Sorry, we did not find any matching results.
We frequently add data and we're interested in what would be useful to people. If you have a specific recommendation, you can reach us at [email protected] .
We are in the process of adding data at the state and local level. Sign up on our mailing list here to be the first to know when it is available.

Search tips:
• Check your spelling
• Try other search terms
• Use fewer words
The state of domestic terrorism in the US
The number of domestic terrorist investigations more than doubled between 2020 and 2021.
Updated on Fri, August 4, 2023 by the USAFacts Team
The incidence of domestic terrorism has sharply increased in the United States over the past decade.
From high-profile incidents like the US Capitol attack on January 6, 2021 to racially motivated acts of violence, these events have shed light on the need to understand and address the threat of domestic terrorism .
What is domestic terrorism?
According to the FBI, domestic terrorism encompasses violent, criminal acts that individuals and/or groups use to further their ideological goals from political, social, racial, or environmental influences within the country’s borders. [1]
These acts appear to be intended to:
- Intimidate or coerce a civilian population;
- Influence the policy of a government by intimidation or coercion; or
- Affect the conduct of a government by mass destruction, assassination, or kidnapping.
These individuals and groups are separated into five different threat categories, which help officials understand the motives of criminal actors better. These categories include:
- Racially or ethnically motivated violent extremism;
- Anti-government or anti-authority violent extremism;
- Animal rights/environmental violent extremism;
- Abortion-related violent extremism;
- All other domestic terrorist threats, with agendas such as personal grievances, or bias related to religion, gender, or sexual orientation.
It’s important to note that rather than being charged with domestic terrorism, prosecutors use other federal and state charges to prosecute people indicted in federal domestic terrorism–related cases.
How many domestic terrorism events occur in the US?
According to the Government Accountability Office , there were 231 domestic terrorism incidents with known offenders between 2010 and 2021, with the number of incidents generally increasing over time.

There were also 145 deaths and 370 injuries caused by domestic terrorism-related incidents with known offenders. Of these, 94 deaths and 111 injuries came from racially or ethnically motivated violent extremists, making up the largest category of incidents over this period. These attacks were often the most lethal of any threat category, such as the racially motivated shootings of police officers in Dallas, Texas in July 2016 and grocery shoppers in Buffalo, New York in May 2022.
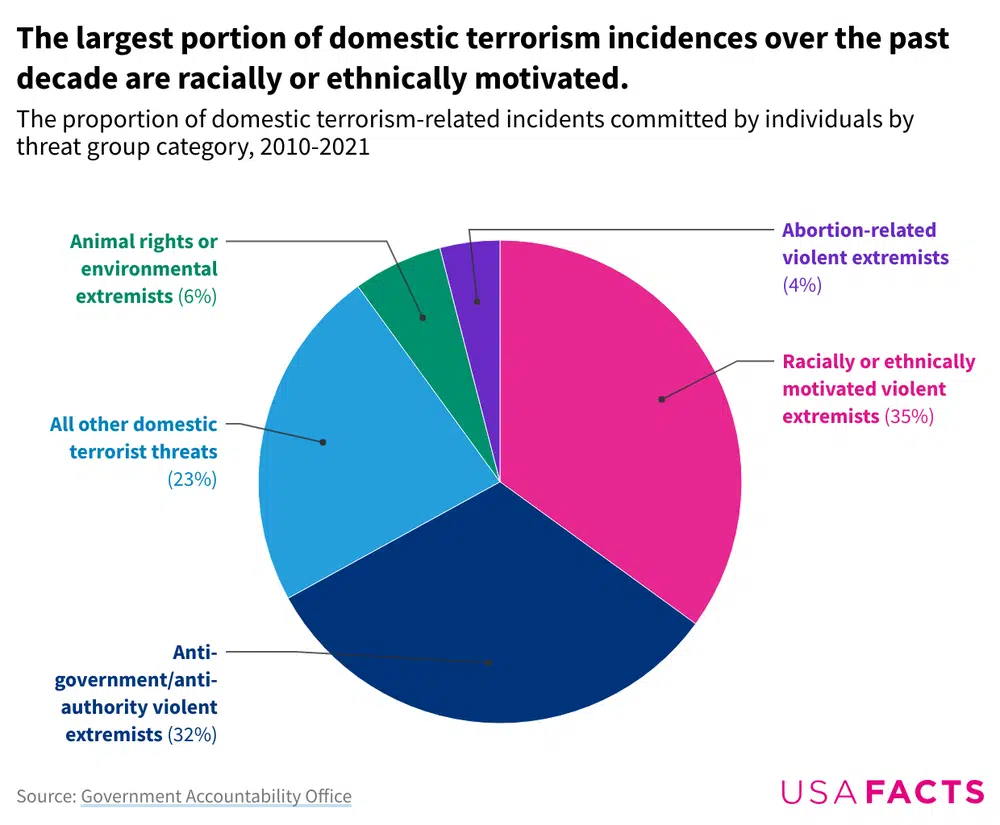
The second largest category, anti-government or anti-authority motivated violent extremism, resulted in 15 deaths during the same period.
The number of federal defendants charged in domestic terrorism-related cases stayed relatively stable before 2019 but rose in 2020 and then double in 2021. An unusually high number of federal cases from 2021 were filed in Washington, DC, although the data does not identify which of these cases are related to the US Capitol attack in January of that year.

How has the government responded to domestic terrorism?
The FBI is tasked with leading domestic terrorism–related investigations and collaborates with the Department of Homeland Security’s (DHS) Office of Intelligence and Analysis to identify internal threats to national security.
The FBI has a growing number of open domestic terrorism–related cases, with a growth rate of 357% from 2013 to 2021. This rate rose sharply beginning in 2018.
The number of potential domestic terrorist attacks which have been interrupted rose roughly around the same time. A disruption is the interruption or inhibition of a threat actor from engaging in a criminal or national security–related activity.

In 2019, the DHS released a strategic counterterrorism framework that included increased information sharing between internal agencies, such as the FBI and CIA, to closely monitor how homegrown terrorist organizations are influenced by foreign actors and identify potential perpetrators of hate crimes early on, among other preventative actions.
Get an overview of crime in the US , see how gun homicides have reached rates not seen since the 1990s , and get data like this weekly by subscribing to our free newsletter .
Agencies like the FBI and Department of Homeland Security use similar, but not identical, definitions of domestic terrorism.
Explore more of USAFacts
Related articles, what kinds of property crime are on the rise.

Firearm background checks: Explained

The latest government data on school shootings
How many guns are made in the us.
Related Data

Violent crimes
1.31 million

Hate crime incidents

Hate crime known offenders
Data delivered to your inbox.
Keep up with the latest data and most popular content.
SIGN UP FOR THE NEWSLETTER
Programs submenu
Regions submenu, topics submenu, poni 2024 capstone conference, dod's gaza pier and the maritime corridor—gaza: the human toll, lessons from myanmar.
- Abshire-Inamori Leadership Academy
- Aerospace Security Project
- Africa Program
- Americas Program
- Arleigh A. Burke Chair in Strategy
- Asia Maritime Transparency Initiative
- Asia Program
- Australia Chair
- Brzezinski Chair in Global Security and Geostrategy
- Brzezinski Institute on Geostrategy
- Chair in U.S.-India Policy Studies
- China Power Project
- Chinese Business and Economics
- Defending Democratic Institutions
- Defense-Industrial Initiatives Group
- Defense 360
- Defense Budget Analysis
- Diversity and Leadership in International Affairs Project
- Economics Program
- Emeritus Chair in Strategy
- Energy Security and Climate Change Program
- Europe, Russia, and Eurasia Program
- Freeman Chair in China Studies
- Futures Lab
- Geoeconomic Council of Advisers
- Global Food and Water Security Program
- Global Health Policy Center
- Hess Center for New Frontiers
- Human Rights Initiative
- Humanitarian Agenda
- Intelligence, National Security, and Technology Program
- International Security Program
- Japan Chair
- Kissinger Chair
- Korea Chair
- Langone Chair in American Leadership
- Middle East Program
- Missile Defense Project
- Project on Critical Minerals Security
- Project on Fragility and Mobility
- Project on Nuclear Issues
- Project on Prosperity and Development
- Project on Trade and Technology
- Renewing American Innovation Project
- Scholl Chair in International Business
- Smart Women, Smart Power
- Southeast Asia Program
- Stephenson Ocean Security Project
- Strategic Technologies Program
- Transnational Threats Project
- Wadhwani Center for AI and Advanced Technologies
- All Regions
- Australia, New Zealand & Pacific
- Middle East
- Russia and Eurasia
- American Innovation
- Civic Education
- Climate Change
- Cybersecurity
- Defense Budget and Acquisition
- Defense and Security
- Energy and Sustainability
- Food Security
- Gender and International Security
- Geopolitics
- Global Health
- Human Rights
- Humanitarian Assistance
- Intelligence
- International Development
- Maritime Issues and Oceans
- Missile Defense
- Nuclear Issues
- Transnational Threats
- Water Security
The First U.S. National Strategy for Countering Domestic Terrorism

Photo: WIN MCNAMEE/POOL/AFP/Getty Images
Critical Questions by Catrina Doxsee and Jake Harrington
Published June 17, 2021
On June 15, 2021, the Biden administration released the United States’ first-ever National Strategy for Countering Domestic Terrorism, which culminated the 100-day review of U.S. government efforts to respond to domestic extremism that President Biden ordered in January. Though galvanized by the January 6, 2021, attack on the U.S. Capitol, this strategy seeks to understand and respond to a long history of domestic terrorist activity in the United States.
Q1: What is the significance of the National Strategy for Countering Domestic Terrorism?
A1: The release of the new national strategy, as well as the broader attention and resources being directed toward countering domestic threats, is a major turning point in U.S. counterterrorism policy.
Most notably, the document codifies in national strategy that domestic violent extremists—specifically those who identify with white supremacist and anti-government militia ideology—pose the “most persistent and lethal threat” to the United States. This reflects the findings of the March 2021 joint comprehensive threat assessment on domestic violent extremism (DVE) by the Office of the Director of National Intelligence (ODNI), the Department of Justice (DOJ), and the Department of Homeland Security (DHS). This assessment is consistent with CSIS analysis , which found that extremists aligned with these ideologies perpetrated 66 percent of terrorist attacks and plots in 2020.
Previous CSIS research also found that the number of terrorist attacks and plots in the United States has grown in recent years. In 2020, that figure reached its highest level in at least a quarter century, with 94 percent of incidents committed by individuals with a domestic-focused grievance (as compared to 5 percent inspired by a Salafi-jihadist ideology). Yet, U.S. counterterrorism policy has maintained its post-9/11 focus on countering foreign Salafi-jihadist threats and homegrown terrorists inspired by groups such as al Qaeda and the Islamic State.
Q2: How will this document change U.S. counterterrorism efforts?
A2: While the strategy reemphasizes a range of techniques that have been hallmarks of U.S. counterterrorism efforts since 9/11—such as increasing information sharing with state, local, and foreign partners—the document also advocates for a new, broader approach to combat the root causes of violence in local communities and online. The strategy’s focus on confronting “long-term contributors to domestic terrorism” is the most innovative—and likely controversial—aspect of the strategy. While counterterrorism strategies issued during the Trump administration also emphasized efforts such as community outreach, resiliency, and social media literacy, this is the first document to directly tie U.S. counterterrorism efforts to broader social issues such as systemic racism, police reform, and gun control.
The document also marks a substantial shift in the way the U.S. government will design and implement violence prevention programs, previously known as countering violent extremism (CVE) efforts. Moving away from traditional CVE models focused on confronting Salafi-jihadist ideology within communities—which were heavily criticized by Arab and Muslim communities during the Obama administration—the new strategy advocates a public-health-based approach to violence prevention. This will expand the role of state and local partners, nongovernmental organizations, and nontraditional U.S. government agency partners such as the Department of Health and Human Services, the Department of Education, and the Department of Veterans Affairs in broader efforts to confront the root causes of politically motivated violence; increase individual and community resilience to extremist ideology; and build radicalization offramps.
Q3: How does the strategy define terrorism? What types of terrorist ideologies will it primarily target?
A3: The strategy does not advance or advocate for any changes in the existing definition of domestic terrorism, which has been codified in law since 2001 and is ideologically agnostic.
Under the strategy, the United States will disrupt or deter any individuals or networks who plan or perpetrate activities meeting the definition of domestic terrorism, regardless of their motivating ideology. The document provides notable examples of domestic terrorist attacks in recent years that span the ideological spectrum, including the 1995 Oklahoma City bombing, the 2016 ambush in Dallas that killed five police officers and injured nine others, the 2017 shooting at a congressional baseball practice, and the 2021 attack at the U.S. Capitol.
Q4: What are the major components of the strategy?
A4: The National Strategy for Countering Domestic Terrorism seeks to promote cross-agency coordination and collaboration at the policy level while maintaining the independent prerogatives of law enforcement agencies at all levels of government to investigate and disrupt terrorist activity.
The strategy is built around four pillars of action.
The first pillar—understanding and sharing domestic-terrorism-related information—aims to improve research and analysis on domestic terrorism trends; improve information sharing both within the government and externally, including dissemination of information to Congress and the public; and better understand and respond to domestic terrorists’ transnational connections.
The second pillar—preventing domestic terrorism recruitment and mobilization to violence—seeks to improve community and individual resilience to violence and disinformation, including through digital and information literacy; support programs that aim to disrupt radicalization pathways and terrorist recruitment efforts, including those specifically targeting veterans; improve public awareness of and access to violence reduction resources; and counter online recruitment and mobilization efforts, including through information sharing with the technology sector.
The third pillar—disrupting and deterring domestic terrorist activity—includes increased funding and personnel flexibility for the DOJ and Federal Bureau of Investigation (FBI) to support investigation and prosecution of terrorist activity; improved training, resources, and interagency cooperation and information sharing, including with agencies at the state, local, tribal, and territorial levels; consideration of additional legislative reforms; and improved screening and vetting processes for government employees.
The final pillar—confronting long-term contributors to domestic terrorism—calls upon the federal government and civil society to tackle long-term factors that shape the environment in which domestic terrorism may be perpetuated—such as racism and bigotry, gun violence, disinformation, and political polarization—or prevented—such as civic education, civic engagement, economic recovery and development, and faith in democratic institutions.
Q5: Does the strategy include the creation of any new legal authorities to designate or prosecute domestic terrorists?
A5: The strategy does not explicitly recommend any new legislation or legal authorities, but these are under consideration. Strategic Goal 3.2—assess potential legislative reforms—notes that the strategy outlines a path forward to combat domestic terrorism under existing authorities. Although the DOJ is examining options for the creation of new authorities, there are a wide range of existing statutes under which domestic terrorist attacks and plots can be prosecuted. Over the years, accused domestic terrorists have been charged under federal hate crime , explosives , and terrorism laws .
The strategy also notes that the federal government is evaluating whether certain global groups or movements that operate in part in the United States should be designated as foreign terrorist organizations (FTOs) or whether to expand efforts to include individuals and groups connected to both international and domestic terrorist activity on the Specially Designated Global Terrorists (SDGT) list. These efforts are important in light of the transnational nature of violent ideologies, particularly those associated with white identity extremism. As the strategy highlights, there are significant transnational dimensions within the broader movements that give rise to domestic terrorism, and there are tools and authorities that the United States could leverage—such as sanctions, designations, and other methods that have been effective in the fight against international terrorism—when appropriate.
Q6: Who’s in charge?
A6: No one, or everyone, depending on how you read the document. It is clear that law enforcement efforts should be conducted independently of policy efforts. The policy implementation is, as noted, diverse. It will rely on multiple federal agencies seeking to empower state, local, and nongovernmental partners to implement key components of the strategy, as well as buy-in and long-term commitment from those partners.
Q7: What are the biggest challenges to implementing the strategy?
A7: The formulation of a national, government-wide strategy to counter domestic terrorism is a strong step forward to counter this significant and growing threat. However, as this effort continues, it is likely to face both short- and long-term challenges.
The strategy repeatedly emphasizes that it will be implemented in a manner that protects privacy and free speech; however, it provides little substance to articulate how this will be accomplished. This is an exceptionally challenging space for federal, state, and local law enforcement. Although the strategy rightly highlights that there is a distinction between expressing controversial or even abhorrent opinions (which are first-amendment protected) and inciting or threatening violence (which is not), the lines between protected and unprotected speech are not always clear. This challenge of “discerning credible threats from online bravado and constitutionally protected speech” was highlighted as a significant challenge for DHS in a recent bipartisan Senate report regarding the January 6 attack on the U.S. Capitol.
Articulating the administration’s plans for reconciling this tension, and—more importantly—winning broad public support for the approach may be one of the most challenging aspects of implementation. This will particularly be the case if new legal authorities such as domestic terrorist designations are introduced, which carry the risk of infringing upon free speech and unjustly targeting political dissidents and minority groups.
In these areas, the strategy will likely face opposition, particularly in advancing legislative recommendations or securing funding for various programs. Recent bipartisan legislation to establish an independent commission on the events of January 6, 2021, failed in the Senate after GOP opposition. A bipartisan bill to enhance civic education nationwide has been bogged down by a misperception that it would require teaching of critical race theory. In the current climate, it is unlikely that any effort to pass broader legislation on domestic terrorism would succeed.
The strategy also relies heavily on external partners such as tech companies. To successfully build and leverage these partnerships, the federal government must mobilize and incentivize the private sector. This will be particularly difficult when it comes to social media companies, which are also likely to face challenges and criticism regarding privacy and censorship. Moreover, some terrorism disruption efforts—such as mitigating the effects of social media algorithms on radicalization pathways—may run counter to broader business strategies.
Finally, the effort to address the root causes of domestic terrorism is a noble but lofty goal. There will be many challenges—both political and logistical—to developing concrete policies to implement this strategy and developing metrics by which to measure success. Still, the articulation of these core challenges in a national strategy document is a significant step forward in the long-term process of grappling with the deeply ingrained factors that enable extremist ideology and violence to persist in U.S. society.
Catrina Doxsee is a program manager and research associate with the Transnational Threats Project at the Center for Strategic and International Studies (CSIS) in Washington, D.C. Jake Harrington is intelligence fellow in the International Security Program at CSIS.
Critical Questions is produced by the Center for Strategic and International Studies (CSIS), a private, tax-exempt institution focusing on international public policy issues. Its research is nonpartisan and nonproprietary. CSIS does not take specific policy positions. Accordingly, all views, positions, and conclusions expressed in this publication should be understood to be solely those of the author(s).
© 2021 by the Center for Strategic and International Studies. All rights reserved.

Catrina Doxsee

Jake Harrington
Programs & projects.

An official website of the United States government, Department of Justice.
Here's how you know
Official websites use .gov A .gov website belongs to an official government organization in the United States.
Secure .gov websites use HTTPS A lock ( Lock A locked padlock ) or https:// means you’ve safely connected to the .gov website. Share sensitive information only on official, secure websites.
Understanding Domestic Radicalization and Terrorism

