Terrorism, counter-terrorism and international humanitarian law

Statement of Christine Beerli, ICRC Vice-President at the 17th edition Bruges Colloquium , 20 -21 october 2016
Terrorism is a scourge to which the international community has been striving to respond for decades. The obvious challenges it poses are not only long-lasting, but also immediate. Wherever we turn these days, across the world, we are confronted with increased risks of terrorist acts. Terrorism is a global phenomenon sometimes closely link to armed conflict; and one which the international community is increasingly facing.
Terrorism negates the fundamental principles of humanity as well as the essential principles and objectives of international humanitarian law (IHL). In this regard, the ICRC condemns acts of terrorism, irrespective of their perpetrators, be they committed in or outside an armed conflict, and is deeply distressed by their devastating impact on communities and individuals.
Indeed, every day we see the dramatic consequences of the fight between States and non-State armed groups designated as terrorist, in particular in Africa and in the Levant. Irrespective of the claimed legitimacy of this fight or the causes espoused by or attributed to those involved therein, what we observe in the field is once again the civilian population bearing the brunt of armed violence. Cities are reduced to rubble, civilians are directly attacked, humanitarian and medical personnel, transports and infrastructures are targeted and prevented from fulfilling their functions, the civilian population is deprived of supplies essential for its survival through siege warfare, humanitarian access is denied and, resulting from all of this, hundreds of thousands of people are internally displaced or have fled their country, leaving a home, a job, a plot of land, or even close relatives behind. In the absence of a political solution, compliance with IHL and the fundamental values underpinning this body of law are required more than ever, from all sides, because prohibition of acts of terrorism and other violations of the law are not just binding on non-State armed groups.

