- Search Menu
- Editor's Choice
- Author Guidelines
- Submission Site
- Open Access
- About Journal of Cybersecurity
- Editorial Board
- Advertising and Corporate Services
- Journals Career Network
- Self-Archiving Policy
- Journals on Oxford Academic
- Books on Oxford Academic


Editors-in-Chief
Tyler Moore
About the journal
Journal of Cybersecurity publishes accessible articles describing original research in the inherently interdisciplinary world of computer, systems, and information security …
Latest articles

Call for Papers
Journal of Cybersecurity is soliciting papers for a special collection on the philosophy of information security. This collection will explore research at the intersection of philosophy, information security, and philosophy of science.
Find out more

High-Impact Research Collection
Explore a collection of freely available high-impact research from 2020 and 2021 published in the Journal of Cybersecurity .
Browse the collection here

Submit your paper
Join the conversation moving the science of security forward. Visit our Instructions to Authors for more information about how to submit your manuscript.

Read and Publish deals
Authors interested in publishing in Journal of Cybersecurity may be able to publish their paper Open Access using funds available through their institution’s agreement with OUP.
Find out if your institution is participating
Related Titles

Affiliations
- Online ISSN 2057-2093
- Print ISSN 2057-2085
- Copyright © 2024 Oxford University Press
- About Oxford Academic
- Publish journals with us
- University press partners
- What we publish
- New features
- Open access
- Institutional account management
- Rights and permissions
- Get help with access
- Accessibility
- Advertising
- Media enquiries
- Oxford University Press
- Oxford Languages
- University of Oxford
Oxford University Press is a department of the University of Oxford. It furthers the University's objective of excellence in research, scholarship, and education by publishing worldwide
- Copyright © 2024 Oxford University Press
- Cookie settings
- Cookie policy
- Privacy policy
- Legal notice
This Feature Is Available To Subscribers Only
Sign In or Create an Account
This PDF is available to Subscribers Only
For full access to this pdf, sign in to an existing account, or purchase an annual subscription.
data security Recently Published Documents
Total documents.
- Latest Documents
- Most Cited Documents
- Contributed Authors
- Related Sources
- Related Keywords
Big Data Security Management Countermeasures in the Prevention and Control of Computer Network Crime
This paper aims to study the Countermeasures of big data security management in the prevention and control of computer network crime in the absence of relevant legislation and judicial practice. Starting from the concepts and definitions of computer crime and network crime, this paper puts forward the comparison matrix, investigation and statistics method and characteristic measure of computer crime. Through the methods of crime scene investigation, network investigation and network tracking, this paper studies the big data security management countermeasures in the prevention and control of computer network crime from the perspective of criminology. The experimental results show that the phenomenon of low age is serious, and the number of Teenagers Participating in network crime is on the rise. In all kinds of cases, criminals under the age of 35 account for more than 50%.
Fog Computing with IoT Device’s Data Security Management Using Density Control Weighted Election and Extensible Authentication Protocol
Integration of blockchain with connected and autonomous vehicles: vision and challenge.
Connected and Autonomous Vehicles (CAVs) are introduced to improve individuals’ quality of life by offering a wide range of services. They collect a huge amount of data and exchange them with each other and the infrastructure. The collected data usually includes sensitive information about the users and the surrounding environment. Therefore, data security and privacy are among the main challenges in this industry. Blockchain, an emerging distributed ledger, has been considered by the research community as a potential solution for enhancing data security, integrity, and transparency in Intelligent Transportation Systems (ITS). However, despite the emphasis of governments on the transparency of personal data protection practices, CAV stakeholders have not been successful in communicating appropriate information with the end users regarding the procedure of collecting, storing, and processing their personal data, as well as the data ownership. This article provides a vision of the opportunities and challenges of adopting blockchain in ITS from the “data transparency” and “privacy” perspective. The main aim is to answer the following questions: (1) Considering the amount of personal data collected by the CAVs, such as location, how would the integration of blockchain technology affect transparency , fairness , and lawfulness of personal data processing concerning the data subjects (as this is one of the main principles in the existing data protection regulations)? (2) How can the trade-off between transparency and privacy be addressed in blockchain-based ITS use cases?