In 2017, there were 10,900 terrorist attacks around the world that killed more than 26,400 people, according to the National Consortium for the Study of Terrorism and Responses to Terrorism (START). [1] The number of terrorist attacks per year in the United States in the post-September 11 era has increased from 33 in 2002 to 65 in 2017. [2] It is evident that the number of terrorist attacks and the lethality of these attacks are increasing at alarming levels within the United States and abroad, and terrorism is a pressing national issue that lies very much within a global context.
With the threat of terrorism on the rise and acts of terrorism occurring increasingly at a national and global level, it is imperative — perhaps now more than ever — that we ensure our resources are being directed to the most practical and evidence-based means of countering violent extremism. Understanding why and how people radicalize, as well as what can be done to prevent radicalization or intervene during the process, are key to countering violent extremism.
See “Defining Terrorism”
What makes this issue complex is that in the United States, terrorist acts are carried out by people who are motivated by a wide variety of ideological viewpoints, who have gone through different radicalization processes, and who have unique grievances or life experiences that lead them toward radicalization to terrorism. This, in turn, makes it difficult to target prevention and intervention efforts toward any one “vulnerable” population. Radicalization to terrorism can be motivated by extremist groups/ideologies, or it can occur at an individual level (commonly referred to as “lone wolf terrorism”). In the United States, terrorists are usually associated with one of the six most commonly known ideologies: right-wing extremism, left-wing extremism, environmental extremism, nationalist/separatist extremism, religious extremism, and single-issue extremism. [3] Further, the nature of radicalization and types of extremist attacks are dynamic, changing from year to year and from decade to decade. [4]
NIJ plays a vital role in funding research related to domestic radicalization and terrorism in the United States. As a federal leader in the field, NIJ’s work is complementary to that of the Department of Homeland Security (DHS) and Department of Defense, as well as international partners in Canada, the United Kingdom, Australia, and New Zealand, among others. Although the field of domestic radicalization and terrorism research as a whole is considered to be in its infancy (compared to other fields in criminology, such as gangs or violent crime), significant achievements have been made.
NIJ’s Terrorism and Radicalization Research
In response to the September 11 terrorist attacks, NIJ started working with the National Academies in 2002 to help craft a research agenda to move the field of terrorism research forward. NIJ funded projects that focused on:
- Developing terrorism databases for analysis.
- Improving the criminal justice response.
- Addressing potential high-risk terrorism targets.
- Examining the links between terrorism and other crimes.
- Studying the organization, structure, and culture of terrorism.
After investing in numerous projects, NIJ played a shared role in the development and longevity of numerous national and global terrorism databases (such as the American Terrorism Study and the Global Terrorism Database) and institutions (such as START at the University of Maryland, the Terrorism Research Center at the University of Arkansas, and the Triangle Center on Terrorism and Homeland Security at Duke University).
In its fiscal year 2012 appropriation, Congress directed NIJ to administer dedicated funding for “research targeted toward developing a better understanding of the domestic radicalization phenomenon, and advancing evidence-based strategies for effective intervention and prevention.” [5] Every year since then, NIJ has received similarly dedicated funding to carry out this mission. In its first five years, the goal of NIJ’s Domestic Radicalization and Terrorism research portfolio was to answer the following questions:
- What are the primary drivers of radicalization to violent extremism, and how do they vary across cohorts (e.g., by grievance, by age, by socioeconomic categories)?
- How is radicalization to violent extremism analogous to other forms of extreme violence, such as mass casualty events and gangs?
- Which policy choices or programmatic interventions prevent or reduce radicalization to violent extremism, induce disengagement from violent extremism, or support deradicalization and desistance from violent extremism?
The program aimed to answer these questions for the benefit of multiple stakeholders but considered criminal justice agencies and their community partners as the primary beneficiaries.
Between 2012 and 2019, NIJ made competitive awards for 34 projects through its annual domestic radicalization and terrorism solicitation. Three of the most common topic areas funded under these awards involve research surrounding:
- The drivers of radicalization.
- The role of the internet and social media in the radicalization and recruitment process.
- Program evaluations of extremism prevention and intervention programs.
Some of the most important findings to date come from a set of NIJ-commissioned papers that summarize key findings from approximately 15 NIJ-funded studies and an international conference. [6] For example, one paper explores research on risk factors associated with radicalization to violent extremism that was presented at an international conference in 2015. These risk factors include violent extremists in an individual’s social network, identity processes, violent extremist belief systems and narratives, group dynamics, connections with violent extremists and violent extremist material through the internet and social media, and grievances. [7]
Two papers on radicalization risk factors [8] and the radicalization process [9] emphasize the social nature of radicalization. Reasons for concern may include an individual’s associates and drastic changes in those relationships. The papers also found 16 potential risk factors associated with attempts to engage in terrorism by both group-based and lone-actor terrorists. Although lone actors tend to be more public with their grievances and their intent to do harm, [10] they share these common risk factors with group-based terrorists:
- Having a criminal history.
- Having mental health issues (or receiving a diagnosis of schizophrenia or delusional disorder).
- Being unemployed.
- Being single.
- Being a loner (or socially isolated).
- Having military experience.
Meanwhile, NIJ-funded researchers at Georgia State University compared the motive, weapon use, and behaviors of three types of terrorists — lone-actor terrorists (not related to or in contact with a terrorist group), solo terrorists (those who act alone but are related to a terror group or network), and mass murderers. They found that these individuals can be distinguished by the degree to which they interact with co-conspirators, their antecedent event behaviors, and whether (and the degree to which) they leak information prior to an attack. [11] NIJ has funded other comparative studies of extremists and gang members, as well as extremists and human traffickers, among others. [12]
NIJ has also funded program evaluations, most notably an evaluation of the first Muslim-led, community-based countering violent extremism (CVE) program. [13] Researchers at the University of Massachusetts Lowell found that peers were the most likely to notice early signs of radicalization, but they had a reduced likelihood of reporting due to a reluctance bias. The research team developed a metric tool called a “suite of measures” that pertains to various types of psychological processes, motivations, states, and social circumstances; the tool can be readily adapted to CVE program evaluations.
Although many of the questions NIJ originally sought to answer have been addressed to some degree, many uncertainties remain. For example, we have learned about many of the drivers of radicalization and the similarities and differences between terrorism and other forms of violent crime. We have also learned that a majority of recruitment and radicalization occurs via the internet and social media. However, one of the most important findings may be that there is no one-size-fits-all approach to these questions. There is no single checklist that determines whether someone is on the path to becoming a terrorist. Additionally, although there have been many takeaways from NIJ-funded evaluations of intervention and prevention programs, the implementation, replication, and evaluation of such programs are still lacking in this field.
Advancing Knowledge
Forthcoming awards and publications in NIJ’s portfolio will help further advance the field of terrorism and radicalization studies. NIJ-funded researchers at the University of Virginia are studying women who have been involved with violent extremism to identify strategies used by the Islamic State group to recruit and radicalize Western women. [14] Another project is using post-September 11 era geocoded, terrorism-related precursor data to identify where people radicalize versus where terrorist events actually take place. [15] This is especially important as some of NIJ’s previously funded research has found that approximately 60% of terrorists lived more than 30 miles away from their terrorist target. [16]
NIJ-funded researchers at the RAND Corporation are conducting interviews with the families and close friends of individuals who have radicalized. [17] These interviews will offer unique insights and perspectives from the people who were closest to the radicalized individual because they are the ones most likely to detect changes in behavior.
A recent NIJ grant will build on landmark studies from Australia and the United Kingdom to understand the dynamics of and barriers to community reporting in the United States. [18] NIJ hopes that the study resulting from this grant will bridge a large research gap by attempting to understand the triggers, thresholds, facilitators, and barriers to reporting terrorism involvement. Further, the results could potentially inform the broader issue of reporting about violence in general, as the study will compare perspectives about reporting involvement in terrorism versus involvement in nonterrorist mass violence. The potential impact on the field is expected to be high, as it would be the first study of its kind to allow for direct comparison of sentiments and issues surrounding reporting by family and close friends in the United States, the United Kingdom, and Australia.
Lastly, in 2017, NIJ began a new publication series called Notes From the Field. [19] This series serves as a platform for leading criminal justice practitioners to share promising practices and lessons learned on pressing issues. It is part of an effort by NIJ to better connect with and learn from law enforcement. Notes From the Field recently launched a series on terrorism prevention to help fill gaps in knowledge and remain on the forefront of the most cutting-edge research in the field.
NIJ’s Role at the Federal and International Levels
NIJ also plays a large role in advancing radicalization and terrorism research at the federal and international levels. The Institute is one of the leading federal agencies that fund research on this topic.
Through meetings, project collaborations, and working groups, NIJ has established successful working relationships with its national and international partners. For example, NIJ has coordinated with DHS and other federal partners through the Countering Violent Extremism Task Force. As a member of the Task Force’s Research and Analysis Working Group, NIJ shares research findings with the group and stays abreast of research priorities, gaps, and progress made across entities within the federal government. NIJ also organizes expert panels at conferences, such as the annual meetings of the International Association of Chiefs of Police and the American Society of Criminology, which helps to translate research findings directly into law enforcement practice and target and enhance future research efforts.
On an international level, NIJ is involved with the Five Country Research and Development (5RD) Network, which includes government agency representatives from Australia, Canada, New Zealand, the United Kingdom, and the United States. The group works to cooperate, collaborate, and exchange information to ensure efficiency and coordination of applied research and development work relevant to a variety of domestic security topics. The DHS Science and Technology research team leads the group, which first met in 2015 to discuss best practices and lessons learned from international partners in efforts to counter violent extremism. The 5RD participants communicate regularly to share information and coordinate efforts to develop new technologies to prevent crime, ensure security, and protect citizens.
The 5RD Network has commissioned systematic reviews of research and evaluation efforts from all five countries to build a “global evidence-base for terrorism prevention, policy, strategy, and activity.” [20] These systematic reviews will cover subtopics such as common factors leading to radicalization, online indicators of radicalization, the role of the media in the radicalization process, and how community support and societal connections influence the prevention of radicalization. Recognizing that the threat of terrorism transcends all borders and ideologies, NIJ is hopeful that the rigorous and high-quality scientific findings from these reviews will help guide policymakers and practitioners in their decision-making.
Looking Forward
NIJ’s focus for the future will be to continue funding rigorous evaluations, developing stronger baseline knowledge of radicalization processes, and informing policy and programming through research to better understand how and why people radicalize, and which programs and policies work best to prevent radicalization from occurring.
Further, NIJ hopes to address significant research gaps in the field, such as gaps in understanding disengagement and deradicalization processes and what programs can be developed and delivered to those incarcerated for terrorist offenses. While it is vital to understand the “push” (forcing) and “pull” (attracting) factors behind why individuals become terrorists to help inform prevention and intervention policies and programs, it is equally important to understand these factors to inform disengagement and deradicalization efforts. If we do not understand what makes terrorism attractive to certain individuals and how terrorism is unique from other forms of violence, we will not be able to prevent, intervene with, deradicalize, or reintegrate those susceptible to this phenomenon. Bridging this gap would not only complement NIJ’s previous investments, it would lead to future opportunities for rigorous comparative research initiatives in conjunction with other topics, such as mass shootings and gangs.
By understanding disengagement and deradicalization, NIJ hopes to inform policy and practice around programming for those convicted of terrorist offenses in confinement as well as post-release. In the United States, it is estimated that 275 individuals have been convicted of terrorism-related charges since the September 11 terrorist attacks. [21] Although some of these individuals are serving life sentences, many others are expected to be released. For example, as of December 1, 2018, 168 individuals have been charged with offenses related to the Islamic State group alone (not including those motivated by any other type of terrorist ideologies); their average sentence is 13.2 years. [22] A majority of these individuals will be released, often sooner than we would expect. Hundreds of others are incarcerated for terrorism offenses or terrorism-related charges across the country, and there is still much to be learned about how these individuals should be reintegrated back into society, what the recidivism rate for these people will be, and to what extent their ideologies have changed after incarceration. Questions about the effectiveness of prison programming, access to services, and success with reintegration remain. Those who commit terrorist offenses are a relatively new and niche population that has been under-studied; immediate research and programming attention are needed to keep up with the growing number of individuals being released on such charges. This is a widely recognized concern in the field of terrorism research, and NIJ hopes to play a key role in fulfilling this urgent research need.
Overall, NIJ funding has allowed for valuable contributions to the field of domestic radicalization and terrorism research. However, there are still many uncertainties around how to intervene before an individual radicalizes or mobilizes to violence. NIJ intends to remain engaged in combating the constantly evolving threats presented by violent extremism through soliciting rigorous research, engaging with stakeholders, and informing policymakers.
For More Information
Learn more about NIJ’s domestic radicalization and terrorism portfolio .
About This Article
This article was published in the NIJ Journal Issue Number 282.
This article discusses the following grants:
- “Across the Universe? A Comparative Analysis of Violent Radicalization Across Three Offender Types with Implications for Criminal Justice Training and Education,” grant number 2013-ZA-BX-0002
- “Evaluation of a Multi-Faceted, U.S. Community-Based Muslim-Led CVE Program,” grant number 2013-ZA-BX-0003
- “Social Media as a Platform for Crafting Gender-Specific Interventions for the Domestic Radicalization of Women,” grant number 2016-ZA-BX-K002
- “Research on Domestic Radicalization to Violent Extremism: Insights from Family and Friends of Current and Former Extremists,” grant number 2017-ZA-CX-0005
- “Innovative Methodologies for Assessing Radicalization Risk: Risk Terrain Modeling and Conjunctive Analysis,” grant number 2017-ZA-CX-0004
- “Community Reporting Thresholds: Sharing Information with Authorities Concerning Terrorism Activity,” grant number 2018-ZA-CX-0004
Sidebar: Defining Terrorism
The definition of terrorism/terrorists is often a contested issue, with academics, government entities, media outlets, and others using varying language to define this concept. For the purposes of soliciting applications for research, NIJ has defined terrorists as “those individuals who commit or provide support for the commission of ideologically motivated violence to further political, social, or religious goals.” NIJ’s focus has been on the radicalization process as it occurs in the United States, regardless of the location of any act of terrorism that may ensue from that process.
Return to text .
[note 1] National Consortium for the Study of Terrorism and Responses to Terrorism (START), “Global Terrorism in 2017,” START Background Report, College Park, MD: University of Maryland, August 2018.
[note 2] START, “American Deaths in Terrorist Attacks, 1995-2017,” START Fact Sheet, College Park, MD: University of Maryland, September 2018.
[note 3] START, “Ideological Motivations of Terrorism in the United States, 1970-2016,” START Background Report, College Park, MD: University of Maryland, November 2017.
[note 4] START, “Ideological Motivations of Terrorism in the United States, 1970-2016.”
[note 5] Consolidated and Further Continuing Appropriations Act, 2012 , Public Law 112–55, 125 Stat. 615, November 18, 2011.
[note 6] National Institute of Justice, “ Radicalization and Violent Extremism: Lessons Learned from Canada, the U.K. and the U.S. , ” Washington, DC: U.S. Department of Justice, National Institute of Justice, July 2015, NCJ 249947; Allison G. Smith, “ How Radicalization to Terrorism Occurs in the United States: What Research Sponsored by the National Institute of Justice Tells Us ,” Washington, DC: U.S. Department of Justice, National Institute of Justice, June 2018, NCJ 250171; Allison G. Smith, “ Risk Factors and Indicators Associated With Radicalization to Terrorism in the United States: What Research Sponsored by the National Institute of Justice Tells Us ,” Washington, DC: U.S. Department of Justice, National Institute of Justice, June 2018, NCJ 251789; and National Institute of Justice, “Overview of Research Sponsored to Support and Evaluate Programs Aimed at Countering Violent Extremism in the United States” (unpublished).
[note 7] National Institute of Justice, “ Radicalization and Violent Extremism: Lessons Learned from Canada, the U.K. and the U.S. ”
[note 8] Smith, “ Risk Factors and Indicators .”
[note 9] Smith, “ How Radicalization to Terrorism Occurs .”
[note 10] John G. Horgan et al., “ Across the Universe? A Comparative Analysis of Violent Behavior and Radicalization Across Three Offender Types with Implications for Criminal Justice Training and Education ,” Final report to the National Institute of Justice, grant number 2013-ZA-BX-0002, June 2016, NCJ 249937.
[note 11] Horgan et al., “ Across the Universe? ”
[note 12] National Institute of Justice, “ Research on Domestic Radicalization and Terrorism ,” January 16, 2020.
[note 13] Michael J. Williams, John G. Horgan, and William P. Evans, “ Evaluation of a Multi-Faceted, U.S. Community-Based, Muslim-Led CVE Program ,” Final report to the National Institute of Justice, grant number 2013-ZA-BX-0003, June 2016, NCJ 249936.
[note 14] National Institute of Justice, “ Social Media As a Platform for Crafting Gender-Specific Interventions for the Domestic Radicalization of Women ,” grant number 2016-ZA-BX-K002.
[note 15] National Institute of Justice, “ Innovative Methodologies for Assessing Radicalization Risk: Risk Terrain Modeling and Conjunctive Analysis ,” grant number 2017-ZA-CX-0004.
[note 16] Brent Smith, “ A Look at Terrorist Behavior: How They Prepare, Where They Strike ,” NIJ Journal 260, July 2008.
[note 17] National Institute of Justice, “ Research on Domestic Radicalization to Violent Extremism: Insights from Family and Friends of Current and Former Extremists ,” grant number 2017-ZA-CX-0005.
[note 18] National Institute of Justice, “ Community Reporting Thresholds: Sharing Information with Authorities Concerning Terrorism Activity ,” grant number 2018-ZA-CX-0004.
[note 19] National Institute of Justice, “ Notes From the Field .”
[note 20] Department of Homeland Security Science and Technology Directorate, “ Systematic Reviews of Terrorism Prevention Research ,” Washington, DC: Department of Homeland Security, September 19, 2018.
[note 21] Lorenzo Vidino and Seamus Hughes, “America’s Terrorism Problem Doesn’t End with Prison — It Might Just Begin There,” Lawfare (blog), June 17, 2018.
[note 22] Lorenzo Vidino and Seamus Hughes, ISIS in America: From Retweets to Raqqa, Washington, DC: The George Washington University, Program on Extremism, December 2015.
About the author
Aisha Javed Qureshi is a social science analyst at NIJ.