BRUGES 2016 PHOTO GALLERY
The rise of non-state armed groups resorting to acts of terrorism is a growing concern domestically but also internationally. This situation has led States and international organizations to react by tightening existing counterterrorism measures and introducing new ones. Of course, the ICRC does not challenge the necessity of States to take legitimate measures to ensure their security. Nonetheless, while taking such measures to eliminate terrorism, the safeguards protecting human life and dignity must be upheld. In the ICRC's view, the international community must be clear and firm on the need for counterterrorism activities to be conducted in full respect of the protection afforded to all individuals by international law, in particular IHL and human rights law. Such respect is in the interest of the international community, as there is today growing recognition that violations of these bodies of international law may in turn exacerbate the very phenomenon that counterterrorism purports to fight.
Neither armed conflict nor terrorism are new forms of violence. Both have existed for a long time and have, for most part, been understood to be separate phenomena, as demonstrated by the different legal frameworks that regulate them. The perception that armed conflict and terrorism differ and that their respective legal rules are distinct has radically changed since September 2001 and the subsequent launching of the so-called "global war on terrorism". Recent years have again seen the rise of non-State armed groups resorting to acts of terrorism and the subsequent engagement of a coalition of States against them. This situation has put the relationship between IHL and the legal framework governing terrorism back into the spotlight and may have even created the perception that there may be a new "global war on terrorism" involving a group or groups of unbounded geographical reach.
The recent actions taken by States against non-State armed groups designated as terrorist and the correlative counterterrorism discourse in both domestic and international fora have significantly contributed to a blurring of the lines between armed conflict and terrorism and their respective legal frameworks. This is further exacerbated by the fact that, often, counterterrorism instruments include situations of armed conflict in their scope of application. The resultant overlaps and contradictions between IHL and the legal instruments specifically designed to address terrorism is problematic. Counterterrorism norms may interfere with IHL's regulation of armed violence, notably by prohibiting conduct that is not unlawful under IHL, creating legal confusion and potentially adversely affecting some of the underlying principles of IHL. In this regard, one should carefully study the consequences of such interference and seek creative ways to ensure the integrity of IHL, thereby maintaining its rationale – which is needed more than ever in current armed conflicts.
The fight against terrorism may take various forms, including armed conflict. Determining when IHL applies to particular counterterrorism activities is not an easy enterprise. Not only because some States may tend to deny the applicability of IHL on the basis that non-State armed groups designated as terrorist organizations cannot be considered party to an armed conflict. How, when and where IHL applies to counterterrorism activities still raises important legal questions.
First of all, it is important to recall that any use of force against non-state armed groups designated as terrorist – or against members and affiliates thereof – is not necessarily synonymous with a situation of armed conflict governed by IHL. When armed force is used, only the facts on the ground are relevant for determining the legal classification of a situation of violence. Some situations may be classified as international armed conflicts, others as non-international armed conflicts, while various acts of violence may fall outside any armed conflict due to lack of requisite nexus. In the ICRC's view, this is also true for the fight against terrorism.
Another crucial question relating to IHL applicability is whether non-state armed groups designated as terrorist fulfil the organization criterion for classifying a situation as a non-international armed conflict. This is all the more difficult in view of the myriad of fluid, multiplying and fragmenting armed groups that frequently take part in the fighting. Often, their structure is difficult to understand. In some cases, some form of leadership structure emerges at some point, claiming to unite different armed groups, often based on pledges of allegiances. This raises the question of what link needs to exist between different armed groups in order to consider formerly distinct entities as one party to an armed conflict. The same question also emerges with regard to different groups that join forces transnationally, such as different armed groups pledging allegiance to the Islamic State group or to Al Qaida.
The spillover of conflicts into neighboring countries, their geographical expanse and their regionalization also appear to have become distinctive features of many contemporary armed conflicts involving non-state armed groups designated as terrorist. The transnational nature of such armed conflict involving a non-state armed group capable of operating in various countries – even non-contiguous ones – directly raises the question of IHL's territorial reach. This is still a much-debated area of the law – in particular when it comes to the applicability of IHL for military operations in the territory of non-belligerent States – that will certainly benefit from your insights.
IHL has been sometimes described – wrongly in the ICRC's view – as a set of rules which hinders the efforts of States to efficiently address their security concerns and fails to provide adequate tools to deal with non-state armed groups designated as terrorist. I am confident that we will be able to dispel some misconceptions in this regard and highlight the fact that, in situations of armed conflict, IHL should not be considered as an obstacle to the fight against terrorism. On the contrary, IHL can be a powerful tool at States' disposal while still providing important protections – complemented by human rights law – for those affected by the armed conflict between States against non-State armed groups designated as terrorist. This added value of IHL is significant in the fields of the use of force and detention.
The phenomenon of the so-called "foreign fighters" – nationals of one country who travel abroad to fight alongside a non-State armed group in the territory of another State – has increased exponentially over the past few years. In order to quell the threats emanating from foreign fighters, States - in particular within the framework of the UN Security Council - have taken a variety of measures, including the use of force, detention (on terrorism charges, among others), and travel bans.
While most of the measures taken to prevent individuals from joining non-State armed groups or to mitigate the threat they may pose upon return are of a law enforcement nature, the applicability of IHL, where appropriate, should not be overlooked. However, so far, little attention has been paid to how IHL deals with the phenomenon of foreign fighters.
The concept of a "foreign fighter" is not a term of art in IHL. The general applicability of IHL to a situation of violence in which such fighters may be engaged does not depend on the nationality of those fighting. It depends only on the facts on the ground and on the fulfilment of certain legal conditions stemming from the relevant norms of IHL, in particular common Articles 2 and 3 of the Geneva Conventions. In other words, in situations of armed conflict, IHL will govern the actions of foreign fighters, as well as any actions against them by parties to that conflict, when such actions have a nexus to the armed conflict concerned.
In this regard, it is important to underline that foreign fighters detained in relation to an armed conflict to which the detaining authorities are party must benefit from the protections afforded by the applicable IHL rules, irrespective of the domestic laws that also govern their detention. Unfortunately, States dealing with the phenomenon of foreign fighters tend to shy away from recognizing the applicability of IHL to their detention. Our discussions will certainly allow us to understand why this is so and to clear up the misapprehension that IHL would not allow States to prosecute foreign fighters – a misapprehension which, in the ICRC's views, has no legal basis under IHL.
For nearly a decade the idea that the risk of radicalization potentially leading to violent actions should be addressed though social prevention programs has significantly progressed. Many States are developing and implementing various domestic plans to address the root causes of this phenomenon. These programs are now usually referred as preventing or countering violent extremism (P/CVE). States' understanding that "terrorism" must be fought through more than simply military or hard security means is in fact not a new avenue. It is mimicking years of counter-insurgency strategies and stabilization concepts implemented in conflict affected countries. Yet such P/CVE model has gained considerable ground amongst countries confronted to so-called home grown terrorism and the re-occurrence of violent actions against their respective population. In this political context, international organizations, the RC/RC Movement and various civil society actors are being asked to partner with states and support this movement through their existing or specially design programs.
The ICRC does not question the merit of these initiatives which may ultimately contribute to limit the risks of violations and abuses. However, while recognizing the general purpose of P/CVE concept as expressed in the recent UN plan of action that is to address the root cause of extreme violence, one should not underestimate its potential adverse effects on the existing legal protection frameworks. There may be also a risk that humanitarian organizations associated with CVE/PVE programs be seen by some States and non-State actors as politically motivated and therefore incapable to carry out a neutral, independent and impartial humanitarian action.
Within the framework of counterterrorism measures, efforts to curb and criminalize all possible direct and indirect support to so-called terrorist organizations have led to increased control and restraint on all activities, including humanitarian activities, that could in any way be seen as providing support to non-State armed groups or individuals designated as terrorists. Consequently, there is a significant risk that such measures, in particular criminal legislation, may further reduce the humanitarian space which the ICRC and other impartial humanitarian organizations need in order to carry out their neutral, independent and impartial activities.
Since 2011, the ICRC has on various occasions shared its concerns that such counter-terrorism measures have the potential to criminalize a range of humanitarian actors and their personnel, and may create obstacles to the funding of humanitarian activities. The unqualified prohibition of acts of "material support," "services" and "assistance to" or "association with" terrorist organizations found in certain criminal laws could, in practice, result in the criminalization of the core activities of impartial humanitarian organizations, and their personnel, that are endeavoring to meet the needs of victims of armed conflicts or situations of violence below the threshold of armed conflict.
In addition, the potential criminalization of humanitarian engagement with non-State armed groups designated as "terrorist organizations" and of humanitarian activities carried out in areas controlled by these groups may be said to reflect a non-acceptance of the notion of neutral, independent and impartial humanitarian action – a notion which the ICRC strives to promote in its operational work in the field.
The ICRC has deployed significant efforts to persuade States to stop legislating against principles they have supported and endorsed through IHL treaties, as well as to ensure that the new legal frameworks being developed as part of counterterrorism strategies do not challenge principled humanitarian action. So far, our work on this crucial issue was not as successful as we had expected, but the ICRC is convinced that stakeholders will understand the necessity to harmonize their policies and legal obligations across the humanitarian and counterterrorism realms.
For more information on the Bruges colloquium, please consult the following website of the College of Europe : http://www.coe-icrc.eu/en
- Search Menu
- Browse content in A - General Economics and Teaching
- Browse content in A1 - General Economics
- A10 - General
- A12 - Relation of Economics to Other Disciplines
- A13 - Relation of Economics to Social Values
- A14 - Sociology of Economics
- Browse content in A2 - Economic Education and Teaching of Economics
- A29 - Other
- Browse content in B - History of Economic Thought, Methodology, and Heterodox Approaches
- B0 - General
- Browse content in B1 - History of Economic Thought through 1925
- B11 - Preclassical (Ancient, Medieval, Mercantilist, Physiocratic)
- B12 - Classical (includes Adam Smith)
- Browse content in B2 - History of Economic Thought since 1925
- B20 - General
- B21 - Microeconomics
- B22 - Macroeconomics
- B25 - Historical; Institutional; Evolutionary; Austrian
- B26 - Financial Economics
- Browse content in B3 - History of Economic Thought: Individuals
- B31 - Individuals
- Browse content in B4 - Economic Methodology
- B41 - Economic Methodology
- Browse content in B5 - Current Heterodox Approaches
- B55 - Social Economics
- Browse content in C - Mathematical and Quantitative Methods
- Browse content in C0 - General
- C00 - General
- C02 - Mathematical Methods
- Browse content in C1 - Econometric and Statistical Methods and Methodology: General
- C10 - General
- C11 - Bayesian Analysis: General
- C12 - Hypothesis Testing: General
- C13 - Estimation: General
- C14 - Semiparametric and Nonparametric Methods: General
- C15 - Statistical Simulation Methods: General
- C19 - Other
- Browse content in C2 - Single Equation Models; Single Variables
- C21 - Cross-Sectional Models; Spatial Models; Treatment Effect Models; Quantile Regressions
- C22 - Time-Series Models; Dynamic Quantile Regressions; Dynamic Treatment Effect Models; Diffusion Processes
- C23 - Panel Data Models; Spatio-temporal Models
- C24 - Truncated and Censored Models; Switching Regression Models; Threshold Regression Models
- C25 - Discrete Regression and Qualitative Choice Models; Discrete Regressors; Proportions; Probabilities
- C26 - Instrumental Variables (IV) Estimation
- Browse content in C3 - Multiple or Simultaneous Equation Models; Multiple Variables
- C31 - Cross-Sectional Models; Spatial Models; Treatment Effect Models; Quantile Regressions; Social Interaction Models
- C32 - Time-Series Models; Dynamic Quantile Regressions; Dynamic Treatment Effect Models; Diffusion Processes; State Space Models
- C33 - Panel Data Models; Spatio-temporal Models
- C34 - Truncated and Censored Models; Switching Regression Models
- C35 - Discrete Regression and Qualitative Choice Models; Discrete Regressors; Proportions
- C36 - Instrumental Variables (IV) Estimation
- Browse content in C4 - Econometric and Statistical Methods: Special Topics
- C41 - Duration Analysis; Optimal Timing Strategies
- C43 - Index Numbers and Aggregation
- Browse content in C5 - Econometric Modeling
- C51 - Model Construction and Estimation
- C52 - Model Evaluation, Validation, and Selection
- C53 - Forecasting and Prediction Methods; Simulation Methods
- C54 - Quantitative Policy Modeling
- Browse content in C6 - Mathematical Methods; Programming Models; Mathematical and Simulation Modeling
- C60 - General
- C61 - Optimization Techniques; Programming Models; Dynamic Analysis
- C62 - Existence and Stability Conditions of Equilibrium
- C63 - Computational Techniques; Simulation Modeling
- Browse content in C7 - Game Theory and Bargaining Theory
- C71 - Cooperative Games
- C72 - Noncooperative Games
- C73 - Stochastic and Dynamic Games; Evolutionary Games; Repeated Games
- C78 - Bargaining Theory; Matching Theory
- Browse content in C8 - Data Collection and Data Estimation Methodology; Computer Programs
- C81 - Methodology for Collecting, Estimating, and Organizing Microeconomic Data; Data Access
- C82 - Methodology for Collecting, Estimating, and Organizing Macroeconomic Data; Data Access
- C83 - Survey Methods; Sampling Methods
- Browse content in C9 - Design of Experiments
- C90 - General
- C91 - Laboratory, Individual Behavior
- C92 - Laboratory, Group Behavior
- C93 - Field Experiments
- Browse content in D - Microeconomics
- Browse content in D0 - General
- D00 - General
- D01 - Microeconomic Behavior: Underlying Principles
- D02 - Institutions: Design, Formation, Operations, and Impact
- D03 - Behavioral Microeconomics: Underlying Principles
- D04 - Microeconomic Policy: Formulation; Implementation, and Evaluation
- Browse content in D1 - Household Behavior and Family Economics
- D10 - General
- D11 - Consumer Economics: Theory
- D12 - Consumer Economics: Empirical Analysis
- D13 - Household Production and Intrahousehold Allocation
- D14 - Household Saving; Personal Finance
- D15 - Intertemporal Household Choice: Life Cycle Models and Saving
- D16 - Collaborative Consumption
- D18 - Consumer Protection
- D19 - Other
- Browse content in D2 - Production and Organizations
- D21 - Firm Behavior: Theory
- D22 - Firm Behavior: Empirical Analysis
- D23 - Organizational Behavior; Transaction Costs; Property Rights
- D24 - Production; Cost; Capital; Capital, Total Factor, and Multifactor Productivity; Capacity
- D29 - Other
- Browse content in D3 - Distribution
- D30 - General
- D31 - Personal Income, Wealth, and Their Distributions
- D33 - Factor Income Distribution
- D39 - Other
- Browse content in D4 - Market Structure, Pricing, and Design
- D40 - General
- D41 - Perfect Competition
- D43 - Oligopoly and Other Forms of Market Imperfection
- D44 - Auctions
- Browse content in D5 - General Equilibrium and Disequilibrium
- D50 - General
- D53 - Financial Markets
- D58 - Computable and Other Applied General Equilibrium Models
- Browse content in D6 - Welfare Economics
- D60 - General
- D61 - Allocative Efficiency; Cost-Benefit Analysis
- D62 - Externalities
- D63 - Equity, Justice, Inequality, and Other Normative Criteria and Measurement
- D64 - Altruism; Philanthropy
- D69 - Other
- Browse content in D7 - Analysis of Collective Decision-Making
- D70 - General
- D71 - Social Choice; Clubs; Committees; Associations
- D72 - Political Processes: Rent-seeking, Lobbying, Elections, Legislatures, and Voting Behavior
- D73 - Bureaucracy; Administrative Processes in Public Organizations; Corruption
- D74 - Conflict; Conflict Resolution; Alliances; Revolutions
- D78 - Positive Analysis of Policy Formulation and Implementation
- Browse content in D8 - Information, Knowledge, and Uncertainty
- D80 - General
- D81 - Criteria for Decision-Making under Risk and Uncertainty
- D82 - Asymmetric and Private Information; Mechanism Design
- D83 - Search; Learning; Information and Knowledge; Communication; Belief; Unawareness
- D84 - Expectations; Speculations
- D85 - Network Formation and Analysis: Theory
- D86 - Economics of Contract: Theory
- Browse content in D9 - Micro-Based Behavioral Economics
- D90 - General
- D91 - Role and Effects of Psychological, Emotional, Social, and Cognitive Factors on Decision Making
- D92 - Intertemporal Firm Choice, Investment, Capacity, and Financing
- Browse content in E - Macroeconomics and Monetary Economics
- Browse content in E0 - General
- E00 - General
- E01 - Measurement and Data on National Income and Product Accounts and Wealth; Environmental Accounts
- E02 - Institutions and the Macroeconomy
- Browse content in E1 - General Aggregative Models
- E10 - General
- E11 - Marxian; Sraffian; Kaleckian
- E12 - Keynes; Keynesian; Post-Keynesian
- E13 - Neoclassical
- E19 - Other
- Browse content in E2 - Consumption, Saving, Production, Investment, Labor Markets, and Informal Economy
- E20 - General
- E21 - Consumption; Saving; Wealth
- E22 - Investment; Capital; Intangible Capital; Capacity
- E23 - Production
- E24 - Employment; Unemployment; Wages; Intergenerational Income Distribution; Aggregate Human Capital; Aggregate Labor Productivity
- E25 - Aggregate Factor Income Distribution