SecNVM: An Efficient and Write-Friendly Metadata Crash Consistency Scheme for Secure NVM
Data security is an indispensable part of non-volatile memory (NVM) systems. However, implementing data security efficiently on NVM is challenging, since we have to guarantee the consistency of user data and the related security metadata. Existing consistency schemes ignore the recoverability of the SGX style integrity tree (SIT) and the access correlation between metadata blocks, thereby generating unnecessary NVM write traffic. In this article, we propose SecNVM, an efficient and write-friendly metadata crash consistency scheme for secure NVM. SecNVM utilizes the observation that for a lazily updated SIT, the lost tree nodes after a crash can be recovered by the corresponding child nodes in NVM. It reduces the SIT persistency overhead through a restrained write-back metadata cache and exploits the SIT inter-layer dependency for recovery. Next, leveraging the strong access correlation between the counter and DMAC, SecNVM improves the efficiency of security metadata access through a novel collaborative counter-DMAC scheme. In addition, it adopts a lightweight address tracker to reduce the cost of address tracking for fast recovery. Experiments show that compared to the state-of-the-art schemes, SecNVM improves the performance and decreases write traffic a lot, and achieves an acceptable recovery time.
Review on Blockchain Technology
Abstract: Blockchain is a technology that has the potential to cause big changes in our corporate environment and will have a significant influence over the next few decades. It has the potential to alter our perception of business operations and revolutionise our economy. Blockchain is a decentralised and distributed ledger system that, since it cannot be tampered with or faked, attempts to assure transparency, data security, and integrity. Only a few studies have looked at the usage of Blockchain Technology in other contexts or sectors, with the majority of current Blockchain Technology research focusing on its use for cryptocurrencies like Bitcoin. Blockchain technology is more than simply bitcoin; it may be used in government, finance and banking, accounting, and business process managementAs a result, the goal of this study is to examine and investigate the advantages and drawbacks of Blockchain Technology for current and future applications. As a consequence, a large number of published studies were thoroughly assessed and analysed based on their contributions to the Blockchain body of knowledge. Keywords: Blockchain Technology, Bitcoin, Cryptocurrency, Digital currency
China’s Data Security Policies Leading to the Cyber Security Law
A novel framework of an iot-blockchain-based intelligent system.
With the growing need of technology into varied fields, dependency is getting directly proportional to ease of user-friendly smart systems. The advent of artificial intelligence in these smart systems has made our lives easier. Several Internet of Things- (IoT-) based smart refrigerator systems are emerging which support self-monitoring of contents, but the systems lack to achieve the optimized run time and data security. Therefore, in this research, a novel design is implemented with the hardware level of integration of equipment with a more sophisticated software design. It was attempted to design a new smart refrigerator system, which has the capability of automatic self-checking and self-purchasing, by integrating smart mobile device applications and IoT technology with minimal human intervention carried through Blynk application on a mobile phone. The proposed system automatically makes periodic checks and then waits for the owner’s decision to either allow the system to repurchase these products via Ethernet or reject the purchase option. The paper also discussed the machine level integration with artificial intelligence by considering several features and implemented state-of-the-art machine learning classifiers to give automatic decisions. The blockchain technology is cohesively combined to store and propagate data for the sake of data security and privacy concerns. In combination with IoT devices, machine learning, and blockchain technology, the proposed model of the paper can provide a more comprehensive and valuable feedback-driven system. The experiments have been performed and evaluated using several information retrieval metrics using visualization tools. Therefore, our proposed intelligent system will save effort, time, and money which helps us to have an easier, faster, and healthier lifestyle.
BARRIERS TO THE ADOPTION OF NEW SAFETY TECHNOLOGIES IN CONSTRUCTION: A DEVELOPING COUNTRY CONTEXT
The adoption rate of new technologies is still relatively low in the construction industry, particularly for mitigating occupational safety and health (OSH) risks, which is traditionally a largely labor-intensive activity in developing countries, occupying ill-afforded non-productive management resources. However, understanding why this is the case is a relatively unresearched area in developing countries such as Malaysia. In aiming to help redress this situation, this study explored the major barriers involved, firstly by a detailed literature review to identify the main barriers hampering the adoption of new technologies for safety science and management in construction. Then, a questionnaire survey of Malaysian construction practitioners was used to prioritize these barriers. A factor analysis further identified six major dimensions underlying the barriers, relating to the lack of OSH regulations and legislation, technological limitations, lack of genuine organizational commitment, prohibitive costs, poor safety culture within the construction industry, and privacy and data security concerns. Taken together, the findings provide a valuable reference to assist industry practitioners and researchers regarding the critical barriers to the adoption of new technologies for construction safety management in Malaysia and other similar developing countries, and bridge the identified knowledge gap concerning the dimensionality of the barriers.
