implementations of Ethernet on FPGA depend upon finite state machines (FSM) programmed in HDL, such as VHDL. Several open-source codes [ 13 ] offer Ethernet implementations in VHDL or Verilog.
6. Conclusion
This review chapter contains an overview of telecommunications protocols that are part of modern telecommunications systems. This chapter also provides an overview on analogue and digital signal modulation techniques that are currently used in many research fields including BCI. The researcher in BCI domain as well as the electrical engineering student may find the flow of information smooth and convenient.
The information in this chapter are intended to introduce the reader as well as the researcher in BCI to the core concepts in communications and to analogue and digital telecommunications protocols in an easy-to-follow approach supported with multiple figures and mathematical expression.
The topics covered in this chapter include core concepts in electrical signals, communications, telecommunications protocols as well as other related topics including communications media, analogue and modulation techniques, software-defined radio, 10-Mbps Ethernet protocol and SIP protocol. The topics in this chapter are presented in an easy and simple style with a number of figures to explain the basic principles and fundamentals of telecommunications protocols.
- 1. Ramadan RA, Vasilakos AV. Brain computer interface: Control signals review. Neurocomputing. 2017; 223 :26-44
- 2. Jiang X, Bian GB, Tian Z. Removal of artifacts from EEG signals: A review. Sensors. 2019; 19 (5)
- 3. Shay WA. Understanding Data Communications and Networks. Boston, USA: PWS Publishing Company; 1994
- 4. Manohar V, Kovitz JM, Rahmat-Samii Y. Synthesis and analysis of low profile, metal-only stepped parabolic reflector antenna. IEEE Transactions on Antennas and Propagation. June 2018; 66 (6):2788-2798
- 5. Sauter M. From GSM to LTE-Advanced Pro and 5G: An Introduction to Mobile Networks and Mobile Broadband. Hoboken, NJ, USA: Wiley; 2017
- 6. Lee W. Mobile Cellular Telecommunications: Analog and Digital Systems. Columbus, OH, USA: McGraw Hill Education; 2017
- 7. Frenzel LE. Principles of Electronic Communication Systems. 4th ed. Columbus, OH, USA: McGraw-Hill; 2016
- 8. Ziemer RE, Tranter WH. Communications Systems, Modulation, and Noise. 6th ed. Hoboken, NJ, USA: John Wiley; 2010
- 9. Siva C, Murthy R, Manoj BS. Ad Hoc Wireless Networks. Upper Saddler River, NJ, USA: Printice Hall; 2004
- 10. Wikipedia. Frequency Modulation, 2019
- 11. Swierczynski P, Fyrbiak M, Koppe P, Paar C. FPGA Trojans through detecting and weakening of cryptographic primitives. IEEE Transactions on IEEE Transactions on Computer-Aided Design of Integrated Circuits and Systems. 2015; 34 (8):1236-1249
- 12. Al-Canaan A, Khoumsi A. Cross-platform approach to advanced IP-telephony services using JAIN-SIP. Journal of Networks. 2010; 5 (7):8080-8814
- 13. Al-Canaan A, Khoumsi A. Advanced IP-Telephony Service Creation using JAIN-SIP API: Crossplatform approach. In: Mosharaka International Conference on Communications, Networking and Information Technology (MIC-CNET 2008); December 2008; Amman, Jordan. pp. 46-51
- 14. Machado-Fernandez J. Software defined radio: Basic principles and applications. Revista Facultad de Ingéniera. 2015; 24 (01):79-96
- 15. Opencores.org . OpenCores; 2015
© 2019 The Author(s). Licensee IntechOpen. This chapter is distributed under the terms of the Creative Commons Attribution 3.0 License , which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.
Continue reading from the same book
Telecommunication systems.
Edited by Isiaka Alimi
Published: 30 October 2019
By Juan Manuel Velazquez Arcos, Ricardo Teodoro Paez ...
1058 downloads
By Iman Almomani and Mamdouh Alenezi
1427 downloads
By Tomas Horvath, Petr Munster and Josef Vojtech
1595 downloads
IntechOpen Author/Editor? To get your discount, log in .
Discounts available on purchase of multiple copies. View rates
Local taxes (VAT) are calculated in later steps, if applicable.
Support: [email protected]
What is the Internet Protocol?
The Internet Protocol (IP) is a set of requirements for addressing and routing data on the Internet. IP can be used with several transport protocols, including TCP and UDP.
Learning Objectives
After reading this article you will be able to:
- Define the Internet Protocol (IP)
- Explain how IP is used to ensure data arrives in the right place
- Explore the differences between TCP/IP and UDP/IP
Related Content
- What is a protocol?
- What is a packet?
- What is a router?
- Autonomous system (AS)
- What is IPsec?
Want to keep learning?
Subscribe to theNET, Cloudflare's monthly recap of the Internet's most popular insights!
Refer to Cloudflare's Privacy Policy to learn how we collect and process your personal data.
Copy article link
What is the Internet Protocol (IP)?
The Internet Protocol (IP) is a protocol, or set of rules, for routing and addressing packets of data so that they can travel across networks and arrive at the correct destination. Data traversing the Internet is divided into smaller pieces, called packets . IP information is attached to each packet, and this information helps routers to send packets to the right place. Every device or domain that connects to the Internet is assigned an IP address , and as packets are directed to the IP address attached to them, data arrives where it is needed.
Once the packets arrive at their destination, they are handled differently depending on which transport protocol is used in combination with IP. The most common transport protocols are TCP and UDP.
What is a network protocol?
In networking, a protocol is a standardized way of doing certain actions and formatting data so that two or more devices are able to communicate with and understand each other.
To understand why protocols are necessary, consider the process of mailing a letter. On the envelope, addresses are written in the following order: name, street address, city, state, and zip code. If an envelope is dropped into a mailbox with the zip code written first, followed by the street address, followed by the state, and so on, the post office won't deliver it. There is an agreed-upon protocol for writing addresses in order for the postal system to work. In the same way, all IP data packets must present certain information in a certain order, and all IP addresses follow a standardized format.
What is an IP address? How does IP addressing work?
An IP address is a unique identifier assigned to a device or domain that connects to the Internet. Each IP address is a series of characters, such as '192.168.1.1'. Via DNS resolvers, which translate human-readable domain names into IP addresses, users are able to access websites without memorizing this complex series of characters. Each IP packet will contain both the IP address of the device or domain sending the packet and the IP address of the intended recipient, much like how both the destination address and the return address are included on a piece of mail.
IPv4 vs. IPv6
The fourth version of IP (IPv4 for short) was introduced in 1983. However, just as there are only so many possible permutations for automobile license plate numbers and they have to be reformatted periodically, the supply of available IPv4 addresses has become depleted. IPv6 addresses have many more characters and thus more permutations; however, IPv6 is not yet completely adopted, and most domains and devices still have IPv4 addresses. For more on IPv4 and IPv6, see What is my IP address?
What is an IP packet?
IP packets are created by adding an IP header to each packet of data before it is sent on its way. An IP header is just a series of bits (ones and zeros), and it records several pieces of information about the packet, including the sending and receiving IP address. IP headers also report:
- Header length
- Packet length
- Time to live (TTL) , or the number of network hops a packet can make before it is discarded
- Which transport protocol is being used (TCP, UDP, etc.)
In total there are 14 fields for information in IPv4 headers, although one of them is optional.
How does IP routing work?
The Internet is made up of interconnected large networks that are each responsible for certain blocks of IP addresses; these large networks are known as autonomous systems (AS) . A variety of routing protocols, including BGP , help route packets across ASes based on their destination IP addresses. Routers have routing tables that indicate which ASes the packets should travel through in order to reach the desired destination as quickly as possible. Packets travel from AS to AS until they reach one that claims responsibility for the targeted IP address. That AS then internally routes the packets to the destination.
Protocols attach packet headers at different layers of the OSI model:
Packets can take different routes to the same place if necessary, just as a group of people driving to an agreed-upon destination can take different roads to get there.
What is TCP/IP?
The Transmission Control Protocol (TCP) is a transport protocol, meaning it dictates the way data is sent and received. A TCP header is included in the data portion of each packet that uses TCP/IP . Before transmitting data, TCP opens a connection with the recipient. TCP ensures that all packets arrive in order once transmission begins. Via TCP, the recipient will acknowledge receiving each packet that arrives. Missing packets will be sent again if receipt is not acknowledged.
TCP is designed for reliability, not speed. Because TCP has to make sure all packets arrive in order, loading data via TCP/IP can take longer if some packets are missing.
TCP and IP were originally designed to be used together, and these are often referred to as the TCP/IP suite. However, other transport protocols can be used with IP.
What is UDP/IP?
The User Datagram Protocol, or UDP , is another widely used transport protocol. It is faster than TCP, but it is also less reliable. UDP does not make sure all packets are delivered and in order, and it does not establish a connection before beginning or receiving transmissions.
Do network switches refer to IP addresses?
A network switch is an appliance that forwards data packets within a local area network (LAN) . Most network switches operate at layer 2, the data link layer, not layer 3, the network layer, and therefore use MAC addresses to forward packets, not IP addresses. To learn more, see What is a network switch?
Getting Started
- For enterprises
- Compare plans
- Get a recommendation
- Request a demo
- Contact sales
About the Network Layer
- Network layer
- What is routing?
Network Types
- Local area network (LAN)
- Wide area network (WAN)
- Metropolitan area network (MAN)
- Campus area network (CAN)
- Personal area network (PAN)
- Network-as-a-service (NaaS)
- What is SDN?
- Enterprise networking
Networking Basics
- How Internet works
- Internet Protocol (IP)
- What is a network switch?
- What is tunneling?
- What is a port?
- Control plane
- What is MSS?
- What is MTU?
- GRE tunneling
- What is MTR?
- IPsec vs. SSL VPNs
- What is IGMP?
- IGMP snooping
- What is MPLS?
- Network security
- SD-WAN vs. MPLS
Learning Center Navigation
- Learning Center Home
- DDoS Learning Center
- DNS Learning Center
- CDN Learning Center
- Serverless Learning Center
- Security Learning Center
- Performance Learning Center
- SSL Learning Center
- Bots Learning Center
- Cloud Learning Center
- Access Management Learning Center
- Privacy Learning Center
- Video Streaming Learning Center
- Email Security Learning Center
- AI Learning Center
Using a modern browser that supports web standards ensures that the site's full visual experience is available. Consider upgrading your browser if you are using an older technology.
University of Technology Sydney
- How to use this handbook
- General information
- Principal dates
- Academic year dates
- Analytics and Data Science
- Communication
- Creative Intelligence and Innovation
- Design, Architecture and Building
- Engineering
- Graduate School of Health
- Information Technology
- International Studies and Social Sciences
- Transdisciplinary Innovation
- Study package directory
49202 Communication Protocols
Warning: The information on this page is indicative. The subject outline for a particular session, location and mode of offering is the authoritative source of all information about the subject for that offering. Required texts, recommended texts and references in particular are likely to change. Students will be provided with a subject outline once they enrol in the subject. Subject handbook information prior to 2025 is available in the Archives .
Postgraduate
Description
Students completing this subject have a good understanding of the theory of communication protocols and its application to popular protocols, in particular TCP/IP, as well as the analysis of performance and troubleshooting protocol issues in large carrier-grade networks. A significant practice-oriented laboratory component allows students to gain deeper insights into the theory through the use of the Wireshark packet sniffing application.
Subject learning objectives (SLOs)
Upon successful completion of this subject students should be able to:
| 1. | Identify fundamental concepts of communication protocols such an encapsulation/decapsulation and overhead; switching, routing, fragmentation, IP addressing, transport layer, and IP/MPLS based services. (D.1) |
|---|---|
| 2. | Use the 'wireshark' packet sniffing program. (D.1) |
| 3. | Combine 1 and 2 above in the implementation, analysis, performance measurement and troubleshooting of networks. (C.1) |
| 4. | Recognise basic configuration and measurement procedures on an industry-standard service router platform. (D.1) |
Course intended learning outcomes (CILOs)
This subject also contributes specifically to the development of the following Course Intended Learning Outcomes (CILOs):
- Design Oriented: FEIT graduates apply problem solving, design thinking and decision-making methodologies in new contexts or to novel problems, to explore, test, analyse and synthesise complex ideas, theories or concepts. (C.1)
- Technically Proficient: FEIT graduates apply theoretical, conceptual, software and physical tools and advanced discipline knowledge to research, evaluate and predict future performance of systems characterised by complexity. (D.1)
Contribution to the development of graduate attributes
Engineers Australia Stage 1 Competencies
Students enrolled in the Master of Professional Engineering should note that this subject contributes to the development of the following Engineers Australia Stage 1 competencies:
- 1.3. In-depth understanding of specialist bodies of knowledge within the engineering discipline.
- 2.1. Application of established engineering methods to complex engineering problem solving.
- 2.2. Fluent application of engineering techniques, tools and resources.
Teaching and learning strategies
Students will learn in this subject through online lecture videos, interactive tutorial classes, individual and collaborative quizzes, lab classes, independent study and study for the final exam. Students are required to watch the online lectures and read the appropriate textbook chapters before coming to class. The textbook has more details and presents information from different viewpoints to the online lectures, thus providing students the opportunity for deeper understanding. Tutorial classes provide students with an opportunity to raise questions, discuss and clarify concepts from the online lectures. Some tutorial classes will involve collaborative quizzes. Collaborative lab classes are designed to reinforce the theory and allow students to learn practical skills as well as question their understanding. Regular quizzes ensure that students keep up-to-date throughout the session. A final exam ensures that students have understood the majority of the important concepts and are able to apply these to industry-standard problems. The assessment structure includes a quiz on IP addressing, with a weight of 20%, in which a mark of at least 80% must be attained after three attempts in order to receive credit for this component.
Content (topics)
- Introduction to protocols, evolution of the Internet
- Applications and Services
- Transport layer
- Data link layer and physical layer
Assessment task 1: Review Quizzes
| Intent: | Regular quizzes are held each block to give students feedback on the progress in understanding key concepts and procedures. |
|---|---|
| Objective(s): | 1 D.1 |
| Type: | Quiz/test |
| Groupwork: | Individual |
| Weight: |
Assessment task 2: Laboratory Test
| Intent: | Lab activities allow students to link theory and practice using industry standard tools and techniques. Students will capture packets using the 'wireshark' software, and analyse the composition, flow and timing of packets and frames in a very similar way to what a professional telecommunication engineer would do in configuring and troubleshooting a real-world network. In the lab exam, students will demonstrate their capabilities to analyse traffic, identify faults and measure network performance in a simulated network environment. |
|---|---|
| Objective(s): | 1, 2 and 3 C.1 and D.1 |
| Type: | Laboratory/practical |
| Groupwork: | Individual |
| Weight: | |
| Criteria: | Completeness (50%) - Did you complete all parts of the lab examination? Did you miss any important faults or significant deviations between the expected and actual network behaviour? Have you adequately interpreted each of your observations? Accuracy (50%) - How accurate and precise were your measurements and observations? Did you correctly calculate any required efficiencies, overheads, throughputs, latencies or other metrics? Did you correctly apply appropriate statistical methods (e.g. calculation of means, standard deviations etc.)? |
Assessment task 3: Final Exam
| Intent: | This provides an opportunity for students to demonstrate their individual understanding of key concepts and procedures as would be used in an industrial setting |
|---|---|
| Objective(s): | 1 and 4 D.1 |
| Type: | Examination |
| Groupwork: | Individual |
| Weight: |
Assessment task 4: IP Addressing Test
| Intent: | To assure that all students passing the subject have a minimum level of understanding of critically important concepts such as IP addressing, subnetting and supernetting. |
|---|---|
| Objective(s): | 1 D.1 |
| Type: | Quiz/test |
| Groupwork: | Individual |
| Weight: |
Minimum requirements
In order to pass the subject, a student must achieve an overall mark of 50% or more.
Required texts
J. Kurose and K. Ross, Computer Networking A Top-Down Approach , 7th ed., Pearson Education.
Other resources
There is a wealth of information on communication protocols. The UTS library has a very large collection of books and electronic resources that you can use to assist your learning in this subject. There are also many internet sites that are of use. Use Google to find them.
All students enrolled in this subject must have a valid login for UTS Canvas. It can be accessed through any web browser using the URL https://canvas.uts.edu.au/ . If you are properly enrolled in the subject in MyStudentAdmin, then you will be automatically enrolled in Canvas. If you are not, then you should check your current enrolment in MyStudentAdmin. If this is correct, then contact the IT Support Helpdesk.
UTS: Handbook | Site map
Networking protocols
- Network Performance Monitoring
- Challenges of Network Performance Monitoring
- Network Device Monitoring
- Agent Based Monitoring
- Network Availability Monitoring
- Network Uptime Monitoring
- Packet Loss Monitoring
- Network Activity Monitoring
- Network Interface Monitoring
- Network Testing Tools
- Network Assessment Tools
- LAN Management
- Hardware Monitor
- Disk Space Monitor
- Hard Drive Monitor
- CPU Monitor
- Uptime Monitoring
- Adaptive Thresholding
- Forecasting Performance Trends
- CPU Usage Monitor
- CPU Temperature Monitor
- CPU Memory Disk Monitor
- Memory Monitoring
- Router Monitoring
- Switch Monitoring
- Switch Management Software
- Ethernet Monitoring
- URL Monitoring
- LAN Monitoring
- IP SLA Monitor
- WAN Monitoring
- WAN RTT Monitoring
- VoIP Monitor
- Network Latency Monitoring
- System Performance Monitoring
- Load balancer Monitoring
- VPN Monitor
- WMI monitoring
- Windows Process Monitor
- Wireless Network Monitor
- Wireless Monitoring
- WiFi Monitor
- Wi-Fi Analyzer
- WLC Monitoring
- UPS monitoring
- Printer Monitoring
- Network Printer Management
- HP Printer Monitoring Software
- Canon Printer Monitoring Software
- Network Device Discovery
- Cisco Monitoring
- Cisco Meraki Monitoring
- Cisco ACI monitoring
- Cisco UCS Monitoring
- Cisco Port Monitor
- Cisco Switch Monitoring
- IBM monitoring
- Syslog Monitoring
- IPMI Monitoring
- SNMP Monitoring Software
- SNMP Trap Monitoring
- 3Com Switch Port Monitoring
- Fortigate Performance Monitoring
- Juniper Network Monitoring
- NOC Monitoring
- Network Performance Test
- Network Link Monitoring
- Server Monitoring
- Server Uptime Monitoring
- Windows Server Monitoring
- Server Health Monitor
- Server Log Management
- Systems Management
- Hyper-V Management Tools
- Linux Server Monitoring
- VMware Monitoring
- ESX Host Monitoring
- Server Virtualization
- Virtual Machine (VM) Monitoring
- Virtual Network Management
- VMware ESXi Monitoring Tool
- vSphere performance monitoring
- Hyper-V Monitoring
- Hyper-V Performance Monitoring
- Citrix XenServer Monitoring
- Citrix Monitoring
- Nutanix monitoring
- Hyperconverged Infrastructure Monitoring
- Virtualization Monitoring Dashboard
- Operating System (OS) Monitoring
- Windows Network Monitor
- Microsoft Network Monitoring
- Linux Network Monitor
- Dell Server Monitoring
- HP Server Monitoring
- Event Log Monitoring
- Exchange Monitoring
- File/ Folder Monitoring
- FTP Monitoring
- Windows Service Monitoring
- Service Monitoring
- Process Monitoring
- Network Mapping
- Network Planning
- Network Path Analysis
- Network Diagram Software
- Grouping Network Elements
- Custom Network Maps
- Network Monitoring Dashboards
- Network Discovery Tool
- Network Topology
- Network Topology Software
- Network Visualization Definition
- Network Visualization
- Network Topology Mapper
- Traceroute Tool
- Network Fault Management
- Network Fault Monitoring
- Network Monitoring Alerts
- Root Cause Analysis for Network Faults
- Network Automation
- Troubleshooting Network Issues
- IT Workflow Automation
- Network Troubleshooting Tools
- Service Level Management Dashboards
- Intent based Networking (IBN)
- Data Center Monitoring
- Data Center Management
- Data Center Networking
- 3D Datacenter Floor
- SAN Monitoring
- Storage Monitoring
- Storage Raid Management
- Tape Library Management
- Storage Monitoring Dashboard
- Storage Capacity Forecasting
- Fabric Switch Management
- NetApp Monitoring
- Dell EMC Storage Monitoring
- IBM Storage Monitoring
- HPE Storage Monitoring
- Scheduled Reports
- Network Performance Reporting
- Business Snapshot Based Reports
- Forecast Reports
- Custom Reports
- Enterprise Monitoring Tools
- Distributed Network Monitoring
- Enterprise Network Monitoring
- Smart Upgrade
- Remote Network Monitoring
- OpManager MSP
- Network Traffic Analysis
- Network Configuration Management
- Firewall Log Management
- IP Address Management
- Switch Port Mapper
- Applications Monitoring
- Integrations
- ServiceDesk Plus Integration
- ServiceDesk Plus Cloud Integration
- ServiceDesk Plus MSP Integration
- ServiceNow Integration
- Jira Service Management Integration
- Slack Integration
- Webhook Integration
- Custom Integrations
- Integration with Analytics Plus
- Monitor IT on the move
- Network Monitoring
- Network Resilience
- MTBF-MTTF-MTTR
- Raid configurations
- Software Defined Data Center
- Troubleshoot Wifi Issues
- Storage Pools and Luns
- Bare Metal Hypervisor
- Application Delivery Controller
- Network Monitoring Metrics
- SLA Monitoring
- Challenges of Network Monitoring
- Network Software
- Network Monitor
- Network Management Software
- Network Management Challenges
- Network Management System
- Network Performance Management
- Network Incident Management
- Network Administration
- Cisco Management
- Network Monitoring Tools
- Real-time Network Monitoring
- Server Management
- Server Performance Management
- Virtual Server Management
- Agentless Network Monitoring
- Wireless network solutions
- Disk Space Monitoring Challenges
- Windows Service Monitoring Challenges
- Network Map
- Virtualization
- Virtualization Best Practices
- Virtualization Challenges
- Hyper-V Performance Monitoring Challenges
- Wi-Fi Management Best Practices
- Network protocols
- Network Routing
- Layer 2 Protocols
- Troubleshooting Network Latency
- Virtualization Sprawl
- Basics of Network Diagrams
- Network Diagrams
- Network Mapping Challenges
- Network Optimization
- Switching Loops
- Route Flapping
- Troubleshooting VLANs
- Best Network Monitor
- Best Free Network Monitoring Software
- Solarwinds Alternative
- PRTG Alternative
- Zabbix Alternative
- Whatsup Gold Alternative
- Nagios XI Alternative
- Spiceworks Alternative
- Customizable Role-based Access Control
- SAML Authentication
What are network protocols?
Network protocols are a set of rules, conventions, and data structures that dictate how devices exchange data across networks. In other words, network protocols can be equated to languages that two devices must understand for seamless communication of information, regardless of their infrastructure and design disparities.
The OSI model: How do network protocols work?
To understand the nuances of network protocols, it's imperative to know about the Open Systems Interconnection (OSI) model first. Considered the primary architectural model for internet working communications, the majority of networking protocols used today are structurally based on the OSI model.
The OSI model splits the communication process between two network devices into 7 layers. A task or group of tasks is assigned to each of these 7 layers. All the layers are self-contained, and the tasks assigned to them can be executed independently.
To put this into context, here is a representation of the communication process between two network devices following the OSI model:
The seven layers in the OSI model can be divided into two groups: upper layers, including layers 7, 6, and 5, and lower layers, including layers 4, 3, 2, and 1. The upper layers deal with application issues, and the lower layers deal with data transport issues.
Network protocol divides the communication process into discrete tasks across every layer of the OSI model. One or more network protocols operate at each layer in the communication exchange.
Following are the detailed descriptions of the functioning of network protocol in computer network in each layer of the OSI model:
Though some say the OSI model is now redundant and less significant than the Transmission Control Protocol (TCP)/IP network model, there are still references to the OSI model even today as the model's structure helps to frame discussions of protocols and contrast various technologies.
Types of network protocols
Now that you know how the OSI model works, you can dive straight into the classification of protocols. The following are some of the most prominent protocols used in network communication.
Application layer network protocols
1. dhcp: dynamic host configuration protocol.
DHCP is a communication protocol that enables network administrators to automate the assignment of IP addresses in a network. In an IP network, every device connecting to the internet requires a unique IP. DHCP lets network admins distribute IP addresses from a central point and automatically send a new IP address when a device is plugged in from a different place in the network. DHCP works on a client-server model.
Advantages of using DHCP
- Centralized management of IP addresses.
- Seamless addition of new clients into a network.
- Reuse of IP addresses, reducing the total number of IP addresses required.
Disadvantages of using DHCP
- Tracking internet activity becomes tedious, as the same device can have multiple IP addresses over a period of time.
- Computers with DHCP cannot be used as servers, as their IPs change over time.
2. DNS: Domain Name System protocol
The DNS protocol helps in translating or mapping host names to IP addresses. DNS works on a client-server model, and uses a distributed database over a hierarchy of name servers.
Hosts are identified based on their IP addresses, but memorizing an IP address is difficult due to its complexity. IPs are also dynamic, making it all the more necessary to map domain names to IP addresses. DNS helps resolve this issue by converting the domain names of websites into numerical IP addresses.
- DNS facilitates internet access.
- Eliminates the need to memorize IP addresses.
Disadvantages
- DNS queries don't carry information pertaining to the client who initiated it. This is because the DNS server only sees the IP from where the query came from, making the server susceptible to manipulation from hackers.
- DNS root servers, if compromised, could enable hackers to redirect to other pages for phishing data.
3. FTP: File Transfer Protocol
File Transfer Protocol enables file sharing between hosts, both local and remote, and runs on top of TCP. For file transfer, FTP creates two TCP connections: control and data connection. The control connection is used to transfer control information like passwords, commands to retrieve and store files, etc., and the data connection is used to transfer the actual file. Both of these connections run in parallel during the entire file transfer process.
- Enables sharing large files and multiple directories at the same time.
- Lets you resume file sharing if it was interrupted.
- Lets you recover lost data, and schedule a file transfer.
- FTP lacks security. Data, usernames, and passwords are transferred in plain text, making them vulnerable to malicious actors.
- FTP lacks encryption capabilities, making it non-compliant with industry standards.
4. HTTP: Hyper Text Transfer Protocol
HTTP is an application layer protocol used for distributed, collaborative, and hypermedia information systems. It works on a client-server model, where the web browser acts as the client. Data such as text, images, and other multimedia files are shared over the World Wide Web using HTTP. As a request and response type protocol, the client sends a request to the server, which is then processed by the server before sending a response back to the client.
HTTP is a stateless protocol, meaning the client and server are only aware of each other while the connection between them is intact. After that, both the client and server forget about each other's existence. Due to this phenomenon, the client and server can't both retain information between requests.
- Memory usage and CPU usage are low because of lesser concurrent connections.
- Errors can be reported without closing connections.
- Owing to lesser TCP connections, network congestion is reduced.
- HTTP lacks encryption capabilities, making it less secure.
- HTTP requires more power to establish communication and transfer data.
5. IMAP and IMAP4: Internet Message Access Protocol (version 4)
IMAP is an email protocol that lets end users access and manipulate messages stored on a mail server from their email client as if they were present locally on their remote device. IMAP follows a client-server model, and lets multiple clients access messages on a common mail server concurrently. IMAP includes operations for creating, deleting, and renaming mailboxes; checking for new messages; permanently removing messages; setting and removing flags; and much more. The current version of IMAP is version 4 revision 1.
- As the emails are stored on the mail server, local storage utilization is minimal.
- In case of accidental deletion of emails or data, it is always possible to retrieve them as they are stored on the mail server.
- Emails won't work without an active internet connection.
- High utilization of emails by end users requires more mailbox storage, thereby augmenting costs.
6. POP and POP3: Post Office Protocol (version 3)
The Post Office Protocol is also an email protocol. Using this protocol, the end user can download emails from the mail server to their own email client. Once the emails are downloaded locally, they can be read without an internet connection. Also, once the emails are moved locally, they get deleted from the mail server, freeing up space. POP3 is not designed to perform extensive manipulations with the messages on the mail server, unlike IMAP4. POP3 is the latest version of the Post Office Protocol.
- Read emails on local devices without internet connection.
- The mail server need not have high storage capacity, as the emails get deleted when they're moved locally.
- If the local device on which the emails were downloaded crashes or gets stolen, the emails are lost.
7. SMTP: Simple Mail Transfer Protocol
SMTP is a protocol designed to transfer electronic mail reliably and efficiently. SMTP is a push protocol and is used to send the email, whereas POP and IMAP are used to retrieve emails on the end user's side. SMTP transfers emails between systems, and notifies on incoming emails. Using SMTP, a client can transfer an email to another client on the same network or another network through a relay or gateway access available to both networks.
- Ease of installation.
- Connects to any system without any restriction.
- It doesn't need any development from your side.
- Back and forth conversations between servers can delay sending a message, and also increases the chance of the message not being delivered.
- Certain firewalls can block the ports used with SMTP.
8. Telnet: Terminal emulation protocol
Telnet is an application layer protocol that enables a user to communicate with a remote device. A Telnet client is installed on the user's machine, which accesses the command line interface of another remote machine that runs a Telnet server program.
Telnet is mostly used by network administrators to access and manage remote devices. To access a remote device, a network admin needs to enter the IP or host name of the remote device, after which they will be presented with a virtual terminal that can interact with the host.
- Compatible with multiple operating systems.
- Saves a lot of time due to its swift connectivity with remote devices.
- Telnet lacks encryption capabilities and sends across critical information in clear text, making it easier for malicious actors.
- Expensive due to slow typing speeds.
9. SNMP: Simple Network Management Protocol
SNMP is an application layer protocol used to manage nodes, like servers, workstations, routers, switches, etc., on an IP network. SNMP enables network admins to monitor network performance, identify network glitches, and troubleshoot them. SNMP protocol is comprised of three components: a managed device, an SNMP agent, and an SNMP manager.
The SNMP agent resides on the managed device. The agent is a software module that has local knowledge of management information, and translates that information into a form compatible with the SNMP manager. The SNMP manager presents the data obtained from the SNMP agent, helping network admins manage nodes effectively.
Currently, there are three versions of SNMP: SNMP v1, SNMP v2, and SNMP v3. Both versions 1 and 2 have many features in common, but SNMP v2 offers enhancements such as additional protocol operations. SNMP version 3 (SNMP v3) adds security and remote configuration capabilities to the previous versions.
Presentation layer network protocols
Lpp: lightweight presentation protocol.
The Lightweight Presentation Protocol helps provide streamlined support for OSI application services in networks running on TCP/IP protocols for some constrained environments. LPP is designed for a particular class of OSI applications, namely those entities whose application context contains only an Association Control Service Element (ACSE) and a Remote Operations Service Element (ROSE). LPP is not applicable to entities whose application context is more extensive, i.e., contains a Reliable Transfer Service Element.
Session layer network protocols
Rpc: remote procedure call protocol.
RPC is a protocol for requesting a service from a program in a remote computer through a network, and can be used without having to understand the underlying network technologies. RPC uses TCP or UDP for carrying the messages between communicating programs. RPC also works on client-server model. The requesting program is the client, and the service providing program is the server.
- RPC omits many protocol layers to improve performance.
- With RPC, code rewriting or redeveloping efforts are minimized.
- Not yet proven to work effectively over wide-area networks.
- Apart from TCP/IP, RPC does not support other transport protocols.
Transport layer network protocols
1. tcp: transmission control protocol.
TCP is a transport layer protocol that provides a reliable stream delivery and virtual connection service to applications through the use of sequenced acknowledgement. TCP is a connection-oriented protocol, as it requires a connection to be established between applications before data transfer. Through flow control and acknowledgement of data, TCP provides extensive error checking. TCP ensures sequencing of data, meaning the data packets arrive in order at the receiving end. Retransmission of lost data packets is also feasible with TCP.
- TCP ensures three things: data reaches the destination, reaches it on time, and reaches it without duplication.
- TCP automatically breaks data into packets before transmission.
- TCP cannot be used for broadcast and multicast connections.
2. UDP: User Datagram Protocol
UDP is a connection-less transport layer protocol that provides a simple but unreliable message service. Unlike TCP, UDP adds no reliability, flow control, or error recovery functions. UDP is useful in situations where the reliability mechanisms of TCP are not necessary. Retransmission of lost data packets isn't possible with UDP.
- Broadcast and multicast connections are possible with UDP.
- UDP is faster than TCP.
- In UDP, it's possible that a packet may not be delivered, be delivered twice, or not be delivered at all.
- Manual disintegration of data packets is needed.
Network layer protocols
1. ip: internet protocol (ipv4).
IPv4 is a network layer protocol that contains addressing and control information, which helps packets be routed in a network. IP works in tandem with TCP to deliver data packets across the network. Under IP, each host is assigned a 32-bit address comprised of two major parts: the network number and host number. The network number identifies a network and is assigned by the internet, while the host number identifies a host on the network and is assigned by a network admin. The IP is only responsible for delivering the packets, and TCP helps puts them back in the right order.
- IPv4 encrypts data to ensure privacy and security.
- With IP, routing data becomes more scalable and economical.
- IPv4 is labor intensive, complex, and prone to errors.
2. IPv6: Internet Protocol version 6
IPv6 is the latest version of the Internet Protocol, a network layer protocol that possesses addressing and control information for enabling packets to be routed in the network. IPv6 was created to deal with IPv4 exhaustion. It increases the IP address size from 32 bits to 128 bits to support more levels of addressing.
- More efficient routing and packet processing compared to IPv4.
- Better security compared to IPv4.
- IPv6 is not compatible with machines that run on IPv4.
- Challenge in upgrading the devices to IPv6.
3. ICMP: Internet Control Message Protocol
ICMP is a network layer supporting protocol used by network devices to send error messages and operational information. ICMP messages delivered in IP packets are used for out-of-band messages related to network operation or misoperation. ICMP is used to announce network errors, congestion, and timeouts, as well assist in troubleshooting.
- ICMP is used to diagnose network issues.
- Sending a lot of ICMP messages increases network traffic.
- End users are affected if malicious users send many ICMP destination unreachable packets.