- E26 - Informal Economy; Underground Economy
- E27 - Forecasting and Simulation: Models and Applications
- Browse content in E3 - Prices, Business Fluctuations, and Cycles
- E30 - General
- E31 - Price Level; Inflation; Deflation
- E32 - Business Fluctuations; Cycles
- E37 - Forecasting and Simulation: Models and Applications
- Browse content in E4 - Money and Interest Rates
- E40 - General
- E41 - Demand for Money
- E42 - Monetary Systems; Standards; Regimes; Government and the Monetary System; Payment Systems
- E43 - Interest Rates: Determination, Term Structure, and Effects
- E44 - Financial Markets and the Macroeconomy
- E47 - Forecasting and Simulation: Models and Applications
- Browse content in E5 - Monetary Policy, Central Banking, and the Supply of Money and Credit
- E50 - General
- E51 - Money Supply; Credit; Money Multipliers
- E52 - Monetary Policy
- E58 - Central Banks and Their Policies
- Browse content in E6 - Macroeconomic Policy, Macroeconomic Aspects of Public Finance, and General Outlook
- E60 - General
- E61 - Policy Objectives; Policy Designs and Consistency; Policy Coordination
- E62 - Fiscal Policy
- E63 - Comparative or Joint Analysis of Fiscal and Monetary Policy; Stabilization; Treasury Policy
- E65 - Studies of Particular Policy Episodes
- E69 - Other
- Browse content in E7 - Macro-Based Behavioral Economics
- E70 - General
- E71 - Role and Effects of Psychological, Emotional, Social, and Cognitive Factors on the Macro Economy
- Browse content in F - International Economics
- Browse content in F0 - General
- F02 - International Economic Order and Integration
- Browse content in F1 - Trade
- F10 - General
- F11 - Neoclassical Models of Trade
- F12 - Models of Trade with Imperfect Competition and Scale Economies; Fragmentation
- F13 - Trade Policy; International Trade Organizations
- F14 - Empirical Studies of Trade
- F15 - Economic Integration
- F16 - Trade and Labor Market Interactions
- F17 - Trade Forecasting and Simulation
- F18 - Trade and Environment
- Browse content in F2 - International Factor Movements and International Business
- F21 - International Investment; Long-Term Capital Movements
- F22 - International Migration
- F23 - Multinational Firms; International Business
- F24 - Remittances
- Browse content in F3 - International Finance
- F30 - General
- F31 - Foreign Exchange
- F32 - Current Account Adjustment; Short-Term Capital Movements
- F33 - International Monetary Arrangements and Institutions
- F34 - International Lending and Debt Problems
- F35 - Foreign Aid
- F36 - Financial Aspects of Economic Integration
- F37 - International Finance Forecasting and Simulation: Models and Applications
- Browse content in F4 - Macroeconomic Aspects of International Trade and Finance
- F40 - General
- F41 - Open Economy Macroeconomics
- F42 - International Policy Coordination and Transmission
- F43 - Economic Growth of Open Economies
- F44 - International Business Cycles
- F45 - Macroeconomic Issues of Monetary Unions
- Browse content in F5 - International Relations, National Security, and International Political Economy
- F50 - General
- F51 - International Conflicts; Negotiations; Sanctions
- F52 - National Security; Economic Nationalism
- F53 - International Agreements and Observance; International Organizations
- F55 - International Institutional Arrangements
- F59 - Other
- Browse content in F6 - Economic Impacts of Globalization
- F62 - Macroeconomic Impacts
- F63 - Economic Development
- F64 - Environment
- Browse content in G - Financial Economics
- Browse content in G0 - General
- G01 - Financial Crises
- G02 - Behavioral Finance: Underlying Principles
- Browse content in G1 - General Financial Markets
- G10 - General
- G11 - Portfolio Choice; Investment Decisions
- G12 - Asset Pricing; Trading volume; Bond Interest Rates
- G14 - Information and Market Efficiency; Event Studies; Insider Trading
- G15 - International Financial Markets
- G18 - Government Policy and Regulation
- Browse content in G2 - Financial Institutions and Services
- G20 - General
- G21 - Banks; Depository Institutions; Micro Finance Institutions; Mortgages
- G22 - Insurance; Insurance Companies; Actuarial Studies
- G24 - Investment Banking; Venture Capital; Brokerage; Ratings and Ratings Agencies
- G28 - Government Policy and Regulation
- Browse content in G3 - Corporate Finance and Governance
- G32 - Financing Policy; Financial Risk and Risk Management; Capital and Ownership Structure; Value of Firms; Goodwill
- G33 - Bankruptcy; Liquidation
- G34 - Mergers; Acquisitions; Restructuring; Corporate Governance
- G35 - Payout Policy
- G38 - Government Policy and Regulation
- Browse content in H - Public Economics
- Browse content in H0 - General
- H00 - General
- Browse content in H1 - Structure and Scope of Government
- H10 - General
- H11 - Structure, Scope, and Performance of Government
- H12 - Crisis Management
- Browse content in H2 - Taxation, Subsidies, and Revenue
- H20 - General
- H21 - Efficiency; Optimal Taxation
- H22 - Incidence
- H23 - Externalities; Redistributive Effects; Environmental Taxes and Subsidies
- H24 - Personal Income and Other Nonbusiness Taxes and Subsidies; includes inheritance and gift taxes
- H25 - Business Taxes and Subsidies
- H26 - Tax Evasion and Avoidance
- Browse content in H3 - Fiscal Policies and Behavior of Economic Agents
- H30 - General
- H31 - Household
- Browse content in H4 - Publicly Provided Goods
- H40 - General
- H41 - Public Goods
- H42 - Publicly Provided Private Goods
- Browse content in H5 - National Government Expenditures and Related Policies
- H50 - General
- H51 - Government Expenditures and Health
- H52 - Government Expenditures and Education
- H53 - Government Expenditures and Welfare Programs
- H54 - Infrastructures; Other Public Investment and Capital Stock
- H55 - Social Security and Public Pensions
- H56 - National Security and War
- Browse content in H6 - National Budget, Deficit, and Debt
- H60 - General
- H61 - Budget; Budget Systems
- H62 - Deficit; Surplus
- H63 - Debt; Debt Management; Sovereign Debt
- Browse content in H7 - State and Local Government; Intergovernmental Relations
- H70 - General
- H71 - State and Local Taxation, Subsidies, and Revenue
- H72 - State and Local Budget and Expenditures
- H75 - State and Local Government: Health; Education; Welfare; Public Pensions
- H76 - State and Local Government: Other Expenditure Categories
- H77 - Intergovernmental Relations; Federalism; Secession
- Browse content in H8 - Miscellaneous Issues
- H83 - Public Administration; Public Sector Accounting and Audits
- H84 - Disaster Aid
- H87 - International Fiscal Issues; International Public Goods
- Browse content in I - Health, Education, and Welfare
- Browse content in I0 - General
- I00 - General
- Browse content in I1 - Health
- I10 - General
- I12 - Health Behavior
- I14 - Health and Inequality
- I15 - Health and Economic Development
- I18 - Government Policy; Regulation; Public Health
- I19 - Other
- Browse content in I2 - Education and Research Institutions
- I20 - General
- I21 - Analysis of Education
- I22 - Educational Finance; Financial Aid
- I23 - Higher Education; Research Institutions
- I24 - Education and Inequality
- I25 - Education and Economic Development
- I26 - Returns to Education
- I28 - Government Policy
- I29 - Other
- Browse content in I3 - Welfare, Well-Being, and Poverty
- I30 - General
- I31 - General Welfare
- I32 - Measurement and Analysis of Poverty
- I38 - Government Policy; Provision and Effects of Welfare Programs
- Browse content in J - Labor and Demographic Economics
- Browse content in J0 - General
- J00 - General
- J01 - Labor Economics: General
- J08 - Labor Economics Policies
- Browse content in J1 - Demographic Economics
- J10 - General
- J11 - Demographic Trends, Macroeconomic Effects, and Forecasts
- J12 - Marriage; Marital Dissolution; Family Structure; Domestic Abuse
- J13 - Fertility; Family Planning; Child Care; Children; Youth
- J14 - Economics of the Elderly; Economics of the Handicapped; Non-Labor Market Discrimination
- J15 - Economics of Minorities, Races, Indigenous Peoples, and Immigrants; Non-labor Discrimination
- J16 - Economics of Gender; Non-labor Discrimination
- J17 - Value of Life; Forgone Income
- J18 - Public Policy
- Browse content in J2 - Demand and Supply of Labor
- J20 - General
- J21 - Labor Force and Employment, Size, and Structure
- J22 - Time Allocation and Labor Supply
- J23 - Labor Demand
- J24 - Human Capital; Skills; Occupational Choice; Labor Productivity
- J26 - Retirement; Retirement Policies
- J28 - Safety; Job Satisfaction; Related Public Policy
- Browse content in J3 - Wages, Compensation, and Labor Costs
- J30 - General
- J31 - Wage Level and Structure; Wage Differentials
- J32 - Nonwage Labor Costs and Benefits; Retirement Plans; Private Pensions
- J33 - Compensation Packages; Payment Methods
- J38 - Public Policy
- Browse content in J4 - Particular Labor Markets
- J41 - Labor Contracts
- J42 - Monopsony; Segmented Labor Markets
- J45 - Public Sector Labor Markets
- J46 - Informal Labor Markets
- J48 - Public Policy
- Browse content in J5 - Labor-Management Relations, Trade Unions, and Collective Bargaining
- J50 - General
- J51 - Trade Unions: Objectives, Structure, and Effects
- J52 - Dispute Resolution: Strikes, Arbitration, and Mediation; Collective Bargaining
- J53 - Labor-Management Relations; Industrial Jurisprudence
- J54 - Producer Cooperatives; Labor Managed Firms; Employee Ownership
- J58 - Public Policy
- Browse content in J6 - Mobility, Unemployment, Vacancies, and Immigrant Workers
- J60 - General
- J61 - Geographic Labor Mobility; Immigrant Workers
- J62 - Job, Occupational, and Intergenerational Mobility
- J63 - Turnover; Vacancies; Layoffs
- J64 - Unemployment: Models, Duration, Incidence, and Job Search
- J65 - Unemployment Insurance; Severance Pay; Plant Closings
- J68 - Public Policy
- Browse content in J7 - Labor Discrimination
- J71 - Discrimination
- Browse content in J8 - Labor Standards: National and International
- J81 - Working Conditions
- J88 - Public Policy
- Browse content in K - Law and Economics
- Browse content in K0 - General
- K00 - General
- Browse content in K1 - Basic Areas of Law
- K11 - Property Law
- K12 - Contract Law
- K13 - Tort Law and Product Liability; Forensic Economics
- K14 - Criminal Law
- K16 - Election Law
- Browse content in K3 - Other Substantive Areas of Law
- K31 - Labor Law
- K32 - Environmental, Health, and Safety Law
- K34 - Tax Law
- K37 - Immigration Law
- Browse content in K4 - Legal Procedure, the Legal System, and Illegal Behavior
- K41 - Litigation Process
- K42 - Illegal Behavior and the Enforcement of Law
- K49 - Other
- Browse content in L - Industrial Organization
- Browse content in L0 - General
- L00 - General
- Browse content in L1 - Market Structure, Firm Strategy, and Market Performance
- L10 - General
- L11 - Production, Pricing, and Market Structure; Size Distribution of Firms
- L12 - Monopoly; Monopolization Strategies
- L13 - Oligopoly and Other Imperfect Markets
- L14 - Transactional Relationships; Contracts and Reputation; Networks
- L16 - Industrial Organization and Macroeconomics: Industrial Structure and Structural Change; Industrial Price Indices
- Browse content in L2 - Firm Objectives, Organization, and Behavior
- L20 - General
- L21 - Business Objectives of the Firm
- L22 - Firm Organization and Market Structure
- L23 - Organization of Production
- L24 - Contracting Out; Joint Ventures; Technology Licensing
- L25 - Firm Performance: Size, Diversification, and Scope
- L26 - Entrepreneurship
- L29 - Other
- Browse content in L3 - Nonprofit Organizations and Public Enterprise
- L30 - General
- L31 - Nonprofit Institutions; NGOs; Social Entrepreneurship
- L32 - Public Enterprises; Public-Private Enterprises
- L33 - Comparison of Public and Private Enterprises and Nonprofit Institutions; Privatization; Contracting Out
- Browse content in L4 - Antitrust Issues and Policies
- L40 - General
- L41 - Monopolization; Horizontal Anticompetitive Practices
- L43 - Legal Monopolies and Regulation or Deregulation
- Browse content in L5 - Regulation and Industrial Policy
- L50 - General
- L51 - Economics of Regulation
- L52 - Industrial Policy; Sectoral Planning Methods
- L53 - Enterprise Policy
- Browse content in L6 - Industry Studies: Manufacturing
- L60 - General
- L66 - Food; Beverages; Cosmetics; Tobacco; Wine and Spirits
- Browse content in L7 - Industry Studies: Primary Products and Construction
- L71 - Mining, Extraction, and Refining: Hydrocarbon Fuels
- L78 - Government Policy
- Browse content in L8 - Industry Studies: Services
- L81 - Retail and Wholesale Trade; e-Commerce
- L83 - Sports; Gambling; Recreation; Tourism
- L86 - Information and Internet Services; Computer Software
- Browse content in L9 - Industry Studies: Transportation and Utilities
- L94 - Electric Utilities
- L98 - Government Policy
- Browse content in M - Business Administration and Business Economics; Marketing; Accounting; Personnel Economics
- Browse content in M1 - Business Administration
- M12 - Personnel Management; Executives; Executive Compensation
- M14 - Corporate Culture; Social Responsibility
- M16 - International Business Administration
- Browse content in M3 - Marketing and Advertising
- M31 - Marketing
- Browse content in M5 - Personnel Economics
- M50 - General
- M51 - Firm Employment Decisions; Promotions
- M52 - Compensation and Compensation Methods and Their Effects
- M53 - Training
- M54 - Labor Management
- M55 - Labor Contracting Devices
- Browse content in N - Economic History
- Browse content in N1 - Macroeconomics and Monetary Economics; Industrial Structure; Growth; Fluctuations
- N10 - General, International, or Comparative
- N11 - U.S.; Canada: Pre-1913
- N12 - U.S.; Canada: 1913-
- N13 - Europe: Pre-1913
- N15 - Asia including Middle East
- Browse content in N2 - Financial Markets and Institutions
- N20 - General, International, or Comparative
- N24 - Europe: 1913-
- N25 - Asia including Middle East
- Browse content in N3 - Labor and Consumers, Demography, Education, Health, Welfare, Income, Wealth, Religion, and Philanthropy
- N31 - U.S.; Canada: Pre-1913
- N33 - Europe: Pre-1913
- N34 - Europe: 1913-
- Browse content in N4 - Government, War, Law, International Relations, and Regulation
- N40 - General, International, or Comparative
- N45 - Asia including Middle East
- N47 - Africa; Oceania
- Browse content in N5 - Agriculture, Natural Resources, Environment, and Extractive Industries
- N50 - General, International, or Comparative
- N53 - Europe: Pre-1913
- N57 - Africa; Oceania
- Browse content in N7 - Transport, Trade, Energy, Technology, and Other Services
- N70 - General, International, or Comparative
- N72 - U.S.; Canada: 1913-
- Browse content in N9 - Regional and Urban History
- N97 - Africa; Oceania
- Browse content in O - Economic Development, Innovation, Technological Change, and Growth
- Browse content in O1 - Economic Development
- O10 - General
- O11 - Macroeconomic Analyses of Economic Development
- O12 - Microeconomic Analyses of Economic Development
- O13 - Agriculture; Natural Resources; Energy; Environment; Other Primary Products
- O14 - Industrialization; Manufacturing and Service Industries; Choice of Technology
- O15 - Human Resources; Human Development; Income Distribution; Migration
- O16 - Financial Markets; Saving and Capital Investment; Corporate Finance and Governance
- O17 - Formal and Informal Sectors; Shadow Economy; Institutional Arrangements
- O18 - Urban, Rural, Regional, and Transportation Analysis; Housing; Infrastructure
- O19 - International Linkages to Development; Role of International Organizations
- Browse content in O2 - Development Planning and Policy
- O22 - Project Analysis
- O23 - Fiscal and Monetary Policy in Development
- O24 - Trade Policy; Factor Movement Policy; Foreign Exchange Policy
- O25 - Industrial Policy
- Browse content in O3 - Innovation; Research and Development; Technological Change; Intellectual Property Rights
- O30 - General
- O31 - Innovation and Invention: Processes and Incentives
- O32 - Management of Technological Innovation and R&D
- O33 - Technological Change: Choices and Consequences; Diffusion Processes
- O34 - Intellectual Property and Intellectual Capital
- O38 - Government Policy
- O39 - Other
- Browse content in O4 - Economic Growth and Aggregate Productivity
- O40 - General
- O41 - One, Two, and Multisector Growth Models
- O42 - Monetary Growth Models
- O43 - Institutions and Growth
- O47 - Empirical Studies of Economic Growth; Aggregate Productivity; Cross-Country Output Convergence
- O49 - Other
- Browse content in O5 - Economywide Country Studies
- O50 - General
- O52 - Europe
- O53 - Asia including Middle East
- O55 - Africa
- O57 - Comparative Studies of Countries
- Browse content in P - Economic Systems
- Browse content in P1 - Capitalist Systems
- P10 - General
- P13 - Cooperative Enterprises
- P16 - Political Economy
- P17 - Performance and Prospects
- Browse content in P2 - Socialist Systems and Transitional Economies
- P20 - General
- P26 - Political Economy; Property Rights
- Browse content in P3 - Socialist Institutions and Their Transitions
- P31 - Socialist Enterprises and Their Transitions
- Browse content in P4 - Other Economic Systems
- P48 - Political Economy; Legal Institutions; Property Rights; Natural Resources; Energy; Environment; Regional Studies
- Browse content in P5 - Comparative Economic Systems
- P50 - General
- Browse content in Q - Agricultural and Natural Resource Economics; Environmental and Ecological Economics
- Browse content in Q0 - General
- Q02 - Commodity Markets
- Browse content in Q1 - Agriculture
- Q11 - Aggregate Supply and Demand Analysis; Prices
- Q13 - Agricultural Markets and Marketing; Cooperatives; Agribusiness
- Q15 - Land Ownership and Tenure; Land Reform; Land Use; Irrigation; Agriculture and Environment
- Q16 - R&D; Agricultural Technology; Biofuels; Agricultural Extension Services
- Q17 - Agriculture in International Trade
- Q18 - Agricultural Policy; Food Policy
- Browse content in Q2 - Renewable Resources and Conservation
- Q20 - General
- Q22 - Fishery; Aquaculture
- Q23 - Forestry
- Q25 - Water
- Q26 - Recreational Aspects of Natural Resources
- Q29 - Other
- Browse content in Q3 - Nonrenewable Resources and Conservation
- Q30 - General
- Q32 - Exhaustible Resources and Economic Development
- Q33 - Resource Booms
- Q34 - Natural Resources and Domestic and International Conflicts
- Q38 - Government Policy
- Browse content in Q4 - Energy
- Q40 - General
- Q41 - Demand and Supply; Prices
- Q42 - Alternative Energy Sources
- Q43 - Energy and the Macroeconomy
- Q48 - Government Policy
- Browse content in Q5 - Environmental Economics
- Q50 - General
- Q51 - Valuation of Environmental Effects
- Q52 - Pollution Control Adoption Costs; Distributional Effects; Employment Effects
- Q53 - Air Pollution; Water Pollution; Noise; Hazardous Waste; Solid Waste; Recycling
- Q54 - Climate; Natural Disasters; Global Warming
- Q56 - Environment and Development; Environment and Trade; Sustainability; Environmental Accounts and Accounting; Environmental Equity; Population Growth
- Q58 - Government Policy
- Browse content in R - Urban, Rural, Regional, Real Estate, and Transportation Economics
- Browse content in R1 - General Regional Economics
- R10 - General
- R11 - Regional Economic Activity: Growth, Development, Environmental Issues, and Changes
- R15 - Econometric and Input-Output Models; Other Models
- Browse content in R2 - Household Analysis
- R23 - Regional Migration; Regional Labor Markets; Population; Neighborhood Characteristics
- R29 - Other
- Browse content in R4 - Transportation Economics
- R40 - General
- R41 - Transportation: Demand, Supply, and Congestion; Travel Time; Safety and Accidents; Transportation Noise
- Browse content in R5 - Regional Government Analysis
- R58 - Regional Development Planning and Policy
- Browse content in Z - Other Special Topics
- Browse content in Z1 - Cultural Economics; Economic Sociology; Economic Anthropology
- Z10 - General
- Z11 - Economics of the Arts and Literature
- Z12 - Religion
- Z13 - Economic Sociology; Economic Anthropology; Social and Economic Stratification
- Z19 - Other
- Browse content in Z2 - Sports Economics
- Z21 - Industry Studies
- Z22 - Labor Issues
- Z29 - Other
- Browse content in Z3 - Tourism Economics
- Z30 - General
- Advance articles
- Author Guidelines
- Submission Site
- Open Access
- About Oxford Economic Papers
- Editorial Board
- Advertising and Corporate Services
- Journals Career Network
- Self-Archiving Policy
- Dispatch Dates
- Terms and Conditions
- Journals on Oxford Academic
- Books on Oxford Academic