Design and Development of Maritime Data Security Management Platform
Since the e-Navigation strategy was put forward, various countries and regions in the world have researched e-Navigation test platforms. However, the sources of navigation data are multi-source, and there are still difficulties in the unified acquisition, processing, analysis and application of multi-source data. Users often find it difficult to obtain the required comprehensive navigation information. The purpose of this paper is to use e-Navigation architecture to design and develop maritime data security management platform, strengthen navigation safety guarantee, strengthen Marine environment monitoring, share navigation and safety information, improve the ability of shipping transportation organizations in ports, and protect the marine environment. Therefore, this paper proposes a four-layer system architecture based on Java 2 Platform Enterprise Edition (J2EE) technology, and designs a unified maritime data storage, analysis and management platform, which realizes the intelligent, visualized and modular management of maritime data at shipside and the shore. This platform can provide comprehensive data resource services for ship navigation and support the analysis and mining of maritime big data. This paper expounds on the design, development scheme and demonstration operation scheme of the maritime data security management platform from the system structure and data exchange mode.
Mapping the quantity, quality and structural indicators of Asian (48 countries and 3 territories) research productivity on cloud computing
PurposeThe purpose of this study was to map the quantity (frequency), quality (impact) and structural indicators (correlations) of research produced on cloud computing in 48 countries and 3 territories in the Asia continent.Design/methodology/approachTo achieve the objectives of the study and scientifically map the indicators, data were extracted from the Scopus database. The extracted bibliographic data was first cleaned properly using Endnote and then analyzed using Biblioshiny and VosViewer application software. In the software, calculations include citations count; h, g and m indexes; Bradford's and Lotka's laws; and other scientific mappings.FindingsResults of the study indicate that China remained the most productive, impactful and collaborative country in Asia. All the top 20 impactful authors were also from China. The other most researched areas associated with cloud computing were revealed to be mobile cloud computing and data security in clouds. The most prominent journal currently publishing research studies on cloud computing was “Advances in Intelligent Systems and Computing.”Originality/valueThe study is the first of its kind which identified the quantity (frequencies), quality (impact) and structural indicators (correlations) of Asian (48 countries and 3 territories) research productivity on cloud computing. The results are of great importance for researchers and countries interested in further exploring, publishing and increasing cross country collaborations related to the phenomenon of cloud computing.
Export Citation Format
Share document.
Academia.edu no longer supports Internet Explorer.
To browse Academia.edu and the wider internet faster and more securely, please take a few seconds to upgrade your browser .
- We're Hiring!
- Help Center
Database Security
- Most Cited Papers
- Most Downloaded Papers
- Newest Papers
- Save to Library
- Last »
- Web Application Security Follow Following
- Database Vault Follow Following
- Oracle Database Vault Follow Following
- Database Watermarking Follow Following
- Social Networking Security and Privacy Follow Following
- Penetration Testing Follow Following
- Wireless Sensor Network Security Follow Following
- XML Databases Follow Following
- Physical security Follow Following
- Data Warehousing and Data Mining Follow Following
Enter the email address you signed up with and we'll email you a reset link.
- Academia.edu Publishing
- We're Hiring!
- Help Center
- Find new research papers in:
- Health Sciences
- Earth Sciences
- Cognitive Science
- Mathematics
- Computer Science
- Academia ©2024
Advertisement
Improved Database Security Using Cryptography with Genetic Operators
- Original Research
- Published: 29 July 2023
- Volume 4 , article number 570 , ( 2023 )

Cite this article
- Sandeep Reddy Devara ORCID: orcid.org/0000-0002-1126-3733 1 &
- Chandrasekhar Azad 1
116 Accesses
Explore all metrics
Database security is of utmost importance in today’s digital age where sensitive data is vulnerable to unauthorized access and cyber-attacks. Various security models have been developed for databases, each concentrating on a different part of the database security challenge. This paper presents a novel approach to improve database security by leveraging the combination of cryptography and genetic operators. The proposed technique involves encrypting the data using cryptographic algorithms, ensuring its confidentiality even in the event of a compromised database login. Additionally, genetic operators are employed to enhance the encryption process, making it more robust against potential vulnerabilities. Through the encryption and comparison mechanisms, only authorized users with the correct credentials can access and decipher the data, providing an additional layer of protection. The effectiveness of this approach is demonstrated through its ability to mitigate common causes of database vulnerabilities and safeguard valuable information. Furthermore, future research directions are suggested further to enhance the efficiency and effectiveness of the encryption algorithms, ultimately strengthening the overall security of databases.