Data link layer network protocols
1. arp: address resolution protocol.
The Address Resolution Protocol helps map IP addresses to physical machine addresses (or a MAC address for Ethernet) recognized in the local network. A table called an ARP cache is used to maintain a correlation between each IP address and its corresponding MAC address. ARP offers the rules to make these correlations, and helps convert addresses in both directions.
- MAC addresses need not be known or memorized, as the ARP cache contains all the MAC addresses and maps them automatically with IPs.
- ARP is susceptible to security attacks called ARP spoofing attacks.
- When using ARP, sometimes a hacker might be able to stop the traffic altogether. This is also known as ARP denial-of-services.
2. SLIP: Serial Line IP
SLIP is used for point-to-point serial connections using TCP/IP. SLIP is used on dedicated serial links, and sometimes for dial-up purposes. SLIP is useful for allowing mixes of hosts and routers to communicate with one another; for example, host-host, host-router, and router-router are all common SLIP network configurations. SLIP is merely a packet framing protocol: It defines a sequence of characters that frame IP packets on a serial line. It does not provide addressing, packet type identification, error detection or correction, or compression mechanisms.
- Since it has a small overhead, it is suitable for usage in microcontrollers.
- It reuses existing dial-up connections and telephone lines.
- It's easy to deploy since it's based on the Internet Protocol.
DIsadvantages
- SLIP doesn't support automatic setup of network connections in multiple OSI layers at the same time.
- SLIP does not support synchronous connections, such as a connection created through the internet from a modem to an internet service provider (ISP).
Have trouble managing your network?
ManageEngine OpManager is a comprehensive network monitoring tool that monitors the health, performance, and availability of all network devices in an IP network, right out of the box. OpManager utilizes most of the protocols listed above to operate, enabling you to have complete control over your network devices. To learn more about OpManager, register for a free demo or download a free trial .
FAQs on Network protocols
What is protocol in networking.
Networking protocol is a set of rules used for the network devices to communicate effectively with each other. These rules are used to process, send and receive data ensuring data accuracy and security.
What are the types of networking protocols?
Network protocols are classified into seven types based on the OSI model such as:
- Application layer network protocol
- Presentation layer network protocol
- Session layer network protocol
- Transport layer network protocol
- Network layer network protocol
- Data-link layer network protocol
- Physical layer network protocol
What are the most common network protocols?
The most common network protocols include:
- FTP- File Transfer Protocol
- HTTP- HyperText Transfer Protocol
- UDP- User Datagram Protocol
- TCP-Transmission Control Protocol
- SSH-Secure SHell
- BGP-Border Gateway Protocol
- SNMP- Simple Network Management Protocol and
- DNS- Domain Name System
- » Network Monitoring
- » Bandwidth Monitoring & Traffic Analysis
- » Network Configuration Management
- » Switch Port & IP Address Management
- » Firewall Management
- » Network Monitoring Software for MSPs
- » IT Operations Management
- » Application Performance Monitoring
- Download
- Live Demo
- Compare
- Get Quote
- Buy Now
- Download
- Request Demo
- Network Management
- Fault Management
- Storage Management
- Data center management
- Automobile & Aviation
- Banking & Finance
- Engineering & Manufacturing
Quick links
- Free trainings
- Customer Testimonials
- Case studies
Why OpManager
- Alternative to PRTG
- Alternative to Solarwinds
- Alternative to Zabbix
Training and Support
- Contact support
- Training and certification
Connect with us:
ManageEngine is a division of Zoho Corp.