Article Contents
1. introduction, 2. on terrorism, 3. event data sets, 4. domestic and transnational terrorism: some data plots, 5. counterterrorism, 6. findings of the articles of the special issue, 7. concluding remarks, acknowledgements, terrorism and counterterrorism: an overview.
- Article contents
- Figures & tables
- Supplementary Data
Todd Sandler, Terrorism and counterterrorism: an overview, Oxford Economic Papers , Volume 67, Issue 1, January 2015, Pages 1–20, https://doi.org/10.1093/oep/gpu039
- Permissions Icon Permissions
This introduction sets the stage for the articles collected in this special issue of Oxford Economic Papers . It begins by introducing essential concepts including domestic terrorism, transnational terrorism, defensive actions, proactive countermeasures, and guerrilla warfare. Three terrorist event databases, used by seven of the articles, are briefly introduced. These data sets are then used to display some stylized facts about domestic and transnational terrorism during the past four decades. Next, some essential strategic distinctions are drawn between defensive and proactive measures in the case of transnational terrorism when multiple countries are confronted by a common terrorist group. These strategic concerns vanish for domestic terrorism as a central government is able to internalize potential externalities. Finally, the key findings of the articles in the special issue are highlighted in two tables.
Terrorism is the premeditated use or threat to use violence by individuals or subnational groups to obtain a political or social objective through the intimidation of a large audience beyond that of the immediate noncombatant victims ( Enders and Sandler, 2012 , p.4). The two essential ingredients of terrorism are its violence and its political or social motive. Terrorists tend to employ shockingly violent acts, such as beheadings, downing of commercial airlines, bombings in public markets, and armed attacks in public places, to intimidate an audience. Their unpredictable and horrific attacks are meant to make everyone feel at risk even though the true likelihood of falling victim to a terrorist incident is rather minuscule, roughly equivalent to that of drowning in one's bathtub ( Mueller, 2006 ). Terrorists seek to circumvent normal channels for political change by traumatizing the public with brutal acts so that governments feel compelled to either address terrorist demands or divert public funds into hardening potential targets. Terrorist campaigns are more prevalent in liberal democracies, where the government's legitimacy hinges on its ability to protect the lives and property of its citizens ( Eubank and Weinberg, 1994 ).
The four airplane hijackings on 11 September 2001 (9/11) are terrorist acts since the perpetrators were members of al-Qaida, a subnational terrorist group, bent on pressuring the USA to remove its troops from Saudi Arabia, which was al-Qaida's primary political goal at the time. These skyjackings intimidated a global audience, caused huge temporary losses to the major stock exchanges ( Chen and Siems, 2004 ), and created $80–90 billion in direct and indirect damages ( Kunreuther et al ., 2003 ). Even though stock exchanges recovered lost values in just over a month, the death of almost 3,000 people caused rich industrial countries to allocate more resources to counterterrorism, shook insurance markets, and made an indelible impression on virtually the entire world. Heinous terrorist incidents continue to capture headlines with recent newsworthy incidents involving al-Shabaab's armed attack on the Westgate Mall in Nairobi, Kenya, on 21 September 2013; Chechen separatists’ suicide bombings of a train station and a trolley in Volgograd, Russia, on 29 and 30 December 2013, respectively; and Boko Haram's kidnapping of more than 200 female students in Chibok, Nigeria, on 14–15 April 2014. These and countless other incidents since 9/11 indicate that the government must allocate resources in an effective and measured manner to counterterrorism activities so that terrorists cannot circumvent legitimate political processes or cause significant economic losses. These losses may involve reduced foreign direct investment ( Enders and Sandler, 1996 ; Abadie and Gardeazabal, 2008 ), lower economic growth ( Abadie and Gardeazabal, 2003 ; Eckstein and Tsiddon, 2004 ; Gaibulloev and Sandler, 2008 , 2011 ), less trade ( Nitsch and Schumacher, 2004 ), reduced tourism ( Enders et al ., 1992 ; Drakos and Kutan, 2003 ), or lost values of stock and bond indexes ( Kollias et al ., 2013 ). Economic impacts of terrorism are greatest in small terrorism-plagued countries and developing countries ( Keefer and Loayza, 2008 ; Sandler and Enders, 2008 ). Modern industrial economies can insulate themselves through judicious fiscal and monetary policy, rapid counterterrorism responses, and the transference of economic activities ( Enders and Sandler, 2012 ). The latter involves economic activities moving from terrorism-prone sectors and regions to safer areas, which advanced, diversified economies allow. Thus, economic activity may switch from the tourism sector to other sectors when the former is targeted. In Spain, economic investment switched from the Basque Country to other Spanish provinces because of Euskadi ta Askatasuna attacks ( Abadie and Gardeazabal, 2003 ).
Modern-day econometric methods—time series, panel, and discrete-choice models—lend themselves to the quantification of these economic losses as shown in this special issue by Choi (2015) , Egger and Gassebner (2015) , and Younas (2015) . Additionally, game-theoretic models can display counterterrorism interactions among terrorists and governments as in the contributions in this issue by Carter (2015) and Kaplan (2015) . In fact, game theory is an excellent tool to study interactions among targeted governments, between rival terrorist groups, between a terrorist group and its sponsoring state, and among the media, the terrorist group, and the public. 1
The purpose of this article is to provide the requisite background to the studies in this special issue of Oxford Economic Papers . This task requires a fuller discussion of the notion of terrorism and its two primary subdivisions—domestic and transnational terrorism—in Section 2. The three event data sets employed in empirical studies, including seven of the eight articles in this issue, are briefly presented in Section 3. In Section 4, two of these data sets are used to display some recent trends and aspects of domestic and transnational terrorism during the last four decades. Essential concepts of counterterrorism are then presented in Section 5, where proactive measures are distinguished from defensive actions. Key findings of the four terrorism and four counterterrorism articles contained in this special issue are highlighted in two summarizing tables in Section 6. Concluding remarks follow in Section 7.
I now return to the definition of terrorism, given at the outset of this article. Any definition of terrorism involves much debate ( Hoffman, 2006 ; Enders and Sandler, 2012 ). The research community is converging to a consensus based on an operational definition on which to construct event data sets to test theoretical propositions. The article puts forward a definition that is consistent with that used by the main event data sets and relied on by researchers. Also, this definition possesses the main ingredients that are agreed on by economists, political scientists, and political economists.
The three stakeholders in this definition are the perpetrators, the victims, and the audience. By limiting terrorism to subnational agents including individuals or a ‘lone wolf’, my definition rules out state terror in which a government terrorizes its own people. The definition, however, does not rule out state-sponsored terrorism where a government clandestinely assists a terrorist group through various means, including supplying weapons, safe haven, intelligence, training, funding, or safe passage ( Mickolus, 1989 ; Bapat, 2006 ). There was a lot of state sponsorship of terrorism during the final decade of the Cold War with groups such as the Abu Nidal Organization serving as a terrorist group for hire ( Hoffman, 2006 ). 2 The most controversial element of my definition is the victim, since some definitions exclude combatants, so that attacks against an occupying army, such as US forces in Iraq or Afghanistan, are not viewed as terrorism. Generally, an attack against peacekeepers, such as the 23 October 1983 suicide bombing of the US Marines barracks at Beirut International Airport, is considered an act of terrorism. The barracks’ bombing had the political objective of removing peacekeepers from Lebanon, which happened in February 1984. Attacks against US soldiers and their dependents stationed in Germany constitute terrorist incidents, because these targeted individuals were noncombatants when attacked. ‘Audience’ refers to the collective that terrorists seek to intimidate through their wanton brutality. With sufficient and sustained intimidation, the audience will apply pressures on the besieged government to concede to the terrorist group's political demands or alternatively to take decisive action to annihilate the group. 3 In the latter case, the Italian authorities dismantled the Italian Red Brigades in the 1980s.
There are some crucial distinctions to draw between terrorism and related concepts. For instance, there is the distinction between terrorism and crime. A kidnapping for ransom is a criminal act of extortion when the kidnappers are not pursuing or financing a political agenda. If a political motive is tied to the kidnapping, then it is a terrorist incident even with ransom demands being made. The hijacking of a commercial airliner by a deranged person is a crime but not terrorism. In the absence of a political motive, an armed attack by a student on fellow students or teachers is a criminal action. Next consider an insurrection, which ‘is a politically based uprising intended to overthrow the established system of governance and to bring about a redistribution of income’ ( Sandler and Hartley, 1995 , p. 307). Leaders of insurrections recruit from the peasantry and general population in the hopes of challenging the government's hold on power ( Grossman, 1991 ). Successful rebel operations can generate new recruits and may ideally cause the government to impose draconian measures on its citizens, which subsequently create more support for the insurgency. If a tipping point is attained, then the government may be sufficiently challenged to lose its power to the rebels.
In distinction to insurrections, guerrilla warfare generally involves a band of rebel forces (e.g., the Revolutionary Armed Forces of Colombia [FARC], Abu Sayyaf in the Philippines, or Shining Path in Peru) that controls a sector of the country, from which to dispatch its operatives to confront government forces. Some guerrilla wars take place in urban centers. In contrast to most terrorist groups, guerrilla groups are larger in number and organized like a military force. Some guerrilla groups engage in terrorist acts, such as the three just-mentioned groups, to raise funds to secure their operations and pursue their political aims. For example, FARC kidnaps government officials and others for ransoms. Unlike an insurrection, guerrilla groups are not bent on overthrowing the government or engaging in propaganda to gain popular support ( Hoffman, 2006 ). Shining Path and FARC apply threats and harsh measures to gain the compliance of the people in the territory that they control. Guerrilla groups rely on surprise and cover to harass numerically superior government forces. Terrorism is a tactic employed by both insurrections and guerrilla movements. As a consequence, many guerrilla groups are listed as terrorist groups despite their control of territory. Often, countries with jungle cover or mountainous terrain provide remote areas where guerrillas can conduct training and operations. In this special issue, Carter (2015) is interested in the interaction between a guerrilla group and the government, as the former chooses between terrorism and the control of territory and the latter chooses between defensive counterterrorism actions and proactive military responses to influence the group's decision.
2.1 Domestic versus transnational terrorism
Domestic terrorism is homegrown and home-directed, and represents the most common form of terrorism. For domestic acts of terrorism, the perpetrators, victims, and audience hail from the venue country, where the attack takes place. Domestic terrorist incidents include Timothy McVeigh's bombing of the Alfred P. Murrah Federal Building in Oklahoma City on 19 April 1995 or Eric Rudolph's anti-abortionist bombing of Centennial Olympic Park in Atlanta, Georgia, on 27 July 1996. Civil wars often involve numerous domestic terrorist attacks before and during the conflict by the adversaries ( Findley and Young, 2012 ). 4 These terrorist acts are more apt to be domestic when an intervention by a third party from outside the country is not involved. Boko Haram's kidnapping of more than 200 female students is a domestic terrorist incident, which involves victims and perpetrators from the venue country of Nigeria. Boko Haram is an Islamic jihadist terrorist group that controls territory in the northeast portion of Nigeria. Given the country's limited military capabilities, its government sought some assistance from the USA in terms of military advisors and intelligence in addressing the significant threat that Boko Haram poses. At times, Boko Haram crosses into Chad. If one or more of the schoolgirls are moved into a neighboring country, then the kidnapping becomes a transnational terrorist incident. In general, poor countries may request foreign assistance if they cannot properly confront an indigenous terrorist group that may attack at home or abroad ( Azam and Thelen, 2010 ; Fleck and Kilby, 2010 ; Bandyopadhyay et al ., 2011 , 2014 ; Young and Findley, 2011 ).
Terrorism is transnational when an incident in the venue country concerns perpetrators or victims from another country. If a terrorist attack in the UK is perpetrated by terrorists from Yemen, then the incident is one of transnational terrorism. When a terrorist attack in France harms Dutch citizens, the attack is transnational. If one or more victims or perpetrators are not citizens of the venue country, then the terrorist attack is transnational. The kidnapping in January 2002 and subsequent murder of US reporter Daniel Pearl in Pakistan is classified as a transnational terrorist incident. The same is true of the near-simultaneous bombings of the US embassies in Kenya and Tanzania on 7 August 1998. Terrorist attacks against another country's embassy, even when perpetrated by citizens of the venue country, are transnational terrorist events because an embassy's grounds represent foreign soil. Similarly, terrorist attacks against international organizations’ personnel or property are considered to be transnational terrorist acts. An important transnational terrorist incident is the August 2006 plot to use liquid explosives to blow up 10 or more transatlantic flights departing the UK for the USA and Canada. A skyjacking originating in one country that is diverted to another country for political purposes is a transnational terrorist event. If a politically motivated hijacked plane has citizens from more than one country, the event is transnational terrorism even if the flight is domestic and ends in the country of origin. On 9/11, the four skyjackings are transnational terrorist acts since the victims were citizens from upward of 80 nations and the perpetrators were foreigners. The kidnapping of US journalist James Foley in Syria on 22 November 2012 and his beheading on 19 August 2014 is a transnational terrorist act. The victim was American, whereas the murderer is allegedly a British citizen from the Islamic State in Iraq and Syria (ISIS), also known as Islamic State (IS).
Transnational terrorist incidents frequently imply transnational externalities—for example, perpetrators from one country impose uncompensated costs on the victims of another country. If a country provides safe haven to a transnational terrorist group that attacks other countries’ interests, then transnational externalities ensue. 5 The Taliban in Afghanistan had given safe haven to Osama bin Laden's al-Qaida, which planned and executed the events of 9/11. When the Taliban would not surrender bin Laden to the USA following 9/11, the USA led an invasion of Afghanistan on 7 October 2001 ( Enders and Sandler, 2012 ). In this extreme case, the transnational externality resulted in a military invasion with the intent to defeat the Taliban and al-Qaida. Transnational externalities also arise from counterterrorism policies of targeted countries, which result in inefficient levels of these policies ( Sandler and Lapan, 1988 ; Sandler and Siqueira, 2006 ; Bueno de Mesquita, 2007 ). Actions by one targeted country to secure its borders and ports of entry may merely transfer the attack abroad, where borders are more porous (see Section 5). Since 9/11, few transnational terrorist incidents occur on US soil but 35% to 40% of such incidents involve US people or property in other countries ( Enders and Sandler, 2006 , 2012 ).
2.2 Some historical considerations of transnational terrorism
Hoffman ( 2006 , pp.63–5) traces the modern era of transnational terrorism to the 22 July 1968 hijacking of an Israeli El Al flight en route from Rome to Athens by three armed members of the Popular Front for the Liberation of Palestine (PFLP) terrorist group. This skyjacking was motivated by the intention of the PFLP terrorist to trade its hostages for Palestinian prisoners held by Israel. This event is noteworthy for a number of reasons. First, through its protracted 40-day negotiations, the Israelis were forced to negotiate with the Palestinian terrorists, which the Israelis had hitherto vowed they would never do ( Hoffman, 1998 , p.68). Second, the media coverage demonstrated to terrorists worldwide that such incidents could garner worldwide attention for their cause. Not surprisingly, transnational terrorist attacks increased greatly in numbers during the years following this incident (see the figures in Section 4). Third, there was evidence of state sponsorship after the diverted plane landed in Algiers as Algerian forces secured the hostages and held some Israeli hostages until 1 September 1968 when a deal was concluded ( Mickolus, 1980 , pp.93–4). Fourth, Israel eventually traded 16 Arab prisoners from the 1967 Arab-Israeli War for the remaining Israeli hostages. This trade showed terrorists that hostage taking could yield significant concessions.
Transnational terrorist groups were primarily nationalists/separatists or leftists (socialists) during the late 1960s until the late 1980s ( Rapoport, 2004 ). Even the Palestinian terrorists were secular until the end of the 1980s with the rise of Hamas, Palestinian Islamic Jihad, and other groups. After the mid-1990s, the religious fundamentalists came to dominate and increased the carnage ( Enders and Sandler, 2000 ; Gaibulloev and Sandler, 2014 ). The phenomenon of religious-based transnational terrorism is not novel and can be traced back to the Sicarii or Zealots, a Jewish sect that conducted a terror campaign against the Romans and their Jewish collaborators in Judea from CE 48 to 73 ( Rapoport, 1984 ; Bloom, 2005 ). Sicarii terrorists engaged in daytime assassinations in public places that typically resulted in the death of the assassin. As such, their dagger attacks were an early form of suicide terrorism, since the perpetrator had little chance of escape. 6 From 1090 to 1256, the Islamic Assassins opposed Sunni rule in Persia and Syria, with the intent to set up their own community and state of believers in the region ( Bloom, 2005 ). Although the Assassins’ terrorist campaign was on a much smaller scale, their goal was similar to that of ISIS. Like the Sicarii, the Assassins relied on politically motivated assassinations, performed with a dagger. Perpetrators usually sacrificed their own lives by making no efforts to escape after the deed.
In the beginning of the 1980s, the first terrorist event data set—International Terrorism: Attributes of Terrorist Events (ITERATE)—was made available to researchers. ITERATE only includes transnational terrorist attacks. Coverage starts in 1968, the beginning of the modern era of transnational terrorism, and runs until the end of 2012, with annual updates in August ( Mickolus et al ., 2013 ). ITERATE codes many variables—for example, incident date, country start location, country end location, attack type, target entity, terrorist group, perpetrators’ nationalities, number of deaths, number of injuries, victims’ nationalities, logistical outcome, US victims, state sponsorship, and scene of attack—in its Common File of over 40 variables. In addition, there is a Fate File indicating the fate of the terrorists—for example, the number of terrorists captured, the number of terrorists sentenced, and their length of incarceration. There is also a Hostage File, which has invaluable observations used by researchers to analyze logistical and negotiation success of hostage taking ( Santifort and Sandler, 2013 ). If an attack is completed as planned, then it is a logistical success. For hostage missions, securing one or more hostages is deemed a logistical success. The Hostage File of ITERATE is currently updated through 2010. Finally, there is a Skyjacking file with additional observations, and variables on skyjacking missions such as the duration of the incidents, airline involved, and negotiation strategies used. ITERATE, like the other event data sets, relies on the news media—print, broadcast, and digital—for the observations of its variables.
An initial focus of empirical studies was on transnational terrorism because ITERATE was the most extensive data set available throughout the 1980s and 1990s. Its lengthy series of daily data were ideal for time-series studies, which dominated the research landscape except for a few survival studies, the first being Atkinson et al .'s (1987) study of the duration of hostage-taking incidents. Today, panel studies are prevalent including those in this special issue— Berrebi and Ostwald (2015) , Choi (2015) , Egger and Gassebner (2015) , Gries et al . (2015) , and Younas (2015) .
Another competing event data set, modeled after ITERATE, is the RAND (2012) data set, which currently codes incidents for 1968–2009 and is not being updated. Gaibulloev (2015) uses the RAND event data in conjunction with Jones and Libicki's (2008) classification of terrorist groups’ ideologies in his study of groups’ location decisions. For 1968–97, RAND event data only include transnational terrorist attacks; after 1998, RAND data distinguish between transnational and domestic terrorist attacks in a manner consistent with my early definitions. Compared to ITERATE, RAND data code fewer variables and, for transnational terrorist incidents, have more limited coverage than ITERATE as demonstrated by Enders (2007) .
The third event data set, germane to this special issue, is that of the Global Terrorism Database (GTD), which records both domestic and transnational terrorist incidents ( La Free and Dugan, 2007 ; National Consortium for the Study of Terrorism and Response to Terrorism, 2013 ). Although GTD recorded both kinds of incidents, until 2013 it did not distinguish between the two kinds of incidents. Enders et al . (2011) devised a five-step procedure for distinguishing between domestic and transnational terrorist incidents in GTD for 1970–2007 and made their breakdown available to researchers. This division is now applied to 2008–2012 (see Enders et al ., 2014 ). A breakdown of terrorism into its two components is essential because the two types of terrorism may affect economic variables and counterterrorism differently—for example, economic growth or foreign direct investment is more influenced by transnational terrorism ( Gaibulloev and Sandler, 2008 ). Moreover, the influence of other variables on domestic and transnational terrorism may differ ( Sandler, 2014 ; Choi, 2015 ). The Enders et al . (2011) procedure does a much better job in distinguishing between the two types of events than recent GTD efforts, based on the authors’ method without attribution. GTD has tens of thousands of unclassified incidents compared to Enders et al . (2011) .
There are some things to note about GTD. First, it has changed its coding conventions a few times, most recently for the 2012 data. Coding was also changed after the National Consortium for the Study of Terrorism and Responses to Terrorism (2013) , based at the University of Maryland, took charge of the data around 2005. As shown by Enders et al . (2011) , there are periods of undercounting and overcounting of incidents, which can be addressed by these authors’ calibration methods. Second, GTD data for 1993 are very incomplete because in an office move by Pinkerton, which originated the database, the box containing 1993 fell off of the truck! Third, perpetrators’ nationalities are not identified. Fourth, GTD does not contain any hostage negotiation variables, making the study of hostage-taking incidents impossible with this database. Fifth, GTD coverage of some kinds of domestic incidents, such as kidnappings, is virtually nonexistent prior to the late 1990s ( Enders et al ., 2011 ).
Key aspects of the articles for the special issue
Notes: *denotes that Enders et al . (2011) breakdown of GTD into domestic and transnational terrorist incidents was used. ITERATE = International Terrorism: Attributes of Terrorist Events; GTD = Global Terrorism Database.
