Stack Exchange Network
Stack Exchange network consists of 183 Q&A communities including Stack Overflow , the largest, most trusted online community for developers to learn, share their knowledge, and build their careers.
Q&A for work
Connect and share knowledge within a single location that is structured and easy to search.

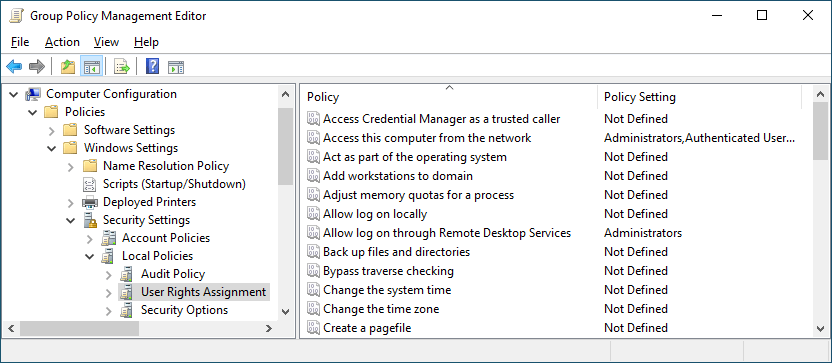
Can't edit Local Security Policy
I'm trying to add users to the Access this computer from the network User Rights Assignment policy but the 'Add' button is disabled:

I'm connecting to the machine via RDP using the local Administrator account (not a domain user). I've also tried to do the same with a domain user that is in the Administrators group but the result is the same.
How can I add a user to this policy?
The machine is running Windows 7.
- remote-desktop
- administrator
- group-policy
- You need to be using a domain user in the Administrator user group – Ramhound Aug 27, 2015 at 12:38
- I am using it (the built-in account..), but I login via RDP. does it matter? – etaiso Aug 27, 2015 at 12:38
- Your not using one, you indicated your using the local Administrator account, you need to be using a user connected to the domain with Administrator permissions. – Ramhound Aug 27, 2015 at 12:44
- I also tried that . it's the same – etaiso Aug 27, 2015 at 12:46
- Update your question; If I had know that; I could have saved time responding. – Ramhound Aug 27, 2015 at 12:51
You cannot edit this User Rights Assignment policy because this setting is being managed by a domain-based Group Policy. In this case, the domain Group Policy setting has precedence and you are prevented from modifying the policy via Local Group Policy.
To modify this policy, either:
- Modify the policy in the applicable domain Group Policy Object.
- Prevent any domain-based GPOs from specifying this setting, then edit the computer's Local Group Policy.
- where can I find this policy in the GPO? – marijnr Jun 13, 2018 at 13:15
- 2 Computer Configuration\Windows Settings\Security Settings\Local Policies\User Rights Assignment – I say Reinstate Monica Jun 13, 2018 at 13:16
You must log in to answer this question.
Not the answer you're looking for browse other questions tagged windows security remote-desktop administrator group-policy ..
- The Overflow Blog
- How to succeed as a data engineer without the burnout
- How do you evaluate an LLM? Try an LLM.
- Featured on Meta
- New Focus Styles & Updated Styling for Button Groups
- Upcoming initiatives on Stack Overflow and across the Stack Exchange network
- Google Cloud will be Sponsoring Super User SE
Hot Network Questions
- Coauthorship of a paper with big name prof
- Could SpaceX ever make a Heavy version of Starship Super Heavy
- Kernel of restriction and cokernel of corestriction of group cohomology
- Implicit licensing when contributing to an open source project
- How to combine multiple pure conditions with an AND operator?
- Does Hippolyta love Theseus in Shakespeare's "A Midsummer Night's Dream?"
- Why do protests happen in the light of their apparent futility?
- Euclidean algorithm for simple closed curves
- How to evenly mix stir fried vegetables with noodles?
- Should I write "a Master of Science degree" or "a master's degree in science" in this case?
- Can I add a breaker to this panel without violating the Rule of Six?
- Can I find words with similar spelling using regular expressions or wildcards?
- When do you need Ethics Approval in Humanities research?
- How does HTTP Keepalive handle multiple requests along with EOF from same origin?
- What are the specific financial implications of not being a US citizen after a spouse dies?
- Why don't airports use different radio frequencies/channels for each plane to prevent communications from interfering with each other?
- Short story; a journalist visits a hospital with inpatients who are mentally ill. One patient pretends to use invisible tools to build a machine
- Why doesn't Israel withdraw from the territories occupied during the Six-Day War of 1967?
- Run function at end of pipe
- Situation with Artemov's paper?
- 2020 VW Jetta SEL air distribution map
- A question on Euler's totient function
- How do Christians address the "Bigfoot" analogy presented by skeptics in relation to the resurrection of Jesus?
- How to represent BFS and DFS between adjacency matrix and list?
AD Security 101: Lock Down Risky User Rights
- Active Directory Security
- Jun 16, 2023
In Active Directory (AD) environments, you can use Group Policy Objects (GPOs) to configure user rights. By using GPOs, you can easily enforce consistent user rights policies across all computers in the domain or organizational unit (OU). This capability makes it easier to manage and maintain user access control over time. But when granted to users who should not have them or when configured incorrectly, certain user rights can pose an AD security risk. Here’s what you need to know to protect AD—and your environment—from risky user rights.
What are user rights?
User rights are permissions that control user actions on a computer system. These rights differ from standard file and folder permissions and apply to specific user actions. User rights include (but are not limited to):
- Allow log on locally : Allows users to log on to a computer locally
- Change the system time : Allows users to change the system time on a computer
- Shut down the system : Allows users to shut down the computer
- Debug programs : Allows users to debug programs running on the computer
- Manage auditing and security log : Allows users to view and manage security logs on a computer
- Take ownership of files or other objects : Allows users to take ownership of files or other objects on a computer
- Load and unload device drivers : Allows users to load or unload device drivers on a computer
- Back up files and directories : Allows users to back up files and directories on a computer
- Restore files and directories : Allows users to restore backed-up files and directories on a computer
- Allow log on through Remote Desktop Services : Allows users to manage remote access to a computer
Using GPOs to configure user rights
To configure user rights using a GPO, first create or edit a GPO that applies to the users or computers that you want to configure. You need to link the GPO to the relevant domain or OU level. Then, you can use the Group Policy Editor application to specify the user rights that you want to assign. (A similar process applies to configuring GPO logon scripts, as discussed in a previous AD Security 101 post .)
To configure user rights:
- Open Group Policy Editor.
- Go to the Computer Configuration section.
- Select Windows Settings .
- Select Security Settings .
- Go to the Local Policies section.
- Select User Rights Assignment .
- Select the user right that you want to configure.
- Add the users or groups that should be granted that right.
For example, to grant a user the right to log on locally to a specific computer, select the Allow log on locally user right and then add the user to the list of allowed users.
Risky user rights and AD security
How can user rights pose a security risk? Consider the following example.
Suppose the Debug programs user right is granted to a user who does not need it. That user—or an attacker who manages to gain access to that user’s credentials—can use this right to:
- Debug a system process that runs as an elevated user
- Inject malicious code
- Gain system-level access
- Access sensitive data or processes that they would not normally have access to
- Disable security features or anti-malware tools on the system
Similarly, if the Change system time user right is granted to a user who should not have the right, that user (or an attacker) can modify the system time and cause issues with time-sensitive applications or services.
Additional potentially risky user rights include:
- Log on as a service
- Allow log on locally
- Act as part of the operating system
To determine which user rights are assigned to a user in AD, you can open the right for editing in the Group Policy Management Console (GPMC). Another option is to use GPO command-based tools (CLI or PowerShell) to check GPOs and their respective settings, including user rights assignments.
However, large organizations with thousands or more user objects and OUs can have tens or hundreds of GPOs, each containing multiple accumulated (and often overlapping) settings. For example, a domain-level GPO might assign specific user rights to one set of users or groups, while another OU-level GPO might add other user rights to some of those same users or groups.
As your AD environment evolves and changes over time, the complexity of the GPOs assigned to domain, sites, or OUs typically also increases. All these assignments gradually become more difficult to manage, making it challenging to determine which setting applies to which user.
Protecting AD from risky user rights
To mitigate the risks associated with a user right:
- Verify that the right is granted only to users who require it for specific tasks.
- Carefully monitor all users who are assigned the right.
- Protect sensitive processes so that they cannot be debugged by unauthorized users.
To ease the task of continuously assessing your AD security posture—including potentially risky user rights—you can use tools such as Purple Knight or Semperis Directory Services Protector (DSP) . When executed in your environment, these tools enumerate and parse all GPOs, determine whether any non-well-known SID has been assigned a “strong” non-default user right, and generate a clear report of these details. You can examine these findings to determine which unnecessary user rights to remove from the GPOs in your environment.
Using Purple Knight to secure risky user rights
Figure 1 shows a Purple Knight report indicating the assignment of a dangerous GPO-granted user right.
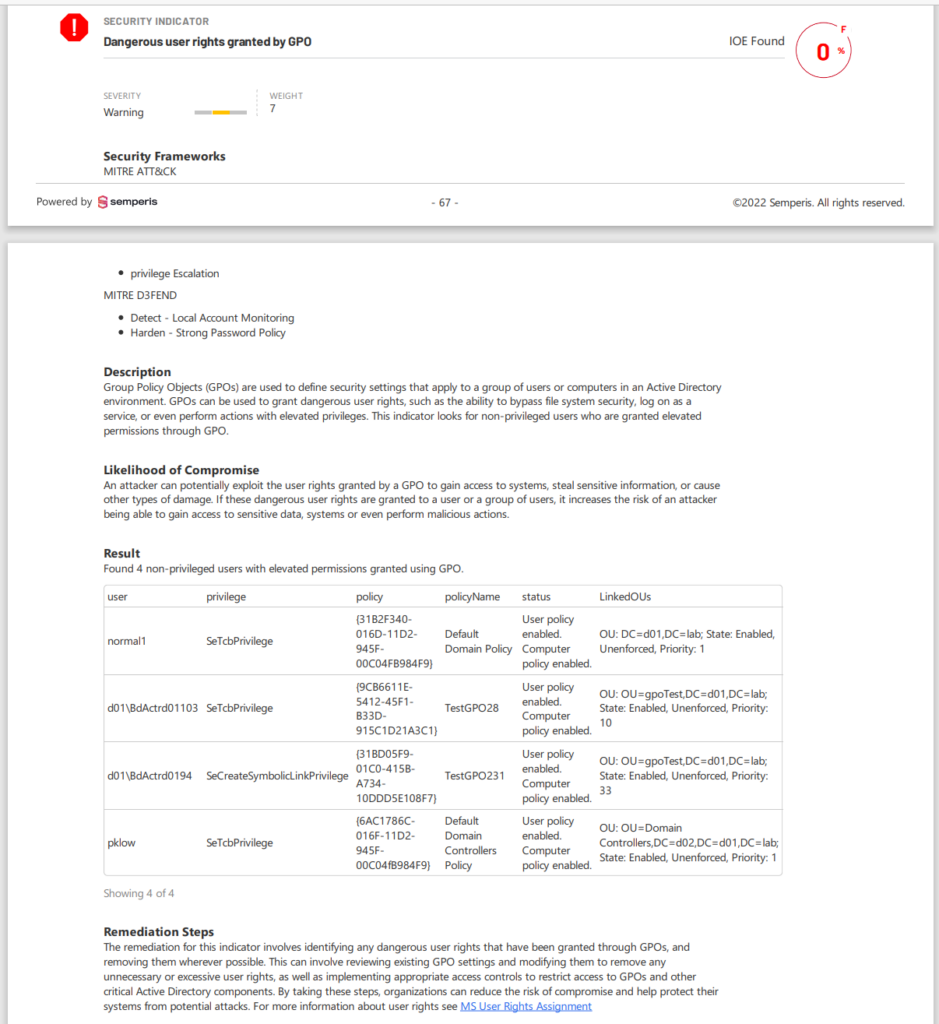
The report shows the severity of risk, describes the likelihood of compromise, lists the users who are assigned the right, and suggests remediation measures.
Using DSP to secure risky user rights
Figure 2 shows a DSP report indicating the assignment of a dangerous user right.
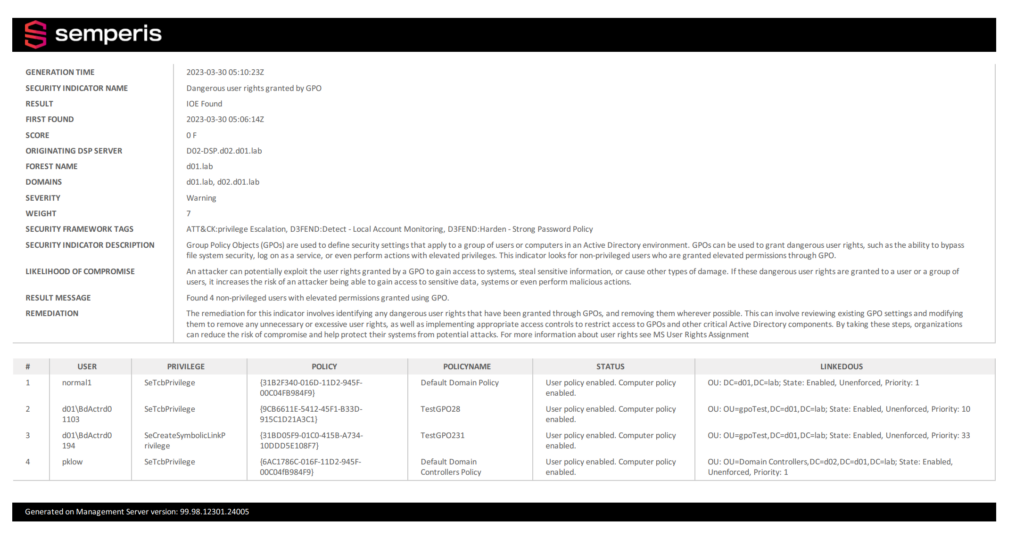
This report includes the same details as the Purple Knight report. With DSP, you also gain remediation capabilities, including custom alerts and automatic rollback of malicious changes, to help you mitigate the risk.
Keep tabs on risky user rights
After mitigating any risky user rights assignments, you should re-scan the AD environment to determine whether additional changes are required. You should continue to perform periodic scans of your AD to verify that no unauthorized changes are made to these settings.
Learn more about AD security
- AD Security 101: GPO Logon Script Security
- Do You Know Your Active Directory Security Vulnerabilities?
- AD Change Auditing and Rollback