Cite this Article
Read more about:, related publications.
- NIJ Journal Issue No. 282
Related Awards
- Across the Universe? A Comparative Analysis of Violent Radicalization Across Three Offender Types with Implications for Criminal Justice Training and Education
- Evaluation of a Multi-Faceted, U.S. Community-Based Muslim-Led CVE Program
- Social Media As a Platform for Crafting Gender-Specific Interventions for the Domestic Radicalization of Women
- Research on Domestic Radicalization to Violent Extremism: Insights from Family and Friends of Current and Former Extremists
- INNOVATIVE METHODOLOGIES FOR ASSESSING RADICALIZATION RISK: RISK TERRAIN MODELING AND CONJUNCTIVE ANALYSIS
- Community Reporting Thresholds: Sharing Information with Authorities Concerning Terrorism Activity.
- Search Menu
- Browse content in A - General Economics and Teaching
- Browse content in A1 - General Economics
- A10 - General
- A12 - Relation of Economics to Other Disciplines
- A13 - Relation of Economics to Social Values
- A14 - Sociology of Economics
- Browse content in A2 - Economic Education and Teaching of Economics
- A29 - Other
- Browse content in B - History of Economic Thought, Methodology, and Heterodox Approaches
- B0 - General
- Browse content in B1 - History of Economic Thought through 1925
- B11 - Preclassical (Ancient, Medieval, Mercantilist, Physiocratic)
- B12 - Classical (includes Adam Smith)
- Browse content in B2 - History of Economic Thought since 1925
- B20 - General
- B21 - Microeconomics
- B22 - Macroeconomics
- B25 - Historical; Institutional; Evolutionary; Austrian
- B26 - Financial Economics
- Browse content in B3 - History of Economic Thought: Individuals
- B31 - Individuals
- Browse content in B4 - Economic Methodology
- B41 - Economic Methodology
- Browse content in B5 - Current Heterodox Approaches
- B55 - Social Economics
- Browse content in C - Mathematical and Quantitative Methods
- Browse content in C0 - General
- C00 - General
- C02 - Mathematical Methods
- Browse content in C1 - Econometric and Statistical Methods and Methodology: General
- C10 - General
- C11 - Bayesian Analysis: General
- C12 - Hypothesis Testing: General
- C13 - Estimation: General
- C14 - Semiparametric and Nonparametric Methods: General
- C15 - Statistical Simulation Methods: General
- C19 - Other
- Browse content in C2 - Single Equation Models; Single Variables
- C21 - Cross-Sectional Models; Spatial Models; Treatment Effect Models; Quantile Regressions
- C22 - Time-Series Models; Dynamic Quantile Regressions; Dynamic Treatment Effect Models; Diffusion Processes
- C23 - Panel Data Models; Spatio-temporal Models
- C24 - Truncated and Censored Models; Switching Regression Models; Threshold Regression Models
- C25 - Discrete Regression and Qualitative Choice Models; Discrete Regressors; Proportions; Probabilities
- C26 - Instrumental Variables (IV) Estimation
- Browse content in C3 - Multiple or Simultaneous Equation Models; Multiple Variables
- C31 - Cross-Sectional Models; Spatial Models; Treatment Effect Models; Quantile Regressions; Social Interaction Models
- C32 - Time-Series Models; Dynamic Quantile Regressions; Dynamic Treatment Effect Models; Diffusion Processes; State Space Models
- C33 - Panel Data Models; Spatio-temporal Models
- C34 - Truncated and Censored Models; Switching Regression Models
- C35 - Discrete Regression and Qualitative Choice Models; Discrete Regressors; Proportions
- C36 - Instrumental Variables (IV) Estimation
- Browse content in C4 - Econometric and Statistical Methods: Special Topics
- C41 - Duration Analysis; Optimal Timing Strategies
- C43 - Index Numbers and Aggregation
- Browse content in C5 - Econometric Modeling
- C51 - Model Construction and Estimation
- C52 - Model Evaluation, Validation, and Selection
- C53 - Forecasting and Prediction Methods; Simulation Methods
- C54 - Quantitative Policy Modeling
- Browse content in C6 - Mathematical Methods; Programming Models; Mathematical and Simulation Modeling
- C60 - General
- C61 - Optimization Techniques; Programming Models; Dynamic Analysis
- C62 - Existence and Stability Conditions of Equilibrium
- C63 - Computational Techniques; Simulation Modeling
- Browse content in C7 - Game Theory and Bargaining Theory
- C71 - Cooperative Games
- C72 - Noncooperative Games
- C73 - Stochastic and Dynamic Games; Evolutionary Games; Repeated Games
- C78 - Bargaining Theory; Matching Theory
- Browse content in C8 - Data Collection and Data Estimation Methodology; Computer Programs
- C81 - Methodology for Collecting, Estimating, and Organizing Microeconomic Data; Data Access
- C82 - Methodology for Collecting, Estimating, and Organizing Macroeconomic Data; Data Access
- C83 - Survey Methods; Sampling Methods
- Browse content in C9 - Design of Experiments
- C90 - General
- C91 - Laboratory, Individual Behavior
- C92 - Laboratory, Group Behavior
- C93 - Field Experiments
- Browse content in D - Microeconomics
- Browse content in D0 - General
- D00 - General
- D01 - Microeconomic Behavior: Underlying Principles
- D02 - Institutions: Design, Formation, Operations, and Impact
- D03 - Behavioral Microeconomics: Underlying Principles
- D04 - Microeconomic Policy: Formulation; Implementation, and Evaluation
- Browse content in D1 - Household Behavior and Family Economics
- D10 - General
- D11 - Consumer Economics: Theory
- D12 - Consumer Economics: Empirical Analysis
- D13 - Household Production and Intrahousehold Allocation
- D14 - Household Saving; Personal Finance
- D15 - Intertemporal Household Choice: Life Cycle Models and Saving
- D16 - Collaborative Consumption
- D18 - Consumer Protection
- D19 - Other
- Browse content in D2 - Production and Organizations
- D21 - Firm Behavior: Theory
- D22 - Firm Behavior: Empirical Analysis
- D23 - Organizational Behavior; Transaction Costs; Property Rights
- D24 - Production; Cost; Capital; Capital, Total Factor, and Multifactor Productivity; Capacity
- D29 - Other
- Browse content in D3 - Distribution
- D30 - General
- D31 - Personal Income, Wealth, and Their Distributions
- D33 - Factor Income Distribution
- D39 - Other
- Browse content in D4 - Market Structure, Pricing, and Design
- D40 - General
- D41 - Perfect Competition
- D43 - Oligopoly and Other Forms of Market Imperfection
- D44 - Auctions
- Browse content in D5 - General Equilibrium and Disequilibrium
- D50 - General
- D53 - Financial Markets
- D58 - Computable and Other Applied General Equilibrium Models
- Browse content in D6 - Welfare Economics
- D60 - General
- D61 - Allocative Efficiency; Cost-Benefit Analysis
- D62 - Externalities
- D63 - Equity, Justice, Inequality, and Other Normative Criteria and Measurement
- D64 - Altruism; Philanthropy
- D69 - Other
- Browse content in D7 - Analysis of Collective Decision-Making
- D70 - General
- D71 - Social Choice; Clubs; Committees; Associations
- D72 - Political Processes: Rent-seeking, Lobbying, Elections, Legislatures, and Voting Behavior
- D73 - Bureaucracy; Administrative Processes in Public Organizations; Corruption
- D74 - Conflict; Conflict Resolution; Alliances; Revolutions
- D78 - Positive Analysis of Policy Formulation and Implementation
- Browse content in D8 - Information, Knowledge, and Uncertainty
- D80 - General
- D81 - Criteria for Decision-Making under Risk and Uncertainty
- D82 - Asymmetric and Private Information; Mechanism Design
- D83 - Search; Learning; Information and Knowledge; Communication; Belief; Unawareness
- D84 - Expectations; Speculations
- D85 - Network Formation and Analysis: Theory
- D86 - Economics of Contract: Theory
- Browse content in D9 - Micro-Based Behavioral Economics
- D90 - General
- D91 - Role and Effects of Psychological, Emotional, Social, and Cognitive Factors on Decision Making
- D92 - Intertemporal Firm Choice, Investment, Capacity, and Financing
- Browse content in E - Macroeconomics and Monetary Economics
- Browse content in E0 - General
- E00 - General
- E01 - Measurement and Data on National Income and Product Accounts and Wealth; Environmental Accounts
- E02 - Institutions and the Macroeconomy
- Browse content in E1 - General Aggregative Models
- E10 - General
- E11 - Marxian; Sraffian; Kaleckian
- E12 - Keynes; Keynesian; Post-Keynesian
- E13 - Neoclassical
- E19 - Other
- Browse content in E2 - Consumption, Saving, Production, Investment, Labor Markets, and Informal Economy
- E20 - General
- E21 - Consumption; Saving; Wealth
- E22 - Investment; Capital; Intangible Capital; Capacity
- E23 - Production
- E24 - Employment; Unemployment; Wages; Intergenerational Income Distribution; Aggregate Human Capital; Aggregate Labor Productivity
- E25 - Aggregate Factor Income Distribution
- E26 - Informal Economy; Underground Economy
- E27 - Forecasting and Simulation: Models and Applications
- Browse content in E3 - Prices, Business Fluctuations, and Cycles
- E30 - General
- E31 - Price Level; Inflation; Deflation
- E32 - Business Fluctuations; Cycles
- E37 - Forecasting and Simulation: Models and Applications
- Browse content in E4 - Money and Interest Rates
- E40 - General
- E41 - Demand for Money
- E42 - Monetary Systems; Standards; Regimes; Government and the Monetary System; Payment Systems
- E43 - Interest Rates: Determination, Term Structure, and Effects
- E44 - Financial Markets and the Macroeconomy
- E47 - Forecasting and Simulation: Models and Applications
- Browse content in E5 - Monetary Policy, Central Banking, and the Supply of Money and Credit
- E50 - General
- E51 - Money Supply; Credit; Money Multipliers
- E52 - Monetary Policy
- E58 - Central Banks and Their Policies
- Browse content in E6 - Macroeconomic Policy, Macroeconomic Aspects of Public Finance, and General Outlook
- E60 - General
- E61 - Policy Objectives; Policy Designs and Consistency; Policy Coordination
- E62 - Fiscal Policy
- E63 - Comparative or Joint Analysis of Fiscal and Monetary Policy; Stabilization; Treasury Policy
- E65 - Studies of Particular Policy Episodes
- E69 - Other
- Browse content in E7 - Macro-Based Behavioral Economics
- E70 - General
- E71 - Role and Effects of Psychological, Emotional, Social, and Cognitive Factors on the Macro Economy
- Browse content in F - International Economics
- Browse content in F0 - General
- F02 - International Economic Order and Integration
- Browse content in F1 - Trade
- F10 - General
- F11 - Neoclassical Models of Trade
- F12 - Models of Trade with Imperfect Competition and Scale Economies; Fragmentation
- F13 - Trade Policy; International Trade Organizations
- F14 - Empirical Studies of Trade
- F15 - Economic Integration
- F16 - Trade and Labor Market Interactions
- F17 - Trade Forecasting and Simulation
- F18 - Trade and Environment
- Browse content in F2 - International Factor Movements and International Business
- F21 - International Investment; Long-Term Capital Movements
- F22 - International Migration
- F23 - Multinational Firms; International Business
- F24 - Remittances
- Browse content in F3 - International Finance
- F30 - General
- F31 - Foreign Exchange
- F32 - Current Account Adjustment; Short-Term Capital Movements
- F33 - International Monetary Arrangements and Institutions
- F34 - International Lending and Debt Problems
- F35 - Foreign Aid
- F36 - Financial Aspects of Economic Integration
- F37 - International Finance Forecasting and Simulation: Models and Applications
- Browse content in F4 - Macroeconomic Aspects of International Trade and Finance
- F40 - General
- F41 - Open Economy Macroeconomics
- F42 - International Policy Coordination and Transmission
- F43 - Economic Growth of Open Economies
- F44 - International Business Cycles
- F45 - Macroeconomic Issues of Monetary Unions
- Browse content in F5 - International Relations, National Security, and International Political Economy
- F50 - General
- F51 - International Conflicts; Negotiations; Sanctions
- F52 - National Security; Economic Nationalism
- F53 - International Agreements and Observance; International Organizations
- F55 - International Institutional Arrangements
- F59 - Other
- Browse content in F6 - Economic Impacts of Globalization
- F62 - Macroeconomic Impacts
- F63 - Economic Development
- F64 - Environment
- Browse content in G - Financial Economics
- Browse content in G0 - General
- G01 - Financial Crises
- G02 - Behavioral Finance: Underlying Principles
- Browse content in G1 - General Financial Markets
- G10 - General
- G11 - Portfolio Choice; Investment Decisions
- G12 - Asset Pricing; Trading volume; Bond Interest Rates
- G14 - Information and Market Efficiency; Event Studies; Insider Trading
- G15 - International Financial Markets
- G18 - Government Policy and Regulation
- Browse content in G2 - Financial Institutions and Services
- G20 - General
- G21 - Banks; Depository Institutions; Micro Finance Institutions; Mortgages
- G22 - Insurance; Insurance Companies; Actuarial Studies
- G24 - Investment Banking; Venture Capital; Brokerage; Ratings and Ratings Agencies
- G28 - Government Policy and Regulation
- Browse content in G3 - Corporate Finance and Governance
- G32 - Financing Policy; Financial Risk and Risk Management; Capital and Ownership Structure; Value of Firms; Goodwill
- G33 - Bankruptcy; Liquidation
- G34 - Mergers; Acquisitions; Restructuring; Corporate Governance
- G35 - Payout Policy
- G38 - Government Policy and Regulation
- Browse content in H - Public Economics
- Browse content in H0 - General
- H00 - General
- Browse content in H1 - Structure and Scope of Government
- H10 - General
- H11 - Structure, Scope, and Performance of Government
- H12 - Crisis Management
- Browse content in H2 - Taxation, Subsidies, and Revenue
- H20 - General
- H21 - Efficiency; Optimal Taxation
- H22 - Incidence
- H23 - Externalities; Redistributive Effects; Environmental Taxes and Subsidies
- H24 - Personal Income and Other Nonbusiness Taxes and Subsidies; includes inheritance and gift taxes
- H25 - Business Taxes and Subsidies
- H26 - Tax Evasion and Avoidance
- Browse content in H3 - Fiscal Policies and Behavior of Economic Agents
- H30 - General
- H31 - Household
- Browse content in H4 - Publicly Provided Goods
- H40 - General
- H41 - Public Goods
- H42 - Publicly Provided Private Goods
- Browse content in H5 - National Government Expenditures and Related Policies
- H50 - General
- H51 - Government Expenditures and Health
- H52 - Government Expenditures and Education
- H53 - Government Expenditures and Welfare Programs
- H54 - Infrastructures; Other Public Investment and Capital Stock
- H55 - Social Security and Public Pensions
- H56 - National Security and War
- Browse content in H6 - National Budget, Deficit, and Debt
- H60 - General
- H61 - Budget; Budget Systems
- H62 - Deficit; Surplus
- H63 - Debt; Debt Management; Sovereign Debt
- Browse content in H7 - State and Local Government; Intergovernmental Relations
- H70 - General
- H71 - State and Local Taxation, Subsidies, and Revenue
- H72 - State and Local Budget and Expenditures
- H75 - State and Local Government: Health; Education; Welfare; Public Pensions
- H76 - State and Local Government: Other Expenditure Categories
- H77 - Intergovernmental Relations; Federalism; Secession
- Browse content in H8 - Miscellaneous Issues
- H83 - Public Administration; Public Sector Accounting and Audits
- H84 - Disaster Aid
- H87 - International Fiscal Issues; International Public Goods
- Browse content in I - Health, Education, and Welfare
- Browse content in I0 - General
- I00 - General
- Browse content in I1 - Health
- I10 - General
- I12 - Health Behavior
- I14 - Health and Inequality
- I15 - Health and Economic Development
- I18 - Government Policy; Regulation; Public Health
- I19 - Other
- Browse content in I2 - Education and Research Institutions
- I20 - General
- I21 - Analysis of Education
- I22 - Educational Finance; Financial Aid
- I23 - Higher Education; Research Institutions
- I24 - Education and Inequality
- I25 - Education and Economic Development
- I26 - Returns to Education
- I28 - Government Policy
- I29 - Other
- Browse content in I3 - Welfare, Well-Being, and Poverty
- I30 - General
- I31 - General Welfare
- I32 - Measurement and Analysis of Poverty
- I38 - Government Policy; Provision and Effects of Welfare Programs
- Browse content in J - Labor and Demographic Economics
- Browse content in J0 - General
- J00 - General
- J01 - Labor Economics: General
- J08 - Labor Economics Policies
- Browse content in J1 - Demographic Economics
- J10 - General
- J11 - Demographic Trends, Macroeconomic Effects, and Forecasts
- J12 - Marriage; Marital Dissolution; Family Structure; Domestic Abuse
- J13 - Fertility; Family Planning; Child Care; Children; Youth
- J14 - Economics of the Elderly; Economics of the Handicapped; Non-Labor Market Discrimination
- J15 - Economics of Minorities, Races, Indigenous Peoples, and Immigrants; Non-labor Discrimination
- J16 - Economics of Gender; Non-labor Discrimination
- J17 - Value of Life; Forgone Income
- J18 - Public Policy
- Browse content in J2 - Demand and Supply of Labor
- J20 - General
- J21 - Labor Force and Employment, Size, and Structure
- J22 - Time Allocation and Labor Supply
- J23 - Labor Demand
- J24 - Human Capital; Skills; Occupational Choice; Labor Productivity
- J26 - Retirement; Retirement Policies
- J28 - Safety; Job Satisfaction; Related Public Policy
- Browse content in J3 - Wages, Compensation, and Labor Costs
- J30 - General
- J31 - Wage Level and Structure; Wage Differentials
- J32 - Nonwage Labor Costs and Benefits; Retirement Plans; Private Pensions
- J33 - Compensation Packages; Payment Methods
- J38 - Public Policy
- Browse content in J4 - Particular Labor Markets
- J41 - Labor Contracts
- J42 - Monopsony; Segmented Labor Markets
- J45 - Public Sector Labor Markets
- J46 - Informal Labor Markets
- J48 - Public Policy
- Browse content in J5 - Labor-Management Relations, Trade Unions, and Collective Bargaining
- J50 - General
- J51 - Trade Unions: Objectives, Structure, and Effects
- J52 - Dispute Resolution: Strikes, Arbitration, and Mediation; Collective Bargaining
- J53 - Labor-Management Relations; Industrial Jurisprudence
- J54 - Producer Cooperatives; Labor Managed Firms; Employee Ownership
- J58 - Public Policy
- Browse content in J6 - Mobility, Unemployment, Vacancies, and Immigrant Workers
- J60 - General
- J61 - Geographic Labor Mobility; Immigrant Workers
- J62 - Job, Occupational, and Intergenerational Mobility
- J63 - Turnover; Vacancies; Layoffs
- J64 - Unemployment: Models, Duration, Incidence, and Job Search
- J65 - Unemployment Insurance; Severance Pay; Plant Closings
- J68 - Public Policy
- Browse content in J7 - Labor Discrimination
- J71 - Discrimination
- Browse content in J8 - Labor Standards: National and International
- J81 - Working Conditions
- J88 - Public Policy
- Browse content in K - Law and Economics
- Browse content in K0 - General
- K00 - General
- Browse content in K1 - Basic Areas of Law
- K11 - Property Law
- K12 - Contract Law
- K13 - Tort Law and Product Liability; Forensic Economics
- K14 - Criminal Law
- K16 - Election Law
- Browse content in K3 - Other Substantive Areas of Law
- K31 - Labor Law
- K32 - Environmental, Health, and Safety Law
- K34 - Tax Law
- K37 - Immigration Law
- Browse content in K4 - Legal Procedure, the Legal System, and Illegal Behavior
- K41 - Litigation Process
- K42 - Illegal Behavior and the Enforcement of Law
- K49 - Other
- Browse content in L - Industrial Organization
- Browse content in L0 - General
- L00 - General
- Browse content in L1 - Market Structure, Firm Strategy, and Market Performance
- L10 - General
- L11 - Production, Pricing, and Market Structure; Size Distribution of Firms
- L12 - Monopoly; Monopolization Strategies
- L13 - Oligopoly and Other Imperfect Markets
- L14 - Transactional Relationships; Contracts and Reputation; Networks
- L16 - Industrial Organization and Macroeconomics: Industrial Structure and Structural Change; Industrial Price Indices
- Browse content in L2 - Firm Objectives, Organization, and Behavior
- L20 - General
- L21 - Business Objectives of the Firm
- L22 - Firm Organization and Market Structure
- L23 - Organization of Production
- L24 - Contracting Out; Joint Ventures; Technology Licensing
- L25 - Firm Performance: Size, Diversification, and Scope
- L26 - Entrepreneurship
- L29 - Other
- Browse content in L3 - Nonprofit Organizations and Public Enterprise
- L30 - General
- L31 - Nonprofit Institutions; NGOs; Social Entrepreneurship
- L32 - Public Enterprises; Public-Private Enterprises
- L33 - Comparison of Public and Private Enterprises and Nonprofit Institutions; Privatization; Contracting Out
- Browse content in L4 - Antitrust Issues and Policies
- L40 - General
- L41 - Monopolization; Horizontal Anticompetitive Practices
- L43 - Legal Monopolies and Regulation or Deregulation
- Browse content in L5 - Regulation and Industrial Policy
- L50 - General
- L51 - Economics of Regulation
- L52 - Industrial Policy; Sectoral Planning Methods
- L53 - Enterprise Policy
- Browse content in L6 - Industry Studies: Manufacturing
- L60 - General
- L66 - Food; Beverages; Cosmetics; Tobacco; Wine and Spirits
- Browse content in L7 - Industry Studies: Primary Products and Construction
- L71 - Mining, Extraction, and Refining: Hydrocarbon Fuels
- L78 - Government Policy
- Browse content in L8 - Industry Studies: Services
- L81 - Retail and Wholesale Trade; e-Commerce
- L83 - Sports; Gambling; Recreation; Tourism
- L86 - Information and Internet Services; Computer Software
- Browse content in L9 - Industry Studies: Transportation and Utilities
- L94 - Electric Utilities
- L98 - Government Policy
- Browse content in M - Business Administration and Business Economics; Marketing; Accounting; Personnel Economics
- Browse content in M1 - Business Administration
- M12 - Personnel Management; Executives; Executive Compensation
- M14 - Corporate Culture; Social Responsibility
- M16 - International Business Administration
- Browse content in M3 - Marketing and Advertising
- M31 - Marketing
- Browse content in M5 - Personnel Economics
- M50 - General
- M51 - Firm Employment Decisions; Promotions
- M52 - Compensation and Compensation Methods and Their Effects
- M53 - Training
- M54 - Labor Management
- M55 - Labor Contracting Devices
- Browse content in N - Economic History
- Browse content in N1 - Macroeconomics and Monetary Economics; Industrial Structure; Growth; Fluctuations
- N10 - General, International, or Comparative
- N11 - U.S.; Canada: Pre-1913
- N12 - U.S.; Canada: 1913-
- N13 - Europe: Pre-1913
- N15 - Asia including Middle East
- Browse content in N2 - Financial Markets and Institutions
- N20 - General, International, or Comparative
- N24 - Europe: 1913-
- N25 - Asia including Middle East
- Browse content in N3 - Labor and Consumers, Demography, Education, Health, Welfare, Income, Wealth, Religion, and Philanthropy
- N31 - U.S.; Canada: Pre-1913
- N33 - Europe: Pre-1913
- N34 - Europe: 1913-
- Browse content in N4 - Government, War, Law, International Relations, and Regulation
- N40 - General, International, or Comparative
- N45 - Asia including Middle East
- N47 - Africa; Oceania
- Browse content in N5 - Agriculture, Natural Resources, Environment, and Extractive Industries
- N50 - General, International, or Comparative
- N53 - Europe: Pre-1913
- N57 - Africa; Oceania
- Browse content in N7 - Transport, Trade, Energy, Technology, and Other Services
- N70 - General, International, or Comparative
- N72 - U.S.; Canada: 1913-
- Browse content in N9 - Regional and Urban History
- N97 - Africa; Oceania
- Browse content in O - Economic Development, Innovation, Technological Change, and Growth
- Browse content in O1 - Economic Development
- O10 - General
- O11 - Macroeconomic Analyses of Economic Development
- O12 - Microeconomic Analyses of Economic Development
- O13 - Agriculture; Natural Resources; Energy; Environment; Other Primary Products
- O14 - Industrialization; Manufacturing and Service Industries; Choice of Technology
- O15 - Human Resources; Human Development; Income Distribution; Migration
- O16 - Financial Markets; Saving and Capital Investment; Corporate Finance and Governance
- O17 - Formal and Informal Sectors; Shadow Economy; Institutional Arrangements
- O18 - Urban, Rural, Regional, and Transportation Analysis; Housing; Infrastructure
- O19 - International Linkages to Development; Role of International Organizations
- Browse content in O2 - Development Planning and Policy
- O22 - Project Analysis
- O23 - Fiscal and Monetary Policy in Development
- O24 - Trade Policy; Factor Movement Policy; Foreign Exchange Policy
- O25 - Industrial Policy
- Browse content in O3 - Innovation; Research and Development; Technological Change; Intellectual Property Rights
- O30 - General
- O31 - Innovation and Invention: Processes and Incentives
- O32 - Management of Technological Innovation and R&D
- O33 - Technological Change: Choices and Consequences; Diffusion Processes
- O34 - Intellectual Property and Intellectual Capital
- O38 - Government Policy
- O39 - Other
- Browse content in O4 - Economic Growth and Aggregate Productivity
- O40 - General
- O41 - One, Two, and Multisector Growth Models
- O42 - Monetary Growth Models
- O43 - Institutions and Growth
- O47 - Empirical Studies of Economic Growth; Aggregate Productivity; Cross-Country Output Convergence
- O49 - Other
- Browse content in O5 - Economywide Country Studies
- O50 - General
- O52 - Europe
- O53 - Asia including Middle East
- O55 - Africa
- O57 - Comparative Studies of Countries
- Browse content in P - Economic Systems
- Browse content in P1 - Capitalist Systems
- P10 - General
- P13 - Cooperative Enterprises
- P16 - Political Economy
- P17 - Performance and Prospects
- Browse content in P2 - Socialist Systems and Transitional Economies
- P20 - General
- P26 - Political Economy; Property Rights
- Browse content in P3 - Socialist Institutions and Their Transitions
- P31 - Socialist Enterprises and Their Transitions
- Browse content in P4 - Other Economic Systems
- P48 - Political Economy; Legal Institutions; Property Rights; Natural Resources; Energy; Environment; Regional Studies
- Browse content in P5 - Comparative Economic Systems
- P50 - General
- Browse content in Q - Agricultural and Natural Resource Economics; Environmental and Ecological Economics
- Browse content in Q0 - General
- Q02 - Commodity Markets
- Browse content in Q1 - Agriculture
- Q11 - Aggregate Supply and Demand Analysis; Prices
- Q13 - Agricultural Markets and Marketing; Cooperatives; Agribusiness
- Q15 - Land Ownership and Tenure; Land Reform; Land Use; Irrigation; Agriculture and Environment
- Q16 - R&D; Agricultural Technology; Biofuels; Agricultural Extension Services
- Q17 - Agriculture in International Trade
- Q18 - Agricultural Policy; Food Policy
- Browse content in Q2 - Renewable Resources and Conservation
- Q20 - General
- Q22 - Fishery; Aquaculture
- Q23 - Forestry
- Q25 - Water
- Q26 - Recreational Aspects of Natural Resources
- Q29 - Other
- Browse content in Q3 - Nonrenewable Resources and Conservation
- Q30 - General
- Q32 - Exhaustible Resources and Economic Development
- Q33 - Resource Booms
- Q34 - Natural Resources and Domestic and International Conflicts
- Q38 - Government Policy
- Browse content in Q4 - Energy
- Q40 - General
- Q41 - Demand and Supply; Prices
- Q42 - Alternative Energy Sources
- Q43 - Energy and the Macroeconomy
- Q48 - Government Policy
- Browse content in Q5 - Environmental Economics
- Q50 - General
- Q51 - Valuation of Environmental Effects
- Q52 - Pollution Control Adoption Costs; Distributional Effects; Employment Effects
- Q53 - Air Pollution; Water Pollution; Noise; Hazardous Waste; Solid Waste; Recycling
- Q54 - Climate; Natural Disasters; Global Warming
- Q56 - Environment and Development; Environment and Trade; Sustainability; Environmental Accounts and Accounting; Environmental Equity; Population Growth
- Q58 - Government Policy
- Browse content in R - Urban, Rural, Regional, Real Estate, and Transportation Economics
- Browse content in R1 - General Regional Economics
- R10 - General
- R11 - Regional Economic Activity: Growth, Development, Environmental Issues, and Changes
- R15 - Econometric and Input-Output Models; Other Models
- Browse content in R2 - Household Analysis
- R23 - Regional Migration; Regional Labor Markets; Population; Neighborhood Characteristics
- R29 - Other
- Browse content in R4 - Transportation Economics
- R40 - General
- R41 - Transportation: Demand, Supply, and Congestion; Travel Time; Safety and Accidents; Transportation Noise
- Browse content in R5 - Regional Government Analysis
- R58 - Regional Development Planning and Policy
- Browse content in Z - Other Special Topics
- Browse content in Z1 - Cultural Economics; Economic Sociology; Economic Anthropology
- Z10 - General
- Z11 - Economics of the Arts and Literature
- Z12 - Religion
- Z13 - Economic Sociology; Economic Anthropology; Social and Economic Stratification
- Z19 - Other
- Browse content in Z2 - Sports Economics
- Z21 - Industry Studies
- Z22 - Labor Issues
- Z29 - Other
- Browse content in Z3 - Tourism Economics
- Z30 - General
- Advance articles
- Author Guidelines
- Submission Site
- Open Access
- About Oxford Economic Papers
- Editorial Board
- Advertising and Corporate Services
- Journals Career Network
- Self-Archiving Policy
- Dispatch Dates
- Terms and Conditions
- Journals on Oxford Academic
- Books on Oxford Academic