This is a preview of subscription content, log in via an institution to check access.
Access this article
Price includes VAT (Russian Federation)
Instant access to the full article PDF.
Rent this article via DeepDyve
Institutional subscriptions
Similar content being viewed by others

Applications of Genetic Algorithms in Cryptology

A Survey of Advanced Encryption for Database Security: Primitives, Schemes, and Attacks

A Novel Genetic Algorithm-Based DES Key Generation Scheme
Sadkhan SB. A proposed genetic algorithm attack for public key cryptosystem. In: 7th international engineering conference “research & innovation amid global pandemic” (IEC), Erbil, Iraq, 2021; p. 194–9.
Bhowmik C, Momin MAI, Shanta FJ and Haque MM. Database security as a gateway to privacy preserving data mining. In: 2021, 2nd International conference on robotics, electrical and signal processing techniques (ICREST), DHAKA, Bangladesh, p. 125–30.
Wang Y, Xi J, Cheng T. The overview of database security threats’ solutions: traditional and machine learning. J Inf Secur. 2021;12(1):34–55.
Google Scholar
Murthy PS and Nagalakshmi V. Database forensics and security mea-sures to defend from cyber threats. In: 3rd International conference on intelligent sustainable systems (ICISS), 2020; p. 1302–7.
Lambora, Gupta K, and Chopra K. Genetic algorithm—a literature review. In: International conference on machine learning, big data, cloud and parallel computing, Faridabad, India, 2019; p. 380–4.
Mittal A, Gupta RK. Encryption and decryption of a message involving Genetic Algorithm. Int J Eng Adv Technol. 2019;9(2):3920–3.
Article Google Scholar
Reddaiah B. Cryptosystem using crossover function and logical operators. Int J Eng Adv Technol. 2019;9(2):55–9.
Mudgal PK, Purohit R, Sharma R, Jangir MK. Application of genetic algorithm in cryptanalysis of mono-alphabetic substitution cipher. In: International conference on computing, communication and automation, 2017; p. 400–5.
Kumar B, Hasani MHSA. Database security risks and control methods. In: First IEEE international conference on computer communication and the internet, 2016; p. 334–40.
Kumar A, Chatterjee K. An efficient stream cipher using genetic algorithm. In: IEEE WiSPNET 2016 conference, 2016; p. 2322–6.
Sagar V, Kumar K. A symmetric key cryptography using genetic algorithm and error back propagation neural network. In: 2nd International conference on computing for sustainable global development (INDIACom), 2015; p. 1386–91.
Thuraisingham B. Database security: past, present and future. In: IEEE international congress on big data, 2015; p. 772–4.
Alsharafat WS. Evolutionary genetic algorithm for encryption. In: IEEE international conference on computational intelligence and computing research, 2014.
Almutairi AH & Alruwaili AH. Security in database systems. In: Global journal of computer science and technology network, web & security, 2012; p. 9–14.
Ruzhi X, Jian G, Liwu D. A database security gateway to the detection of SQL attacks. In: 3rd International conference on advanced computer theory and engineering (ICACTE), Chengdu, China, 2010; p. 537–40.
Imran S, Hyder I. Security issues in databases. In: Second international conference on future information technology and management engineering, 2009; p. 541–5.
Ambhore PB, Meshram BB, Waghmare VB. A implementation of object oriented database security. In: First international workshop on knowledge discovery and data mining (WKDD 2008), Adelaide, Australia, 2008;p. 359–65.
Bertino E, Sandhu R. Database security-concepts, approaches, and challenges. IEEE Trans Dependable Secure Comput. 2005. https://doi.org/10.1109/TDSC.2005.9 .