Sign Up for the Latest Semperis News

Contribute to the Windows forum! Click here to learn more 💡
April 9, 2024
Contribute to the Windows forum!
Click here to learn more 💡
Windows 10 Top Forum Contributors: neilpzz - Ramesh Srinivasan - _AW_ - questions_ - Volume Z 👍✅
April 17, 2024
Windows 10 Top Forum Contributors:
neilpzz - Ramesh Srinivasan - _AW_ - questions_ - Volume Z 👍✅
- Search the community and support articles
- Search Community member
Ask a new question
Locked local policy -- need to unlock
I went to make changes in the local computer policy, specifically >windows settings> security settings>local policies>user rights assignment. It appears that security settings>local policies>user rights assignment are locked as are the local policies (little padlock on the file) I am the administrator of the computer -- the only user -- how do I unlock these folders so I can make changes. This is a personal computer. Any help would be appreciated.
Report abuse
Replies (13) .
* Please try a lower page number.
* Please enter only numbers.
- Independent Advisor
Was this reply helpful? Yes No
Sorry this didn't help.
Great! Thanks for your feedback.
How satisfied are you with this reply?
Thanks for your feedback, it helps us improve the site.
Thanks for your feedback.
Hi, Geoffrey. I'll be happy to assist you today. Sorry to know you're experiencing this policy issue. What we need to do first is perform the following procedure in order to reset security policies: Please open CMD as administrator then paste the following commands then reboot the computer: SECEDIT /configure /cfg %windir%\inf\defltbase.inf /db defltbase.sdb /verbose RD /S /Q "%WinDir%\System32\GroupPolicyUsers" RD /S /Q "%WinDir%\System32\GroupPolicy" RD /S /Q %localappdata%\GroupPolicy\DataStore Please let me know if you need any further assistance.
thanks -- the first three commands worked -- the fourth and final one gave me a not found error. Rebooted anyway and still locked.
the exact error is " The system cannot find the path specified."
1 person found this reply helpful
Thanks for your feedback, Geoffrey. Please open a normal CMD session, then type the following command to generate a policy result file containing policies currently applied to your user and computer: gpresult /h desktop\result.html Next upload the file to OneDrive or another file share service and share the file publicly. Paste the link here, please.
Getting invalid pointer error with a blank html file generated.
Have the same issue -- blank file created in the target folder
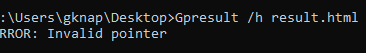
The change does not hold. Once I close the policy app the change disappears and reboot, tried it a couple of different ways. But same result.
Question Info
- Norsk Bokmål
- Ελληνικά
- Русский
- עברית
- العربية
- ไทย
- 한국어
- 中文(简体)
- 中文(繁體)
- 日本語

Windows security encyclopedia
#microsoft #windows #security
Search form
User rights assignment, related content.
- All about AI
- Google Bard
- Inflection AI Pi Chatbot
- Anthropic Claude
- Generative AI
- AI Image Generation
- AI Regulation
- AI Research
- Large Language Models (LLM)
- Surface Pro
- Surface Laptop
- Surface Book
- Surface Duo
- Surface Neo
- Surface Studio
- Surface Hub
- Surface Pen
- Surface Headphones
- Surface Earbuds
- About WinBuzzer
- Follow Us: PUSH, Feeds, Social
- Write for Us
- Cookie Policy and Privacy Policy
- Terms of Service
How to Reset All Local Group Policy Settings in Windows 11 or Windows 10
We show you how to reset Local Group Policy Settings in Windows 10, via both the Local Group Policy Editor and the command line. This is also an easy way to fix group policy by removing any previously made changes.