Article Contents
1. introduction, 2. on terrorism, 3. event data sets, 4. domestic and transnational terrorism: some data plots, 5. counterterrorism, 6. findings of the articles of the special issue, 7. concluding remarks, acknowledgements, terrorism and counterterrorism: an overview.
- Article contents
- Figures & tables
- Supplementary Data
Todd Sandler, Terrorism and counterterrorism: an overview, Oxford Economic Papers , Volume 67, Issue 1, January 2015, Pages 1–20, https://doi.org/10.1093/oep/gpu039
- Permissions Icon Permissions
This introduction sets the stage for the articles collected in this special issue of Oxford Economic Papers . It begins by introducing essential concepts including domestic terrorism, transnational terrorism, defensive actions, proactive countermeasures, and guerrilla warfare. Three terrorist event databases, used by seven of the articles, are briefly introduced. These data sets are then used to display some stylized facts about domestic and transnational terrorism during the past four decades. Next, some essential strategic distinctions are drawn between defensive and proactive measures in the case of transnational terrorism when multiple countries are confronted by a common terrorist group. These strategic concerns vanish for domestic terrorism as a central government is able to internalize potential externalities. Finally, the key findings of the articles in the special issue are highlighted in two tables.
Terrorism is the premeditated use or threat to use violence by individuals or subnational groups to obtain a political or social objective through the intimidation of a large audience beyond that of the immediate noncombatant victims ( Enders and Sandler, 2012 , p.4). The two essential ingredients of terrorism are its violence and its political or social motive. Terrorists tend to employ shockingly violent acts, such as beheadings, downing of commercial airlines, bombings in public markets, and armed attacks in public places, to intimidate an audience. Their unpredictable and horrific attacks are meant to make everyone feel at risk even though the true likelihood of falling victim to a terrorist incident is rather minuscule, roughly equivalent to that of drowning in one's bathtub ( Mueller, 2006 ). Terrorists seek to circumvent normal channels for political change by traumatizing the public with brutal acts so that governments feel compelled to either address terrorist demands or divert public funds into hardening potential targets. Terrorist campaigns are more prevalent in liberal democracies, where the government's legitimacy hinges on its ability to protect the lives and property of its citizens ( Eubank and Weinberg, 1994 ).
The four airplane hijackings on 11 September 2001 (9/11) are terrorist acts since the perpetrators were members of al-Qaida, a subnational terrorist group, bent on pressuring the USA to remove its troops from Saudi Arabia, which was al-Qaida's primary political goal at the time. These skyjackings intimidated a global audience, caused huge temporary losses to the major stock exchanges ( Chen and Siems, 2004 ), and created $80–90 billion in direct and indirect damages ( Kunreuther et al ., 2003 ). Even though stock exchanges recovered lost values in just over a month, the death of almost 3,000 people caused rich industrial countries to allocate more resources to counterterrorism, shook insurance markets, and made an indelible impression on virtually the entire world. Heinous terrorist incidents continue to capture headlines with recent newsworthy incidents involving al-Shabaab's armed attack on the Westgate Mall in Nairobi, Kenya, on 21 September 2013; Chechen separatists’ suicide bombings of a train station and a trolley in Volgograd, Russia, on 29 and 30 December 2013, respectively; and Boko Haram's kidnapping of more than 200 female students in Chibok, Nigeria, on 14–15 April 2014. These and countless other incidents since 9/11 indicate that the government must allocate resources in an effective and measured manner to counterterrorism activities so that terrorists cannot circumvent legitimate political processes or cause significant economic losses. These losses may involve reduced foreign direct investment ( Enders and Sandler, 1996 ; Abadie and Gardeazabal, 2008 ), lower economic growth ( Abadie and Gardeazabal, 2003 ; Eckstein and Tsiddon, 2004 ; Gaibulloev and Sandler, 2008 , 2011 ), less trade ( Nitsch and Schumacher, 2004 ), reduced tourism ( Enders et al ., 1992 ; Drakos and Kutan, 2003 ), or lost values of stock and bond indexes ( Kollias et al ., 2013 ). Economic impacts of terrorism are greatest in small terrorism-plagued countries and developing countries ( Keefer and Loayza, 2008 ; Sandler and Enders, 2008 ). Modern industrial economies can insulate themselves through judicious fiscal and monetary policy, rapid counterterrorism responses, and the transference of economic activities ( Enders and Sandler, 2012 ). The latter involves economic activities moving from terrorism-prone sectors and regions to safer areas, which advanced, diversified economies allow. Thus, economic activity may switch from the tourism sector to other sectors when the former is targeted. In Spain, economic investment switched from the Basque Country to other Spanish provinces because of Euskadi ta Askatasuna attacks ( Abadie and Gardeazabal, 2003 ).
Modern-day econometric methods—time series, panel, and discrete-choice models—lend themselves to the quantification of these economic losses as shown in this special issue by Choi (2015) , Egger and Gassebner (2015) , and Younas (2015) . Additionally, game-theoretic models can display counterterrorism interactions among terrorists and governments as in the contributions in this issue by Carter (2015) and Kaplan (2015) . In fact, game theory is an excellent tool to study interactions among targeted governments, between rival terrorist groups, between a terrorist group and its sponsoring state, and among the media, the terrorist group, and the public. 1
The purpose of this article is to provide the requisite background to the studies in this special issue of Oxford Economic Papers . This task requires a fuller discussion of the notion of terrorism and its two primary subdivisions—domestic and transnational terrorism—in Section 2. The three event data sets employed in empirical studies, including seven of the eight articles in this issue, are briefly presented in Section 3. In Section 4, two of these data sets are used to display some recent trends and aspects of domestic and transnational terrorism during the last four decades. Essential concepts of counterterrorism are then presented in Section 5, where proactive measures are distinguished from defensive actions. Key findings of the four terrorism and four counterterrorism articles contained in this special issue are highlighted in two summarizing tables in Section 6. Concluding remarks follow in Section 7.
I now return to the definition of terrorism, given at the outset of this article. Any definition of terrorism involves much debate ( Hoffman, 2006 ; Enders and Sandler, 2012 ). The research community is converging to a consensus based on an operational definition on which to construct event data sets to test theoretical propositions. The article puts forward a definition that is consistent with that used by the main event data sets and relied on by researchers. Also, this definition possesses the main ingredients that are agreed on by economists, political scientists, and political economists.
The three stakeholders in this definition are the perpetrators, the victims, and the audience. By limiting terrorism to subnational agents including individuals or a ‘lone wolf’, my definition rules out state terror in which a government terrorizes its own people. The definition, however, does not rule out state-sponsored terrorism where a government clandestinely assists a terrorist group through various means, including supplying weapons, safe haven, intelligence, training, funding, or safe passage ( Mickolus, 1989 ; Bapat, 2006 ). There was a lot of state sponsorship of terrorism during the final decade of the Cold War with groups such as the Abu Nidal Organization serving as a terrorist group for hire ( Hoffman, 2006 ). 2 The most controversial element of my definition is the victim, since some definitions exclude combatants, so that attacks against an occupying army, such as US forces in Iraq or Afghanistan, are not viewed as terrorism. Generally, an attack against peacekeepers, such as the 23 October 1983 suicide bombing of the US Marines barracks at Beirut International Airport, is considered an act of terrorism. The barracks’ bombing had the political objective of removing peacekeepers from Lebanon, which happened in February 1984. Attacks against US soldiers and their dependents stationed in Germany constitute terrorist incidents, because these targeted individuals were noncombatants when attacked. ‘Audience’ refers to the collective that terrorists seek to intimidate through their wanton brutality. With sufficient and sustained intimidation, the audience will apply pressures on the besieged government to concede to the terrorist group's political demands or alternatively to take decisive action to annihilate the group. 3 In the latter case, the Italian authorities dismantled the Italian Red Brigades in the 1980s.
There are some crucial distinctions to draw between terrorism and related concepts. For instance, there is the distinction between terrorism and crime. A kidnapping for ransom is a criminal act of extortion when the kidnappers are not pursuing or financing a political agenda. If a political motive is tied to the kidnapping, then it is a terrorist incident even with ransom demands being made. The hijacking of a commercial airliner by a deranged person is a crime but not terrorism. In the absence of a political motive, an armed attack by a student on fellow students or teachers is a criminal action. Next consider an insurrection, which ‘is a politically based uprising intended to overthrow the established system of governance and to bring about a redistribution of income’ ( Sandler and Hartley, 1995 , p. 307). Leaders of insurrections recruit from the peasantry and general population in the hopes of challenging the government's hold on power ( Grossman, 1991 ). Successful rebel operations can generate new recruits and may ideally cause the government to impose draconian measures on its citizens, which subsequently create more support for the insurgency. If a tipping point is attained, then the government may be sufficiently challenged to lose its power to the rebels.
In distinction to insurrections, guerrilla warfare generally involves a band of rebel forces (e.g., the Revolutionary Armed Forces of Colombia [FARC], Abu Sayyaf in the Philippines, or Shining Path in Peru) that controls a sector of the country, from which to dispatch its operatives to confront government forces. Some guerrilla wars take place in urban centers. In contrast to most terrorist groups, guerrilla groups are larger in number and organized like a military force. Some guerrilla groups engage in terrorist acts, such as the three just-mentioned groups, to raise funds to secure their operations and pursue their political aims. For example, FARC kidnaps government officials and others for ransoms. Unlike an insurrection, guerrilla groups are not bent on overthrowing the government or engaging in propaganda to gain popular support ( Hoffman, 2006 ). Shining Path and FARC apply threats and harsh measures to gain the compliance of the people in the territory that they control. Guerrilla groups rely on surprise and cover to harass numerically superior government forces. Terrorism is a tactic employed by both insurrections and guerrilla movements. As a consequence, many guerrilla groups are listed as terrorist groups despite their control of territory. Often, countries with jungle cover or mountainous terrain provide remote areas where guerrillas can conduct training and operations. In this special issue, Carter (2015) is interested in the interaction between a guerrilla group and the government, as the former chooses between terrorism and the control of territory and the latter chooses between defensive counterterrorism actions and proactive military responses to influence the group's decision.
2.1 Domestic versus transnational terrorism
Domestic terrorism is homegrown and home-directed, and represents the most common form of terrorism. For domestic acts of terrorism, the perpetrators, victims, and audience hail from the venue country, where the attack takes place. Domestic terrorist incidents include Timothy McVeigh's bombing of the Alfred P. Murrah Federal Building in Oklahoma City on 19 April 1995 or Eric Rudolph's anti-abortionist bombing of Centennial Olympic Park in Atlanta, Georgia, on 27 July 1996. Civil wars often involve numerous domestic terrorist attacks before and during the conflict by the adversaries ( Findley and Young, 2012 ). 4 These terrorist acts are more apt to be domestic when an intervention by a third party from outside the country is not involved. Boko Haram's kidnapping of more than 200 female students is a domestic terrorist incident, which involves victims and perpetrators from the venue country of Nigeria. Boko Haram is an Islamic jihadist terrorist group that controls territory in the northeast portion of Nigeria. Given the country's limited military capabilities, its government sought some assistance from the USA in terms of military advisors and intelligence in addressing the significant threat that Boko Haram poses. At times, Boko Haram crosses into Chad. If one or more of the schoolgirls are moved into a neighboring country, then the kidnapping becomes a transnational terrorist incident. In general, poor countries may request foreign assistance if they cannot properly confront an indigenous terrorist group that may attack at home or abroad ( Azam and Thelen, 2010 ; Fleck and Kilby, 2010 ; Bandyopadhyay et al ., 2011 , 2014 ; Young and Findley, 2011 ).
Terrorism is transnational when an incident in the venue country concerns perpetrators or victims from another country. If a terrorist attack in the UK is perpetrated by terrorists from Yemen, then the incident is one of transnational terrorism. When a terrorist attack in France harms Dutch citizens, the attack is transnational. If one or more victims or perpetrators are not citizens of the venue country, then the terrorist attack is transnational. The kidnapping in January 2002 and subsequent murder of US reporter Daniel Pearl in Pakistan is classified as a transnational terrorist incident. The same is true of the near-simultaneous bombings of the US embassies in Kenya and Tanzania on 7 August 1998. Terrorist attacks against another country's embassy, even when perpetrated by citizens of the venue country, are transnational terrorist events because an embassy's grounds represent foreign soil. Similarly, terrorist attacks against international organizations’ personnel or property are considered to be transnational terrorist acts. An important transnational terrorist incident is the August 2006 plot to use liquid explosives to blow up 10 or more transatlantic flights departing the UK for the USA and Canada. A skyjacking originating in one country that is diverted to another country for political purposes is a transnational terrorist event. If a politically motivated hijacked plane has citizens from more than one country, the event is transnational terrorism even if the flight is domestic and ends in the country of origin. On 9/11, the four skyjackings are transnational terrorist acts since the victims were citizens from upward of 80 nations and the perpetrators were foreigners. The kidnapping of US journalist James Foley in Syria on 22 November 2012 and his beheading on 19 August 2014 is a transnational terrorist act. The victim was American, whereas the murderer is allegedly a British citizen from the Islamic State in Iraq and Syria (ISIS), also known as Islamic State (IS).
Transnational terrorist incidents frequently imply transnational externalities—for example, perpetrators from one country impose uncompensated costs on the victims of another country. If a country provides safe haven to a transnational terrorist group that attacks other countries’ interests, then transnational externalities ensue. 5 The Taliban in Afghanistan had given safe haven to Osama bin Laden's al-Qaida, which planned and executed the events of 9/11. When the Taliban would not surrender bin Laden to the USA following 9/11, the USA led an invasion of Afghanistan on 7 October 2001 ( Enders and Sandler, 2012 ). In this extreme case, the transnational externality resulted in a military invasion with the intent to defeat the Taliban and al-Qaida. Transnational externalities also arise from counterterrorism policies of targeted countries, which result in inefficient levels of these policies ( Sandler and Lapan, 1988 ; Sandler and Siqueira, 2006 ; Bueno de Mesquita, 2007 ). Actions by one targeted country to secure its borders and ports of entry may merely transfer the attack abroad, where borders are more porous (see Section 5). Since 9/11, few transnational terrorist incidents occur on US soil but 35% to 40% of such incidents involve US people or property in other countries ( Enders and Sandler, 2006 , 2012 ).
2.2 Some historical considerations of transnational terrorism
Hoffman ( 2006 , pp.63–5) traces the modern era of transnational terrorism to the 22 July 1968 hijacking of an Israeli El Al flight en route from Rome to Athens by three armed members of the Popular Front for the Liberation of Palestine (PFLP) terrorist group. This skyjacking was motivated by the intention of the PFLP terrorist to trade its hostages for Palestinian prisoners held by Israel. This event is noteworthy for a number of reasons. First, through its protracted 40-day negotiations, the Israelis were forced to negotiate with the Palestinian terrorists, which the Israelis had hitherto vowed they would never do ( Hoffman, 1998 , p.68). Second, the media coverage demonstrated to terrorists worldwide that such incidents could garner worldwide attention for their cause. Not surprisingly, transnational terrorist attacks increased greatly in numbers during the years following this incident (see the figures in Section 4). Third, there was evidence of state sponsorship after the diverted plane landed in Algiers as Algerian forces secured the hostages and held some Israeli hostages until 1 September 1968 when a deal was concluded ( Mickolus, 1980 , pp.93–4). Fourth, Israel eventually traded 16 Arab prisoners from the 1967 Arab-Israeli War for the remaining Israeli hostages. This trade showed terrorists that hostage taking could yield significant concessions.
Transnational terrorist groups were primarily nationalists/separatists or leftists (socialists) during the late 1960s until the late 1980s ( Rapoport, 2004 ). Even the Palestinian terrorists were secular until the end of the 1980s with the rise of Hamas, Palestinian Islamic Jihad, and other groups. After the mid-1990s, the religious fundamentalists came to dominate and increased the carnage ( Enders and Sandler, 2000 ; Gaibulloev and Sandler, 2014 ). The phenomenon of religious-based transnational terrorism is not novel and can be traced back to the Sicarii or Zealots, a Jewish sect that conducted a terror campaign against the Romans and their Jewish collaborators in Judea from CE 48 to 73 ( Rapoport, 1984 ; Bloom, 2005 ). Sicarii terrorists engaged in daytime assassinations in public places that typically resulted in the death of the assassin. As such, their dagger attacks were an early form of suicide terrorism, since the perpetrator had little chance of escape. 6 From 1090 to 1256, the Islamic Assassins opposed Sunni rule in Persia and Syria, with the intent to set up their own community and state of believers in the region ( Bloom, 2005 ). Although the Assassins’ terrorist campaign was on a much smaller scale, their goal was similar to that of ISIS. Like the Sicarii, the Assassins relied on politically motivated assassinations, performed with a dagger. Perpetrators usually sacrificed their own lives by making no efforts to escape after the deed.
In the beginning of the 1980s, the first terrorist event data set—International Terrorism: Attributes of Terrorist Events (ITERATE)—was made available to researchers. ITERATE only includes transnational terrorist attacks. Coverage starts in 1968, the beginning of the modern era of transnational terrorism, and runs until the end of 2012, with annual updates in August ( Mickolus et al ., 2013 ). ITERATE codes many variables—for example, incident date, country start location, country end location, attack type, target entity, terrorist group, perpetrators’ nationalities, number of deaths, number of injuries, victims’ nationalities, logistical outcome, US victims, state sponsorship, and scene of attack—in its Common File of over 40 variables. In addition, there is a Fate File indicating the fate of the terrorists—for example, the number of terrorists captured, the number of terrorists sentenced, and their length of incarceration. There is also a Hostage File, which has invaluable observations used by researchers to analyze logistical and negotiation success of hostage taking ( Santifort and Sandler, 2013 ). If an attack is completed as planned, then it is a logistical success. For hostage missions, securing one or more hostages is deemed a logistical success. The Hostage File of ITERATE is currently updated through 2010. Finally, there is a Skyjacking file with additional observations, and variables on skyjacking missions such as the duration of the incidents, airline involved, and negotiation strategies used. ITERATE, like the other event data sets, relies on the news media—print, broadcast, and digital—for the observations of its variables.
An initial focus of empirical studies was on transnational terrorism because ITERATE was the most extensive data set available throughout the 1980s and 1990s. Its lengthy series of daily data were ideal for time-series studies, which dominated the research landscape except for a few survival studies, the first being Atkinson et al .'s (1987) study of the duration of hostage-taking incidents. Today, panel studies are prevalent including those in this special issue— Berrebi and Ostwald (2015) , Choi (2015) , Egger and Gassebner (2015) , Gries et al . (2015) , and Younas (2015) .
Another competing event data set, modeled after ITERATE, is the RAND (2012) data set, which currently codes incidents for 1968–2009 and is not being updated. Gaibulloev (2015) uses the RAND event data in conjunction with Jones and Libicki's (2008) classification of terrorist groups’ ideologies in his study of groups’ location decisions. For 1968–97, RAND event data only include transnational terrorist attacks; after 1998, RAND data distinguish between transnational and domestic terrorist attacks in a manner consistent with my early definitions. Compared to ITERATE, RAND data code fewer variables and, for transnational terrorist incidents, have more limited coverage than ITERATE as demonstrated by Enders (2007) .
The third event data set, germane to this special issue, is that of the Global Terrorism Database (GTD), which records both domestic and transnational terrorist incidents ( La Free and Dugan, 2007 ; National Consortium for the Study of Terrorism and Response to Terrorism, 2013 ). Although GTD recorded both kinds of incidents, until 2013 it did not distinguish between the two kinds of incidents. Enders et al . (2011) devised a five-step procedure for distinguishing between domestic and transnational terrorist incidents in GTD for 1970–2007 and made their breakdown available to researchers. This division is now applied to 2008–2012 (see Enders et al ., 2014 ). A breakdown of terrorism into its two components is essential because the two types of terrorism may affect economic variables and counterterrorism differently—for example, economic growth or foreign direct investment is more influenced by transnational terrorism ( Gaibulloev and Sandler, 2008 ). Moreover, the influence of other variables on domestic and transnational terrorism may differ ( Sandler, 2014 ; Choi, 2015 ). The Enders et al . (2011) procedure does a much better job in distinguishing between the two types of events than recent GTD efforts, based on the authors’ method without attribution. GTD has tens of thousands of unclassified incidents compared to Enders et al . (2011) .
There are some things to note about GTD. First, it has changed its coding conventions a few times, most recently for the 2012 data. Coding was also changed after the National Consortium for the Study of Terrorism and Responses to Terrorism (2013) , based at the University of Maryland, took charge of the data around 2005. As shown by Enders et al . (2011) , there are periods of undercounting and overcounting of incidents, which can be addressed by these authors’ calibration methods. Second, GTD data for 1993 are very incomplete because in an office move by Pinkerton, which originated the database, the box containing 1993 fell off of the truck! Third, perpetrators’ nationalities are not identified. Fourth, GTD does not contain any hostage negotiation variables, making the study of hostage-taking incidents impossible with this database. Fifth, GTD coverage of some kinds of domestic incidents, such as kidnappings, is virtually nonexistent prior to the late 1990s ( Enders et al ., 2011 ).
Key aspects of the articles for the special issue
Notes: *denotes that Enders et al . (2011) breakdown of GTD into domestic and transnational terrorist incidents was used. ITERATE = International Terrorism: Attributes of Terrorist Events; GTD = Global Terrorism Database.
A variety of empirical techniques are applied by the six empirical articles. In his cross-sectional study of the location choice of terrorist groups, Gaibulloev (2015) relies on a conditional logit estimator. To account for the count nature of the dependent terrorism variable, Choi (2015) and Gries et al . (2015) apply a negative binomial panel estimator. Endogeneity between the dependent variable and one or more independent variables is addressed in various ways: the Berrebi and Ostwald (2015) article employs instrumental variables (IV), consisting of lagged domestic terrorist attacks in neighboring countries, whereas the Younas (2015) article uses system generalized method of moments (SGMM) to augment his feasible generalized least squares (FGLS) estimates. The Gries et al . (2015) article addresses endogeneity with lagged values of the independent variables and also SGMM estimates. The Choi (2015) article primarily uses lagged independent variables to partly handle the endogeneity concern.

ITERATE transnational terrorist incidents and total casualties per year, 1968–2012

GTD terrorist incidents per year, 1970–2012

ITERATE attacks against US interests per year, 1968–2012

Annual number of casualties per attack
This special issue contains articles on terrorism and counterterrorism. Given my discussion of terrorism and its concepts, it is now instructive to introduce some basic concepts and concerns that are associated with the practice of counterterrorism.
Quite simply, counterterrorism corresponds to actions to ameliorate the threat and consequences of terrorism. These actions can be taken by governments, military alliances, international organizations (e.g., INTERPOL), private corporations, or private citizens. Counterterrorism comes in two basic varieties: defensive and proactive measures.
Defensive countermeasures protect potential targets by making attacks more costly for terrorists or reducing their likelihood of success. When, however, successful terrorist attacks ensue, defensive actions also serve to limit the resulting losses to the target. Defensive measures have generally been reactive, instituted after some successful or innovative terrorist attacks. In the USA, airline passengers are now required to remove their shoes when being screened, following the innovative, but fortunately unsuccessful, attempt by Richard Reid to bring down American Airlines flight 63 en route from Paris to Miami on 22 December 2001 with explosives hidden in his shoes. Before the installation of metal detectors to screen passengers at US airports on 5 January 1973, there were on average over 25 skyjackings each year in the USA ( Enders et al ., 1990 ). After their installation, attempted US skyjackings dropped to fewer than four a year. The success of these metal detectors in US airports led to their installation worldwide over the next six months. Following the downing of Pan Am flight 103 over Lockerbie, Scotland, on 21 December 1988 and the downing of UTA flight 772 over Niger on 19 September 1989, bomb-detecting devices were used to screen checked luggage. Defensive or protective counterterror actions may involve more than technological barriers. Other instances of defensive measures include target hardening, such as defensive perimeters around government buildings or embassies, or guards at key points of a country's infrastructure. Defensive measures can also take the form of issuing terrorism alerts, enacting stiffer penalties for terrorism offenses, enhancing first-responder capabilities, and stockpiling antibiotics and antidotes for biological and chemical terrorist attacks. This list of defensive actions is by no means exhaustive.
By contrast, proactive measures are offensive as a targeted government directly confronts the terrorist group or its supporters. Proactive measures may destroy terrorists’ resources (e.g., training camps), curb their finances, eliminate their safe havens, or kill and capture their members. In recent years, the Obama administration has relied on drone attacks to assassinate terrorist leaders and operatives. Proactive operations may assume myriad other forms, including a retaliatory raid against a state sponsor that provides resources, training, sanctuary, logistical support, or intelligence to a terrorist group. On 15 April 1986, the USA launched a retaliatory bombing raid on targets in Libya for its alleged support in the terrorist bombing of the La Belle discotheque in West Berlin on 4 April 1986, where 3 died and 231 were wounded, including 62 Americans ( Mickolus et al ., 1989 , vol. 2, pp.365–7). Another proactive measure takes the form of a preemptive attack against a terrorist group or a harboring country, such as the US-led invasion of Afghanistan four weeks after 9/11. A preemptive strike differs from a retaliatory raid because the former is more sustained and meant to severely compromise the capabilities of the terrorists to conduct future missions. Such strikes or raids concern transnational terrorism where a targeted country confronts the foreign threat. Other proactive measures include infiltrating terrorist groups, engaging in military action, conducting propaganda campaigns against the terrorists, and gathering intelligence to foil terror plots ( Kaplan, 2015 ). ‘Military action’ generally refers to operations by the host government against a resident terrorist group as in Carter (2015) . Actions that improve the economy, which in turn reduces grievances, can also be proactive ( Choi, 2015 ). Younas (2015) demonstrates empirically that increased globalization of a country's economy may also be proactive by limiting harmful and therefore grievance-causing effects of terrorism on economic growth. In this special issue, the four counterterrorism articles primary address aspects of proactive measures. Only Carter (2015) considers both defensive and proactive counterterrorism responses.
The game-theoretic literature on counterterrorism draws some fascinating strategic contrasts between defensive and proactive countermeasures. Suppose that two or more countries are confronted by the same Islamic jihadist terrorist group—for example, al-Qaida in the Arabian Peninsula (AQAP). In this transnational terrorism scenario, each at-risk country is inclined to work at cross-purposes by engaging in a defensive race in the hopes of transferring the terrorist attacks to other targeted countries ( Sandler and Lapan, 1988 ; Arce and Sandler, 2005 ). In the process, the countries engage in too much defense since the negative transference externality is not internalized. The only check on this adverse ‘defense race’ stems from the countries having large interests abroad, which may be hit when attacks are transferred abroad—recall Fig. 3 and attacks against US interests ( Bandyopadhyay and Sandler, 2011 ; Bandyopadhyay et al ., 2011 ).
Next consider proactive measures in these multicountry scenarios. Any country's actions to confront the common terrorist threat confer purely public (nonrival and nonexcludable) benefits to all potential target countries. As a result, there is too little proactive response as each country tries to free ride on the actions of other countries. Thus, defensive measures are strategic complements as one country's actions encourage those of other countries (i.e., reaction paths are upward-sloping), whereas proactive measures are strategic substitutes as one country's actions inhibit those of other countries (i.e., reaction paths are downward-sloping) ( Eaton, 2004 ; Sandler and Siqueira, 2006 ). Moreover, leadership can be shown to curb the defensive race, whereas leadership exacerbates the free-riding underprovision of offensive measures ( Sandler and Siqueira, 2006 ). Thus, there is no simple fix for these concerns among sovereign targeted nations.
For domestic terrorism, countries possess the proper incentives to choose defensive and proactive measures judiciously, because all associated costs and benefits are internalized ( Enders and Sandler, 2012 ). Thus, Kaplan's (2015) finding that the USA staffs about the right number of intelligence analysts to intercept terror plots is consistent with past game-theoretic findings regarding domestic counterterrorism optimality. Carter's (2015) article is also geared to domestic terrorism, whereas Choi (2015) and Younas (2015) may involve economic-based countermeasures for either type of terrorism.
Key findings of terrorism studies
Key findings of counterterrorism studies
This special issue contains many noteworthy advances in the study of terrorism. Gaibulloev (2015) is the first article to address terrorist groups’ base location choice; currently, the study of terrorist group survival is an active area of research. Berrebi and Ostwald (2015) is the initial study to examine the impact of terrorism on fertility. Younas (2015) and Choi (2015) refine the relationship between terrorism and growth; Egger and Gassebner (2015) show that terrorism has less of an effect on trade than conventionally believed. Kaplan (2015) investigates the social efficiency of intelligence staffing in intercepting terror plots. Carter's (2015) analysis is novel because the terrorist group must decide between terrorist attacks and holding territory in reaction to the government's countermeasures. The interface between terrorism and other forms of political violence is seldom studied. Finally, the Gries et al . (2015) study extends knowledge of the determinants of anti-American terrorist attacks, which comprise 35–40% of all transnational terrorism.
Terrorism remains an active research area in economics, political economy, and political science. Given the microeconomic and macroeconomic consequences of terrorism, its study is a fitting topic for a general economics journal such as Oxford Economic Papers . Following 9/11, industrial countries engaged in a huge reallocation of resources toward counterterrorism, whose efficacy can be best studied and understood with the theoretical and empirical tools drawn from economics.
The rise of ISIS and the considerable threat that its Western fighters pose for their home countries means that terrorism will remain a policy concern. AQAP's war on the USA and its allies is yet another terrorist threat. Just as Africa appears to be achieving sustained economic growth in select countries, significant terrorist challenges arise from Boko Haram and al-Shabaab in Nigeria and Kenya, respectively. Failed states—for example, Afghanistan, Iraq, Somalia, Syria, and Yemen—supply safe havens for terrorist groups that threaten Western interests. It is my hope that this special issue on terrorism and counterterrorism will stimulate further research in these two topics.
The present collection arises from a set of papers presented at the sixth conference on Terrorism and Counterterrorism Policy at the University of Texas, Dallas. Held between 21 May and 24 May 2014, this conference invited many leading contributors to the study of terrorism and counterterrorism. Past conferences resulted in special issues published in Economics &Politics (November 2009), Journal of Conflict Resolution (April 2010), Journal of Peace Research (May 2011), Public Choice (December 2011), and Southern Economic Journal (April 2013). While assuming full responsibility for any remaining shortcomings, this article has profited from comments from Anindya Banerjee, who also advised me on the special issue. Khusrav Gaibulloev read and commented on an earlier version. Finally, I thank all of this special issue's reviewers, most of whom are major contributors to the study of terrorism. These reviewers provided rigorous reviews in a timely fashion. All articles went through a careful and demanding prescreening process, followed by two rounds of reviews by two to three anonymous referees. I appreciate the understanding of those authors whose papers did not make it into the special issue.
On the game-theoretic literature on terrorism, see Bandyopadhyay and Sandler (2011) , Bandyopadhyay et al . ( 2011 , 2014 ), Sandler and Arce (2003) , Bueno de Mesquita (2005) , and Sandler and Siqueira (2009) .
The Abu Nidal Organization was headed by Sabri Khali al-Banna. Its notorious attacks included the simultaneous armed attacks on the Rome and Vienna airports on 27 December 1985, the armed attack on the Neve Shalom Synagogue in Istanbul on 6 September 1986, and the attempted hijacking of Pan Am flight 73 in Karachi, Pakistan, on 5 September 1986 ( Enders and Sandler, 2012 ). This group is credited with the first simultaneous terrorist attacks.
On alternative ways that terrorist groups end, see Carter (2012) , Gailbulloev and Sandler (2014) , and Phillips (2014a) .
On the relationship between civil wars and terrorism, see Sambanis (2008) .
How terrorist groups choose their home base is discussed in this special issue by Gaibulloev (2015) . On the definition of terrorist groups, see Phillips (2014b) .
In this special issue, Choi (2015) investigates suicide terrorism, which may be domestic or transnational in nature. Suicide terrorist attacks grew in numbers after 1988 ( Santifort-Jordan and Sandler, 2014 ).
Abadie A. Gardeazabal J. ( 2003 ) The economic cost of conflict: a case study of the Basque Country , American Economic Review , 93 , 113 – 32 .
Google Scholar
Abadie A. Gardeazabal J. ( 2008 ) Terrorism and the world economy , European Economic Review , 52 , 1 – 27 .
Arce D.G. Sandler T. ( 2005 ) Counterterrorism: a game-theoretic analysis , Journal of Conflict Resolution , 49 , 183 – 200 .
Atkinson S.E. Sandler T. Tschirhart J. ( 1987 ) Terrorism in a bargaining framework , Journal of Law and Economics , 30 , 1 – 21 .
Azam J.-P. Thelen V. ( 2010 ) Foreign aid versus military intervention in the war on terror , Journal of Conflict Resolution , 54 , 237 – 61 .
Bandyopadhyay S. Sandler T. ( 2011 ) The interplay between preemptive and defensive counterterrorism measures: a two-stage game , Economica , 78 , 546 – 64 .
Bandyopadhyay S. Sandler T. Younas J. ( 2011 ) Foreign aid as counterterrorism policy , Oxford Economic Papers , 63 , 423 – 47 .
Bandyopadhyay S. Sandler T. Younas J. ( 2014 ) Foreign direct investment, aid, and terrorism , Oxford Economic Papers , 66 , 25 – 50 .
Bapat N. A. ( 2006 ) State bargaining with transnational terrorist groups , International Studies Quarterly , 50 , 213 – 29 .
Berrebi C. Ostwald J. ( 2015 ) Terrorism and fertility: evidence for a causal inference of terrorism on fertility , Oxford Economic Papers , 67 , 63 – 82 .
Bloom M. ( 2005 ) Dying to Kill: The Allure of Suicide Terror , Columbia University Press , New York .
Google Preview
Bueno de Mesquita E. ( 2005 ) The quality of terror , American Journal of Political Science , 49 , 515 – 30 .
Bueno de Mesquita E. ( 2007 ) Politics and the suboptimal provision of counterterror , International Organization , 61 , 9 – 36 .
Carter D.B. ( 2012 ) A blessing or curse? State support for terrorist groups , International Organization , 66 , 129 – 51 .
Carter D.B. ( 2015 ) When terrorism is evidence of state success: securing the state against territorial groups , Oxford Economic Papers , 67 , 116 – 32 .
Chen A.H. Siems T.F. ( 2004 ) The effects of terrorism on global capital markets , European Journal of Political Economy , 20 , 249 – 66 .
Choi S.-W. ( 2015 ) Economic growth and terrorism: domestic, international, and suicide , Oxford Economic Papers , 67 , 157 – 81 .
Drakos K. Kutan A.M. ( 2003 ) Regional effects of terrorism on tourism in three Mediterranean countries , Journal of Conflict Resolution , 47 , 621 – 41 .
Eaton B.C. ( 2004 ) The elementary economics of social dilemmas , Canadian Journal of Economics , 37 , 805 – 29 .
Eckstein Z. Tsiddon D. ( 2004 ) Macroeconomic consequences of terror: theory and the case of Israel , Journal of Monetary Economics , 51 , 971 – 1002 .
Egger P. Gassebner M. ( 2015 ) International terrorism as a trade impediment? Oxford Economic Papers , 67 , 42 – 62 .
Enders W. ( 2007 ) Terrorism: an empirical analysis , in Sandler T. Hartley K. (eds) Handbook of Defense Economics: Defense in a Globalized World , North-Holland , Amsterdam .
Enders W. Hoover G.A. Sandler T. ( 2014 ) The changing nonlinear relationship between income and terrorism , Journal of Conflict Resolution , doi: 10.1177/0022002714535252 .
Enders W. Sandler T. ( 1996 ) Terrorism and foreign direct investment in Spain and Greece , Kyklos , 49 , 331 – 52 .
Enders W. Sandler T. ( 2000 ) Is transnational terrorism becoming more threatening? A time-series investigation , Journal of Conflict Resolution , 44 , 307 – 32 .
Enders W. Sandler T. ( 2006 ) Distribution of transnational terrorism among countries by income classes and geography after 9/11 , International Studies Quarterly , 50 , 367 – 93 .
Enders W. Sandler T. ( 2012 ) The Political Economy of Terrorism , 2nd edn., Cambridge University Press , New York .
Enders W. Sandler T. Cauley J. ( 1990 ) UN conventions, technology, and retaliation in the fight against terrorism: an econometric evaluation , Terrorism and Political Violence , 2 , 83 – 105 .
Enders W. Sandler T. Gaibulloev K. ( 2011 ) Domestic versus transnational terrorism: data, decomposition, and dynamics , Journal of Peace Research , 48 , 319 – 37 .
Enders W. Sandler T. Parise G.F. ( 1992 ) An econometric analysis of the impact of terrorism on tourism , Kyklos , 45 , 531 – 54 .
Eubank W.L. Weinberg L.B. ( 1994 ) Does democracy encourage terrorism? , Terrorism and Political Violence , 6 , 417 – 35 .
Faria J.R. ( 2003 ) Terror cycles , Studies in Nonlinear Dynamics and Econometrics , 7 , 1 – 11 .
Findley M.G. Young J.K. ( 2012 ) Terrorism and civil war: a spatial and temporal approach to a conceptual problem , Perspectives on Politics , 10 , 285 – 305 .
Fleck R.K. Kilby C. ( 2010 ) Changing aid regimes? US foreign aid from the Cold War to the war on terror , Journal of Development Economics , 91 , 185 – 97 .
Gaibulloev K. ( 2015 ) Terrorist group location decision: an empirical investigation , Oxford Economic Papers , 67 , 21 – 41 .
Gaibulloev K. Sandler T. ( 2008 ) Growth consequences of terrorism in Western Europe , Kyklos , 61 , 411 – 24 .
Gaibulloev K. Sandler T. ( 2011 ) The adverse effect of transnational and domestic terrorism on growth in Africa , Journal of Peace Research , 48 , 355 – 71 .
Gaibulloev K. Sandler T. ( 2014 ) An empirical analysis of alternative ways that terrorist groups end , Public Choice , 160 , 25 – 44 .
Gries T. Meierrieks D. Redlin M. ( 2015 ) Oppressive governments, dependence on the United States and anti-American terrorism , Oxford Economic Papers , 67 , 83 – 103 .
Grossman H.I. ( 1991 ) A general equilibrium model of insurrections , American Economic Review , 81 , 912 – 21 .
Hoffman B. ( 1998 ) Inside Terrorism , Columbia University Press , New York .
Hoffman B. ( 2006 ) Inside Terrorism , rev. edn., Columbia University Press , New York .
Jones S.G. Libicki M.C. ( 2008 ) How Terrorist Groups End: Lessons for Countering al Qa'ida , Monograph MG-741-1, RAND, Santa Monica, CA .
Kaplan E.H. ( 2015 ) Socially efficient detection of terror plots , Oxford Economic Papers , 67 , 104 – 15 .
Keefer P. Loayza N. (eds) ( 2008 ) Terrorism, Economic Development, and Political Openness , Cambridge University Press , New York .
Kollias C. Papadamou S. Arvanitis V. ( 2013 ) Does terrorism affect the stock-bond covariance? Evidence from European countries , Southern Economic Journal , 79 , 832 – 48 .
Kunreuther H. Michel-Kerjan E. Porter P. ( 2003 ) Assessing, managing and financing extreme events: dealing with terrorism , Working Paper 10179, National Bureau of Economic Research .
La Free G. Dugan L. ( 2007 ) Introducing the global terrorism database , Terrorism and Political Violence , 19 , 181 – 204 .
Mickolus E.F. ( 1980 ) Transnational Terrorism: A Chronology of Events 1968–1979 , Greenwood Press , Westport, CT .
Mickolus E.F. ( 1989 ) What constitutes state support to terrorism? , Terrorism and Political Violence , 1 , 287 – 93 .
Mickolus E.F. Sandler T. Murdock J.M. ( 1989 ) International Terrorism in the 1980s: A Chronology of Events , 2 vols. , Iowa State University Press , Ames .
Mickolus E.F. Sandler T. Murdock J.M. Flemming P. ( 2013 ) International Terrorism: Attributes of Terrorist Events, 1968–2013 (ITERATE) , Vinyard Software , Ponte Vedra, FL .
Mueller J. ( 2006 ) Overblown: How Politicians and the Terrorism Industry Inflate National Security Threats and Why We Believe Them , Free Press , New York .
National Consortium for the Study of Terrorism and Responses to Terrorism . ( 2013 ) Global Terrorism Database , available at http://www.start.umd.edu/gtd/ (accessed 25 August 2013) .
Nitsch V. Schumacher D. ( 2004 ) Terrorism and international trade: an empirical investigation , European Journal of Political Economy , 20 , 423 – 33 .
Phillips B.J. ( 2014a ) Terrorist group cooperation and longetivity , International Studies Quarterly , 58 , 336 – 47 .
Phillips B.J. ( 2014b ) What is a terrorist group? Conceptual issues and empirical implications , Terrorism and Political Violence , doi: 10.1080/09546553.2013.800048 .
RAND . ( 2012 ) RAND database of worldwide terrorism incidents , available at http://www.rand.org/nsrd/projects/terrorism-incidents.html (accessed 3 August 2012) .
Rapoport D.C. ( 1984 ) Fear and trembling: terrorism in three religious traditions , American Political Science Review , 78 , 658 – 77 .
Rapoport D.C. ( 2004 ) Modern terror: the four waves , in Cronin A.K. Ludes J.M. (eds) Attacking Terrorism: Elements of a Grand Strategy , Georgetown University Press , Washington, DC .
Sambanis N. ( 2008 ) Terrorism and civil war , in Keefer P. Loayza N. (eds) Terrorism, Economic Development and Political Openness , Cambridge University Press , New York .
Sandler T. ( 2014 ) The analytical study of terrorism: taking stock , Journal of Peace Research , 51 , 257 – 71 .
Sandler T. Arce D.G. ( 2003 ) Terrorism and game theory , Simulation &Gaming , 34 , 319 – 37 .
Sandler T. Enders W. ( 2008 ) Economic consequences of terrorism in developed and developing countries: an overview , in Keefer P. Loayza N. (eds) Terrorism, Economic Development and Political Openness , Cambridge University Press , New York .
Sandler T. Hartley K. ( 1995 ) The Economics of Defense , Cambridge University Press , Cambridge .
Sandler T. Lapan H.E. ( 1988 ) The calculus of dissent: an analysis of terrorists’ choice of targets , Synthese , 76 , 245 – 61 .
Sandler T. Siqueira K. ( 2006 ) Global terrorism: deterrence versus preemption , Canadian Journal of Economics , 50 , 1370 – 87 .
Sandler T. Siqueira K. ( 2009 ) Games and terrorism: recent developments , Simulation &Gaming , 40 , 164 – 92 .
Santifort C. Sandler T. ( 2013 ) Terrorist success in hostage-taking mission , Public Choice , 156 , 125 – 37 .
Santifort-Jordan C. Sandler T. ( 2014 ) An empirical study of suicide terrorism: a global analysis , Southern Economic Journal , 80 , 981 – 1001 .
Younas J. ( 2015 ) Does globalization mitigate the adverse effects of terrorism on growth? Oxford Economic Papers , 67 , 133 – 56 .
Young J.K. Findley M.G. ( 2011 ) Can peace be purchased? A sectoral-level analysis of aid's influence on transnational terrorism , Public Choice , 149 , 365 – 81 .
Email alerts
Citing articles via.
- Recommend to your Library
Affiliations
- Online ISSN 1464-3812
- Print ISSN 0030-7653
- Copyright © 2024 Oxford University Press
- About Oxford Academic
- Publish journals with us
- University press partners
- What we publish
- New features
- Open access
- Institutional account management
- Rights and permissions
- Get help with access
- Accessibility
- Advertising
- Media enquiries
- Oxford University Press
- Oxford Languages
- University of Oxford
Oxford University Press is a department of the University of Oxford. It furthers the University's objective of excellence in research, scholarship, and education by publishing worldwide
- Copyright © 2024 Oxford University Press
- Cookie settings
- Cookie policy
- Privacy policy
- Legal notice
This Feature Is Available To Subscribers Only
Sign In or Create an Account
This PDF is available to Subscribers Only
For full access to this pdf, sign in to an existing account, or purchase an annual subscription.