Lin F-T, Kao C-Y. A genetic algorithm for ciphertext-only attack in cryptanalysis. In: 1995, IEEE, 1995; p. 650–4.
Rana SK, Rana SK, Nisar K, Ag Ibrahim AA, Rana AK, Goyal N, Chawla P. Blockchain technology and artificial intelligence based decentralized access control model to enable secure interoperability for healthcare. Sustainability. 2022;14(15):9471.
Rana A, Sharma S, Nisar K, Ibrahim AAA, Dhawan S, Chowdhry B, Hussain S, Goyal N. The rise of blockchain internet of things (BIoT): secured, device-to-device architecture and simulation scenarios. Appl Sci. 2022;12(15):7694.
Kakkar L, Gupta D, Tanwar S, Saxena S, Alsubhi K, et al. A secure and efficient signature scheme for IoT in healthcare. Comput Mater Continua. 2022;73(3):6151–68.
Download references
Author information
Authors and affiliations.
Department of Computer Science and Engineering, NIT Jamshedpur, Jamshedpur, Jharkhand, 831014, India
Sandeep Reddy Devara & Chandrasekhar Azad
You can also search for this author in PubMed Google Scholar
Corresponding author
Correspondence to Sandeep Reddy Devara .
Ethics declarations
Conflict of interest.
The authors have no relevant financial or non-financial interests to disclose.
Additional information
Publisher's note.
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
This article is part of the topical collection “Research Trends in Communication and Network Technologies” guest edited by Anshul Verma, Pradeepika Verma and Kiran Kumar Pattanaik.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
Reprints and permissions
About this article
Devara, S.R., Azad, C. Improved Database Security Using Cryptography with Genetic Operators. SN COMPUT. SCI. 4 , 570 (2023). https://doi.org/10.1007/s42979-023-01990-z
Download citation
Received : 08 March 2023
Accepted : 01 June 2023
Published : 29 July 2023
DOI : https://doi.org/10.1007/s42979-023-01990-z
Share this article
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
- Database security
- IP snoopers
- Cryptography
- Genetic algorithm
- Authentication
- Find a journal
- Publish with us
- Track your research
Research on the Big Data Security Application Based on Artificial Intelligence Technology in Operators
Ieee account.
- Change Username/Password
- Update Address
Purchase Details
- Payment Options
- Order History
- View Purchased Documents
Profile Information
- Communications Preferences
- Profession and Education
- Technical Interests
- US & Canada: +1 800 678 4333
- Worldwide: +1 732 981 0060
- Contact & Support
- About IEEE Xplore
- Accessibility
- Terms of Use
- Nondiscrimination Policy
- Privacy & Opting Out of Cookies
A not-for-profit organization, IEEE is the world's largest technical professional organization dedicated to advancing technology for the benefit of humanity. © Copyright 2024 IEEE - All rights reserved. Use of this web site signifies your agreement to the terms and conditions.
Journal of Materials Chemistry A
Zn alloying strategy to improve the photoluminescence of cugas 2 /zns core/shell quantum dots †.

* Corresponding authors
a Department of Physics, Savitribai Phule Pune University, Pune 411 007, India E-mail: [email protected]
b Symbiosis Center for Nanoscience and Nanotechnology, Symbiosis International University, Lavale, Pune 412 115, India
c Atomic & Molecular Physics Division, Bhabha Atomic Research Centre, Mumbai 400 094, India
d Beamline Development and Application Section, Bhabha Atomic Research Centre, Mumbai 400 094, India
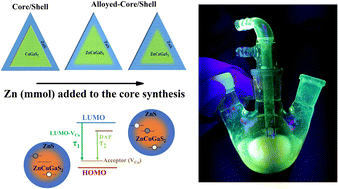
Research efforts are being devoted to realize colloidal, heavy metal ion free, and luminescent quantum dots. We address radiative recombination in Zn alloyed CuGaS 2 /ZnS core/shell chalcopyrite quantum dots (CQDs) emitting in the blue-green spectral region. QDs show a systematic increase in the optical band gap and emission energy with an increasing amount of Zn in their core. Intentionally making non-stoichiometric CQDs with core/shell geometry enables defect related emission with high intensity. The location of Cu related defect levels along with the valence band and conduction band edge was determined from electrochemical cyclic voltammetry (CV) measurements. The evolution of band gap energies with respect to Zn concentration examined using CV measurements matches well with the optical absorption data. The presence of Cu vacancies in off-stoichiometric samples introduces intra-gap levels, which serve as common acceptor levels for optical transitions. Luminescence transitions in these materials stem from the radiative recombination of electrons from conduction levels as well as donor levels, with holes localized at acceptor levels. Temperature dependent and excitation laser intensity dependent emission measurements confirm the role of the Cu vacancy related acceptor level in the emission. Local structure studies via extended X-ray absorption fine structure and X-ray absorption near edge structure analysis were carried out to understand how Zn is incorporated in CuGaS 2 quantum dots and affects the luminescence. Electron spin resonance measurements confirm the presence of paramagnetic defect complexes. X-ray absorption near edge structure measurements indicate that Cu co-exists in +1 and +2 oxidation states in CuGaS 2 quantum dots.