Table of Contents:
Microsoft provides all kinds of customization options via Windows Settings, but more advanced changes to your system can be made in the Local Group Policy Editor, also known as gpedit. The only problem is that gpedit isn’t the most intuitive app in the world. Mistakes are made and sometimes you need to reset a group policy in Windows 11 or Windows 10. Generally, there are two methods to reset Windows group policies. One involves manually changing each via the usual editor, and the other lets you reset every group policy in one go via the command line. It’s usually best to start with the first – disabling the most recent or potentially problematic policies. If that has no effect, you can clear them all with a command or switch each off in the policy editor. We’re going to show you how to do both in this tutorial.
⚠️ Please note: The process described below is the same in Windows 11 as it is in Windows 10. However, bear in mind that we’ll be using screenshots from Windows 10, so your UI may look a little different. We’ll point out any changes you need to be aware of as they come up.
How to Reset Group Policy Settings Using the Local Group Policy Editor

How to Reset All Group Policy Settings via Command Line (CMD)

FAQ – Frequently Asked Questions About Group Policy (Gpedit)
What should i do if resetting group policy settings does not resolve my issue.
If resetting the group policy settings doesn’t solve your problem, it’s possible the issue is not related to group policies. Consider other troubleshooting steps such as checking for conflicting software, scanning your system for malware, ensuring your system has the latest Windows updates installed, and performing a system restore to revert your system to a previous, stable state. These steps can help isolate the problem further and possibly uncover a resolution.
Can resetting group policy settings impact system performance?
Resetting group policy settings to their default states generally improves system performance, especially if the reset resolves misconfigurations or conflicting policies that may have been causing issues. However, resetting does not inherently speed up your computer; performance improvements would specifically result from eliminating problematic configurations. After a reset, monitoring system performance can help assess the impact and guide any further optimization steps.
How long does it take for group policy changes to take effect?
Group policy changes made through the Local Group Policy Editor typically take effect immediately after applying the changes or issuing the gpupdate /force command. Nonetheless, policies that influence user sign-in processes or require system services to restart, such as those related to startup scripts or security settings, may necessitate a system reboot to effect changes. If changes don’t seem to apply, verify by rebooting your computer and rechecking the policy settings.
How can I back up my group policy settings before resetting them?
To back up your group policy settings, especially if you’ve tailored many configurations, you can use PowerShell scripts or the Group Policy Management Console (GPMC) where available. For individual settings, note them down or take screenshots. For broader backups, GPMC allows for backing up entire Group Policy Objects (GPOs), which is useful for administrators managing multiple policies. These backups can be restored if needed, ensuring a safety net before making significant alterations or resets.
Are there any risks involved in using the command line method to reset group policies?
Using the command line to reset group policies carries minimal risk when commands are entered correctly and with understanding their function. Nevertheless, incorrect commands or typos can lead to unintended changes or deletion of critical system directories. It’s essential to double-check commands before executing them and to use administrative credentials judiciously. For those unsure, practicing on a non-critical system or virtual machine can help build confidence.
Can resetting group policy settings correct problems with Windows Updates?
Yes, resetting group policy settings can often resolve issues related to Windows Updates, particularly if prior configurations inadvertently interfered with the update process. After resetting, recheck for updates through the Windows Update settings page. If issues persist, consider troubleshooting with the Windows Update Troubleshooter and ensuring that your device’s date and time are correctly set, as these can also affect update availability and installation.
What happens to custom policy settings when I reset group policies?
When you reset group policies, all custom settings are removed, and policies revert to their default state, typically “ Not Configured “. This action means that any specific restrictions, configurations, or customizations previously in place will be lost. To restore your desired settings, you will need to manually configure each policy again, using references or notes you have kept. It’s advisable to document custom settings before resetting to facilitate easier reconfiguration.
Can I reset group policy settings for a specific user profile only?
Yes, it’s possible to reset group policy settings specifically for a single user profile by focusing on the “ User Configuration ” policies within the Local Group Policy Editor. This section allows you to adjust policies applied at the user level. Remember that changes made here won’t affect “ Computer Configuration ” policies, which apply system-wide. For targeted resets, navigate to the specific “ User Configuration ” policy, revert it to “ Not Configured “, and apply the change.
Can resetting group policy settings affect installed software or applications?
While resetting group policy settings mainly affects how Windows operates and user configurations, it can indirectly influence software or applications, especially those reliant on specific policies for functionality or access permissions. For instance, resetting policies related to software restriction or execution might allow previously blocked applications to run or vice versa. It’s crucial to review and potentially reconfigure policies that directly manage software behavior post-reset.
Will resetting group policy settings remove installed Windows features or programs?
Resetting group policy settings to their default configurations does not uninstall or directly modify installed software, Windows features, or programs. Instead, it affects the policies regulating system and user behavior, including access controls, user interfaces, and operational settings. To manage program features or Windows components, you would need to use the appropriate Windows settings or control panels directly.
How can I disable or enable specific Windows features using group policy settings?
To disable or enable specific Windows features through group policy settings, navigate to the “ Computer Configuration > Administrative Templates > Windows Components ” section within the Local Group Policy Editor. This area contains policies for managing various components and features of the Windows operating system. By enabling or disabling these policies, you can control the availability and behavior of features such as Windows Defender, Windows Update, and much more. Always review the policy description to understand its impact before applying changes.
Is it possible to restrict access to Control Panel and PC settings using group policy?
Yes, you can restrict access to the Control Panel and PC settings by navigating to “ User Configuration > Administrative Templates > Control Panel ” in the Local Group Policy Editor. Here, enabling the “ Prohibit access to Control Panel and PC settings ” policy prevents users from accessing these settings. This can be useful in managed environments where limiting user configurations is necessary to maintain system integrity or compliance with organizational policies.
How do I manage user rights and permissions through group policy settings?
To manage user rights and permissions, access the “ Computer Configuration > Windows Settings > Security Settings > Local Policies > User Rights Assignment ” section in the Local Group Policy Editor. This area allows administrators to define which users or groups have permissions to perform specific tasks on the system, such as logging on as a service, backing up files and directories, or shutting down the system. Each policy lists the rights it governs, enabling granular control over user activities and system access.
Can group policy settings manage network and internet settings?
Group policy settings provide a robust framework for managing network configurations and internet settings. By navigating to “ Computer Configuration > Administrative Templates > Network ” within the Local Group Policy Editor, you can access policies that control network connections, bandwidth management, Wi-Fi settings, and more. These policies enable administrators to enforce consistent network behavior across all system users, enhancing security and optimizing network resource usage.
How can I ensure my group policy settings are consistently enforced on all user accounts?
To enforce group policy settings consistently across all user accounts, configure the desired policies under the “ Computer Configuration ” section for system-wide application and use the “ User Configuration ” section for policies that should apply to individual user accounts. Utilizing the “ gpupdate /force ” command helps apply and refresh policy settings immediately. In environments with multiple users or computers, consider using Active Directory Group Policy Objects (GPOs) for centralized management and consistent enforcement of policies across the network.

Related: How to Download and Use the Group Policy Editor (gpedit.msc) in Windows 11 Home or Windows 10 Home

Related: How to Use System Restore in Windows 11
Related: How to Reset Windows 11 or Windows 10 (Normal or Factory Reset)

- fix group policy
- Local Group Policy Editor
- Reset Group Policy
- reset group policy command line
- reset group policy windows 10
- Reset Local Group Policy Settings
Recent News
Microsoft Tests Integrating Ads into Windows 11 Start Menu

Microsoft Dynamics 365 to Undergo Price Revision in October 2024
Subscribe to WinBuzzer on Google News