- Network infrastructure
- Kinza Yasar, Technical Writer
- Mary E. Shacklett, Transworld Data
- Amy Novotny, Senior Managing Editor
What is TCP/IP?
TCP/IP stands for Transmission Control Protocol/Internet Protocol and is a suite of communication protocols used to interconnect network devices on the internet. TCP/IP is also used as a communications protocol in a private computer network -- an intranet or extranet .
The entire IP suite -- a set of rules and procedures -- is commonly referred to as TCP/IP. TCP and IP are the two main protocols, though others are included in the suite . The TCP/IP protocol suite functions as an abstraction layer between internet applications and the routing and switching fabric.
TCP/IP specifies how data is exchanged over the internet by providing end-to-end communications that identify how it should be broken into packets , addressed, transmitted, routed and received at the destination. TCP/IP requires little central management and is designed to make networks reliable with the ability to recover automatically from the failure of any device on the network.
Internet Protocol Version 4 ( IPv4 ) is the primary version used on the internet today. However, due to a limited number of addresses, a newer protocol known as IPv6 was developed in 1998 by the Internet Engineering Task Force ( IETF ). IPv6 expands the pool of available addresses from IPv4 significantly and is progressively being embraced.
How are TCP and IP different?
The two main protocols in the IP suite serve specific functions and have numerous differences. The key differences between TCP and IP include the following:
- It ensures a reliable and orderly delivery of packets across networks.
- TCP is a higher-level smart communications protocol that still uses IP as a way to transport data packets, but it also connects computers, applications, web pages and web servers.
- TCP understands holistically the entire stream of data that these assets require to operate and it ensures the entire volume of data needed is sent the first time.
- TCP defines how applications can create channels of communication across a network.
- It manages how a message is assembled into smaller packets before they're transmitted over the internet and reassembled in the right order at the destination address.
- TCP operates at Layer 4, or the transport layer, of the Open Systems Interconnection ( OSI model ).
- TCP is a connection-oriented protocol, which means it establishes a connection between the sender and the receiver before delivering data to ensure reliable delivery.
- As it does its work, TCP can also control the size and flow rate of data. It ensures that networks are free of any congestion that could block the receipt of data. An example is an application that wants to send a large amount of data over the internet. If the application only used IP, the data would have to be broken into multiple IP packets. This would require multiple requests to send and receive data, as IP requests are issued per packet.
- With TCP, only a single request to send an entire data stream is needed; TCP handles the rest.
- TCP runs checks to ensure data is delivered. It can detect problems that arise in IP and request retransmission of any data packets that were lost.
- TCP can reorganize packets so they're transmitted in the proper order. This minimizes network congestion by preventing network bottlenecks caused by out-of-order packet delivery.
- IP is a low-level internet protocol that facilitates data communications over the internet.
- IP delivers packets of data that consist of a header, which contains routing information, such as the source and destination of the data and the data payload itself.
- It defines how to address and route each packet to ensure it reaches the right destination. Each gateway computer on the network checks this IP address to determine where to forward the message.
- IP is limited by the amount of data it can send. The maximum size of a single IP data packet, which contains both the header and the data, is between 20 and 24 bytes. This means that longer strings of data must be broken into multiple data packets that have to be sent independently and then reorganized into the correct order.
- It provides the mechanism for delivering data from one network node to another.
- IP operates at Layer 3, or the network access layer, of the OSI model.
- IP is a connection-less protocol, which means it doesn't guarantee delivery nor does it provide error checking and correction.
Other components in a TCP/IP network
Other components present in a TCP/IP network include subnet masks, network address translation ( NAT ) and various protocols.
A subnet mask tells a computer, or other network device, what portion of the IP address is used to represent the network and what part is used to represent hosts, or other computers, on the network. A NAT is the virtualization of IP addresses. It helps improve security and decrease the number of IP addresses an organization needs.
Common TCP/IP protocols include the following:
- Hypertext Transfer Protocol. HTTP handles the communication between a web server and a web browser.
- HTTP Secure. HTTP Secure handles secure communication between a web server and a web browser.
- File Transfer Protocol . FTP handles transmission of files between computers.
- Domain name system. DNS translates domain names into IP addresses.
- Simple mail transfer protocol. SMTP is used for email communications and is responsible for the transmission of emails between mail servers.
- User datagram protocols. UDP is a connectionless protocol that offers faster but less dependable data delivery. It's widely used in real-time applications such as video streaming and online gaming.
How does TCP/IP work?
TCP/IP uses the client-server model of communication in which a user or machine -- a client -- is provided a service, such as sending a webpage, by another computer -- a server -- in the network.
Collectively, the TCP/IP suite of protocols is classified as stateless, which means each client request is considered new because it's unrelated to previous requests. Being stateless frees up network paths so they can be used continuously.
The transport layer itself, however, is stateful. It transmits a single message and its connection remains in place until all the packets in a message have been received and reassembled at the destination.
The TCP/IP model differs slightly from the seven-layer OSI networking model designed after it. The OSI reference model defines how applications can communicate over a network.
Why is TCP/IP important?
TCP/IP is the fundamental protocol suite that enables data transfer and communication across the internet and other networks. It's nonproprietary and, as a result, isn't controlled by any single company. Therefore, the IP suite can be modified easily. It's compatible with all operating systems (OSes), so it can communicate with any other system. The IP suite is also compatible with all types of computer hardware and networks.
TCP/IP is highly scalable and, as a routable protocol, can determine the most efficient path through the network. It's widely used in current internet architecture.
The 4 layers of the TCP/IP model
TCP/IP functionality is divided into the following four layers, each of which includes specific protocols:
- Application layer. The application layer is the top layer and provides applications with standardized data exchange. Its protocols include HTTP, FTP, Post Office Protocol 3 ( POP3 ), SMTP, DNS, Dynamic Host Configuration Protocol and SNMP . At the application layer, the payload is the actual application data.
- Transport layer. The transport layer is responsible for maintaining end-to-end communications across the network. TCP handles communications between hosts and provides flow control, multiplexing and reliability. The transport protocols include TCP and User Datagram Protocol (UDP), which is sometimes used instead of TCP for special purposes.
- Internet layer. The internet layer, also called the network layer , deals with packets and connects independent networks to transport the packets across network boundaries. The network layer protocols are IP and Internet Control Message Protocol , which are used for error reporting.
- Network link layer. The network link layer, also known as the network interface layer or data link layer , consists of protocols that operate only on a link -- the network component that interconnects nodes or hosts in the network. The protocols in this lowest layer include Ethernet for local area networks and Address Resolution Protocol .
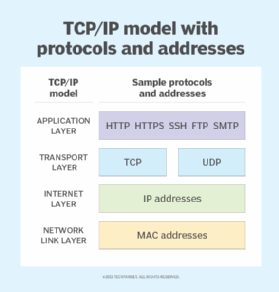
Uses of TCP/IP
TCP/IP can be used for the following tasks:
- Remote login and interactive file transfer. TCP/IP provides remote login over the network for interactive file transfer to deliver email and webpages over the network.
- Remote access to a file system. TCP/IP provides remote access to a server host's file system, enabling users to access and manage files stored on the server from a remote location.
- Represents information flow. TCP/IP is used to represent how information changes form as it travels over a network from the concrete physical layer to the abstract application layer. It details the basic protocols, or methods of communication, at each layer as information passes through.
- End-to-end data transmission. It outlines how end-to-end communications should be achieved by dividing data into packets, addressing them, transmitting them, routing them and receiving them at the destination.
- Cloud computing. TCP/IP is used in cloud computing to facilitate communication between cloud-based services, applications and virtual machines. TCP/IP ensures that cloud resources and clients communicate reliably and securely across the internet.
Pros and cons of TCP/IP
The advantages of using the TCP/IP model include the following:
- It helps establish a connection between different types of computers.
- It works independently of the OS.
- TCP/IP supports many routing protocols.
- It uses a client-server architecture that's highly scalable.
- TCP/IP can be operated independently.
- It supports several routing protocols.
- It's lightweight and doesn't place unnecessary strain on a network or computer.
The disadvantages of TCP/IP include the following:
- It's complicated to set up and manage.
- The transport layer doesn't guarantee the delivery of packets.
- It isn't easy to replace protocols in TCP/IP.
- It doesn't clearly separate the concepts of services, interfaces and protocols, so it isn't suitable for describing new technologies in new networks.
- It's especially vulnerable to synchronization attacks, which are a type of denial-of-service attack in which a bad actor uses TCP/IP.
TCP/IP model vs. OSI model
TCP/IP and OSI are the most widely used communication networking protocols. The main difference between the two models is that OSI is a conceptual model that isn't practically used for communication. Rather, it defines how applications can communicate over a network. TCP/IP, on the other hand, is a practical execution that's widely used to establish links and network interaction.
The TCP/IP protocols lay out standards on which the internet was created, while the OSI model provides guidelines on how communication must be done. Therefore, TCP/IP is a more practical model.
The TCP/IP and OSI models have similarities and differences . The main similarity is in the way they're constructed to both use layers, although TCP/IP consists of just four layers, while the OSI model consists of the following seven layers:
- Layer 7 : the application layer, lets the user -- software or human -- interact with the application or network when the user wants to read messages, transfer files or engage in other network-related activities.
- Layer 6 : the presentation layer , translates or formats data for the application layer based on the semantics or syntax that the app accepts.
- Layer 5 : the session layer , sets up, coordinates and terminates conversations between apps.
- Layer 4 : the transport layer , transfers data across a network and provides error-checking mechanisms and data flow controls.
- Layer 3 : the network layer , moves data into and through other networks.
- Layer 2 , the data link layer , handles problems that occur as a result of bit transmission errors.
- Layer 1 : the physical layer , transports data using electrical, mechanical or procedural interfaces.
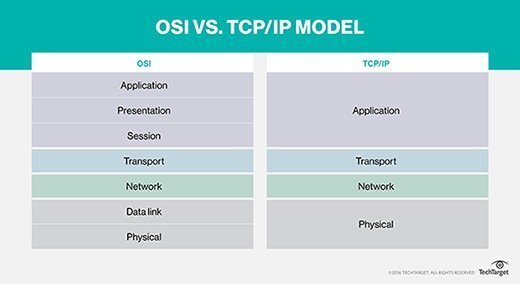
The application layer is the upper layer for both the TCP/IP model and the OSI model. Although this layer performs the same tasks in each model, those tasks can vary depending on the data each receives.
The functions performed in each model are also similar because each uses a network layer and transport layer to operate. The TCP/IP and OSI models are each mostly used to transmit data packets. Although they use different means and different paths, they still reach their destinations.
The similarities between the TCP/IP model and the OSI model include the following:
- They're both logical models.
- They define networking standards.
- They divide the network communication process into layers.
- They provide frameworks for creating and executing networking standards and devices.
- They enable one manufacturer to make devices and network components that can coexist and work with the devices and components made by other manufacturers.
The differences between the TCP/IP model and the OSI model include the following:
- TCP/IP uses just one layer -- the application layer -- to define the functionalities of the upper layers, while OSI uses three layers -- application, presentation and session.
- TCP/IP uses one layer -- the physical layer -- to define the functionalities of the bottom layers, while OSI uses two layers -- physical and data link.
- The TCP/IP header size is 20 bytes, while the OSI header is 5 bytes.
- TCP/IP is a protocol-oriented standard, whereas OSI is a generic model based on the functionalities of each layer.
- TCP/IP follows a horizontal approach, while OSI follows a vertical approach.
- In TCP/IP, the protocols were developed first and then the model. In OSI, the model was developed first and then the protocols in each layer were developed.
- TCP/IP helps establish a connection between different types of computers, whereas OSI helps standardize routers , switches, motherboards and other hardware.
The history of TCP/IP
The Defense Advanced Research Projects Agency , the research branch of the U.S. Department of Defense, created the TCP/IP model in the 1970s for use in ARPANET , a wide area network that preceded the internet. TCP/IP was originally designed for the Unix OS, and it has been built into all the OSes that came after it.
The TCP/IP model and its related protocols are now maintained by the IETF.
Protocols are the building block of networks. Discover the roles and functionalities of the most used network protocols .
Continue Reading About TCP/IP
- What to know about UDP vulnerabilities and security
- Factors to consider in network redundancy design
- Intro to encapsulation and decapsulation in networking
- Most commonly used IoT protocols and standards
- What's the difference between a MAC address and IP address?
Related Terms
Dig deeper on network infrastructure.