A variety of empirical techniques are applied by the six empirical articles. In his cross-sectional study of the location choice of terrorist groups, Gaibulloev (2015) relies on a conditional logit estimator. To account for the count nature of the dependent terrorism variable, Choi (2015) and Gries et al . (2015) apply a negative binomial panel estimator. Endogeneity between the dependent variable and one or more independent variables is addressed in various ways: the Berrebi and Ostwald (2015) article employs instrumental variables (IV), consisting of lagged domestic terrorist attacks in neighboring countries, whereas the Younas (2015) article uses system generalized method of moments (SGMM) to augment his feasible generalized least squares (FGLS) estimates. The Gries et al . (2015) article addresses endogeneity with lagged values of the independent variables and also SGMM estimates. The Choi (2015) article primarily uses lagged independent variables to partly handle the endogeneity concern.
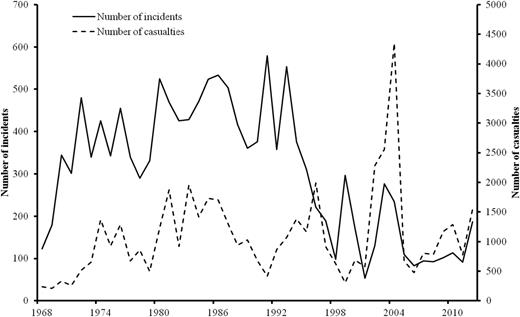
ITERATE transnational terrorist incidents and total casualties per year, 1968–2012
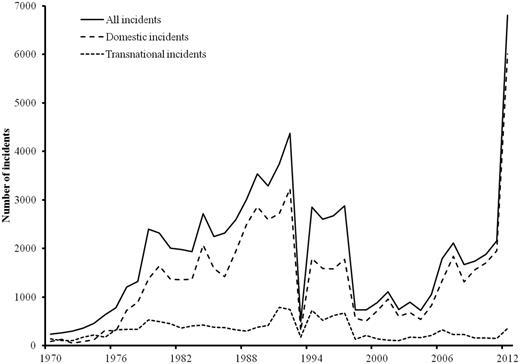
GTD terrorist incidents per year, 1970–2012
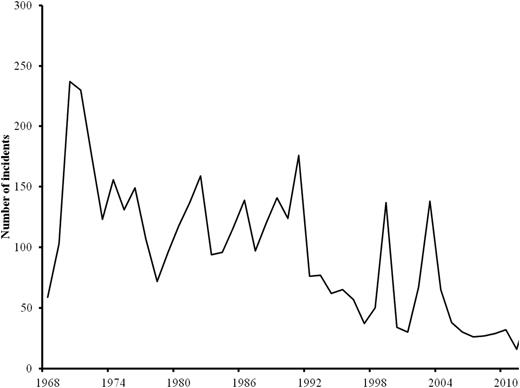
ITERATE attacks against US interests per year, 1968–2012
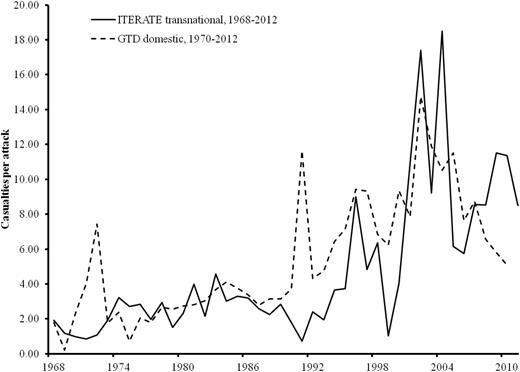
Annual number of casualties per attack
This special issue contains articles on terrorism and counterterrorism. Given my discussion of terrorism and its concepts, it is now instructive to introduce some basic concepts and concerns that are associated with the practice of counterterrorism.
Quite simply, counterterrorism corresponds to actions to ameliorate the threat and consequences of terrorism. These actions can be taken by governments, military alliances, international organizations (e.g., INTERPOL), private corporations, or private citizens. Counterterrorism comes in two basic varieties: defensive and proactive measures.
Defensive countermeasures protect potential targets by making attacks more costly for terrorists or reducing their likelihood of success. When, however, successful terrorist attacks ensue, defensive actions also serve to limit the resulting losses to the target. Defensive measures have generally been reactive, instituted after some successful or innovative terrorist attacks. In the USA, airline passengers are now required to remove their shoes when being screened, following the innovative, but fortunately unsuccessful, attempt by Richard Reid to bring down American Airlines flight 63 en route from Paris to Miami on 22 December 2001 with explosives hidden in his shoes. Before the installation of metal detectors to screen passengers at US airports on 5 January 1973, there were on average over 25 skyjackings each year in the USA ( Enders et al ., 1990 ). After their installation, attempted US skyjackings dropped to fewer than four a year. The success of these metal detectors in US airports led to their installation worldwide over the next six months. Following the downing of Pan Am flight 103 over Lockerbie, Scotland, on 21 December 1988 and the downing of UTA flight 772 over Niger on 19 September 1989, bomb-detecting devices were used to screen checked luggage. Defensive or protective counterterror actions may involve more than technological barriers. Other instances of defensive measures include target hardening, such as defensive perimeters around government buildings or embassies, or guards at key points of a country's infrastructure. Defensive measures can also take the form of issuing terrorism alerts, enacting stiffer penalties for terrorism offenses, enhancing first-responder capabilities, and stockpiling antibiotics and antidotes for biological and chemical terrorist attacks. This list of defensive actions is by no means exhaustive.
By contrast, proactive measures are offensive as a targeted government directly confronts the terrorist group or its supporters. Proactive measures may destroy terrorists’ resources (e.g., training camps), curb their finances, eliminate their safe havens, or kill and capture their members. In recent years, the Obama administration has relied on drone attacks to assassinate terrorist leaders and operatives. Proactive operations may assume myriad other forms, including a retaliatory raid against a state sponsor that provides resources, training, sanctuary, logistical support, or intelligence to a terrorist group. On 15 April 1986, the USA launched a retaliatory bombing raid on targets in Libya for its alleged support in the terrorist bombing of the La Belle discotheque in West Berlin on 4 April 1986, where 3 died and 231 were wounded, including 62 Americans ( Mickolus et al ., 1989 , vol. 2, pp.365–7). Another proactive measure takes the form of a preemptive attack against a terrorist group or a harboring country, such as the US-led invasion of Afghanistan four weeks after 9/11. A preemptive strike differs from a retaliatory raid because the former is more sustained and meant to severely compromise the capabilities of the terrorists to conduct future missions. Such strikes or raids concern transnational terrorism where a targeted country confronts the foreign threat. Other proactive measures include infiltrating terrorist groups, engaging in military action, conducting propaganda campaigns against the terrorists, and gathering intelligence to foil terror plots ( Kaplan, 2015 ). ‘Military action’ generally refers to operations by the host government against a resident terrorist group as in Carter (2015) . Actions that improve the economy, which in turn reduces grievances, can also be proactive ( Choi, 2015 ). Younas (2015) demonstrates empirically that increased globalization of a country's economy may also be proactive by limiting harmful and therefore grievance-causing effects of terrorism on economic growth. In this special issue, the four counterterrorism articles primary address aspects of proactive measures. Only Carter (2015) considers both defensive and proactive counterterrorism responses.
The game-theoretic literature on counterterrorism draws some fascinating strategic contrasts between defensive and proactive countermeasures. Suppose that two or more countries are confronted by the same Islamic jihadist terrorist group—for example, al-Qaida in the Arabian Peninsula (AQAP). In this transnational terrorism scenario, each at-risk country is inclined to work at cross-purposes by engaging in a defensive race in the hopes of transferring the terrorist attacks to other targeted countries ( Sandler and Lapan, 1988 ; Arce and Sandler, 2005 ). In the process, the countries engage in too much defense since the negative transference externality is not internalized. The only check on this adverse ‘defense race’ stems from the countries having large interests abroad, which may be hit when attacks are transferred abroad—recall Fig. 3 and attacks against US interests ( Bandyopadhyay and Sandler, 2011 ; Bandyopadhyay et al ., 2011 ).
Next consider proactive measures in these multicountry scenarios. Any country's actions to confront the common terrorist threat confer purely public (nonrival and nonexcludable) benefits to all potential target countries. As a result, there is too little proactive response as each country tries to free ride on the actions of other countries. Thus, defensive measures are strategic complements as one country's actions encourage those of other countries (i.e., reaction paths are upward-sloping), whereas proactive measures are strategic substitutes as one country's actions inhibit those of other countries (i.e., reaction paths are downward-sloping) ( Eaton, 2004 ; Sandler and Siqueira, 2006 ). Moreover, leadership can be shown to curb the defensive race, whereas leadership exacerbates the free-riding underprovision of offensive measures ( Sandler and Siqueira, 2006 ). Thus, there is no simple fix for these concerns among sovereign targeted nations.
For domestic terrorism, countries possess the proper incentives to choose defensive and proactive measures judiciously, because all associated costs and benefits are internalized ( Enders and Sandler, 2012 ). Thus, Kaplan's (2015) finding that the USA staffs about the right number of intelligence analysts to intercept terror plots is consistent with past game-theoretic findings regarding domestic counterterrorism optimality. Carter's (2015) article is also geared to domestic terrorism, whereas Choi (2015) and Younas (2015) may involve economic-based countermeasures for either type of terrorism.
Key findings of terrorism studies
Key findings of counterterrorism studies
This special issue contains many noteworthy advances in the study of terrorism. Gaibulloev (2015) is the first article to address terrorist groups’ base location choice; currently, the study of terrorist group survival is an active area of research. Berrebi and Ostwald (2015) is the initial study to examine the impact of terrorism on fertility. Younas (2015) and Choi (2015) refine the relationship between terrorism and growth; Egger and Gassebner (2015) show that terrorism has less of an effect on trade than conventionally believed. Kaplan (2015) investigates the social efficiency of intelligence staffing in intercepting terror plots. Carter's (2015) analysis is novel because the terrorist group must decide between terrorist attacks and holding territory in reaction to the government's countermeasures. The interface between terrorism and other forms of political violence is seldom studied. Finally, the Gries et al . (2015) study extends knowledge of the determinants of anti-American terrorist attacks, which comprise 35–40% of all transnational terrorism.
Terrorism remains an active research area in economics, political economy, and political science. Given the microeconomic and macroeconomic consequences of terrorism, its study is a fitting topic for a general economics journal such as Oxford Economic Papers . Following 9/11, industrial countries engaged in a huge reallocation of resources toward counterterrorism, whose efficacy can be best studied and understood with the theoretical and empirical tools drawn from economics.
The rise of ISIS and the considerable threat that its Western fighters pose for their home countries means that terrorism will remain a policy concern. AQAP's war on the USA and its allies is yet another terrorist threat. Just as Africa appears to be achieving sustained economic growth in select countries, significant terrorist challenges arise from Boko Haram and al-Shabaab in Nigeria and Kenya, respectively. Failed states—for example, Afghanistan, Iraq, Somalia, Syria, and Yemen—supply safe havens for terrorist groups that threaten Western interests. It is my hope that this special issue on terrorism and counterterrorism will stimulate further research in these two topics.
The present collection arises from a set of papers presented at the sixth conference on Terrorism and Counterterrorism Policy at the University of Texas, Dallas. Held between 21 May and 24 May 2014, this conference invited many leading contributors to the study of terrorism and counterterrorism. Past conferences resulted in special issues published in Economics &Politics (November 2009), Journal of Conflict Resolution (April 2010), Journal of Peace Research (May 2011), Public Choice (December 2011), and Southern Economic Journal (April 2013). While assuming full responsibility for any remaining shortcomings, this article has profited from comments from Anindya Banerjee, who also advised me on the special issue. Khusrav Gaibulloev read and commented on an earlier version. Finally, I thank all of this special issue's reviewers, most of whom are major contributors to the study of terrorism. These reviewers provided rigorous reviews in a timely fashion. All articles went through a careful and demanding prescreening process, followed by two rounds of reviews by two to three anonymous referees. I appreciate the understanding of those authors whose papers did not make it into the special issue.
On the game-theoretic literature on terrorism, see Bandyopadhyay and Sandler (2011) , Bandyopadhyay et al . ( 2011 , 2014 ), Sandler and Arce (2003) , Bueno de Mesquita (2005) , and Sandler and Siqueira (2009) .
The Abu Nidal Organization was headed by Sabri Khali al-Banna. Its notorious attacks included the simultaneous armed attacks on the Rome and Vienna airports on 27 December 1985, the armed attack on the Neve Shalom Synagogue in Istanbul on 6 September 1986, and the attempted hijacking of Pan Am flight 73 in Karachi, Pakistan, on 5 September 1986 ( Enders and Sandler, 2012 ). This group is credited with the first simultaneous terrorist attacks.
On alternative ways that terrorist groups end, see Carter (2012) , Gailbulloev and Sandler (2014) , and Phillips (2014a) .
On the relationship between civil wars and terrorism, see Sambanis (2008) .
How terrorist groups choose their home base is discussed in this special issue by Gaibulloev (2015) . On the definition of terrorist groups, see Phillips (2014b) .
In this special issue, Choi (2015) investigates suicide terrorism, which may be domestic or transnational in nature. Suicide terrorist attacks grew in numbers after 1988 ( Santifort-Jordan and Sandler, 2014 ).
Abadie A. Gardeazabal J. ( 2003 ) The economic cost of conflict: a case study of the Basque Country , American Economic Review , 93 , 113 – 32 .
Google Scholar
Abadie A. Gardeazabal J. ( 2008 ) Terrorism and the world economy , European Economic Review , 52 , 1 – 27 .
Arce D.G. Sandler T. ( 2005 ) Counterterrorism: a game-theoretic analysis , Journal of Conflict Resolution , 49 , 183 – 200 .
Atkinson S.E. Sandler T. Tschirhart J. ( 1987 ) Terrorism in a bargaining framework , Journal of Law and Economics , 30 , 1 – 21 .
Azam J.-P. Thelen V. ( 2010 ) Foreign aid versus military intervention in the war on terror , Journal of Conflict Resolution , 54 , 237 – 61 .
Bandyopadhyay S. Sandler T. ( 2011 ) The interplay between preemptive and defensive counterterrorism measures: a two-stage game , Economica , 78 , 546 – 64 .
Bandyopadhyay S. Sandler T. Younas J. ( 2011 ) Foreign aid as counterterrorism policy , Oxford Economic Papers , 63 , 423 – 47 .
Bandyopadhyay S. Sandler T. Younas J. ( 2014 ) Foreign direct investment, aid, and terrorism , Oxford Economic Papers , 66 , 25 – 50 .
Bapat N. A. ( 2006 ) State bargaining with transnational terrorist groups , International Studies Quarterly , 50 , 213 – 29 .
Berrebi C. Ostwald J. ( 2015 ) Terrorism and fertility: evidence for a causal inference of terrorism on fertility , Oxford Economic Papers , 67 , 63 – 82 .
Bloom M. ( 2005 ) Dying to Kill: The Allure of Suicide Terror , Columbia University Press , New York .
Google Preview
Bueno de Mesquita E. ( 2005 ) The quality of terror , American Journal of Political Science , 49 , 515 – 30 .
Bueno de Mesquita E. ( 2007 ) Politics and the suboptimal provision of counterterror , International Organization , 61 , 9 – 36 .
Carter D.B. ( 2012 ) A blessing or curse? State support for terrorist groups , International Organization , 66 , 129 – 51 .
Carter D.B. ( 2015 ) When terrorism is evidence of state success: securing the state against territorial groups , Oxford Economic Papers , 67 , 116 – 32 .
Chen A.H. Siems T.F. ( 2004 ) The effects of terrorism on global capital markets , European Journal of Political Economy , 20 , 249 – 66 .
Choi S.-W. ( 2015 ) Economic growth and terrorism: domestic, international, and suicide , Oxford Economic Papers , 67 , 157 – 81 .
Drakos K. Kutan A.M. ( 2003 ) Regional effects of terrorism on tourism in three Mediterranean countries , Journal of Conflict Resolution , 47 , 621 – 41 .
Eaton B.C. ( 2004 ) The elementary economics of social dilemmas , Canadian Journal of Economics , 37 , 805 – 29 .
Eckstein Z. Tsiddon D. ( 2004 ) Macroeconomic consequences of terror: theory and the case of Israel , Journal of Monetary Economics , 51 , 971 – 1002 .
Egger P. Gassebner M. ( 2015 ) International terrorism as a trade impediment? Oxford Economic Papers , 67 , 42 – 62 .
Enders W. ( 2007 ) Terrorism: an empirical analysis , in Sandler T. Hartley K. (eds) Handbook of Defense Economics: Defense in a Globalized World , North-Holland , Amsterdam .
Enders W. Hoover G.A. Sandler T. ( 2014 ) The changing nonlinear relationship between income and terrorism , Journal of Conflict Resolution , doi: 10.1177/0022002714535252 .
Enders W. Sandler T. ( 1996 ) Terrorism and foreign direct investment in Spain and Greece , Kyklos , 49 , 331 – 52 .
Enders W. Sandler T. ( 2000 ) Is transnational terrorism becoming more threatening? A time-series investigation , Journal of Conflict Resolution , 44 , 307 – 32 .
Enders W. Sandler T. ( 2006 ) Distribution of transnational terrorism among countries by income classes and geography after 9/11 , International Studies Quarterly , 50 , 367 – 93 .
Enders W. Sandler T. ( 2012 ) The Political Economy of Terrorism , 2nd edn., Cambridge University Press , New York .
Enders W. Sandler T. Cauley J. ( 1990 ) UN conventions, technology, and retaliation in the fight against terrorism: an econometric evaluation , Terrorism and Political Violence , 2 , 83 – 105 .
Enders W. Sandler T. Gaibulloev K. ( 2011 ) Domestic versus transnational terrorism: data, decomposition, and dynamics , Journal of Peace Research , 48 , 319 – 37 .
Enders W. Sandler T. Parise G.F. ( 1992 ) An econometric analysis of the impact of terrorism on tourism , Kyklos , 45 , 531 – 54 .
Eubank W.L. Weinberg L.B. ( 1994 ) Does democracy encourage terrorism? , Terrorism and Political Violence , 6 , 417 – 35 .
Faria J.R. ( 2003 ) Terror cycles , Studies in Nonlinear Dynamics and Econometrics , 7 , 1 – 11 .
Findley M.G. Young J.K. ( 2012 ) Terrorism and civil war: a spatial and temporal approach to a conceptual problem , Perspectives on Politics , 10 , 285 – 305 .
Fleck R.K. Kilby C. ( 2010 ) Changing aid regimes? US foreign aid from the Cold War to the war on terror , Journal of Development Economics , 91 , 185 – 97 .
Gaibulloev K. ( 2015 ) Terrorist group location decision: an empirical investigation , Oxford Economic Papers , 67 , 21 – 41 .
Gaibulloev K. Sandler T. ( 2008 ) Growth consequences of terrorism in Western Europe , Kyklos , 61 , 411 – 24 .
Gaibulloev K. Sandler T. ( 2011 ) The adverse effect of transnational and domestic terrorism on growth in Africa , Journal of Peace Research , 48 , 355 – 71 .
Gaibulloev K. Sandler T. ( 2014 ) An empirical analysis of alternative ways that terrorist groups end , Public Choice , 160 , 25 – 44 .
Gries T. Meierrieks D. Redlin M. ( 2015 ) Oppressive governments, dependence on the United States and anti-American terrorism , Oxford Economic Papers , 67 , 83 – 103 .
Grossman H.I. ( 1991 ) A general equilibrium model of insurrections , American Economic Review , 81 , 912 – 21 .
Hoffman B. ( 1998 ) Inside Terrorism , Columbia University Press , New York .
Hoffman B. ( 2006 ) Inside Terrorism , rev. edn., Columbia University Press , New York .
Jones S.G. Libicki M.C. ( 2008 ) How Terrorist Groups End: Lessons for Countering al Qa'ida , Monograph MG-741-1, RAND, Santa Monica, CA .
Kaplan E.H. ( 2015 ) Socially efficient detection of terror plots , Oxford Economic Papers , 67 , 104 – 15 .
Keefer P. Loayza N. (eds) ( 2008 ) Terrorism, Economic Development, and Political Openness , Cambridge University Press , New York .
Kollias C. Papadamou S. Arvanitis V. ( 2013 ) Does terrorism affect the stock-bond covariance? Evidence from European countries , Southern Economic Journal , 79 , 832 – 48 .
Kunreuther H. Michel-Kerjan E. Porter P. ( 2003 ) Assessing, managing and financing extreme events: dealing with terrorism , Working Paper 10179, National Bureau of Economic Research .
La Free G. Dugan L. ( 2007 ) Introducing the global terrorism database , Terrorism and Political Violence , 19 , 181 – 204 .
Mickolus E.F. ( 1980 ) Transnational Terrorism: A Chronology of Events 1968–1979 , Greenwood Press , Westport, CT .
Mickolus E.F. ( 1989 ) What constitutes state support to terrorism? , Terrorism and Political Violence , 1 , 287 – 93 .
Mickolus E.F. Sandler T. Murdock J.M. ( 1989 ) International Terrorism in the 1980s: A Chronology of Events , 2 vols. , Iowa State University Press , Ames .
Mickolus E.F. Sandler T. Murdock J.M. Flemming P. ( 2013 ) International Terrorism: Attributes of Terrorist Events, 1968–2013 (ITERATE) , Vinyard Software , Ponte Vedra, FL .
Mueller J. ( 2006 ) Overblown: How Politicians and the Terrorism Industry Inflate National Security Threats and Why We Believe Them , Free Press , New York .
National Consortium for the Study of Terrorism and Responses to Terrorism . ( 2013 ) Global Terrorism Database , available at http://www.start.umd.edu/gtd/ (accessed 25 August 2013) .
Nitsch V. Schumacher D. ( 2004 ) Terrorism and international trade: an empirical investigation , European Journal of Political Economy , 20 , 423 – 33 .
Phillips B.J. ( 2014a ) Terrorist group cooperation and longetivity , International Studies Quarterly , 58 , 336 – 47 .
Phillips B.J. ( 2014b ) What is a terrorist group? Conceptual issues and empirical implications , Terrorism and Political Violence , doi: 10.1080/09546553.2013.800048 .
RAND . ( 2012 ) RAND database of worldwide terrorism incidents , available at http://www.rand.org/nsrd/projects/terrorism-incidents.html (accessed 3 August 2012) .
Rapoport D.C. ( 1984 ) Fear and trembling: terrorism in three religious traditions , American Political Science Review , 78 , 658 – 77 .
Rapoport D.C. ( 2004 ) Modern terror: the four waves , in Cronin A.K. Ludes J.M. (eds) Attacking Terrorism: Elements of a Grand Strategy , Georgetown University Press , Washington, DC .
Sambanis N. ( 2008 ) Terrorism and civil war , in Keefer P. Loayza N. (eds) Terrorism, Economic Development and Political Openness , Cambridge University Press , New York .
Sandler T. ( 2014 ) The analytical study of terrorism: taking stock , Journal of Peace Research , 51 , 257 – 71 .
Sandler T. Arce D.G. ( 2003 ) Terrorism and game theory , Simulation &Gaming , 34 , 319 – 37 .
Sandler T. Enders W. ( 2008 ) Economic consequences of terrorism in developed and developing countries: an overview , in Keefer P. Loayza N. (eds) Terrorism, Economic Development and Political Openness , Cambridge University Press , New York .
Sandler T. Hartley K. ( 1995 ) The Economics of Defense , Cambridge University Press , Cambridge .
Sandler T. Lapan H.E. ( 1988 ) The calculus of dissent: an analysis of terrorists’ choice of targets , Synthese , 76 , 245 – 61 .
Sandler T. Siqueira K. ( 2006 ) Global terrorism: deterrence versus preemption , Canadian Journal of Economics , 50 , 1370 – 87 .
Sandler T. Siqueira K. ( 2009 ) Games and terrorism: recent developments , Simulation &Gaming , 40 , 164 – 92 .
Santifort C. Sandler T. ( 2013 ) Terrorist success in hostage-taking mission , Public Choice , 156 , 125 – 37 .
Santifort-Jordan C. Sandler T. ( 2014 ) An empirical study of suicide terrorism: a global analysis , Southern Economic Journal , 80 , 981 – 1001 .
Younas J. ( 2015 ) Does globalization mitigate the adverse effects of terrorism on growth? Oxford Economic Papers , 67 , 133 – 56 .
Young J.K. Findley M.G. ( 2011 ) Can peace be purchased? A sectoral-level analysis of aid's influence on transnational terrorism , Public Choice , 149 , 365 – 81 .
Email alerts
Citing articles via.
- Recommend to your Library
Affiliations
- Online ISSN 1464-3812
- Print ISSN 0030-7653
- Copyright © 2024 Oxford University Press
- About Oxford Academic
- Publish journals with us
- University press partners
- What we publish
- New features
- Open access
- Institutional account management
- Rights and permissions
- Get help with access
- Accessibility
- Advertising
- Media enquiries
- Oxford University Press
- Oxford Languages
- University of Oxford
Oxford University Press is a department of the University of Oxford. It furthers the University's objective of excellence in research, scholarship, and education by publishing worldwide
- Copyright © 2024 Oxford University Press
- Cookie settings
- Cookie policy
- Privacy policy
- Legal notice
This Feature Is Available To Subscribers Only
Sign In or Create an Account
This PDF is available to Subscribers Only
For full access to this pdf, sign in to an existing account, or purchase an annual subscription.
Rule of Law Responses to Terrorism
Under international law, states have the responsibility to bring terrorists to justice. This means that states need to ratify and effectively implement the relevant conventions and binding UNSCRs, criminalize terrorist offences, establish appropriate penalties and sentences that duly reflect the seriousness of the crimes and facilitate mutual legal assistance in accordance with international law.
The counter-terrorism framework has expanded significantly since 9/11. To combat this, during the last decade governments have increasingly adopted legislation that criminalizes the preparation, facilitation and incitement of terrorism. Furthermore, states have implemented a range of administrative measures – including listing procedures, the use of watchlists, control orders and deprivation of nationality – aimed at the prevention of terrorism. Some of these efforts pose serious challenges to human rights and the rule law. States, but also the United Nations Security Council need to be held accountable for the counter-terrorism laws and policies that they have created.
The terrorism threat landscape is becoming more diversified and complex. While some progress has been made, a significant number of FTFs and their families are still in detention or make-shifts camps and elsewhere in Northeastern Syria, posing a challenge to the international community. The legal debate relating to repatriation is still on-going. The rise of right-wing extremism, in particular in Europe and the United States, but other regions is growing concern. Perpetrators – irrespective of their ideological motivation – should be held accountable in accordance with the rule of law and respect for human rights.
Our Priority Areas
- Foreign ‘Terrorist’ Fighters and their families
- Right-wing extremism through a criminal just ice lens
- A RoL-based CT framework
- Accountability for Terrorism-related Crimes
- Evidence Collection, including Battlefield Evidence
- The use of administrative measures in a CT context
Key Activities