Stack Exchange Network
Stack Exchange network consists of 183 Q&A communities including Stack Overflow , the largest, most trusted online community for developers to learn, share their knowledge, and build their careers.
Q&A for work
Connect and share knowledge within a single location that is structured and easy to search.
How can I locate Registry key for Group policy settings?
How can I locate the registry entry for the below values
- Perform volume maintenance tasks
- Lock pages in memory
under Local Computer Policy\Computer Configuration\Windows Settings\Security Settings\User Rights Management .
I tried the below 3 ways.
- Find the Registry key for corresponding Group Policy : (1)Final Link broken (2)Couldn't locate above in reference guide or MSDN doc.
- Which Registry Settings a Group Policy Object Modifies : No policy-related registry key located in Procmon
- How Settings are Stored : Nothing insightful in the .ini file.
End goal is to automate configuration thru Powershell [ Set-ItemProperty ]
- group-policy
- windows-server-2016
3 Answers 3
As you can see in the Group Policy Settings Reference Guide (see your 1st link; in particular, Windows10andWindowsServer2016PolicySettings.xlsx document ), most of security settings (e.g. User Rights , Password Policy , Audit Policy etc.) are not registry keys . Those are stored in the Secedit.sdb database.
For your task, you can use Microsoft's secedit command line tool (at least, export and import):
secedit Configures and analyzes system security by comparing your current configuration to specified security templates. Syntax secedit [/analyze /db <database file name> /cfg <configuration file name> [/overwrite] /log <log file name> [/quiet]] [/configure /db <database file name> [/cfg <configuration filename>] [/overwrite] [/areas [securitypolicy | group_mgmt | user_rights | regkeys | filestore | services]] [/log <log file name>] [/quiet]] [/export /db <database file name> [/mergedpolicy] /cfg <configuration file name> [/areas [securitypolicy | group_mgmt | user_rights | regkeys | filestore | services]] [/log <log file name>]] [/generaterollback /db <database file name> /cfg <configuration file name> /rbk <rollback file name> [/log <log file name>] [/quiet]] [/import /db <database file name> /cfg <configuration file name> [/overwrite] [/areas [securitypolicy | group_mgmt | user_rights | regkeys | filestore | services]] [/log <log file name>] [/quiet]] [/validate <configuration file name>] Parameters Secedit: analyze Allows you to analyze current systems settings against baseline settings that are stored in a database. The analysis results are stored in a separate area of the database and can be viewed in the Security Configuration and Analysis snap-in. Secedit: configure Allows you to configure a system with security settings stored in a database. Secedit: export Allows you to export security settings stored in a database. Secedit: generaterollback Allows you to generate a rollback template with respect to a configuration template. Secedit: import Allows you to import a security template into a database so that the settings specified in the template can be applied to a system or analyzed against a system. Secedit: validate Allows you to validate the syntax of a security template.
Answer : Look for the below keys/entries under [Privilege Rights] section in the exported configuration file (you can add/change them easy using Powershell):
- SeLockMemoryPrivilege Lock pages in memory
- SeManageVolumePrivilege Perform volume maintenance tasks
Read (and follow) Windows Security Baselines as well:
A security baseline is a group of Microsoft-recommended configuration settings that explains their security impact. These settings are based on feedback from Microsoft security engineering teams, product groups, partners, and customers.
- Is there a way to read and write to Secedit.sdb using the Get-PolicyFileEntry cmdlet in the PolicyFileEditor module? – Ayan Mullick May 8, 2018 at 14:34
- 1 PolicyFileEditor module = commands and DSC resource for modifying Administrative Templates settings in local GPO registry.pol files. Nothing about Secedit.sdb afaik. – JosefZ May 8, 2018 at 19:37
You can use GPSearch resource to get corresponding keys: https://gpsearch.azurewebsites.net/
Also, you can try to apply the policy and track the changes in the registry with Process Monitor: https://docs.microsoft.com/en-us/sysinternals/downloads/procmon
- The above policies don't show up on the GPSearch site probably since they aren't stored in the registry... – Ayan Mullick May 18, 2018 at 18:36
While this answer isn't applicable for the policies specified in the question, I just wanted to throw https://admx.help in the ring for finding any registry keys relating to administrative templates policies. I prefer it over GPSearch mentioned by batistuta09 as it is much easier to read the information relating to the key/s, in my opinion.
To locate a desired key, scroll to and click on your OS of choice, then the policy categories trees for administrative templates we're all familiar with will appear on the right-hand side to be explored.
For example, I wanted to locate any keys associated with enabling the policy "Specify settings for optional component installation and component repair" locally on my Windows 10 machine (Local Computer Policy > Computer Configuration > Administrative Templates > System). On the website home page, you navigate as follows:
Windows 10 and Windows Server 2016 > Administrative Templates (Computers) > System > Specify settings for optional component installation and component repair
Once the policy is selected, any associated keys and their details are displayed clearly.
2022 edit: Updated url from getadmx.com to admx.help. Thanks, @Henke.
You must log in to answer this question.
Not the answer you're looking for browse other questions tagged powershell group-policy windows-server-2016 automation ..
- The Overflow Blog
- How to succeed as a data engineer without the burnout
- How do you evaluate an LLM? Try an LLM.
- Featured on Meta
- New Focus Styles & Updated Styling for Button Groups
- Upcoming initiatives on Stack Overflow and across the Stack Exchange network
Hot Network Questions
- Air mixture in space suits?
- How to measure q-factor?
- How to draw leftright arrow in a table
- Plotting a CSV file containing multiple co-ordinates of a route as points on QGIS
- macro to change line color in tikz
- How does HTTP Keepalive handle multiple requests along with EOF from same origin?
- In The Lord of the Rings, did anyone ever say "The fellowship is now complete."?
- What options do I have for latex-free interior house paint?
- Should I write "a Master of Science degree" or "a master's degree in science" in this case?
- Why do protests happen in the light of their apparent futility?
- Removing polygons that look like lines in QGIS
- 2020 VW Jetta SEL air distribution map
- Using explosive flux charges as an electric cannon power source
- How to apply the Cahn–Ingold–Prelog priority rules to an isotopically-labeled molecule?
- Does Hippolyta love Theseus in Shakespeare's "A Midsummer Night's Dream?"
- Can street names be normalized to single form?
- Can we use "It varies a lot" at the beginning of a new paragraph?
- How to represent BFS and DFS between adjacency matrix and list?
- Is there a valid reason why Canon's webcam plugin asks to scan my external drives?
- How to avoid accidentally sharing proprietary information when working for a competitor of a former employer?
- How do I make an arrayed object fit a 3D curve?
- Infinitive as an instruction
- Could the theory of evolution become common knowledge in a society with medieval technology?
- Science Fiction boardgame.Two players (maybe more possible) Torus shaped spaceship gameboard You control reproducing aliens. Played 1986-1988