U.S. Government Accountability Office
The Rising Threat of Domestic Terrorism in the U.S. and Federal Efforts to Combat It
Domestic terrorism is on the rise. Several attacks have been widely reported in the last few years. For example, in May 2022, a racially-motivated individual shot and killed 10 people in Buffalo, New York. A 2018 attack on a Pittsburgh synagogue left 11 people dead. All but eight states across the U.S. experienced at least one incident of domestic terrorism between 2010 and 2021. And over the last 10 years, domestic terrorism-related investigations have grown by 357%.
Today’s WatchBlog post looks at our new report on the rising threat of domestic terrorism and federal efforts to combat it.

What do we know about domestic terrorism incidents?
Domestic terrorism is generally defined by law as involving criminal acts dangerous to human life on U.S. soil that appear intended to coerce a civilian population or influence or affect the conduct of government.
There were 231 incidents (meaning attacks or plots) that met the definition of domestic terrorism between 2010 and 2021, according to DHS. They occurred across the United States, but the greatest number of incidents occurred in states with major metropolitan areas—such as California (Los Angeles, San Diego, and San Francisco), New York (New York City), and Washington, D.C.
Domestic Terrorism Incidents by State, 2010 through 2021
Why are these attacks happening?
According to DHS, there were 231 domestic terrorism incidents between 2010 and 2021. Of these, about 35% (the largest category) were classified as racially- or ethnically-motivated. These attacks were also the most lethal. For example, in July 2016, a racially-motivated individual killed five police officers in Dallas. More recently, in May 2022, a racially-motivated individual shot and killed 10 people in Buffalo, New York.
Anti-government or anti-authority motivated violent extremism was the second largest category of incidents, and resulted in 15 deaths over the same time period.
There were also domestic terrorism incidents linked to animal rights extremists and abortion-related violent extremists, among other motivations. Animal rights-related incidents did not result in any deaths during this time period; incidents related to abortion-related violent extremists led to 3 deaths.
Domestic Terrorism-Related Incidents by Category, from 2010 through 2021

What is being done to combat domestic terrorism threats?
The FBI is responsible for leading domestic terrorism-related investigations and intelligence efforts involving terrorist activities or plots. The Department of Homeland Security (DHS) tracks terrorism-related incidents, and is responsible for gathering and sharing intelligence on emerging terrorist threats with federal, state, and local governments and private entities.
The federal government has been actively investigating and prosecuting acts of domestic terrorism. The number of FBI domestic terrorism investigations has more than doubled since 2020, and the number of open FBI investigations specifically has more than quadrupled from 1,981 in FY 2013 to 9,049 in FY 2021.
The annual number of federal district court prosecutions and charges has also increased, including a sharp increase in FY 2021 (see chart below). We found that prosecutors charged 1,584 defendants in 1,255 cases in federal district court with crimes that were related to domestic terrorism from October 2010 through July 2021.
Number of Federal Defendants Charged in Domestic Terrorism-Related Cases, October 2010 through July 2021
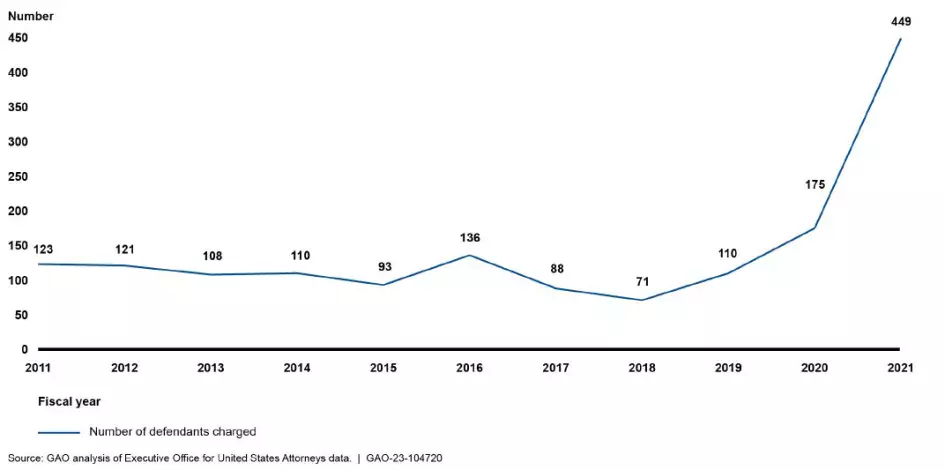
Domestic terrorism and other threats are rapidly evolving, and combatting these threats requires close collaboration between FBI, DHS, and other federal, state, and local agencies.
In our new report , we found that the FBI and DHS generally followed leading collaboration practices—sharing information with each other and their federal, state and local partners. However, they haven’t assessed whether their collaboration agreements fully reflect their needs or how they should work together. Additionally, they did not submit comprehensive data to Congress in required reports. For example, FBI officials told us they did not use the data DHS collects on domestic terrorism incidents because they weren’t aware DHS was collecting it. DHS officials in turn told us they didn’t share their incident data with their FBI counterparts because they weren’t asked for it.
We recommended in our report that FBI and DHS assess their existing collaboration agreements to see if they have a fully integrated way to share information and stop threats. We also recommended that they periodically evaluate the effectiveness of their collaborative practices. Having up-to-date, relevant formal agreements would address some of the concerns officials shared with us, and would make the FBI and DHS better partners to combat domestic terrorism.
Learn more about federal efforts to combat domestic terrorism in our new report .
- Comments on the GAO’s WatchBlog? Contact [email protected] .
GAO Contacts

Related Posts

Vehicle Crash Tests: Do We Need a Better Group of Dummies?

DHS Security Preparations for the January 6 Attack at the Capitol

Building a Border Barrier: the U.S. Army Corps of Engineers’ Contracting Efforts
Related products, domestic terrorism: further actions needed to strengthen fbi and dhs collaboration to counter threats, product number.