Curriculum Development for the Rule of Law
Protecting Intelligence Sources & Witnesses


Jessica Dorsey

Fiona de Londras

Ahmad El-Muhammady

Allan Ngari

Christophe Paulussen

Letta M. Tayler

Clive Walker

ESSAY SAUCE
FOR STUDENTS : ALL THE INGREDIENTS OF A GOOD ESSAY
Essay: International law and terrorism
Essay details and download:.
- Subject area(s): Law essays
- Reading time: 15 minutes
- Price: Free download
- Published: 12 January 2017*
- File format: Text
- Words: 4,254 (approx)
- Number of pages: 18 (approx)
- Tags: Terrorism essays
Text preview of this essay:
This page of the essay has 4,254 words. Download the full version above.
Introduction Spain, Iraq, Syria, Egypt, Lebanon, Turkey and now also Belgium and France are one of the countries who are victims of horrifying terrorist attacks. Terrorism used to be sporadic, however, during the years 2013-2016, terrorist attacks evolved into systematic attacks. Terrorism is not only a national crime, but also, a crime of international concern, as we shall see in the thesis. The whole world lives and experiences the impact of terrorism. Recently, terrorism is introduced in the field of International Criminal Law, namely, by the Special Tribunal for Lebanon. The latter is established due to the assassination of former Prime Minister Rafiq al Hariri of Lebanon and approximately, 22 other victims. The Tribunal is a ‘’hybrid’’ tribunal, meaning, that it has both international and national (Lebanese) elements. The Judges of the STL defined the crime of terrorism on the basis of Lebanese criminal law and relied thereby also on a existing international convention, and Customary International Law. However, the International Criminal Court does not have jurisdiction over terrorism, except the crimes defined in art. 5 of the Rome Statute of the International Criminal Court, namely, genocide, crimes against humanity, war crimes, and the crime of aggression. Consequently, this thesis aims to research: ‘’Prosecuting terrorism in the International Criminal Court: What can the International Criminal Court learn from the Special Tribunal for Lebanon concerning Terrorism?‘’ For the purposes of this thesis, the following sources will be used: case law of various international courts and tribunals, international conventions, law journals and books, and negotiations of the United Nations regarding the issue of Terrorism, and also, other United Nation documents with regards to terrorism. Initially, the discussion about the lack of a clear international definition of terrorism will start. With the focus on various international conventions and the current situation on the definition of this crime. Moreover, focusing on the Draft Comprehensive Convention and shortly, on the decision of the Special Tribunal for Lebanon for defining terrorism (Chapter 1). Followed by, the findings of the State parties during the negotiations of the Rome Statute in 1998, and also the current situation regarding the inclusion of the crime of terrorism in the International Criminal Court will be manifested. This chapter forms rather a political part of the thesis. The findings of the States are important and essential in order to understand the reasons, the court lacking jurisdiction of this crime (Chapter 2). Accordingly, the crime of terrorism will be discussed and analyzed in the light of crimes against humanity and war crimes. The analyses will focus on, whether terrorism can be covered by those two provisions. Furthermore, some obstacles of the ICC will be advocated, as the complementarity principle of the ICC and the referral issues (Chapter 3). Concurrently, the Special Tribunal for Lebanon’s reasoning and rulings of the Appeals Chamber will be discussed in depth and in length, which might be a little opening door for including this crime internationally (Chapter 4). Furthermore, the discussions about a ‘’Special Court for Prosecuting Terrorism’’ in international criminal law will be manifested. The arguments, pros and cons will be advocated as to the introduction of such a Court, which only deals with terrorism. Thereby, a view in the domestic systems of some States will be taken into account (Chapter 5). Finally, in the conclusion the research question will be answered according to all these named chapters. Chapter 1: The growing need to define terrorism internationally There are imminent struggles in finding a clear, international definition on terrorism, mainly for the reason that terrorism is understood differently by each person. For example, Osama Bin Laden was first a liberator and then a terrorist, Nelson Mandela was first a terrorist and then became a liberator. This is a evident example demonstrating us that the difficulty for defining this crime: ‘One person’s terrorist is another man’s freedom fighter’ . So, what is actually terrorism? Some say that the search for an accepted definition on terrorism in international law resembles ‘the Quest for the Holy Grail’. This demonstrates again that not everyone has the same view regarding the definition of this crime, it is thus rather subjective. The struggle of finding a clear international definition is tangible since the 1930’s. Since then, there were serious efforts made to achieve consensus on a general definition of terrorism. For instance, the 1937 Convention for the Prevention and Punishment of Terrorism provided a definition on terrorism, unfortunately, it was never adopted due to the difficulties for achieving an agreement on the definition. Currently, there were new attempts to achieve a definition of terrorism, however, there was always a deadlock in achieving such definition. There are some regional conventions which specifically address particular types of terrorism, for instance the Arab Convention on the Suppression of Terrorism, The European Convention on the Suppression of Terrorism, The Convention for the Suppression of Terrorist Bombings, and so on. In total there are twelve conventions addressing a particular type of terrorism. It is noteworthy to say, that these conventions are not intended to define terrorism, they basically address specific conduct that may fall within the purview of what we know the overarching term of terrorism. The conventions impose obligations on States to criminalize terrorism in their national legal systems. They also set obligate State parties to take measures for the prevention of terrorism. Furthermore, the State parties are obliged to cooperate in the prosecution of this terrorism, for example in sense of extradition or submission of the accused. 1.1 The draft Comprehensive Convention on International Terrorism The discussion regarding the draft Comprehensive Convention on International Terrorism is for this thesis of great significance. The International Criminal Court (ICC) will be discussed in chapter two regarding this Convention. It all started with the General Assembly of the United Nations, which decided in its resolution 54/110 of 9 December 1999 to give consideration to the elaboration of a Comprehensive Convention on International Terrorism. It entrusted with this task both the Ad Hoc Committee, which was established by resolution 51/210. During the adoption of resolution 1373 in response to the 9/11 attacks, the Security Council called on all Member States to become parties of existing international conventions concerning terrorism. Also, the Security Council called upon States to adopt wide-ranging measures on their domestic level. This implied that terrorism needed to be defined under international law, and the Security Council saw the necessity of it. The latter has placed pressure on the General Assembly, in order to react to a situation that requires firm action on its behalf. States were not happy with the Security Council’s exercise of Chapter VII authority to mandate certain conduct and impose treaty obligations. Moreover, during the working group of the Ad Hoc Committee States were unequivocal in their condemnation of terrorism in all forms and manifestations. However, taking away the non-agreement on the definition of this crime, there was a some progress in the achievement of a generic definition of terrorism. According to Article 2 of the Draft Comprehensive Convention, terrorism is ‘unlawfully and intentionally causing death or serious bodily injury to any person; b) serious damage to public and private property, including a State or government facility (…); or (c) other such damage where it is likely to result in major economic loss. Furthermore, the definition requires that ‘the purpose of the conduct, by its nature or context, is to intimidate a population, or to compel a Government or an international organization to do or abstain from doing any act’. However, Article 18 sets out an exception on Article 2 regarding ‘acts carried out during an armed conflict or governed by International Humanitarian Law. Currently’, the draft excludes only ‘armed forces’, thereby exempting only State forces and not others whose conduct would also be governed by International Humanitarian Law, for instance, non-state-actors. The exclusion states that ‘the activities of armed forces during an armed conflict, as those terms are understood under international humanitarian law, which are already governed by that law, are not governed by this Convention.’ This Convention increased thus some legal and political consequences. The legal consequence lay in the fact that practically no one agrees on a definition. Chapter 2 will discuss the political consequences in the eyes of the States who are opposed or imposed for including the crime of terrorism in the jurisdiction of the International Criminal Court. On 3 and 4 October 2016 the discussions on the Draft Comprehensive Convention will be further discussed , hopefully, the State Parties can then agree on a clear definition, due to the evolving nature of this crime. It should be put on the first of the list. 1.2 The Special Tribunal for Lebanon on the definition of Terrorism For the purposes of this thesis, the Special Tribunal’s rulings and findings on the definition of terrorism are important. In anticipation of Chapter 4, I would like to give some words with regards to the definition of terrorism. Judge Antonio Cassese was one of the judges who defined terrorism under International Criminal Law, but also, under Lebanese Law. The Articles 2 and 3 of the STL Statute are about terrorism. Pursuant to Article 2 of the STL Statute, the Tribunal can apply both Lebanese Law and International law for the purpose of interpreting Lebanese Law. The STL took two rules into account, alongside, to the Lebanese Law on Terrorism, in order determine the definition of terrorism: The Arab Convention against Terrorism and customary international law on terrorism. Chapter 4 includes the analyzes of this important ruling of the STL and its impact will then continue. Interim conclusion Hence, the will to define terrorism exists, but the agreement on the need for a definition is not in accordance by an agreement on its substance. The work on the Comprehensive Convention on International Terrorism started by the end of 2000, which means in the immediate aftermath of the 9/11 attacks, the United Nations failed to adopt this convention. Even when the pressure was very high and all States were condemning the attacks of 9/11, still, until today we have not an agreed definition. In this chapter, the STL is very shortly discussed, perhaps, the STL can be an opening door in order to define and to prosecute this crime internationally, to be continued. Chapter 2: The International Criminal Court: a permanent international Court One of the most important developments of international criminal, is the creation of a permanent criminal court with potentially worldwide jurisdiction. The International Criminal Court has the power to exercise jurisdiction over persons for the most serious crimes of international concern (art. 1 Rome Statute). Furthermore, art. 5 Rome Statute provides the crimes where the Court has Jurisdiction over, namely: the crime of genocide (art. 6), crimes against humanity (art. 7), war crimes (art. 8) and the crime of aggression (art. 8 bis) the latter will be in force in 2017. The draft Statute of the ICC proposed by the International Law Commission would have given the court jurisdiction over more offences than the ICC has now, for instance, there was a list of ‘ treaty crimes’ which included offences under the multilateral terrorism conventions, the UN 1988 drug convention, the Apartheid Convention and grave breaches of the Geneva Conventions. Since the ICC can only deal with the crimes described above, terrorism is missing, the question is, how is it possible that a serious crime as terrorism can be missed in the jurisdiction of the ICC? The main reason for this lack is the willing of the State parties who did not want to include this crime in the jurisdiction of the Court. For a clear understanding of this thesis it is necessary to underline the reasons of the States during the negotiations of the Rome Statute of 15 June to 17 July 1998. Since this thesis questions about the prosecution of the crime terrorism under international criminal law, more specifically the ICC, it is important to have knowledge about the findings of States regarding this matter. For instance, why is this crime not included in the Rome Statute? What are the underlying reasons of this decision? First, the discussion of the crime of terrorism in 1998 will be discussed, in the second paragraph the discussions of 2009 during the Review conference will be demonstrated. 2.1. Situation in 1998 during the negotiations of the Rome Statute of the International Criminal Court During the negotiations of the Rome Statute in 1998 there were opposing and imposing State parties, as to whether include the crime of terrorism in the Rome Statute. One of the imposers were Algeria, Armenia, Turkey and India. There were more imposers, however, only these States will be discussed in this thesis in order to illustrate. The delegations of Algeria stated for instance that terrorism is one of the serious crimes, which threatens the international peace and security. Therefore, it should be included in the Rome Statute. In line with this, Armenia also noted that terrorism should be included in the Statute, however, that a clear definition in the Statute is needed for this crime, in order to avoid misunderstandings and interpretations in the future. Turkey was of the opinion that the crime of terrorism was linked with transnational organized crime, the latter was already legally delimited, according to Turkey. However, the international community had failed to develop a general definition on terrorism, Turkey stated. Furthermore, the delegations of Turkey noted that States must refrain from organizing and encouraging terrorist activities. Moreover, that the systematic and prolonged terrorism was a crime of international concern. A systematic terrorism campaign waged by a group against a civilian population would be a crime under international law, and would therefore fall under art. 5 of the draft Statute. Turkey concluded with stating that terrorism was often sustained by large-scale drug trafficking, which had an undeniable international impact, which justifies that the both crimes should be cover under art. 5 of the Rome Statute. Also India was one of the countries which highly was imposed for including the crime of terrorism in the Rome Statute. The delegations of India found it incomprehensible that the Statute should fail to address terrorism, which is truly an international crime, and had taken more lives than the so-called core crimes in recent decades. I find my self in the arguments of India, stating that terrorism had taken more lives than the other crimes in the Rome Statute, however, it is not a question of currency of victims, it is a question the threat to the international globe. In addition, the statements of Turkey, that terrorism is systematic and prolonged, if at that time, were terrorism was much lesser than now, it is now then more severe. Thus, terrorism has intensified. The statements of Armenia, regarding the not existence of a clear definition, is somewhat true, this is still one of the main reasons why terrorism is not included in the ICC, and also one of the reasons why the inclusion of the crime was rejected. This discussion will be continued in the next paragraph. Where there are imposing parties, there are always opposing parties. One of the countries who was opposed for including terrorism in the Rome Statute was Iraq. Also the United Kingdom was opposed, with stating that it is difficult to include treaty crimes, such as terrorism, it was thus a complex issue. Mainly, because the Court was not the adequate forum to try cases of terrorism. Accordingly, the delegation of UK could not see a way of including treaty crimes that would command a general acceptance. Also, the Arab League was one of the opposing State Parties. It find that there had been no agreed definition on the crime of terrorism, preferably, they would not see terrorism be included in the Statute. However, they stated, should the Conference have the intention to include it, it might be guided by the definition of the crime of aggression and the crime of terrorism laid down in the Arab Convention for the Suppression of Terrorism, which was adopted in Cairo in April 1998. Also, the United States of America was one of the opposing State parties, stating that including the crime of terrorism would serve no useful purpose, the United States also did not support Resolution E in annex I to the Final Act, for the reason that it seemed to reflect the view that crimes of terrorism should necessarily be included within the jurisdiction of the Court, subject only to the question of defining them. By conferring such jurisdiction on the Court, it might hamper essential transitional efforts at effectively fighting such crimes. It is understandable that the US does not support resolution E of the final act, since that leaves a door open for the ICC, whether or not to include terrorism in the future, if the States, come up with an agreed definition. Perhaps, the US wants to close all the doors for giving the ICC jurisdiction over this crime. The argument of UK, that the Court is not the best forum to try issues of terrorism, does not find, in my opinion any scrutiny, terrorism, as stated by many other States, is a serious crime of international concern, it is a worldwide crime. Hence, why would the Court not be the ‘’best’’ forum to have jurisdiction over it? Of course, the ICC is a last resort court , however, if the states are unwilling or unable to carry out the prosecution, the ICC has jurisdiction. The United States was in all forms and manifestations against the idea of inclusion the crime of terrorism, which is understandable due to the fact that the US wants to maintain the terrorism in the hands of domestic systems. The argument of the Arab League, is for a part, now used by the STL, the STL relied on the Arab Convention for the Suppression of Terrorism, which brought up in life an international hybrid tribunal. 2.2. The Review Conference in 2009 on the inclusion of Terrorism in the International Criminal Court During the Review Conference in 2009 the issue of terrorism was again raised. However, the idea of including the crime of terrorism was rejected, mainly, because there were more States opposed to this idea, rather than, in favor. In the discussions, the Conference stated that the, Conference should focus on strengthening the role of the Court in international Criminal Justice, by including the universality of the Rome Statute. The Conference noticed that terrorism was already covered by sixteen multilateral conventions hence, there was no problem of a lack of a definition according to the delegations. Does that mean that the problem of a lack of definition is solved? It is true, that the crime is covered by many conventions, but there is still not an agreement on the content of it, as said in the previous chapter. However, it may the case that the draft Comprehensive Convention will again, not be completed on 3 and 4 October 2016. Perhaps, that the Court can rely on other international conventions which already have defined the crime of terrorism. This was, as we also have seen in chapter one, ruled by the STL, the STL referred hereby to the Arab Convention (an international convention, between all Arab States) and Customary International Law. During the Review Conference the Netherlands came up with a detailed proposal regarding the inclusion of the crime of terrorism. Firstly, the Netherlands stated that since there is a lack of the definition of terrorism, the same can be done as to the crime of aggression, by including the crime of terrorism in art. 5 (1), simultaneously, postponing the exercise of jurisdiction over this crime until an agreement on the definition, and the conditions for the exercise of jurisdiction are agreed. Secondly, to establish an informal working-group (compared to the working-group on the crime of aggression). The working-group should thus be tasked with examining the question of the extend to which the Statute might need to be adapted as a result of the introduction of the crime of terrorism, within the jurisdiction of the Court, as well as other questions relevant to the extension of jurisdiction. However, the approach of the Netherlands was rejected due to two reasons: The States were of the opinion that it was not appropriate to make a reference to the crime of aggression, since the Rome Statute had now entered into force, there were doubts to the feasibility of incorporating the crime of terrorism in the Court’s jurisdiction, because of the absence of a legal definition. Also, as we have seen in the earlier passage, the Arab League was also of the opinion that terrorism might be guided trough the crime of aggression. Which demonstrates, that States, after ten years, made up their minds, and start to think the same. Perhaps, the ongoing intensity about terrorism will give the States a boost for defining terrorism as soon as possible and give the ICC jurisdiction over this crime. The Netherlands also referred to Resolution E Final act which already stated : ‘’ Affirming that the statute of the international criminal court provides for a review mechanism, which allows for an expansion in the future of the jurisdiction of the court. Recommends that a Review Conference pursuant to article 123 of the Statute of the International Criminal Court consider the crimes of terrorism and drug crimes with a view to arriving at an acceptable definition and their inclusion in the list of crimes within the jurisdiction of the court.’’ By including resolution E in the Final act, the ICC did exclude terrorism completely of its jurisdiction. Which is positive thing, giving the imposing parties some reliance on the ICC. In accordance with this, the Netherlands proposed to modify the Rome Statute as follows: Article 5: (a) The crime of genocide; (b) Crimes against humanity; (c) War crimes; (d) The crime of aggression; (e) The crime of terrorism. ‘’The Court shall exercise jurisdiction over the crime of terrorism once a provision is adopted in accordance with articles 121 and 123 defining the crime and setting out the conditions under which the Court shall exercise jurisdiction with respect to this crime. Such a provision shall be consistent with the relevant provisions of the Charter of the United Nations.’’ The discussions about the proposal of the Netherland’s will also be discussed on 3 and 4 October 2016, as earlier written. Perhaps the States will change their minds, due to the increasing nature of this crime, and have more the willingness than first in order to define a definition. Perhaps, the proposal of the Netherlands will then be accepted. Interim conclusion As we have seen in this chapter, it is still disputable what ‘’terrorism’’ actually is, there are many imposers, however, more States opposed to the idea of bringing this crime under the Rome Statute. Perhaps, States will be able to find a solution in the upcoming conference. The proposal of the Netherlands is also a good start, perhaps, more States will come up with proposal’s compared like this, but also, it will encourage the States to think more about the notion of terrorism under the Rome Statute. In line with this, resolution E of the final act, does not opt out that terrorism can one day be included in the Court, thus, it seems not an impossible task to include it, whereby the drafters had such a case in their minds. Also, some States, stated that the ICC already covers the crime of terrorism, if that is the case, then why not including the crime as an independent crime in the Statute? This will be further discussed in the next chapter. Provisional bibliography United Nations Documents: United Nations Diplomatic Conference of Plenipotentiaries on the Establishment of the International Criminal Court, Rome 15 June to 17 July 1998, Official Records, Volume II. Informal text of Article 2, Report of the Working Group on Measures to Eliminate International Terrorism; Un. Doc. A/C.6/56/L.9, Annex I.B. Assembly of State Parties, International Criminal Court, Eight Session, The Hague 15 November 2009, ICC-ASP 8/43. Provisional programme of work of the Sixth Committee for the seventy-first session, 1. Journals: Aviv Cohen, ‘Prosecuting Terrorist at the International Criminal Court: Reevaluating an unused legal tool to combat Terrorism’, (2012), Vol. 20:2, Michigan State International Law Review. Eric Creegan, ‘A Permanent Hybrid Court for Terrorism’, (2011) 237-313, American University, International Law Review 26 no. 2. Matthew Gillet and Matthias Schuster: ‘The Special Tribunal for Lebanon Defines Terrorism’, (2011) – 989-1020, Journal of Criminal Justice. Mahmoud Hmoud, ‘Negotiating the Draft Comprehensive Convention on International Terrorism’, (2006), Journal of International Criminal Justice. G. Levitt, ‘Is ‘’Terrorism’’ Worth Defining?’, Ohio Northern University Law Review (1986). Lucy Martinez, ‘Prosecuting Terrorists at the International Criminal Court: Possibilities and Problems’, (2002-2003), Vol. 34:1, Rutgers Law Journal. Laura M. Olson, ‘Prosecuting Suspected Terrorist: The ‘’War on Terror’’ Demands Reminders About War, Terrorism and International Law’, (2010), Vol.24, Emory International Law Review. R. Higgins, ‘The General International Law of Terrorism, in R. Higgins and M. Flory, Terrorism and International Law’, (1997), Routledge, London. Sandra L. Hodgkinson, ‘Are Ad Hoc Tribunals an Effective Tool for Prosecuting International Terrorism Cases?’, (2010), Vol. 24, Emory International Law Review. B. Saul, ‘Defining Terrorism in International Law’, (2008), Oxford University Press, USA. Jean-Marc Sorel, ‘Some Questions About the Definition of Terrorism and the Fight Against Its Financing’, (2003). Books: Robert Cryer et al., An Introduction to International Criminal Law and Procedure, Cambridge third edition (2014). Helen Duffy, The war on Terror and The Framework of International Law Cambridge University Press (2005). Case law: Interlocutory Decision on the Applicable Law: Terrorism, Conspiracy, Homicide, Perpetration, Cumulative Charging (Appeals Chamber), STL-11-01/I, 16 February 2011. Order on Preliminary Questions Addressed to the Judges of the Appeals Chamber pursuant to Rule 68, paragraph (G) of the Rules of Procedure and Evidence STL-11-01/I, 21 January 2011. Resolutions: Council Resolution 1566, 2004. Council Resolution 1373, (S/620) 2009. Law Conventions: Rome Statute of the International Criminal Court (1998). International Convention for the Suppression of Terrorist Bombings (1998) The Arab Convention on the Suppression of Terrorism (1998). The Statute of The Special Tribunal for Lebanon (2009).
...(download the rest of the essay above)
Discover more:
- Terrorism essays
Recommended for you
- Terrorism today and ISIS
- Importance of International Humanitarian Law in armed conflict regarding terrorism
- Shedding Light on Human Rights Violations: Guantanamo Bay & Other Inter. Black Sites
About this essay:
If you use part of this page in your own work, you need to provide a citation, as follows:
Essay Sauce, International law and terrorism . Available from:<https://www.essaysauce.com/law-essays/essay-international-law-terrorism/> [Accessed 18-04-24].
These Law essays have been submitted to us by students in order to help you with your studies.
* This essay may have been previously published on Essay.uk.com at an earlier date.
Essay Categories:
- Accounting essays
- Architecture essays
- Business essays
- Computer science essays
- Criminology essays
- Economics essays
- Education essays
- Engineering essays
- English language essays
- Environmental studies essays
- Essay examples
- Finance essays
- Geography essays
- Health essays
- History essays
- Hospitality and tourism essays
- Human rights essays
- Information technology essays
- International relations
- Leadership essays
- Linguistics essays
- Literature essays
- Management essays
- Marketing essays
- Mathematics essays
- Media essays
- Medicine essays
- Military essays
- Miscellaneous essays
- Music Essays
- Nursing essays
- Philosophy essays
- Photography and arts essays
- Politics essays
- Project management essays
- Psychology essays
- Religious studies and theology essays
- Sample essays
- Science essays
- Social work essays
- Sociology essays
- Sports essays
- Types of essay
- Zoology essays
Law Enforcement and Terrorism Essay
We have all witnessed the adverse impacts of terrorism on our social and economic stability in our country. This only attests that it is not and will never be a hoax. Let us face it. The loss of our beloved ones, the loss of the right personnel, the economic instability of our country and many others are some of the bad impacts of terrorism.
As a result of this, a lot of pressure from citizens has been imparted on the local law enforcement agencies. This has forced law enforcement agencies to reposition their line of work to fight terrorism before more severe terrorist acts are carried out. This paper therefore tries to explicate the strategies towards local law enforcement in the process of protecting my community against terrorism.
Whenever terrorist attacks occur, the first bodies to blame are usually the law enforcement agencies. It is thus the obligation of the law enforcement agencies to work diligently to ensure that the next terrorism attacks do not occur. The first tactic to take is to enforce and improve the local federal partnerships.
This is whereby the leaders of the federal as well as the local enforcement agencies cooperate to reinforce the existing partnerships. This is to be done since evidently, domestic security largely depends on the law enforcement agencies working together. This is also after the realization that agencies at each level have an imperative role to fill.
In order for local federal partnerships to succeed, there should be mutual understanding of each and everyone’s role in preventing terrorism as well as understanding each other’s weaknesses (Fraser, Scott, Heisey, and Wasserman, 1998). A managerial session should be organized with the main agenda of improving the local and federal partnerships.
The session should allow the members participating to exchange freely information and dismiss misperceptions in an open and productive forum. Through this, several obstacles will be removed leading to successful local federal partnerships.
During this executive session, several issues will be raised and at the same time solutions will be provided to the problems. Recommendations will also be given to counteract future problems that may arise in the local and federal agencies. However, in cases where time would be a limiting factor, some problems will be postponed to be solved in future executive forums. During the provision of recommendations, there is no need of assigning ownership to any agency.
It is however good to enforce recommendations for improving training immediately. The issues and recommendations raised in the first session will be of great importance as they will serve as starting points for the successive forums. The sessions may focus on different topics such as policing immigrant communities, homeland security systems, intelligence as well as bio-terrorism.
Through community policing, complex problems related to crimes will be addressed and resolved and the quality of life will be improved. An array of techniques to perk up the efficacy of the police as well as the sheriff agencies will be made available. Community policing will also help in the prevention and responsiveness to the incidences of terrorism.
This will be enforced through the active involvement of citizens. Therefore, in order for the law enforcement agencies to fight terrorism, assets and resources as well as partnerships traced in the community policing approaches need to be made.
The managerial staff of the law enforcement agency should learn and understand the cultural and religious beliefs of the community. A mutual communication should be developed among the leaders with an aim of protecting the community against terrorist attacks. There is need to develop multicultural forums and councils with the essential expertise to inspect hate crimes. Students as well as other educational institutions need to be protected to prevent hate crimes through cooperation between campus officers and law enforcement agencies.
According to Kahaner (1997), while protecting students, there is need for the local law enforcement to use all the resources available to understand both the cultural and the religious beliefs of the community. As stated previously, the local and federal enforcement agencies should mutually cooperate with one another and in the process, educate the constituents regarding their role in offering protection to the community against terrorism.
This is through helping the local law enforcement agencies during their investigations. The media also has a greater role in creating awareness among the community members regarding its function in reducing the rates of crimes. The media will enhance public education campaigns of the community against crimes.
The tools and resources for improving communication need to be developed. Amongst them are retaining of officers with the ability to speak diversified languages, inventing video tapes for training and the distribution of multi-language brochures. The enforcement of these tools will improve the delivery of police service in the community as well as other communities (Reaves & Hickman, 2002).
The local law enforcement should be in partnership with the police in detection of any criminal activities. The group of individuals that detect the crime should then notify other teams (local law enforcement) through the lines of communication that they have developed. This should be followed by intervention whereby the concerned teams concentrate on criminal investigation.
There will be the responsibility of the health care system to manage the terrorist attacks basing on their health care surge. The teams as well as other law enforcement agencies should communicate effectively so that the indispensable precautions are provided to other citizens. In the process, other remedial arrangements will be provided.
In conclusion, here are the most vital issues during preparation and response to terrorism attacks. First is funding. This should be done so that strong cooperation among the various law enforcement agencies, fire fighting units, the public and the health care quarter is built.
Training should be enforced to improve the intelligence in detection of any criminal activities. The last thing to put into practice is to share ones knowledge with others on matters relating to terrorism. Sharing should also be done among the agencies. If this is put into practice, I am sure that my community will be decidedly protected from terrorist attacks.
Fraser, B. C., Scott, M., Heisey, J., Wasserman, R. (1998). Challenge to change: The 21 st century policing project. Washington, DC: Police Executive Research Forum.
Kahaner, L. (1997). Competitive intelligence:How to gather, analyze and use information to move your business to the top. New York,NY: Simon Shuster.
Reaves, A. B., Hickman, J. M. (2002). Census of state and local law enforcement agencies. Washington, DC: Bureau of Justice Statistics
- Chicago (A-D)
- Chicago (N-B)
IvyPanda. (2019, March 25). Law Enforcement and Terrorism. https://ivypanda.com/essays/law-enforcement-and-terrorism/
"Law Enforcement and Terrorism." IvyPanda , 25 Mar. 2019, ivypanda.com/essays/law-enforcement-and-terrorism/.
IvyPanda . (2019) 'Law Enforcement and Terrorism'. 25 March.
IvyPanda . 2019. "Law Enforcement and Terrorism." March 25, 2019. https://ivypanda.com/essays/law-enforcement-and-terrorism/.
1. IvyPanda . "Law Enforcement and Terrorism." March 25, 2019. https://ivypanda.com/essays/law-enforcement-and-terrorism/.
Bibliography
IvyPanda . "Law Enforcement and Terrorism." March 25, 2019. https://ivypanda.com/essays/law-enforcement-and-terrorism/.
- Community Policing and Traditional Policing
- "Policing Terrorism" by Waddington
- The Models of Policing
- Hate Crimes in New York
- Predictive Policing: Intelligence-Led Policing for Law Enforcement Managers
- Policing in America: Future and Challenges
- Community Policing Programs in The U.S.
- Intelligence–Led Policing
- Community Policing and Police Psychology
- Traditional vs. Contemporary Policing in America
- Minorities and Policing
- What New Demands on Policing Have Resulted From the International ‘War on Terror’?
- Discipline as an Integral Part of Effective Police Supervision
- Relation Between Justice and Inequality
- Concept of National and Transnational Entities
Terrorism Essay for Students and Teacher
500+ words essay on terrorism essay.
Terrorism is an act, which aims to create fear among ordinary people by illegal means. It is a threat to humanity. It includes person or group spreading violence, riots, burglaries, rapes, kidnappings, fighting, bombings, etc. Terrorism is an act of cowardice. Also, terrorism has nothing to do with religion. A terrorist is only a terrorist, not a Hindu or a Muslim.