- This article is part of the themed collection: Journal of Materials Chemistry A HOT Papers
Supplementary files
- Supplementary information PDF (729K)
Article information
Download citation, permissions.
Zn alloying strategy to improve the photoluminescence of CuGaS 2 /ZnS core/shell quantum dots
M. A. Haque, A. Lohar, Y. Jadhav, R. Kumar, S. N. Jha, D. Bhattacharyya, S. Jadkar, S. Sartale and S. Mahamuni, J. Mater. Chem. A , 2024, Advance Article , DOI: 10.1039/D4TA01134A
To request permission to reproduce material from this article, please go to the Copyright Clearance Center request page .
If you are an author contributing to an RSC publication, you do not need to request permission provided correct acknowledgement is given.
If you are the author of this article, you do not need to request permission to reproduce figures and diagrams provided correct acknowledgement is given. If you want to reproduce the whole article in a third-party publication (excluding your thesis/dissertation for which permission is not required) please go to the Copyright Clearance Center request page .
Read more about how to correctly acknowledge RSC content .
Social activity
Search articles by author.
This article has not yet been cited.
Advertisements

IMAGES
VIDEO
COMMENTS
This paper talks about the basics of database including its meaning, characteristics, role etc. with special focus on different security challenges in the database. Moreover, this paper highlights the basics of security management, tools in this regard. Hence different areas of database security have mentioned in this paper in a simple sense.
Data are today an asset more critical than ever for all organizations we may think of. Recent advances and trends, such as sensor systems, IoT, cloud computing, and data analytics, are making possible to pervasively, efficiently, and effectively collect data. However for data to be used to their full power, data security and privacy are critical. Even though data security and privacy have been ...
The paper also discusses the impact of emerging trends such as cloud computing, big data, and the Internet of Things on database security. By synthesizing existing research, this review aims to ...
co ver from hardw are and softw are failure as well as mec hanisms to m itigate. Database Security: Concepts and Approaches 5. malicious data access denials which make the database system una v ...
There are a number of studies that look at database security from different angles. In their study [], Mai et al. suggest using cloud-based security measures to safeguard power system databases.Using an RSA encryption method, public and private keys are generated for database encryption; a huge prime integer is chosen randomly from the cloud platform's Simple Storage Service and used as the ...
Abstract: With the growth and increasing sophistication of the Internet and the increasing dependence, it appeared more and more services over the Internet-based database, so it increases the risks facing databases. The number of attacks against these repositories has also increased. A database danger refers to an item, individual or other entity that poses a risk of misuse or manipulation of ...
Abstract and Figures. This research paper delves into the critical realm of database security, a pressing concern for modern organizations with sensitive data. It explores various security threats ...
Database security has received a great deal of attention since the mid-1970s starting from discretionary security for System R and Ingres to access control models to multilevel database systems to security for emerging data management systems to data privacy to privacy-preserving data mining to data mining for security applications to big data security and privacy. This paper describes the ...
Abstract. Data is a critical merit resource and due to its importance, data protection is a noteworthy component of database security. ... This research paper coheres databases and its security in any organization. Issues of unauthorized access, deception, vulnerability, authentication and fabrication has been discussed along with the solutions ...
of the most current database security studies. • It also highlights the importance of maintaining careful attention to database security and suggests a direction for future research in this field. 1.2 Motivation for the paper Several research in the literature seeks to give a solution for database security. However, before moving forward with
In this paper, we survey the state of the art in access control for database systems, discuss the main research issues, and outline possible directions for future research. ... VA, USA (Received in final revised/arm 16 May 1995) Abstract As an increasing number of organizations become dependent on access to their data over the Internet, the ...