- NIST 800-53
- Common Controls Hub
Windows Server 2019 Enable computer and user accounts to be trusted for delegation user right must not be assigned to any groups or accounts on domain-joined member servers and standalone systems.
User Rights Assignment Policy
Check that your User Rights Assignment policy settings comply with security standards in both your Group Policy Objects and on all your Windows computers at once with our reporting tool XIA Configuration .
Use the built-in Windows compliance benchmark to expose servers and workstations that do not meet your security policies.
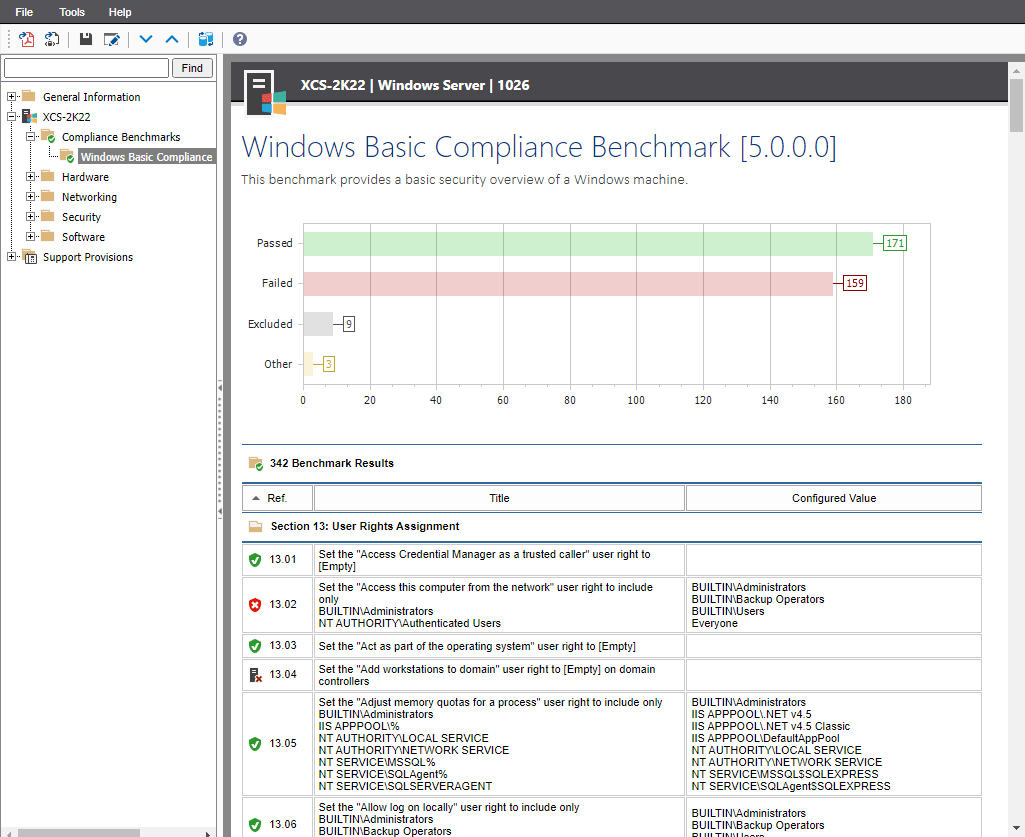
XIA Configuration has a non-intrusive architecture with agentless data collection and PowerShell support .
User Rights Assignment in Group Policy
User Rights Assignment policy settings are typically viewed in the Group Policy Management Console in the following section:
Computer Configuration > Windows Settings > Security Settings > Local Policies > User Rights Assignment
XIA Configuration presents this data in a modern, intuitive web interface and provides reporting functionality allowing you to audit all your Group Policy Objects at once.
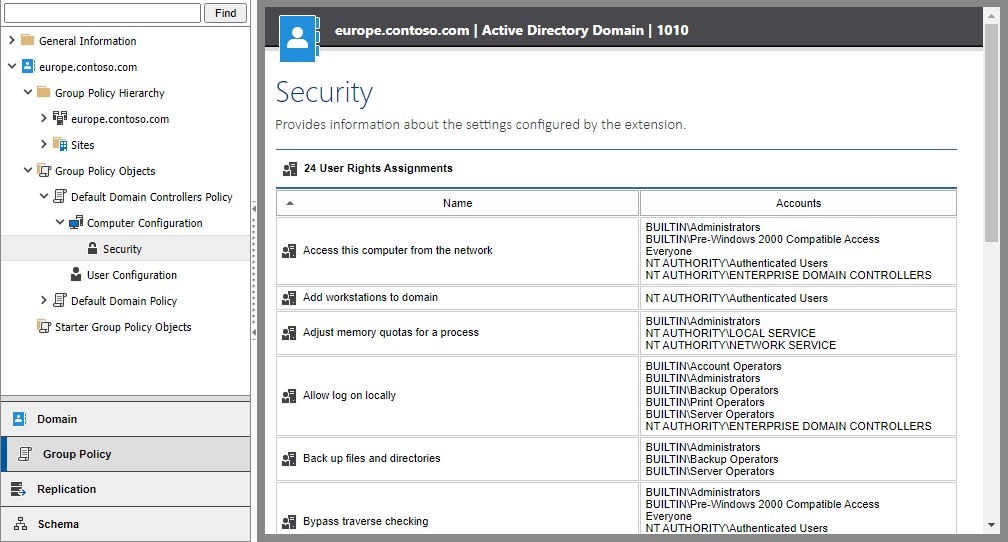
Audit and document your User Rights Assignment settings
If you're performing a security audit on your network, checking group policy settings is essential. As well as getting data from Group Policy, XIA Configuration also automates the retrieval of applied security settings across all your Windows computers.
- The reporting feature allows you to query all your computers at once
- The Windows compliance benchmark allows you to check your data complies with security standards
- Report filters allow you to get the data you need for external auditors
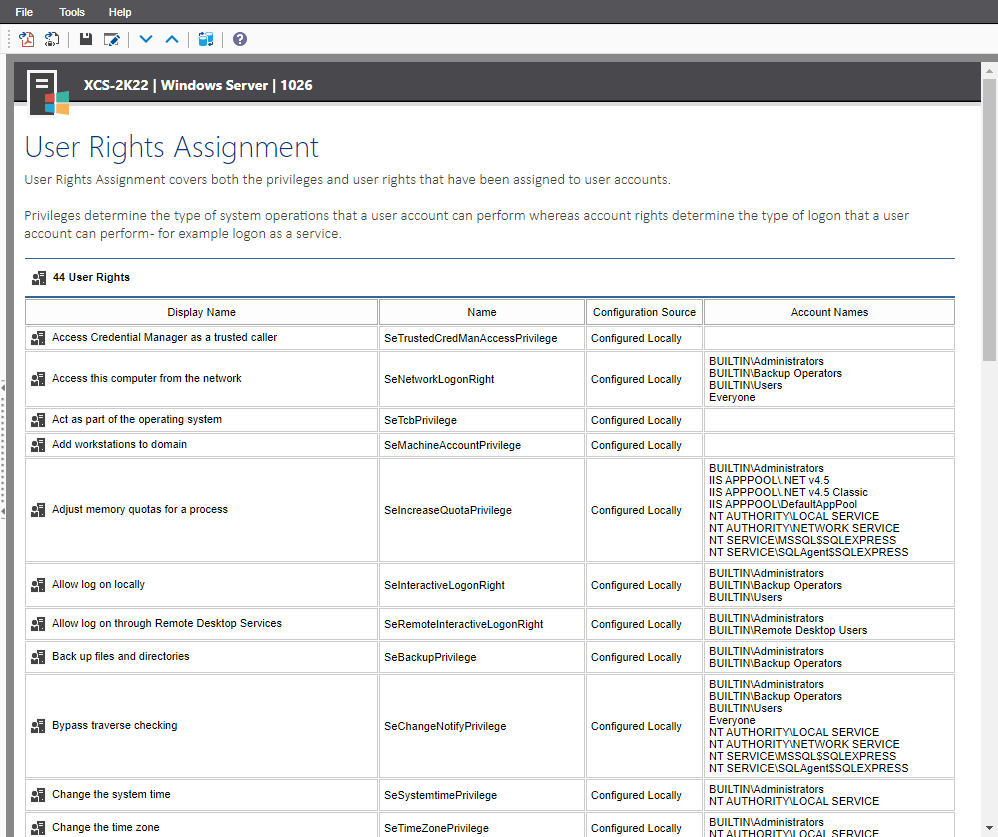
Check your User Rights Assignment security settings
Both the privileges and the user rights that have been assigned to user accounts are covered.
- Display name - for example "Access to this computer from the network"
- Internal right or privilege name - for example "SeNetworkLogonRight"
- Configuration Source (Local / Group Policy (GPO))
- Users and groups with this right assigned
Press the Show details link to view all the user rights retrieved by XIA Configuration.
- Access Credential Manager as a trusted caller
- Access this computer from the network
- Act as part of the operating system
- Add workstations to domain
- Adjust memory quotas for a process
- Allow log on locally
- Allow log on through Remote Desktop Services
- Back up files and directories
- Bypass traverse checking
- Change the system time
- Change the time zone
- Create a pagefile
- Create a token object
- Create global objects
- Create permanent shared objects
- Create symbolic links
- Debug programs
- Deny access to this computer from the network
- Deny log on as a batch job
- Deny log on as a service
- Deny log on locally
- Deny log on through Remote Desktop Services
- Enable computer and user accounts to be trusted for delegation
- Force shutdown from a remote system
- Generate security audits
- Impersonate a client after authentication
- Increase a process working set
- Increase scheduling priority
- Load and unload device drivers
- Lock pages in memory
- Log on as a batch job
- Log on as a service
- Manage auditing and security log
- Modify an object label
- Modify firmware environment values
- Obtain an impersonation token for another user in the same session
- Perform volume maintenance tasks
- Profile single process
- Profile system performance
- Remove computer from docking station
- Replace a process-level token
- Restore files and directories
- Shut down the system
- Synchronize directory service data
- Take ownership of files or other objects
To see all the Windows settings supported by XIA Configuration, navigate up to Windows .
Try auditing your user rights assignment settings for free
No commitments. No costs. Try XIA Configuration today.
Up to Windows
By continuing to browse, you are agreeing to our use of cookies as explained in our Cookie Policy .
The Federal Register
The daily journal of the united states government, request access.
Due to aggressive automated scraping of FederalRegister.gov and eCFR.gov, programmatic access to these sites is limited to access to our extensive developer APIs.
If you are human user receiving this message, we can add your IP address to a set of IPs that can access FederalRegister.gov & eCFR.gov; complete the CAPTCHA (bot test) below and click "Request Access". This process will be necessary for each IP address you wish to access the site from, requests are valid for approximately one quarter (three months) after which the process may need to be repeated.
An official website of the United States government.
If you want to request a wider IP range, first request access for your current IP, and then use the "Site Feedback" button found in the lower left-hand side to make the request.
This browser is no longer supported.
Upgrade to Microsoft Edge to take advantage of the latest features, security updates, and technical support.
Security policy settings
- 1 contributor
This reference topic describes the common scenarios, architecture, and processes for security settings.
Security policy settings are rules that administrators configure on a computer or multiple devices for protecting resources on a device or network. The Security Settings extension of the Local Group Policy Editor snap-in allows you to define security configurations as part of a Group Policy Object (GPO). The GPOs are linked to Active Directory containers such as sites, domains, or organizational units, and they enable you to manage security settings for multiple devices from any device joined to the domain. Security settings policies are used as part of your overall security implementation to help secure domain controllers, servers, clients, and other resources in your organization.
Security settings can control:
- User authentication to a network or device.
- The resources that users are permitted to access.
- Whether to record a user's or group's actions in the event log.
- Membership in a group.
To manage security configurations for multiple devices, you can use one of the following options:
- Edit specific security settings in a GPO.
- Use the Security Templates snap-in to create a security template that contains the security policies you want to apply, and then import the security template into a Group Policy Object. A security template is a file that represents a security configuration, and it can be imported to a GPO, applied to a local device, or used to analyze security.
For more info about managing security configurations, see Administer security policy settings .
The Security Settings extension of the Local Group Policy Editor includes the following types of security policies:
Account Policies. These policies are defined on devices; they affect how user accounts can interact with the computer or domain. Account policies include the following types of policies:
- Password Policy. These policies determine settings for passwords, such as enforcement and lifetimes. Password policies are used for domain accounts.
- Account Lockout Policy. These policies determine the conditions and length of time that an account will be locked out of the system. Account lockout policies are used for domain or local user accounts.
- Kerberos Policy. These policies are used for domain user accounts; they determine Kerberos-related settings, such as ticket lifetimes and enforcement.
Local Policies. These policies apply to a computer and include the following types of policy settings:
Audit Policy. Specify security settings that control the logging of security events into the Security log on the computer, and specifies what types of security events to log (success, failure, or both).
For devices running Windows 7 and later, we recommend to use the settings under Advanced Audit Policy Configuration rather than the Audit Policy settings under Local Policies.
User Rights Assignment. Specify the users or groups that have sign-in rights or privileges on a device
Security Options. Specify security settings for the computer, such as Administrator and Guest Account names; access to floppy disk drives and CD-ROM drives; installation of drivers; sign-in prompts; and so on.
Windows Firewall with Advanced Security. Specify settings to protect the device on your network by using a stateful firewall that allows you to determine which network traffic is permitted to pass between your device and the network.
Network List Manager Policies. Specify settings that you can use to configure different aspects of how networks are listed and displayed on one device or on many devices.
Public Key Policies. Specify settings to control Encrypting File System, Data Protection, and BitLocker Drive Encryption in addition to certain certificate paths and services settings.
Software Restriction Policies. Specify settings to identify software and to control its ability to run on your local device, organizational unit, domain, or site.
Application Control Policies. Specify settings to control which users or groups can run particular applications in your organization based on unique identities of files.
IP Security Policies on Local Computer. Specify settings to ensure private, secure communications over IP networks by using cryptographic security services. IPsec establishes trust and security from a source IP address to a destination IP address.
Advanced Audit Policy Configuration. Specify settings that control the logging of security events into the security log on the device. The settings under Advanced Audit Policy Configuration provide finer control over which activities to monitor as opposed to the Audit Policy settings under Local Policies.
Windows edition and licensing requirements
The following table lists the Windows editions that support Windows security policy settings and auditing:
Windows security policy settings and auditing license entitlements are granted by the following licenses:
For more information about Windows licensing, see Windows licensing overview .
Policy-based security settings management
The Security Settings extension to Group Policy provides an integrated policy-based management infrastructure to help you manage and enforce your security policies.
You can define and apply security settings policies to users, groups, and network servers and clients through Group Policy and Active Directory Domain Services (AD DS). A group of servers with the same functionality can be created (for example, a Microsoft Web (IIS) server), and then Group Policy Objects can be used to apply common security settings to the group. If more servers are added to this group later, many of the common security settings are automatically applied, reducing deployment and administrative labor.
Common scenarios for using security settings policies
Security settings policies are used to manage the following aspects of security: accounts policy, local policy, user rights assignment, registry values, file and registry Access Control Lists (ACLs), service startup modes, and more.
As part of your security strategy, you can create GPOs with security settings policies configured specifically for the various roles in your organization, such as domain controllers, file servers, member servers, clients, and so on.
You can create an organizational unit (OU) structure that groups devices according to their roles. Using OUs is the best method for separating specific security requirements for the different roles in your network. This approach also allows you to apply customized security templates to each class of server or computer. After creating the security templates, you create a new GPO for each of the OUs, and then import the security template (.inf file) into the new GPO.