An explanation of TCP/IP

Transmission Control Protocol (TCP)

network load balancing (NLB)

session layer

Microsoft 365 Copilot, an AI assistant, offers several promising features. Find out how to configure Copilot with Teams workflows...
With its AI capabilities, Microsoft Copilot provides several enhancements to Microsoft Teams functionality, including meeting ...
Organizations have ramped up their use of communications platform as a service and APIs to expand communication channels between ...
Auditing is a crucial part of mobile device security, but IT admins must ensure their approach is thorough and consistent. Learn ...
With the right software, almost any mobile device can be a payment terminal. Learn about the mobile point-of-sale options beyond ...
To keep corporate and user data safe, IT must continuously ensure mobile app security. Mobile application security audits are a ...
Lenovo adds to its AI portfolio with a new GPU-as-a-service offering, a move that challenges Dell and HPE. It also adds ...
AT&T claims its negotiated contract with VMware pre-Broadcom acquisition is not being honored, casting light on recent product ...
Rocky Linux and AlmaLinux are new distributions created after Red Hat announced the discontinuation of CentOS. These ...
Popular pricing models for managed service providers include monitoring only, per device, per user, all-you-can-eat or ...
Global IT consultancies take a multilayered approach to GenAI training by developing in-house programs, partnering with tech ...
IT service providers are upskilling a large portion of their workforces on the emerging technology. The campaign seeks to boost ...

What are Communication Protocols & Their Working
In the digital world, communication protocols create many rules. For instance, on the Internet, the formation of these protocols can be done by groups such as the association of WWW (World Wide Web) or W3C & the IETF (Internet Engineering Task) assists in providing worldwide operations & limits different types of liability as well as vulnerabilities within these technologies. Communication protocol plays a key role when HTTP turns into HTTPS otherwise an extensive use of SSL (Secure Sockets Layer) certificate becomes the standard. Other types of protocols use the data packets within global network routes and sometimes its looks like particle physics. So, technology is advancing day by day, so different communication protocols are used in advanced networks. The Internet of Things (IoT) assures the latest developing communications protocols to connect the wide set of devices to a universal network. This article discusses an overview of communication protocols in embedded systems.
What are Communication Protocols?
The proper descriptions of digital message formats as well as rules are known communication protocols. The main function of these protocols is to exchange messages from one computer system to another. These are significant in telecommunications systems as they consistently send and receive messages. These protocols cover error detection & correction, signaling, and authentication. They can also explain the semantics, syntax & brings analog & digital communications together.

The implementation of these protocols can be done within hardware as well as software. So communications protocols are available around thousand types which are used all over in analog & digital communications, so computer networks cannot be present without them.
Introduction
- Protocol : A set of rules and regulations is called a protocol.
- Communication: Exchange of information from one system to another system with a medium is called communication.
- Communication Protocol: A set of rules and regulations that allow two electronic devices to connect to exchange the data with one and another.
Why is Communication Protocol Important?
Communication protocols assist varied network devices to converse with each other by transmitting the analog signals, digital signals, different files & process the data from one device to other devices. These types of protocols are applicable in telecommunication & computer networks where suitable rules are executed to transmit information from source to destination. The most vital protocols within networking are TCP (Transmission Control Protocol) & User datagram protocol (UDP).
Types of Communication Protocols
There are two types of communication protocols which are classified below:
Inter System Protocol
Intra system protocol.
The inter-system protocol using to communicate the two different devices. Like communication between computer to microcontroller kit. The communication is done through an inter bus system.

The different categories of intersystem protocol mainly include the following.
UART Protocol
Usart protocol, usb protocol.
UART stands for a universal asynchronous transmitter and receiver. UART Protocols is a serial communication with two wired protocols. The data cable signal lines are labeled as Rx and Tx. Serial communication is commonly used for transmitting and receiving the signal. It is transferred and receives the data serially bit by bit without class pulses. The UART takes bytes of data and sends the individual bits in a sequential manner.
UART is a half-duplex protocol. Half-duplex means transferring and receiving the data but not at the same time. Most of the controllers have hardware UART on board. It uses a single data line for transmitting and receiving the data. It has one start bit, 8-bit data and a one-stop bit mean the 8-bit data transfer one’s signal is high to low.
Ex: Emails, SMS, Walkie-talkie.
USART stands for a universal synchronous and asynchronous transmitter and receiver. It is a serial communication of a two-wire protocol. The data cable signal lines are labeled as Rx and TX. This protocol is used to transmitting and receiving the data byte by byte along with the clock pulses. It is a full-duplex protocol that means transmitting and receiving data simultaneously to different board rates. Different devices communicate with microcontroller to this protocol.
Ex:-Telecommunications.
USB stands for universal serial bus. Again it is a serial communication of two-wire protocol. The data cable signal lines are labeled D+ and D-. This protocol is used to communicate with the system peripherals.USB protocol is used to send and receive the data serially to the host and peripheral devices.USB communication requires driver software that is based on the functionality of the system.USB devices can transfer data on the bus without any request on the host computer.
Now a day’s most devices are using this technique for communicating with USB protocol. Like a computer to communicate with an ARM controller using USB. USB transfer the data to different modes .first one is slow speed mode 10kbps to 100 kbps; the second one is full speed mode 500kbps to 10mbps, high-speed mode 25mbps to 400 Mbps.USB maximum cable length of 4 meters.
Ex: Mouse, Keyboard, Hubs, switches, pen drive.
Differences Between the Inter System Protocols
The intersystem protocols mainly include UART, USART, and USB
|
| ||
| The term UART stands for Universal Asynchronous Transmitter and Receiver | The term USART stands for Universal Synchronous and Asynchronous Data Transmitter and Receiver | The term USB stands for Universal Serial Bus |
| UART mainly includes two wire-based protocols like transmitter and receiver | USART is a two-wire protocol like Transmitter and Receiver | USB is a two-wire protocol like D+ & D- |
| It transmits as well as receives pockets of data by byte without classes pulse | It transmits and receives a block of data through classes pulses | It transmits and receives the data through clock pulses |
| UART is a half-duplex communication | USART is a full-duplex communication | USB is also full-duplex communication |
| UART is slow as compared to USART | USART is slow as compared to USB | It is fast as compared to USART and UART |
The Intra system protocol is used to communicate the two devices within the circuit board. While using these intra system protocols, without going to intrasystem protocols we will expand the peripherals of the microcontroller. The circuit complexity and power consumption will be increased by using the intrasystem protocol. Using intra system protocols circuit complexity and power consumption, the cost is decreased and it is very secure to accessing the data.

The different categories of intrasystem protocol mainly include the following.
I2C Protocol
Spi protocol, can protocol.
I2C stands for the inter-integrated circuit and it requires only two wires connecting all peripherals to the microcontroller. I2C requires two wires SDA (serial data line) and SCL (serial clock line) to carry information between devices. It is a master to a slave communication protocol. Each slave has a unique address. The master device sends the address of the target slave device and reads/writes the flag. The address matches any slave device that the device is ON, the remaining slave devices are disabled mode.
Once the address is match communication proceed between the master and that slave device and transmitting and receiving the data. The transmitter sends 8-bit data, the receiver replies 1-bit of acknowledgment. When the communication is completed master issues the stop condition. The I2C bus was developed by Philips Semiconductors. Its original purpose is to provide an easy way to connect CPU to peripherals chips.
Peripheral devices in embedded systems are often connected to the microcontroller as memory-mapped devices. I2C requires only two wires for connecting all the peripherals to the microcontroller. These active wires, called SDA and SCL, are both bidirectional. SDA line is a serial data line and the SCA line is a serial clock line.
I2C Pull-up Resistors
Why given the pull-up resistors in I2C SCL and SDA line.
- Both SDA and SCL lines are open-drain drivers.
- It can drive output low canot driver it high.
- For the lines to be able to go high you must provide pull-up resistors
SPI stands for the serial peripheral interface. It is one of the serial communication protocol developed by Motorola. Sometimes SPI protocol is also called a 4-wire protocol. It requires four wires MOSI, MISO, SS, and SCLK.SPI protocol used to communicate the master and slave devices. The master first configures the clock using a frequency.
The master then selects the particular slave device for communication by pulling the chip select button. That particular device is selected and starts the communication between the master and that particular slave. The master selects only one slave at a time. It is a full-duplex communication protocol. Not limited to 8-bit words in the case of bit transferring.
CAN stands for the controller area network. It is a serial communication protocol. It requires two wires CAN High (H+) and CAN low (H-). It was developed by the Robert bosh company in 1985 for in-vehicle networks. It is based on a message-oriented transmission protocol.
Differences Between the Intra System Protocols
The intra system protocols mainly include I2C, SPI, and CAN
|
| ||
| I2C is an inter-integrated circuit | SPI stands for serial peripheral interface | The CAN stands for controller area network |
| It is implemented by Philips | SPI is developed by Motorola | CAN is developed by Bosch |
| I2C is a half-duplex protocol | SPI is a full-duplex protocol | CAN is a full-duplex protocol |
| Synchronization | Synchronization | Synchronization |
| It is a two-wire protocol like SCL & SDL | It is a four-wire protocol like SCL, MISO, MOSI & SS | It is a two-wire protocol like CANH+ and CAN H- |
| It is a multi-master protocol | It is a single master protocol | It is a multi-master protocol |
| It is used in the circuit board | It is used in the circuit board | It is used in two circuit board |
Communication Protocols in IoT
The IoT based devices are more susceptible to threats. So these security loopholes can be reduced by using the correct protocols. Communication protocols in IoT are types of communication that ensure the finest security toward the data being exchanged among the IoT connected devices.
The connection of these devices can be done through an IP network otherwise a non IP network but, there is a disparity within their power, range & memory used. The connection throughout IP networks is difficult & takes huge memory as well as power from these devices as the range is not a trouble. Alternatively, Bluetooth which is known as non-IP networks needs low power and memory however they have a limitation in the range.
The main benefits of IoT communication protocols are high quality, credibility, interoperability, innovation flexibility & global scalability. IoT protocols are available in two types mainly IoT network protocols and IoT data protocols.
The list of Top 10 IoT Communication Protocols includes the following.
- NFC (Near Field Communication)
Data Communication Protocols
Data communication protocols are very significant for communication because they are used for understanding the networks or computers or devices to each other.
These types of protocols use typical rules as well as methods like a common language to interact with computers or networks to each other. For instance, if a user wants to send an e-mail to another, then the user will create the e-mail on his personal computer by including the details along with the message and attachments. Once the user sends the e-mail, then immediately multiple actions can take place so that the receiver gets the email. The message moves over the network and reaches the recipient. These protocols provide the information on how the note will be enclosed so that it can move over the system, how the receiver computer can verify for errors, etc
PLC Communication Protocols
The following primary communication protocols are used for the PLC as well as other connections of the network which supports through different PLC software products. These protocols mainly depend on the basic three parts like baud rate, length of network & the number of nodes. The list of PLC communication protocols includes the following.
- DF-1 Protocol
- Host Link Protocol
- Mechatrolink
- PPI- Point to Point
- Ethernet Powerlink
- Multi-Point Interface (MPI)
- Data Highway (DH)
- Actuator Sensor Interface (ASI)
- Highway Addressable Remote Transducer Protocol (HART)
- Ethernet Global Data (EGD)
- Factory Interface Network Service Protocol (FINS)
- Open Smart Grid Protocol (OSGP)
- Recommended Standard (RS-232, RS- 422, and RS-485) Protocols
- Bristol Standard Asynchronous Protocol (BSAP)
- Distributed Network Protocol (DNP3)
- Service Request Transport Protocol (SRTP)
- Smart Distributed System Protocol (SDS)
- Process Image Exchange Protocol (PIEP)
Characteristics of PLC Communication Protocols
The standard protocols are used once PLC modules are connected over the network. The different types these protocols mainly supports different speed, distance & the number of connecting devices.
- Ethernet protocol baud rate is 100 Mb/s, length is Few Km and 255 nodes.
- RS-485 baud rate is 10 Kb/s, the length is 1.2 Km, and 32 nodes
- Profibus protocol baud rate is 5-12 Mb/s, the length is 15 Km and 127 nodes.
- RS-232 baud rate is 19.2 Kb/s, the length is 10m and 1 node
- MPI protocol baud rate is 19.2- 38.4 Kb/s, the length is 50 m and 32 nodes.
- PC Adapter baud rate is 9600 Kb/s, length is 15 m, and 1 node
- PPI protocol baud rate is 187.5 Kb/s, the length is 500 m, and 1 node.
- USB Adapter baud rate is 57.6 Kb/s, the length is 10 m and 1sec
- DH protocol baud rate is 230.4 Kb/s, the length is 3.048 Km, and 64 nodes
- Device Net protocol braud rate is 500 Kb/s, the length is 0.487, and 64 nodes
- Control Net protocol baud rate is5 Mb/s, the length is 30 Km
Communication Protocols in Cloud Computing
The cloud supports two communication protocols for communication as well as connection like MQTT and HTTP. The communication of these devices can be done through Cloud IoT Core across a bridge either the HTTP or the MQTT. These bridges are central components in Cloud IoT Core. Once you create a registry of a device, then you can choose protocols to allow HTTP, MQTT, etc. The standard protocol like MQTT is used frequently and it is supported through embedded devices. This protocol is common in the interactions of the machine to machine.
HTTP is a connectionless protocol, so devices do not maintain a connection to the cloud IoT core. As an alternative, they send requests as well as get responses. The protocols of cloud computing are a set of rules that permit two electronic elements to unite as well as exchange the data with each other. It is mainly used for communication, storage, encryption, networks, decryption, security, management of user login, etc. Some cloud computing protocols include
- Gossip Protocol
- MTP (Media Transfer Protocol)
- CLNP (Connection Less Network Protocol)
- CEE (Coverage Enhanced Ethernet Protocol)
- SRP (State Routing Protocol)
- SSHP (Secure Shell Protocol)
- IGMP (Internet Group Management Protocol)
Thus, this is all about an overview of communication protocols , types, differences between inter-system protocol and intrasystem protocol. Here is a question for you, what are Arduino communication protocols?
Share This Post:

Comments are closed.
New York University
Computer Science Department
Courant Institute of Mathematical Sciences
Course Title: Data Communication & Networks Course Number: g22.2662-001
Instructor: Jean-Claude Franchitti Session: 4
Assignment #2
I. Due Thurday March 6, 2008, at the beginning of class.
II. Objectives
- See protocols in action.
III. References
- Slides and handouts posted on the course Web site
- Textbook chapters as applicable
IV. Software Required
- Wireshark Packet Sniffer and Packet Capture Library (see section V below).
- Microsoft Word.
- Win Zip as necessary.
V. Assignment
Preamble and Disclaimer:
As noted on the corresponding SourceForge site, the Ethereal development team switched names from Ethereal to Wireshark in May 2006 due to trademark issues (see http://www.wireshark.org/faq.html#q1.2 for more details on this). Incidentally, some people pronounce the name Ethereal as “ether-real,” while others pronounce it “e-thir-E-al,” as in the English word ethereal, which means ghostly or insubstantial. The Ethereal name’s origin comes from the Ethernet protocol, a link-level protocol that is studied extensively in Chapter 5 of the textbook, and in the class labs.
1. Wireshark Lab - Getting Started
One’s understanding of network protocols can often be greatly deepened by “seeing protocols in action” and by “playing around with protocols” – observing the sequence of messages exchanged between two protocol entities, delving down into the details of protocol operation, and causing protocols to perform certain actions and then observing these actions and their consequences. This can be done in simulated scenarios or in a “real” network environment such as the Internet. The Java applets that accompany the textbook take the first approach. In the Wireshark labs, we’ll take the latter approach. You’ll be running various network applications in different scenarios using a computer on your desk, at home, or in a lab. You’ll observe the network protocols in your computer “in action,” interacting and exchanging messages with protocol entities executing elsewhere in the Internet. Thus, you and your computer will be an integral part of “live” labs in this class. You’ll observe, and you’ll learn, by doing.
The basic tool for observing the messages exchanged between executing protocol entities is called a packet sniffer . As the name suggests, a packet sniffer captures (“sniffs”) messages being sent/received from/by your computer; it will also typically store and/or display the contents of the various protocol fields in these captured messages. A packet sniffer itself is passive. It observes messages being sent and received by applications and protocols running on your computer, but never sends packets itself. Similarly, received packets are never explicitly addressed to the packet sniffer. Instead, a packet sniffer receives a copy of packets that are sent/received from/by application and protocols executing on your machine.
Figure 1 shows the structure of a packet sniffer. At the right of Figure 1 are the protocols (in this case, Internet protocols) and applications (such as a web browser or ftp client) that normally run on your computer. The packet sniffer, shown within the dashed rectangle in Figure 1 is an addition to the usual software in your computer, and consists of two parts. The packet capture library receives a copy of every link-layer frame that is sent from or received by your computer. Recall from the discussion from section 1.5.2 in the text (Figure 1.20 in the 4 th Edition of the textbook used for the class) that messages exchanged by higher layer protocols such as HTTP, FTP, TCP, UDP, DNS, or IP all are eventually encapsulated in link-layer frames that are transmitted over physical media such as an Ethernet cable. In Figure 1, the assumed physical media is an Ethernet, and so all upper layer protocols are eventually encapsulated within an Ethernet frame. Capturing all link-layer frames thus gives you all messages sent/received from/by all protocols and applications executing in your computer.
The second component of a packet sniffer is the packet analyzer , which displays the contents of all fields within a protocol message. In order to do so, the packet analyzer must “understand” the structure of all messages exchanged by protocols. For example, suppose we are interested in displaying the various fields in messages exchanged by the HTTP protocol in Figure 1. The packet analyzer understands the format of Ethernet frames, and so can identify the IP datagram within an Ethernet frame. It also understands the IP datagram format, so that it can extract the TCP segment within the IP datagram. Finally, it understands the TCP segment structure, so it can extract the HTTP message contained in the TCP segment. Finally, it understands the HTTP protocol and so, for example, knows that the first bytes of an HTTP message will contain the string “GET,” “POST,” or “HEAD,” as shown in Figure 2.8 in the text.
We will be using the Wireshark packet sniffer (i.e., www.wireshark.org) for these labs, allowing us to display the contents of messages being sent/received from/by protocols at different levels of the protocol stack. (Technically speaking, Wireshark is a packet analyzer that uses a packet capture library in your computer). Wireshark is a free network protocol analyzer that runs on Windows, Linux/Unix, and Mac computers. It’s an ideal packet analyzer for our labs – it is stable, has a large user base and well-documented support that includes:
(a) A user-guide (i.e., http://www.wireshark.org/docs/ )
(b) Man pages (i.e., http://www.wireshark.org/docs/man-pages/ )
(c) A detailed FAQ (i.e., http://www.wireshark.org/faq.html )
(d) Rich functionality that includes the capability to analyze more than 500 protocols
(e) A well-designed user interface
The Wireshark packet sniffer operates in computers using Ethernet to connect to the Internet, as well as so-called point-to-point protocols such as PPP.
2. Wireshark Lab – Getting Wireshark
In order to run Wireshark, you will need to have access to a computer that supports both Wireshark and the libpcap packet capture library. If the libpcap software is not installed within your operating system, you will need to install libpcap or have it installed for you in order to use Wireshark. See http://www.wireshark.org/download.html for a list of supported operating systems and download sites.
Download and install the Wireshark and (if needed) the libpcap software:
· If needed, download and install the libpcap software. Pointers to the libpcap software are provided from the Wireshark download pages. For Windows machines, the libpcap software is known as WinPCap , and can be found at http://winpcap.mirror.ethereal.com/ .
· Go to www.wiresharkl.org and download and install the Wireshark binary for your computer. It is recommended to download from http://sourceforge.net/project/showfiles.php?group_id=255 which includes a WinPCap bundle option.
· Download the Wireshark user guide. You will most likely only need Chapters 1 and 3.
The Wireshark FAQ has a number of helpful hints and interesting tidbits of information, particularly if you have trouble installing or running Wireshark.
3. Wireshark Lab – Running Wireshark
When you run the Wireshark program, the Wireshark graphical user interface shown in Figure 2a will be displayed. Initially, no data will be displayed in the various windows.
Figure 2a: Wireshark Capture Options Window
Figure 2 below shows the original Ethereal graphical user interface along with an explanation of the various areas which applies to both Ethereal and Wireshark.
The Wireshark interface has five major components:
· The command menus are standard pulldown menus located at the top of the window. Of interest to us now are the File and Capture menus. The File menu allows you to save captured packet data or open a file containing previously captured packet data, and exit the Wireshark application. The Capture menu allows you to begin packet capture.
· The packet-listing window displays a one-line summary for each packet captured, including the packet number (assigned by Wireshark; this is not a packet number contained in any protocol’s header), the time at which the packet was captured, the packet’s source and destination addresses, the protocol type, and protocol-specific information contained in the packet. The packet listing can be sorted according to any of these categories by clicking on a column name. The protocol type field lists the highest level protocol that sent or received this packet, i.e., the protocol that is the source or ultimate sink for this packet.
· The packet-header details window provides details about the packet selected (highlighted) in the packet listing window. (To select a packet in the packet listing window, place the cursor over the packet’s one-line summary in the packet listing window and click with the left mouse button.). These details include information about the Ethernet frame and IP datagram that contains this packet. The amount of Ethernet and IP-layer detail displayed can be expanded or minimized by clicking on the right-pointing or down-pointing arrowhead to the left of the Ethernet frame or IP datagram line in the packet details window. If the packet has been carried over TCP or UDP, TCP or UDP details will also be displayed, which can similarly be expanded or minimized. Finally, details about the highest level protocol that sent or received this packet are also provided.
· The packet-contents window displays the entire contents of the captured frame, in both ASCII and hexadecimal format.
· Towards the top of the Wireshark graphical user interface, is the packet display filter field, into which a protocol name or other information can be entered in order to filter the information displayed in the packet-listing window (and hence the packet-header and packet-contents windows). In the example below, we’ll use the packet-display filter field to have Wireshark hide (not display) packets except those that correspond to HTTP messages.
4. Wireshark Lab – Taking Wireshark for a Test Run
The best way to learn about any new piece of software is to try it out! Do the following
1. Start up your favorite web browser, which will display your selected homepage.
2. Start up the Wireshark software. You will initially see a window similar to that shown in Figure 2, except that no packet data will be displayed in the packet-listing, packet-header, or packet-contents window, since Wireshark has not yet begun capturing packets.
3. To begin packet capture, select the Capture pull down menu and select Options . This will cause the “Wireshark: Capture Options” window to be displayed, as shown in Figure 3.
Figure 3: Wireshark Capture Options Window
4. You can use all of the default values in this window. The network interfaces (i.e., the physical connections) that your computer has to the network will be shown in the Interface pull down menu at the top of the Capture Options window. In case your computer has more than one active network interface (e.g., if you have both a wireless and a wired Ethernet connection), you will need to select an interface that is being used to send and receive packets (mostly likely the wired interface). After selecting the network interface (or using the default interface chosen by Wireshark), click Start . Packet capture will now begin - all packets being sent/received from/by your computer are now being captured by Wireshark!
5. After you begin packet capture, you can select Statistics > Protocol Hierarchy from the command menus to obtain a summary of the number of packets of various types that are being captured as shown in Figure 4.
Figure 4: Wireshark Protocol Hierarchy Statistics
6. While Wireshark is running, enter the URL: http://gaia.cs.umass.edu/ethereal-labs/INTRO-ethereal-file1.html and have that page displayed in your browser. In order to display this page, your browser will contact the HTTP server at gaia.cs.umass.edu and exchange HTTP messages with the server in order to download this page, as discussed in section 2.2 of the text. The Ethernet frames containing these HTTP messages will be captured by Wireshark.
7. After your browser has displayed the INTRO-ethereal-file1.html page, stop Wireshark packet capture by selecting Capture > Stop in the Wireshark in the command menus. The Wireshark window will display all packets captured since you began packet capture. The Wireshark window should now look similar to Figure 2. You now have live packet data that contains all protocol messages exchanged between your computer and other network entities! The HTTP message exchanges with the gaia.cs.umass.edu web server should appear somewhere in the listing of packets captured. But there will be many other types of packets displayed as well (see, e.g., the many different protocol types shown in the Protocol column in Figure 2). Even though the only action you took was to download a web page, there were evidently many other protocols running on your computer that are unseen by the user. We’ll learn much more about these protocols as we progress through the text! For now, you should just be aware that there is often much more going on than “meet’s the eye”!
8. Type in “http” (without the quotes, and in lower case – all protocol names are in lower case in Wireshark) into the display filter specification window at the top of the main Wireshark window. Then select Apply (to the right of where you entered “http”). This will cause only HTTP message to be displayed in the packet-listing window.
9. The HTTP GET message that was sent from your computer to the gaia.cs.umass.edu HTTP server should be shown among the first few http message shown in the packet-listing window. When you select the HTTP GET message, the Ethernet frame, IP datagram, TCP segment, and HTTP message header information will be displayed in the packet-header window. Recall that the HTTP GET message that is sent to the gaia.cs.umass.edu web server is contained within a TCP segment, which is contained (encapsulated) in an IP datagram, which is encapsulated in an Ethernet frame. If this process of encapsulation isn’t quite clear yet, review section 1.5 in the text. By clicking on the expansion buttons (+ or -) to the left side of the packet details window, you can minimize or maximize the amount of Frame, Ethernet, Internet Protocol, and Transmission Control Protocol information displayed. Maximize the amount information displayed about the HTTP protocol. Your Wireshark display should now look roughly as shown in Figure 5 (Note, in particular, the minimized amount of protocol information for all protocols except HTTP, and the maximized amount of protocol information for HTTP in the packet-header window).
10. Exit Wireshark
Figure 5: Wireshark Display After Step 9
Congratulations! You’ve now completed the first lab.
5. Wireshark Lab – What to hand in
The goal of this first lab was primarily to introduce you to Wireshark. The following questions will demonstrate that you’ve been able to get Wireshark up and running, and have explored some of its capabilities. Answer the following questions, based on your Wireshark experimentation.
1. What is the MAC address of your Host? You can find this in the frame level information.
2. List the different protocols that appear in the protocol column in the unfiltered packet-listing window in step 4.7 above.
3. How long did it take from when the HTTP GET message was sent until the HTTP OK reply was received? (By default, the value of the Time column in the packet-listing window is the amount of time, in seconds, since Wireshark tracing began. To display the Time field in time-of-day format, select the Wireshark View pull down menu, then select Time Display Format , then select Time-of-day .)
4. What is the Internet address of the gaia.cs.umass.edu (also known as www-net.cs.umass.edu)? What is the Internet address of your computer?
5. Print the two HTTP messages displayed in step 4.9 above. To do so, select Print from the Wireshark File command menu, and select “ Selected Packet Only” under Packet Range and “As displayed” under Packet Format and then click OK.
Save your capture in a capture file named Nxxx.cap where Nxxx is your student ID.
Submit this capture file and the answers to the questions above.
Email your assignment (archive) file to your TA.
VI. Deliverables
- Electronic: Your assignment (archive) file must be emailed to the TA. The file must be created and sent by the beginning of class. After the class period, the homework is late. The email clock is the official clock.
- Written: Printout of the file(s) included in your assignment (archive) file. The cover page supplied on the next page must be the first page of your assignment file
Fill in the blank area for each field.
The sequence of the hardcopy submission is:
1. Cover sheet
1. Assignment Answer Sheet(s)
VII. Sample Cover Sheet
Name ________________________ Username: ______________ Date: ____________ (last name, first name) Section: ___________
Assignment 2
Assignment Layout (25%)
o Assignment is neatly assembled on 8 1/2 by 11 paper.
o Cover page with your name (last name first followed by a comma then first name), username and section number with a signed statement of independent effort is included.
o Answers to all assignment questions are correct. o File name is correct.
Total in points ___________________ Professor’s Comments:
Affirmation of my Independent Effort: _____________________________
(Sign here)
- System Design Tutorial
- What is System Design
- System Design Life Cycle
- High Level Design HLD
- Low Level Design LLD
- Design Patterns
- UML Diagrams
- System Design Interview Guide
- Crack System Design Round
- System Design Bootcamp
- System Design Interview Questions
- Microservices
- Scalability
Why are Communication Protocols important in System Design?
Communication protocols serve as the backbone of modern computing systems, enabling devices and components to exchange information seamlessly and reliably. In system design, the choice and implementation of communication protocols play a critical role in determining the performance, scalability, and robustness of the system.
Communication protocols are essential in system design for several key reasons:
1. Interoperability
Communication protocols define a common language and set of rules for different components to communicate effectively. This ensures that components from different vendors or platforms can work together seamlessly, enabling interoperability in complex systems.
2. Reliability
Communication protocols provide mechanisms for error detection, correction, and recovery, ensuring that data is transmitted reliably even in the presence of network issues or failures. This is crucial for maintaining the integrity and consistency of data in distributed systems.
3. Performance
Efficient communication protocols can significantly impact the performance of a system. By optimizing data transmission and reducing overhead, protocols can help improve latency, throughput, and overall system responsiveness.
4. Scalability
Scalability is a key consideration in system design, especially for large-scale distributed systems. Communication protocols that support scalability, such as those based on asynchronous messaging or distributed computing principles, can help ensure that the system can grow to accommodate increasing demands.
5. Security
Communication protocols play a crucial role in ensuring the security of data transmission. Protocols that support encryption, authentication, and secure channels help protect sensitive information from unauthorized access or tampering.
6. Flexibility and Extensibility
Well-designed communication protocols are flexible and extensible, allowing them to adapt to changing requirements and accommodate new features or functionalities without requiring significant changes to the underlying system architecture.
In summary, communication protocols are a fundamental aspect of system design, providing the foundation for efficient, reliable, and secure communication between components. The careful selection and implementation of communication protocols are essential for building robust and scalable systems that can meet the demands of modern computing environments
Please Login to comment...
Similar reads.
- System Design
- System Design QnA
- OpenAI o1 AI Model Launched: Explore o1-Preview, o1-Mini, Pricing & Comparison
- How to Merge Cells in Google Sheets: Step by Step Guide
- How to Lock Cells in Google Sheets : Step by Step Guide
- PS5 Pro Launched: Controller, Price, Specs & Features, How to Pre-Order, and More
- #geekstreak2024 – 21 Days POTD Challenge Powered By Deutsche Bank
Improve your Coding Skills with Practice
What kind of Experience do you want to share?
Assignment 14 Networking and communication
"Hi everyone ,Week 14 Networking and communications.This week is realy important as my project point of view.Since i am thinking of to establish a wi-fi network for my board and talked to web server.So i am looking to finish it.
Group assignment
- Send a message between two projects
Individual assignment
- Design, build, and connect wired or wireless node(s) with network or bus addresses
- Wired or wireless node(s)with network or bus addresses
Table of Content
- Types of communication
- About serial communication
- Synchronous Serial Protocols
- SPI Protocol
- I2C Serial Communication
- Asynchronous Serial Protocols
- Designing Attiny 45 bridge and node boards for asynchronous serial communication
- Schematic of bridge & nodes boards
- Board layout of bridge & nodes boards
- Milling & soldering of Bridge & nodes boards
- Programming Attiny 45 bridge & node boards
- Test the communication between Atiny 45 bridge & node boards
Asynchronous Serial Communication With AT Commands
- About ESP-01
- Pin configuration of ESP -01
- Hardware requirment
- Interface Arduino with ESP -01
Run AT commands to establish a wi-fi environment for arduino
- Run AT commands to talk to webserver
- Learning outcomes
Project work:
Types of commuincation protocols.
There are different types of data transfer available in the digital electronics such as serial communication and parallel communication. Similarly the protocols are divided into two types such as Serial Communication Protocol and Parallel Communication Protocols. Examples of Parallel Communication Protocols are ISA, ATA, SCSI, PCI and IEEE-488. Similarly there are several examples of Serial Communication Protocols such as CAN, ETHERNET, I2C, SPI, RS232, USB, 1-Wire, and SATA etc.
Two types of communication
- 1.Serial communication
- 2.Parallel communication
- Comparision of Serial Vs Prallel communication
- Serial communication