Computers & Security, 11 (1992) 41-56 Security in Database Systems A Research Perspective* Teresa F. Lunt Computer Science Laboratory, SRI International, Menlo Park, CA 99025, USA Database security has been the subject of active research for the past several years. In the last five years, rapid progress has been made in defining what security ...
Abstract. As an increasing number of organizations become dependent on access to their data over the Internet, the need for adequate security measures is becoming more and more critical. The most popular security measure these days is a firewall. However, a firewall is not immune to penetration, and it does not provide any protection of ...
One way to maintain the security of the database is to use encryption techniques. The method used to secure the database is encryption using the ROTI3 and Caesar Cipher methods. Both of these methods have advantages in processing speed. For thisreason, the author will compare the use of the two algorithms above in terms of the encryption and ...
Journal of Cybersecurity publishes accessible articles describing original research in the inherently interdisciplinary world of computer, systems, and information security …. Journal of Cybersecurity is soliciting papers for a special collection on the philosophy of information security. This collection will explore research at the ...
And Control . Characteristic Measure. This paper aims to study the Countermeasures of big data security management in the prevention and control of computer network crime in the absence of relevant legislation and judicial practice. Starting from the concepts and definitions of computer crime and network crime, this paper puts forward the ...
This research paper delves into the critical realm of database security, a pressing concern for modern organizations with sensitive data. It explores various security threats faced by database ...
The aim of this paper is to examine both current data security research and to analyse whether "traditional" vulnerability registries provide a sufficient insight on DBMS security, or they should be rather inspected by using IoTSE-based and respective passive testing, or dynamically inspected by DBMS holders conducting an active testing.
Coalesce Techniques to Secure Web Applications and Databases against SQL Injection Attacks. Abstract- SQL Injection attacks are one of the gravest threats for web applications. In this paper, we propose coalesce techniques to mitigate SQL injection attacks and focus on the research of the attack protection module.
The purpose of the paper is to highlight and threat types and their impacts on sensitive data, and presents different security models. The assumption underlying this study is that by understanding the weaknesses and the threats facing databases, database administrators can then begin to create a security plan to better protect their databases.
Unmanned Aerial Vehicles (UAVs) are integral in various sectors like agriculture, surveillance, and logistics, driven by advancements in 5G. However, existing research lacks a comprehensive approach addressing both data freshness and security concerns. In this paper, we address the intricate challenges of data freshness, and security, especially in the context of eavesdropping and jamming in ...
Database security is of utmost importance in today's digital age where sensitive data is vulnerable to unauthorized access and cyber-attacks. Various security models have been developed for databases, each concentrating on a different part of the database security challenge. This paper presents a novel approach to improve database security by leveraging the combination of cryptography and ...
The use of pointed or edged tools or objects is one of the most challenging aspects of today's application of physical human-robot interaction (pHRI). One reason for this is that the severity of harm caused by such edged or pointed impactors is less well studied than for blunt impactors. Consequently, the standards specify well-reasoned force and pressure thresholds for blunt impactors and ...
Abstract and Figures. Security of Data is the most important task in today's world. Over the years various encryption schemes have been developed in order to protect the database from various ...
The application of individual tree detection algorithms for assessing forest inventories and aiding decision-making in forestry has been a subject of research for more than two decades. Nevertheless, there is a notable research gap in the development of robust algorithms capable of automatically detecting trees of different species, ages, and varied crown sizes in dense forest environments.
Abstract: The importance of data security and privacy is increasing under the trend of digital development and has become an important work research direction for government and enterprises, operators carry a large amount of data of users in the industry. This paper describes potential data security threats in the big data environment, especially operators, and proposes a security protection ...
Research efforts are being devoted to realize colloidal, heavy metal ion free, and luminescent quantum dots. We address radiative recombination in Zn alloyed CuGaS 2 /ZnS core/shell chalcopyrite quantum dots (CQDs) emitting in the blue-green spectral region. QDs show a systematic increase in the optical band gap and emission energy with an increasing amount of Zn in their core.