GAO's mission is to provide Congress with fact-based, nonpartisan information that can help improve federal government performance and ensure accountability for the benefit of the American people. GAO launched its WatchBlog in January, 2014, as part of its continuing effort to reach its audiences—Congress and the American people—where they are currently looking for information.
The blog format allows GAO to provide a little more context about its work than it can offer on its other social media platforms. Posts will tie GAO work to current events and the news; show how GAO’s work is affecting agencies or legislation; highlight reports, testimonies, and issue areas where GAO does work; and provide information about GAO itself, among other things.
Please send any feedback on GAO's WatchBlog to [email protected] .
Mobile Menu Overlay
The White House 1600 Pennsylvania Ave NW Washington, DC 20500
FACT SHEET: National Strategy for Countering Domestic Terrorism
On his first full day in office, President Biden directed his national security team to lead a 100-day comprehensive review of U.S. Government efforts to address domestic terrorism, which has evolved into the most urgent terrorism threat the United States faces today. As a result of that review, the Biden Administration is releasing the first-ever National Strategy for Countering Domestic Terrorism to address this challenge to America’s national security and improve the federal government’s response.
Domestic terrorism is not a new threat in the United States, yet it is a threat Americans have endured too often in recent years. The comprehensive strategy provides a nationwide framework for the U.S. Government and partners to understand and share domestic terrorism related information; prevent domestic terrorism recruitment and mobilization to violence; disrupt and deter domestic terrorism activity; and confront long term contributors to domestic terrorism. Our approach will protect both the nation and the civil liberties of its citizens.
Under Federal law, “ domestic terrorism ” is defined as “activities that involve acts dangerous to human life that are a violation of the criminal laws of the United States or of any State; appear to be intended to intimidate or coerce a civilian population, to influence the policy of a government by intimidation or coercion, or to affect the conduct of a government by mass destruction, assassination, or kidnapping; and occur primarily within the territorial jurisdiction of the United States.”
The review was rooted in an expert assessment of the domestic terrorism threat provided by the intelligence and law enforcement communities. An unclassified summary of that assessment was released in March so the public could see the key findings. It found that the two most lethal elements of today’s domestic terrorism threat are (1) racially or ethnically motivated violent extremists who advocate for the superiority of the white race and (2) anti-government or anti-authority violent extremists, such as militia violent extremists.
To develop a government-wide strategy to counter domestic terrorists, the Biden Administration consulted extensively with a wide array of experts across the U.S. Government as well as with leaders in Congress, state and local governments, academia, civil society, religious communities, and foreign governments. Throughout the process, we embraced the protection of civil rights and civil liberties as a national security imperative . The strategy we are releasing today is carefully tailored to address violence and reduce the factors that lead to violence, threaten public safety, and infringe on the free expression of ideas. It is organized around four pillars – the core elements of how the Biden Administration will improve the U.S. Government’s response to this persistent, evolving, and lethal threat to our people, our democracy, and our national security:
PILLAR 1: UNDERSTAND AND SHARE DOMESTIC TERRORISM-RELATED INFORMATION
The U.S. Government will enhance domestic terrorism analysis and improve information sharing throughout law enforcement at the federal, state, local, tribal, and territorial levels, and, where appropriate, private sector partners. The Department of Justice (DOJ) and Federal Bureau of Investigation (FBI) have implemented a robust system to methodically track domestic terrorism cases nationwide. The Department of State as well as the intelligence and law enforcement communities are learning more from foreign partners about the international dimensions of this threat.
The Department of State will continue to assess whether additional foreign entities linked to domestic terrorism can be designated as Foreign Terrorist Organizations or Specially Designated Global Terrorists under relevant statutory criteria. The Department of the Treasury, in coordination with law enforcement, is exploring ways to enhance the identification and analysis of financial activity of domestic terrorists. The Department of Homeland Security (DHS) is enhancing its analysis of open-source information to identify threats earlier and will create a structured mechanism for receiving and sharing within government credible non-governmental analysis.
PILLAR 2: PREVENT DOMESTIC TERRORISM RECRUITMENT AND MOBILIZATION TO VIOLENCE
Drawing on the expertise of a variety of departments and agencies, the U.S. Government has revamped support to community partners who can help to prevent individuals from ever reaching the point of committing terrorist violence . The U.S. Government will strengthen domestic terrorism prevention resources and services . For the first time, the Department of Homeland Security (DHS) has designated “Domestic Violent Extremism” as a National Priority Area within the Department’s Homeland Security Grant Program, which means that over $77 million will be allocated to state, local, tribal, and territorial partners to prevent, protect against, and respond to domestic violent extremism. DHS and FBI are working to strengthen local prevention, threat assessment, and threat management frameworks. The Department of Defense (DOD) is incorporating training for servicemembers separating or retiring from the military on potential targeting of those with military training by violent extremist actors. The U.S. Government will improve public awareness of federal resources to address concerning or threatening behavior before violence occurs.
The U.S. Government will augment its efforts to address online terrorist recruitment and mobilization to violence by domestic terrorists through increased information sharing with the technology sector and the creation of innovative ways to foster digital literacy and build resilience to recruitment and mobilization. The United States also recently joined the Christchurch Call to Action to Eliminate Terrorist and Violent Extremist Content Online , an international partnership between governments and technology companies that works to develop new multilateral solutions to eliminating terrorist content online while safeguarding the freedom of online expression.
PILLAR 3: DISRUPT AND DETER DOMESTIC TERRORISM ACTIVITY
The work of Federal law enforcement as well as our state, local, tribal, and territorial law enforcement partners is critical to countering domestic terrorism. The U.S. Government will increase support to Federal, state, and local law enforcement in addressing domestic terrorism nationwide . U.S. Attorney’s Offices and FBI field offices across the country have formally made domestic terrorism a top priority and are tracking comprehensively domestic terrorism-related cases, reallocating or requesting appropriate funding and resources as needed to target the threat. That includes over $100 million in additional resources for DOJ, FBI, and DHS included in the President’s Fiscal Year 2022 Budget to ensure that the Federal Government has the analysts, investigators, prosecutors, and other personnel and resources it needs to thwart domestic terrorism and do justice when the law has been broken. State, local, tribal, and territorial law enforcement will have access to increased intelligence sharing and training on domestic terrorism and associated threats. DOJ is closely examining whether new legislative authorities that balance safety and the protection of civil liberties are necessary and appropriate. The U.S. Government is improving employee screening to enhance methods for identifying domestic terrorists who might pose insider threats . The Office of Personnel Management will consider updates to the forms used to apply for sensitive roles in the Federal Government that could assist investigators in identifying potential domestic terrorism threats. DOD, DOJ, and DHS are similarly pursuing efforts to ensure domestic terrorists are not employed within our military or law enforcement ranks and improve screening and vetting processes. Training and resources will be developed for state, local, tribal, and territorial law enforcement partners as well as sensitive private sector partners to enable them to enhance their own employee screening programs and prevent individuals who pose domestic terrorism threats from being placed in positions of trust.
PILLAR 4: CONFRONT LONG-TERM CONTRIBUTORS TO DOMESTIC TERRORISM
Every component of the government has a role to play in rooting out racism and bigotry and advancing equity for all Americans. The U.S. Government, in close partnership with civil society, will address the long-term contributors that are responsible for much of today’s domestic terrorism. This includes reducing and protecting Americans from racial, ethnic, and religious hatred, and stemming the flow of firearms to individuals intending to commit acts of domestic terrorism. We will work to ensure that law enforcement operates without bias in countering domestic terrorism and provides for the public safety of all Americans. In a true democracy, violence cannot be an acceptable mode of seeking political or social change .
The U.S. Government is committed to strengthening trust in American democracy and its ability to deliver for the American people, including through relief and opportunity provided by the American Rescue Plan, the American Jobs Plan and the American Families Plan. The U.S. Government will also work to find ways to counter the polarization often fueled by disinformation, misinformation, and dangerous conspiracy theories online , supporting an information environment that fosters healthy democratic discourse.
In implementing this strategy, and at the direction of President Biden, we will remain focused on addressing violence and reducing the threat of violence while vigilantly safeguarding peaceful expression of a wide range of views and freedom of political association.
Stay Connected
We'll be in touch with the latest information on how President Biden and his administration are working for the American people, as well as ways you can get involved and help our country build back better.
Opt in to send and receive text messages from President Biden.
528 Terrorism Essay Topic Ideas & Examples
⁉️ how to write a terrorism essay: do’s and don’ts, 🏆 best terrorism topic ideas & essay examples, 🥇 most interesting terrorism topics to write about, ⚡ shocking terrorism essay topics, 📌 simple & easy terrorism essay titles, 👍 good essay topics on terrorism, 💡 interesting topics to write about terrorism, ❓ terrorism essay questions.
Current-day problems, from global warming to human rights, continue to be a topical subject, urging students to address acute issues.
However, this relatability means that you, as an essay writer, may find yourself faced with conflicting facts and circumstances, which your inherent bias may affect.
Thus, a terrorism essay becomes not merely an academic endeavor, but an attempt to immerse yourself in contemporary issues with a multitude of opinions.
- Research and outline your subject beforehand. This process will not only save your time but also help you structure your thoughts and arguments coherently.
- Use tools, such as topic sentences and brainstorming techniques, in the prewriting phase of your paper. Doing so will help you understand how you would like to develop your central theme.
- Start compiling a bibliography early on. When many different viewpoints exist, creating a structured argument in favor of a particular approach may require a wide array of supporting book and journal titles.
- Give a historical overview of your issue. For example, if you are writing about global terrorism, then it is apparent that a worldwide network of violent radicals did not come into existence overnight. Acknowledge and explain the origins of your assigned issue.
- Read other’s sample essays. This action will help you gain a better understanding of what works and what does not in terrorism essay topics.
- Use terrorism essay quotations. Since this is a contemporary issue, then there are bound to be many people involved in activities to counter terrorism, survivors of attacks, and general onlookers. Utilize their perspectives and memories to give your essay a unique touch.
- Remain respectful throughout your paper. Recognize the gravity of your essay and understand the privilege you have when writing about ideas that you may not have experienced.
- Write your essay with no references. Despite watching TV coverages, listening to critics, and reading tabloids, none of us are experts on war or terrorism. Always cite the sources of your information to uphold the integrity of your work.
- Plagiarize from the work of others. While you may read essays written by your peers or those that are available online, directly copying from them is an academic offense.
- Go off point. If you are writing about the history of Al Qaeda, do not disintegrate your work into a how to stop terrorism essay. However, you may give some points in your conclusion on how the overall situation may be amended.
- Write controversial terrorism essay titles. While your title should be catchy and grab your readers’ attention, you should not resort to cheap tactics to make your headings memorable by shock value. Remember that your audience may perceive this tactic as making light of your subject, thus destroying your hard-earned credibility.
- Try to advocate for a pro-terrorist approach. While it is a sound idea to subvert some essay topics, this is not the case in such papers and your work should always be against terrorism.
- Integrate examples from unreliable sources. While readers are often less informed than the essay’s writer is, the opposite may also occur. Therefore, always check the facts, which you include in your work, to avoid embarrassment.
- Draw out your essay to stress the seriousness of the subject. Use your instructor’s specified word count as a measure for how much you should write. Your readers will not appreciate a long-winded paper, as they are hoping instead to get a quick and concise introduction to an important problem.
Want to get more inspiration on terrorism essay topics? Head over to IvyPanda!
- “To Any Would-Be Terrorists” by Naomi Shihab Nye While trying to address the extremist audience, the writer resorted to the strong methods of personification to be able to talk straight to each reading the letter. Despite the character of the text, the writer […]
- Cause and Effect of Terrorism There are several effects of terrorism that are destructive in the nature. The effects are destruction of properties, loss of lives and decline in the economy of a country.
- Analyzing the Concept of Terrorism It is worth noting that a clear definition of terrorism is mostly subjective and is rarely objective due to the fact that it is an act of political violence.
- Terror in “The Dumb Waiter” Play by Harold Pinter Pinter exemplifies the existential view of the absurd and the non-existence in The Dumb Waiter in the same manner as that employed in Waiting for Godot by Beckett.
- An Analysis of Terrorist Activities The main terrorist attack of al Qaeda was the 9/11 Bombing of the World Trade Centers, claiming the lives of thousands of people and leading to the beginning of the War on Terror.
- Human and Technical Intelligence in Countering Terrorism The application of technical intelligence for the public good has to prioritise on several factors including human welfare in assisting the authorities in detecting and combating terrorism.
- Eco-Defense and Kinds of Ecological Terrorism Two basic practices of tree spiking exist; spiking the tree at the bottom of the tree trunk, and spiking the tree way above the trunk, as high as one can reach.
- The Psychological Explanation of Terrorism Therefore, most psychologists argue that in the quest to underpin the possible causes of terrorist activities, there is the need to discriminate between the motivations for joining, being retained, and disserting terrorist factions.
- What Makes Terrorism Different From Other Forms of Violence The purpose of this paper is to define terrorism and identify the crucial features that distinguish terrorism from different types of abuse.
- Analysis of a Domestic Terrorist Group and Homeland Security Policies The Boogaloo Movement is a severe menace, and the government must take all necessary measures to put a stop to it, it is concluded.
- Suspected Terrorist Interrogation and Use of Torture Regardless, torture is still popular across the globe, and it has elicited a new debate questioning whether it is immoral and unacceptable to use torture in the case of efforts to fight terror in the […]
- Terrorism, Corruption, and Climate Change as Threats Therefore, threats affecting countries around the globe include terrorism, corruption, and climate change that can be mitigated through integrated counter-terror mechanisms, severe punishment for dishonest practices, and creating awareness of safe practices.
- Problems the US Faced in the Prosecution of the International Terrorists Differentiating a potential extremist from the rest of the population has been challenging because most international criminals interact with civilians and become part of them.
- Terrorist Impact on Maritime Transportation Security Notably, the United States established the Transportation Security Administration under the Department of Transportation, which was soon transferred to the newly formed Homeland Security Department.
- International Terrorism: Waves and Countermeasures The concept of modern terrorism emerged in Russia, and after a decade, it spread to Western Europe, the Balkans, and Asia.
- The Nexus of Homeland Security and Terrorism The Department of Homeland Security is one of the several bureaucracies formed to tackle the issues of rising insecurity due to external powers and potential facilitators within the US.
- The Future and Change of Terrorism As a result, even if terrorists get their hands on these weapons, they might hesitate to use them on individuals because of the associated implications.
- The Terrorist Attack Recovery Process Terrorism response strategies and the recovery process vary according to the scope of damages and the implications of the methods used in the terror attacks.
- Preparing for a Potential Terrorist Attack The ultimate aim of preparedness is to limit exposure to adversities during and after a terrorist attack. Thus, a recommended approach to limiting the potential security hazard of terrorist attacks is assessing its attributes and […]
- Role of Terrorism in Russo-Ukrainian War Due to this factor, one of the most influential and widespread typologies of terrorism is the New Terrorism that emerged after the tragedy of 2001 in the USA.
- Anti-Terrorism Clarification Act of 2018 Therefore, the current policies are a response to existing problems, and as the problem inside the country has become smaller, the reaction has also decreased.
- Role of Media in Terrorism and Its Force Multipliers The following passages describe the role of the media in terrorism, how terrorists use laws to their advantage, the concept of asymmetrical warfare, and force multiplier as they apply to terrorism.
- Anti-Terrorism Security Complex for Civil Aviation It is expected that the increase in the number of flights in the absence of a strengthened anti-terrorist culture should also lead to an increase in the number of unintended consequences of such flights – […]
- Terrorism: Goals and Strategies Their main purpose can range from changing the direction of the politics in the state to overthrowing the exciting government and establishing control over the population.
- Religious Terrorism: Ideologies and Methods of Al Qaeda and ISIS Strict adherence to the recorded practices and sayings of the Prophet in the letter of the Koran is emphasized. It endorses the rationalization of terrorism and violence in the efforts to fight against infidels.
- Principles of Leadership and Future of Terrorism At the present time, leadership is presented in various forms; however, the primary objectives of the model generally include the improvement of organizational performance and the enhancement of the relationships between the members.
- The 2012 Tel Aviv Bus Bombing and Crisis Management Musa was the manufacturer and detonator of the bomb, which he used Mafarji to deliver inside the Tel Aviv-based commuter bus.
- Terrorism: The Role of Social Media This paper will discuss the role of the internet in terrorist activities, with a focus on social media. In the electronic age, terrorists use social media for recruitment, training, public terror, and action.
- The Role of the Military in Domestic Terrorism Acts The video focuses on the issue of domestic terrorism in the U.S.in light of the January 6th attack on the Capitol.
- Addressing Challenges of Religious Terrorism The various methods used in religious terrorism are spiritual scriptures to justify the violent acts and the use of apocalyptic images of destruction to justify the actions.
- Terrorism and Changes in Police Management Firstly, the police and organizations related to the population’s safety prioritized the prevention of terrorism to minimize the damage. Organizing in the police station involves the creation of organizational structure, points of authority, and responsibilities.
- Terrorists’ Minds and Radicalization Processes Moreover, the models agree that radicalization is a stepwise process in which one stage or step leads to another and eventually reaches the act of terrorism.
- The Terrorism and Oil Industry Relationship Since terrorism is a source of political instability in the world, there is expected to be a positive correlation between oil prices and terrorist attacks. The purpose of this research was to examine the relationship […]
- Understanding the Definition of WMDs and the Constraints on Terrorist Acquisition The most known WMD a nuclear weapon is limited in numbers and difficult to create. The most probable WMD for terrorists to acquire are chemical weapons.
- Online Interventions Addressing Terrorism and Radicalization The study will also identify that the Sakinah campaign can be considered a suitable example of how it is possible to address Internet terrorism and radicalization.
- A Terrorism Attack in the Middle East Countries in the Middle East are prone to terrorist attacks rendering it one of the unsafest regions in the world. The importance of this study is to understand the purpose of terrorist attacks in the […]
- Behavioral Factors of Individual Terrorists The behavior of individual terrorists is dictated by the group dynamics, their mental health, and well-being, as well as the underlying incentives for joining a terrorist organization.
- The Ways Terrorists Raise and Move Money Moreover, the government has put into action the freezing orders and blocking of united states individuals who are presumed to have a hand in terrorist activities.
- Terrorism and Transnational Organized Crime as Threats to Homeland Security The US is among the nations that have suffered some of the worst terrorist attacks worldwide and it is also a hub of international criminal activities due to its wealth of resources and powerful economic […]
- Planning for Terrorist Events: Case Study To review the response of France’s forces and evaluate its efficiency To provide several recommendations for the prevention of attacks during the FIFA World Cup 2022 in Qatar Terrorist attacks that took place across Paris […]
- Global Impact of 9-11 Events on Terrorism Prevention Many people resorted to religion and faith, and the majority reported that they were praying more frequently. Moreover, it stimulated the intervention in Iraq and Afghanistan to fight terrorist groups.
- September 11, 2001 Attacks: What We Have Learned About Terrorism Since 9,11 The world has remembered one of the most tragic attacks in the USA in 2001, and the consequences of this event stay one of the most discussed.
- Global Counter-Terrorism Strategy One of the most serious problems of modern political society is the threat of terrorism, which, due to globalization, requires the unification of the international community.
- The Case of Saudi Arabia’s Soft Counter-Terrorism Strategy Therefore, this assessment is essential for government agencies, consulting organizations, and society in general, since innocent people suffer from the consequences of terrorism.
- Terrorism Prevention: Operation Geronimo Intelligence briefings had been vital in this operation, and there was sufficient evidence to show that the wanted terrorist was in the compound. In conclusion, the operation was a necessary undertaking in ensuring international peace […]
- Trump Tells Story About Killing Terrorists With Bullets Dipped in Pigs’ Blood The text reflects on Donald Trump’s recollection of the myth that terrorists were killed before the bullets used were dipped in pig blood.
- US Strategy From the Cold War to the Post-Global War on Terrorism Before the collapse of the United Soviet Socialist Republic in 1991, the United State’s strategy during the Cold War era had been one of deterrence to the potential threats of the USSR and its allies […]
- Analysis of the Terrorist Organizations: “Red Brigades” and “Boko Haram” The most famous action in the organization’s history is the abduction and murder of the former Prime Minister of Italy Aldo Moro in the spring of 1978.
- Tools Required to Intercept and Obstruct Terrorism in the US The very first section of this act is devoted to strengthening the internal security of the population of the States in the framework of countering terrorism.
- Countering Terrorism Through Innovative Approaches The vital issue of this meeting became the issue of the technological development of international terrorism, its rapid growth in the online world, and acquaintance with the most recent technologies.
- Iran’s Involvement in Sponsoring Global Terrorism Due to the particular features of the theocratic regimes, in the case of Iran, the inclination towards terrorism can be explained by two pillars of the Islamic doctrine underlining the constitution.
- Criminalistics: Forensic Science, Crime, and Terrorism These writings can be on the second, third, and so on pages, depending on the pressure on the writing subject, that is, a pen or pencil.
- Terrorism: the Victim of Terrorism and of Mechanisms to Combat It The Concept of Terrorism: Unlawful act Broad interpretations Threatening lives Generic term of terror Caused by forces opposed to the state Sociopolitical
- Countering Terrorism and Preventive Measures Considering the events of the past century, including the first and 9/11 bombing of the World Trade Center in 1993 and 2001, United States Embassy in Beirut and Kuwait bombing, and many other attacks, the […]
- Why Terrorism Is Not a Serious Threat to International and National Security We accept the existence of this threat, but we are still sure terrorism narrative as an existential threat is doing more damage to a larger amount of people than local terroristic attacks.
- Biowarfare and Bioterrorism: History and Origin According to Edmond and William, the dawn of bioterrorism dates back to the nineteenth century, when Louis Pasteur and Robert Koech studied and understood the basics of microbiology. Moreover, another application of biological weapons is […]
- Response to a Hypothetical Terrorist Event Prior to explicit action, the first thing to do in such a situation is to assess the environment depending on the location of terrorists and the type of attack and to outline the civilians that […]
- Biological Warfare and Agro-Terrorism However, the most important thing from which those infected with botulism die is paralysis of the respiratory muscles and the respiratory failure that follows. The bacteria Bacillus Anthracis, which causes anthrax, is one of the […]
- Terrorism Impacts on Policing in Belgium Nevertheless, when studying the world experience of countries facing the threat of high extremist activity and falling victim to attacks by militant fanatics at the beginning of the 21st century, the Belgian government has strengthened […]
- Researching of Morals of Terrorists Terrorism attacks are a form of violence, and the moral implication is death in the form of revenge. Realism is a form of acceptance that everyone on the battlefield is a civilian with their families.
- The Structures, Motivations, and Qualities of Terrorist Groups This implies that the structures of terrorist groups are determined by the capacity and character of the government and society where they operate.
- The Functionalism Theory Assumptions of Terrorism The functionalism theory echoes the candid assumptions of terrorism and further resonates with the evolving terrorism threat. As Barkan outlines, the functionalism perspective postulates that terrorism creates social bonding and solidarity within societies at war.
- Terrorism: Cargo and Passenger Screening To avoid such events, security systems need to be improved by the management both in the field of technological equipment and in the training of professionals.
- The United Kingdom’s Strategy for Countering Terrorism The objectives of this strategy are the prevention of radical manifestations in the fields of labor, law, politics, science and education, culture and sports, communication, and healthcare. In addition, it is characterized by legal information […]
- Motivations of Lone-Wolf Terrorists The phenomenon of lone-wolf terrorism is an interesting one because it challenges one to attempt to understand the motivation of a person to commit a violent criminal act knowing of the severe consequences.
- Public Policy Issue: Domestic Terrorism At the same time, proponents of the policy argue that the rise of domestic terrorism is due to the failure of holding accountable and confronting the perpetrators by the responsible authorities and not a case […]
- Radicalization and Terrorism in the United States The individuals or self-proclaimed bombers are one of the major threats that the USA will have to be on the lookout for most of the time.
- America: Racism, Terrorism, and Ethno-Culturalism The myth of the frontier is one of the strongest and long-lived myths of America that animates the imagination of the Americans even to this day.
- Domestic, Transnational, and Maritime Terrorism All types of terrorism are based on the forcible imposition of a worldview, ideology, morality, politics using violence, threats of murder or other forms as the primary means of achieving goals.
- “Terrorism” Is a Biased Term According to Bin Ladin, the bombing of the World Trade Center was an intimidation technique targeting the Americans due to the violence against the Islamic community.
- Terrorism and Data Mining Algorithms However, this is a necessary evil as the nation’s security has to be prioritized since these attacks lead to harm to a larger population compared to the infringements.
- Cyber-Terrorism and International Interventions Most of the cyber-attacks that have occurred involve the direction of the malware and attacks to specific critical systems and Information Technology infrastructures.
- Terrorism and Media Coverage In that regard, the issue of media coverage is specifically important to consider in situations involving hostages, as the media either covering a news report or responding to the terrorists’ demands is in a position […]
- Airfreight Security Breaches and Terrorism The majority of terrorist attacks happened after the 1990s, thereby indicating the deterioration of the security system and breaches in it.
- Terror and Religion One of the common religious terror activities has been on martyrdom, the practice of causing death to oneself on the basis of being a witness to ideological and theological perspectives and beliefs.
- Encryption, Stenography & Cyber Criminal Terrorist The internet and the ICT system as a whole are vulnerable to cyber attacks. This is the method of using to trademark to protect our images and copyright on our intellectual properties.
- Radicalization and Terrorism Phenomena A precursor to radicalization and terrorism is the lack of proper socio-political integration of certain communities in countries. Radicalization lies at the heart of terrorism and plays a central role in the propagation of ideas.
- Boko Haram Terrorist Organization: History and Facts Since the inception of the organization in 2002, the primary goal of Boko Haram has been to impose Islamic rule in Nigeria by promoting a version of the religion that forbids participation in any social […]
- Local Efforts to Counter the Terror Threat in New York City The program encompasses a series of both current and future policy efforts that are associated with the private sector security as well as counterterrorism in the state.
- Cyber-Terrorism and Healthcare Information Systems – Past, Present, and Future The cyber appliances in the health sector then again sustain correspondence amongst shareholders and service providers and as well support resources management.
- Bioterrorism Response by Healthcare Organizations Bioterrorism is a frequently used term that proves human responsibility on the development of its outcomes and effects on people and other living beings on Earth.
- Response to Terrorist Attacks: The Role of Military and Public Sector Entities Nevertheless, to understand the basis of such partnership, one has to understand the actions that the public sector takes and has taken to respond to terrorism in the United States and globally.
- Terrorism: What Is It and How to Counter It? Counterterrorism is one of the goals of international cooperation and is an activity aimed at preventing and combating terrorism. One of the most important areas of action is also to prevent the radicalization of both […]
- Emergency Operations in Case of Radiological Terrorism An excellent example of an explosion that profoundly affected the Americans is the 9/11 attack that led to the destruction of the Twin Towers and the Pentagon.
- Command Structure of Sharing the Information About Possible Acts of Terror Following the infamous events of 9/11, the government of the United States introduced new strategies and roles that have continued to reshape the roles and involvement of law enforcers in cases of terrorism.
- Bio-Terrorism: When Microbes Become a Threat to Human Existence In general, due to the cooperation of scientists, policymakers, and public agencies across the globe, the international community has recognized the potential of biological weapons and is prepared for the majority of threats.
- How Terrorism Impacts the Human Experience From the point of view of modern definitions or attempts to define these phenomena, the difference is most often established in the globality of the character, duration of the act, and the number of actors […]
- Annotated Bibliography About Terrorism This is a book review article written by Khanna on the book “Terrorism as a war” written by Walter Laqueur and published by Continuum Books.
- Cyberterrorism, Competing Factions, and Possible Course of Action Various aspects can be analyzed concerning cyberterrorism, competing factors, and possible course of actions in corporations to show that cyberterrorism is a legitimate option for the expression of grievances by terrorists.
- Importance of Emergency Response to Terrorist Attack According to the scenario presented, it makes sense to involve the DoD since the terrorists, supposedly AWOLs, pose an extreme threat to the lives of civilians and the military.
- National Response to Terrorism & Natural Disaster The National Response Framework governs the national security and crisis response to dynamic emergencies and natural disasters that occur in the community.
- Terrorism: Definitions, Features Shared by Terrorists However, since there is no agreed-upon definition of a terrorist attack, it is possible to state that some incidents were omitted from the statistics. Terrorism is difficult to combat and requires the input of international […]
- Alienation and Solidarity: The Logic of Suicide Terrorism Pape’s “The Strategic Logic of Suicide Terrorism” discusses the growing prevalence of suicide attacks in the arsenal of terrorist movements from 1980 onward.
- Terrorists and Their Rights Under US Laws The key problems of the research are the ways in which Islamists are protected by the US legislation and society, where the threat comes from, and what the consequences might be.
- Anti-Terrorism Protocol and Counter-Terrorism Units The 1995 Tokyo sarin attack is a case in point because it proved the real possibility of such a scenario and was used as the reference for the L.A. First of all, as shown in […]
- Oklahoma City Bombing as Domestic Terrorist Act The federal building housed the offices of various government agencies, including the Bureau of Alcohol, Tobacco, and Firearms, which was directly involved in the Waco debacle. The attack allowed McVeigh to send a message to […]
- Foreign Fighters and Contemporary Terrorism Finally, recruiters have received access to the vulnerable groups directly, which is demonstrated in the book In the Skin of a Jihadist written by an investigative journalist Anne Erelle.
- Terrorist Attacks: Paul Hanson vs. Patrick Crusius He made some preparations in the form of stockpiling weapons and researching the locations in which they reside. Crusius was more discrete in his information gathering, though it was still the failure of the FBI […]
- Terrorism Liaison Officer’s Responsibilities The analyst was involved in the assessment of the case and contributed to false-positive reporting regarding the journalist and other civilians being terrorists.
- Domestic Security Agencies and Cyberterrorism Thus, it can be concluded that terrorism and cyberterrorism have become one of the many global challenges, and for this reason, they should be the object of close attention to the world community.
- Terrorism in the United States of America The group might disintegrate in the future because of its dwindling number of followers, leadership wrangles, and a lack of finances to fund its activities.
- Identifying Terrorism-Related Situations In the selected setting of Philadelphia, the general environment appears to be in control, yet further measures may need to be undertaken to prevent the instances of protests from reaching a state of havoc.
- Task Force and the Fusion Center: Terrorism Prevention Thus, it can be argued that the main task of JTTF in targeted violence prevention is crime investigation and intelligence generation.
- Fusion Centers: The Role in Terrorism Prevention Boston Globe reports that the information-sharing system currently in use is not efficient in preventing terrorism, highlighting the fact that the FBI and the CIA probes of Tamerlan Tsarnaev were unbeknown to Massachusetts counterterrorist units.
- DHS and Intelligence: Terrorism The organization of the fight against terrorism requires a comprehensive approach to the analysis of the sources and subjects of terrorist activity, a clear definition of the functions and areas of responsibility of each item […]
- The Molly Maguires as a Domestic Terrorism Group It is these origins of the Molly Maguires terrorist group that gave them their thirst for blood and led to the killing of a myriad of Irishmen until the group was exterminated in the proximities […]
- Australian Anti-Terrorism Laws In the quest to protect citizens, some governments have gone to the extend of inflicting torture on terror suspects in need to obtain some information from the suspect, which raises concern about the suspect’s civil […]
- Bioterrorism Preparedness and Public Health Response Therefore, the current state of the preparedness cannot be estimated as high or sufficient, and the approach needs to be elaborated.
- Aggressive Behavior Among the Al-Shabaab Terrorists The former are the underlying sources that propel susceptible individuals to radicalization, while the latter are the incentives that the terrorist groups offer to attract and retain recruits.
- War on Terrorism: Budget and Policy Discussion The discussion of the specific Acts and Policies directed at USA security is going to be considered with the purpose to follow the changes which occurred in the USA after 9/11 attacks.
- Criminology: Terrorism–Security Policy for Large Events This attack proved to the government the vulnerability of the state concerning external threats, especially because, prior to the attack, the customary means of attack had been the use of military force as evidenced in […]
- Causes of Terrorism Terrorism is defined as violent actions that are aimed at instilling fear to people as a means of coercing them to submit to ideologies of a certain group.
- Violent Resistance and Terrorism The following study is an attempt to establish the root causes of violent resistance, the challenges facing the world due to violent resistance, and possible remedies to the problem citing specific cases that are helpful […]
- Terror Groups – Abu Nidal Organization Abu Nidal is the Arabic meaning of ‘father of the struggle.’ The terror group was named after its leader and founder Sabri al-Banna who was born in Palestine to a land owning family. Among the […]
- Impacts of Terrorism on Police Mission in the U.S. The incidence of September 11 2001 has remarkably transformed the police force in the U.S. There is an increase in the level of monitoring of international travels and boundaries by the police force.
- Homeland Security: Digital Crime and Terrorism Activities However, the US law enforcement system is characterized by the activities of different agencies, including the Federal Bureau of Investigations, Department of Homeland Security, Secret Service, Immigration and Customs Enforcement.
- Understanding the Basics of Terrorism On the other side of the rail is another man lying flat on the ground with a sniper rifle in his hands ready to wreak havoc.
- “Policing Terrorism” by Waddington He is of the argument that case-specific policing is focused on the outcome of court verdicts. He points out an incident in which the palace security was breached, and the commissioner of police reacted to […]
- Definite Paths to Terrorism: Main Dimensions This assimilation is enforced by the use of violence to instil discipline and loyalty in the participants. In conclusion, there are other dimensions of the Islamic terrorism namely Al-Qaeda and Hezbollah.
- War on Terror: Propaganda and Freedom of the Press in the US There was the launching of the “Center for Media and Democracy”, CMD, in the year 1993 in order to create what was the only public interest at that period. There was expansive use of propaganda […]
- Terrorism and U.S. National Security Thomas Jefferson was the author of the Statute of Virginia for religious freedom in the year 1777 as well as the author of the famous United States Declaration of independence in the year 1776.
- Domestic Terrorism Trends: Challenges of the Coming Years Under the provisions of the US PATRIOT act, acts of domestic terrorism entail dangerous acts that pose a threat to human life and amount to a violation of various criminal laws of the US and/or […]
- Organizations Convincing to Become a Suicide Terrorist One of the underlying tenets taught to candidate suicide bombers is: “Islam is the answer and jihad is the way”. Pathological altruism refers to any behavior or personal tendency in which ‘the goal or motivation […]
- Bioterrorism: Term Review According to Meinhardt, “water supplies and water distribution systems represent potential target for terrorist activity in the United States because of the critical need for water in every sector of our industrialized society”.
- US & UK Human Rights While Countering Terrorism The threat of terror and the further legal reactions of the nations to the problem were considered as challenging, and it is necessary to examine differences and similarities associated with the promotion of human rights […]
- Organizational Change: Models Influencing American Terrorism This paper seeks to discuss the three models of terrorism, the effects of international terrorism locally, and the impacts of international terrorism on local cell groups.
- The Goal of a Terrorist Attack This objective is being accomplished by the mean of exposing people to the graphic accounts of terrorist acts-in-making, as was the case with the attacks of 9/11.
- Local Response to Terrorism Local response to terrorism involves using the resources and the law enforcement officers at the state and county level to detect and prevent acts of terror.
- Adjusting to Terrorism: The Issue of Detention Without Trial The country also needs to train more prosecutors and legal experts so that justice is disseminated to suspected terrorists who continue to be held at Guantanamo Bay without trial.
- Biological Terrorism: Dealing With the Threat It is therefore the responsibility of the recipient of this information to take action to secure his/her life against the potential lethality of the agent in question.
- The Maritime Terrorism Risk and Liability The research describes in detail aspects of maritime terrorism but does not clearly state the research question to be explored. However, in the summary part of the research paper there is several questions implied as […]
- Bioterrorism Preparedness in Healthcare Organizations It is also necessary to carry out a test on the public health emergencies for this would help the department to be aware of the strengths and weaknesses which are in the system.
- Adjusting to Terrorism In the US, the Department of Homeland Security is the primary body that deals with all matters of homeland security, including the prevention of terrorism. As such, the department needs to address it as a […]
- Impact of Terrorism on the Economy The premise of the essay is to evaluate the nature and the nature and the severity of the risks posed by terrorism on IFAD a United Nations specialized agency.
- A Criminal Justice Approach to Suppressing Terrorism The threat of terrorism substituted communism as the rationale which was used for justifying the state of emergency in America prior to 1990s.
- Comparison Between Organized Crime And Terrorism Organized crime refers to unlawful activities conducted by members of highly organized gangs and associations. Its defined by members and activities of a group.
- Boilover: Fire Aspects of the World Trade Center Terrorist Attacks Analysis These includes the intensity of the incident heat on the burning object, the composition of the burning fire, the ability of air that supports combustion to reach the burning fire, the mass of the burning […]
- Secure Transportation System Against Global Terror The good news is that cooperation, coordination, and new technology can be used to secure the global transportation system and halt the activities of terror groups.
- Sharing Terror Data: Criminal Analysis The FBI continuing investigation of the attacks to identify the hijackers and their sponsors, codenamed “PENTTBOM,” represents the largest investigation ever in the history of the agency.
- Torture and War Towards Terrorism An example of mental torture can be explained by the following; Y is a friend to X, they have been caught in the same crime act, Y is then taken to a separate room adjacent […]
- Women and Terrorism Relations The role of women in secular terrorist organizations has been more pronounced in history due to the conservative nature of religious terrorist movements, which often exclude women from their ranks.
- Investigation Methods: Terrorism and Cyber Crime The question on whether the investigations in these areas of cyber crime and terrorism to remain incident driven or to adopt strategic approach are still is of great concern to the security agencies and the […]
- Terrorism: Assessing the Past to Forecast the Future The terrorists groups all over the world, having the knowledge of lethargic weapons held by their enemies, are engaged in the discoveries of how the rapidly growing technology may improve the lethargy of their current […]
- Terrorism Response Strategy The preliminary assessment is performed on the basis that before implementing any rescue operations, the hazards that are contained in the area must be positively identified and the resources available or necessary to deal with […]
- Homeland Security and Terrorism The important root causes of terrorism are mainly two: a perceived sense of social & political injustice such that the group seeks to right the wrong and, the view that violence is the only way […]
- Terrorism Preparedness and Response The third and most important step to take is to switch off the available electrical gadgets to prevent the spread of fire. Of importance to prevent such catastrophes is cooperation from citizens, media, and the […]
- Terrorism Mitigation and Risk In order to avert the danger of possible portable nuclear attacks, it is important to assess the possibility and impact of attacks in the first place.
- Terrorism Risk Assessment: Threat of Al Shabaab and Hezbollah to the USA Attacks such as those that happened outside the US and more are likely to occur due to what Hezbollah perceives as the US posing a threat to its ties with Iran.
- Four Priorities of Action for Combating Terrorism on Our Shores There is therefore the need to employ new pragmatic foreign policy steps that promote the national interest within the broader values of international peace and security if any gains are to be realized in the […]
- The Cyber Terrorism Plan and Counter Strategy The news of hacking the website of the Pentagon will immediately get the attention of the media and this message will spread everywhere at the speed of light.
- The Potential for State Sponsored Terrorism Also, he mainly tries to bring all the enemies of the United States together and he believes that the United States is a devilish country.
- Bioterrorism and Biosecurity The epidemiology of the infection is spread in the world evenly though in some of the parts there is only one form of Anthrax, for instance in the United States of America and therefore our […]
- Bioterrorism and Biosecurity – Aum Shinrikyo The Aum Shinrikyo began their attacks in 1994 in Matsumoto where they used the refrigerator truck to release sarin near the homes of three judges who were overseeing a lawsuit that was predicted to go […]
- Terrorism: A Definition and Analysis The Federal Bureau of Investigation defines terrorism as the perpetration of violence and force unlawfully against people or property with a sole aim of intimidating or coercing the government or the targeted population or any […]
- International Political Economy, Democratization, and Terrorism IPE describes the global power dynamics that control international trade and finance, fuel globalization, and wealth distribution across the globe. Sachs argues that globalization and the emergence of political economics have led to the increased […]
- Terrorism Definition at the National Level The development of a unified definition of terrorism at the global level is challenging because the domestic laws of several countries differ significantly.
- War and Terrorism in the Modern World They are used to frighten the public and pursue political goals, for example, to change the government in the country. For instance, acts of terrorism are meant to inflict fear and intimidation to put pressure […]
- Sociology. Terror and Violence Impacts A comparison between theory and the actual case is made in order to promote the claim that terror leads to mental health issues that will pursue the victims for the whole life, but such consequences […]
- US and Terrorism Relations Overview The US and its allies intensified attacks on ISIS bases and areas of control, assassinated ISIS leaders, reclaimed regions captured by the group, cut off their supply of funds, and imposed restrictions on travel to […]
- Agro-Terrorism: Definition and Impacts The ultimate objective for agro-terrorism is to cause economic damage and lead to loss of confidence among the population in the government. It is the responsibility of the FDA and DHS Agro division to monitor, […]
- Terrorism and Trauma in American Literature
- War on Terror: The Battle Continues
- Terrorism Nowadays: Islamic State of Iraq and Syria
- How Terrorism Affects Airline Security
- Terrorist Networks as a Threat to the United States Today
- Consequence Management and Terrorist Attacks Analysis
- Terrorist Groups’ Establishment: The Theory of Four-Wave Terroristic Groups
- Homeland Security: Terrorism Issue
- Domestic & Global Terrorism and Its legal Aspects
- Crime Myths and Domestic Terrorism
- Terrorist Attacks in Paris, 13th November 2015
- Hue Newton: A Terrorist and a Thinker
- Impact on Terrorist Activities of Regional Governments
- Regional Terrorism: The Bali Bombing, Australian and Indonesian Responses
- How to End Terrorism: Diplomacy or Military Action?
- Terrorism: Methods and Weapons
- Terrorism: Analysis of Definitions
- Screening for Terrorist for Aviation Security
- The Role of Hashemite Kingdom of Jordan in the Fight Against Terrorism
- Terrorist Event Countering: First Responders Risk
- Financing Terrorism: Challenges and Solutions
- Hashemite Kingdom of Jordan and Terrorism
- Domestic Terrorism: Burning Social Issue
- Al Shabaab: An Intriguing Example of Islamist Terror
- Causes and Motivations of Terrorism
- Ali Al-Timimi’s Case of Terrorism
- “The Lessons of Terror: A History of Warfare Against Civilians” by C. Carr
- Biological and Chemical Terrorism: Preparedness and Response
- Legislation Related to Bioterrorism
- Israel’s Response to Munich Terror Attack
- Bioterrorism and Its Harmful Consequences
- Domestic Terrorism in USA
- The Evolution of Terrorism on the World Stage
- Terrorism and Liberal Democracy: What We Should Know
- Michael Collins and His Terrorist Method
- Biological Weapon and Bioterrorism
- War and Terrorism in Algeria
- Is Terrorism Still the Most Important Security Issue for Australia?
- Primoratz’ Definition of Terrorism
- War on Terror and Its Effect on Individual Right
- Terrorism and Modern Society
- Terrorism: An Objective Definition
- Crimes Against the State: Terrorist Attacks and Death Penalty
- “Nuclear Terrorism: Risks, Consequences, and Response” by Jim Walsh: Stimulating Ideas, Logical Organization, Engaging Voice
- Origins of Terrorism and Solutions
- Terrorists R’ Us: Different Perspectives, the Real Meaning
- Middle-East and Africa Terrorist Movements
- Terrorism in Western Europe: Finland, Denmark and England
- Most Effective Anti-Terrorist Tactics, Organizations in the World
- The History of Ku Klux Klan: A Terrorist Organization Founded in the Southern States After the American Civil War
- The Use of Counter-Terrorism Attacks During the Algerian War of Independence From F.L.N.
- History and Financing of Terrorism: From Time Immemorial to Nowadays
- Comparison Between Secular and Religious Terror
- The Origins of Modern Terrorism
- Cultural Reaction of English Civilians Against Terrorist Situations in Their Country
- Political Violence and Terrorism. Crowd Behavior
- Domestic Terrorism: The Forgotten Threat
- Is Terrorism an Act of War?: Different Types of Terrorism
- Types of Terrorism: Centers Establishment
- Sociology of Terror: Contemporary Sense
- Anti-Terrorists Tactics and Organizations
- Understanding the War on Terror in the United States
- Foreign Policy Challenges Created by the War on Terror
- The Threat of International Terrorism in Modern World
- Middle-Eastern and African Terrorist Movements
- Terrorist Organizations and Funding
- Terrorist Recruitment Process: Who Joins and Why
- Should the U.S. Use Torture on Terror Suspects?
- Nigeria – Preventing Nuclear Terrorism
- Terrorism Impact on Global Business Environment
- Bioterrorism: Impact of Science and Technology
- Terrorism. Irish Republican Army
- Community Policing and War on Terror
- Biosecurity and Bioterrorism
- Terrorism Today and Its Definition
- Religious Violence. Terror in the Mind of God by Juergensmeyer
- Terrorism and U.S. Foreign Policy by P. R. Pillar
- Palestinian Islamic Jihad: Radical Terrorism
- Money Laundering and Terrorist Finance
- Pakistan’s Double Game in the War on Terror
- Eradicated Terrorism in the World
- The Interrelation Between Terrorism and Technology
- War on Terror & Violation of Constitutional Rights
- Media and the War on Global Terrorism
- Is the Geneva Convention Applicable to War on Terror?
- Adjusting to Terrorism in Modern World
- Death Sentence to Muslim Terrorists: Should We Murder People Who Had Done the Same Before?
- How the US is Dealing with Terrorism?
- Terrorism and Security Issues Review
- “Terrorism in Latin America” by Mark Sullivan
- How Terrorist Have Financial and Recruitment Growth Since 1980
- Effects of the September 11, 2001 Terror Attacks on Sino-American Relations
- Recent Developments in the History of Terrorism
- War on Terrorism: Role of Law Enforcement
- Current Issues in Iraq and Terrorism
- War on Terror. 42-Day Detention: An Equitable Solution?
- Early Response to Weapons of Mass Destruction Terrorism
- Terrorism and the Affects on American Way of Living
- Counter Terrorism Measures in the UK
- The War on Terrorism in the United States
- United States & EU Efforts to Fight Terrorism
- Global Terrorism and State Security Measures
- American Governmnet Against the Threat of Terrorism
- Terrorism: 9/11 Conspiracy Theories
- Trends in Global Terrorism. Conflict Resolution and Iraq
- “Terrorism and Economic Security” by Robert L. Hutchings
- The War on Terror Cannot be Won
- Bioterrorism and Health Care Delivery
- Terrorism and Weapons of Mass Destruction
- Terrorism: Countering and Responding to the Treat
- Crimean Crisis and Russian State Terrorism
- Cyberterrorism as a Global Concern
- The United States and Terrorism
- Anti-Terrorist New York City Police Department Shield
- Terrorist Ideologies: Selecting a Target
- A Terrorist Attack on Atlanta, Georgia
- How Counselors Assist Survivors of Terrorism
- Fraud, Money Laundering, and Terrorism Financing
- Comprehensive Terrorist-Related Screening Procedures
- Terrorism and National Security
- Terrorism and Security Dilemma After 9/11
- International Law: Extradition of Terrorists
- The Functioning of Terrorist Groups
- Suicide Terrorism and Its Psychological Factors
- Terrorist Organization: Euskadi Ta Askatasuna (ETA)
- The Great Terror in the Factories, 1935–1938
- Workers During “The Great Terror” by R. Conquest
- “Terror and Democracy at the Age of Stalin” by Goldman
- Female Gender Role in “The Terrorist” Film
- Terrorism Studies and Framing Concept
- Terrorism as Spectacle: Extremist Propaganda
- Terror in the Mind of God by Mark Juergensmeyer
- Counter Terrorism and Public Awareness Plan
- Terrorist Organization Hezbollah: Tactics and Strategies
- The Hezbollah Terrorist Organization
- Terrorism, Social Activism and Political Violence
- “Faces of State Terrorism” by Laura Westra
- Organized Terrorism Against Government Leaders
- War on Terror and Its Victory Meaning
- Terrorism Definitions by the Global Community
- Islamic Terrorism in Ridley Scott’s “Body of Lies”
- Can Terrorism Only Be Defeated by Military Means?
- Terrorism Impact on Tourism Industry After 2015
- Terrorist Attack: Contemporary Social or Cultural Issues
- Poverty as a Factor of Terrorist Recruitment
- War on Drugs and Terror and American Promise
- Hazard Vulnerability Analysis and Terrorism
- Terrorist Participation and Its Motives
- The UAE Against Money Laundering and Terrorism Financing
- Cyberterrorism as the Greatest Risk for the US
- Cultural Miscommunication and Hostility Against Muslims
- Domestic Terrorism and Homegrown Extremism in America
- The Rise of Terrorist Organisations in Post-Invasion Iraq
- Factors That Motivate to Terrorism
- Domestic Terrorism in the United States of America
- State-Sponsored and Non-State Terrorism
- Terrorism, Human Trafficking, and International Response
- Internet Crimes and Digital Terrorism Prevention
- Vietnam War vs. War on Terror in the Middle East
- Immigration Services Against Crime and Terrorism
- Ideology and Terrorism: Rights from Wrongs?
- Islamic and Christian Religion and Terrorism
- American War on Terror and Operational Strategies
- Death Penalty for Murder by Terrorism
- Local Operational Planning for Potential Terrorist Threats
- Preventing Terrorism: Strategies and Challenges
- Terrorism, Hate Crimes and Racial Profiling
- Terrorism Preventive Measures in the United States
- Aum Shinrikyo Terrorist Group’s Activity
- Bioterrorism Attacks and Nursing Countermeasures
- Intelligence, Civil Law, and Terrorism Investigations
- Terrorism Prevention on the International Level
- Psychological Profiling in Terrorism Prevention
- Terrorism Definitions and Controversies
- Violent Extremism and Suicide Terrorist Attacks
- Al-Qaeda Emergence, Ideology, and New Terrorism
- Terror Attacks and Intelligence Community in the US
- Distressed Terrorism: Politics, Religion and Ideology
- Terrorism or Hate Crime: Similarities and Differences
- War on Terror: Critical Terrorism Studies’ Views
- Egyptian Tourism Industry and Terrorism Effects
- Terrorism and US Activities in the Middle East
- Islamic State Global Terror Threat Countermeasures
- War on Terror in Saudi Arabia and Arab Gulf States
- Saudi Arabian Lone Wolf Terrorism in 2011-2016
- Terrorist Groups: Critical Discourse Analysis
- War on Terror in Central Asia and the Caucasus
- US Intelligence to Prevent Terrorist Attacks
- Terrorism: Power of the Islamic State of Iraq and Syria Power
- Female Terrorism: Causes and Features
- Terrorism: the Evolution of ISIS
- Cyber Security’s and Counter Terrorism’ Intersection
- What Are the Global Impact of Terrorism in Business Domain?
- East African Community Counter-Terrorism Vision
- Terrorism and Torture: History and Arguments
- How Does Modern Terrorism Operate?
- Digital Media Usage to Recruit and Promote Terrorism
- Modern Terrorism and Globalization
- Stereotyping Terrorists and Mental Sanity
- Homeland Security Changes: Adjusting to Terrorism
- Propaganda: Terrorist, Government, State, Non-State
- Paternalist Terror in China in 1950-1953
- China in 1950-53: “Paternalist Terror” by J. Strauss
- Terrorist and Government Propaganda in Media
- Human Trafficking as a Terrorist Activity
- Coping with Terrorism in the USA
- Terrorism in the Middle East
- Contemporary Terrorism: The American Army Special Forces
- Conventions on Terrorism in the 21st Century
- Countering Terrorism: The US Intelligence Community
- Terrorism and Its Organisations: Al Qaeda and ISIL
- First Responders to Terrorist Attack
- Violence and Terror Definition Comparison
- The Westgate Terror Attack in Kenya
- Fighting Terrorism: “Iraqi Freedom” and “Enduring Freedom”
- Terrorist Organizations: Al-Qaeda and ETA
- Current Hurdles in Combating Terrorism
- Ethnic, Racial and Religious Profiling in Terrorism
- Halal Food and Terrorist Organizations in Australia
- Osama Bin Laden’s Role in Terror
- Hospitals Security Upgrade: Terrorist or Criminal Actions
- Homeland Security: Basque ETA Terrorist Organization
- International Counter Terrorism’ Elements
- Terrorism: Aspects, Approaches and Implications
- Use of Torture Against Terror Suspects
- Bioterrorism: Biological Agents as Weapons
- Different Methods Against Terrorism: Israel and Palestine
- Terrorism: The Islamic State of Iraq and the Levant
- Terrorism: Post-9/11 Maritime Security Initiatives in the USA
- Bio-Terrorism Preparedness and Response
- Jonathan Moreno: Bioethics After the Terror
- What is the Best Way for Fighting Terrorism According to Mortenson?
- The Advanced Community Planning in Response to the Potential Threat of Terrorism
- The Impacts of the Intelligence Reform and Terrorism Prevention Act of 2004 on the National Intelligence Community
- War on Terrorism: How to Cope With the Global Threat?
- Terrorism and the Global Economies
- The Primary Causes of Terrorist Political Violence
- Terrorism as a Serious Threat
- Rumsfeld’s Memo & The War on Global Terrorism
- Terrorism Handling in Our Life
- Defense Imperatives: “Thwarting Terrorism & Bringing Terrorists to Justice”
- Understanding the Failure of the Global War on Terrorism and Suggestions for Future Strategies
- Counter-Terrorism and the Patriot Act
- Al-Qaeda as a Terrorist Organization
- Financial Markets After Terrorist Assault and The Enron Financial Outrage
- Terrorism, Counter-Terrorism, and Intelligence
- Torture as a Counter-Terrorism Tool in 21st Century
- Lessons From the Mumbai Terrorist Attacks
- Proliferation of Nuclear Weapons to Rogue States and International Terrorists
- Does Poverty Lead to Terrorism?
- Terrorism and Jihadist Movement
- US Exceptionalism in Constructing and Conceptualizing a Terrorist
- American Exceptionalism in Constructing and Conceptualizing a Terrorist
- History of Cyber Terrorism
- “Monsters, Inc.” and the War on Terror
- Economic Concerns in the Aftermath of Terrorism
- Terrorism in International Relations
- Terrorism in Israel and Palestine
- Local, State, and Federal Partnerships: Terrorism
- Hezbollah: A Terrorist Organisation?
- United States Domestic Terrorism
- Impacts of the ‘War on Terror’ on Human Rights
- International Terrorism: The Challenge to Global Security
- Salafist Takfiri Terrorism
- Anti Money Laundering and Combating the Financing of Terrorism
- Weapons of Mass Destruction: The Terrorist Threat
- Terrorists’ Usage of Chemical or Biological Agents
- Cyber Security Threat Posed by a Terrorist Group
- The Effect of Terrorism on Human Rights: The Clash Between the Human Rights Advocates and Victims of Terrorism
- Eliminating Terrorism at the Domestic Level
- Terrorism, Poverty and Financial Instability
- United States War on Terror Policy
- The Real Cause of Terrorism in Palestine
- Terrorism: Searching for a Definition
- Industrial Terrorism in Modern World
- Terrorist Cells and Groups Within the Northern Region of Africa
- Terrorism as a Communication Strategy
- How the U.S. Can Combat the Terrorist Threat in Africa?
- Hypothetical Scenario of a Terrorist Attack
- NYPD Counterterrorism Program
- Terrorism Before and After the September 11 Attacks
- U.S. War in Afghanistan: Pros and Cons
- Orientalist Constructions of Muslim Bodies and the Rhetoric of the «War on Terror»
- Jemaah Islamiyah Terrorist Group
- The U.S. Government Strategies Against the Terrorist Threats
- How Readily Terrorists Can Acquire Nuclear Weapons
- Post September 11, 2001 Terrorist Attacks
- Civil Liberties, Habeas Corpus and War on Terror
- Concept of Terrorism Phenomenon in Modern World
- Handling of Bio-Terrorist Threats
- The Spectacle of Terror
- Foreign Policy: United States and Fight with Terrorism
- Law Enforcement and Terrorism
- What New Demands on Policing Have Resulted From the International ‘War on Terror’?
- Leila Khaled: Freedom Fighter or Terrorist?
- Religious and Secular Terrorism: Analyzing Differences and Points of Intersection
- “Arabic Islamic Culture” and Terrorism: Inherent Concepts or Not?
- Terrorist Acts Prevention and Aftermaths Minimization
- Torture During the Algerian War and Its Relevance on the War on Terror
- The Definition of Terrorism
- International Terrorism: The Operations of the Hezbollah
- The Kurdish Conflict in the Middle East
- The US Anti-Terrorism Efforts Are Failing
- The Media and Terrorism
- Terrorist Groups in Turkey
- Terrorism: The United States’ Involvement
- Terrorism: Can Terrorism Ever Be Justified?
- America’s War on Terrorism
- Terrorism, Its Groups and Categories
- Terrorism in Political Protest
- Impact of Terrorism on Italian Economy
- “What Is the Definition of Terrorism? And Why Is the White House Afraid of Using the Term?” by Timothy Kelly
- Habeas Corpus and the War on Terror
- Civil Liberties, Habeas Corpus and the War on Terror
- Benefits of Preparing for Emergencies and Terrorism
- Preparing for Incidents of Terrorism at the Local Level
- Domestic Terrorism in the Post 9/11 Era
- Bush Doctrine, Explanation of the Administration and War on Terror
- Moral Convictions of Terrorists
- Why Terrorism is a Contested Concept
- Presidential Powers and the War on Terror
- Agro-Terrorism: The Lessons to Learn
- Terrorism: The War on Iraq
- Stereotyping Comparison: All Italians Are in a Mob, All Jamaicans Smoke Weed, All Muslims Are Terrorists
- The Al-Qaida Terrorist Group’s Recent Happenings
- The Fight Against Terrorism by Christian and Islam Leaders
- Is Terrorism Ever Justified?
- The War on Terrorism
- The Terrorist Attacks in the United States
- The Problems of Terrorism in Modern World
- Counter-Terrorism Plans Development
- Consequence Management After the 9/11 Terrorist Attacks
- Intelligence Reform and Terrorist Prevention Act
- Terror and Terrorism
- September 11: Terror Attack and Huge Casualties
- The Concept of Terrorism
- Homeland Security: Collecting Information about Terrorism
- Terrorists and the Left and Right: Definitions & Examples
- Should the USA Use Drones to Combat Terrorism?
- How Are Terrorists Financing Their Acts of Terrorism?
- What Can History Teach Us About Terrorism?
- Why Do Americans Feel More Sympathy for Western Terrorism?
- How Can the United States of America Better Defend Itself Against Terrorism?
- Can the U.S. Prevent Future Acts of Domestic Terrorism?
- What Has Been the Effect of Globalization on Terrorism?
- How Can Businesses Cope With Terrorism?
- Can Democracy Stop Terrorism?
- Should the U.S. Government Be Scared of Cyber Terrorism?
- Why Does Western Europe Experience More Terrorism Than America?
- Are Terrorism and Globalization Linked to Politics?
- What Are the Causes of Terrorism, and How Can It Be Stopped?
- Are Muslim Communities Affected by Counter-Terrorism Legislation?
- Does American Foreign Policy Cause Terrorism?
- Does the Media Encourage Terrorism?
- Does the Terrorism Act Infringe Upon Our Human Rights?
- What Challenges Are Posed by International Terrorism to Democracy?
- How Can the Digital World Lead to a New Type of Terrorism?
- Whose Support Matters for the Occurrence of Terrorism?
- How America Prevents Terrorism?
- Does Higher Education Decrease Support for Terrorism?
- Can Foreign Aid Dampen the Threat of Terrorism to International Trade?
- Should Americans Fear Urban Terrorism?
- Can Illegal Immigration Lead to Terrorism?
- Does Distinguishing Domestic Terrorism From International Terrorism Help?
- Will the American Economy Benefit From the War Against Terrorism?
- Are Some Rights Negotiable When It Comes to Fighting Terrorism?
- Why Has Terrorism Become Such an Important Issue Over the Last 40 Years?
- Will Terrorism Lose Its Significance?
- Chicago (A-D)
- Chicago (N-B)
IvyPanda. (2024, March 3). 528 Terrorism Essay Topic Ideas & Examples. https://ivypanda.com/essays/topic/terrorism-essay-examples/
"528 Terrorism Essay Topic Ideas & Examples." IvyPanda , 3 Mar. 2024, ivypanda.com/essays/topic/terrorism-essay-examples/.
IvyPanda . (2024) '528 Terrorism Essay Topic Ideas & Examples'. 3 March.
IvyPanda . 2024. "528 Terrorism Essay Topic Ideas & Examples." March 3, 2024. https://ivypanda.com/essays/topic/terrorism-essay-examples/.
1. IvyPanda . "528 Terrorism Essay Topic Ideas & Examples." March 3, 2024. https://ivypanda.com/essays/topic/terrorism-essay-examples/.
Bibliography
IvyPanda . "528 Terrorism Essay Topic Ideas & Examples." March 3, 2024. https://ivypanda.com/essays/topic/terrorism-essay-examples/.
- Islam Topics
- Organized Crime Titles
- Islamophobia Paper Topics
- Nuclear Weapon Essay Topics
- Sunni Islam Paper Topics
- Torture Essay Ideas
- North Korea Titles
- Racial Profiling Essay Topics
- Share full article
Advertisement
Subscriber-only Newsletter
David Wallace-Wells
The campus protests signal the end of an era for the democrats.