- Parallel communication

1. About Serial Commuincation Protocols

What is serial communication Protocol?
Before starting with Serial Communication Protocols, Let’s break the terminology in three parts. The communication is very well known terminology which involves the exchange of information between two or more mediums. In embedded systems, the communication means the exchange of data between two microcontrollers in the form of bits. This exchange of data bits in microcontroller is done by some set of defined rules known as communication protocols. Now if the data is sent in series i.e. one after the other then the communication protocol is known as Serial Communication Protocol. More specifically, the data bits are transmitted one at a time in sequential manner over the data bus or communication channel in Serial Communication. Refer from circuitdigest.com
1.1 Synchronous Serial Communication
1.1.1 spi protocol.
Communication in SPI is done by a master and slave relationship, in which master initiates data frame. When the master generates the clock and selects a slave the data can be transferred either in one or in both the direction simultaneously.

1.1.2 I2C Serial Communication
I2C interface is a simple bidirectional interface which uses a single data line to transmit and receive the data. I2C is a serial 2 wire bus designed to communicate between the IC’s using a minimum number of pins. It is half duplex, synchronous serial communication protocol. The data transmission always initiated by the master. Each device on the I2C bus has a specific device address to differentiate between other devices that are on the same I2C bus. The I2C interface consists of a Serial Clock Line(SCL) and Serial Data Address(SDA). Data transfer may be initiated only when the bus is idle. A bus is considered idle if both SDA and SCL lines are high after a STOP condition. I2C supports transfer speed of around 100kHz (original standard, or 400kHz using the most recent standard).

2.1 Asynchronous serial communication
In asynchronous Serial Interface, the external clock signal is absent. The Asynchronous Serial Interfaces can be seen in mostly in long distance applications and are a perfect fit for the stable communication. In asynchronous Serial Interface the absence of external Clock Source makes it rely on several parameters such as Data Flow Control, Error Control, Baud Rate Control, Transmission Control and Reception Control. On the transmitter side, there is a shifting of parallel data onto the serial line using its own clock. Also it adds the start, stop and parity check bits. On the receiver side, the receiver extracts the data using its own clock and convert the serial data back to the parallel form after stripping off the start, stop, and parity bits. The well-known examples are RS-232, RS-422 and RS-485.
2.1.1 RS232
What is rs232 protocol.
The RS232 (Recommended Standard 232) is very common protocol used to connect different peripherals such as Monitors, CNCs etc. The RS232 comes in male and female connectors. The RS232 is point-to-point topology with maximum one device connected and covers distance up to 15 meters at 9600 bps. Information on the RS-232 interface is transmitted digitally by logical 0 and 1. The logical "1" (MARK) corresponds to a voltage in the range from -3 to -15 V. The logical "0" (SPACE) corresponds to a voltage in the range from +3 to +15 V. It comes in DB9 connector which has 9 pinouts such as TxD, RxD, RTS, CTS, DTR, DSR, DCD, GND.
Types of Serial Cables
To make serial communication possible between DTE and DCE, two types of RS232 cables exist. They are Null modem and Straight-cable. In null modem cable, the TX (Transmitter) pin of the male connector is linked up with the RX (Receiver) pin of the female and the RX pin of the male is connected to TX pin of the female.

How RS232 Communication Works?
The working of RS-232 can be understood by the protocol format. As RS-232 is a point-to-point asynchronous communication protocol, it sends data in a single direction. Here, no clock is required for synchronizing the transmitter and receiver. The data format is initiated with a start bit followed by 7-bit binary data, parity bit and stop bit which are sent one after another.
What is Handshaking?
Handshaking is the process which is used to transfer the signal from DTE to DCE to make the connection before the actual transfer of data. The messaging between transmitter & receiver can be done by handshaking. The connectors DB9 and Db25 are used for handshaking purpose. When no handshaking is performed, only the TxD (Transmitter) and RxD are cross-coupled. Other pins, RTS, CTS, DSR, and DTR are connected in loopback fashion. To use the handshaking technique, RTS and CTS are cross-coupled. Also, DTR and DSR are also connected in cross mode.
Why to use Handshaking?
To send and receive the information without loss of data, it is necessary to maintain robust communication between the transmitter and receiver. To do that, buffer is used. Buffer is a temporary storage location which allows the transmitter and receiver to store the data until the information is processed by each other at different speeds.

As shown in above figure , If the transmitter sends data at a higher speed, the receiver may fail to receive. In this case, character ‘C’ is missed by the receiver. To avoid this, handshaking is used. Handshaking allows the transmitter and receiver device to agree before the communication is going to start.Refer from https://www.codrey.com/embedded-systems/rs232-serial-communication/
2.1.2 RS422
The RS422 is similar to RS232 which allows to simultaneously send and receive messages on separate lines but uses a differential signal for this. In the RS-422 network, there can only be one transmitting device and up to 10 receiving devices. The data transfer speed in RS-422 depends on the distance and can vary from 10 kbps (1200 meters) to 10 Mbps (10 meters). The RS-422 line is 4 wires for data transmission (2 twisted wires for transmission and 2 twisted wires for receiving) and one common GND ground wire. The voltage on the data lines can be in the range from -6 V to +6 V. The logical difference between A and B is greater than +0.2 V. Logical 1 corresponds to the difference between A and B less than -0.2 V. The RS-422 standard does not define a specific type of connector, usually it can be a terminal block or a DB9 connector.
2.1.3 RS485
Since RS485 uses multi-point topology, it is most used in the industries and are industry preferred protocol. RS422 can connect 32 line drivers and 32 receivers in a differential configurations but with the help of additional repeaters and signal amplifiers up to 256 devices. The RS-485 does not define a specific type of connector, but it is often a terminal block or a DB9 connector. The speed of operation also depends on the length of the line and can reach 10 Mbit / s at 10 meters. The voltage on the lines is in the range from -7 V to +12 V. There are two types of RS-485 such as half duplex mode RS-485 with 2 contacts and full duplex mode RS-485 with 4 contacts.
2.1.3 1-Wire
Dallas Semiconductor's 1-Wire bus is an asynchronous, master/slave bus with no protocol for multi-master. Like the I2 C bus, 1-Wire is half-duplex, using an open-drain topology on a single wire for bidirectional data transfer. However, the 1-Wire bus also allows the data wire to transfer power to the slave devices, although this is somewhat limited. Though limited to a maximum speed of 16Kbps, bus length can be upwards of 1,000 feet, given the proper pull-up resistor. For more detail on the 1-Wire bus, read H. Michael Willey's “One Cheap Network Topology” (January, 2001).https://www.embedded.com/serial-protocols-compared/
Designing Attiny 45 bridge & node boards for asynchronous serial communication
For the networking and communication week,I decided to learn asynchronous communication between One Bridge and two node.For that i made one Attiny 45 bridge and two Attiny 45 as node .Lets go to design it......
Schematic of Attiny 45 as Bridge
I referred the Neil document and redesign the attiny 45 board as a bridge.
EAGLE → Projects > eagle > Bridge attiny45

Schematic of Attiny 45 as Node
I referred the Neil document and redesign the attiny 45 board as a node.
EAGLE → Projects > eagle > Node attiny45

Board layout of Attiny 45 as bridge & nodes

PCB Milling of Attiny 45 bridge

PCB Milling of Attiny 45 node

Soldering and stuffing Attiny 45

Programming Attiny45 bridge boards
Programming steps for bridge board, do hardware arrangement:.
- Step 1:Connect the hello.bus.45.bridge to the computer using a FTDI cable
- Step 2:Connect the hello.ISP.44 to the computer using a miniUSB-A to USB-B cable
- Step 3:Connect the hello.bus.45.bridge and the hello.ISP.44 using the IDC cable
- Step 4:Check that everything is ok using the system profiler
Write Arduino code for bridge board
- Defined bridge board address 0
- Declare PB3 & PB4 as TX & RX
- LED pins to PB0 of Attiny 45 boards
- Upload the code into Attiny 45 bridge board
- In this way ATtiny 45 bridge board got programmed
- Also unfortunately we didint have FTDI cable so i used Arduino pins for serial communication.
Programming Steps for node board
- Step 1.Connect the hello.bus.45.bridge to the computer using a FTDI cable
- Step 2.Connect the hello.bus.45.bridge to the computer using a FTDI cable
- Step 3.Connect the hello.ISP.44 to the computer using a miniUSB-A to USB-B cable
- Step 4.Connect the hello.bus.45.node (1) and the hello.ISP.44 using the IDC cable
- Step 5.Check that everything is ok using the system profiler
Write Arduino code for node board
- Only make one change in above code i.e.defined bridge board address 1
- Upload node code
- In this way ATtiny 45 node board got programmed
Interface bridge & nodes

Test the communication between Attiny 45 bridge & nodes
After programming bridge and nodes boards seperately now the time to test them .So Connect the three hello.bus.45 boards using the data cable and then
- Hit 0 → bridge blinks
- Hit 1 → node 1 blinks
- Hit 2 → node 2 blinks
Group assignments
For this week group assignments i have decided to do communication with Atmega 328p with local webserver.Actually i want to learn this wireless communication for project work as well.So i choose this task for myself as part of group assignments.
In this tutorial I am going to show you how to set up the ESP-01 Wi-Fi module, how to configure it, and then verify it.In short i want establish communication between the module and another board.

The advantage of Asynchronous Communication is that you don't need the communication being done in sequence, mainly when you define the request code but not the receiving code.Refer from:(https://www.instructables.com/id/Asynchronous-Serial-Communication-With-AT-Commands/)
In the first option, you’re using the Module as an add-on and writing code in the Arduino to talk to it. The other model is that you’re trying to work on the module directly to program it or upgrade it. For our final project here we will have code on the Arduino talking to the module, but to make sure everything is working we’ll be talking to the Module directly (kind of). More on that later.
About ESP 01
he ESP8266 ESP-01 is a Wi-Fi module that allows microcontrollers access to a Wi-Fi network. This module is a self-contained SOC (System On a Chip) that doesn’t necessarily need a microcontroller to manipulate inputs and outputs as you would normally do with an Arduino, for example, because the ESP-01 acts as a small computer. Depending on the version of the ESP8266, it is possible to have up to 9 GPIOs (General Purpose Input Output). Thus, we can give a microcontroller internet access like the Wi-Fi shield does to the Arduino, or we can simply program the ESP8266 to not only have access to a Wi-Fi network, but to act as a microcontroller as well. This makes the ESP8266 very versatile, and it can save you some money and space in your projects. In this tutorial we are going to show you how to set up the ESP-01 Wi-Fi module, configure it, and verify that there is communication established between the module and another device & talked to web server as well.