Importing a security template to a GPO ensures that any accounts to which the GPO is applied automatically receive the template's security settings when the Group Policy settings are refreshed. On a workstation or server, the security settings are refreshed at regular intervals (with a random offset of at most 30 minutes), and, on a domain controller, this process occurs every few minutes if changes have occurred in any of the GPO settings that apply. The settings are also refreshed every 16 hours, whether or not any changes have occurred.
These refresh settings vary between versions of the operating system and can be configured.
By using Group Policy−based security configurations in conjunction with the delegation of administration, you can ensure that specific security settings, rights, and behavior are applied to all servers and computers within an OU. This approach makes it simple to update many servers with any other changes required in the future.
Dependencies on other operating system technologies
For devices that are members of a Windows Server 2008 or later domain, security settings policies depend on the following technologies:
Active Directory Domain Services (AD DS)
The Windows-based directory service, AD DS, stores information about objects on a network and makes this information available to administrators and users. By using AD DS, you can view and manage network objects on the network from a single location, and users can access permitted network resources by using a single sign in.
Group Policy
The infrastructure within AD DS that enables directory-based configuration management of user and computer settings on devices running Windows Server. By using Group Policy, you can define configurations for groups of users and computers, including policy settings, registry-based policies, software installation, scripts, folder redirection, Remote Installation Services, Internet Explorer maintenance, and security.
Domain Name System (DNS)
A hierarchical naming system used for locating domain names on the Internet and on private TCP/IP networks. DNS provides a service for mapping DNS domain names to IP addresses, and IP addresses to domain names. This service allows users, computers, and applications to query DNS to specify remote systems by fully qualified domain names rather than by IP addresses.
A part of the Windows operating system that provides interactive logon support. Winlogon is designed around an interactive logon model that consists of three components: the Winlogon executable, a credential provider, and any number of network providers.
Security configuration interacts with the operating system setup process during a clean installation or upgrade from earlier versions of Windows Server.
Security Accounts Manager (SAM)
A Windows service used during the sign-in process. SAM maintains user account information, including groups to which a user belongs.
Local Security Authority (LSA)
A protected subsystem that authenticates and signs in users to the local system. LSA also maintains information about all aspects of local security on a system, collectively known as the Local Security Policy of the system.
Windows Management Instrumentation (WMI)
A feature of the Microsoft Windows operating system, WMI is the Microsoft implementation of Web-Based Enterprise Management (WBEM), which is an industry initiative to develop a standard technology for accessing management information in an enterprise environment. WMI provides access to information about objects in a managed environment. Through WMI and the WMI application programming interface (API), applications can query for and make changes to static information in the Common Information Model (CIM) repository and dynamic information maintained by the various types of providers.
Resultant Set of Policy (RSoP)
An enhanced Group Policy infrastructure that uses WMI in order to make it easier to plan and debug policy settings. RSoP provides public methods that expose what an extension to Group Policy would do in a what-if situation, and what the extension has done in an actual situation. These public methods allow administrators to easily determine the combination of policy settings that apply to, or will apply to, a user or device.
Service Control Manager (SCM)
Used for configuration of service startup modes and security.
Used for configuration of registry values and security.
- File system
Used for configuration of security.
File system conversions
Security is set when an administrator converts a file system from FAT to NTFS.
Microsoft Management Console (MMC)
The user interface for the Security Settings tool is an extension of the Local Group Policy Editor MMC snap-in.
Security settings policies and Group Policy
The Security Settings extension of the Local Group Policy Editor is part of the Security Configuration Manager tool set. The following components are associated with Security Settings: a configuration engine; an analysis engine; a template and database interface layer; setup integration logic; and the secedit.exe command-line tool. The security configuration engine is responsible for handling security configuration editor-related security requests for the system on which it runs. The analysis engine analyzes system security for a given configuration and saves the result. The template and database interface layer handles reading and writing requests from and to the template or database (for internal storage). The Security Settings extension of the Local Group Policy Editor handles Group Policy from a domain-based or local device. The security configuration logic integrates with setup and manages system security for a clean installation or upgrade to a more recent Windows operating system. Security information is stored in templates (.inf files) or in the Secedit.sdb database.
The following diagram shows Security Settings and related features.
Security Settings Policies and Related Features
Provides the core security engine functionality.
Provides the client-side interfaces to the security configuration engine and provides data to Resultant Set of Policy (RSoP).
Wsecedit.dll
The Security Settings extension of Local Group Policy Editor. scecli.dll is loaded into wsecedit.dll to support the Security Settings user interface.
The Local Group Policy Editor MMC snap-in.
Security Settings extension architecture
The Security Settings extension of the Local Group Policy Editor is part of the Security Configuration Manager tools, as shown in the following diagram.
Security Settings Architecture
The security settings configuration and analysis tools include a security configuration engine, which provides local computer (non-domain member) and Group Policy−based configuration and analysis of security settings policies. The security configuration engine also supports the creation of security policy files. The primary features of the security configuration engine are scecli.dll and scesrv.dll.
The following list describes these primary features of the security configuration engine and other Security Settings−related features.
This .dll file is hosted in services.exe and runs under local system context. scesrv.dll provides core Security Configuration Manager functionality, such as import, configure, analyze, and policy propagation.
Scesrv.dll performs configuration and analysis of various security-related system parameters by calling corresponding system APIs, including LSA, SAM, and the registry.
Scesrv.dll exposes APIs such as import, export, configure, and analyze. It checks that the request is made over LRPC (Windows XP) and fails the call if it isn't.
Communication between parts of the Security Settings extension occurs by using the following methods:
- Component Object Model (COM) calls
- Local Remote Procedure Call (LRPC)
- Lightweight Directory Access Protocol (LDAP)
- Active Directory Service Interfaces (ADSI)
- Server Message Block (SMB)
- Windows Management Instrumentation (WMI) calls
On domain controllers, scesrv.dll receives notifications of changes made to SAM and the LSA that need to be synchronized across domain controllers. Scesrv.dll incorporates those changes into the Default Domain Controller Policy GPO by using in-process scecli.dll template modification APIs. Scesrv.dll also performs configuration and analysis operations.
This Scecli.dll is the client-side interface or wrapper to scesrv.dll. scecli.dll is loaded into Wsecedit.dll to support MMC snap-ins. It's used by Setup to configure default system security and security of files, registry keys, and services installed by the Setup API .inf files.
The command-line version of the security configuration and analysis user interfaces, secedit.exe, uses scecli.dll.
Scecli.dll implements the client-side extension for Group Policy.
Scesrv.dll uses scecli.dll to download applicable Group Policy files from SYSVOL in order to apply Group Policy security settings to the local device.
Scecli.dll logs application of security policy into WMI (RSoP).
Scesrv.dll policy filter uses scecli.dll to update Default Domain Controller Policy GPO when changes are made to SAM and LSA.
The Security Settings extension of the Group Policy Object Editor snap-in. You use this tool to configure security settings in a Group Policy Object for a site, domain, or organizational unit. You can also use Security Settings to import security templates to a GPO.
Secedit.sdb
This Secedit.sdb is a permanent system database used for policy propagation including a table of persistent settings for rollback purposes.
User databases
A user database is any database other than the system database created by administrators for the purposes of configuration or analysis of security.
.Inf Templates
These templates are text files that contain declarative security settings. They're loaded into a database before configuration or analysis. Group Policy security policies are stored in .inf files on the SYSVOL folder of domain controllers, where they're downloaded (by using file copy) and merged into the system database during policy propagation.
Security settings policy processes and interactions
For a domain-joined device, where Group Policy is administered, security settings are processed in conjunction with Group Policy. Not all settings are configurable.
Group Policy processing
When a computer starts and a user signs in, computer policy and user policy are applied according to the following sequence:
The network starts. Remote Procedure Call System Service (RPCSS) and Multiple Universal Naming Convention Provider (MUP) start.
An ordered list of Group Policy Objects is obtained for the device. The list might depend on these factors:
- Whether the device is part of a domain and, therefore, subject to Group Policy through Active Directory.
- The location of the device in Active Directory.
- Whether the list of Group Policy Objects has changed. If the list of Group Policy Objects hasn't changed, no processing is done.
Computer policy is applied. These settings are the ones under Computer Configuration from the gathered list. This process is a synchronous one by default and occurs in the following order: local, site, domain, organizational unit, child organizational unit, and so on. No user interface appears while computer policies are processed.
Startup scripts run. These scripts are hidden and synchronous by default; each script must complete or time out before the next one starts. The default time-out is 600 seconds. You can use several policy settings to modify this behavior.