By David Wallace-Wells
Opinion Writer
Each college had a choice; in most places, they chose to escalate.
At Indiana University, a police sniper was stationed on the roof of a building; at the University of Virginia, they dispersed protesters with pepper spray; at U.C.L.A., it was with rubber bullets; and at the University of Texas in Austin they arrested dozens of students on pretexts so flimsy that the local district attorney threw out all the charges within 48 hours, and then they returned for a second round of arrests a week later.
The two mass arrests at Columbia bookended the rapid escalation: When New York City police officers swarmed the green on April 18, there were hardly any similar encampments anywhere else in the country, and it would have been reasonable to think that campus unrest had peaked back in the fall; but by April 30, when the nation’s largest police force entered occupied Hamilton Hall, something like a national protest movement had sprung up over the course of just two weeks. By May 2, according to The Appeal , a nonprofit criminal-justice news site, there were at least 100 encampments in nearly 40 states, and more than 2,000 protesters had been arrested. In proudly defending the mass arrests in New York, Mayor Eric Adams did not focus on trespassing or the disruption to campus life. What he emphasized instead was the urgent need to literally police an ideological threat. “These are our children,” he said, “and we can’t allow them to be radicalized.”
Almost as soon as the horrifying news of Hamas’ Oct. 7 attacks reached the United States, the country, and especially its media, treated college campuses as a significant front of the brutal war they initiated. This attitude is several kinds of narcissistic, but in its way it is also only natural: Campus conflicts are both more proximate and more personal than the war itself for many Americans; the initial Hamas attack was gruesome, and the Israeli response has been extreme, intensifying the always-fraught domestic politics of the United States’ relationship with Israel; and the spectacle of college protests, which inevitably mix political fervor with adolescent grandiosity and hints of potential generational change, seems almost designed to generate discourse about “kids these days.”
But what has transpired in the aftermath of the first crackdowns on campuses — as protests and counterprotests have grown more intense, with some universities seeking to negotiate with increasingly militant student leaders but most calling the cops instead — is also not just a story about the war in Gaza or a new generational divide. It is also a case study in the dynamics of escalation, and I’d like to emphasize three stories, each related, that may help explain the pattern.
The first is the militarization of American police forces and the rise of what Radley Balko has called the “warrior cop,” especially after Sept. 11 — a period in which, it is important to remember, the United States has gotten vastly safer, but during which law enforcement has nevertheless gotten far more martial, in their weaponry and gear, their tactics and training, and indeed their outward-facing “thin blue line” rhetoric, as well.
The second is the recent turn against all forms of protest, by law enforcement and the public, in the aftermath of the mass climate change marches of 2019 and the Black Lives Matter movement of 2020. Over the last five years, significant legal restrictions on protest have been turned into law globally . Nearly half of American states have also imposed limits; several states have even passed bills granting immunity to drivers who run over protesters, and New York Democrats have proposed a law that would define road-blocking protests as “domestic terrorism.”
But we also hear more and more from critics who believe that any protest that simply inconveniences others has crossed a line to become counterproductive or offensive. Last week, President Biden scolded college students for pitching tents on their quads, warning that “dissent must never lead to disorder” and asserting that “order must prevail.” The House had just passed a bill that could restrict criticism of the state of Israel by labeling it as antisemitic, Nancy Pelosi previously called on the F.B.I. to investigate protesters, and there are some hints that such investigations are ongoing.
And the third is the breaking apart of the ideological alliance, which held relatively firm for about a decade and a half, between the liberal-establishment values of the country’s institutional elite and the progressive values of the country’s social-justice voices. This strange and unstable coalition of left-of-center groups and institutions held for more than a decade and a half, first under Barack Obama — who seemed to many to embody a new kind of “radical establishment” — and then under Donald Trump — who inspired a desperate alliance of big-tent resistance liberalism. The alliance always seemed a bit hypocritical to some skeptics on the left and many critics on the right, but it also represented the basic grammar of liberal power through the long 2010s. If, in 2013 or 2019, you were in charge of, say, Harvard, or Facebook, or the Creative Artists Agency, even Pershing Square Capital Management or The New York Times, it was tempting to believe that you were not just acting as a force for self-advancement and elite reproduction but also delivering social justice in your work and affirming, even advancing, the progressive arc of history.
After Covid, and Biden’s election, and the arrival of an “anti-woke” backlash among a certain class of American elites, that ideological coalition began to splinter, and it is now much harder to pretend that those two sets of values are natural complements, or even two halves of a liberal cultural hegemony. This challenge was confronted by the country’s elite universities late last year, when criticism about how campus administrators had handled anti-Israel protests grew into a larger debate about diversity, equity and inclusion and the structure of the self-styled meritocracy: Would the University of Pennsylvania and Harvard and M.I.T. choose to conduct themselves as avowedly elite institutions, concerned primarily with elevating their own status and the privileged standing of their students, or instead as a democratic force, devoted to reshaping the American leadership class toward criteria other than who performed best on the S.A.T.?
For a time, these goals hadn’t appeared to be in such obvious tension, at least according to the people committed to balancing them, who offered visions of a diversified but meritocratic elite as though they were postcards from an inevitable-seeming virtuous future. But in recent years it has come to seem less workable to have it both ways, and now two of the three college presidents who testified before Congress in December have since been forced to resign under the pressure of that tension. Minouche Shafik, Columbia’s president, testified last month and may soon be on her way out, as well, unable to bridge the gap between the school’s protest-friendly faculty and its apparently horrified donors, or to inoculate the school and its administration against criticism from the likes of Mike Johnson and Elise Stefanik, who just a few years ago would have seemed completely irrelevant figures in any such campus saga.
This is not just a story about college students and universities, elite or otherwise, especially given that many school administrators have effectively de-escalated protests with negotiation . The same pattern has unfolded in the corporate world, with what was near-universal commitment to environmental, social and governance principles, producing in relatively short order a widespread backlash and walk-back, similar to the recent turn against D.E.I. initiatives. There is a growing rift between the Democratic establishment and activist factions, social media companies have retreated from their efforts to shape and define the public square, and legacy media organizations have tried to recalibrate their ideological positioning after going too far, especially in 2020. The “diploma divide” hasn’t stopped growing, with well-educated Americans voting for Democrats by huge margins, but the ideological content of those elite commitments has begun to shift. The war on woke may be fizzling out , but it has already left its mark .
It’s not yet clear what this might mean for the country’s electoral politics. To trust the polls, few Americans seem to care all that deeply about the war in Gaza, despite wall-to-wall coverage of the war itself and the protests about it, and in surveys more people say the response by colleges to those protests has been “not harsh enough” than say it has been “too harsh.” As November pulls closer into view, the old desperate anti-Trump coalition may temporarily solidify again, despite warnings from the left that Biden’s support for Israel’s war might yield mass abstention among young voters. What follows the election is in many ways unsure, but neither outcome seems all that likely to revitalize that resistance coalition, which already looks less like a postcard of the future and more like a prepandemic time capsule.
Beyond elections, cultural politics matter, too, of course, as do the shape and orientation of institutions, and while America’s elite universities are not exactly tilting right, their pretense toward progressivism has been dropped with remarkable speed. Just six years ago, Columbia devoted a semester-long program and a three-day conference to honoring the school’s mythic 1968 protests, and its then-president, Lee Bollinger, called the decision to call in the police to break up that student occupation “a serious breach of the ethos of the university.” Perhaps it is a sign of simple institutional hypocrisy that Bollinger’s successor, one presidential term later, seems so much less ambivalent about deploying actual force against the school’s students, however outrageous or unruly. But it’s also a sign of the times, and how they’ve changed.
Further Reading
New York Magazine turns an entire issue over to the staff of the Columbia Spectator to cover the protests and crackdown. (The Spectator editors also weigh in here .)
Abdallah Fayyad writes in Vox about those colleges which tried to de-escalate (and why more made the other choice).
David Pozen of Columbia Law on what has been revealed about American universities by their response to campus dissent.
Lois Beckett of the Guardian speaks with Annelise Orleck, the former head of Dartmouth’s Jewish studies department, about her own violent arrest.
Branko Milanovic, an economist from CUNY’s Graduate Center, on “universities as factories.”
In the Chronicle of Higher Education, N.Y.U. historian Thomas Sugrue writes about “college presidents behaving badly.”
Columbia’s Adam Tooze reflects , in his Chartbook newsletter, on the “state as blunt force” and his “impressions of the Columbia campus clearance.”
You are using an outdated browser. Upgrade your browser today or install Google Chrome Frame to better experience this site.