Pin configuration:

Next, we have the Pinout connections. Depending on the article you’re looking at the connections will change. It’s important to understand the pins and how they’re used. In general, you have a VCC for power and your common GND. You also have TX and RX to transmit and Receive. You have two GPIO pins, a reset pin, and a CH_PD pin. This board is designed to be an add-on to another micro-controller and offers a feature for being able to turn it on or off by setting the CH_PD pin from High to Low. In my case, I’m going to leave it on all the time so I’m just pulling high all the time.
CH_PD is a chip controlled power down and needs to pull high in order to run Speaking of voltage, all the articles I’ve seen warnings not to give it too much power, but mine seemed to need more than the 3.5v Arduino served up. In my tests, the module wouldn’t start up correctly with 3.5v which made it very difficult to debug early on. I ended up switching to the 5v pin and everything has been great.
Hardware requirments
- Arduino UNO
- ESP-01 Module
- Male/female wires

Interface Arduino with ESP 01
Arduino -- ESP-01
Follow these steps.
- connect both ESP's VCC/3.3V/Power Pin and Enable Pin (red wires) to 10K resistor then to Uno's +3.3V power pin.
- connect ESP's Ground/GND Pin (Black Wire) to Uno's Ground/GND Pin.
- connect ESP's TX (green wire) to Uno's Pin 3
- cconnect ESP's RX (blue wire) to 1K resistor then to Uno's Pin 2.
- cconnect ESP's RX (blue wire) to 1K resistor then to Uno's GND Pin.
- Arduino -- Arduino
- Reset -- GND
Establish WI-Fi for Arduino through ESP -01

In the circuit there are 2 resistor one of 1k ohm and the other one of 2.2k ohm. The two resistors are used to step down the 5V which comes to arduino into about 3.43V which goes to the ESP-01 board (connected to RX pin of the ESP-01) because the ESP8266EX chip works with 3.3V only and applying a 5V directly may damage it. On the other hand, the TX pin of the ESP-01 is connected directly to the Arduino board without any voltage level converter because here the ESP-01 sends data (at 3.3V) to the Arduino board using this pin.
Note:There is other ways to build a programmer for the ESP-01 module for example by using FT232RL USB to serial converter from FTDI Chip
open the serial monitor and type the following command: You should get an “OK” response. This means that the module is working and that you are good to go. Now we are ready to test a two way communication between the module and another device.

- AT+CWMODE=1
In this tutorial, we are going to set the module to operate in STA mode by typing the following command:

Once we have the ESP-01 operating in STA mode, we need to connect to a Wi-Fi network. First we can check if we are already connected to one by sending the command:
his will display the station IP address of our ESP-01 module.

If you don’t get an IP address after entering the previous command, use the following command to connect to your network:
- AT+CWJAP= “Wi-FiNetwork”,“Password”

Then we need to enable multiple connections before we can configure the ESP8266 ESP-01 module as a server. Type the next command:
- AT+CIPMUX=1
Once again, each number is associated with a type of connection: Single = 0 Multiple = 1

The following step is to start the server at port 80:
- AT+CIPSERVER=1,80

We can now use the following commands to send some data and display it in our web browser’s window:
- AT+CIPSEND=0,15

- Type "IP address of your ESP module"
Once we hit enter, our message is displayed on the web browser’s window as shown in the image above.

- AT+CIPCLOSE=0
For more details click here for group assignments Group assignment
Learning outcomes:.
- Understand Serial vs Parallel communication.
- Understand how to coomunicate between bridge and multiple nodes via asynchronous communication protocol.
- Understand how to set up wi-fi environment for any board.
- Undestand how to communicate board & webserver as well.
- MASTER_schematic
- node_schematic
- MASTER_board
- master_code
Channelization Protocols Explained
Last updated: March 18, 2024
- Network Protocols
Baeldung Pro comes with both absolutely No-Ads as well as finally with Dark Mode , for a clean learning experience:
>> Explore a clean Baeldung
Once the early-adopter seats are all used, the price will go up and stay at $33/year.
1. Introduction
In this tutorial, we’ll explain the channelization protocols used in the media access control (MAC) sub-layer of the datalink layer in the OSI model to coordinate data transmission by multiple users through a channel.
2. Channelization and Channelization Protocols
We must constantly develop and enhance methods by which more users can connect and transmit information via a link, also known as a channel, without colliding or interfering.
According to the OSI model, the data link layer (DLL) transmits data through a network channel from one node to another. We subdivided the DLL into the logical link control (LLC) layer and the media access control (MAC) layer, each with its own set of protocols.
We employ the LLC sub-layer when using a dedicated link to send data from one node to another. In contrast, multiple users would attempt to use the available channel to send data concurrently if dedicated channels were unavailable. This could result in a collision. To coordinate this kind of data transmission, we employ the MAC sub-layer.
Channelization is the process by which we coordinate the transmission of data in non-dedicated channels to prevent collision and crosstalk, and channelization protocols are the MAC protocols we employ to coordinate this transmission.
Channels are communication resources we assign to a user to establish communication with other users in the network. These resources include frequency, time, code, space, bandwidth , and so on. We name each channelization protocol based on the kind of channel resources we employ for channelization. These protocols are:
- Frequency division multiple access (FDMA)
- Time division multiple access (TDMA)
- Code division multiple access (CDMA)
- Space division multiple access (SDMA)
- Orthogonal Frequency division multiple access (OFDMA)
Now let’s explain each protocol one by one.
3. Frequency Division Multiple Access (FDMA) Protocol
We design the FDMA protocol by utilizing the channel resource of frequency. By dividing the channel’s bandwidth into non-overlapping frequency bands or slices, we allocate each user a distinct band for exclusive transmission and reception . This enables the concurrent operation of multiple users within a single communication channel. To mitigate interference and crosstalk during data transmission, we equip each user with a customized bandpass filter complemented by a small guard band.
The following figure depicts the FDMA protocol scenario:
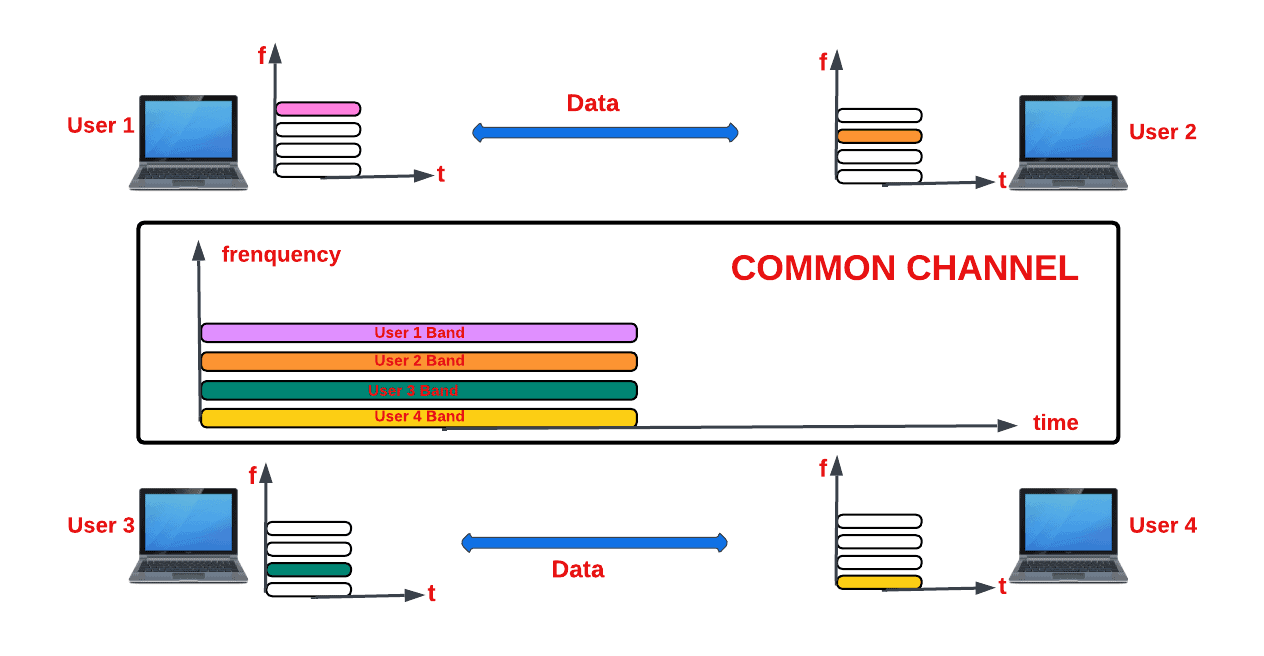
As seen in the above diagram, four users are attempting to access the same channel. To accommodate the four users without interfering with one another, we utilize FDMA to split the channel into four frequency bands.
3.1. Merits and Limitations of FDMA Protocols
Some notable merits which FDMA protocols offer us are:
- enable simultaneous transmission through the same frequency channel, with each user operating at a single frequency
- using frequency as the channel resource eliminates timing-related issues often encountered in TDMA protocols
- FDMA effectively resolves the near-far problem inherent in CDMA protocols by implementing bandpass filtering
- as we assign users frequency slots, this allows for distinct transmission and reception at different frequencies
However, the FDMA protocol does come with two significant limitations:
- the design of high-performing hardware filters proves to be a challenging task
- despite the inclusion of guard bands, FDMA remains susceptible to crosstalk, potentially leading to interference and transmission disruptions
3.2. Frequency Allocation Schemes in FDMA Protocols
Regarding frequency slot assignment within the FDMA protocol, we employ two common methods, which are:
- Fixed assignment multiple access (FAMA)
- Demand assignment multiple access (DAMA)
We use FAMA to allocate frequency slots to users whether they utilize it or not, ensuring a fixed allocation scheme. On the other hand, we use DAMA to assign frequency slots to users only upon their explicit request, offering a more dynamic and efficient resource allocation approach.
4. Time Division Multiple Access (TDMA) Protocol
Time serves as the channel resource for this protocol. Using the TDMA protocol, we divide each user’s signal into a different time slot and assign each time slot to a different user . This technique enables numerous users to share and use the same frequency channel. The global system of mobile communication (GSM) system, a 2G cellular system, is one significant application where we have used the TDMA protocol.
A typical TDMA protocol looks like this:
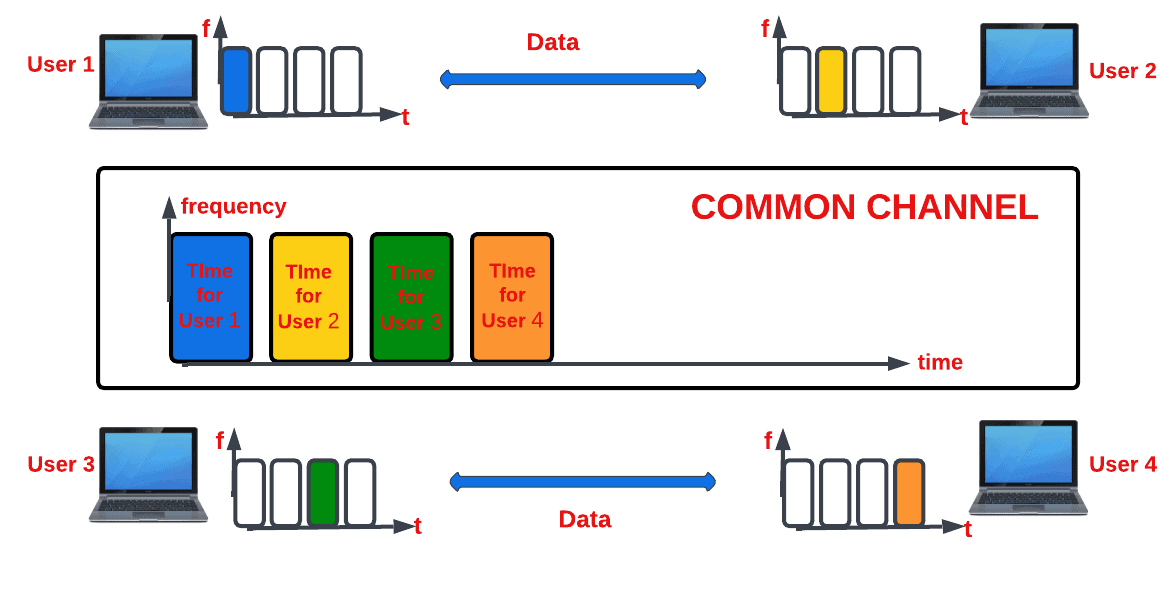
Synchronizing the various users of the channel is one of the biggest challenges we face when utilizing the TDMA protocol. To achieve synchronization, we ensure each user knows their respective slots’ start and endpoints. This is difficult to achieve, especially if the users are spread over a large area. To minimize this challenge, we insert guard times to each user channel.
Another significant drawback we encounter when utilizing TDMA systems is the potential for causing interference at a frequency that closely adjoins another user’s active time slot. This interference manifests as the buzzing sound we occasionally hear when a TDMA phone is near a radio or speakers.
Just like in the FDMA protocol, there are two methods we use to administer time slots to users:
- Fixed time division multiple access (F-TDMA)
- Dynamic time division multiple access (D-TDMA)
While we use F-TDMA for fixed allocation of time slots to users, we use D-TDMA to assign time slots to users based on the traffic demand of the channel.
5. Code Division Multiple Access (CDMA) Protocol
The channel resource for this protocol is code. I n the CDMA protocol, we allow multiple users to simultaneously transmit their data signals over the entire bandwidth of the common channel by assigning unique spreading codes to each user . This technique helps us utilize the channel more effectively.
Let’s see what a CDMA protocol looks like:
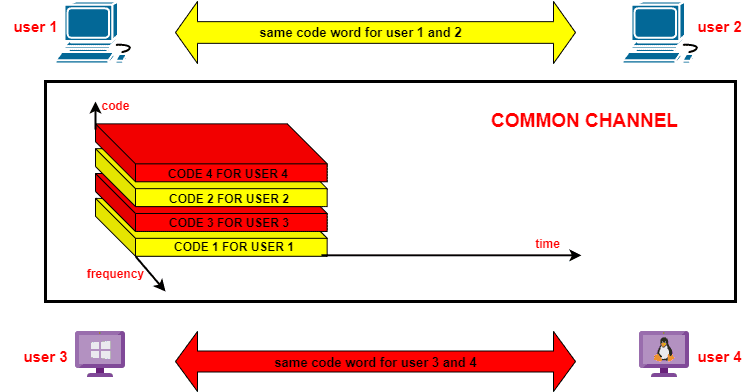
The beauty of this protocol is that we don’t share the frequency as we do in FDMA, and neither do we share time as we do in TDMA. In CDMA, we employ both time and frequency for users to send their data over the entire bandwidth of the channel with a unique spreading code allotted to the user. Only receivers having this unique code can receive the sent messages.
In CDMA, we use the spread spectrum principle to utilize unique transmission codes . Let us discuss this principle more in-depth.
5.1. Spread Spectrum
Spread spectrum is a technique that enables us to transfer signals via communication channels by purposefully extending the signal’s bandwidth beyond what is necessary for transmission . We expand the signal bandwidth in order to keep transmission interference to a bare minimum. To offset the waste of bandwidth due to overspreading, we allow multiple users to access the channel.
We implement the spread spectrum in two ways:
- Direct sequence spread spectrum (DSSS)
- Frequency hopping spread spectrum (FHSS)
Let’s now discuss each method.
In DSSS, we multiply the message signal with a locally generated spreading pseudorandom noise (PN) code, which we refer to as chips, to widen the signal’s bandwidth . By multiplying the signal, we broadcast at the receiver by a locally produced copy of the PN code sequence, and we can decode the information. We have incorporated DSSS into GPS and Wi-Fi networks.
To spread the message signal in FHSS, we transmit it with rapidly changing carrier frequencies among several frequencies occupying a large bandwidth . We control the “frequency hopping” of the message signal by a PN code known to the sender and receiver. In this way, we send and receive data without interference and eavesdropping.
We employ two strategies to manage CDMA protocols based on spread spectrum technologies:
- Direct sequence code division multiple access (DS-CDMA)
- Frequency hopping code division multiple access (FH-CDMA)
Based on the same logic as their spread spectrum counterparts, we apply these techniques.
5.2. Advantages and Disadvantages of CDMA
CDMA offers several advantages over other communication technologies, such as FDMA and TDMA. Firstly, CDMA significantly increases user capacity compared to FDMA and TDMA. Moreover, it allows for simultaneous voice and data communication, which is impossible with TDMA and FDMA.
Another significant advantage of CDMA is its high level of security in transmitting information. In CDMA, we employ a unique code for each user, making accessing information difficult for unauthorized users. Additionally, the probability of interference is minimal in CDMA, providing reliable communication.
Furthermore, CDMA enables us to use the entire spectrum, offering more flexibility in communication. With CDMA, we can take advantage of the entire bandwidth available, which is impossible with FDMA or TDMA.
Despite its advantages, CDMA also has some significant drawbacks that must be considered. Firstly, the system’s operation is highly complex, making it difficult to set up and maintain.
Moreover, In CDMA, we use orthogonal codes for both the sender and the receiver in a synchronous manner to recover the original data accurately. If this requirement is unmet, the system experiences self-jamming, making communication challenging.
6. Space Division Multiple Access (SDMA)
In this protocol, we utilize space as the channel resource. We allocate the same frequency to users that are separated by a certain distance, which we refer to as the reuse distance . To accomplish this, we employ a smart and highly directional antenna that directs a beam of radio waves to a specific location in space where a user is located.
To enable the reuse of the same channel, we use another smart and highly directional antenna to beam his signal to a different location in the same space where other users are located. This smart antenna system is known as a Multiple Input Multiple Output (MIMO) system.
A typical SDMA protocol looks like this:
From the figure, we see that the same channel-1 is reused to send data to three different users because a reuse distance separates them.
By using a highly directional beam, we can minimize interference and improve the quality of communication for users in the network. Additionally, the MIMO system can increase the network’s capacity by allowing multiple users to communicate simultaneously without affecting each other’s signals.
This protocol provides us with some merits:
- it helps us to optimize the use of power and minimize the wastage of energy
- we are able to save the channel bandwidth and utilize it more effectively
- it helps us reduce interference to near zero
- we can control and regulate the energy we radiate to the receiver
To achieve the full potential of the SDMA protocol, we must carefully design it, which we always find very tedious.
7. Orthogonal Frequency Division Multiple Access (OFDMA)
As the world is witnessing an increasing demand for individual data consumption, we recognize the necessity to enhance the existing protocol standards to meet this demand. To address this, we devised a solution that merged the benefits of FDMA and TDMA protocols in an orthogonal fashion, thereby preventing interference.
This innovation led to the emergence of the OFDMA protocol. To accomplish this, we utilized the channel resource by combining frequency and time in an orthogonal manner. Now, let’s delve into the functionality of the OFDMA protocol:
The OFDMA protocol actively takes a channel and partitions it into smaller frequency units which we know as resource units (RUs). We then allocate these RUs to users according to their respective data consumption demands .
For instance, if a user intends to send an email, we assign a small RU due to the minimal data requirement. Conversely, a user aiming to video call their boss receives a larger RU allocation.
To ensure interference avoidance, we divide the RUs in an orthogonal manner. Subsequently, we employ a single access point (AP) to aggregate all assigned users to their respective RUs, facilitating the delivery of their messages to the intended recipients.
Thanks to the dynamic efficiency we embedded in the design of the OFDMA protocol, we can assign receivers RUs based on the data size they expect to receive.
This is a typical OFDMA protocol layout:
The OFDMA protocol significantly mitigates the unpredictability experienced by users in highly congested areas by enabling more users to connect concurrently to a single access point (AP). In doing so, OFDMA effectively addresses congestion issues.
Furthermore, this protocol exemplifies exceptional efficiency by seamlessly allocating either the entirety of a channel or dividing it to accommodate multiple users, depending on the specific traffic demands.
8. Conclusion
In this article, we discussed how channelization protocols play a critical role in optimizing the utilization of communication channels in various systems. We showed that each protocol possesses unique advantages and challenges tailored to specific requirements and environments.
- Français
- Español
Communications and Public Advocacy intern, United Nations Women’s Peace and Humanitarian Fund
Advertised on behalf of.
New York, UNITED STATES OF AMERICA
Type of Contract :
Starting date :.
15-Nov-2024
Application Deadline :
01-Oct-24 (Midnight New York, USA)
Post Level :
Duration of initial contract :, time left :, languages required :.
English
Expected Duration of Assignment :
UNDP is committed to achieving workforce diversity in terms of gender, nationality and culture. Individuals from minority groups, indigenous groups and persons with disabilities are equally encouraged to apply. All applications will be treated with the strictest confidence. UNDP does not tolerate sexual exploitation and abuse, any kind of harassment, including sexual harassment, and discrimination. All selected candidates will, therefore, undergo rigorous reference and background checks.
UN Women, grounded in the vision of equality enshrined in the Charter of the United Nations, works for the elimination of discrimination against women and girls; the empowerment of women; and the achievement of equality between women and men as partners and beneficiaries of development, human rights, humanitarian action and peace and security.
The United Nations Women’s Peace and Humanitarian Fund (WPHF) is a partnership between the United Nations, Member States, and the civil society, which supports women led and women’s rights organizations working to build peace and provide humanitarian response throughout the world. The WPHF Secretariat provides support to the Funding Board, mobilizes resources from Governments, companies, foundations and individuals, designs funding windows and mechanisms, provides day to day support to Country Offices implementing WPHF programmes, ensures timely and quality monitoring and reporting. The Secretariat’s mandate is also to strengthen stakeholders’ knowledge of and engagement with women, peace and security issues through proper internal and external communications, advocacy and outreach. Finally, the Secretariat provides knowledge management services for the WPHF, and manages the Community of Practice (CoP) for WPHF partners and grantees.
The Communications and Public Advocacy Intern will work closely with the WPHF communications and advocacy teams—under the supervision of the WPHF Communications and Advocacy Specialist—to support the execution of the Secretariat’s communications and social media strategies, including drafting messaging and creating content for WPHF’s global channels. The intern will also work with the Communications and Advocacy Analyst to boost WPHF’s visibility and global reach, identifying opportunities in relevant online conversations and supporting the development of the Fund’s media outreach strategy. Additionally, the intern will assist with organizing events, advocacy campaigns, and activations related to Women, Peace, Security, and Humanitarian Action (WPS-HA), preparing presentations, conducting research, and drafting reports.
Duties and Responsibilities
- Support the communications team with daily content creation across WPHF’s social media platforms (X, Facebook, LinkedIn, Instagram and TikTok), newsletters, and event coverage, in line with WPHF’s communications and outreach strategy;
- Assist in brainstorming and executing social media strategies to amplify relevant campaigns, international days (e.g., International Women’s Day, International Day of Peace), and key WPHF initiatives, ensuring maximum engagement and visibility;
- Contribute to the scheduling, systematization, organization, and translation of all WPHF social media and communications content;
- Explore live conversations, calls for action, and social media activations, as appropriate;
- Support the communications team in drafting, updating, and translating content for the WPHF global website;
- Assist the communications team in creating an internal database of media contacts and publications relevant to WPHF and its work, in line with the Secretariat’s new media outreach strategy;
- Support the organization of outreach and advocacy events, as well as other WPHF engagement and missions throughout the year, including preparations for the Women, Peace and Security Open Debate, COP29, CSW, ECOSOC, etc;
- Assist the advocacy team during meetings and engagements with partners and external stakeholders, including preparing presentations, mapping funding opportunities, and identifying potential partners;
- Carry out other tasks assigned to support the WPHF secretariat, as required.
Competencies
Core Values:
- Respect for Diversity
- Professionalism
Core Competencies:
- Awareness and Sensitivity Regarding Gender Issues
- Accountability
- Creative Problem Solving
- Effective Communication
- Inclusive Collaboration
- Stakeholder Engagement
- Leading by Example
Please visit this link for more information on UN Women’s Core Values and Competencies :
https://www.unwomen.org/-/media/headquarters/attachments/sections/about%20us/employment/un-women-values-and-competencies-framework-en.pdf?la=en&vs=637
Required Skills and Experience
- University studies in one of the following disciplines: International relations, gender studies, social and/or political science, international development, human rights, international law or other relevant subjects is required.
- Meet one of the following:
- Be enrolled in a graduate school programme (second university degree or equivalent, or higher);
- Be enrolled in the final academic year of a first university degree programme (minimum Bachelor's level or equivalent);
- Have graduated with a university degree and, if selected, must commence the internship within two-years period of graduation; or
- Be enrolled in a postgraduate professional traineeship program which is part of a degree programme and undertake the internship as part of the program requirements.
- Excellent communication skills (written and oral) in English are required;
- Working knowledge of another UN language, especially French and/or Arabic, is an advantage.
Renumeration:
Interns who are not in receipt of financial support from other sources such as universities or other institutions will receive a stipend from UN Women to partially subsidize their basic living costs for the duration of the internship.
Application Information:
- All applicants must submit a completed and signed P.11 form with their application.
- Due to the high volume of applications received, UN Women can ONLY contact successful candidates.
- The successful candidate will be required to provide proof of enrollment in a valid health insurance plan at the duty station of the internship, proof of school enrollment or degree, a scanned copy of their passport/national ID and a copy of a valid visa (as applicable).
In July 2010, the United Nations General Assembly created UN Women, the United Nations Entity for Gender Equality and the Empowerment of Women. The creation of UN Women came about as part of the UN reform agenda, bringing together resources and mandates for greater impact. It merges and builds on the important work of four previously distinct parts of the UN system (DAW, OSAGI, INSTRAW and UNIFEM), which focused exclusively on gender equality and women's empowerment.
At UN Women, we are committed to creating a diverse and inclusive environment of mutual respect. UN Women recruits, employs, trains, compensates, and promotes regardless of race, religion, color, sex, gender identity, sexual orientation, age, ability, national origin, or any other basis covered by appropriate law. All employment is decided on the basis of qualifications, competence, integrity and organizational need.
If you need any reasonable accommodation to support your participation in the recruitment and selection process, please include this information in your application.
UN Women has a zero-tolerance policy on conduct that is incompatible with the aims and objectives of the United Nations and UN Women, including sexual exploitation and abuse, sexual harassment, abuse of authority and discrimination. All selected candidates will be expected to adhere to UN Women’s policies and procedures and the standards of conduct expected of UN Women personnel and will therefore undergo rigorous reference and background checks. (Background checks will include the verification of academic credential(s) and employment history. Selected candidates may be required to provide additional information to conduct a background check.)