The user presses CTRL+ALT+DEL to sign in.
After the user is validated, the user profile loads; it's governed by the policy settings that are in effect.
An ordered list of Group Policy Objects is obtained for the user. The list might depend on these factors:
- Whether the user is part of a domain and, therefore, subject to Group Policy through Active Directory.
- Whether loopback policy processing is enabled, and if so, the state (Merge or Replace) of the loopback policy setting.
- The location of the user in Active Directory.
User policy is applied. These settings are the ones under User Configuration from the gathered list. These settings are synchronous by default and in the following order: local, site, domain, organizational unit, child organizational unit, and so on. No user interface appears while user policies are processed.
Logon scripts run. Group Policy−based logon scripts are hidden and asynchronous by default. The user object script runs last.
The operating system user interface that is prescribed by Group Policy appears.
Group Policy Objects storage
A Group Policy Object (GPO) is a virtual object that is identified by a Globally Unique Identifier (GUID) and stored at the domain level. The policy setting information of a GPO is stored in the following two locations:
Group Policy containers in Active Directory.
The Group Policy container is an Active Directory container that contains GPO properties, such as version information, GPO status, plus a list of other component settings.
Group Policy templates in a domain's system volume folder (SYSVOL).
The Group Policy template is a file system folder that includes policy data specified by .admx files, security settings, script files, and information about applications that are available for installation. The Group Policy template is located in the SYSVOL folder in the <domain>\Policies subfolder.
The GROUP_POLICY_OBJECT structure provides information about a GPO in a GPO list, including the version number of the GPO, a pointer to a string that indicates the Active Directory portion of the GPO, and a pointer to a string that specifies the path to the file system portion of the GPO.
Group Policy processing order
Group Policy settings are processed in the following order:
Local Group Policy Object.
Each device running a Windows operating system beginning with Windows XP has exactly one Group Policy Object that is stored locally.
Any Group Policy Objects that have been linked to the site are processed next. Processing is synchronous and in an order that you specify.
Processing of multiple domain-linked Group Policy Objects is synchronous and in an order you specify.
Organizational units.
Group Policy Objects that are linked to the organizational unit that is highest in the Active Directory hierarchy are processed first, then Group Policy Objects that are linked to its child organizational unit, and so on. Finally, the Group Policy Objects that are linked to the organizational unit that contains the user or device are processed.
At the level of each organizational unit in the Active Directory hierarchy, one, many, or no Group Policy Objects can be linked. If several Group Policy Objects are linked to an organizational unit, their processing is synchronous and in an order that you specify.
This order means that the local Group Policy Object is processed first, and Group Policy Objects that are linked to the organizational unit of which the computer or user is a direct member are processed last, which overwrites the earlier Group Policy Objects.
This order is the default processing order and administrators can specify exceptions to this order. A Group Policy Object that is linked to a site, domain, or organizational unit (not a local Group Policy Object) can be set to Enforced with respect to that site, domain, or organizational unit, so that none of its policy settings can be overridden. At any site, domain, or organizational unit, you can mark Group Policy inheritance selectively as Block Inheritance . Group Policy Object links that are set to Enforced are always applied, however, and they can't be blocked. For more information, see Group Policy Basics – Part 2: Understanding Which GPOs to Apply .
Security settings policy processing
In the context of Group Policy processing, security settings policy is processed in the following order.
During Group Policy processing, the Group Policy engine determines which security settings policies to apply.
If security settings policies exist in a GPO, Group Policy invokes the Security Settings client-side extension.
The Security Settings extension downloads the policy from the appropriate location such as a specific domain controller.
The Security Settings extension merges all security settings policies according to precedence rules. The processing is according to the Group Policy processing order of local, site, domain, and organizational unit (OU), as described earlier in the "Group Policy processing order" section. If multiple GPOs are in effect for a given device and there are no conflicting policies, then the policies are cumulative and are merged.
This example uses the Active Directory structure shown in the following figure. A given computer is a member of OU2, to which the GroupMembershipPolGPO GPO is linked. This computer is also subject to the UserRightsPolGPO GPO, which is linked to OU1, higher in the hierarchy. In this case, no conflicting policies exist so the device receives all of the policies contained in both the UserRightsPolGPO and the GroupMembershipPolGPO GPOs.
Multiple GPOs and Merging of Security Policy
The resultant security policies are stored in secedit.sdb, the security settings database. The security engine gets the security template files and imports them to secedit.sdb.
The security settings policies are applied to devices. The following figure illustrates the security settings policy processing.
Security Settings Policy Processing
Merging of security policies on domain controllers
Password policies, Kerberos, and some security options are only merged from GPOs that are linked at the root level on the domain. This merging is done to keep those settings synchronized across all domain controllers in the domain. The following security options are merged:
- Network Security: Force sign out when sign-in hours expire
- Accounts: Administrator account status
- Accounts: Guest account status
- Accounts: Rename administrator account
- Accounts: Rename guest account
Another mechanism exists that allows security policy changes made by administrators by using net accounts to be merged into the Default Domain Policy GPO. User rights changes that are made by using Local Security Authority (LSA) APIs are filtered into the Default Domain Controllers Policy GPO.
Special considerations for domain controllers
If an application is installed on a primary domain controller (PDC) with operations master role (also known as flexible single master operations or FSMO) and the application makes changes to user rights or password policy, these changes must be communicated to ensure that synchronization across domain controllers occurs. Scesrv.dll receives a notification of any changes made to the security account manager (SAM) and LSA that need to be synchronized across domain controllers and then incorporates the changes into the Default Domain Controller Policy GPO by using scecli.dll template modification APIs.
When security settings are applied
After you've edited the security settings policies, the settings are refreshed on the computers in the organizational unit linked to your Group Policy Object in the following instances:
- When a device is restarted.
- Every 90 minutes on a workstation or server and every 5 minutes on a domain controller. This refresh interval is configurable.
- By default, Security policy settings delivered by Group Policy are also applied every 16 hours (960 minutes) even if a GPO hasn't changed.
Persistence of security settings policy
Security settings can persist even if a setting is no longer defined in the policy that originally applied it.
Security settings might persist in the following cases:
- The setting hasn't been previously defined for the device.
- The setting is for a registry security object.
- The settings are for a file system security object.
All settings applied through local policy or through a Group Policy Object are stored in a local database on your computer. Whenever a security setting is modified, the computer saves the security setting value to the local database, which retains a history of all the settings that have been applied to the computer. If a policy first defines a security setting and then no longer defines that setting, then the setting takes on the previous value in the database. If a previous value doesn't exist in the database, then the setting doesn't revert to anything and remains defined as is. This behavior is sometimes referred to as "tattooing".
Registry and file security settings will maintain the values applied through Group Policy until that setting is set to other values.
Permissions required for policy to apply
Both Apply Group Policy and Read permissions are required to have the settings from a Group Policy Object apply to users or groups, and computers.
Filtering security policy
By default, all GPOs have Read and Apply Group Policy both Allowed for the Authenticated Users group. The Authenticated Users group includes both users and computers. Security settings policies are computer-based. To specify which client computers will or won't have a Group Policy Object applied to them, you can deny them either the Apply Group Policy or Read permission on that Group Policy Object. Changing these permissions allows you to limit the scope of the GPO to a specific set of computers within a site, domain, or OU.
Do not use security policy filtering on a domain controller as this would prevent security policy from applying to it.
Migration of GPOs containing security settings
In some situations, you might want to migrate GPOs from one domain environment to another environment. The two most common scenarios are test-to-production migration, and production-to-production migration. The GPO copying process has implications for some types of security settings.
Data for a single GPO is stored in multiple locations and in various formats; some data is contained in Active Directory and other data is stored on the SYSVOL share on the domain controllers. Certain policy data might be valid in one domain but might be invalid in the domain to which the GPO is being copied. For example, Security Identifiers (SIDs) stored in security policy settings are often domain-specific. So copying GPOs isn't as simple as taking a folder and copying it from one device to another.
The following security policies can contain security principals and might require some more work to successfully move them from one domain to another.
- User rights assignment
- Restricted groups
- The GPO DACL, if you choose to preserve it during a copy operation
To ensure that data is copied correctly, you can use Group Policy Management Console (GPMC). When there's a migration of a GPO from one domain to another, GPMC ensures that all relevant data is properly copied. GPMC also offers migration tables, which can be used to update domain-specific data to new values as part of the migration process. GPMC hides much of the complexity involved in the migrating GPO operations, and it provides simple and reliable mechanisms for performing operations such as copy and backup of GPOs.
In this section
Additional resources.