- IMF at a Glance
- Surveillance
- Capacity Development
- IMF Factsheets List
- IMF Members
- IMF Timeline
- Senior Officials
- Job Opportunities
- Archives of the IMF
- Climate Change
- Fiscal Policies
- Income Inequality
Flagship Publications
Other publications.
- World Economic Outlook
- Global Financial Stability Report
- Fiscal Monitor
- External Sector Report
- Staff Discussion Notes
- Working Papers
- IMF Research Perspectives
- Economic Review
- Global Housing Watch
- Commodity Prices
- Commodities Data Portal
- IMF Researchers
- Annual Research Conference
- Other IMF Events
IMF reports and publications by country
Regional offices.
- IMF Resident Representative Offices
- IMF Regional Reports
- IMF and Europe
- IMF Members' Quotas and Voting Power, and Board of Governors
- IMF Regional Office for Asia and the Pacific
- IMF Capacity Development Office in Thailand (CDOT)
- IMF Regional Office in Central America, Panama, and the Dominican Republic
- Eastern Caribbean Currency Union (ECCU)
- IMF Europe Office in Paris and Brussels
- IMF Office in the Pacific Islands
- How We Work
- IMF Training
- Digital Training Catalog
- Online Learning
- Our Partners
- Country Stories
- Technical Assistance Reports
- High-Level Summary Technical Assistance Reports
- Strategy and Policies
For Journalists
- Country Focus
- Chart of the Week
- Communiqués
- Mission Concluding Statements
- Press Releases
- Statements at Donor Meetings
- Transcripts
- Views & Commentaries
- Article IV Consultations
- Financial Sector Assessment Program (FSAP)
- Seminars, Conferences, & Other Events
- E-mail Notification
Press Center
The IMF Press Center is a password-protected site for working journalists.
- Login or Register
- Information of interest
- About the IMF
- Conferences
- Press briefings
- Special Features
- Middle East and Central Asia
- Economic Outlook
- Annual and spring meetings
- Most Recent
- Most Popular
- IMF Finances
- Additional Data Sources
- World Economic Outlook Databases
- Climate Change Indicators Dashboard
- IMF eLibrary-Data
- International Financial Statistics
- G20 Data Gaps Initiative
- Public Sector Debt Statistics Online Centralized Database
- Currency Composition of Official Foreign Exchange Reserves
- Financial Access Survey
- Government Finance Statistics
- Publications Advanced Search
- IMF eLibrary
- IMF Bookstore
- Publications Newsletter
- Essential Reading Guides
- Regional Economic Reports
- Country Reports
- Departmental Papers
- Policy Papers
- Selected Issues Papers
- All Staff Notes Series
- Analytical Notes
- Fintech Notes
- How-To Notes
- Staff Climate Notes
Mission Concluding Statement
St. vincent and the grenadines: staff concluding statement of the 2024 article iv mission.
May 8, 2024
A Concluding Statement describes the preliminary findings of IMF staff at the end of an official staff visit (or ‘mission’), in most cases to a member country. Missions are undertaken as part of regular (usually annual) consultations under Article IV of the IMF's Articles of Agreement, in the context of a request to use IMF resources (borrow from the IMF), as part of discussions of staff monitored programs, or as part of other staff monitoring of economic developments.
The authorities have consented to the publication of this statement. The views expressed in this statement are those of the IMF staff and do not necessarily represent the views of the IMF’s Executive Board. Based on the preliminary findings of this mission, staff will prepare a report that, subject to management approval, will be presented to the IMF Executive Board for discussion and decision.
Washington, DC: An IMF staff team, led by Ms. Nan Geng, visited Kingstown during April 23 – May 7, 2024, for the 2024 Article IV consultation discussions on economic developments and macroeconomic policies. The team issued the following statement:
St. Vincent and the Grenadines has achieved a robust recovery from recent compounded shocks, supported by the authorities’ decisive policy responses, large-scale investment projects, and robust growth in tourism. The outlook is favorable but subject to downside risks mainly stemming from the uncertain external environment. In addition, the economy is facing challenges from a rapidly ageing population and the ever-present threat of natural disasters and climate change, amid the still high public debt. Policies need to be calibrated to continue to build buffers and resilience and support sustainable and inclusive growth while safeguarding debt sustainability and financial sector stability.
Recent Developments, Outlook, and Risks
The economy rebounded strongly in 2022-23, returning to pre-pandemic output levels. Growth reached 3.1 percent in 2022 and is estimated to have accelerated to 5.8 percent in 2023. This was supported by large public and private investment and a robust recovery of tourism, which were partly offset by a drop in agriculture due to lingering effects from volcanic eruptions and the historic high temperature in 2023. Stayover arrivals approached pre-pandemic levels in 2023 supported by significant improvement in airlift. Formal employment surpassed pre-pandemic levels in 2022 and is estimated to have continued to grow in 2023, fueled by the recovery in tourism and higher demand in other services. Nevertheless, recent compounded shocks have left a lasting negative impact on employment of young men. As regards public finances, even though non-interest current spending was significantly reduced, the fiscal deficit is estimated to have widened in 2022-23 largely due to the phasing of port-related spending and temporary factors. Public debt declined from its peak in 2021 to about 87 percent of GDP in 2023 but remains well above pre-pandemic levels. The external position improved in 2022-23 supported by recovery in goods exports and tourism receipts.
The outlook is favorable though subject to downside risks. Growth is projected at 4.9 percent in 2024, which implies that economic activity would surpass the level projected for the medium term before the pandemic. Near-term growth will be supported by continued recovery in tourism and strong investment on infrastructure, particularly the port project. Inflation is projected to ease to around 2 percent by end-2024, on account of lower imported inflation. Risks to the outlook stem primarily from an abrupt global slowdown, commodity price volatility, potential delays in investment projects, and the ever-present threat of natural disasters and climate change. On the upside, stronger-than-expected tourism development and agriculture sector recovery could enhance growth and improve the external position.
Support Resilient and Inclusive Growth and Safeguard Debt Sustainability Through a More Efficient Tax and Expenditure Framework
The fiscal stance embedded in the 2024 budget strikes an appropriate balance between maintaining fiscal prudence and supporting inclusive and resilient growth. The government continues to rationalize current spending and build the Contingencies Fund while prioritizing capital spending on reconstruction, essential upgrade and resilience building of economic infrastructure, and health and education investments to propel people-centered and sustainable growth.
The team welcomes the authorities’ continued commitment to reaching the regional debt target and the medium-term fiscal strategy set out in the 2021 Rapid Credit Facility. This includes further strengthening tax administration, continued containment of the growth of wages (as manifested in the prudent public sector wage growth over 2023-25 agreed in the recent round of negotiation) and non-priority current spending, and prioritizing capital programs to balance the needs for a resilient recovery with safeguarding debt sustainability. As such, the primary balance is expected to improve to a surplus of about 3¼ percent of GDP from 2026 once the large-scale projects are near completion. This would put the debt-to-GDP ratio on a downward path from 2025 and, if sustained, reach 60 percent before the regional target date of 2035.
The elevated global uncertainty and the country’s high vulnerability to shocks call for contingency planning and stronger fiscal buffers. The team welcomes the authorities’ adoption of a Disaster Risk Financing Strategy and the ongoing efforts to establish a new Catastrophe Deferred Drawdown Option of US$20 million with the World Bank and contingency budgetary planning for disaster responses and resilience activities. In addition to these efforts, bringing the primary surplus to around 3¾ percent of GDP in the medium term (about ½ percentage above the current medium-term target) would build a safety margin for public debt to guard against risks and meet the regional debt target and debt sustainability with a higher probability.
Continued efforts to build a more efficient and equitable tax and expenditure framework will help create space to withstand shocks and support resilient and inclusive growth. Significant work is underway to improve the efficiency and inclusiveness of public spending and services and should be sustained, including modernizing the social assistance system, digitalizing government infrastructure, platforms, and services, adopting gender-responsive budgeting, and implementing the recommendations from IMF’s Public Investment Management Assessment with a Climate Module (C-PIMA). On the revenue side, the efficiency and progressivity of the tax system can be improved while enhancing revenue by drawing on the comprehensive roadmap for tax reforms from recent IMF technical assistance. The proposed reform roadmap includes enhancing the progressivity and fairness of personal income tax, improving the design of tax incentives and corporate income tax, streamlining value-added tax (VAT), and modernizing recurrent property tax.
Coordinated reforms to the National Insurance Services and Public Sector Pension System (PSPS) are needed to improve their efficiency, sustainability, and fairness. The team welcomes the recently launched pension reform package to bolster the National Insurance Services’ (NIS) financial sustainability in view of the rapid population ageing and the still low contributions compared to generous payouts. Additional measures to ensure NIS’s long-term sustainability and further enhance its efficiency and fairness could be considered, including linking retirement age to life expectancy and applying a uniform accrual rate across years to promote long careers. Reforming the non-contributory PSPS to better align it with the NIS is urgently needed to improve fairness and reduce fiscal costs.
Continued strengthening of fiscal institutions is key to underpin fiscal efforts and reinforce fiscal credibility . The government is stepping up efforts to enhance revenue administration, including through the recent initiative to enforce VAT for private home vacation rentals, modernizing the Customs Act, and digitalizing the tax information management system. The team welcomes the publication of the Fiscal Responsibility Mechanism’s (FRM) first report, pursuant to the Fiscal Responsibility Framework (FRF) adopted in 2020. In view of the tight global financial conditions and still elevated debt level, it will be important to further strengthen the FRF and signal a credible medium-term fiscal plan, including by recalibrating and fully operationalizing the FRF, timely publishing and incorporating forward-looking budgetary advice into the FRM report, improving the budget process and medium-term fiscal planning, and strengthening SOE oversight and the cash management system.
Build Climate Resilience and Advance Structural Reforms to Promote Investment, Employment, and Productivity
Sustained efforts to address supply-side bottlenecks would help unleash a higher growth potential. Ongoing investment on critical public infrastructure, including the port, roads, airports, water supply, and agriculture production, along with the development of sectoral strategies guided by the National Development Plan, is instrumental in alleviating structural bottlenecks, improving competitiveness, and releasing the country’s full potential of comparative advantage on tourism and agriculture. Strengthening linkages with agriculture and fisheries will help increase the domestic value-added of tourism. In addition, with relatively high internet access and low cost, the country is well-positioned to benefit from the ongoing digital transformation of government, business, and financial infrastructure and services. This transformation is expected to enhance productivity and the business environment. Ongoing efforts to streamline the Investment Act and establish single windows for land registration and trade are critical to improve the investment climate.
A well-functioning labor market, with skills attuned to market needs and higher participation, is critical for boosting productivity and employment, especially in view of the rapid population ageing. The team welcomes the establishment of the Prime Ministerial Advisory Council on Youth and the recently launched comprehensive education reform with focuses on curriculum reforms and expansion of post-secondary and technical and vocational education and training, which will help reduce skill mismatches and integrate the youth into the labor market. Recent strengthening of parental leaves would encourage participation and formality and reduce gender gaps. Targeted social investments could further help unleash the full potential of the female labor force, including by enhancing access to affordable and quality child and elderly care and reducing adolescent pregnancy. The team welcomes the planned introduction of a permanent unemployment insurance, but it needs to be carefully designed and complemented by continued strong efforts in active labor market policies to ensure the scheme’s sustainability and achieve the desired labor market outcomes.
Building resilience to natural disasters and climate change remains a priority . The authorities have stepped up efforts to strengthen structural and financial resilience, including by incorporating resilience feature into new infrastructure, adopting a Disaster Risk Financing Strategy, tapping Green Climate Fund, and enhancing the disaster management plan and legislation. Efforts to transition to renewable energy are ongoing, including the introduction of new solar projects and a new revenue-neutral import tax regime to promote cleaner motor vehicles. Ongoing work to modernize the Electricity Act and update the National Energy Policy would help provide an enabling environment to support the transition.
Maintain Financial Sector Stability
The financial system remains sound, but efforts should continue to reduce balance sheet vulnerabilities. Capital and liquidity buffers are ample. Non-performing loans (NPLs) have declined from the 2022 peak and remain below regional averages, with no significant impact from the expiration of the pandemic moratorium. Banks’ profitability has fully recovered to pre-pandemic levels, but provisioning levels—while above the regional average—fall below the new regional requirement and should be bolstered and disposal of long-dated NPLs accelerated. Despite the still relatively small size of credit union loans compared to those of banks, the increasing role of the less stringently regulated credit union sector in credit provision warrants continued vigilance in oversight of asset quality and underwriting standards, especially in the absence of resolution frameworks and financial safety nets.
Building on past achievements, the authorities should sustain the efforts to strengthen regulatory and supervisory frameworks and improve crisis preparedness. Priorities include (i) completing the transition to risk-based supervision, including incorporating climate risks, (ii) adopting amendments to the FSA Act, (iii) establishing a National Crisis Committee to develop a crisis management framework for the non-bank financial sector and deposit insurance schemes in consultation with the Ministry of Finance and the Eastern Caribbean Central Bank (ECCB), and (iv) supporting the establishment of an ECCU regional standards setting body for non-bank financial institutions.
Continued strengthening of the effectiveness of the AML/CFT framework remains important to minimize the risks of losing correspondent banking relationships. The authorities have updated the Anti-Money Laundering and Combating the Financing of Terrorism (AML/CFT) legal framework and started implementing risk-based supervision for some of the higher-risk sectors. Efforts should continue to implement other recommendations of the 2024 Caribbean Financial Action Task Force (CFATF) Mutual Evaluation.
The IMF mission would like to thank the authorities, private sector counterparts and other stakeholders for their warm hospitality and the candid and constructive discussions.
IMF Communications Department
Media relations.
PRESS OFFICER: Reah Sy
Phone: +1 202 623-7100 Email: [email protected]
@IMFSpokesperson

IMAGES
COMMENTS
This Essay asks whether a domestic terrorism statute is necessary in order to achieve charging parity between domestic and international terrorism. If so, what would such a statute look like? ... Domestic Terrorism Penalties Act of 2019, H.R. 4187, 116th Cong. (2019) [hereinafter Weber" Bill"]. 114:1061 (2020)
Introduction. There has been growing concern about the threat of domestic terrorism, with extremists motivated by political, racial, ethnic, economic, health, and other grievances. In October 2020, the FBI arrested Adam Fox, Barry Croft, and several other accomplices in a plot to kidnap and potentially execute Michigan Governor Gretchen Whitmer.
Domestic Terrorism: Overview of Federal Criminal Law and Constitutional Issues Congressional Research Service 2 crime, however, under numerous statutes prohibiting terrorism6 and other types of violent or destructive conduct.7 In addition, domestic terrorism may be relevant to the sentencing of those convicted of federal crimes.8 Any congressional consideration of additional legislation in the ...
The FBI is tasked with leading domestic terrorism-related investigations and collaborates with the Department of Homeland Security's (DHS) Office of Intelligence and Analysis to identify internal threats to national security. The FBI has a growing number of open domestic terrorism-related cases, with a growth rate of 357% from 2013 to 2021.
"domestic terrorism" as "activities that involve acts dangerous to human life that are a violation of the criminal laws of the United States or of any State; appear to be intended to intimidate
On June 15, 2021, the Biden administration released the United States' first-ever National Strategy for Countering Domestic Terrorism, which culminated the 100-day review of U.S. government efforts to respond to domestic extremism that President Biden ordered in January. Though galvanized by the January 6, 2021, attack on the U.S. Capitol, this strategy seeks to understand and respond to a ...
Threats like domestic terrorism, which last posed a threat in the 1970s, are now back and pose a threat to democracy itself in the United States. ... States must take advantage of the next few years to plan and resource the efforts needed to end the current wave of terrorism. READ THE ESSAY. Hyper-tribalism and the domestic terrorism threat ...
Introduction. Since the terrorist attacks of September 11, 2001 (9/11), domestic terrorists—people who commit crimes within the homeland and draw inspiration from U.S.-based extremist ideologies and movements1—have not received as much attention from federal law enforcement as their violent jihadist counterparts.
Public Policy Issue: Domestic Terrorism Essay. The 9/11 terrorist attacks triggered the dramatic escalation of severe and destructive attacks in the country. Although America has intensified its defense, the rise of domestic terrorism is proving to be an urgent public policy issue. Hate and extremist groups are the leading perpetrators of ...
In 2017, there were 10,900 terrorist attacks around the world that killed more than 26,400 people, according to the National Consortium for the Study of Terrorism and Responses to Terrorism (START). [1] The number of terrorist attacks per year in the United States in the post-September 11 era has increased from 33 in 2002 to 65 in 2017. [2]
For domestic acts of terrorism, the perpetrators, victims, and audience hail from the venue country, where the attack takes place. Domestic terrorist incidents include Timothy McVeigh's bombing of the Alfred P. Murrah Federal Building in Oklahoma City on 19 April 1995 or Eric Rudolph's anti-abortionist bombing of Centennial Olympic Park in ...
The September 11 th 2001 attacks involved the crashing of two planes by terrorist jets into the Twin Towers, which led to the collapse of the towers two hours later. The third plane hit pentagon, and the fourth crashed in Pennsylvania (BBC News 2001). This act of terrorism was conducted by the Al-Qaeda, costing over 3,000 lives and leaving many ...
Domestic terrorism is on the rise. Several attacks have been widely reported in the last few years. For example, in May 2022, a racially-motivated individual shot and killed 10 people in Buffalo, New York. A 2018 attack on a Pittsburgh synagogue left 11 people dead. All but eight states across the U.S. experienced at least one incident of domestic terrorism between 2010 and 2021.
The U.S. Government will enhance domestic terrorism analysis and improve information sharing throughout law enforcement at the federal, state, local, tribal, and territorial levels, and, where ...
A person engages in domestic terrorism if they do an act ""dangerous to human life"" that is a violation of the criminal laws of a state or the United States, if the act appears to be intended to: (i) intimidate or coerce a civilian population; (ii) influence the policy of a government by intimidation or coercion; or (iii) to affect the conduct.
George, J., & Wilcox, L. M. (1996). American Extremists. Prometheus Books, P. 44. This essay, "United States Domestic Terrorism" is published exclusively on IvyPanda's free essay examples database. You can use it for research and reference purposes to write your own paper. However, you must cite it accordingly . Donate a paper.
Domestic Terrorism Essay. Domestic Terrorism America is home to people with varied cultural backgrounds who have been confined into one political and geographical territory. These people may have issues and conflicts but still find themselves living together because of shared territorial borders (Zalman, 2013).
Essay on Domestic Terrorism. National terrorism has been the focus of attention since September 11. But now domestic terrorism is becoming increasingly common among hate groups across the nation. Domestic terrorism can be defined as visible crime, or "street crime.". These acts would consist of violent crimes, (acts against people in which ...
Researching of Morals of Terrorists. Terrorism attacks are a form of violence, and the moral implication is death in the form of revenge. Realism is a form of acceptance that everyone on the battlefield is a civilian with their families. The Structures, Motivations, and Qualities of Terrorist Groups.
Domestic terrorism and international terrorism are the two main types of terrorism we deal with in the United States. Domestic terrorism is defined by the FBI as, "violent, criminal acts committed by individuals and groups to further ideological goals stemming from domestic influences, such as those of a political, religious, social, racial, or environmental nature" (FBI, 2016).
Each college had a choice; in most places, they chose to escalate. At Indiana University, a police sniper was stationed on the roof of a building; at the University of Virginia, they dispersed ...
Washington, DC: An IMF staff team, led by Ms. Nan Geng, visited Kingstown during April 23 - May 7, 2024, for the 2024 Article IV consultation discussions on economic developments and macroeconomic policies. The team issued the following statement: St. Vincent and the Grenadines has achieved a robust recovery from recent compounded shocks, supported by the authorities' decisive policy ...