Types of Terrorism
Terrorism is of two kinds, one is political terrorism which creates panic on a large scale and another one is criminal terrorism which deals in kidnapping to take ransom money. Political terrorism is much more crucial than criminal terrorism because it is done by well-trained persons. It thus becomes difficult for law enforcing agencies to arrest them in time.
Terrorism spread at the national level as well as at international level. Regional terrorism is the most violent among all. Because the terrorists think that dying as a terrorist is sacred and holy, and thus they are willing to do anything. All these terrorist groups are made with different purposes.
Causes of Terrorism
There are some main causes of terrorism development or production of large quantities of machine guns, atomic bombs, hydrogen bombs, nuclear weapons, missiles, etc. rapid population growth, Politics, Social, Economic problems, dissatisfaction of people with the country’s system, lack of education, corruption, racism, economic inequality, linguistic differences, all these are the major elements of terrorism, and terrorism flourishes after them. People use terrorism as a weapon to prove and justify their point of view. The riots among Hindus and Muslims are the most famous but there is a difference between caste and terrorism.
The Effects Of Terrorism
Terrorism spreads fear in people, people living in the country feel insecure because of terrorism. Due to terrorist attacks, millions of goods are destroyed, the lives of thousands of innocent people are lost, animals are also killed. Disbelief in humanity raises after seeing a terrorist activity, this gives birth to another terrorist. There exist different types of terrorism in different parts of the country and abroad.
Today, terrorism is not only the problem of India, but in our neighboring country also, and governments across the world are making a lot of effort to deal with it. Attack on world trade center on September 11, 2001, is considered the largest terrorist attack in the world. Osama bin Laden attacked the tallest building in the world’s most powerful country, causing millions of casualties and death of thousands of people.
Get the huge list of more than 500 Essay Topics and Ideas
Terrorist Attacks in India
India has suffered several terrorist attacks which created fear among the public and caused huge destruction. Here are some of the major terrorist attacks that hit India in the last few years: 1991 – Punjab Killings, 1993 – Bombay Bomb Blasts, RSS Bombing in Chennai, 2000 – Church Bombing, Red Fort Terrorist Attack,2001- Indian Parliament Attack, 2002 – Mumbai Bus Bombing, Attack on Akshardham Temple, 2003 – Mumbai Bombing, 2004 – Dhemaji School Bombing in Assam,2005 – Delhi Bombings, Indian Institute of Science Shooting, 2006 – Varanasi Bombings, Mumbai Train Bombings, Malegaon Bombings, 2007 – Samjhauta Express Bombings, Mecca Masjid Bombing, Hyderabad Bombing, Ajmer Dargah Bombing, 2008 – Jaipur Bombings, Bangalore Serial Blasts, Ahmedabad Bombings, Delhi Bombings, Mumbai Attacks, 2010 – Pune Bombing, Varanasi Bombing.
The recent ones include 2011 – Mumbai Bombing, Delhi Bombing, 2012 – Pune Bombing, 2013 – Hyderabad Blasts, Srinagar Attack, Bodh Gaya Bombings, Patna Bombings, 2014 – Chhattisgarh Attack, Jharkhand Blast, Chennai Train Bombing, Assam Violence, Church Street Bomb Blast, Bangalore, 2015 – Jammu Attack, Gurdaspur Attack, Pathankot Attack, 2016 – Uri Attack, Baramulla Attack, 2017 – Bhopal Ujjain Passenger Train Bombing, Amarnath Yatra Attack, 2018 Sukma Attack, 2019- Pulwama attack.
Agencies fighting Terrorism in India
Many police, intelligence and military organizations in India have formed special agencies to fight terrorism in the country. Major agencies which fight against terrorism in India are Anti-Terrorism Squad (ATS), Research and Analysis Wing (RAW), National Investigation Agency (NIA).
Terrorism has become a global threat which needs to be controlled from the initial level. Terrorism cannot be controlled by the law enforcing agencies alone. The people in the world will also have to unite in order to face this growing threat of terrorism.
Customize your course in 30 seconds
Which class are you in.

- Travelling Essay
- Picnic Essay
- Our Country Essay
- My Parents Essay
- Essay on Favourite Personality
- Essay on Memorable Day of My Life
- Essay on Knowledge is Power
- Essay on Gurpurab
- Essay on My Favourite Season
- Essay on Types of Sports
Leave a Reply Cancel reply
Your email address will not be published. Required fields are marked *
Download the App

- Election 2024
- Entertainment
- Newsletters
- Photography
- Personal Finance
- AP Investigations
- AP Buyline Personal Finance
- Press Releases
- Israel-Hamas War
- Russia-Ukraine War
- Global elections
- Asia Pacific
- Latin America
- Middle East
- Election Results
- Delegate Tracker
- AP & Elections
- March Madness
- AP Top 25 Poll
- Movie reviews
- Book reviews
- Personal finance
- Financial Markets
- Business Highlights
- Financial wellness
- Artificial Intelligence
- Social Media
A knife attack in Australia against a bishop and a priest is being treated as terrorism, police say
Australian police say suspect arrested after reported stabbing at church in Sydney

Australian police say a knife attack in Sydney that wounded a bishop and a priest during a church service as horrified worshippers watched online and in person and sparked a riot, was an act of terrorism.

Australian Prime Minister Anthony Albanese described a knife attack in Sydney against two clergymen on Tuesday as “disturbing”. Australian police say the attack in a western Sydney church is being treated as terrorism.

The premier of Australia’s New South Wales state has warned the community in Western Sydney not take the law into their own hands after police declared Monday’s stabbings at a Sydney church a “terrorist incident”.

Police in the Australian State of New South Wales have declared Monday’s stabbings at a Sydney church a “terrorist incident”.
Security officers stand guard outside Orthodox Assyrian church in Sydney, Australia, Monday, April 15, 2024. Police in Australia say a man has been arrested after a bishop and churchgoers were stabbed in the church. There are no life-threatening injuries. (AP Photo/Mark Baker)
- Copy Link copied
Police officers check vandalized vehicles, including theirs, outside a church where a bishop and churchgoers were reportedly stabbed in Sydney Australia, Monday, April 15, 2024. Police in Australia say a man has been arrested after a bishop and churchgoers were stabbed in the church. There are no life-threatening injuries. (AP Photo/Mark Baker)
Policemen stand guard outside a church where a bishop and churchgoers were reportedly stabbed in Sydney Australia, Monday, April 15, 2024. Police in Australia say a man has been arrested after a bishop and churchgoers were stabbed in the church. There are no life-threatening injuries. (AP Photo/Mark Baker)
Policeman stand guard outside a church where a bishop and churchgoers were reportedly stabbed in Sydney Australia, Monday, April 15, 2024. (AP Photo/Mark Baker)
Policeman stand guard outside a church where a bishop and churchgoers were reportedly stabbed in Sydney Australia, Thursday, May 25, 2023. (AP Photo/Mark Baker)
A Police car is seen vandalised outside a church where a bishop and churchgoers were reportedly stabbed in Sydney Australia, Monday, April 15, 2024. (AP Photo/Mark Baker)
A policeman stands guard outside a church where a bishop and churchgoers were reportedly stabbed in Sydney Australia, Monday, April 15, 2024. (AP Photo/Mark Baker)
Security officers stand guard outside a church where a bishop and churchgoers were reportedly stabbed in Sydney Australia, Monday, April 15, 2024. (AP Photo/Mark Baker)
Riot police drives away after securing outside a church where a bishop and churchgoers were reportedly stabbed in Sydney Australia, Monday, April 15, 2024. Police in Australia say a man has been arrested after a bishop and churchgoers were stabbed in the church. There are no life-threatening injuries. (AP Photo/Mark Baker)
The Sydney Opera House is illuminated with a black ribbon Monday, April 15, 2024, as part of the national day of mourning following the stabbing deaths of several people at a shopping mall on April 13. Australian police are examining why a lone assailant who stabbed several people to death in a busy Sydney shopping mall and injured more than a dozen others targeted women while avoiding men. (AP Photo/Mark Baker)
A police officer investigates in a church where a bishop and churchgoers were reportedly stabbed in Sydney Australia, Monday, April 15, 2024. Police in Australia say a man has been arrested after a bishop and churchgoers were stabbed in the church. There are no life-threatening injuries. (AP Photo/Mark Baker)
Police officers check vandalized vehicles outside a church where a bishop and churchgoers were reportedly stabbed in Sydney Australia, Monday, April 15, 2024. Police in Australia say a man has been arrested after a bishop and churchgoers were stabbed in the church. There are no life-threatening injuries. (AP Photo/Mark Baker)
SYDNEY (AP) — Australian police say a knife attack in Sydney that wounded a bishop and a priest during a church service as horrified worshippers watched online and in person, and sparked a riot was an act of terrorism.
Police arrested a 16-year-old boy Tuesday after the stabbing at Christ the Good Shepherd Church that injured Bishop Mar Mari Emmanuel and a priest. Both are expected to survive.
Security officers stand guard outside Orthodox Assyrian church in Sydney, Australia, Monday, April 15, 2024. (AP Photo/Mark Baker)
New South Wales Police Commissioner Karen Webb said the suspect’s comments pointed to a religious motive for the attack.
“We’ll allege there’s a degree of premeditation on the basis that this person has travelled to that location, which is not near his residential address, he has travelled with a knife and subsequently the bishop and the priest have been stabbed,” Webb said. “They’re lucky to be alive.”
The teenager was known to police but was not on a terror watch list, Webb said.
The Australian Security Intelligence Organization, the nation’s main domestic spy agency, and Australian Federal Police had joined state police in a counter-terrorism task force to investgate who else was potentially involved.
ASIO director-general Mike Burgess said the investigation had yet to uncover any associated threats.
“It does appear to be religiously motivated, but we continue our lines of investigation,” Burgess said.
“Our job is to look at individuals connected with the attacker to assure ourselves that there is no-one else in the community with similar intent. At this stage, we have no indications of that,” Burgess added.
On ASIO’s advice, the risk of a terrorist attack in Australia is rated at “possible.” That is the second lowest level after “not expected” on the five-tier National Terrorism Threat Advisory System.
The boy had been convicted in January of a range of offenses including possession of a switch blade knife, being armed with a weapon with an intention to commit an indictable offence, stalking, intimidation and damaging property, Australian Broadcasting Corp. reported.
A Sydney court released him on a good behavior bond, the ABC reported.
The boy had also used a switch blade, which is an illegal weapon in Australia, in Monday’s attack, the ABC reported.
Juvenile offenders cannot be publicly identified in New South Wales state.
In response to the attack, Prime Minister Anthony Albanese said “there is no place for violence in our community. There’s no place for violent extremism.”
The Christ the Good Shepherd in suburban Wakeley streams sermons online and worshippers watched as a person in black clothes approached the altar and stabbed the bishop and priest Isaac Royel during a church service Monday evening before the congregation overpowered him, police said.
A crowd of hundreds seeking revenge gathered outside the Orthodox Assyrian church, hurling bricks and bottles, injuring police officers and preventing police from taking the teen outside, officials said.
The teen suspect and at least two police officers were also hospitalized, Acting Assistant Police Commissioner Andrew Holland told journalists.
Paramedics treated 30 patients, with seven taken to hospitals, NSW Ambulance commissioner Dominic Morgan said.
“This was a rapidly evolving situation where the crowds went from 50 to a number of hundreds of people in a very rapid period of time,” Morgan said.
“Our paramedics became directly under threat ... and had to retreat into the
church,” Morgan added.
The church in a message on social media said the bishop and priest were in stable condition and asked for people’s prayers. “It is the bishop’s and father’s wishes that you also pray for the perpetrator,” the statement said.
Holland commended the congregation for subduing the teen before calling police. When asked if the teen’s fingers had been severed, he said the hand injuries were “severe.”
More than 100 police reinforcements arrived before the teen was taken from the church in the hours-long incident. Several police vehicles were damaged, Holland said.
“A number of houses have been damaged. They’ve broken into a number of houses to gain weapons to throw at the police. They’ve thrown weapons and items at the church itself. There were obviously people who wanted to get access to the young person who caused the injuries to the clergy people,” he said.
Australians were still in shock after a lone assailant stabbed six people to death in a Sydney shopping mall on Saturday and injured more than a dozen others.
Holland suggested the weekend attack heightened the community’s response to the church stabbing.
“Given that there has been incidents in Sydney the last few days with knives involved, obviously there’s concerns,” he said. “We’ve asked for everyone to think rationally at this stage. “
The church said in a statement on Tuesday the 53-year-old Iraq-born bishop’s condition was “improving.”
Emmanuel has a strong social media following and is outspoken on a range of issues. He proselytizes to both Jews and Muslims and is critical of liberal Christian denominations.
He also speaks out on global political issues and laments the plight of Palestinians in Gaza.
The bishop, described in local media as a figure sometimes seen as divisive on issues such as COVID-19 restrictions, was in national news last year with comments about gender.
A video posted in May 2023 by the ABC about a campaign targeting the LGBTQ+ community showed the bishop in a sermon saying that “when a man calls himself a woman, he is neither a man nor a woman, you are not a human, then you are an it. Now, since you are an it, I will not address you as a human anymore because it is not my choosing, it your choosing.”
McGuirk reported from Melbourne, Australia.

Symposium to Explore Significance of 18th-Century Philosopher’s Essay on Perpetual Peace in Today’s World

A one-day symposium April 19, supported by the Central New York Humanities Corridor, will explore how philosopher Immanuel Kant’s 1795 essay “Toward Perpetual Peace” can help lay the foundation for lasting peace.
Philosopher Immanuel Kant’s 1795 essay “Toward Perpetual Peace” still holds significant relevance even now more than two centuries after it was first published. With ongoing wars across the globe, securing peace remains elusive.
An upcoming one-day symposium will explore how Kant’s principles can help lay the foundation for lasting peace. The symposium is supported by the Central New York Humanities Corridor , whose administrative home is based at the Syracuse University Humanities Center . The event, “ The Contemporary Relevance of Perpetual Peace, ” will be held Friday, April 19, at Cornell University, with a symposium and workshop on one of Kant’s most widely read essays, Zum ewigen Frieden (“Toward Perpetual Peace”).
The symposium, as part of the Perpetual Peace Project , is organized by Gregg Lambert , Dean’s Professor of the Humanities in the College of Arts and Sciences and a founder and co-director of the Perpetual Peace Project, and Peter Gilgen , director of the Institute for German Cultural Studies and associate professor in the Department of German Studies and Graduate Field of Comparative Literature at Cornell University.
The Perpetual Peace Project, an ongoing international forum on the concept of peace, began as an initiative of the Humanities Center in 2008.