IMAGES
VIDEO
COMMENTS
1 Press the Win + R keys to open Run, type secpol.msc into Run, and click/tap on OK to open Local Security Policy. 2 Expand open Local Policies in the left pane of Local Security Policy, and click/tap on User Rights Assignment. (see screenshot below step 3) 3 In the right pane of User Rights Assignment, double click/tap on the policy (ex: "Shut down the system") you want to add users and/or ...
The constant names are used when referring to the user right in log events. You can configure the user rights assignment settings in the following location within the Group Policy Management Console (GPMC) under Computer Configuration\Windows Settings\Security Settings\Local Policies\User Rights Assignment, or on the local device by using the ...
In the console tree, click Computer Configuration, select Windows Settings, and then select Security Settings. Do one of the following: Select Account Policies to edit the Password Policy or Account Lockout Policy. Select Local Policies to edit an Audit Policy, a User Rights Assignment, or Security Options. In the details pane, double-click the ...
Any change to the user rights assignment for an account becomes effective the next time the owner of the account logs on. Group Policy. Settings are applied in the following order through a Group Policy Object (GPO), which will overwrite settings on the local computer at the next Group Policy update: Local policy settings; Site policy settings
4. You cannot edit this User Rights Assignment policy because this setting is being managed by a domain-based Group Policy. In this case, the domain Group Policy setting has precedence and you are prevented from modifying the policy via Local Group Policy. To modify this policy, either:
Run "gpedit.msc". Navigate to Local Computer Policy >> Computer Configuration >> Windows Settings >> Security Settings >> Local Policies >> User Rights Assignment. If any groups or accounts other than the following are granted the "Allow log on locally" user right, this is a finding: Administrators. Users.
I want to modify the user rights associated with a local user account.I want to add groups and users to a particular User Rights. This is done by opening the group policy and opening the following folder in the console tree: Computer Configuration\Windows Settings\Security Settings\Local Policies\User Rights Assignment.
Open Group Policy Editor. Go to the Computer Configuration section. Select Windows Settings. Select Security Settings. Go to the Local Policies section. Select User Rights Assignment. Select the user right that you want to configure. Add the users or groups that should be granted that right.
Verify the effective setting in Local Group Policy Editor. Run "gpedit.msc". Navigate to Local Computer Policy >> Computer Configuration >> Windows Settings >> Security Settings >> Local Policies >> User Rights Assignment. If the following groups or accounts are not defined for the "Deny log on locally" right, this is a finding. Domain Systems ...
In a non-domain environment, gpedit.msc lets me associate various "user rights" (like "create a pagefile" or "create permanent shared objects") with users or accounts. This is in Computer Configuration | Windows Settings | Security Settings | Local Policies | User Rights Assignment. Where exactly do I do this in AD?
Administrative templates - Intune UserRights - UserRights Policy 1. I have two options to deploy UserRights settings: Group Policy if the device is domain joined or Hybrid Azure AD Joined. Computer Configuration\Windows Settings\Security Settings\Local Policies\User Rights Assignment. Custom Windows 10 policy CSP using Intune for Azure AD ...
Computer Configuration\Policies\Windows Settings\Security Settings\Local Policies\User Rights Assignment. Default values. The following table lists the actual and effective default policy values for the most recent supported versions of Windows. Default values are also listed on the policy's property page.
I went to make changes in the local computer policy, specifically >windows settings> security settings>local policies>user rights assignment. It appears that security settings>local policies>user rights assignment are locked as are the local policies (little padlock on the file) I am the administrator of the computer -- the only user -- how do I unlock these folders so I can make changes.
User Rights Assignment. Access Credential Manager as a trusted caller. Access this computer from the network. Act as part of the operating system. Add workstations to a domain. Adjust memory quotas for a process. Allow log on locally. Allow log on through Remote Desktop Services. Backup files and directories.
To manage user rights and permissions, access the "Computer Configuration > Windows Settings > Security Settings > Local Policies > User Rights Assignment" section in the Local Group Policy ...
Verify the effective setting in Local Group Policy Editor. Run "gpedit.msc". Navigate to Local Computer Policy >> Computer Configuration >> Windows Settings >> Security Settings >> Local Policies >> User Rights Assignment. If any accounts or groups other than the following are granted the "Allow log on locally" user right, this is a finding.
Perform volume maintenance tasks. Lock pages in memory. under Local Computer Policy\Computer Configuration\Windows Settings\Security Settings\User Rights Management . I tried the below 3 ways. Find the Registry key for corresponding Group Policy : (1)Final Link broken (2)Couldn't locate above in reference guide or MSDN doc.
Computer Configuration\Windows Settings\Security Settings\Local Policies\User Rights Assignment. Default values. The following table lists the actual and effective default policy values for the most recent supported versions of Windows. Default values are also listed on the policy's property page.
You have opened the Local Group Policy Editor and under Computer Configuration, you have navigated to: Computer Configuration > Windows Settings > Security Settings > Local Policies > User Rights Assignment. Which of the following policies needs to be configured to define which users can log on to the local computer?
Navigate to Local Computer Policy >> Computer Configuration >> Windows Settings >> Security Settings >> Local Policies >> User Rights Assignment. If any accounts or groups are granted the "Enable computer and user accounts to be trusted for delegation" user right, this is a finding. For server core installations, run the following command:
Check your User Rights Assignment security settings. Both the privileges and the user rights that have been assigned to user accounts are covered. Press the Show details link to view all the user rights retrieved by XIA Configuration. To see all the Windows settings supported by XIA Configuration, navigate up to Windows. No commitments. No costs.
REFERENCES. TestOut Client Pro - 8.3 User Rights and Account Policies. Study with Quizlet and memorize flashcards containing terms like To increase security for your Windows notebook system while traveling, you decide to require a smart card in order to sign on. You also want users to be signed out automatically when the smart card is removed.
The constant names are used when referring to the user right in log events. You can configure the user rights assignment settings in the following location within the Group Policy Management Console (GPMC) under Computer Configuration\Windows Settings\Security Settings\Local Policies\User Rights Assignment, or on the local computer by using the ...
This site displays a prototype of a "Web 2.0" version of the daily Federal Register. It is not an official legal edition of the Federal Register, and does not replace the official print version or the official electronic version on GPO's govinfo.gov. The documents posted on this site are XML ...
The following table lists the Windows editions that support Windows security policy settings and auditing: Windows Pro ... accounts policy, local policy, user rights assignment, registry values, file and registry Access Control Lists (ACLs), service startup modes, and more. ... The security settings configuration and analysis tools include a ...