IMAGES
VIDEO
COMMENTS
5. File Transfer Protocol (FTP) FTP is a client-server protocol, with which a client requests a file and the server supplies it. FTP runs over TCP/IP-- a suite of communications protocols -- and requires a command channel and a data channel to communicate and exchange files, respectively. Clients request files through the command channel and ...
Learn the most common types of network protocols and how they work in a computer network. The web page covers TCP, UDP, IP, DNS, NAT, SNMP, SMB, FTP, TFTP, HTTP, HTTPS, SMTP and more.
Learn about protocols, the agreements between computers for how they will carry out tasks on a network. Explore the layered structure of Internet protocols, from physical to application, and how they enable communication and data transfer.
A communication protocol is a system of rules that allows two or more entities to transmit information via any variation of a physical quantity. Learn about the history, concept, and examples of communication protocols, such as TCP/IP, OSI, and X.25.
Learn about the rules and types of network protocols that devices use to communicate over a network. See examples of communication, security, and management protocols such as HTTP, HTTPS, FTP, TCP, UDP, SSL/TLS, SSH, DHCP, SNMP, ICMP, and BGP.
Learn about networks and communication systems, their types, criteria, uses, and issues. A network is a set of devices connected by communication links, such as computers, routers, switches, and modems.
Also known as the network layer, the internet layer receives and sends packets for the network. This layer comprises IP, Address Resolution Protocol (ARP) and Internet Control Message Protocol (ICMP). Network access layer. The network access layer of TCP/IP combines the physical and data-link layers of the OSI model.
Communication protocols are formal descriptions of digital message formats and rules for exchanging messages in or between computing systems. They are important for creating consistency and universality in telecommunications systems and other systems. Learn more about the properties, types, and purposes of communication protocols.
Learn about network protocols, a set of rules governing exchange of information in a network. Understand the OSI model and its seven layers, and the common protocols used by each layer, such as TCP/IP, FTP, PPP, etc.
Learn about telecommunications protocols, media, modulation techniques and applications in wireless and optical networks. This chapter covers analogue and digital communications, software-defined radio, Ethernet, SIP and BCI systems.
IP is a protocol for routing and addressing packets of data on the Internet. It can be used with TCP or UDP, and it has different versions (IPv4 and IPv6). Learn more about IP, IP addresses, IP packets, and TCP/IP and UDP/IP.
49202 Communication Protocols. Warning: The information on this page is indicative. The subject outline for a particular session, location and mode of offering is the authoritative source of all information about the subject for that offering. Required texts, recommended texts and references in particular are likely to change.
The following are some of the most prominent protocols used in network communication. Application layer network protocols 1. DHCP: Dynamic Host Configuration ...
Represents information flow. TCP/IP is used to represent how information changes form as it travels over a network from the concrete physical layer to the abstract application layer. It details the basic protocols, or methods of communication, at each layer as information passes through. End-to-end data transmission.
49202 Communication Protocols 6cp; 1.5hpw (tutorial/workshop/quiz, online), 2hpw (laboratory, online); availability: all courses There are course requisites for this subject. See access conditions. Anti-requisite(s): 41092 Network Fundamentals Postgraduate. Description. Students completing this subject have a good understanding of the theory of communication protocols and its application to ...
Learn what communication protocols are and why they are important for digital systems. Explore the different types of intersystem and intrasystem protocols, such as UART, USART, USB, I2C, SPI and CAN, and their features and applications.
The protocol type field lists the highest level protocol that sent or received this packet, i.e., the protocol that is the source or ultimate sink for this packet. · The packet-header details window provides details about the packet selected (highlighted) in the packet listing window.
Communication protocols are essential in system design for several key reasons: 1. Interoperability. Communication protocols define a common language and set of rules for different components to communicate effectively. This ensures that components from different vendors or platforms can work together seamlessly, enabling interoperability in ...
Examples of Parallel Communication Protocols are ISA, ATA, SCSI, PCI and IEEE-488. Similarly there are several examples of Serial Communication Protocols such as CAN, ETHERNET, I2C, SPI, RS232, USB, 1-Wire, and SATA etc. ... For this week group assignments i have decided to do communication with Atmega 328p with local webserver.Actually i want ...
Learn about the major industrial automation communication protocols, such as PROFINET, EtherNet/IP, EtherCAT, Modbus, and more. Compare their features, benefits, and applications for different industrial networks.
Learn about the different channelization protocols used in the MAC sub-layer of the OSI model to coordinate data transmission by multiple users through a channel. The web page covers FDMA, TDMA, CDMA, SDMA, and OFDMA protocols with examples and diagrams.
The Communications and Public Advocacy Intern will work closely with the WPHF communications and advocacy teams—under the supervision of the WPHF Communications and Advocacy Specialist—to support the execution of the Secretariat's communications and social media strategies, including drafting messaging and creating content for WPHF's ...