Gregg Lambert
“The purpose of the project is to raise awareness and attention to the fact that war is not one regional issue,” Lambert says. “It is a global issue, and the number of wars only seems to increase each year.”
Open to the public, Friday’s symposium, which also is a celebration of Kant’s 300th birthday, will begin with three individual papers that examine different aspects of Kant’s treatise and its contemporary relevance.
“Kant’s popular essay was reviewed and cited as an inspiration by numerous thinkers from the start,” Gilgen says. “Anyone thinking about peace and what it means and implies had/has to take Kant’s profound remarks into account.”
The treatise served as an inspiration for the League of Nations, the first worldwide intergovernmental organization, founded in 1920, as well as its successor organization, the United Nations, in 1945.
“At the symposium, we hope to draw on a wide audience interested in Kant’s political philosophy as well as the theory and practice of peace—a topic that could not be more timely in light of the many ongoing conflicts in different parts of the world,” Gilgen says.

Peter Gilgen
The second half of the event is dedicated to a workshop on the Perpetual Peace Project.
Lambert, who is also founding director of the Syracuse University Humanities Center in the College of Arts and Sciences, and Adam Nocek , associate professor in the School of Arts, Media and Engineering, Arizona State University, and co-director of the Perpetual Peace Project, will present the workshop, which will launch the Perpetual Peace Academy. The academy will feature a curriculum created by faculty from all over the world, contributing designs of courses that they would teach in a virtual setting.
“We are really trying to engage students on all campuses and other participants in talking about the Perpetual Peace Project, and then we’re going to inaugurate the Perpetual Peace Academy,” Lambert says. “The academy will be driven by international faculty who want to contribute their ideas from across the disciplines.”
Along with his presence at the symposium, Nocek also joined Lambert in Lambert’s undergraduate seminar, Problems in Marxism: Perpetual Peace , Tuesday for a discussion with students, and other participants, about the Perpetual Peace Academy. Nocek’s time at the symposium and in the seminar is supported as part of Syracuse University’s Distinguished Visiting Collaborator (DVC) initiative of the CNY Humanities Corridor.

Vivian May, director of the SU Humanities Center and lead director of the CNY Humanities Corridor, says the scholar mini-residency bridges the Syracuse University campus with another corridor campus, a model that deepens collaborative networks.
“In conversation with Lambert, Gilgen, and a range of other interlocutors over the course of his visit, Adam Nocek , founding director of the Center for Philosophical Technologies at Arizona State University, will discuss the importance of philosopher Immanuel Kant’s yet-to-be-realized concept of ‘perpetual peace,’” May says. “I encourage everyone who can to engage with this year’s DVC events and activities, as they offer an important opportunity for us to step back, refuse broad acceptance of violence and devastation, and actively pursue planetary peace—a peace that centers climate justice and holistic thriving.”
Since its start in 2008, the Perpetual Peace Project, structured around Kant’s six preliminary articles, has gone through three phases, with the first at Syracuse University and the United Nations in New York. This first phase included a co-edited and re-issue of a new book publication of Kant’s “Perpetual Peace” and several different events.
In partnership with the Humanities Center and the Centre for Humanities at Utrecht University in the Netherlands, the second phase from 2013-15 included a series of events commemorating the Treaty of Utrecht and a documentary film.

This latest phase has reinaugurated the project following the invasion of Ukraine by Russia in 2022. Lambert partnered with Nocek to kick off this latest phase, including a launch event conference at the University of Warsaw, Poland, followed by conferences at the Institute of Philosophy of the Czech Academy and the Jan Evangelista Purkyně University in Ústí nad Labem, both in the Czech Republic.
Friday’s symposium features a presentation by Gilgen, moderated by Elke Siegel, German studies, Cornell; a presentation by Patchen Markell, associate professor, government, Cornell, and moderated by Karin Nisenbaum , Renée Crown Professor in the Humanities and assistant professor, College of Arts and Sciences, Syracuse University; and a presentation by Neil Saccamano, associate professor, literatures in English, Cornell, and moderated by Verena Erlenbusch-Anderson , associate professor, philosophy, College of Arts and Sciences, Syracuse University.
For this latest phase, Lambert edited a new version of Kant’s original treatise, which has been published and is available for event participants.
Kathleen Haley
- Chancellor Syverud Provides Updates to University Senate on Shared Governance Related to Honorary Degrees, Benefits, Sustainability and Athletics Thursday, April 18, 2024, By News Staff
- Professor Receives NSF CAREER Award to Research Context Sensitive Fuzzing for Networked Systems Thursday, April 18, 2024, By Kwami Maranga
- Department of Public Safety Seeking Community Feedback Thursday, April 18, 2024, By News Staff
- 5 Students Use Couri Hatchery to Prepare for New York Business Plan Competition Wednesday, April 17, 2024, By Dawn McWilliams
- Victory for Veterans: Law Expert Reacts to Supreme Court Decision Wednesday, April 17, 2024, By Vanessa Marquette
More In Media, Law & Policy
College of law to add housing clinic for fall 2024.
The College of Law is adding a Housing Clinic to its clinical legal education offerings beginning in the Fall 2024 semester. The Housing Clinic will operate in partnership with Legal Services of Central New York and the Legal Aid Society…
The Power of Curiosity Fuels Award-Winning News Anchor Mary Calvi ’90
Mary Calvi’s early path to become an award-winning news reporter and anchor is a familiar one: Calvi ’90 fell in love with journalism at a young age, cultivated an intense curiosity and became determined to cover the news. But it…
Pollster Joins Maxwell School Panel to Explore Super Tuesday and Beyond
The 2024 presidential race between frontrunners President Joe Biden and former President Donald Trump is the “highest intensity, lowest interest” race Maxwell alumnus John Zogby G’74 said he has seen in his 40-plus years of leading national public opinion polls….
Data Journalism Project Launches, Focuses on Impact of Police Vehicle Accidents in New York
Police vehicle accidents and the impact such crashes have had on communities across New York State are the focus of a new data journalism project involving Newhouse School students working in partnership with reporters from the USA Today Network and Central Current….
IDJC Receives Neo4j Research Grant to Track 2024 Campaign Misinformation
The Institute for Democracy, Journalism and Citizenship (IDJC) has been awarded a $250,000 research grant from Neo4j and use of the company’s graph database technology as part of an initiative to identify misinformation trends in the U.S. presidential election and…
Subscribe to SU Today
If you need help with your subscription, contact [email protected] .
Connect With Us
For the media.
- Share full article
Advertisement
Supported by
Guest Essay
I Hope to Repeal an Arcane Law That Could Be Misused to Ban Abortion Nationwide

By Tina Smith
Ms. Smith is a Democratic senator from Minnesota and a former Planned Parenthood executive.
A long discredited, arcane 150-year-old law is back in the news in 2024, and that should terrify anyone who supports reproductive freedom. Last week at the Supreme Court, the Comstock Act of 1873 was referenced on three separate occasions during oral arguments in a case dealing with access to mifepristone, one of two drugs typically used in medication abortions.
Anti-abortion activists like to bring up the Comstock Act because one of its clauses prohibits sending through the mail “every article, instrument, substance, drug, medicine or thing” that could possibly lead to an abortion. Even if the Supreme Court doesn’t take the bait, a newly re-elected President Trump could order his Department of Justice to start interpreting that line to mean that it is illegal to mail mifepristone — a safe, effective, Food and Drug Administration-approved drug — to doctors and pharmacies, as well as to patients directly. The same could go for medical supplies that are used in performing surgical abortions. That could effectively make abortion impossible to access even in places like Minnesota, which has affirmatively protected a woman’s right to choose by passing reproductive freedom laws.
In response, I’m prepared to fight back — including by introducing legislation to take away the Comstock Act as a tool to limit reproductive freedom.
Let me take a step back and explain how ridiculous it is that we’re even talking about this legislative relic today. The Comstock Act hasn’t been broadly enforced since the 1930s. The Biden administration considers it utterly irrelevant. Many legal experts consider it dead letter law. And once you know its back story, it becomes clear why no one has paid much attention to it in nearly a century.
Back in the 1860s, a former Civil War soldier from rural Connecticut named Anthony Comstock moved to New York City for work. He was shocked and appalled by what he found. Advertisements for contraception! Open discussions of sexual health! It all struck Comstock as terribly lewd and anti-Christian.
So he made it his mission to clean up society, creating the loftily named New York Society for the Suppression of Vice and gathering evidence for police raids on places that distributed material he thought was obscene or promoted indecent living. In the early 1870s he took his crusade to Washington, lobbying for federal legislation that would empower the post office to search for and seize anything in the mail that met Comstock’s criteria for being “obscene,” “lewd” or just plain “filthy.” Morality, as determined by Comstock, would be the law of the land, and Comstock himself would be its enforcer, appointed by Congress as a special agent of the post office.
In a fit of Victorian puritanism, Congress passed the Comstock Act into law. But it quickly became apparent that Comstock’s criteria were unworkably vague. In its broad wording, the law not only made it illegal to send pornography through the mail, it also outlawed the sending of medical textbooks for their depictions of the human body, personal love letters that hinted at physical as well as romantic relationships, and even news stories.
The whole thing was very silly and impracticable, and that’s why the Comstock Act was relegated to the dustbin of history.
But conservative activists recently revived it from obscurity as part of their playbook for a potential second Trump term: The 887-page plan nicknamed Project 2025 being promoted by groups like the Heritage Foundation explicitly calls for a newly elected second-term President Trump to use this zombie law to severely ratchet back abortion access in America without congressional action.
Legislation to repeal Comstock could take many forms, and we need to do it the right way. That’s why I’ve begun reaching out to my colleagues in the House of Representatives and the Senate to build support and see what legislation to repeal the Comstock Act might look like. Anti-abortion extremists will continue to exploit any avenue they can find to get the national ban they champion, and I want to make sure my bill shuts down every one of those avenues. Once the Supreme Court has had its say (and many legal analysts speculate that the mifepristone case heard last week should be thrown out on procedural grounds, and may well be), I’ll be ready to have mine.
Here’s the bottom line: We can’t let anyone — not the Supreme Court, not Donald Trump and certainly not a random busybody from the 19th century — take away Americans’ right to access medication abortion. We must protect the ability of doctors, pharmacies and patients to receive in the mail the supplies they need to exercise their right to reproductive care.
As the only former Planned Parenthood executive serving in the Senate, I feel I have a special responsibility to protect not just abortion rights but also abortion access.
Very few Republicans will admit to wanting to see a total, no-exceptions ban on abortion in all 50 states, but the Comstock Act could allow them to achieve that in effect, if not in so many words.
Americans deserve better. The Constitution demands better. And common sense dictates that we stop this outrageous backdoor ploy to eliminate abortion access in its tracks.
Tina Smith is a Democratic senator from Minnesota and a former Planned Parenthood executive.
The Times is committed to publishing a diversity of letters to the editor. We’d like to hear what you think about this or any of our articles. Here are some tips . And here’s our email: [email protected] .
Follow the New York Times Opinion section on Facebook , Instagram , TikTok , WhatsApp , X and Threads .

IMAGES
VIDEO
COMMENTS
Before briefly tracing the history of international responses to terrorism, this essay presents observations on the question of definition or nomenclature. The first quality worth remarking on is the sheer diversity and range of activities encompassed by even restrictive notions of terrorism. In international law, for example, terrorism is
conducive to the spread of terrorism, including the lack of rule of law and violations of human rights, ethnic, national and religious discrimination, political exclusion, and socio-economic marginalization; to foster the active participation and leadership of civil society; to condemn human rights violations, prohibit them in national law ...
Christopher P. Costa draws on experience with international terrorism to raise the need to combat hyper-tribalism that is driving domestic terrorism. Amb. Nathan A. Sales points to the advantages of counterterrorism partnerships, even in an era of great-power competition. Mary B. McCord calls for taking on the insider threat within law enforcement.
By John C. Yoo∗ & James C. Ho+. This paper will identify and discuss two legal questions raised by the war on terrorism that have generated significant controversy among academics and public commentators. First, did the September 11, 2001 attacks initiate a war, or "international armed conflict" to use the vocabulary of modern public ...
Domestic Terrorism: Overview of Federal Criminal Law and Constitutional Issues Congressional Research Service 2 crime, however, under numerous statutes prohibiting terrorism6 and other types of violent or destructive conduct.7 In addition, domestic terrorism may be relevant to the sentencing of those convicted of federal crimes.8 Any congressional consideration of additional legislation in the ...
Extract from ICRC publication "International humanitarian law: answers to your questions". IHL does not provide a definition of 'terrorism', but prohibits most acts committed in armed conflict that would commonly be considered 'terrorist'. It is a basic principle of IHL that persons fighting in armed conflict must, at all times, distinguish ...
The purpose of this chapter is not to describe the terrorist phenomenon, but rather to analyse the range of responses to it and their compliance with human rights law. This analysis necessarily takes into consideration the legal nature of terrorism under international law and its rapid transformations in the aftermath of the terrorist attacks ...
Abstract. This chapter focuses on international law as it applies to terrorism. It notes the lack of an internationally accepted definition of terrorism in international law and outlines the scope of states' duties to prevent and repress terrorism while complying with international humanitarian law (IHL), international humanitarian rights law (IHRL), and international refugee law (IRL).
For much terrorism scholarship (critical and otherwise), then, the existence of far-right terrorism and extremism is ontologically distinct from the labelling of specific actors, events or threats thus. This means that the fundamentally discursive existence of those actors and events is rarely explicitly acknowledged.
Statement of Christine Beerli, ICRC Vice-President at the 17th edition Bruges Colloquium , 20 -21 october 2016 Terrorism is a scourge to which the international community has been striving to respond for decades. The obvious challenges it poses are not only long-lasting, but also immediate. Wherever we turn these days, across the world, we are confronted with increased risks of terrorist acts ...
1. Introduction. Terrorism is the premeditated use or threat to use violence by individuals or subnational groups to obtain a political or social objective through the intimidation of a large audience beyond that of the immediate noncombatant victims (Enders and Sandler, 2012, p.4).The two essential ingredients of terrorism are its violence and its political or social motive.
In the last two decades, governments have increasingly adopted legislation that criminalizes the preparation, facilitation and incitement of terrorism — as well as a range of administrative measures such as watchlists and the deprivati… of nationality. Some of these efforts pose serious challenges to human rights and the rule of law. By ensuring that counter-terrorism laws and measures are ...
Introduction. Terrorism has been the most prominent security issue since the start of the new millennium. Footnote 1 Since 2014, series of deadly attacks in France, Belgium, Germany, the United States, and Great Britain have fueled new anxieties about terrorist incidents, particularly in Western countries. That the terrorism label has remained ambiguous and contentious, with hundreds of ...
This paper researches on terrorism and counter-terrorism in the context of human rights. It puts the real scenario of how victims and perpetrators of terrorism are treated (or should be treated) with regard to fundamental aspects of human rights. Introduction. In as much as terrorism has a direct effect on human rights, recent years have ...
Essay . CONSIDERING A DOMESTIC TERRORISM STATUTE AND ITS ALTERNATIVES † Francesca Laguardia . ABSTRACT—Recent years have seen an increase in right-wing extremist violence within the United States, which has highlighted the disparities in law enforcement's handling of "international" as opposed to "domestic" terrorism.
Introduction. The academic study of terrorism is often described as beset by numerous and pervasive conceptual and methodological problems. Footnote 1 Critiques of the state of the art have appeared since the 1970s and their conclusions have been worryingly similar. Footnote 2 One of these is that the definitional debate on what exactly constitutes terrorism continues to exert a detrimental ...
Terrorism, the calculated use of violence to create a general climate of fear in a population and thereby to bring about a particular political objective. Definitions of terrorism are complex and controversial; because of the inherent ferocity of terrorism, the term in its popular usage has developed an intense stigma.
The law on terrorism in the United Kingdom has been described as 'an unmitigated disaster' [1]. In todays society the threat of terrorism is at a dangerous level and the legislation in place has been unstable to say the least. Much criticism is to do with the compatibility of the legislation with the ECHR [2].
Below is the article summary. For the full article, see terrorism . terrorism, Systematic use of violence to create a general climate of fear in a population and thereby to bring about a particular political objective. It has been used throughout history by political organizations of both the left and the right, by nationalist and ethnic groups ...
The findings of this study suggest that globalization has contributed to the rise of terrorism, and that its impacts on global peace and. security are complex and multi-faceted. The impact of ...
This page of the essay has 4,254 words. Download the full version above. Introduction. Spain, Iraq, Syria, Egypt, Lebanon, Turkey and now also Belgium and France are one of the countries who are victims of horrifying terrorist attacks. Terrorism used to be sporadic, however, during the years 2013-2016, terrorist attacks evolved into systematic ...
After the attacks of Sept. 11, 2001, President George W. Bush secretly ordered a warrantless wiretapping program code-named Stellarwind. It violated the Foreign Intelligence Surveillance Act of ...
The loss of our beloved ones, the loss of the right personnel, the economic instability of our country and many others are some of the bad impacts of terrorism. As a result of this, a lot of pressure from citizens has been imparted on the local law enforcement agencies. This has forced law enforcement agencies to reposition their line of work ...
Third: what are the implications for constitutional theory of our natural-law moment? This essay sketches answers to these questions, with the caveat that much more could be said about them. This essay was originally delivered as the Herbert W. Vaughan Memorial Lecture at Harvard Law School on April 9, 2024.
500+ Words Essay on Terrorism Essay. Terrorism is an act, which aims to create fear among ordinary people by illegal means. It is a threat to humanity. It includes person or group spreading violence, riots, burglaries, rapes, kidnappings, fighting, bombings, etc. Terrorism is an act of cowardice. Also, terrorism has nothing to do with religion.
April 10, 2024. Right-wing House Republicans on Wednesday blocked legislation to extend an expiring warrantless surveillance law that national security officials call crucial to gathering ...
BBC World Service files urgent appeal to UN over abuse of national security and counter-terrorism laws against BBC News Persian journalists. For the first time, the complaint is addressed to the ...
Updated 9:51 AM PDT, April 15, 2024. SYDNEY (AP) — Horrified worshipers watched online and in person as a 15-year-old boy stabbed a bishop and a priest during a church service in Sydney on Monday evening before the congregation overpowered him, police said. A crowd of hundreds seeking revenge gathered outside the Orthodox Assyrian church ...
Open to the public, Friday's symposium, which also is a celebration of Kant's 300th birthday, will begin with three individual papers that examine different aspects of Kant's treatise and its contemporary relevance. "Kant's popular essay was reviewed and cited as an inspiration by numerous thinkers from the start," Gilgen says.
A long discredited, arcane 150-year-old law is back in the news in 2024, and that should terrify anyone who supports reproductive freedom. Last week at the Supreme Court, the Comstock Act of 1873 ...